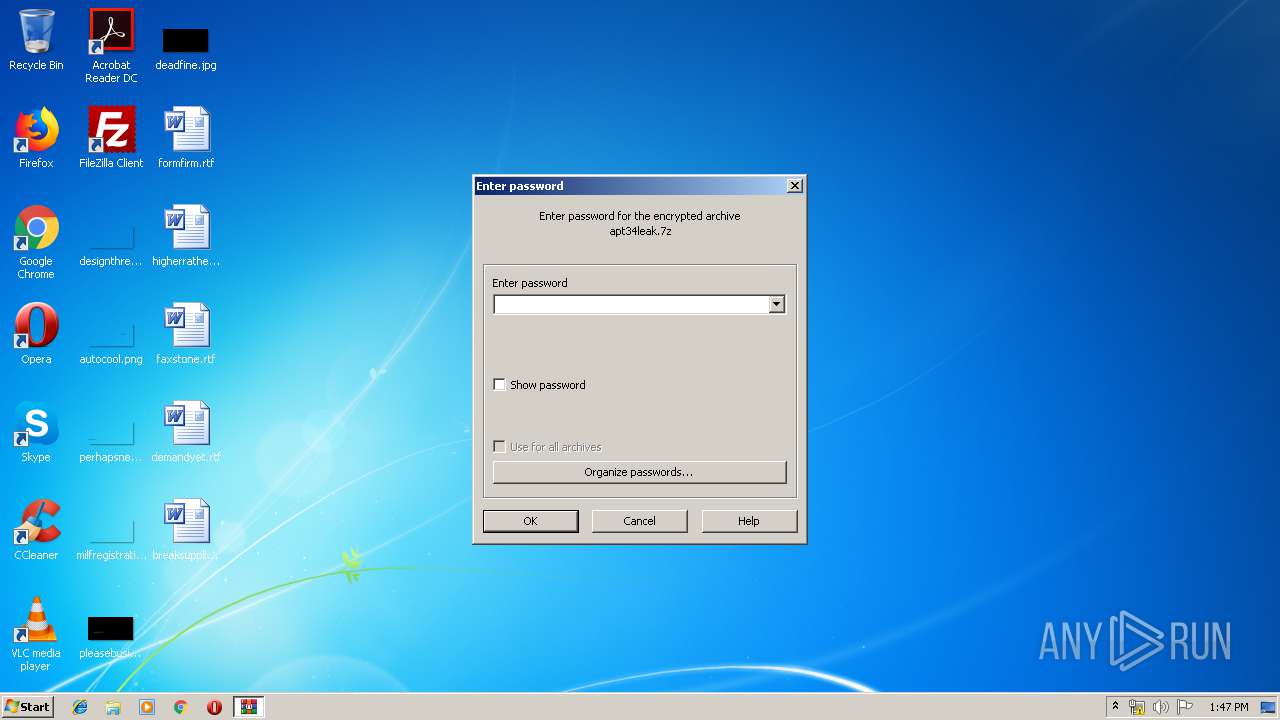
| File name: | apt34leak.7z |
| Full analysis: | https://app.any.run/tasks/febb51eb-3058-458d-9402-7cfe8da25d35 |
| Verdict: | Malicious activity |
| Analysis date: | May 07, 2019, 12:46:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 797B13E4E232028334D95BA03B1CC6AD |
| SHA1: | 068214E5A04CBE454B4689C046770227F5B09C07 |
| SHA256: | 06DE1E67107FDD120F4E97732371698C2AB16640934C7E2AA41034C8EBEC2C87 |
| SSDEEP: | 393216:eePLmaHl9paUtNtZbn2jkrJmI14x+nrSRRm5nuA:e+yMlK4PZyYk4nrSRg5uA |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2564)
Application was dropped or rewritten from another process
- newPanel-dbg.exe (PID: 3356)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3464)
Creates files in the user directory
- powershell.exe (PID: 1688)
- powershell.exe (PID: 3640)
- powershell.exe (PID: 3804)
- powershell.exe (PID: 2432)
- powershell.exe (PID: 584)
- powershell.exe (PID: 1920)
- powershell.exe (PID: 3524)
- powershell.exe (PID: 916)
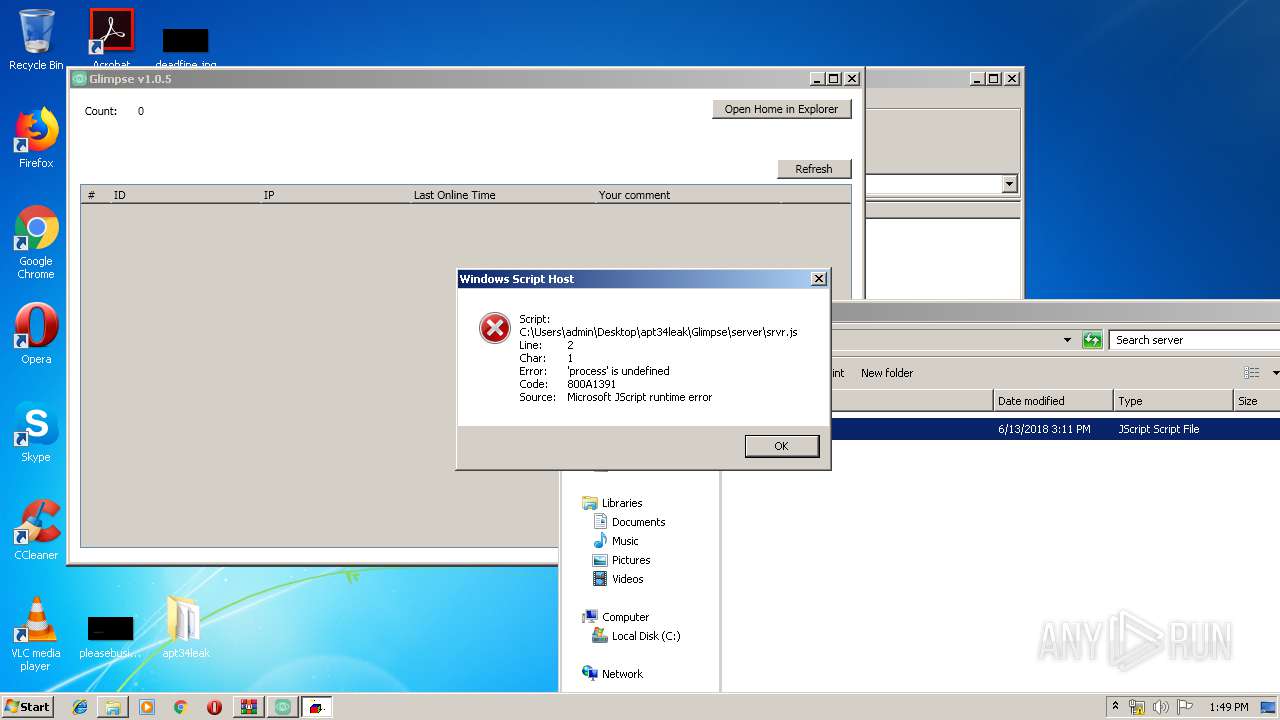
Executes PowerShell scripts
- WScript.exe (PID: 1908)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
64
Monitored processes
16
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: PresentationFontCache.exe Exit code: 0 Version: 3.0.6920.4902 built by: NetFXw7 Modules
| |||||||||||||||
| 584 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -exec bypass -file <AGENT PATH> | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294770688 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
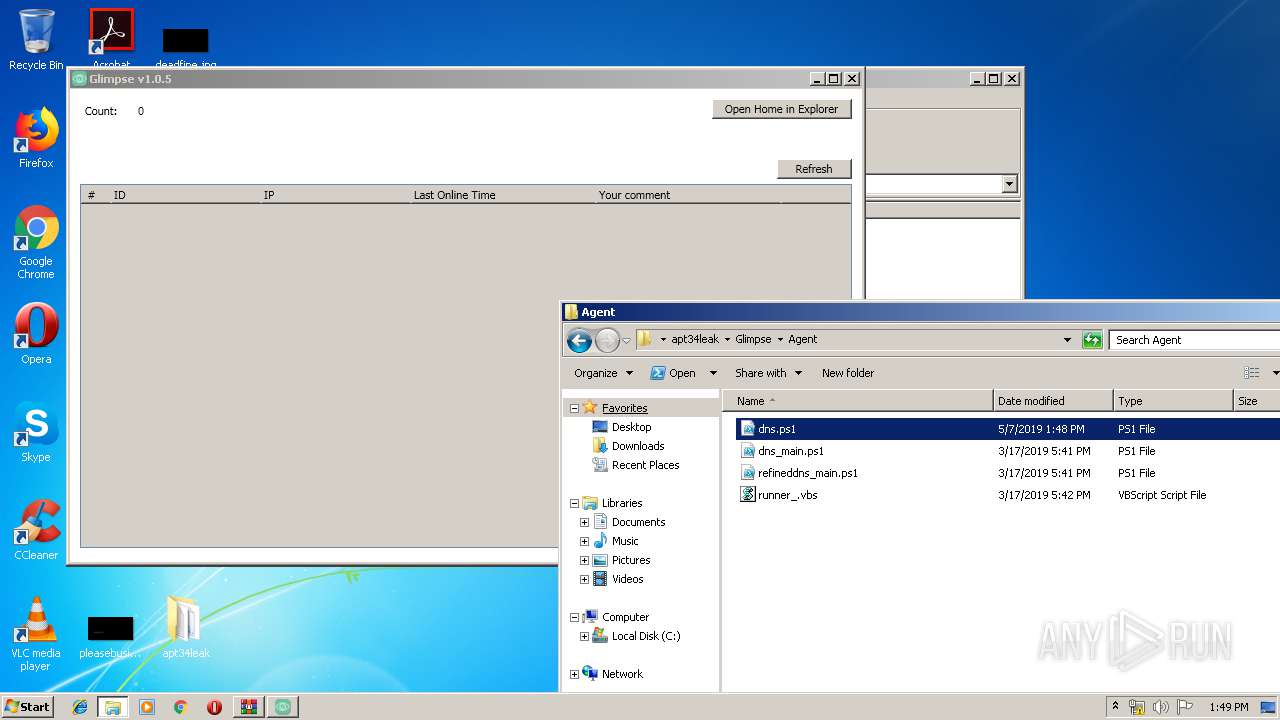
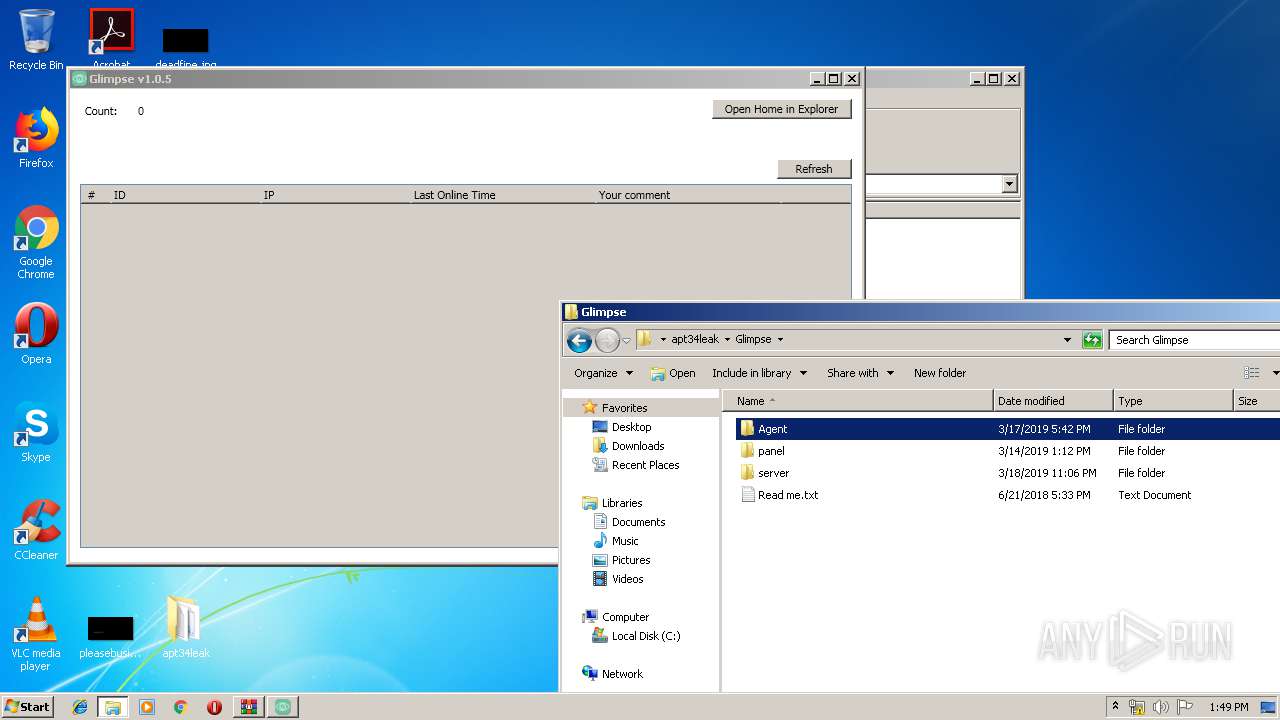
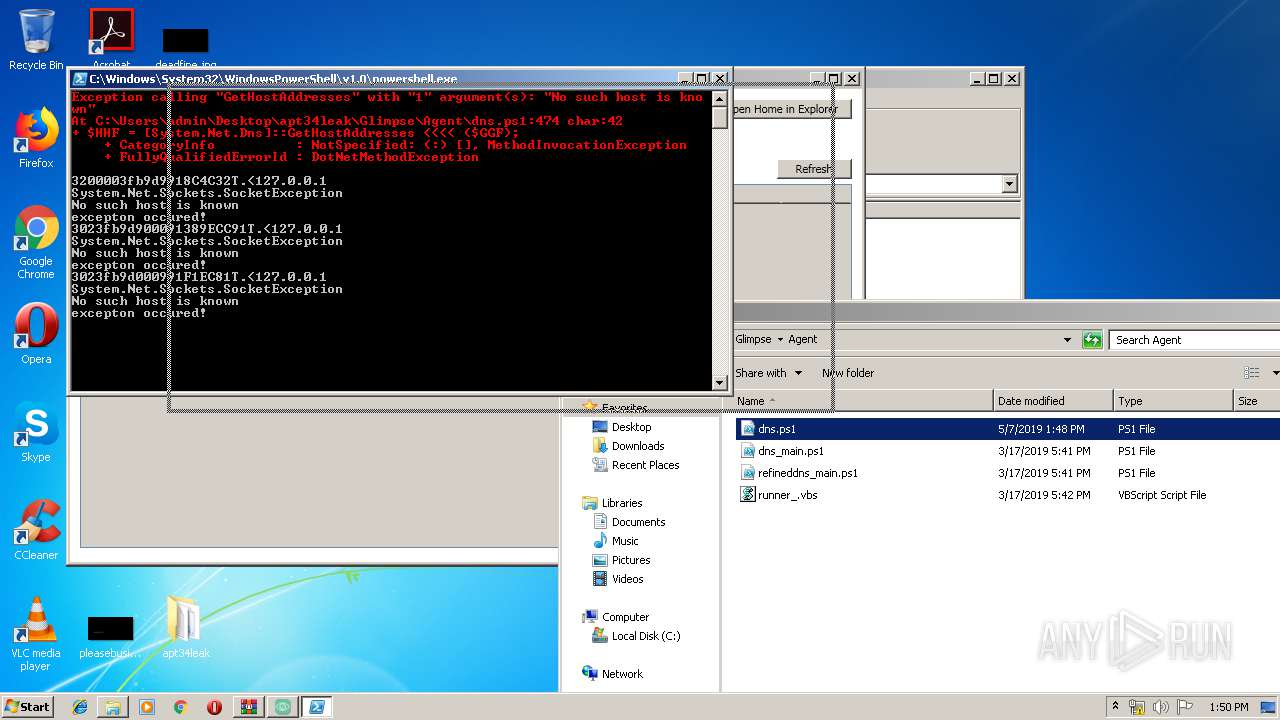
| 916 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\apt34leak\Glimpse\Agent\dns.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
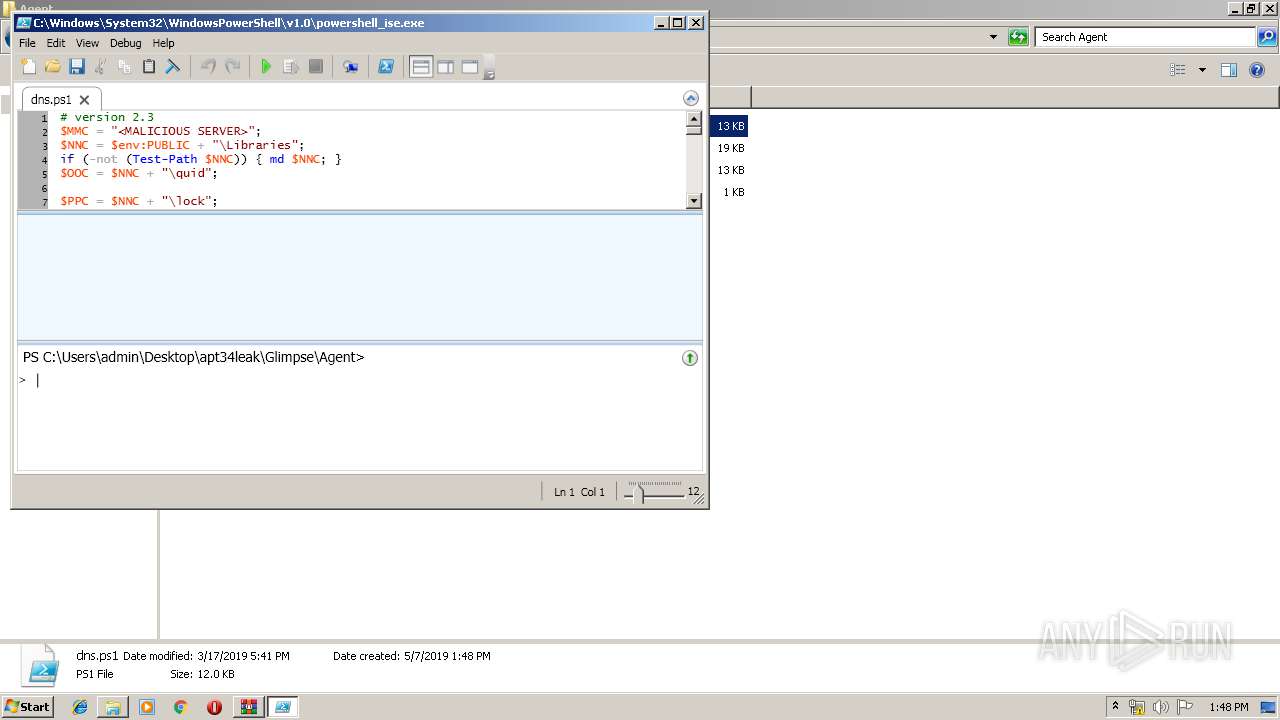
| 996 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe" "C:\Users\admin\Desktop\apt34leak\Glimpse\Agent\dns.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1688 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\apt34leak\Glimpse\Agent\dns.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1908 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\apt34leak\Glimpse\Agent\runner_.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1920 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\apt34leak\Glimpse\Agent\dns.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\Desktop\apt34leak\Glimpse\Agent\dns.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2472 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\apt34leak.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2564 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 644
Read events
2 147
Write events
497
Delete events
0
Modification events
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\apt34leak.7z | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
48
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Abu Dhabi airports.zip | compressed | |
MD5:0D38306C9D22BDBFDE4490BA075DF131 | SHA256:84F1F7331835ACD1FA0842501B9C1563C5B9381A0F4D0CB21E99E2415C00EDE9 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Jordan NITC - National Information Technology Center.zip | compressed | |
MD5:E6594128F9658EDEDBD892CB3E3B9267 | SHA256:F0B0DB92B378D3936F092B2B68F9AD82605185C5E1C6B6EA2FDE78B20929E7F1 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Emirates Federal Competitiveness and Statistics Authority.zip | compressed | |
MD5:849E23239A30C3FB9CCD26CC78276C97 | SHA256:1268A6DA7CC7F45DDD80BA143002E86C87E2C45D27E9943D8A41493B3C5F39C0 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Lamprell Energy Ltd.zip | compressed | |
MD5:059C7E00990385ED7F0923D89E7C8645 | SHA256:D55D625111A7D6CBEEC718A7D4BE6792A432122A9AF9866E7FA29756FD319C31 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Emirates National Oil Co (2).zip | compressed | |
MD5:D4D28C4EB6D92CA453C51C7D7E143BCC | SHA256:9F7A168A4A582F7487B2745A040D3FF35BCEBD78C9802197A5D97122B9E44037 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Kuwait Amiri Diwan da.gov.kw.zip | compressed | |
MD5:67099C949502839F5969134BAAD862B2 | SHA256:4BBEE2990C622C8729AA2836E191DFE0AAD274CE2ECEF43C5F7F68AF7F591432 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Emirates Policy Center.zip | compressed | |
MD5:1EB5E28751E9725C0A87C1ED1E9EEFD9 | SHA256:AED8E59EF052DA37829BD391D4D72998D90C85DB2BF015B1007FDE0F0680F21B | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\National Securtiy Agency of Bahrain.zip | compressed | |
MD5:8702898F061CBC6ECFFF40BE8B1B7553 | SHA256:01F31E92E35CBAFB1C73F7B5D009201A03873DE43A0FF76EA0D6A36A04FC4539 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Abu Dhabi Statistics Center scad.ae.zip | compressed | |
MD5:EE7B1B428CD840205BD1DAAC53D4316B | SHA256:34244AEFBB98934DCE0A8A59D33BDA13C14EF73860C032D349B3094A6F9AAEB1 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\apt34leak\Emirates NMC National Media Company.zip | compressed | |
MD5:3B3874C26FF8E388E849E5E147E76A6D | SHA256:60DDA03F6E5A1F557D3208E80C804ACF5FE43FA31143B8E04BB23416FEAC3B75 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
powershell_ise.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
powershell_ise.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
powershell_ise.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
powershell_ise.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
powershell_ise.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
powershell_ise.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
powershell_ise.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
powershell_ise.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
powershell_ise.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
powershell_ise.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|