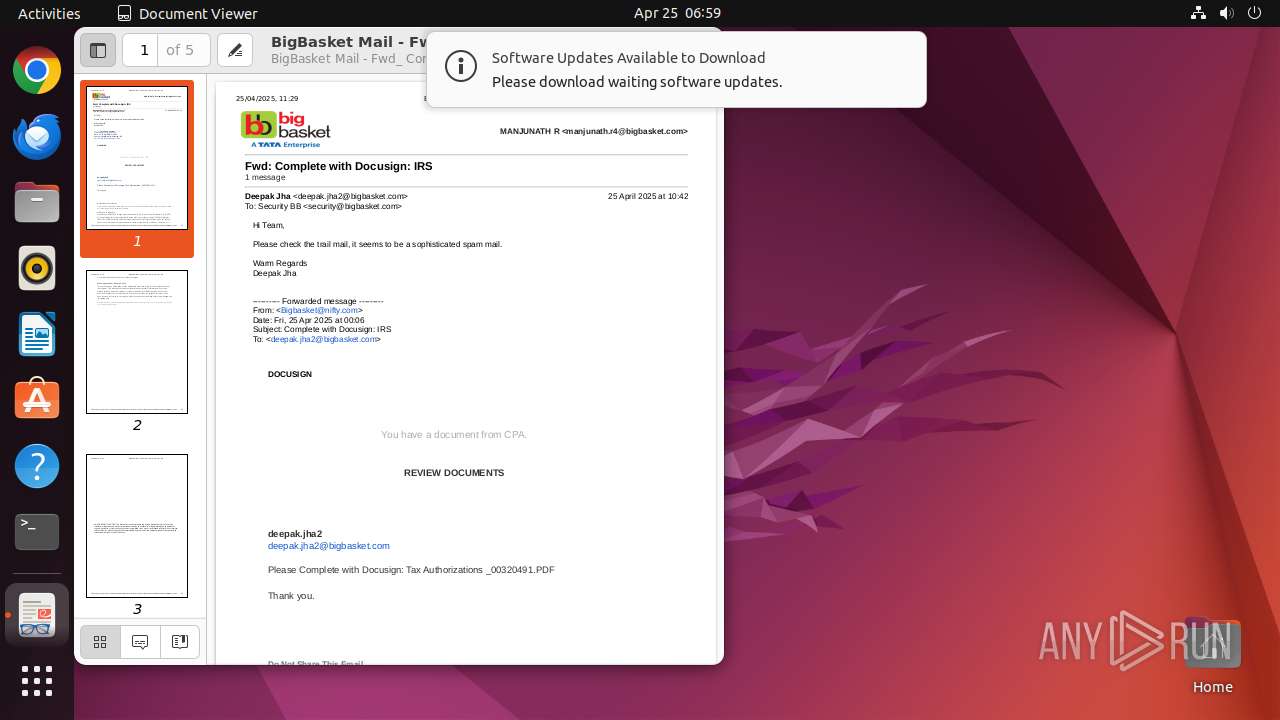
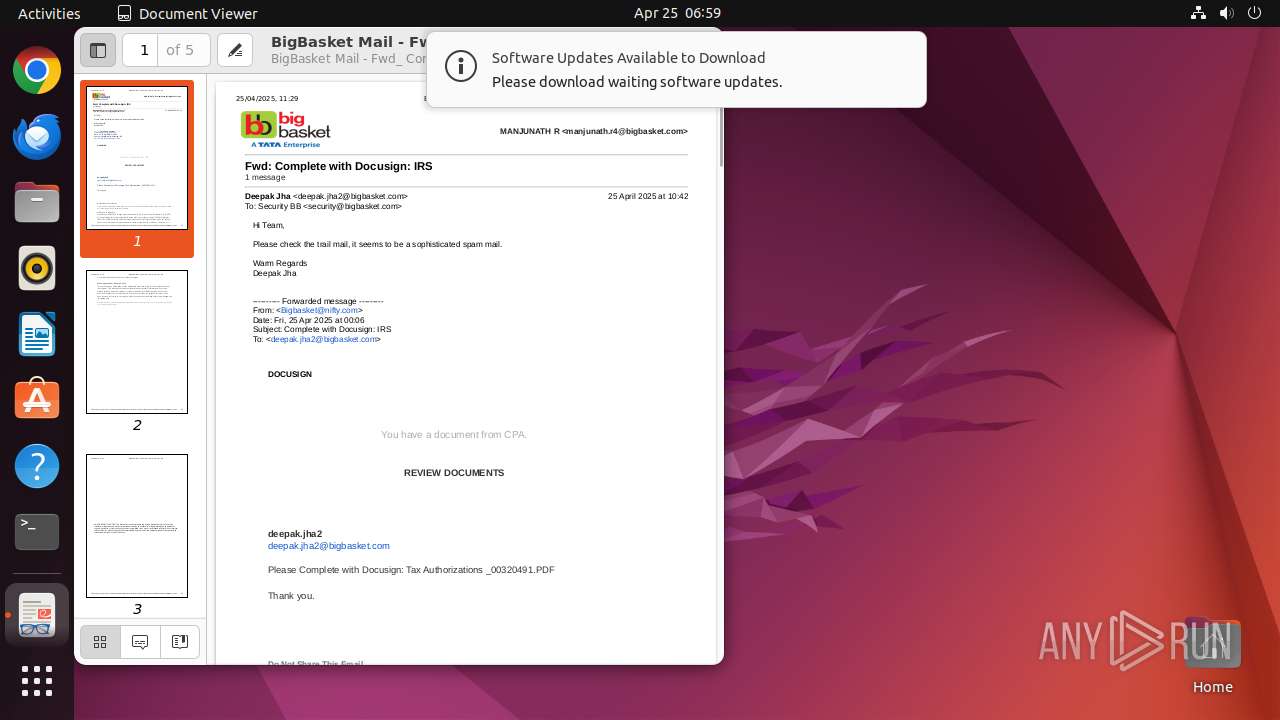
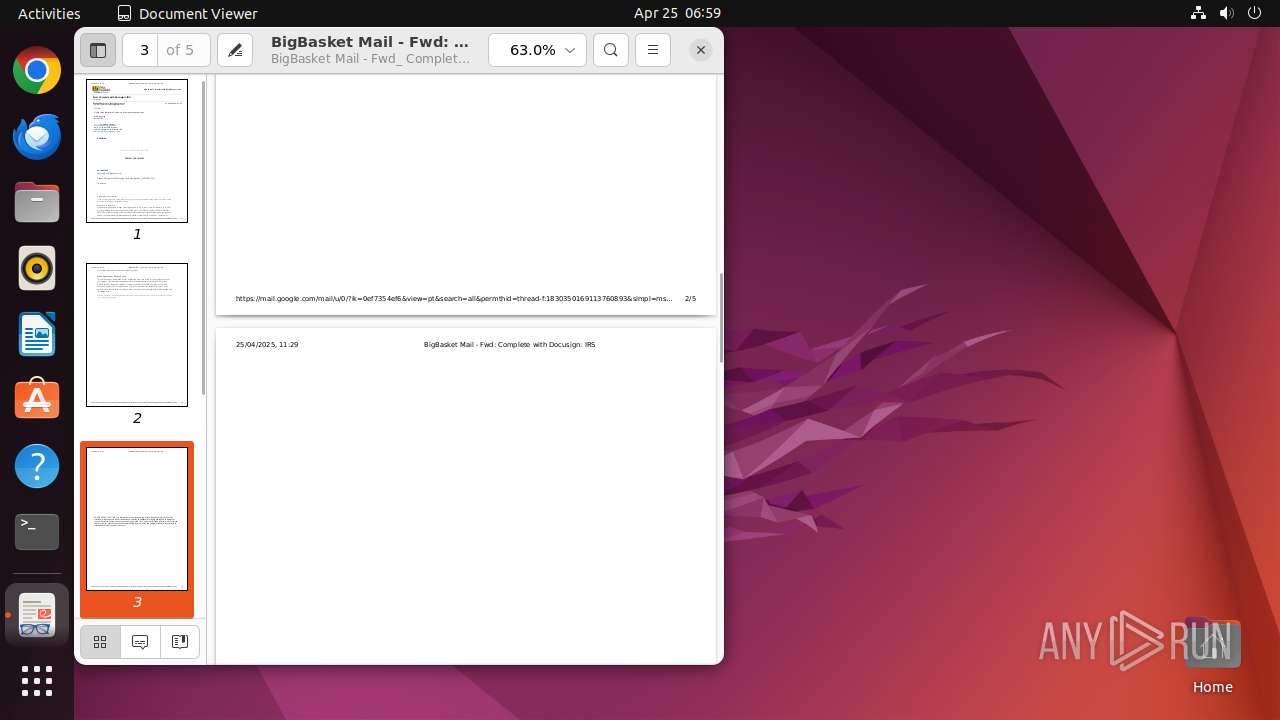
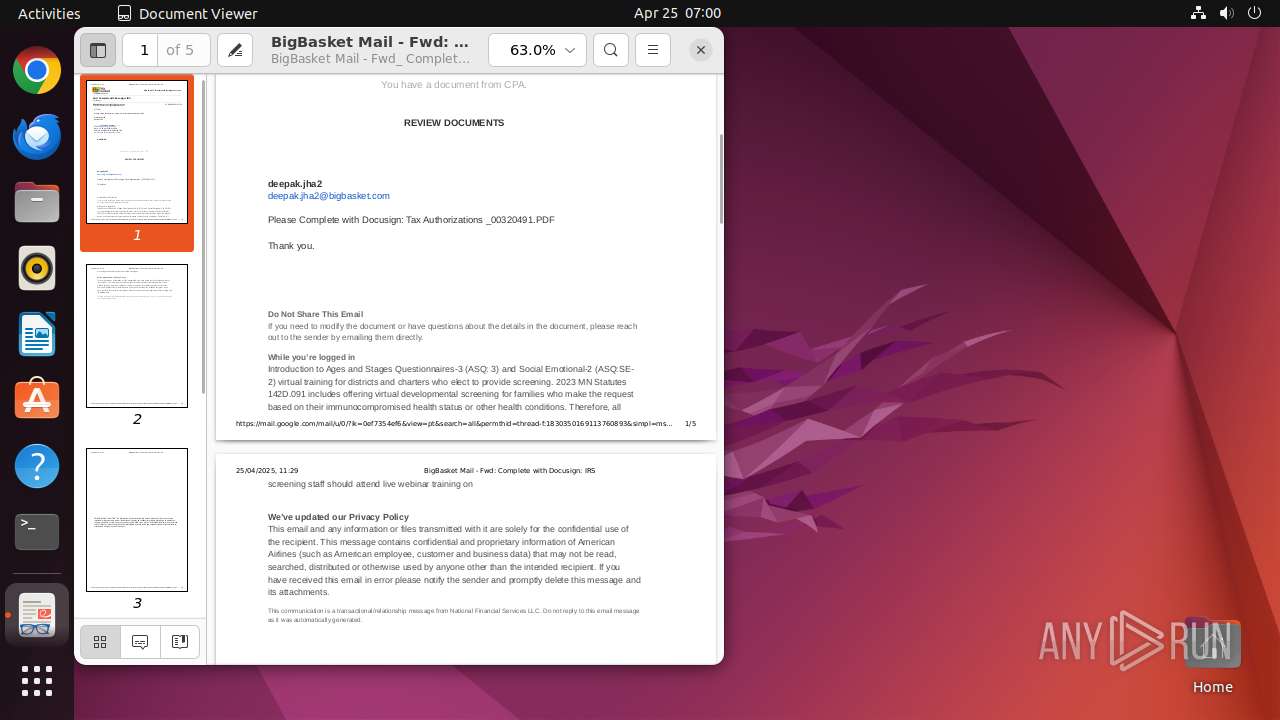
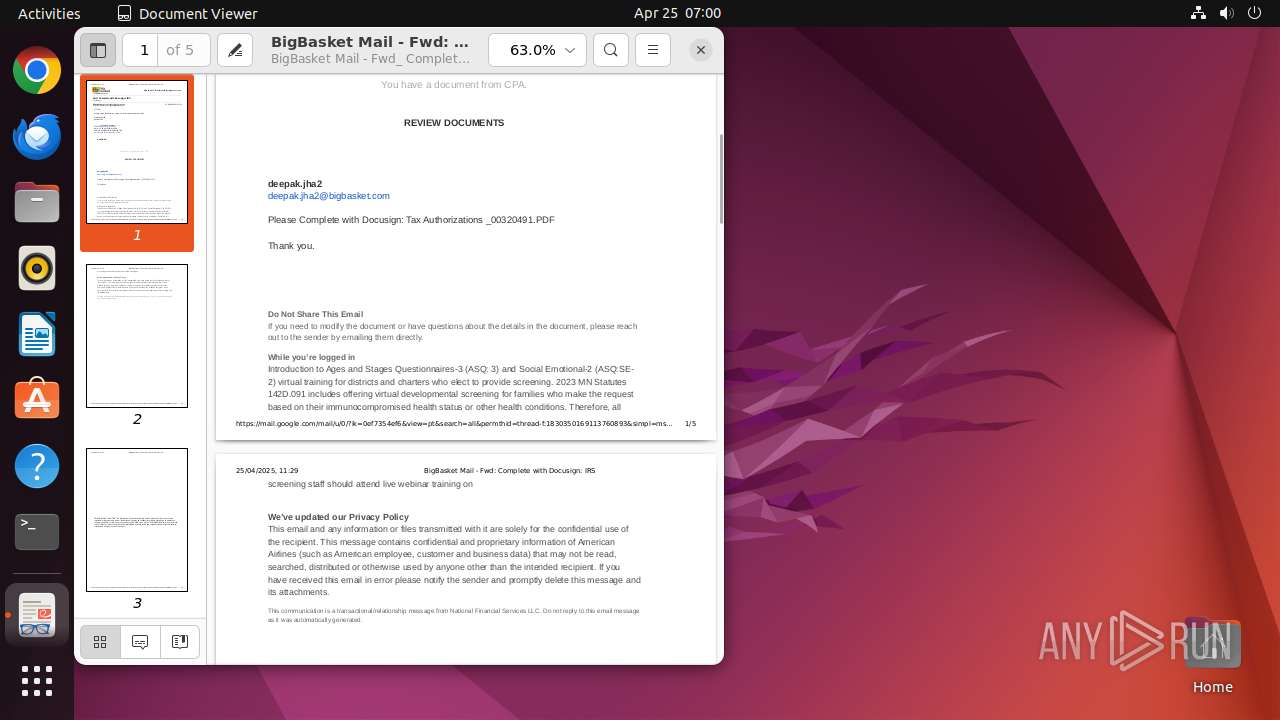
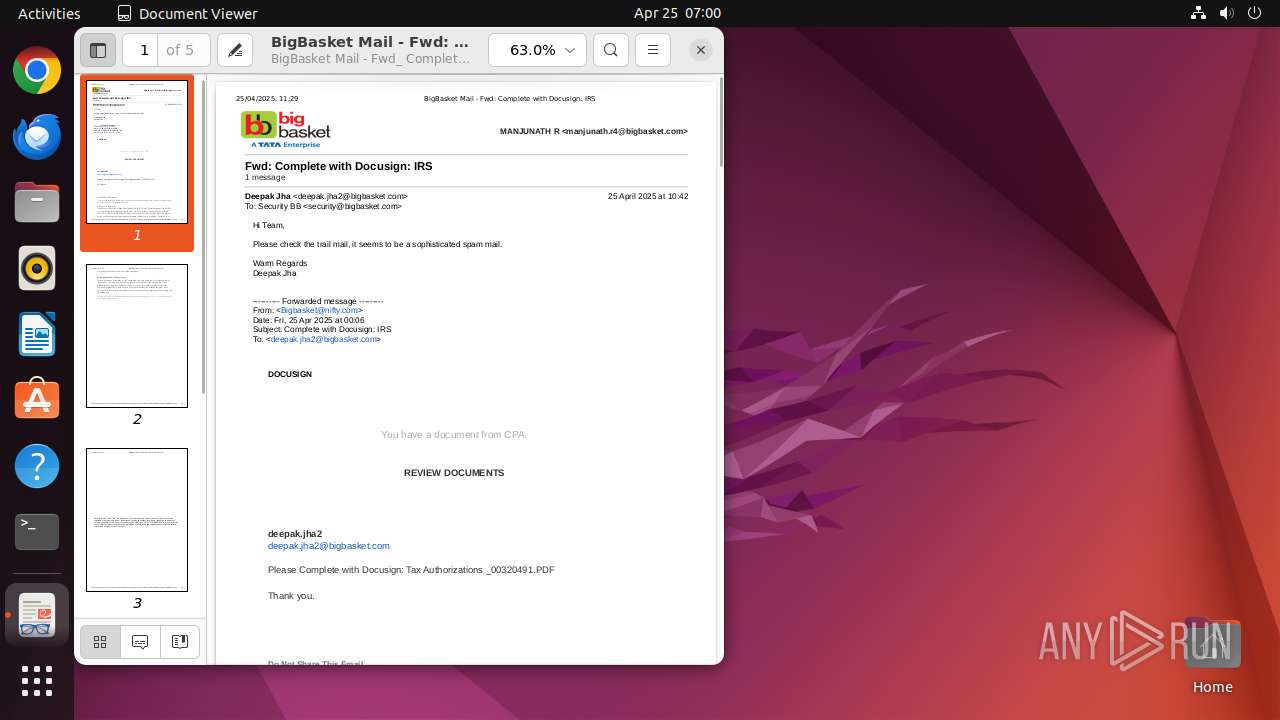
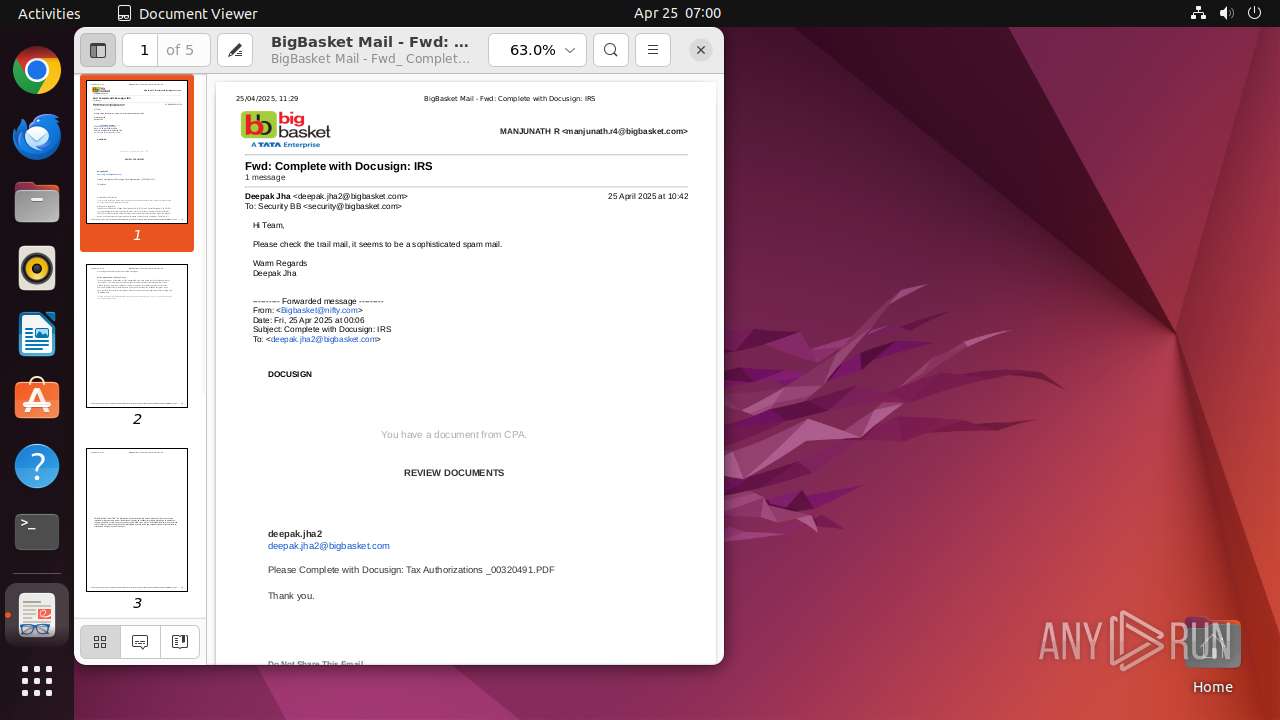
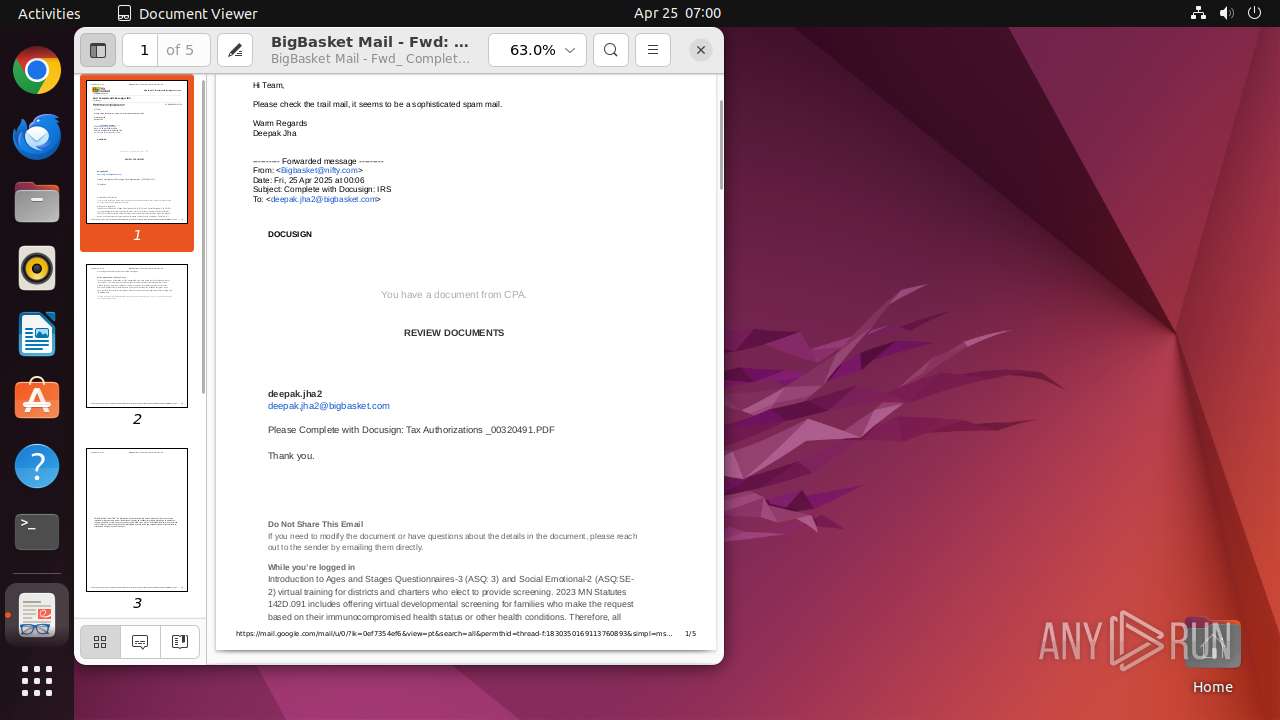
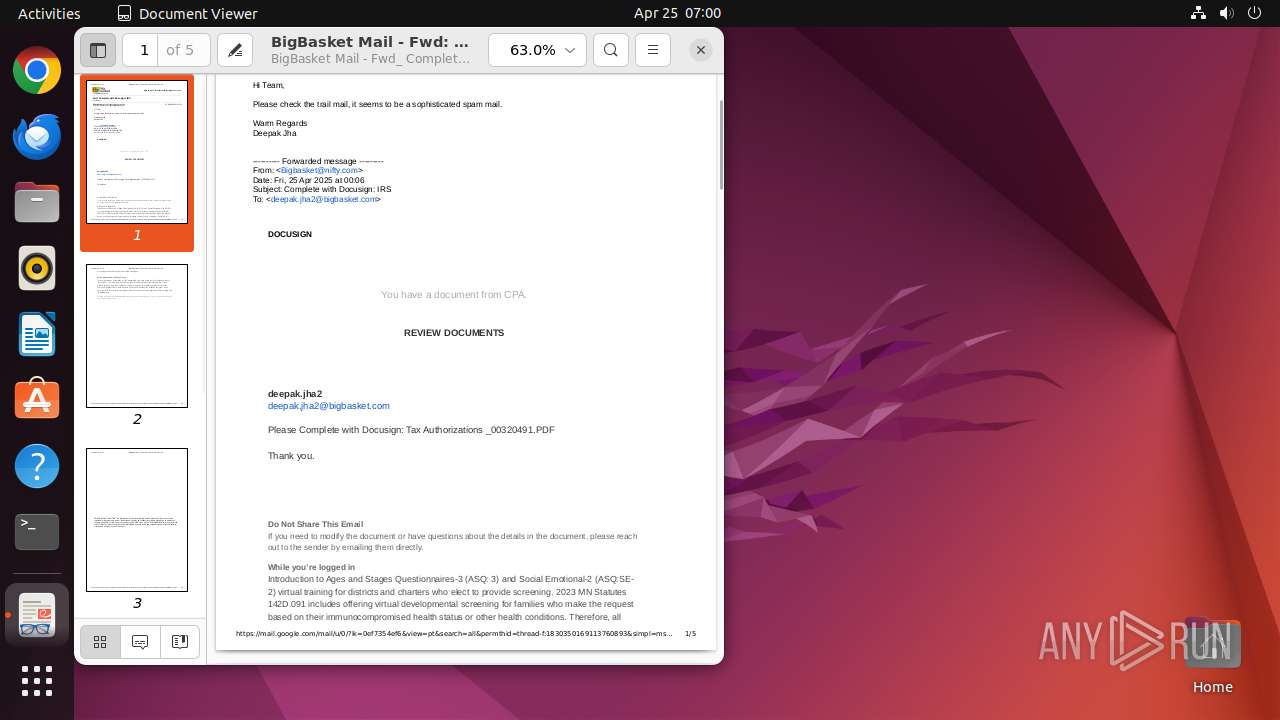
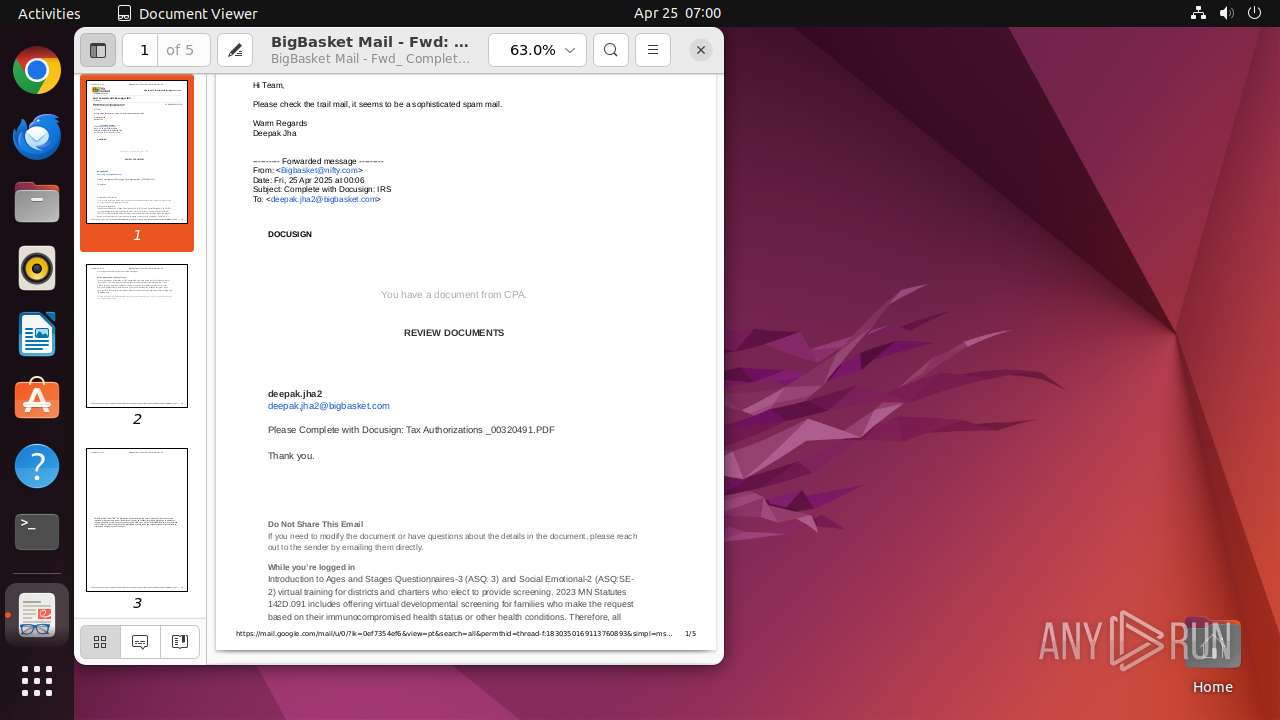
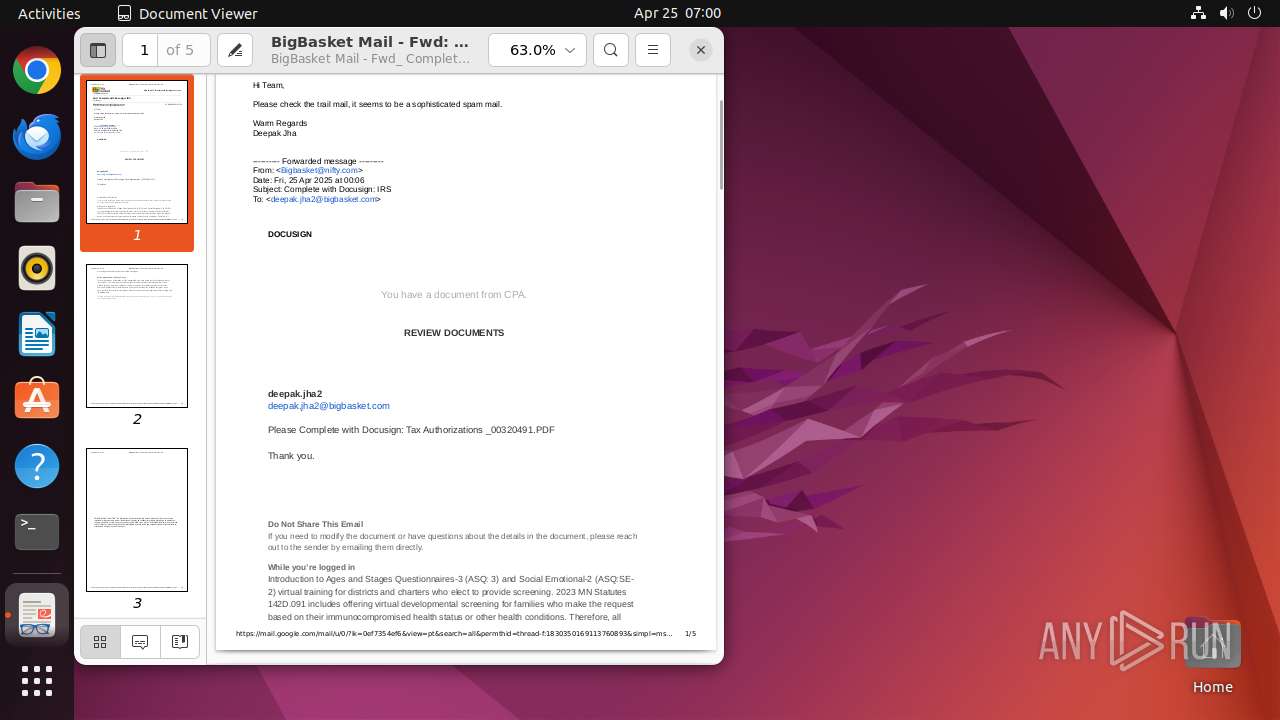
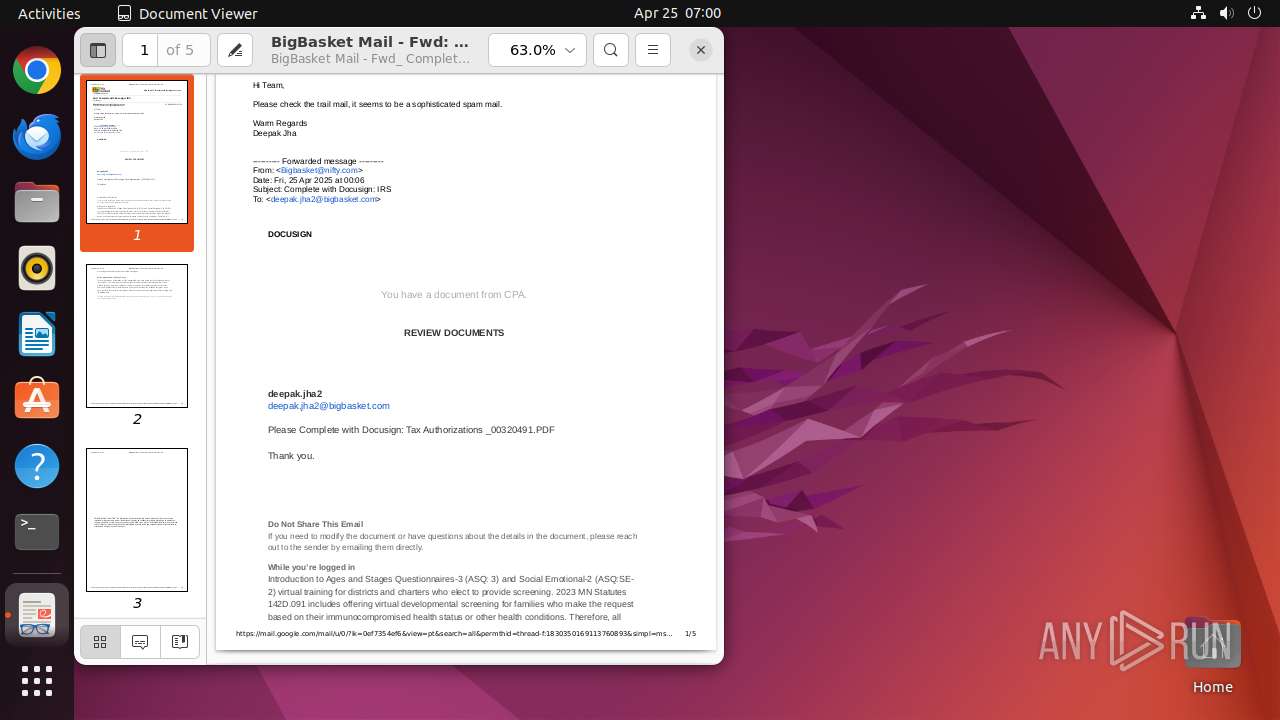
| File name: | BigBasket Mail - Fwd_ Complete with Docusign_ IRS.pdf |
| Full analysis: | https://app.any.run/tasks/a2c64d13-4e69-4f8e-85c6-aac84e9407c4 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 05:59:34 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.4, 5 page(s) |
| MD5: | 9ECC9FAF966DCCC44285623368847032 |
| SHA1: | C3A7C0DC5B9DC1A205EFB3B014B4142EA374BFDB |
| SHA256: | 06ABA35AA8FC87C1CA40B2F240D1EB40E96DC69A00BFF4FEE96B91D09FE29EC0 |
| SSDEEP: | 6144:aDNmVhLpesObP76+jzqbxNxxYTVKURT93lC:gNmh9nOzG+jzqbTYTVKeT9o |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads profile file
- evince (PID: 40661)
Reads passwd file
- evince (PID: 40661)
Executes commands using command-line interpreter
- sudo (PID: 40659)
INFO
Checks timezone
- evince (PID: 40661)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.4 |
|---|---|
| Linearized: | No |
| PageCount: | 5 |
| TaggedPDF: | Yes |
| Language: | en-GB |
| Title: | BigBasket Mail - Fwd: Complete with Docusign: IRS |
| Creator: | Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36 |
| Producer: | Skia/PDF m134 |
| CreateDate: | 2025:04:25 05:59:07+00:00 |
| ModifyDate: | 2025:04:25 05:59:07+00:00 |
Total processes
232
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 40658 | /bin/sh -c "DISPLAY=:0 sudo -iu user evince \"/tmp/BigBasket Mail - Fwd_ Complete with Docusign_ IRS\.pdf\" " | /usr/bin/dash | — | any-guest-agent |
User: user Integrity Level: UNKNOWN | ||||
| 40659 | sudo -iu user evince "/tmp/BigBasket Mail - Fwd_ Complete with Docusign_ IRS\.pdf" | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 40660 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40661 | evince "/tmp/BigBasket Mail - Fwd_ Complete with Docusign_ IRS\.pdf" | /usr/bin/evince | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 40662 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | evince |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40667 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40668 | /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only | /usr/bin/dbus-daemon | — | dbus-daemon |
User: user Integrity Level: UNKNOWN Exit code: 9 | ||||
| 40669 | /usr/libexec/evinced | /usr/libexec/evinced | — | dbus-daemon |
User: user Integrity Level: UNKNOWN | ||||
| 40678 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40682 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 40661 | evince | /home/user/.local/share/recently-used.xbel.33RH52 | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
11
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.190.96:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
— | — | 195.181.175.40:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
512 | snapd | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
512 | snapd | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
google.com |
| whitelisted |
api.snapcraft.io |
| whitelisted |
12.100.168.192.in-addr.arpa |
| unknown |