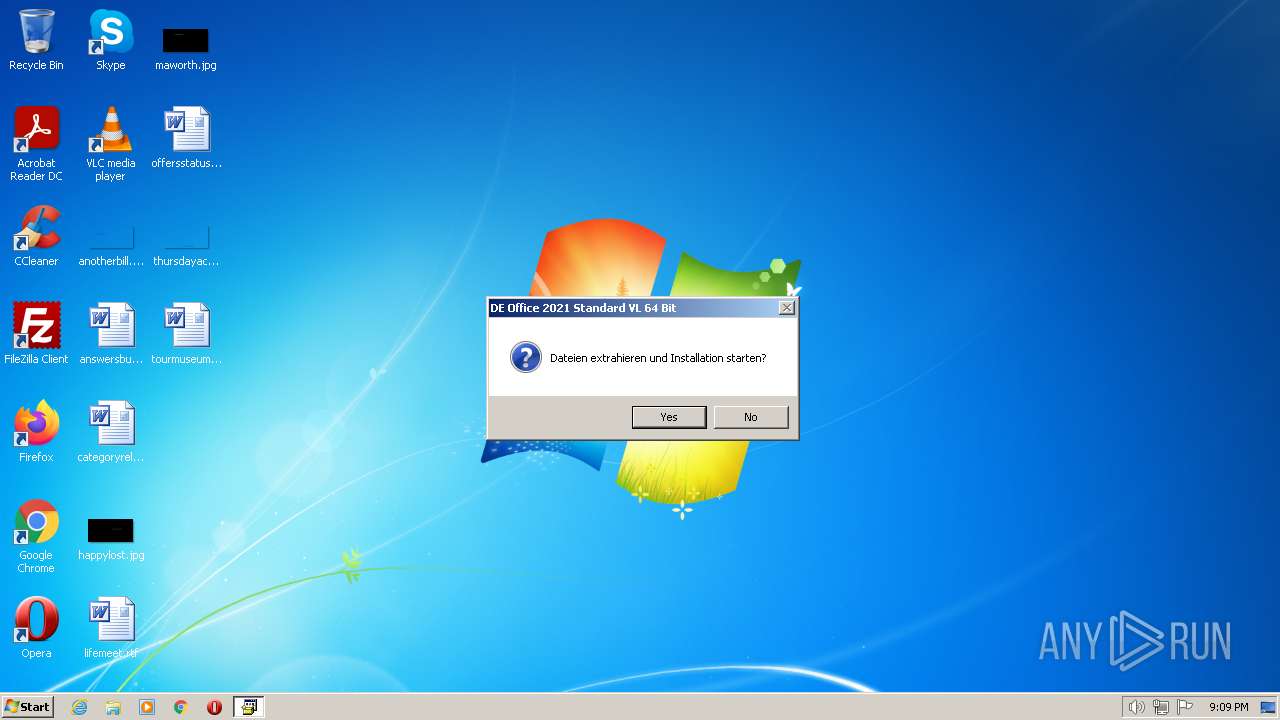
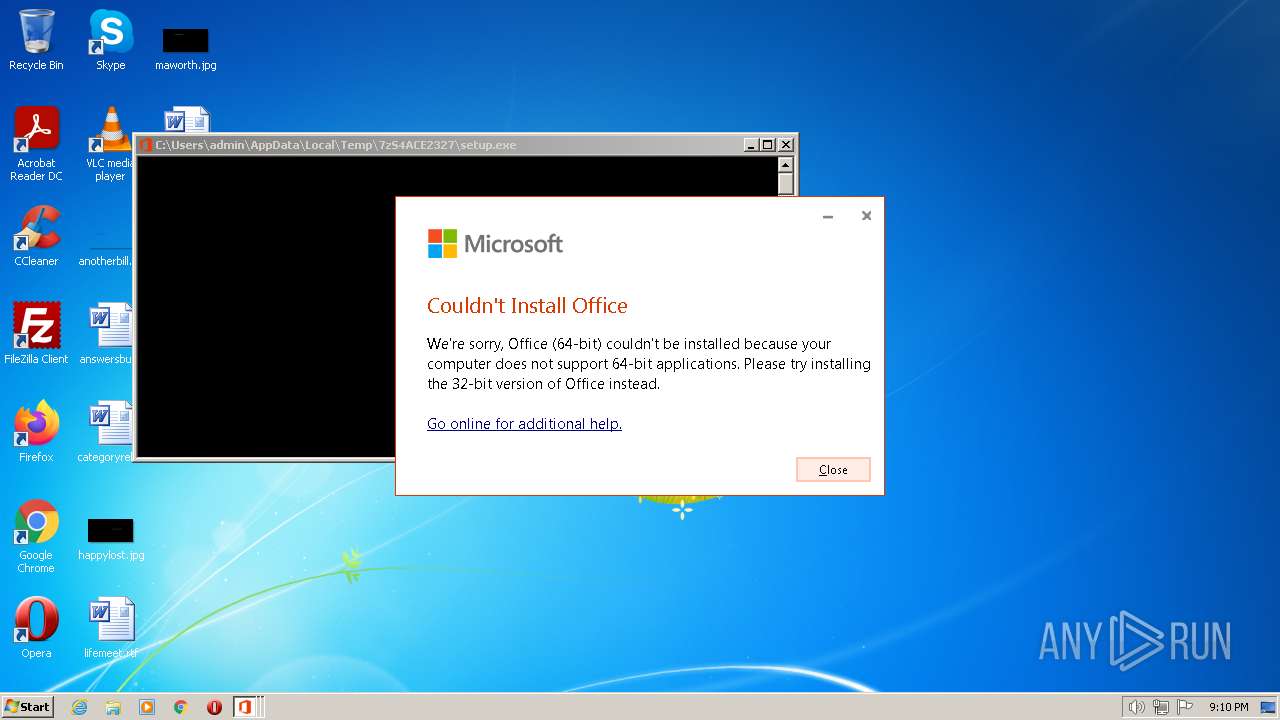
| File name: | DE_OfficeStandard2021_VL_64bit.exe |
| Full analysis: | https://app.any.run/tasks/b0528fdf-1bd6-48ee-ae95-9cb12e0c7923 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 21:09:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9796AF6D8AD32F8ED4B2FF6C6BEFDF7D |
| SHA1: | 33A72F11B2D2CE03BB2EF7842EA0615BC256467C |
| SHA256: | 06D3719C9529D75B1CC7BDF6B6248697E479B2F1363967F5A9294A3C8CCEDCF1 |
| SSDEEP: | 49152:b8i8DAyaARmp13kzsC91iMDtM+H75f5fLKrxtdp5OS6u3Gx+RwOoiA3nzpw7R4nC:b8iya13/HMZM275RTKVtYRF+RrFA3nzq |
MALICIOUS
Application was dropped or rewritten from another process
- setup.exe (PID: 3480)
SUSPICIOUS
Reads settings of System Certificates
- powershell.exe (PID: 3212)
- setup.exe (PID: 3480)
- powershell.exe (PID: 788)
Reads the Internet Settings
- setup.exe (PID: 3480)
- DE_OfficeStandard2021_VL_64bit.exe (PID: 3236)
Adds/modifies Windows certificates
- setup.exe (PID: 3480)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 788)
- powershell.exe (PID: 3212)
Reads security settings of Internet Explorer
- setup.exe (PID: 3480)
Checks Windows Trust Settings
- setup.exe (PID: 3480)
INFO
Reads the computer name
- DE_OfficeStandard2021_VL_64bit.exe (PID: 3236)
- setup.exe (PID: 3480)
Checks supported languages
- DE_OfficeStandard2021_VL_64bit.exe (PID: 3236)
- setup.exe (PID: 3480)
Reads Microsoft Office registry keys
- setup.exe (PID: 3480)
Checks proxy server information
- setup.exe (PID: 3480)
Process checks computer location settings
- setup.exe (PID: 3480)
Reads security settings of Internet Explorer
- powershell.exe (PID: 788)
- powershell.exe (PID: 3212)
Reads product name
- setup.exe (PID: 3480)
Reads the CPU's name
- setup.exe (PID: 3480)
Reads Environment values
- setup.exe (PID: 3480)
Reads CPU info
- setup.exe (PID: 3480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2016-Oct-04 15:12:31 |
| Detected languages: |
|
| CompanyName: | Igor Pavlov |
| FileDescription: | 7z Setup SFX |
| FileVersion: | 16.04 |
| InternalName: | 7zS.sfx |
| LegalCopyright: | Copyright (c) 1999-2016 Igor Pavlov |
| OriginalFilename: | 7zS.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 16.04 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 272 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 5 |
| TimeDateStamp: | 2016-Oct-04 15:12:31 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 93125 | 93184 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.63827 |
.rdata | 98304 | 14356 | 14848 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.23725 |
.data | 114688 | 9264 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.87468 |
.sxdata | 126976 | 4 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_LNK_INFO, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.0203931 |
.rsrc | 131072 | 2736 | 3072 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.331 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.75404 | 744 | UNKNOWN | English - United States | RT_ICON |
2 | 3.18403 | 296 | UNKNOWN | English - United States | RT_ICON |
97 | 3.04857 | 184 | UNKNOWN | English - United States | RT_DIALOG |
188 | 2.17822 | 84 | UNKNOWN | English - United States | RT_STRING |
207 | 1.43775 | 52 | UNKNOWN | English - United States | RT_STRING |
1 (#2) | 2.38262 | 96 | UNKNOWN | English - United States | RT_STRING |
1 (#3) | 2.37086 | 34 | UNKNOWN | English - United States | RT_GROUP_ICON |
1 (#4) | 3.45504 | 700 | UNKNOWN | English - United States | RT_VERSION |
Imports
KERNEL32.dll |
MSVCRT.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
Total processes
46
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 788 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile "$package = Get-AppxPackage Microsoft.Office.Desktop -allUsers; if (!$package) { $Error.Add(\"Package is not installed\")}; if ($error.Count -eq 0) { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch' -InputObject '1' -Encoding ascii; } else { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch' -InputObject '0' -Encoding ascii; Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateError.scratch' -InputObject $error -Encoding ascii;} " | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 856 | "C:\Users\admin\AppData\Local\Temp\DE_OfficeStandard2021_VL_64bit.exe" | C:\Users\admin\AppData\Local\Temp\DE_OfficeStandard2021_VL_64bit.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7z Setup SFX Exit code: 3221226540 Version: 16.04 Modules
| |||||||||||||||
| 3212 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile "$package = Get-AppxPackage Microsoft.Office.Desktop -allUsers; if (!$package) { $Error.Add(\"Package is not installed\")}; if ($error.Count -eq 0) { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch' -InputObject '1' -Encoding ascii; } else { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateResult.scratch' -InputObject '0' -Encoding ascii; Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Office.ValidateError.scratch' -InputObject $error -Encoding ascii;} " | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3236 | "C:\Users\admin\AppData\Local\Temp\DE_OfficeStandard2021_VL_64bit.exe" | C:\Users\admin\AppData\Local\Temp\DE_OfficeStandard2021_VL_64bit.exe | Explorer.EXE | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Setup SFX Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 3480 | "C:\Users\admin\AppData\Local\Temp\7zS4ACE2327\setup.exe" /configure Configuration.xml | C:\Users\admin\AppData\Local\Temp\7zS4ACE2327\setup.exe | DE_OfficeStandard2021_VL_64bit.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Exit code: 0 Version: 16.0.14326.20152 Modules
| |||||||||||||||
Total events
17 643
Read events
17 497
Write events
144
Delete events
2
Modification events
| (PID) Process: | (3236) DE_OfficeStandard2021_VL_64bit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3236) DE_OfficeStandard2021_VL_64bit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3236) DE_OfficeStandard2021_VL_64bit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3236) DE_OfficeStandard2021_VL_64bit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3480) setup.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3480) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | UIFallbackLanguages |
Value: x-none | |||
| (PID) Process: | (3480) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | HelpLanguageTag |
Value: en-US | |||
| (PID) Process: | (3480) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | PreferredEditingLanguage |
Value: en-US | |||
| (PID) Process: | (3480) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | PreviousPreferredEditingLanguage |
Value: en-US | |||
| (PID) Process: | (3480) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | WordChangeInstallLanguage |
Value: No | |||
Executable files
1
Suspicious files
10
Text files
10
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 788 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ea11wc1f.bbj.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3480 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:— | SHA256:— | |||
| 3480 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3480 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:— | SHA256:— | |||
| 3480 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4C7F163ED126D5C3CB9457F68EC64E9E | der | |
MD5:— | SHA256:— | |||
| 3480 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | der | |
MD5:— | SHA256:— | |||
| 3480 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\setup.exe_Rules.xml | xml | |
MD5:— | SHA256:— | |||
| 3480 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:— | SHA256:— | |||
| 3236 | DE_OfficeStandard2021_VL_64bit.exe | C:\Users\admin\AppData\Local\Temp\7zS4ACE2327\Configuration.xml | text | |
MD5:— | SHA256:— | |||
| 3212 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Office.ValidateError.scratch | text | |
MD5:03CA949E980AD3A9B98D66D053ACAE2C | SHA256:BD3B1323C2E19053EED647AC73AED55053789FB505EDD068514810B5149BAA12 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
18
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3480 | setup.exe | HEAD | 200 | 8.253.95.117:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v64_16.0.14332.20416.cab | US | — | — | whitelisted |
868 | svchost.exe | HEAD | 200 | 8.253.95.117:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v64_16.0.14332.20416.cab | US | — | — | whitelisted |
868 | svchost.exe | GET | 200 | 8.253.95.117:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v64_16.0.14332.20416.cab | US | compressed | 10.7 Kb | whitelisted |
3480 | setup.exe | GET | 200 | 2.19.126.97:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | DE | der | 557 b | whitelisted |
3480 | setup.exe | GET | 200 | 2.19.126.97:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | DE | der | 555 b | whitelisted |
3480 | setup.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | US | der | 1.56 Kb | whitelisted |
3480 | setup.exe | HEAD | 200 | 8.253.95.117:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v64_16.0.14332.20416.cab | US | — | — | whitelisted |
868 | svchost.exe | GET | 206 | 8.253.95.117:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v64_16.0.14332.20416.cab | US | binary | 1 b | whitelisted |
868 | svchost.exe | HEAD | 200 | 8.253.95.117:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v64_16.0.14332.20416.cab | US | binary | 1 b | whitelisted |
3480 | setup.exe | GET | 200 | 2.19.126.97:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | DE | der | 824 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3480 | setup.exe | 52.109.77.1:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | suspicious |
3480 | setup.exe | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
3480 | setup.exe | 52.109.88.33:443 | mrodevicemgr.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | suspicious |
1376 | svchost.exe | 20.50.201.195:443 | vortex-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | suspicious |
3480 | setup.exe | 8.253.95.117:80 | officecdn.microsoft.com | LEVEL3 | US | unknown |
868 | svchost.exe | 8.253.95.117:80 | officecdn.microsoft.com | LEVEL3 | US | unknown |
3480 | setup.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1376 | svchost.exe | 40.79.189.59:443 | vortex-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | JP | whitelisted |
3480 | setup.exe | 104.79.89.142:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3480 | setup.exe | 2.19.126.97:80 | crl.microsoft.com | Akamai International B.V. | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nexusrules.officeapps.live.com |
| whitelisted |
ecs.office.com |
| whitelisted |
vortex-win.data.microsoft.com |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexus.officeapps.live.com |
| whitelisted |