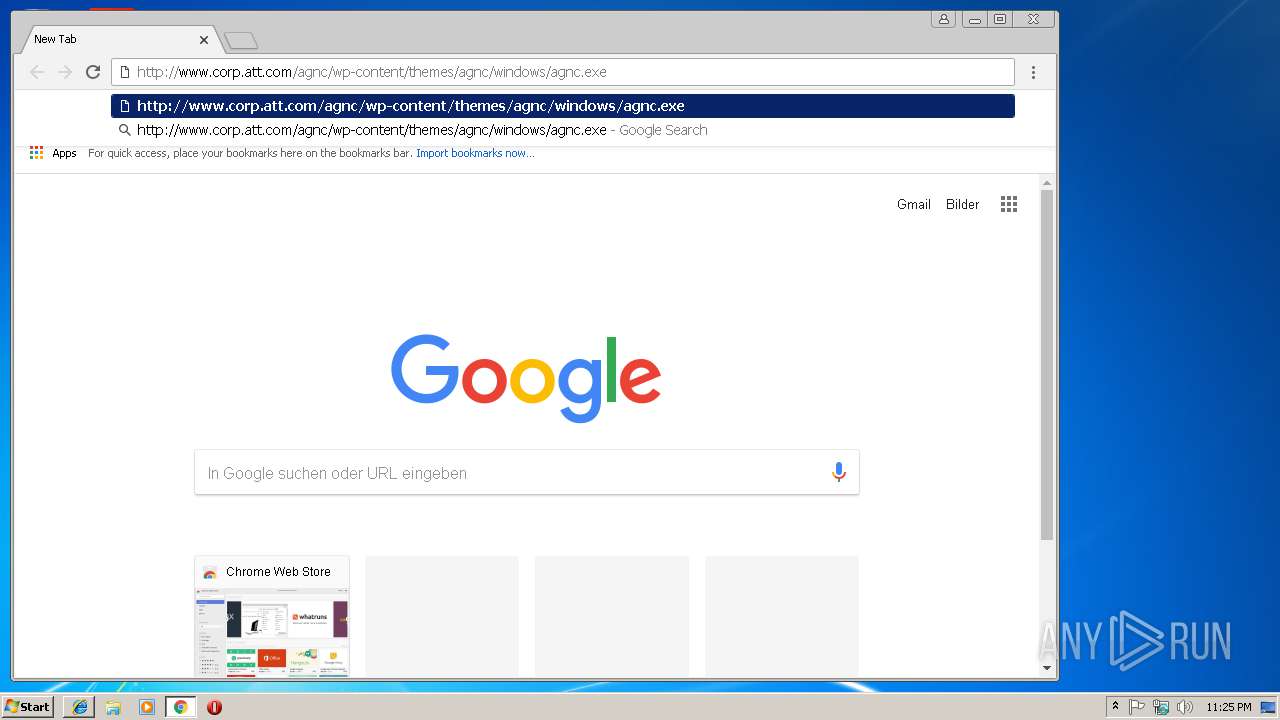
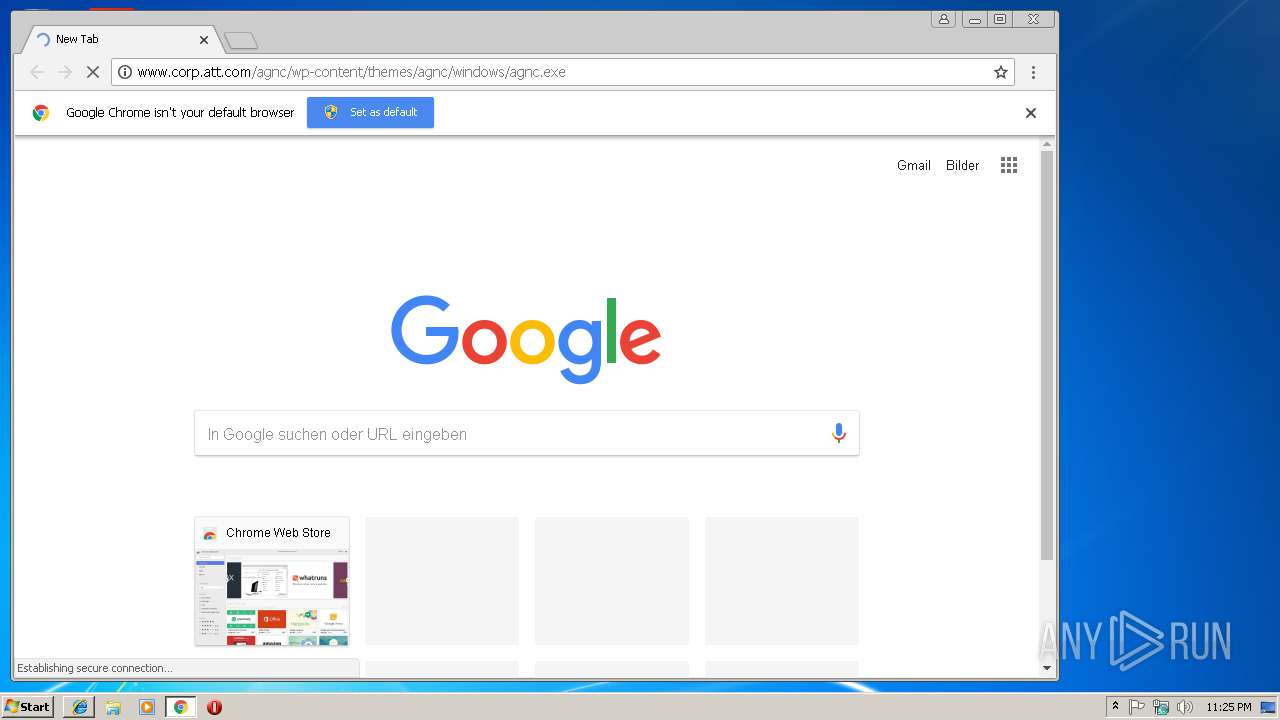
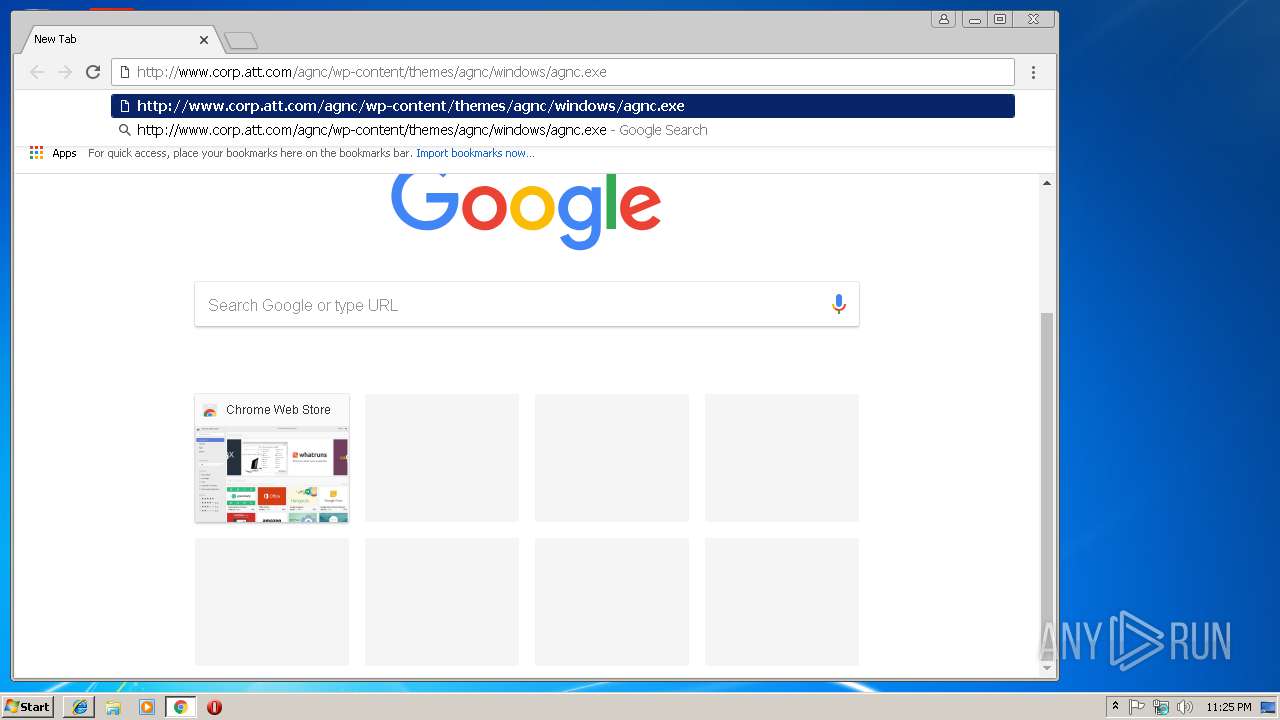
| URL: | http://www.corp.att.com/agnc/wp-content/themes/agnc/windows/agnc.exe |
| Full analysis: | https://app.any.run/tasks/a25784e3-30d9-4267-be28-29d8db7102ed |
| Verdict: | Malicious activity |
| Threats: | Trojans are a group of malicious programs distinguished by their ability to masquerade as benign software. Depending on their type, trojans possess a variety of capabilities, ranging from maintaining full remote control over the victim’s machine to stealing data and files, as well as dropping other malware. At the same time, the main functionality of each trojan family can differ significantly depending on its type. The most common trojan infection chain starts with a phishing email. |
| Analysis date: | March 14, 2019, 23:24:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 324E7779F5B51D4D8854164131813390 |
| SHA1: | 7B966BD8A8867C2B88D4AD5EF381931E3565979D |
| SHA256: | 06783E33267841C0B4489D7518FB1224109F867F792EE8DDBD508A3C3FC8AB4B |
| SSDEEP: | 3:N1KJS48kKoQlAQrFwdSKiIGLN:Cc4coQlAkFwQnIGLN |
MALICIOUS
Application was dropped or rewritten from another process
- agnc.exe (PID: 296)
- agnc.exe (PID: 2372)
- agnc.exe (PID: 3472)
- NetVC.exe (PID: 2248)
- NetClientSvc.exe (PID: 3080)
- SwiCardDetect.exe (PID: 2128)
- NetAutoconnectFocusSvc.exe (PID: 3504)
- NetLogSvc.exe (PID: 3812)
- NetClient.exe (PID: 2476)
- netcfgsvr.exe (PID: 2852)
- NetVC.exe (PID: 3580)
- CellularPlugInController.exe (PID: 2864)
- COMSierraCdmaSDKServer.exe (PID: 3612)
- COMSierraGSMSDKServer.exe (PID: 3440)
- COMGobiSDKServer.exe (PID: 2696)
- COMSierraGobiSDKServer.exe (PID: 3128)
- COMOptionSDKServer.exe (PID: 1556)
- COMSIE~1.EXE (PID: 2536)
- COMATCommandSDKServer.exe (PID: 2572)
- COMWMBServer.exe (PID: 1244)
Writes to a start menu file
- msiexec.exe (PID: 3788)
Registers / Runs the DLL via REGSVR32.EXE
- msiexec.exe (PID: 3788)
Loads dropped or rewritten executable
- NetClientSvc.exe (PID: 3080)
- SwiCardDetect.exe (PID: 2128)
- NetAutoconnectFocusSvc.exe (PID: 3504)
- NetLogSvc.exe (PID: 3812)
- MSIEXEC.EXE (PID: 312)
- NetClient.exe (PID: 2476)
- netcfgsvr.exe (PID: 2852)
- CellularPlugInController.exe (PID: 2864)
- COMSierraGSMSDKServer.exe (PID: 3440)
- COMSierraCdmaSDKServer.exe (PID: 3612)
- COMGobiSDKServer.exe (PID: 2696)
- COMSierraGobiSDKServer.exe (PID: 3128)
- COMOptionSDKServer.exe (PID: 1556)
- COMSIE~1.EXE (PID: 2536)
- COMATCommandSDKServer.exe (PID: 2572)
- COMWMBServer.exe (PID: 1244)
Changes the autorun value in the registry
- NetClient.exe (PID: 2476)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3228)
- MSIEXEC.EXE (PID: 312)
- MsiExec.exe (PID: 3716)
- DrvInst.exe (PID: 2036)
- msiexec.exe (PID: 3788)
- DrvInst.exe (PID: 3120)
- MsiExec.exe (PID: 3560)
- DrvInst.exe (PID: 3772)
Creates files in the Windows directory
- msiexec.exe (PID: 3788)
- DrvInst.exe (PID: 2036)
- DrvInst.exe (PID: 3120)
- MsiExec.exe (PID: 3560)
- DrvInst.exe (PID: 3772)
- SwiCardDetect.exe (PID: 2128)
- CellularPlugInController.exe (PID: 2864)
Creates files in the driver directory
- DrvInst.exe (PID: 2036)
- DrvInst.exe (PID: 3120)
- DrvInst.exe (PID: 3772)
- MsiExec.exe (PID: 3560)
Removes files from Windows directory
- DrvInst.exe (PID: 2036)
- DrvInst.exe (PID: 3120)
- DrvInst.exe (PID: 3772)
- MsiExec.exe (PID: 3560)
Starts Microsoft Installer
- agnc.exe (PID: 3472)
Creates COM task schedule object
- MsiExec.exe (PID: 3560)
- msiexec.exe (PID: 3788)
Creates or modifies windows services
- DrvInst.exe (PID: 3772)
Reads Environment values
- NetClientSvc.exe (PID: 3080)
- NetClient.exe (PID: 2476)
- CellularPlugInController.exe (PID: 2864)
Creates files in the program directory
- NetLogSvc.exe (PID: 3812)
Reads Internet Cache Settings
- NetClient.exe (PID: 2476)
Reads internet explorer settings
- NetClient.exe (PID: 2476)
Connects to server without host name
- NetClient.exe (PID: 2476)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2960)
Reads Internet Cache Settings
- chrome.exe (PID: 3228)
- iexplore.exe (PID: 3244)
Reads internet explorer settings
- iexplore.exe (PID: 3244)
Application launched itself
- iexplore.exe (PID: 2960)
- chrome.exe (PID: 3228)
- msiexec.exe (PID: 3788)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2708)
- MsiExec.exe (PID: 3716)
- MsiExec.exe (PID: 3560)
Searches for installed software
- msiexec.exe (PID: 3788)
Low-level read access rights to disk partition
- vssvc.exe (PID: 292)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 3788)
Creates a software uninstall entry
- msiexec.exe (PID: 3788)
Creates files in the program directory
- msiexec.exe (PID: 3788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
87
Monitored processes
49
Malicious processes
18
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
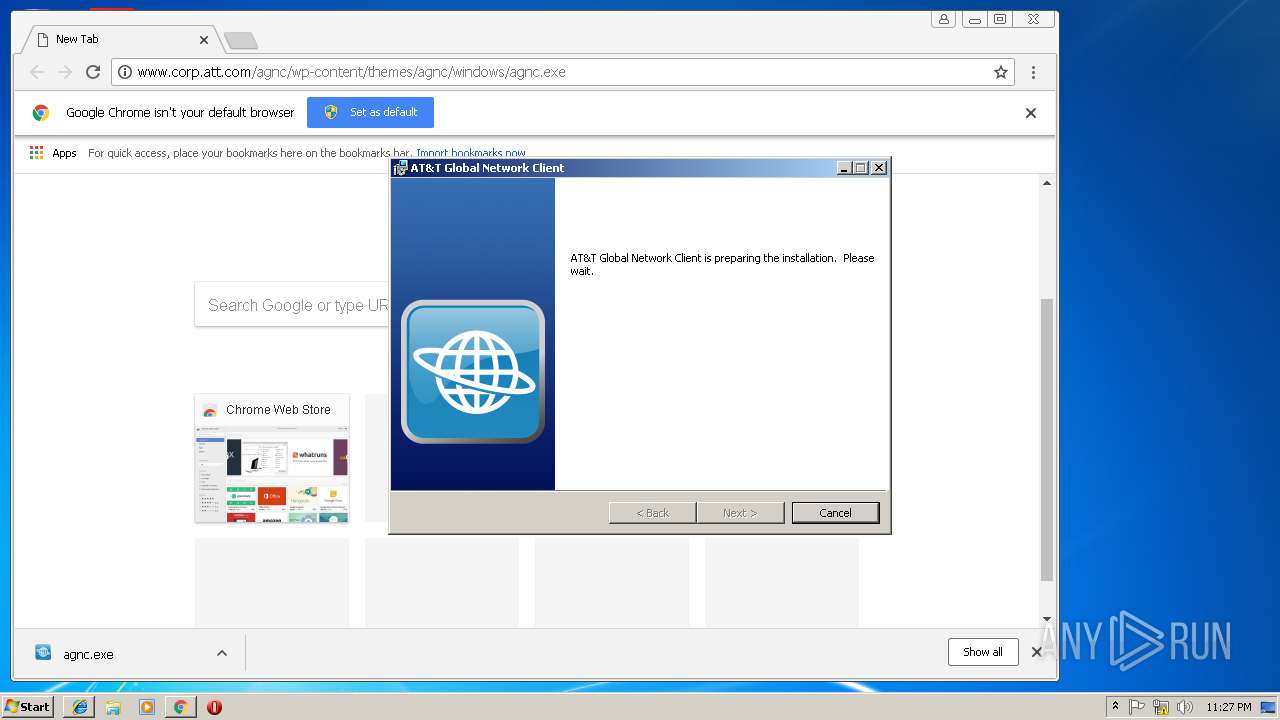
| 296 | "C:\Users\admin\Downloads\agnc.exe" | C:\Users\admin\Downloads\agnc.exe | chrome.exe | ||||||||||||
User: admin Company: AT&T Integrity Level: HIGH Description: Installer for the AT&T Global Network Client Exit code: 0 Version: 9.9.1.222 Modules
| |||||||||||||||
| 312 | "C:\Windows\system32\MSIEXEC.EXE" /i "C:\Users\admin\AppData\Local\Downloaded Installations\{971A2C4B-EE73-4B92-B681-42D253556B13}\agnc.msi" /l*v C:\Users\admin\AppData\Local\Temp\agnc_install.log TRANSFORMS="C:\Users\admin\AppData\Local\Downloaded Installations\{971A2C4B-EE73-4B92-B681-42D253556B13}\1033.MST" SETUPEXEDIR="C:\Users\admin\Downloads" SETUPEXENAME="agnc.exe" | C:\Windows\system32\MSIEXEC.EXE | agnc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 792 | C:\Windows\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {995C996E-D918-4a8c-A302-45719A6F4EA7} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1244 | "C:\Program Files\AT&T Global Network Client\WMB\COMWMBServer.exe" -Embedding | C:\Program Files\AT&T Global Network Client\WMB\COMWMBServer.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: AT&T Integrity Level: SYSTEM Description: Windows Mobile Broadband COM Server Exit code: 0 Version: 9.9.1.222 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\AT&T Global Network Client\OptionSDK\COMOptionSDKServer.exe" -Embedding | C:\Program Files\AT&T Global Network Client\OptionSDK\COMOptionSDKServer.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: AT&T Integrity Level: SYSTEM Description: Option COM Server Exit code: 0 Version: 9.9.1.222 Modules
| |||||||||||||||
| 2036 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{60a3cb41-1f6e-056f-a5d2-4033135de324}\avpnnic.inf" "0" "67e6067df" "000005C0" "WinSta0\Default" "00000538" "208" "C:\Program Files\AT&T Global Network Client\avpnnic" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Sierra Wireless Inc\Common\SwiCardDetect.exe" | C:\Program Files\Sierra Wireless Inc\Common\SwiCardDetect.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Sierra Wireless, Inc. Integrity Level: SYSTEM Description: Sierra Wireless Inc Card Detect Service Exit code: 0 Version: 11.3.1302.0 Modules
| |||||||||||||||
| 2216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=852,12880393318024985150,387484032312687251,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=2396435E0D7CBC7B54F6B00580119E8B --mojo-platform-channel-handle=3896 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=852,12880393318024985150,387484032312687251,131072 --enable-features=PasswordImport --service-pipe-token=6E65F2F0D56CF7B65F073A119A824B28 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6E65F2F0D56CF7B65F073A119A824B28 --renderer-client-id=3 --mojo-platform-channel-handle=2052 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
5 912
Read events
3 314
Write events
2 529
Delete events
69
Modification events
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {5A4B307D-46B0-11E9-AA93-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2960) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307030004000E00170018002F001400 | |||
Executable files
202
Suspicious files
193
Text files
713
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2960 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\a42fabe8-ff26-4e1b-bd1b-53489cfe717a.tmp | — | |
MD5:— | SHA256:— | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF21535f.TMP | text | |
MD5:— | SHA256:— | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF21536e.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
31
DNS requests
18
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3228 | chrome.exe | GET | 301 | 23.8.7.35:80 | http://www.corp.att.com/agnc/wp-content/themes/agnc/windows/agnc.exe | NL | — | — | malicious |
3244 | iexplore.exe | GET | 301 | 23.8.7.35:80 | http://www.corp.att.com/agnc/wp-content/themes/agnc/windows/agnc.exe | NL | — | — | malicious |
3228 | chrome.exe | GET | 301 | 23.8.7.35:80 | http://www.corp.att.com/agnc/wp-content/themes/agnc/windows/agnc.exe | NL | — | — | malicious |
2476 | NetClient.exe | POST | 200 | 204.146.172.230:80 | http://204.146.172.230/iProbe1?&s=default | US | binary | 44 b | unknown |
2476 | NetClient.exe | POST | 200 | 204.146.172.230:80 | http://204.146.172.230/iProbe1?&s=default | US | binary | 44 b | unknown |
2960 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3244 | iexplore.exe | 23.8.7.35:80 | www.corp.att.com | Akamai International B.V. | NL | whitelisted |
3228 | chrome.exe | 172.217.23.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2960 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3244 | iexplore.exe | 23.8.7.35:443 | www.corp.att.com | Akamai International B.V. | NL | whitelisted |
3228 | chrome.exe | 216.58.208.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3228 | chrome.exe | 216.58.207.67:443 | www.google.de | Google Inc. | US | whitelisted |
3228 | chrome.exe | 172.217.17.106:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3228 | chrome.exe | 172.217.21.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
3228 | chrome.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
3228 | chrome.exe | 23.8.7.35:443 | www.corp.att.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.corp.att.com |
| malicious |
www.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3244 | iexplore.exe | A Network Trojan was detected | ET TROJAN EXE Download Request To Wordpress Folder Likely Malicious |
3228 | chrome.exe | A Network Trojan was detected | ET TROJAN EXE Download Request To Wordpress Folder Likely Malicious |
3228 | chrome.exe | A Network Trojan was detected | ET TROJAN EXE Download Request To Wordpress Folder Likely Malicious |
3228 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
3228 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
Process | Message |
|---|---|
NetLogSvc.exe | Scheduler +I 03/14 23:28:16.024 0664: Did not find command to execute in registry
|
NetLogSvc.exe | AconFocusSvc+I 03/14 23:28:16.305 0F30: --------- Started NetAutoconnectFocusSvc ---------
|
NetLogSvc.exe | Firewall +I 03/14 23:28:16.805 04D8: Enter CFirewallSvc::FirewallSvcStartup
|
NetLogSvc.exe | Firewall +I 03/14 23:28:16.820 04D8: Enter CFirewallSvc::StartLogTrace
|
NetLogSvc.exe | Filter +I 03/14 23:28:16.820 04D8: Enter CNetFwDiag::startNetFwTrace
|
NetLogSvc.exe | Filter +I 03/14 23:28:16.820 04D8: Firewall network events logging thread started
|
NetLogSvc.exe | Filter +I 03/14 23:28:16.820 0FCC: Enter CNetFwDiag::ShowRecentNetEvents
|
NetLogSvc.exe | Firewall +E 03/14 23:28:16.820 04D8: IsTrustedDomainKeyPresent - RegQueryValueEx returned 2
|
NetLogSvc.exe | Firewall +I 03/14 23:28:16.820 04D8: Did not find TrustedDomains in registry; NOT registering interface change callback
|
NetLogSvc.exe | AconFocusSvc+I 03/14 23:28:16.883 0F30: RunMessageLoop called
|