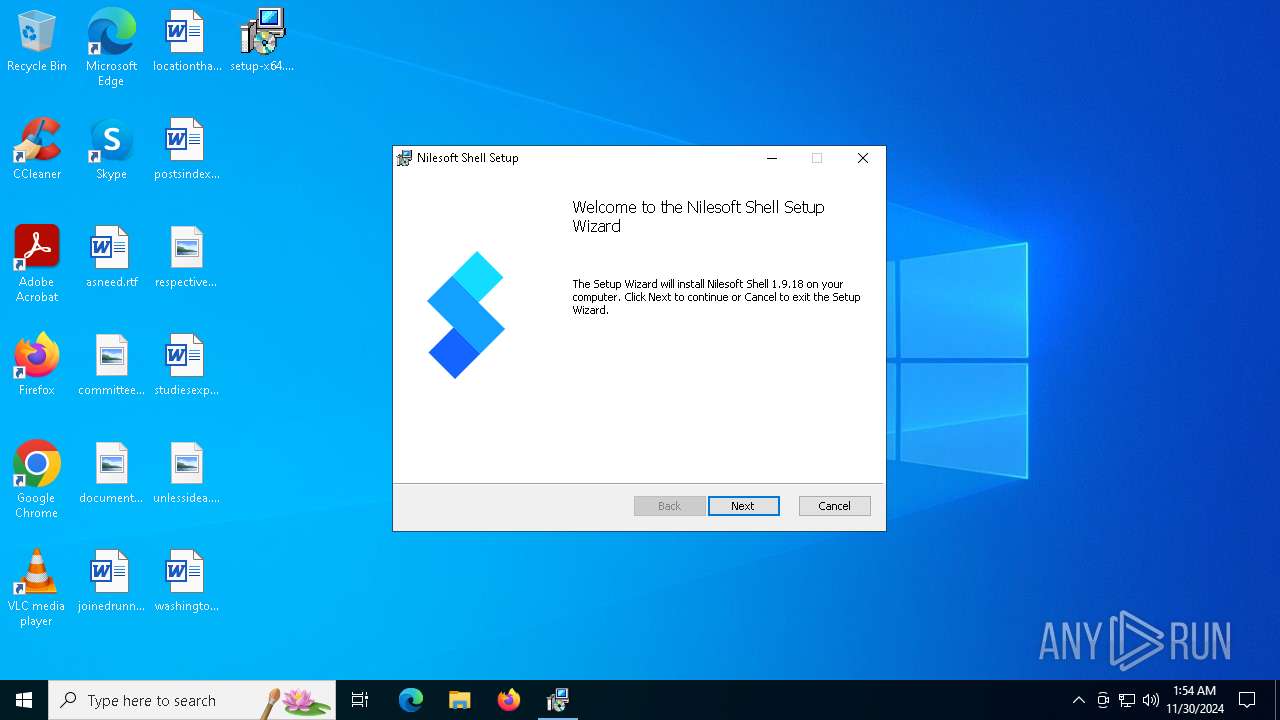
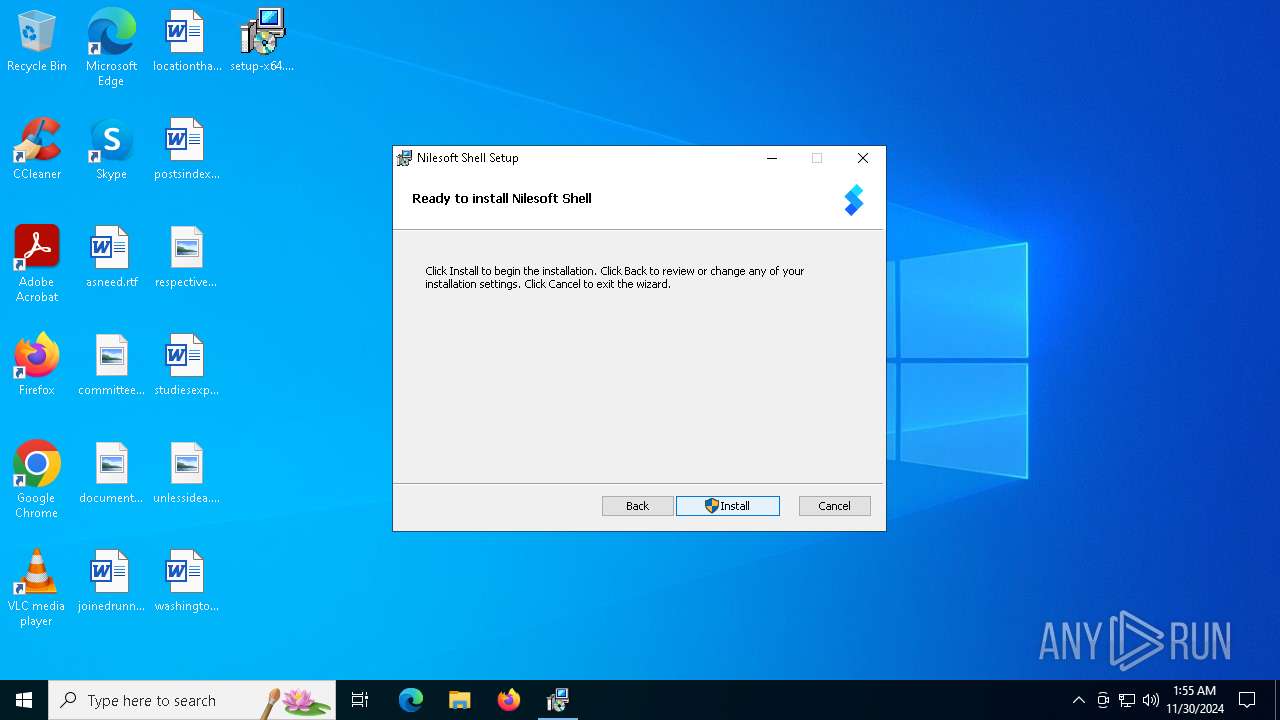
| File name: | setup-x64.msi |
| Full analysis: | https://app.any.run/tasks/960e86b8-d3ef-4cd6-82ab-84586e808fe1 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2024, 01:54:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Nilesoft Shell 1.9.18 x64 Setup, Author: Nilesoft, Keywords: context-menu, right-click, file-explorer, Comments: Nilesoft Shell, Template: x64;1033, Revision Number: {04203AF0-96C0-4606-A225-00E6AB068ED7}, Create Time/Date: Tue Nov 26 20:41:52 2024, Last Saved Time/Date: Tue Nov 26 20:41:52 2024, Number of Pages: 500, Number of Words: 2, Name of Creating Application: WiX Toolset (5.0.2.0), Security: 2 |
| MD5: | 41CC840FA78C573FB89F342C7AFCBF12 |
| SHA1: | D44E137C6450B96E5C58978B4344ACCAE6464F5B |
| SHA256: | 06A44D6831E2AAB27D8913B312AB65C3E0B1BE739D02F6F88EDFB8747C74D8A4 |
| SSDEEP: | 49152:D+0rXEaEdVIChv4+Kb00WvTLc7yi5pH6EW5Xb5wcR4Fo9NM46iwuIz4W3v/xvX2s:DxEdVIChvmblWbLc7HzHJYNOuN6lR4gZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1480)
Executes as Windows Service
- VSSVC.exe (PID: 4468)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5320)
- StartMenuExperienceHost.exe (PID: 5328)
The process creates files with name similar to system file names
- msiexec.exe (PID: 1480)
Reads the date of Windows installation
- msiexec.exe (PID: 5320)
- StartMenuExperienceHost.exe (PID: 5328)
- SearchApp.exe (PID: 520)
Creates/Modifies COM task schedule object
- shell.exe (PID: 5872)
INFO
Reads the computer name
- msiexec.exe (PID: 1480)
- msiexec.exe (PID: 5320)
- StartMenuExperienceHost.exe (PID: 5328)
- SearchApp.exe (PID: 520)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1480)
An automatically generated document
- msiexec.exe (PID: 3832)
Manages system restore points
- SrTasks.exe (PID: 4992)
Checks supported languages
- msiexec.exe (PID: 5320)
- msiexec.exe (PID: 1480)
- shell.exe (PID: 5872)
- StartMenuExperienceHost.exe (PID: 5328)
- SearchApp.exe (PID: 520)
Application launched itself
- msiexec.exe (PID: 1480)
Creates a software uninstall entry
- msiexec.exe (PID: 1480)
Process checks computer location settings
- msiexec.exe (PID: 5320)
- StartMenuExperienceHost.exe (PID: 5328)
- SearchApp.exe (PID: 520)
The process uses the downloaded file
- msiexec.exe (PID: 5320)
Reads product name
- shell.exe (PID: 5872)
Reads Environment values
- shell.exe (PID: 5872)
- SearchApp.exe (PID: 520)
Creates files in the program directory
- shell.exe (PID: 5872)
Sends debugging messages
- StartMenuExperienceHost.exe (PID: 5328)
Checks proxy server information
- SearchApp.exe (PID: 520)
Reads the software policy settings
- SearchApp.exe (PID: 520)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Nilesoft Shell 1.9.18 x64 Setup |
| Author: | Nilesoft |
| Keywords: | context-menu, right-click, file-explorer |
| Comments: | Nilesoft Shell |
| Template: | x64;1033 |
| RevisionNumber: | {04203AF0-96C0-4606-A225-00E6AB068ED7} |
| CreateDate: | 2024:11:26 20:41:52 |
| ModifyDate: | 2024:11:26 20:41:52 |
| Pages: | 500 |
| Words: | 2 |
| Software: | WiX Toolset (5.0.2.0) |
| Security: | Read-only recommended |
Total processes
131
Monitored processes
10
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3564 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3832 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\setup-x64.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4468 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4992 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5320 | C:\Windows\System32\MsiExec.exe -Embedding A8688F969AF7A28B95A53669B8E98F86 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5328 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5872 | "C:\Program Files\Nilesoft Shell\shell.exe" -r -s -t -restart | C:\Program Files\Nilesoft Shell\shell.exe | msiexec.exe | ||||||||||||
User: admin Company: Nilesoft Integrity Level: HIGH Description: Nilesoft Shell Exit code: 1 Version: 1.9.18 Modules
| |||||||||||||||
| 6428 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 506
Read events
17 146
Write events
344
Delete events
16
Modification events
| (PID) Process: | (1480) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000019274BE2CA42DB01C8050000C4110000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1480) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000FE6508E2CA42DB01C8050000C4110000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1480) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000FE6508E2CA42DB01C8050000C4110000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1480) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000038FD43E2CA42DB01C8050000C4110000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1480) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000038FD43E2CA42DB01C8050000C4110000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1480) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (4468) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000008786C9E2CA42DB0174110000FC150000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4468) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000008786C9E2CA42DB0174110000CC020000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4468) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000008786C9E2CA42DB0174110000D00D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4468) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000008786C9E2CA42DB017411000034090000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
8
Suspicious files
26
Text files
99
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1480 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1480 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{0718d488-b683-4a41-aa7d-f822710df9ac}_OnDiskSnapshotProp | binary | |
MD5:170E4A98BB16508D714AE9D3C46BA09A | SHA256:94B3B0576A7859381311B3600082FF808E7CDA250EC284ACCA6A04E83165D2BC | |||
| 1480 | msiexec.exe | C:\Windows\Installer\MSICCC9.tmp | executable | |
MD5:7BBAE6FC3C5A5DC625BE43E001B2E8AF | SHA256:A887383025796AEA4F18D25D07C67EEC15D967C098D0BFD555F8806506C5436A | |||
| 1480 | msiexec.exe | C:\Program Files\Nilesoft Shell\shell.exe | executable | |
MD5:0D4A905369048F934A1B0472F581D7B6 | SHA256:548FB2007054B9CF5E90D407C366F048E041F606A023F552D0C99D20FF3FA7A6 | |||
| 1480 | msiexec.exe | C:\Program Files\Nilesoft Shell\imports\taskbar.nss | text | |
MD5:260FB00C05E6B77642A36AA8C423F238 | SHA256:915E178329803BF5805C6A7D8BCB7A223D27B7A2DC35FB75E93584BD38A38D74 | |||
| 1480 | msiexec.exe | C:\Program Files\Nilesoft Shell\LICENSE | text | |
MD5:0DDC18B9BE107FE63EFFEDFD84F64724 | SHA256:6AEF50956245B6CA8BC5191B98B101ADB5460B6D947940CA457321D3022C6C2D | |||
| 1480 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:1C8BF49CBCA0B55E1060ACED91DFCD82 | SHA256:12C767E4E72E8B2A8A2B0F998EFD7CE51823C958F1E35C02FC616D5E2FF19E58 | |||
| 1480 | msiexec.exe | C:\Program Files\Nilesoft Shell\readme.txt | text | |
MD5:D9934E876F5F71A952068D9AADFAB63C | SHA256:CDA839657ACEF7EE63811FBB19CD01A724F97D63FDA4DD55FFBB3C4612D02E25 | |||
| 1480 | msiexec.exe | C:\Program Files\Nilesoft Shell\imports\file-manage.nss | html | |
MD5:15B733805BE680EE1CFC97019EB1E673 | SHA256:B1FE8E12ECA260077DD57D076A29C8616DAA8A7AA97CD6D3AE72BC2E0E4613B2 | |||
| 1480 | msiexec.exe | C:\Program Files\Nilesoft Shell\imports\images.nss | text | |
MD5:DB66AAAFA80B55A1AF1C91F74365DFBF | SHA256:CD7B5CE437028663ECADBCC036B58E4588E16158889D781125893400661121B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
23
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 104.126.37.145:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.126.37.145:443 | https://r.bing.com/rb/3H/ortl,cc,nc/4-xJy3tX6bM2BGl5zKioiEcQ1TU.css?bu=A4gCjAKPAg&or=w | unknown | text | 15.5 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.131:443 | https://r.bing.com/rb/6m/cir3,ortl,cc,nc/721j67Wlp0RIfqXSsYlKD2mNH-Y.css?bu=M8IKvArICrwKrAu8CrILvAq8CrwKvQu8CsQLvArKC7wK0Au8CtYLvAraCrwK4Aq8CtQKvAq8CqMLvArvCrwK9Qq8CukKvAr7CoULiAu8CrwKoAuOC7wKlAuXC7wKggy8CtwLvAqwDA&or=w | unknown | text | 443 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.145:443 | https://www.bing.com/manifest/threshold.appcache | unknown | text | 3.37 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.131:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | s | 21.3 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.145:443 | https://r.bing.com/rb/6m/ortl,cc,nc/QNBBNqWD9F_Blep-UqQSqnMp-FI.css?bu=AbwK&or=w | unknown | text | 6 b | whitelisted |
— | — | GET | 200 | 104.126.37.131:443 | https://r.bing.com/rb/6m/ortl,cc,nc/_BjeFNPDJ-N9umMValublyrbq4Y.css?bu=CZ0MvAqiDLwKpgy8CrwKvAq8Cg&or=w | unknown | text | 428 Kb | whitelisted |
— | — | POST | 204 | 104.126.37.145:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
520 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |