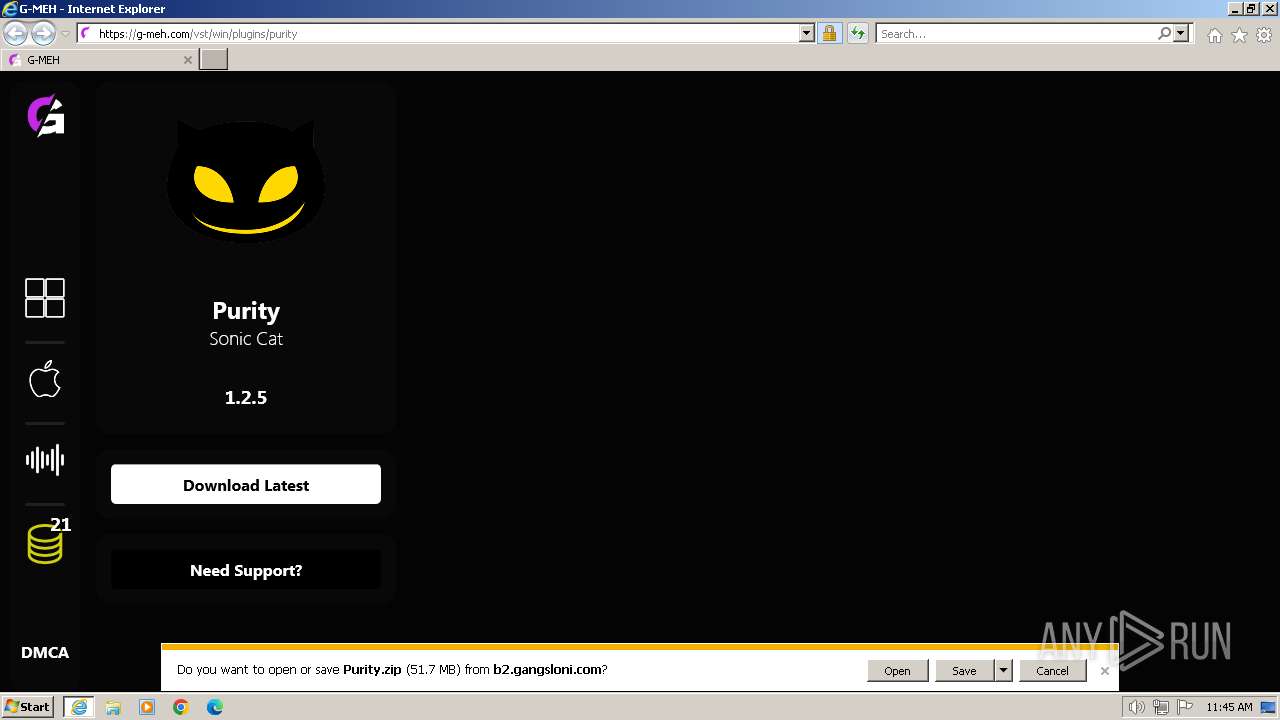
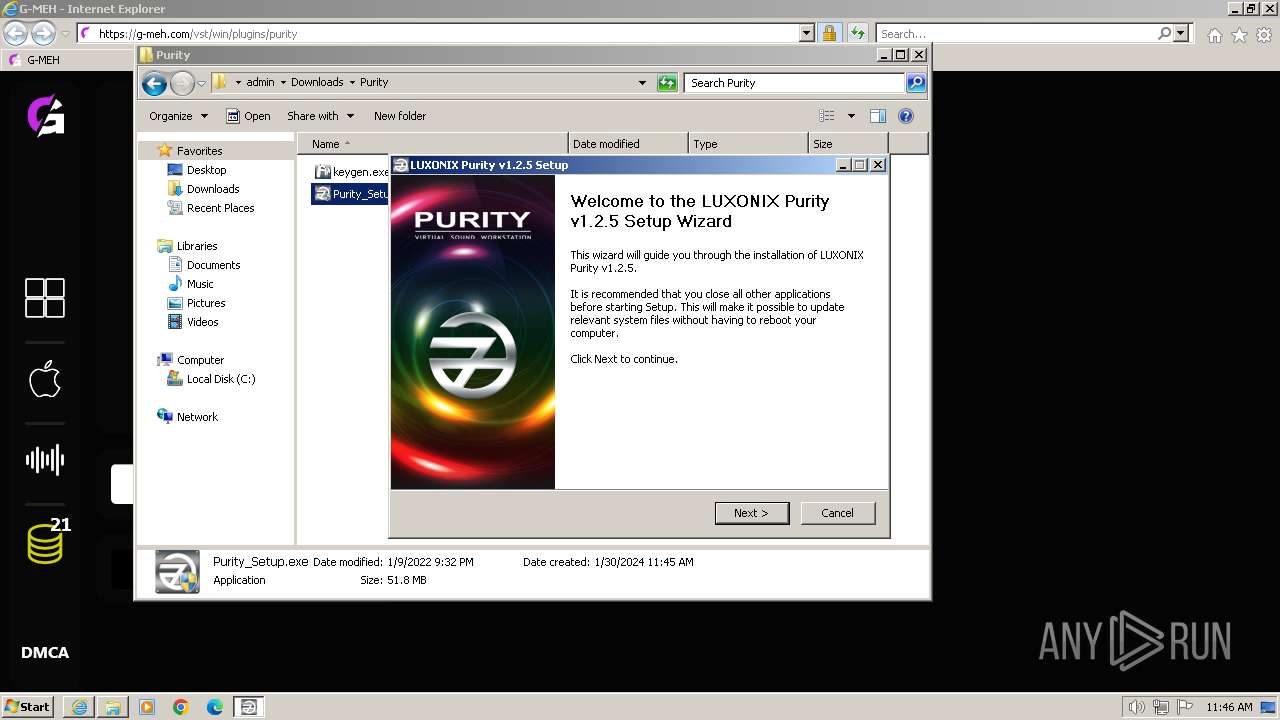
| URL: | https://g-meh.com/vst/win/plugins/purity |
| Full analysis: | https://app.any.run/tasks/84e94673-ea25-4acd-8993-13323e54cd2d |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2024, 11:45:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 90B18538055589139441DAB0225DCD4E |
| SHA1: | 9E3521DB9241F838729DBEE2DE046466413DDFCE |
| SHA256: | 06B888D8C41A882D26091C9098DCA2E2555D5F3965763B89BC9E5B9F7A6C7B03 |
| SSDEEP: | 3:N83KKvS:2aH |
MALICIOUS
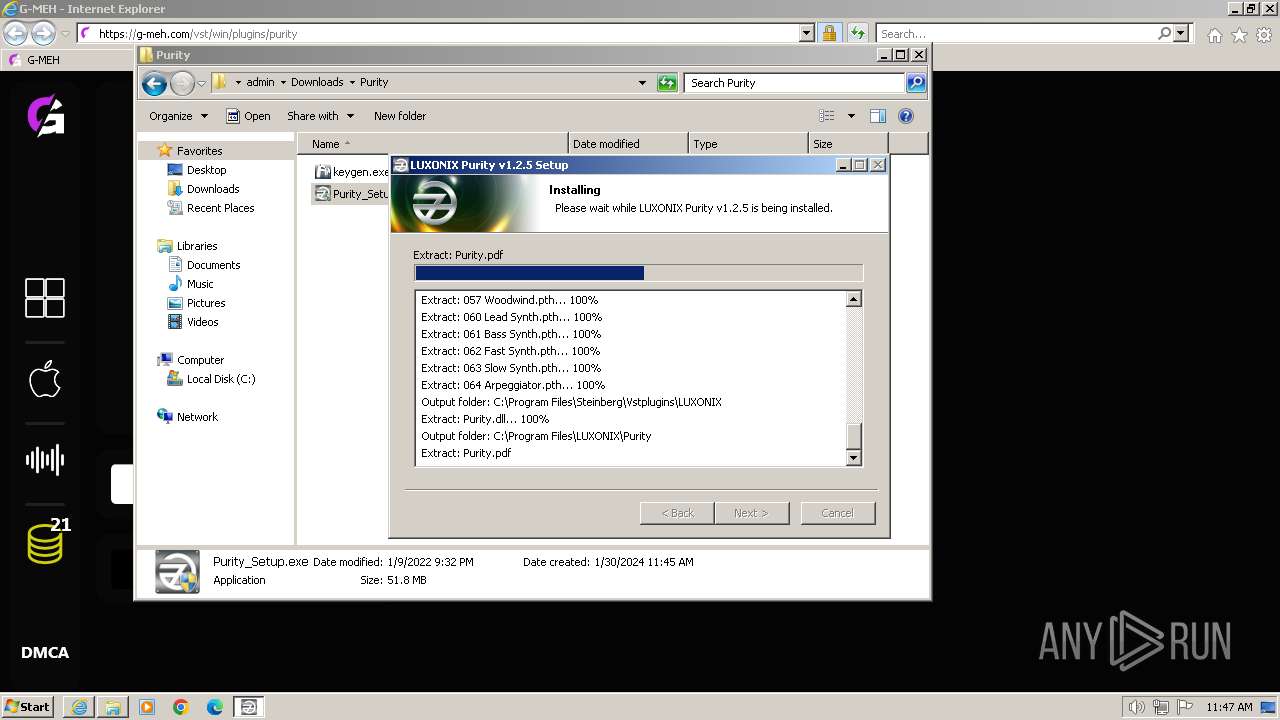
Drops the executable file immediately after the start
- Purity_Setup.exe (PID: 3720)
- Purity_Setup.exe (PID: 2960)
Creates a writable file in the system directory
- Purity_Setup.exe (PID: 3720)
SUSPICIOUS
Executable content was dropped or overwritten
- Purity_Setup.exe (PID: 3720)
- Purity_Setup.exe (PID: 2960)
The process creates files with name similar to system file names
- Purity_Setup.exe (PID: 3720)
- Purity_Setup.exe (PID: 2960)
Malware-specific behavior (creating "System.dll" in Temp)
- Purity_Setup.exe (PID: 3720)
- Purity_Setup.exe (PID: 2960)
Process drops legitimate windows executable
- Purity_Setup.exe (PID: 3720)
The process drops C-runtime libraries
- Purity_Setup.exe (PID: 3720)
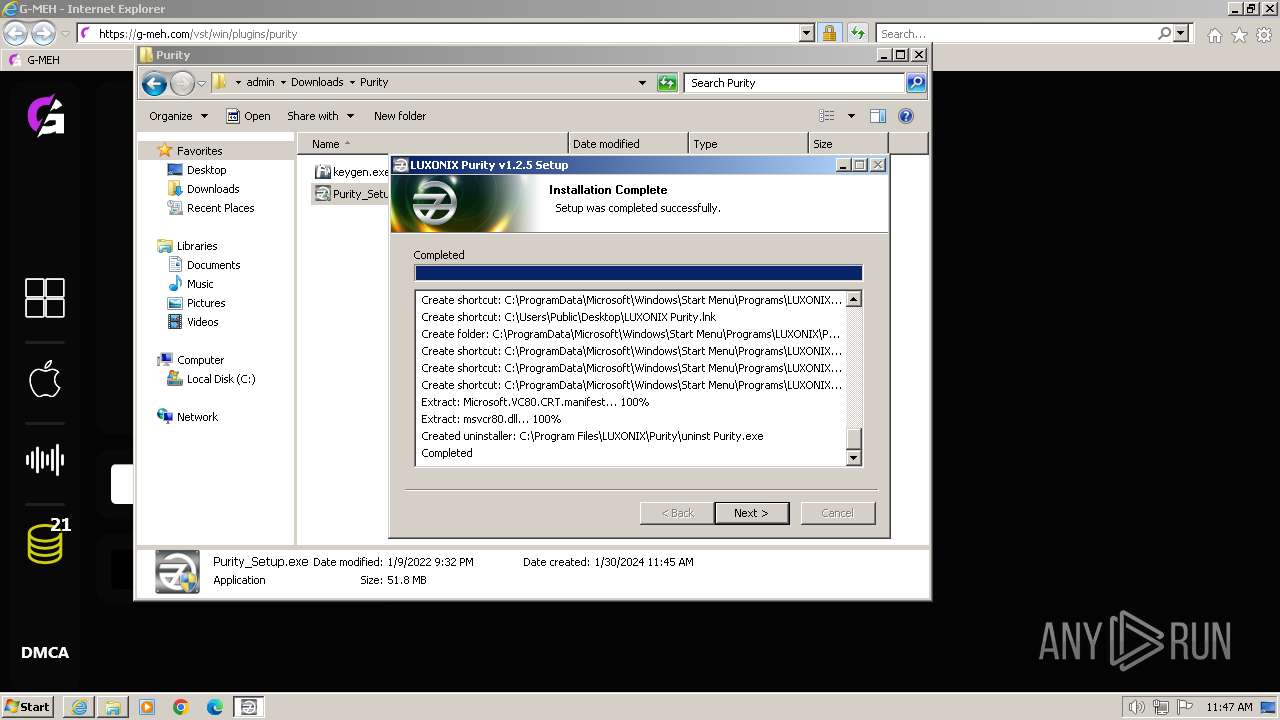
Creates a software uninstall entry
- Purity_Setup.exe (PID: 2960)
Searches for installed software
- Purity_Setup.exe (PID: 2960)
Reads the Internet Settings
- Purity.exe (PID: 1992)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2912)
Manual execution by a user
- WinRAR.exe (PID: 2912)
- Purity_Setup.exe (PID: 3300)
- Purity_Setup.exe (PID: 3720)
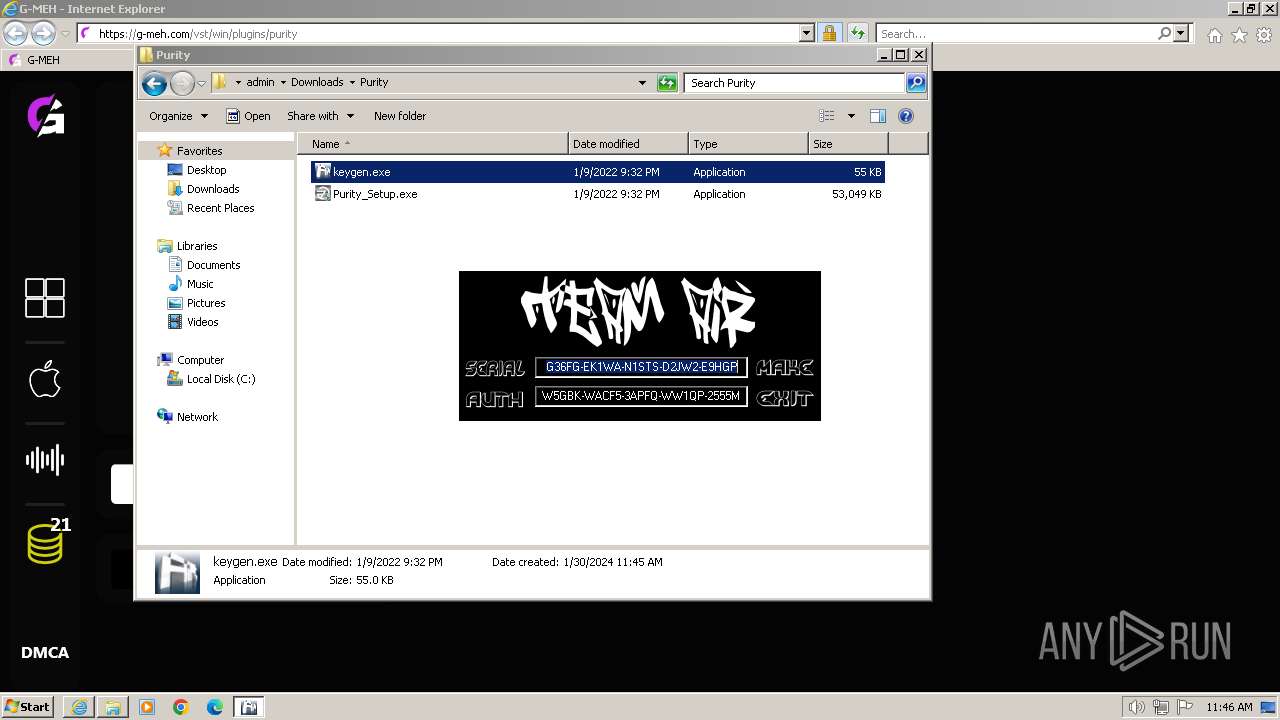
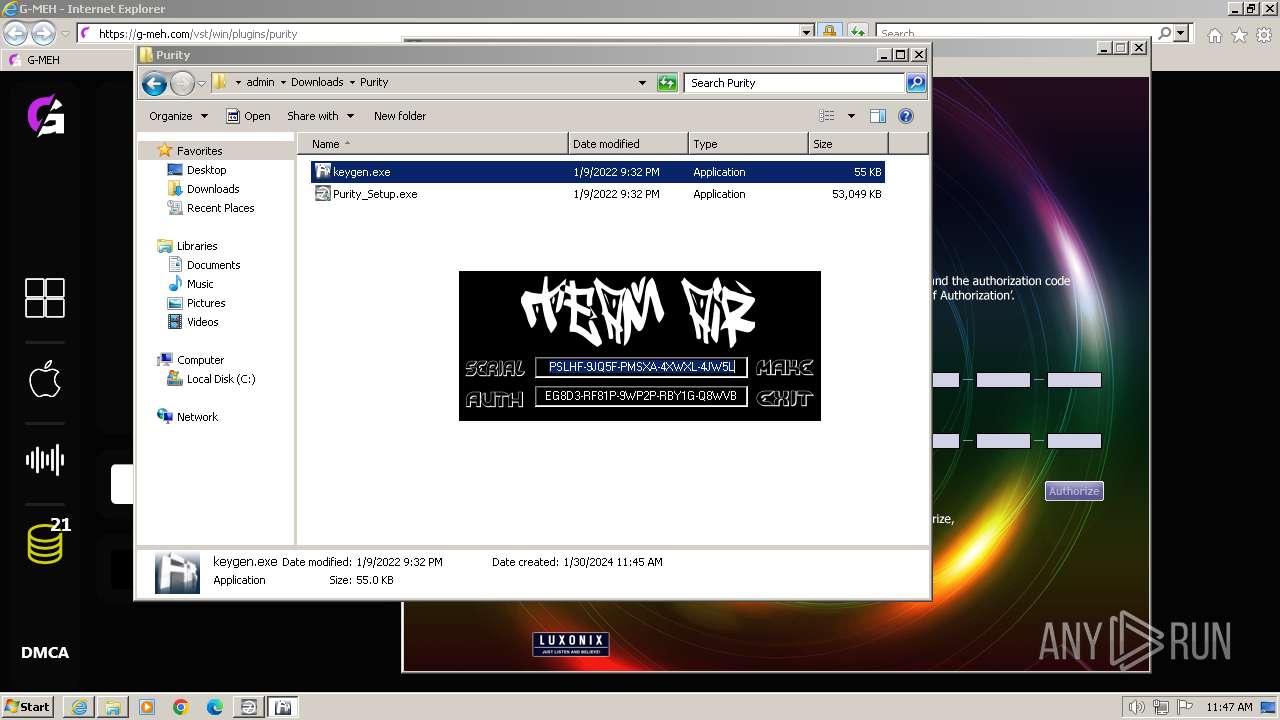
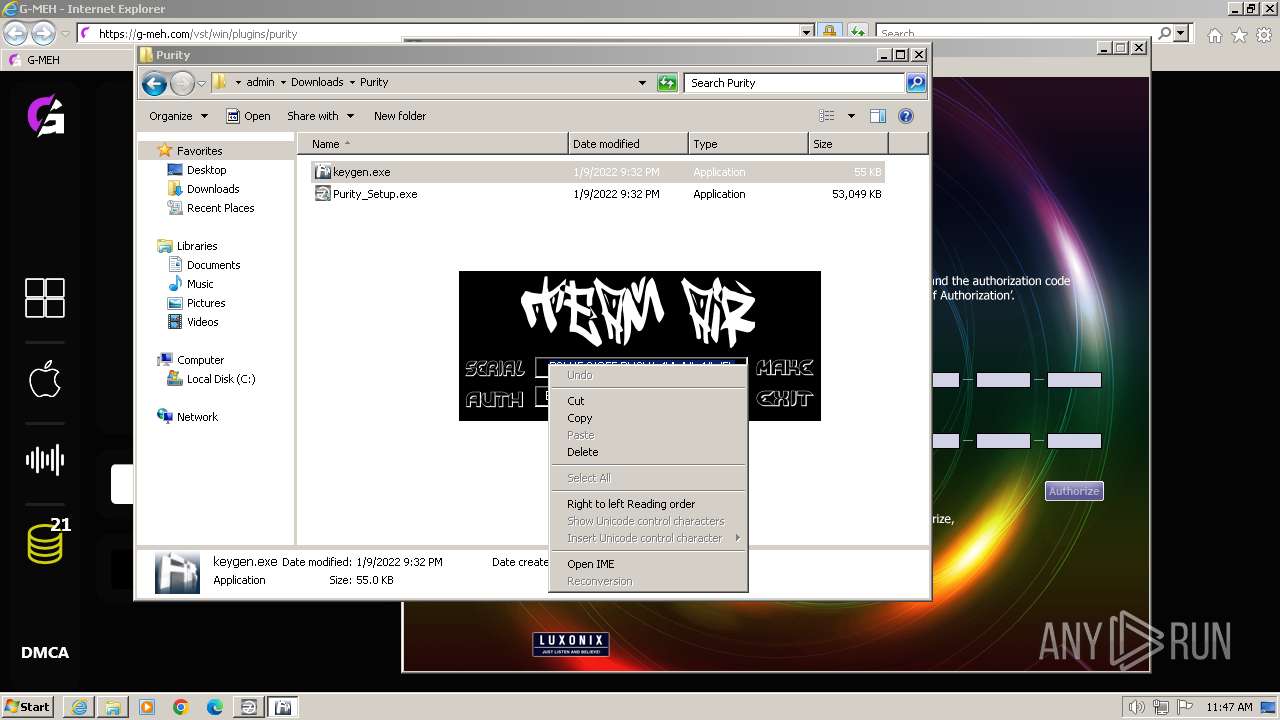
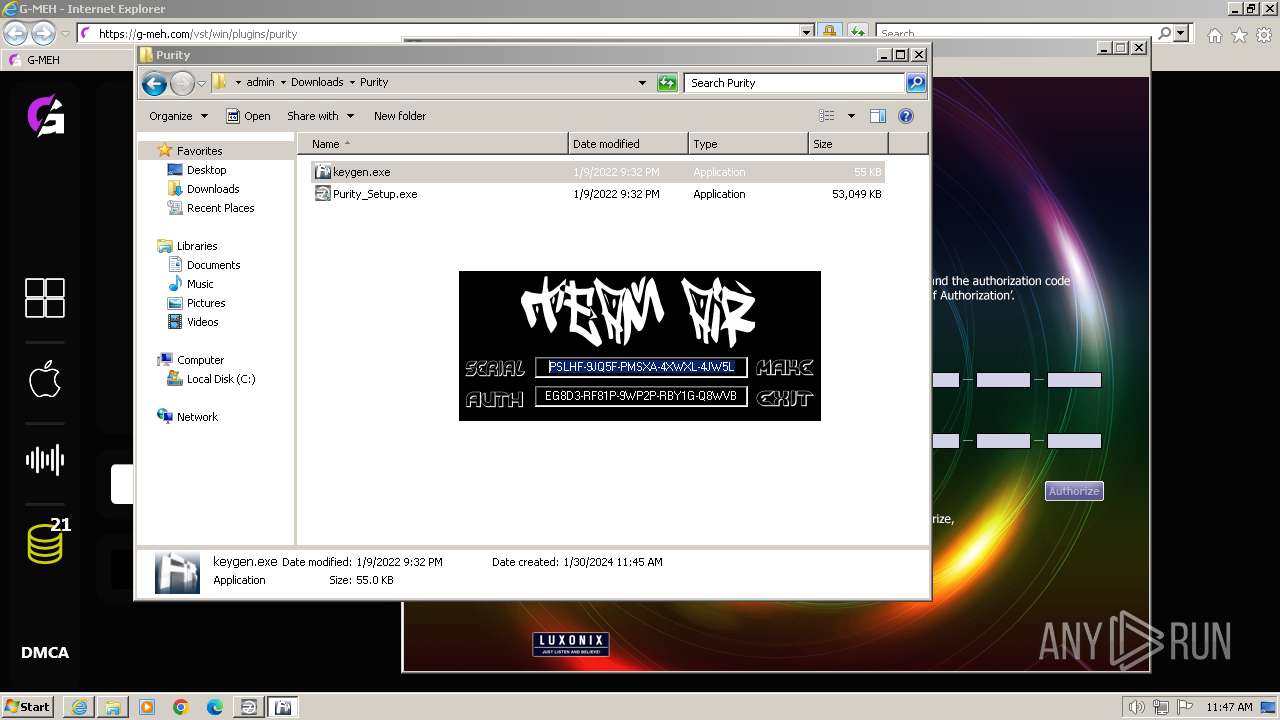
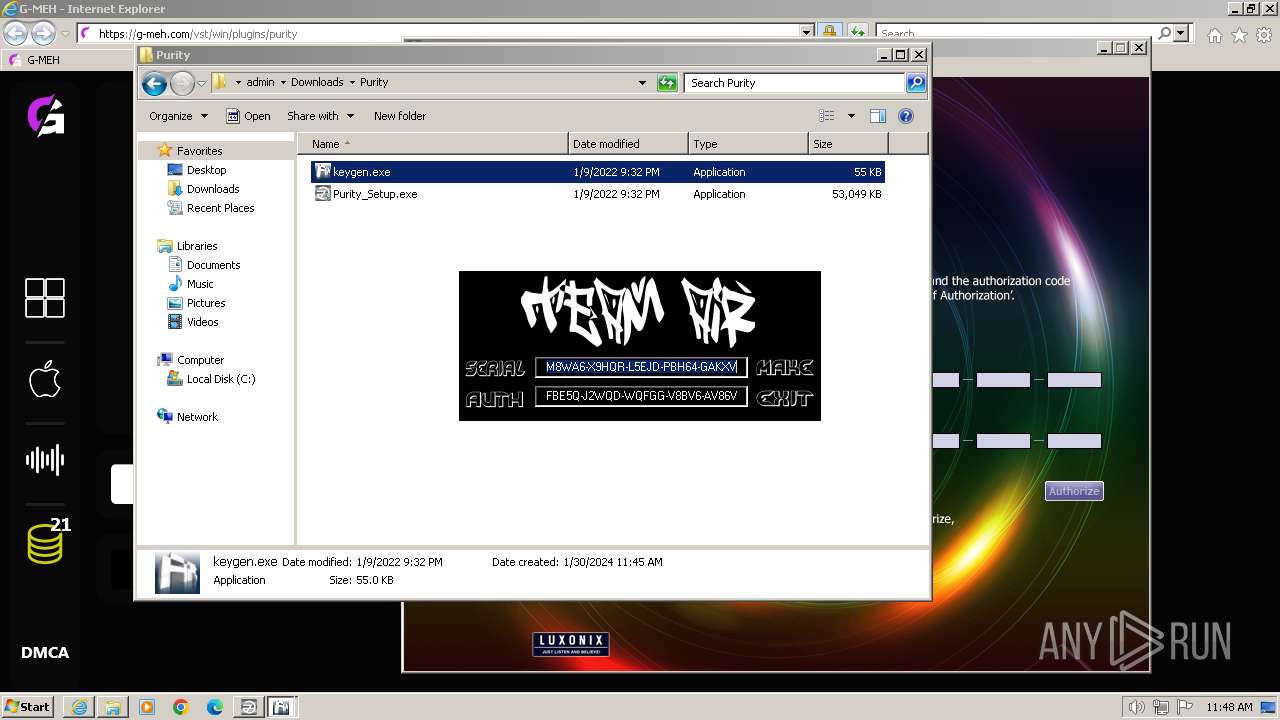
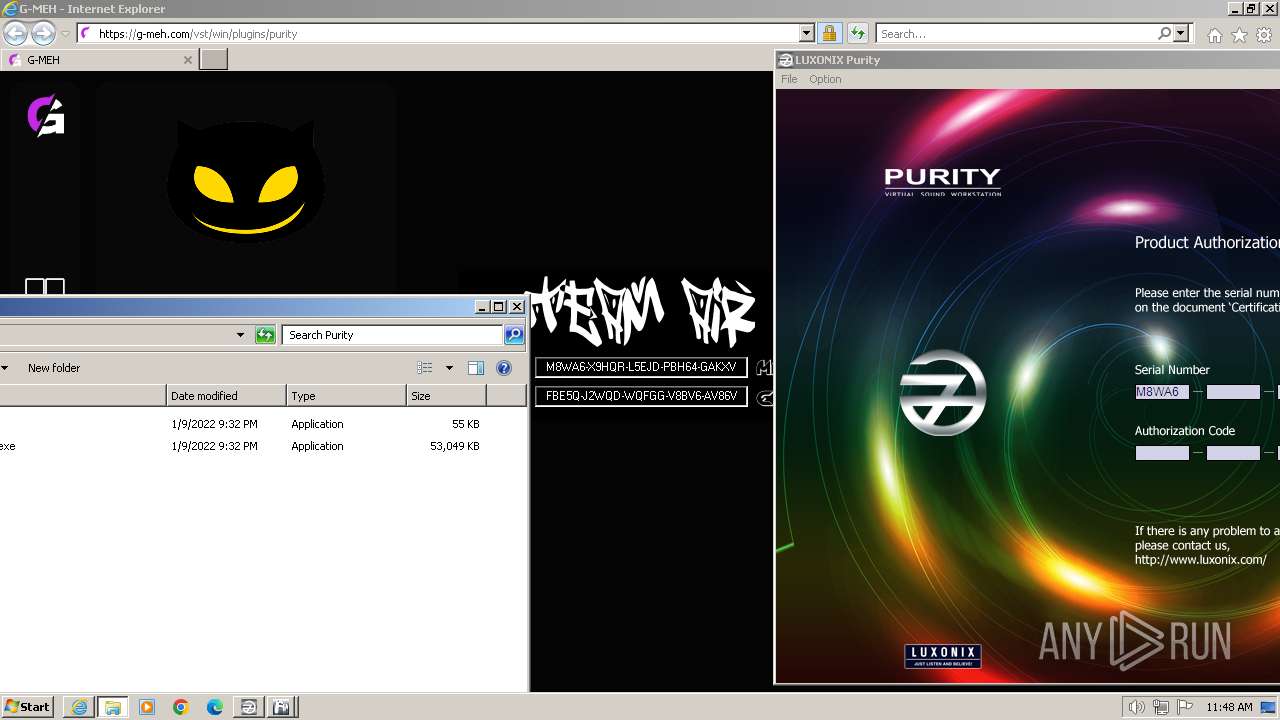
- keygen.exe (PID: 3304)
- Purity_Setup.exe (PID: 2960)
- Purity_Setup.exe (PID: 3940)
- keygen.exe (PID: 1540)
- keygen.exe (PID: 948)
The process uses the downloaded file
- iexplore.exe (PID: 1588)
- WinRAR.exe (PID: 2912)
Application launched itself
- iexplore.exe (PID: 1588)
Checks supported languages
- Purity_Setup.exe (PID: 3720)
- keygen.exe (PID: 3304)
- Purity_Setup.exe (PID: 2960)
- Purity.exe (PID: 1992)
- keygen.exe (PID: 948)
- keygen.exe (PID: 1540)
Reads the computer name
- Purity_Setup.exe (PID: 3720)
- Purity_Setup.exe (PID: 2960)
- Purity.exe (PID: 1992)
- keygen.exe (PID: 3304)
- keygen.exe (PID: 948)
- keygen.exe (PID: 1540)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2912)
Create files in a temporary directory
- Purity_Setup.exe (PID: 3720)
- Purity_Setup.exe (PID: 2960)
- Purity.exe (PID: 1992)
Creates files in the program directory
- Purity_Setup.exe (PID: 3720)
- Purity.exe (PID: 1992)
Reads the machine GUID from the registry
- Purity.exe (PID: 1992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1588 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
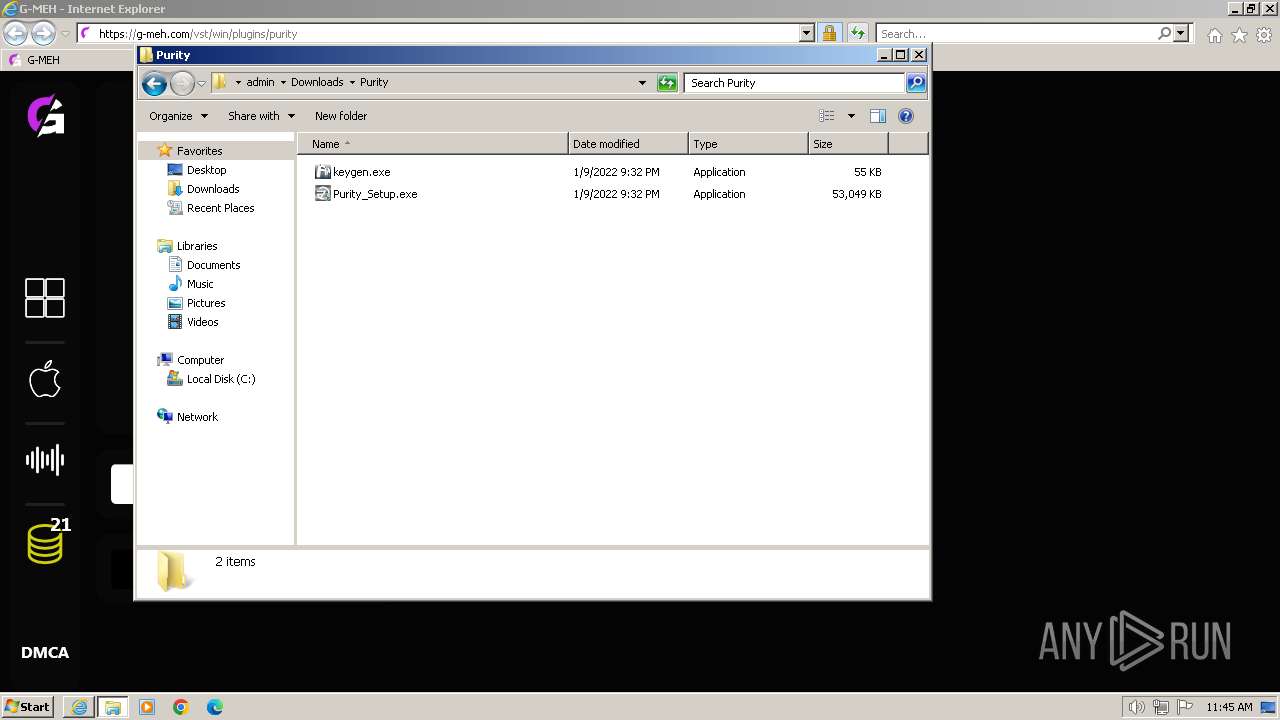
| 948 | "C:\Users\admin\Downloads\Purity\keygen.exe" | C:\Users\admin\Downloads\Purity\keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1540 | "C:\Users\admin\Downloads\Purity\keygen.exe" | C:\Users\admin\Downloads\Purity\keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1588 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://g-meh.com/vst/win/plugins/purity" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
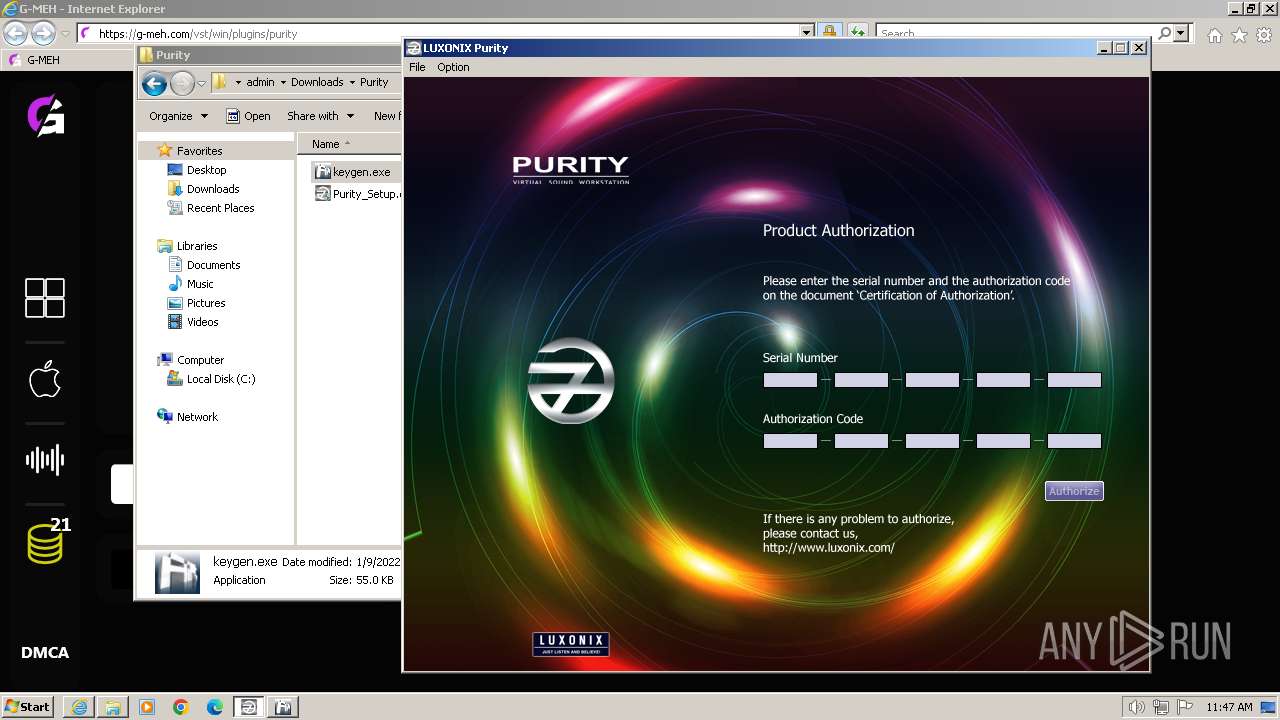
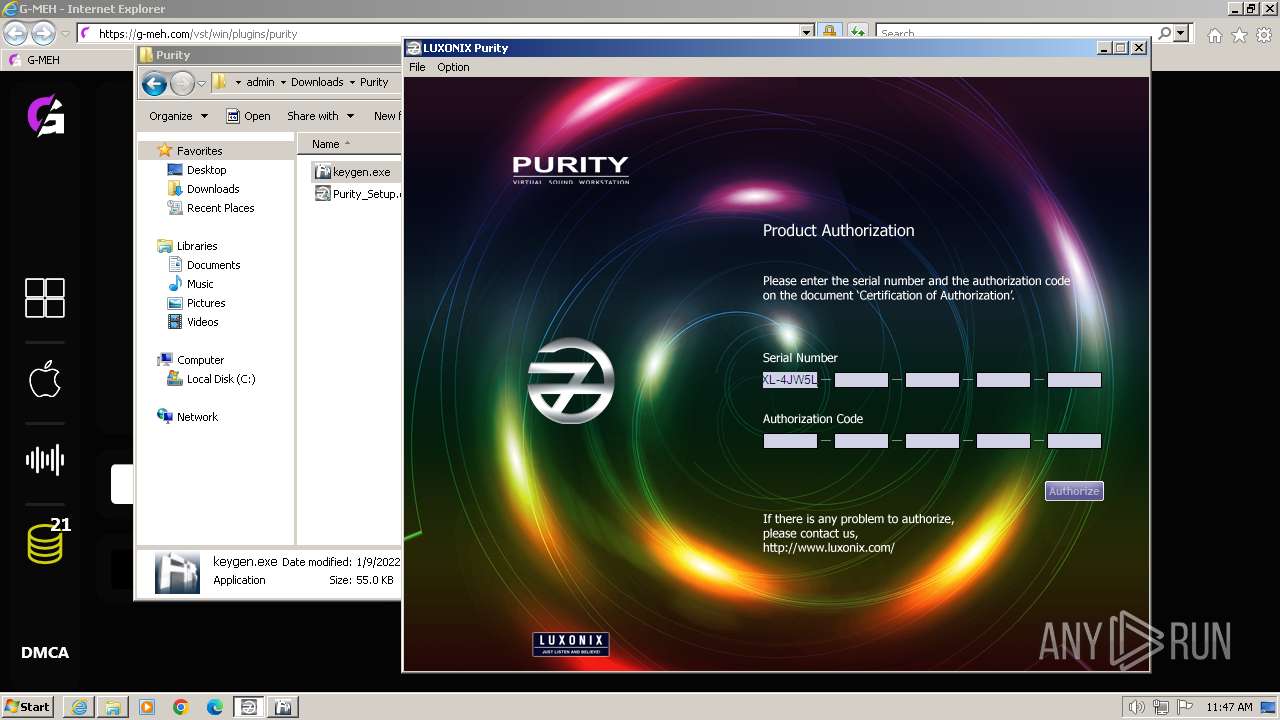
| 1992 | "C:\Program Files\LUXONIX\Purity\Purity.exe" | C:\Program Files\LUXONIX\Purity\Purity.exe | Purity_Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2912 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\Purity.zip" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2960 | "C:\Users\admin\Downloads\Purity\Purity_Setup.exe" | C:\Users\admin\Downloads\Purity\Purity_Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3300 | "C:\Users\admin\Downloads\Purity\Purity_Setup.exe" | C:\Users\admin\Downloads\Purity\Purity_Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3304 | "C:\Users\admin\Downloads\Purity\keygen.exe" | C:\Users\admin\Downloads\Purity\keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3600 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1588 CREDAT:3282193 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
26 057
Read events
25 926
Write events
125
Delete events
6
Modification events
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1588) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
14
Suspicious files
85
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:DB62A7A6AAE68EFCD6966FDB66EF82F5 | SHA256:91657A213267FBF98EE2659C5FEE9F088BCD35A3DDCFA0020D9BCC81B681F610 | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\a40e717ea31d100f[1].css | text | |
MD5:BD86AD8D3FD3331E9449818E221E3F04 | SHA256:465D35276B48C22C390FA32AD95192E88ED617F5241A2B6166B859745CA3CE30 | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\_ssgManifest[1].js | text | |
MD5:B6652DF95DB52FEB4DAF4ECA35380933 | SHA256:6F5B4AA00D2F8D6AED9935B471806BF7ACEF464D0C1D390260E5FE27F800C67E | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\0e91cec604b6cfb3[1].css | text | |
MD5:9454034FC71B0CF83E89007445B77A40 | SHA256:E39B260530CD3C120C1A2D439700105071F17B59991419C70FA95AA44FF0B945 | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:2FB864475E132421F49F93A3C47D8E05 | SHA256:9D41FB8AAF167F4BE387287F0F25301C1F1463C643CEAB32CE4A7731301F1302 | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\polyfills-c67a75d1b6f99dc8[1].js | text | |
MD5:837C0DF77FD5009C9E46D446188ECFD0 | SHA256:0225EB034D024A03BDC90EA6C79F56193662E7C3EEE909696298820E517CBB83 | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\_buildManifest[1].js | text | |
MD5:B18DB52846888C39EAC91CF4CB9F860E | SHA256:753D4297013A828ABE228A8A01EBE88E96F120F1EF688F0F00A92F635F619A2B | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\g-meh[1].svg | image | |
MD5:11949B1620B604D2D3D36DE7B33B0AF3 | SHA256:7E7819F5D24725CCC52E7B1284E3B96D1F9960EAC01B00EA3AA24D3E484A6626 | |||
| 896 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\main-6ce2ac113bf0e699[1].js | text | |
MD5:FAF7A1E6604D2C61D6DFC6C30DDE48C8 | SHA256:497DD88C7FD63B6156FC1AB25FFD360BE8A0B84ED2F91AFC31B3783C173D2FF8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
38
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
896 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d7a4c83e7f191cf0 | unknown | — | — | unknown |
896 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f324de6a56943962 | unknown | — | — | unknown |
896 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
1588 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?95d95b669c097e41 | unknown | — | — | unknown |
896 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
896 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1588 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5565915fab5f2bac | unknown | — | — | unknown |
3600 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b150b552b216e1f4 | unknown | compressed | 65.2 Kb | unknown |
3600 | iexplore.exe | GET | 200 | 2.19.105.18:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3600 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fcbfea4cae399b90 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
896 | iexplore.exe | 104.21.73.4:443 | g-meh.com | CLOUDFLARENET | — | unknown |
896 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
896 | iexplore.exe | 142.250.74.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
896 | iexplore.exe | 104.16.56.101:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
896 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1588 | iexplore.exe | 104.21.73.4:443 | g-meh.com | CLOUDFLARENET | — | unknown |
1588 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
g-meh.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
b2.gangsloni.com |
| unknown |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Purity.exe | - initialize options
|
Purity.exe | [ERROR] failed to read option (C:\Program Files\LUXONIX\Purity\Purity.ini)
|
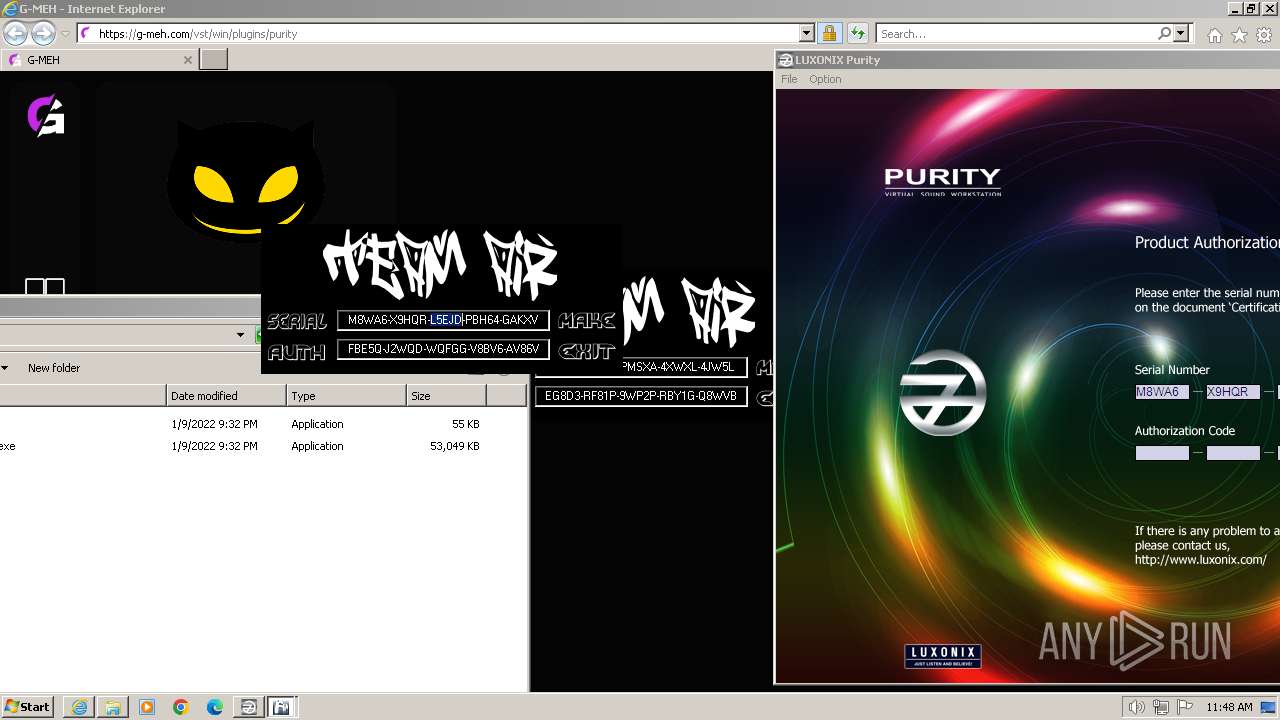
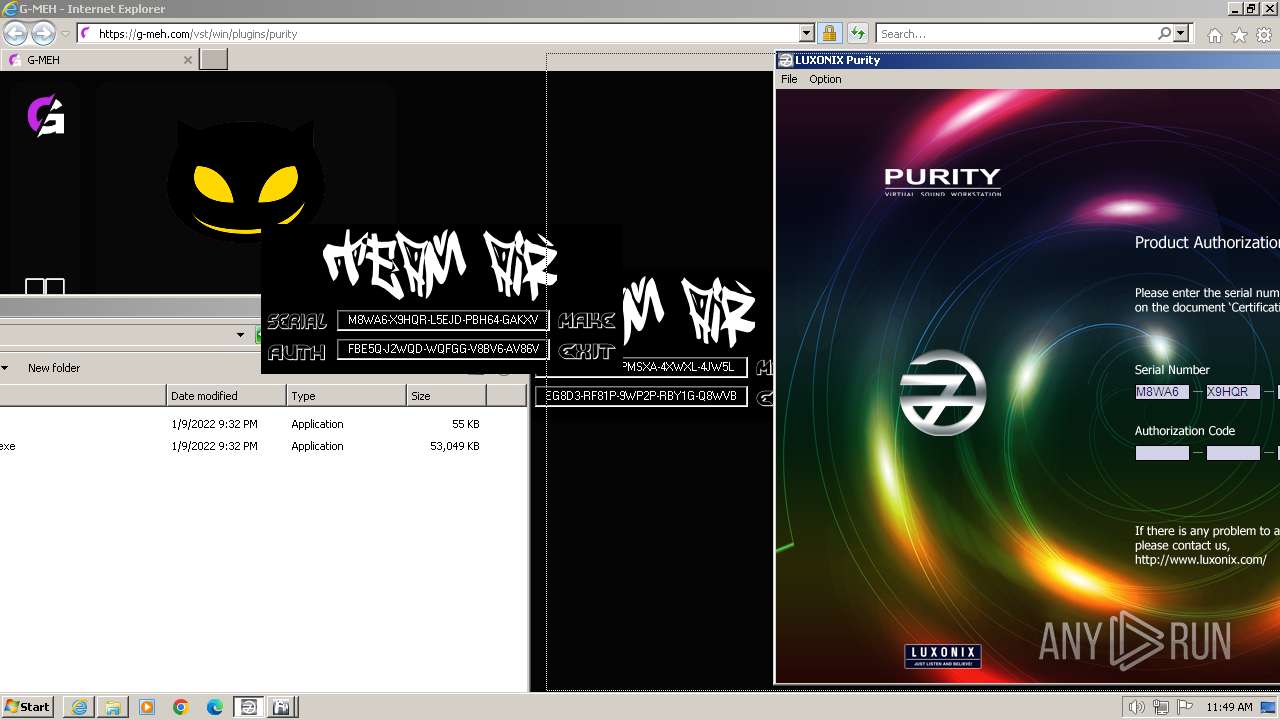
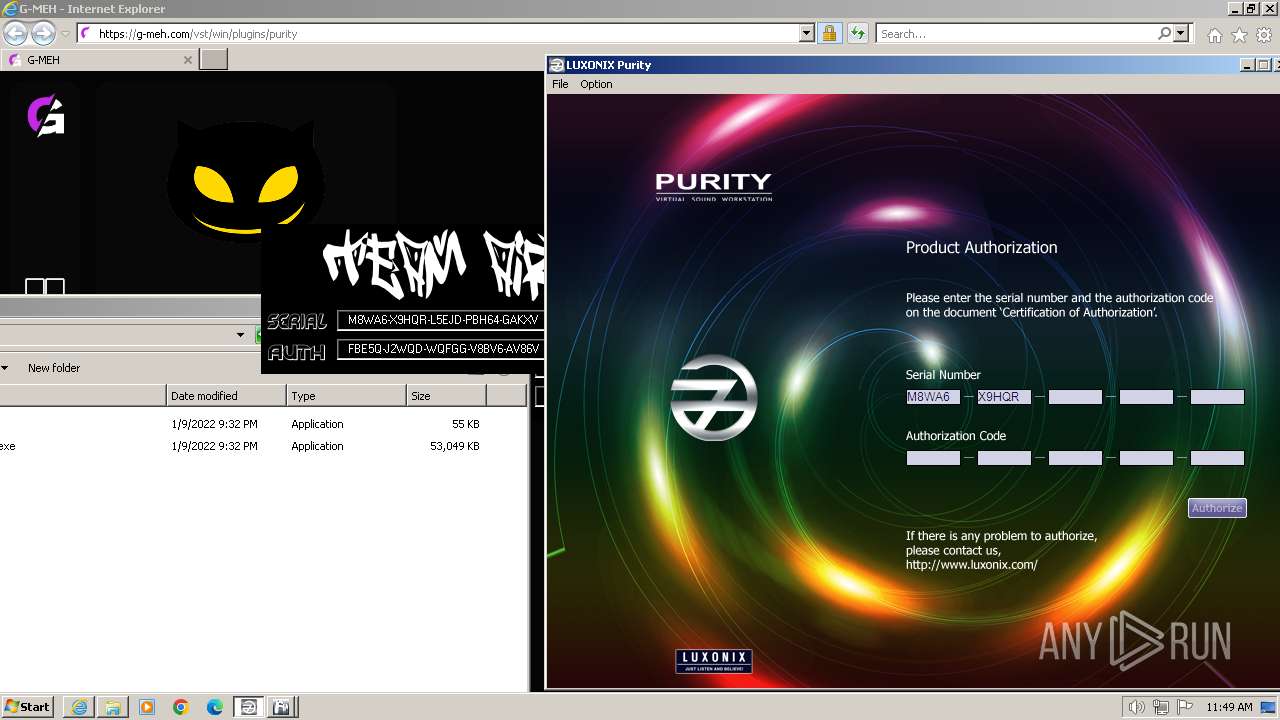
Purity.exe | - VST:LUXONIX:Purity:version 1.2.5.2
|
Purity.exe | - Plug-in Path: C:\Program Files\LUXONIX\Purity\Purity.dll
|
Purity.exe | - VST:LUXONIX:Purity:Path(Appl): C:\Program Files\LUXONIX\Purity\
|
Purity.exe | - Total 588 Wavetables (Melody 299, Drum 289)
|
Purity.exe | - Total 1322 Samples (Loop 1022, 1shot 300)
|
Purity.exe | - Total 1366 Patches (Combi 345, Single 1021)
|
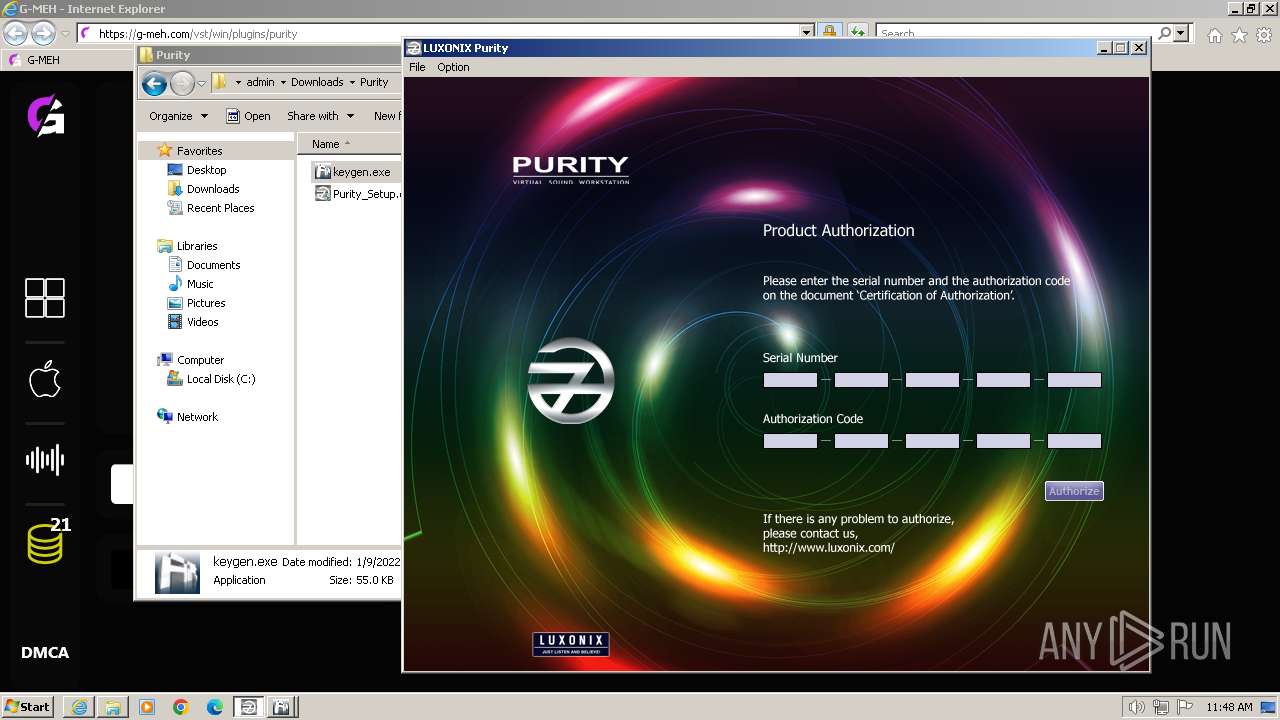
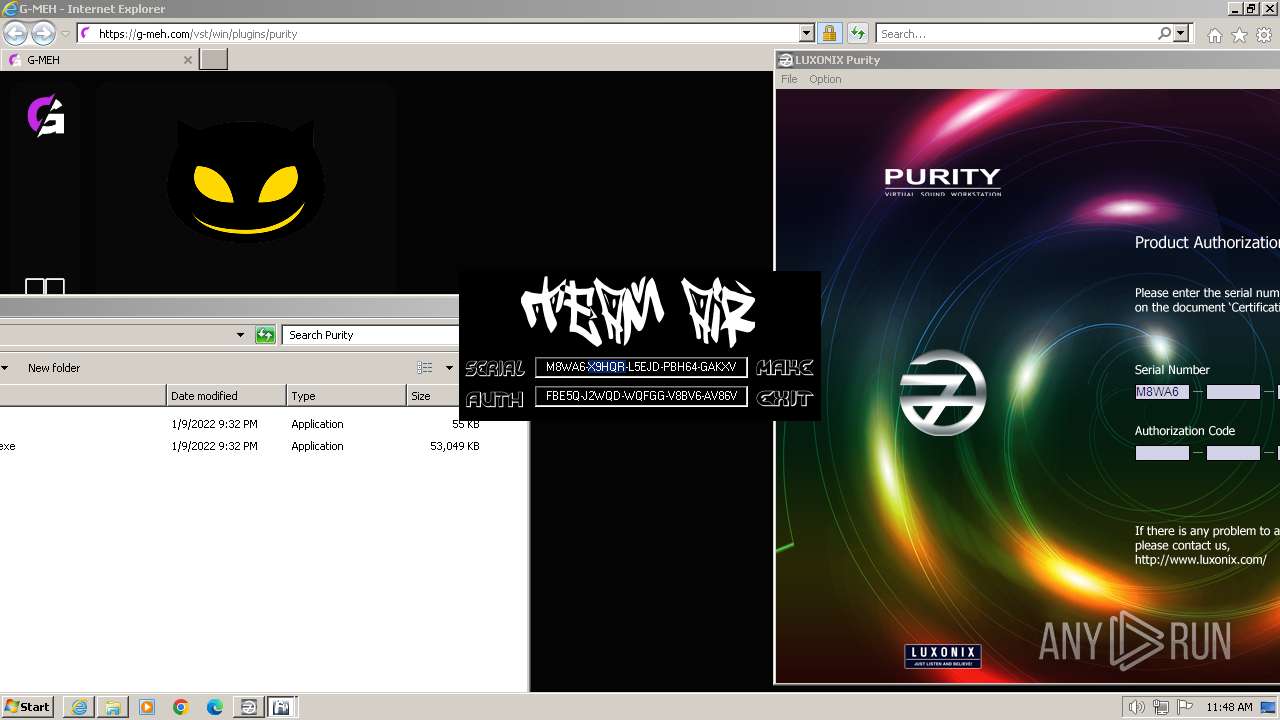
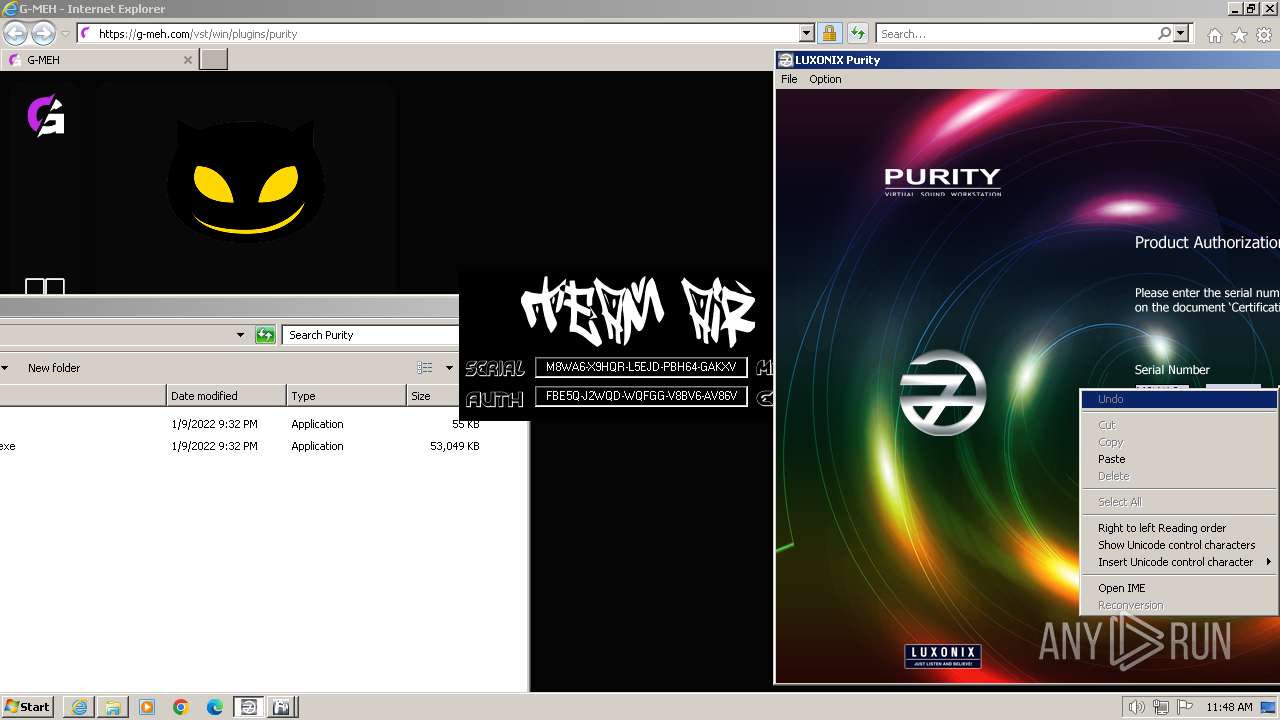
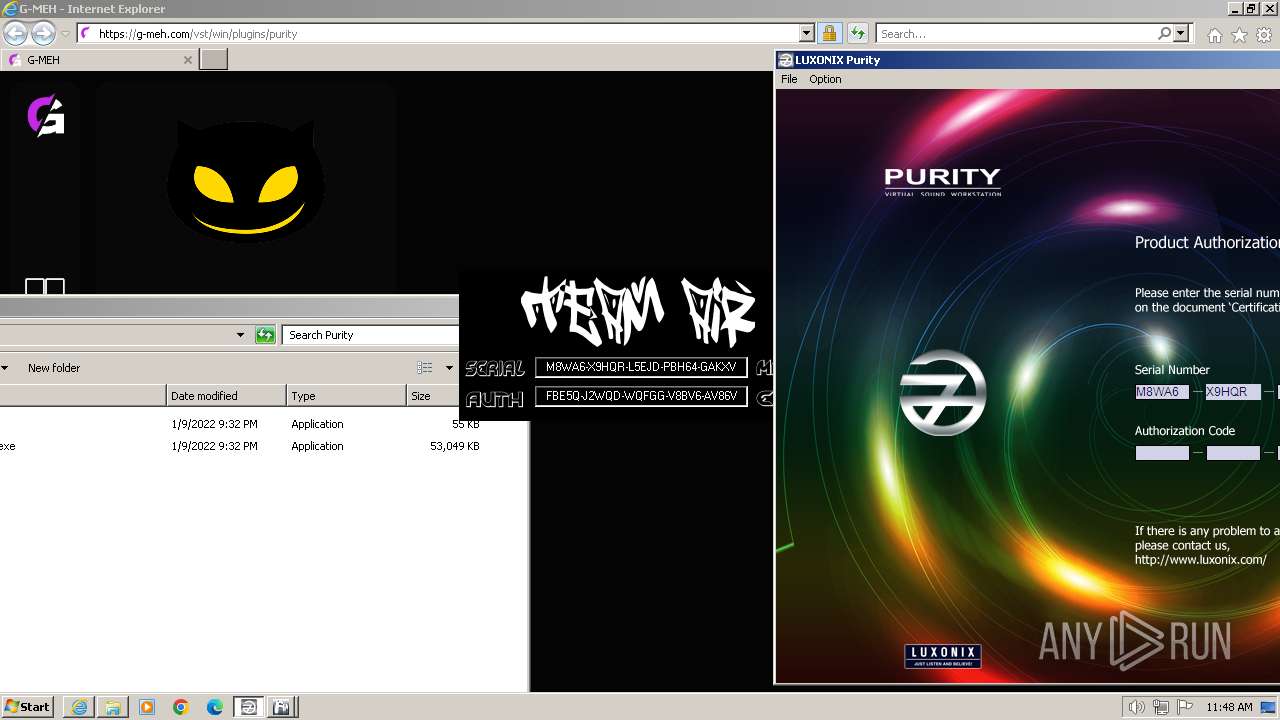
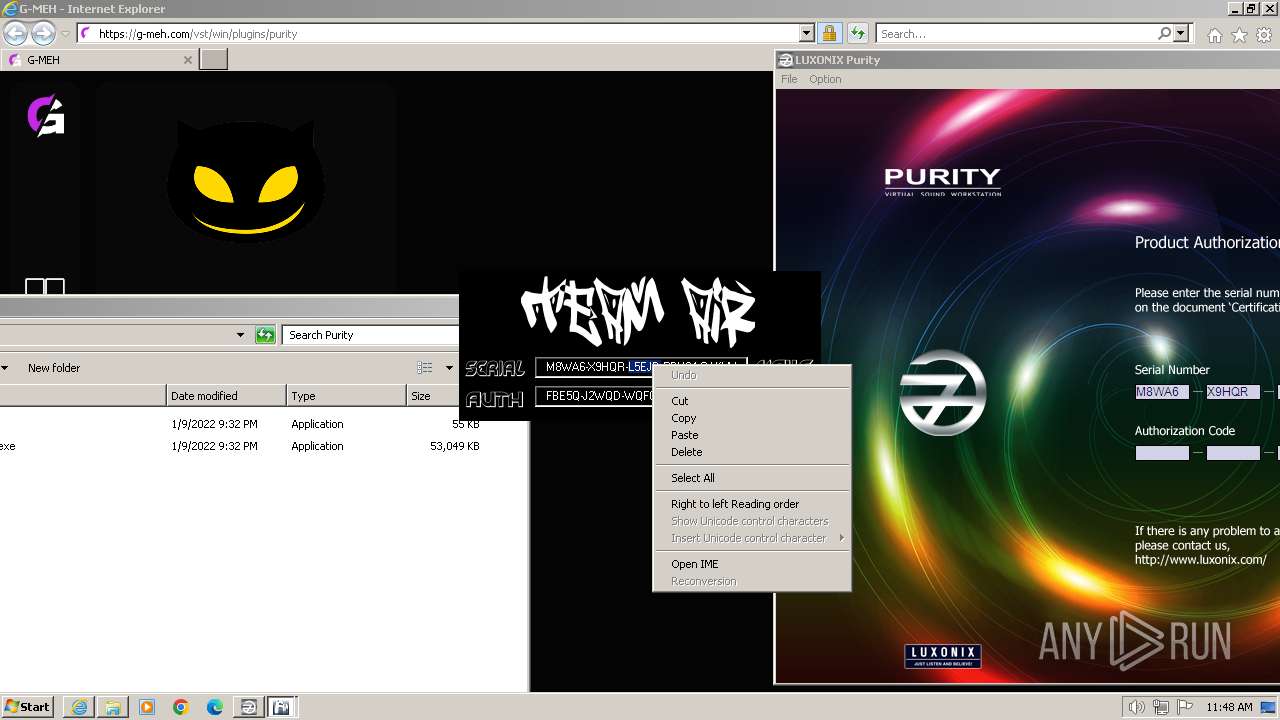
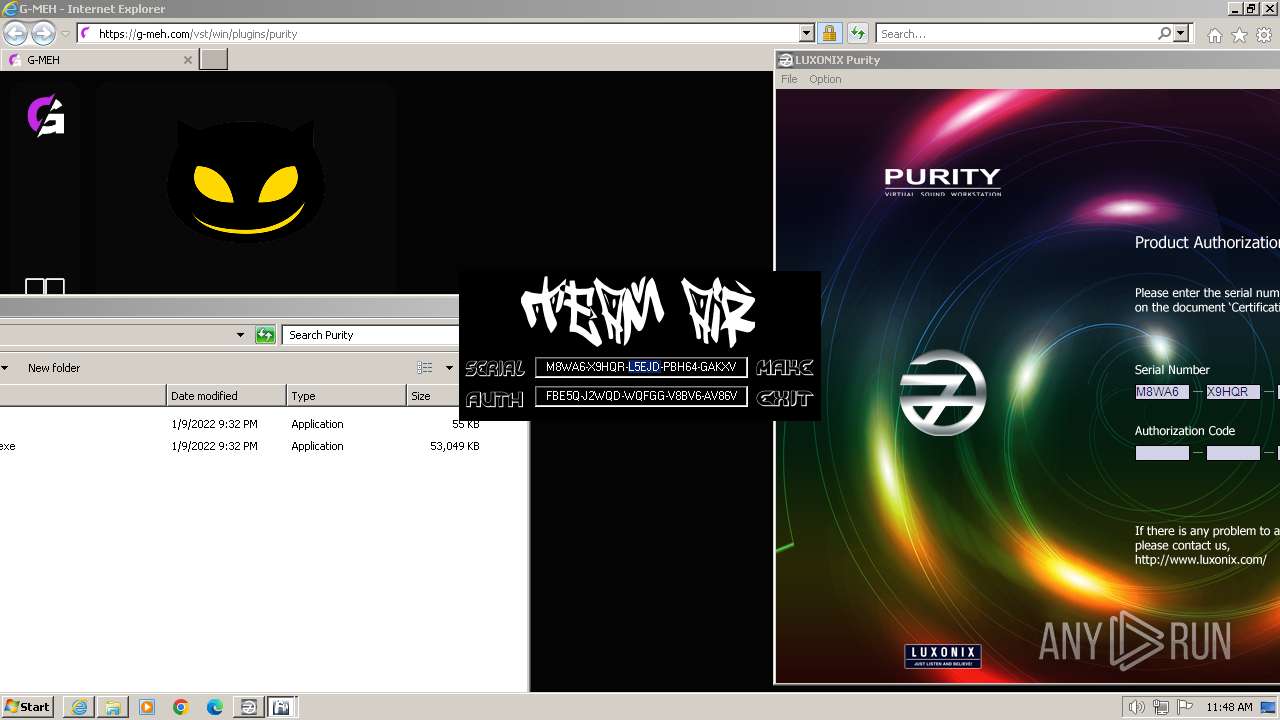
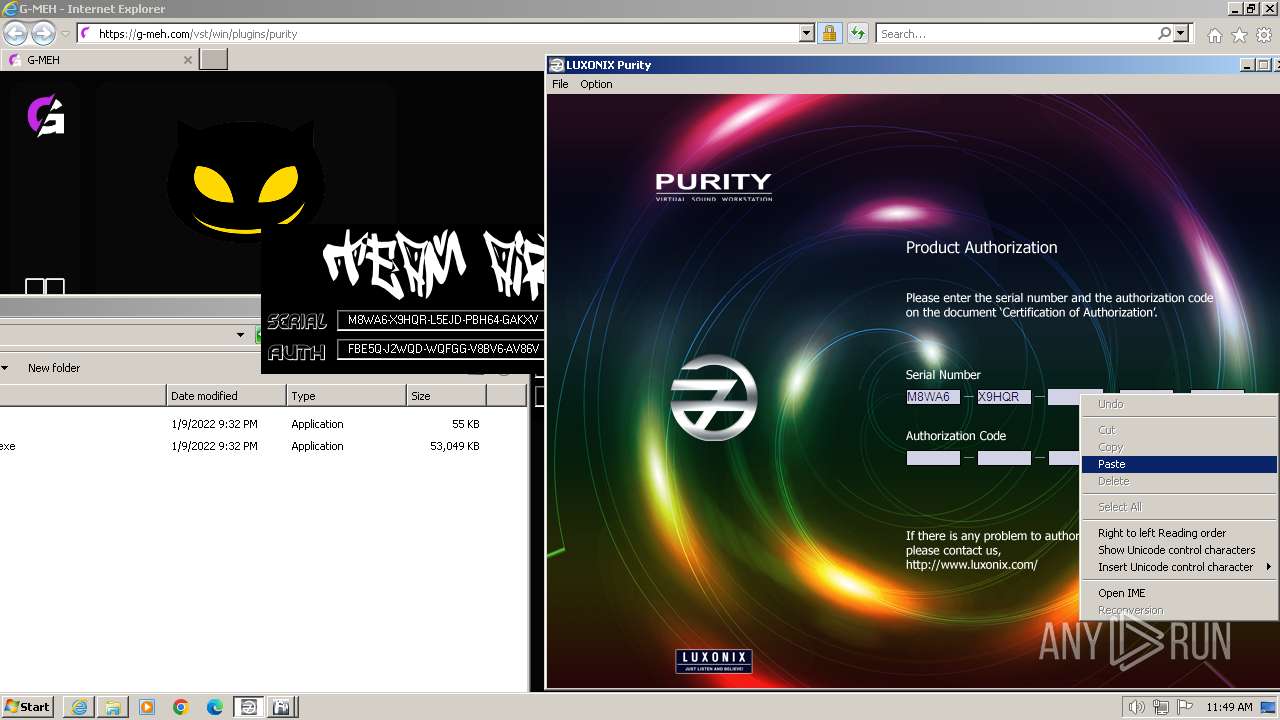
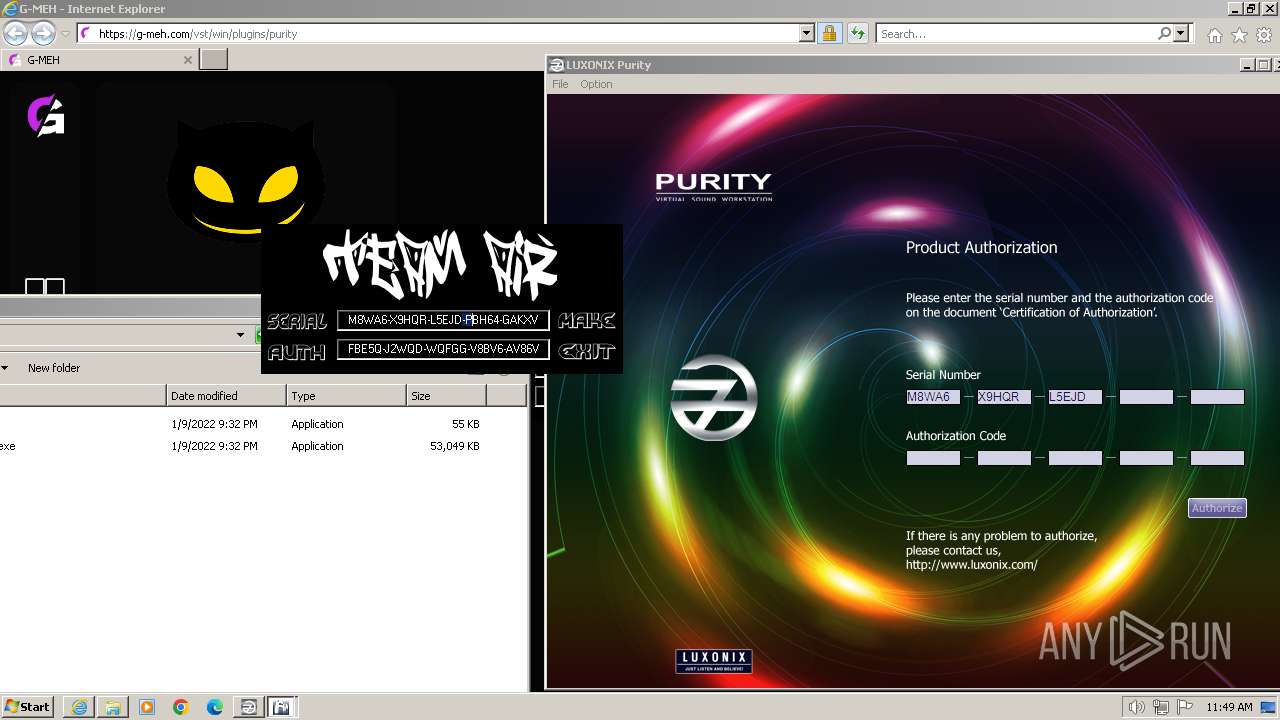
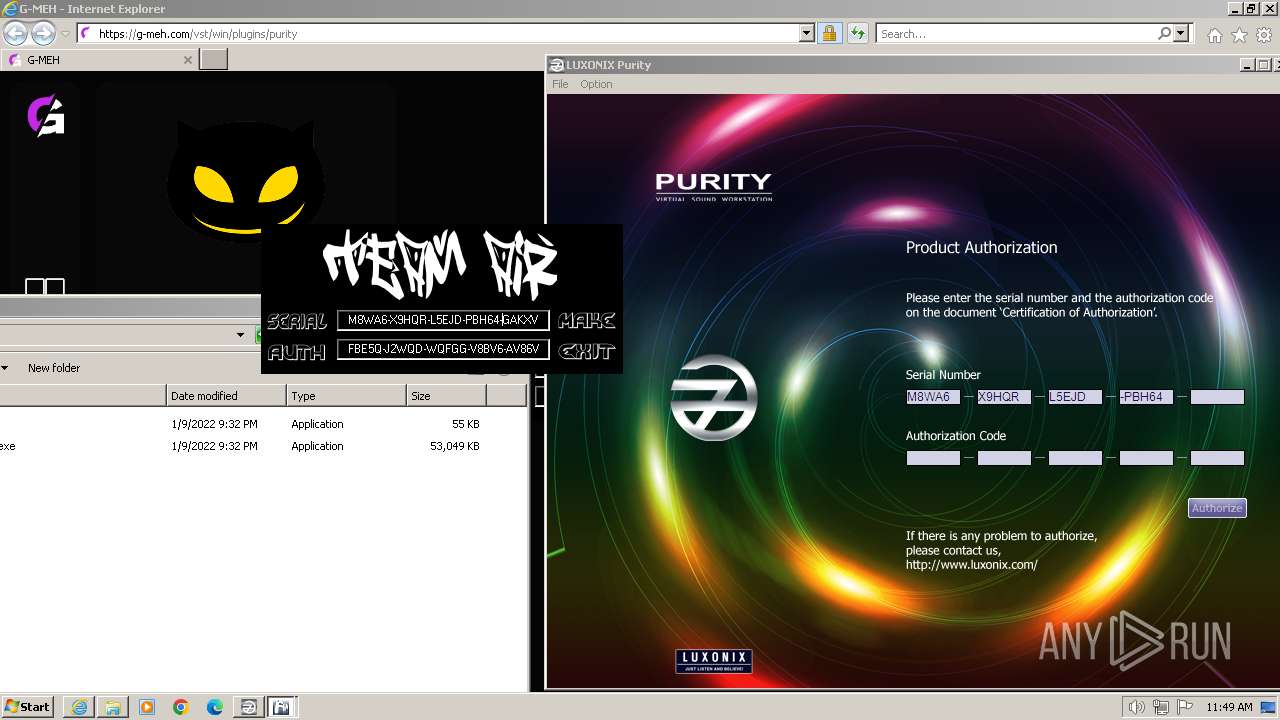
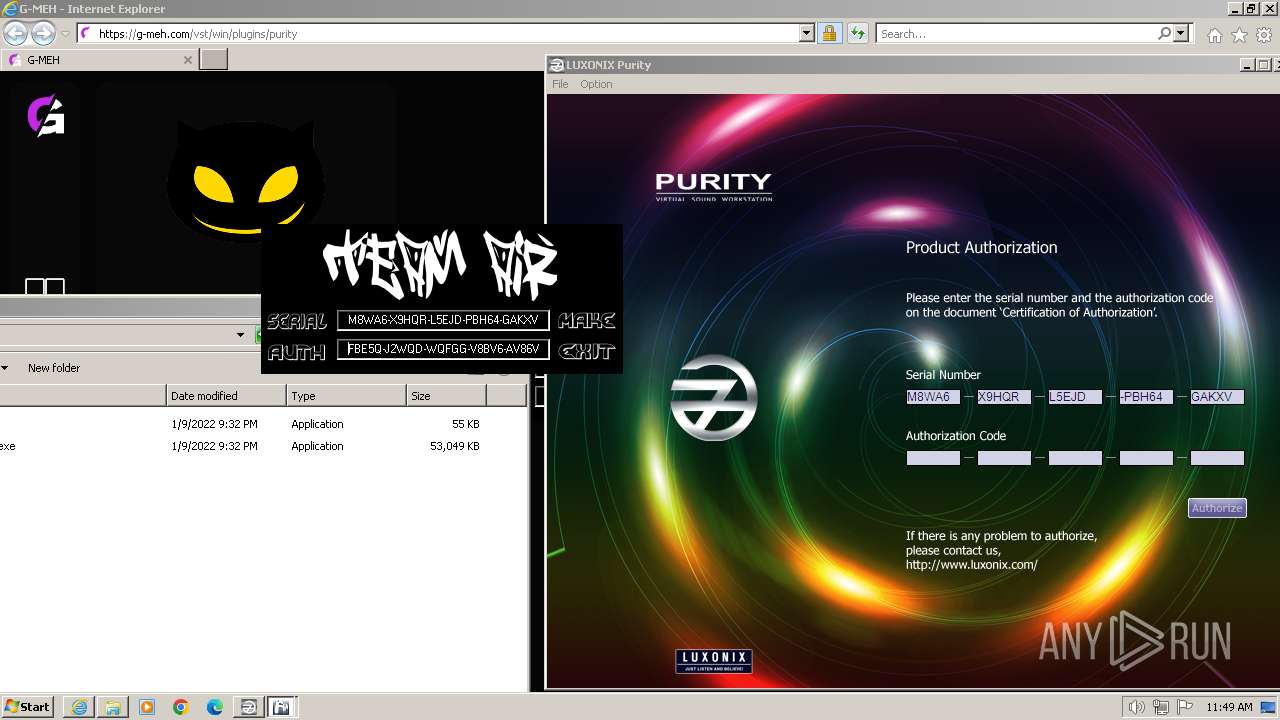
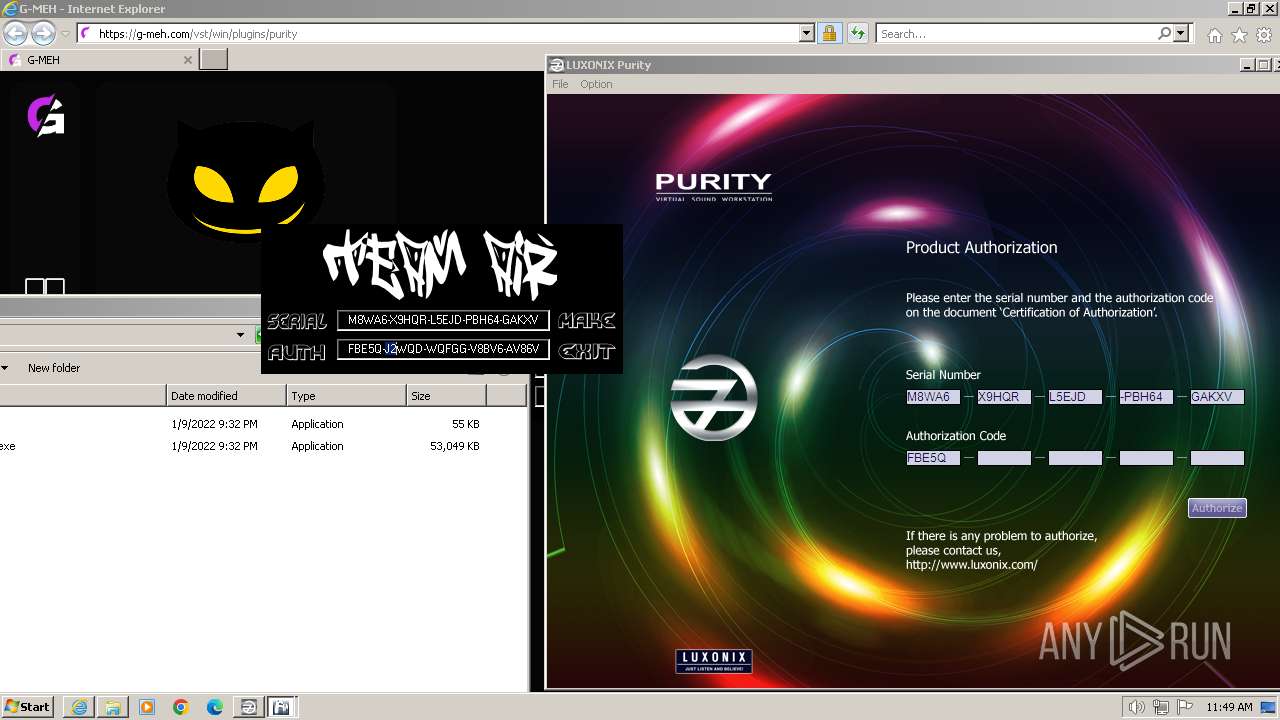
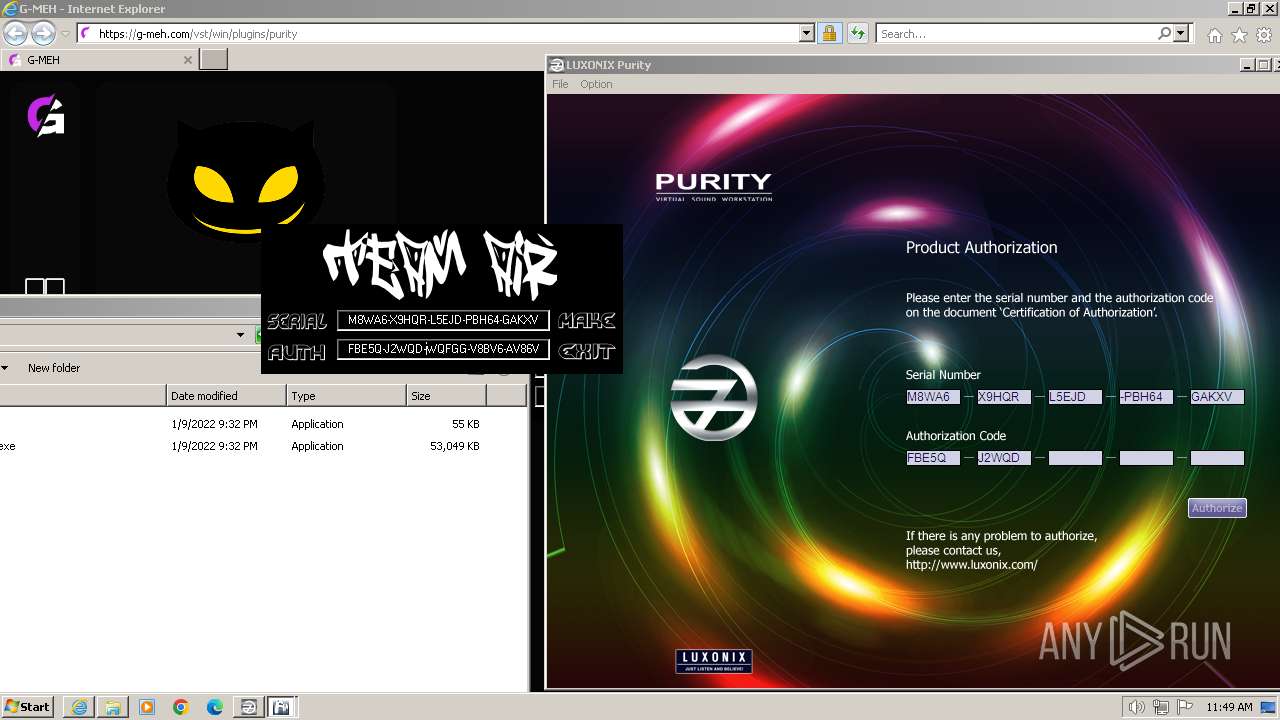
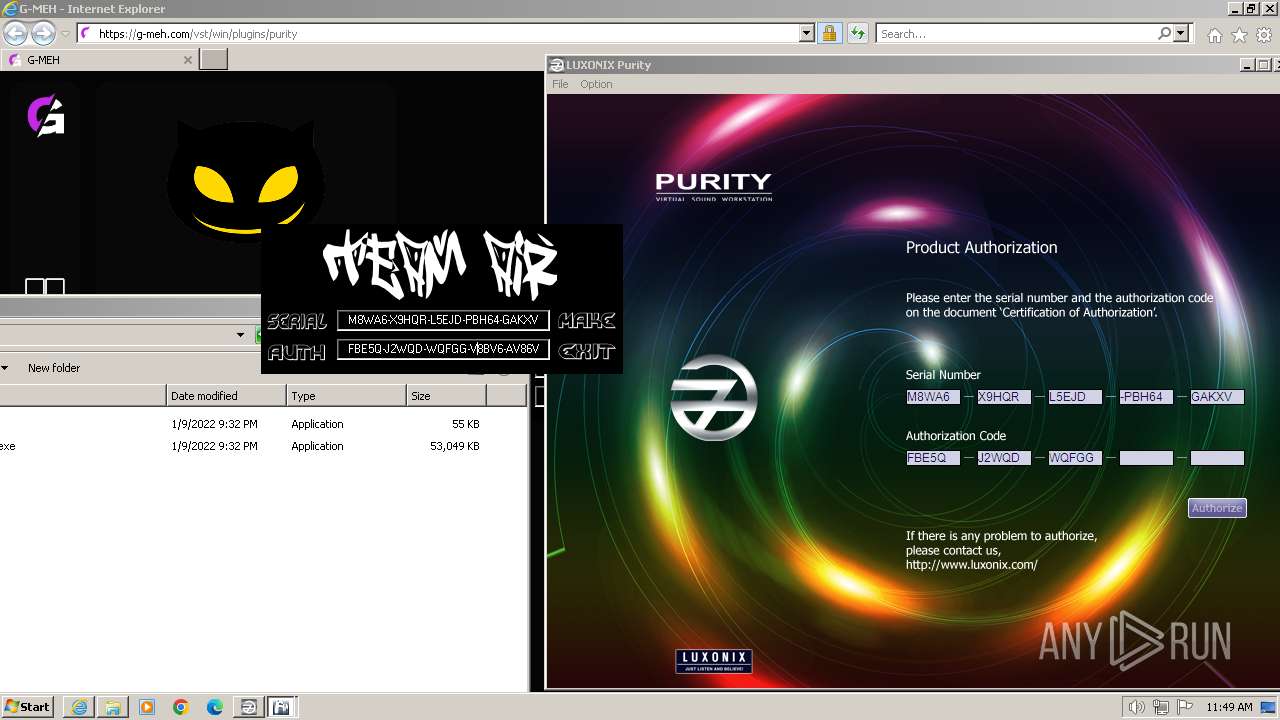
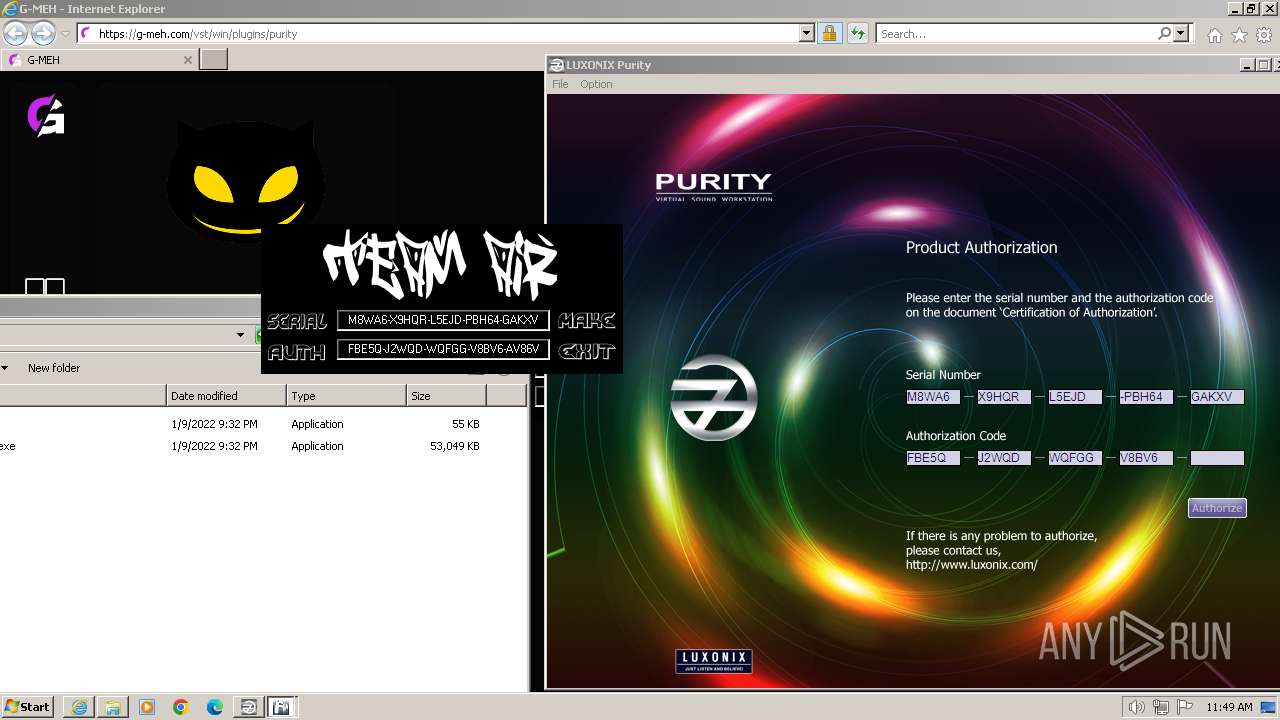
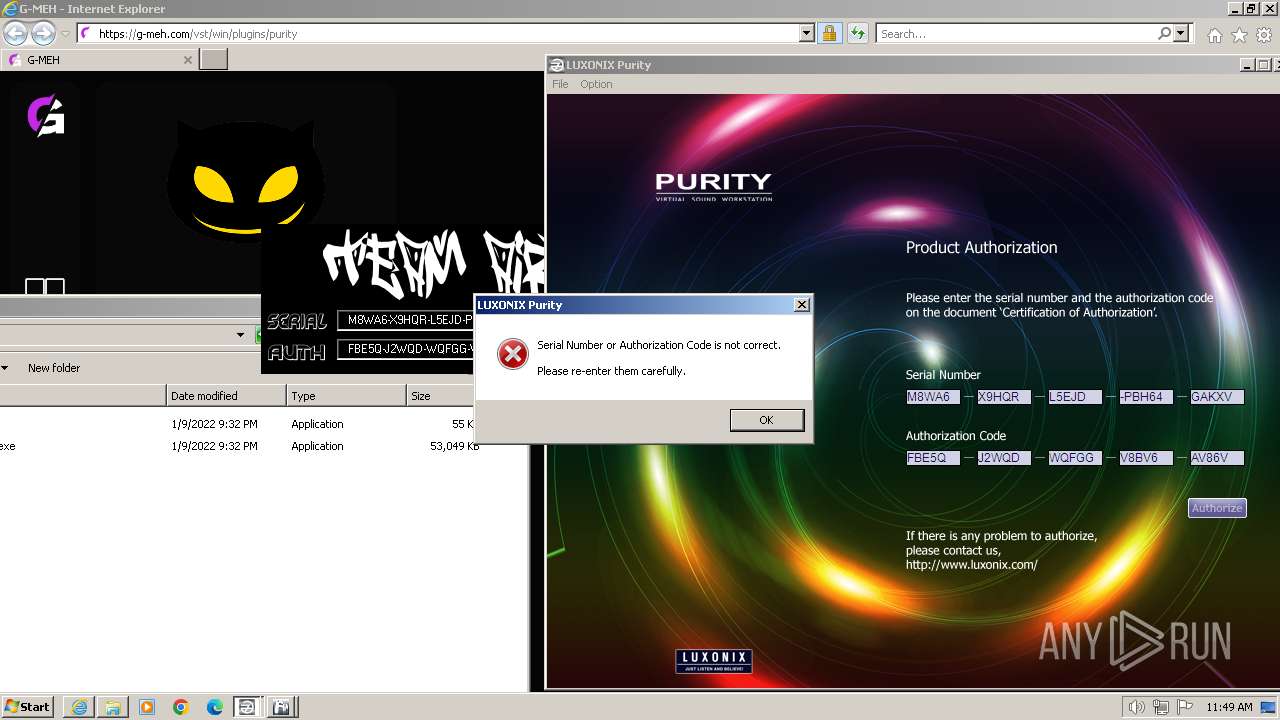
Purity.exe | [2024/01/30 11:49:54] [ERROR] Serial Number or Authorization Code is not correct. - Please re-enter them carefully.
|