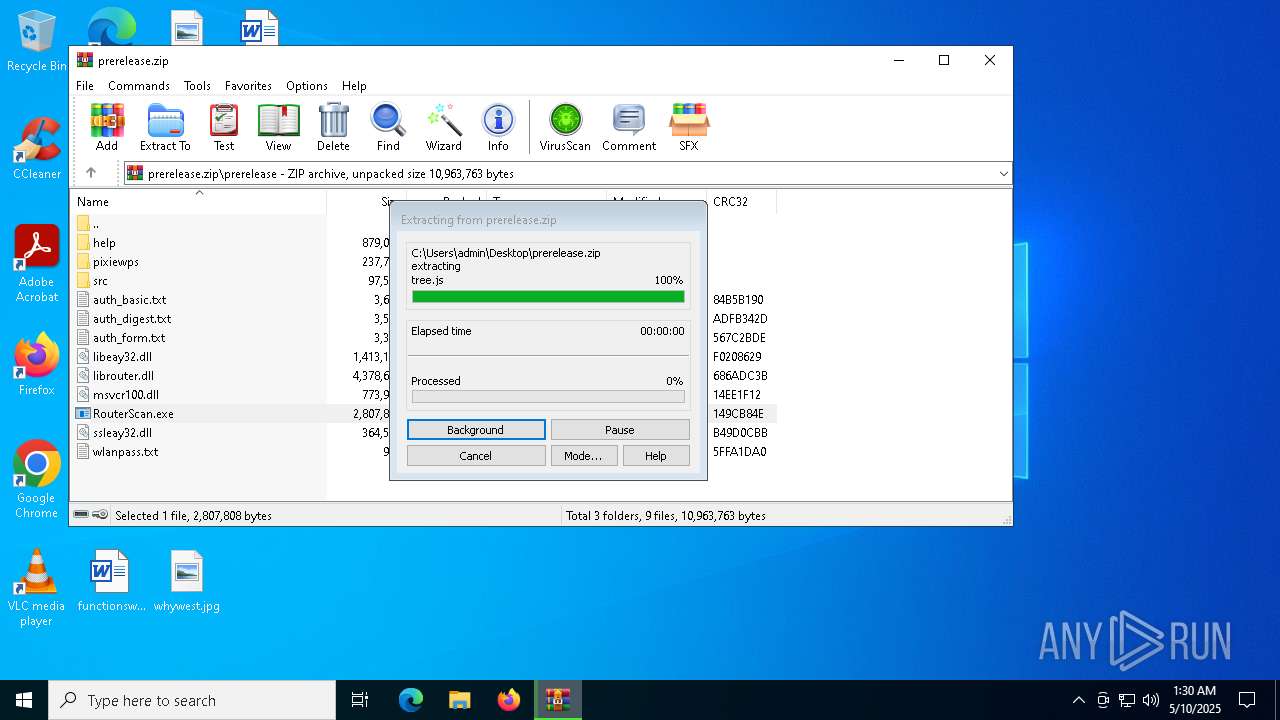
| File name: | prerelease.zip |
| Full analysis: | https://app.any.run/tasks/44e32948-d6c3-45e7-ad5b-ccc6f9893367 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 01:30:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BCEC7C96C05A87DF1964DC764F823293 |
| SHA1: | 5B7818482963FFC9FACBA239C66ED0639DD65F5B |
| SHA256: | 06706EA75723188800ADE3201A1F2F712DC8D73279A5CAD3DBDDD1338F53AAE1 |
| SSDEEP: | 98304:lbtGFdepvE0HLs3FkuYLdhlCgW9XFX6FfUTHwYCsFqxupNN7JVrKODhF2afH3hh9:Fv8qJtY |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6808)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6808)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6808)
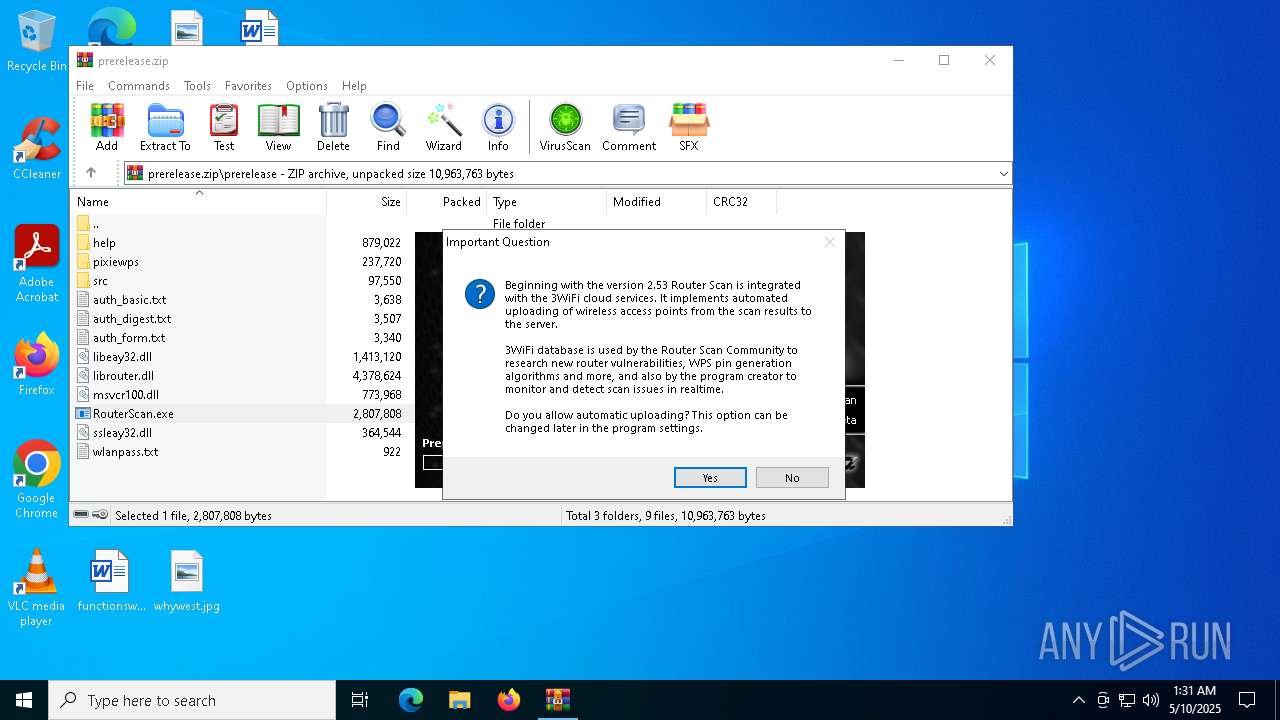
Potential Corporate Privacy Violation
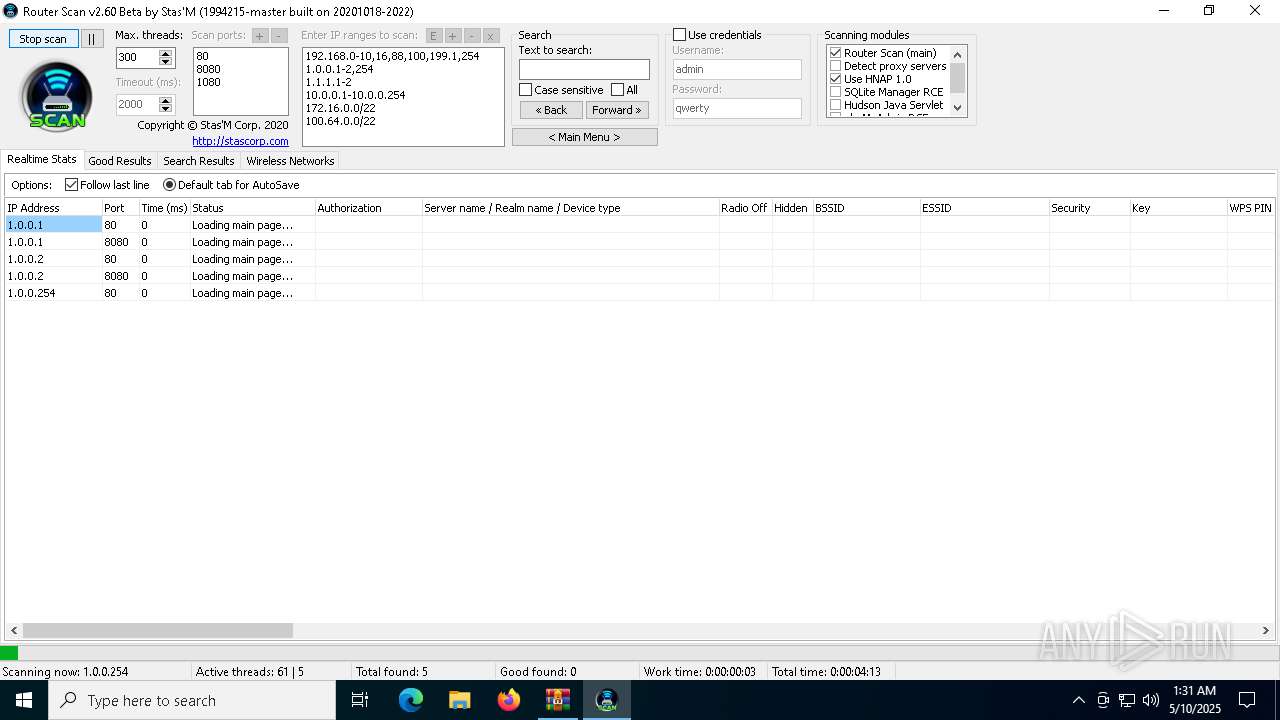
- RouterScan.exe (PID: 5124)
Connects to the server without a host name
- RouterScan.exe (PID: 5124)
Connects to unusual port
- RouterScan.exe (PID: 5124)
INFO
Checks supported languages
- RouterScan.exe (PID: 5124)
Reads the computer name
- RouterScan.exe (PID: 5124)
The sample compiled with english language support
- WinRAR.exe (PID: 6808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6808)
Create files in a temporary directory
- RouterScan.exe (PID: 5124)
Reads the machine GUID from the registry
- RouterScan.exe (PID: 5124)
Compiled with Borland Delphi (YARA)
- RouterScan.exe (PID: 5124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:02:03 21:39:42 |
| ZipCRC: | 0x84b5b190 |
| ZipCompressedSize: | 1506 |
| ZipUncompressedSize: | 3638 |
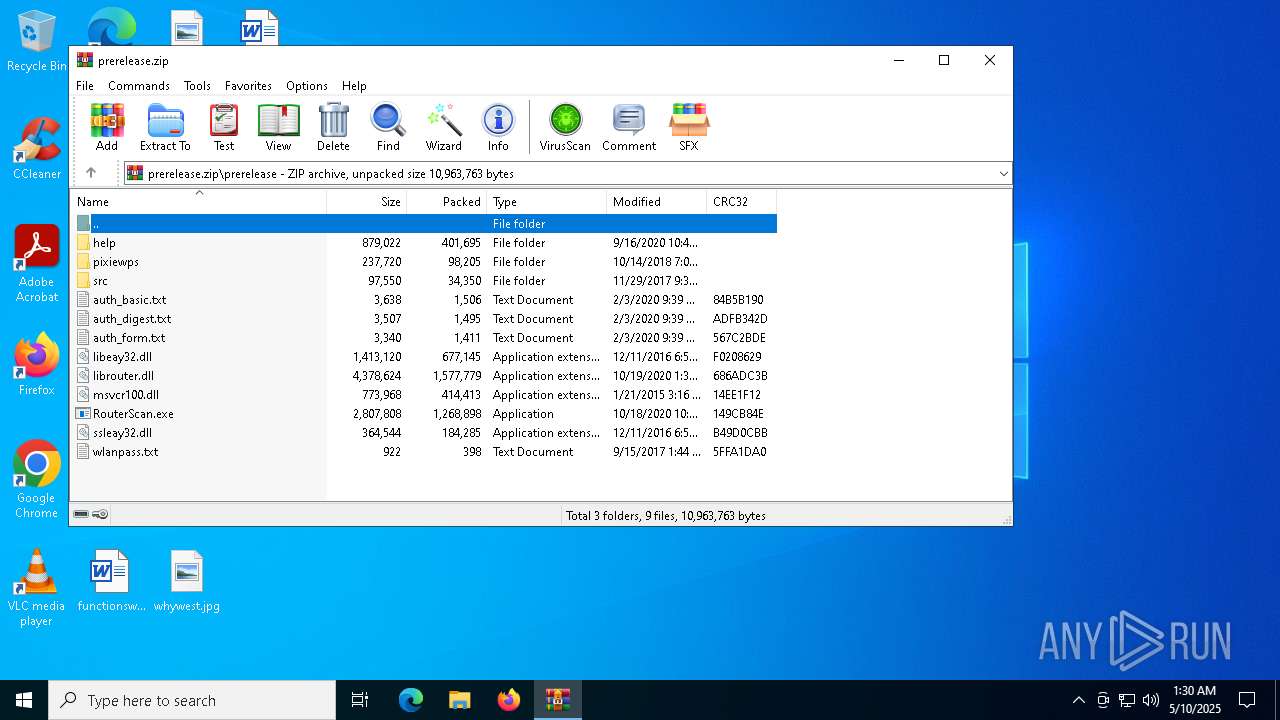
| ZipFileName: | prerelease/auth_basic.txt |
Total processes
130
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
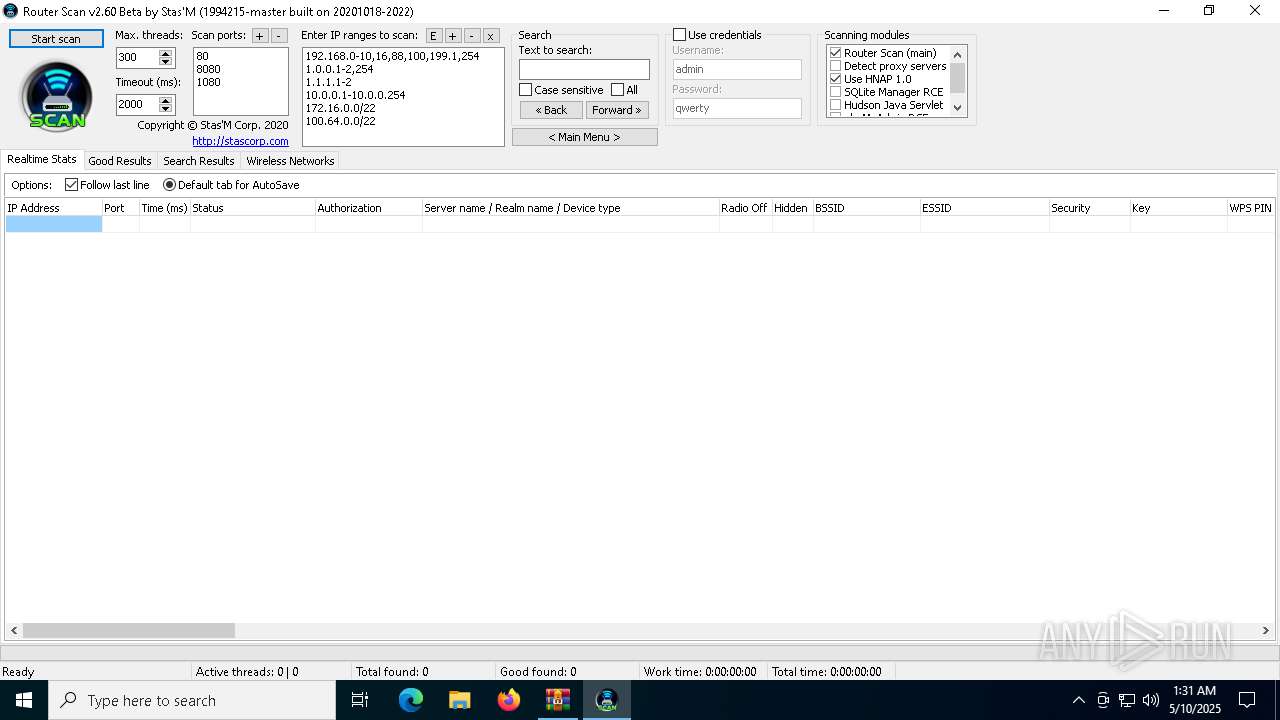
| 5124 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\RouterScan.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\RouterScan.exe | WinRAR.exe | ||||||||||||
User: admin Company: Stas'M Corp. Integrity Level: MEDIUM Description: Router Scan by Stas'M Version: 2.6.0.0 Modules
| |||||||||||||||
| 5408 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6808 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\prerelease.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 891
Read events
1 883
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\prerelease.zip | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
8
Suspicious files
0
Text files
105
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\auth_form.txt | text | |
MD5:51A1D6E6690D9E8DDF044D1CDFE104CB | SHA256:91AE5E6459A40C8084BE102693A8C09D5179A3E78B8A11860CCE6E69CA533623 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\auth_digest.txt | text | |
MD5:92E17CF1451BBADE83DC873533853260 | SHA256:86DB3629D98F47EA078EE41B54F2833BFBD5F632D0FCE3B342E099AAD368421D | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\help\data\code.css | text | |
MD5:EB21D6145A7B341CA198228B2C9930A8 | SHA256:FAB0FD6EEDFD3F618BC3C9522F259F51BF1FF09181A1D482FB965829F2387018 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\auth_basic.txt | text | |
MD5:A0B944354DE912EB81C0F660D963A669 | SHA256:1729FA47EDE6A8B5046FEF6C538431D4E8BB9020D9124E20C872E01495F91FB6 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\help\data\manual\window_settings_http.png | image | |
MD5:E004D89FA88E7E069C40934086BAB5F2 | SHA256:E23B06E03D796B81739DD9FA84A10844F41C4D9AFF0A1C980A5697A3127543CC | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\help\data\manual\window_settings_output.png | image | |
MD5:E75B191C653264D265F260D34F4AAB07 | SHA256:97517E959FC4592D3E489DD168C578A1394A7F95BA81D86B86CD0BE7EE87FEC2 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\help\data\manual\window_settings_tweaks.png | image | |
MD5:4FB7C2CF547C26B19B7A23625AF31BB5 | SHA256:98E78BEE484433721613CBD145A73C1FCB61D05B739E46A4F115AE76EA47BE28 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\help\data\manual\menu_table.png | image | |
MD5:8764457F339A125AC67BB57D98961D4A | SHA256:79CBBB622DC431B03D00089BF5D74B290F7A97F8DF3BE504A42CF7C81FC0DC94 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\help\data\manual\window_columns.png | image | |
MD5:8E40085DA25C761B7E6D6C8665BFE167 | SHA256:27EC3B2CF19A288129A4010D2381294271896049675E31E59A8790B508B6DA89 | |||
| 6808 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6808.46631\prerelease\help\data\code.js | text | |
MD5:0E184C0A27519CD3B4EA684FA5F7B12D | SHA256:0D2596B4DBF933CB26CAC77694E36E65A40B9938815A1561F11DCE5056D0DBBB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
768
DNS requests
13
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1324 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1324 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
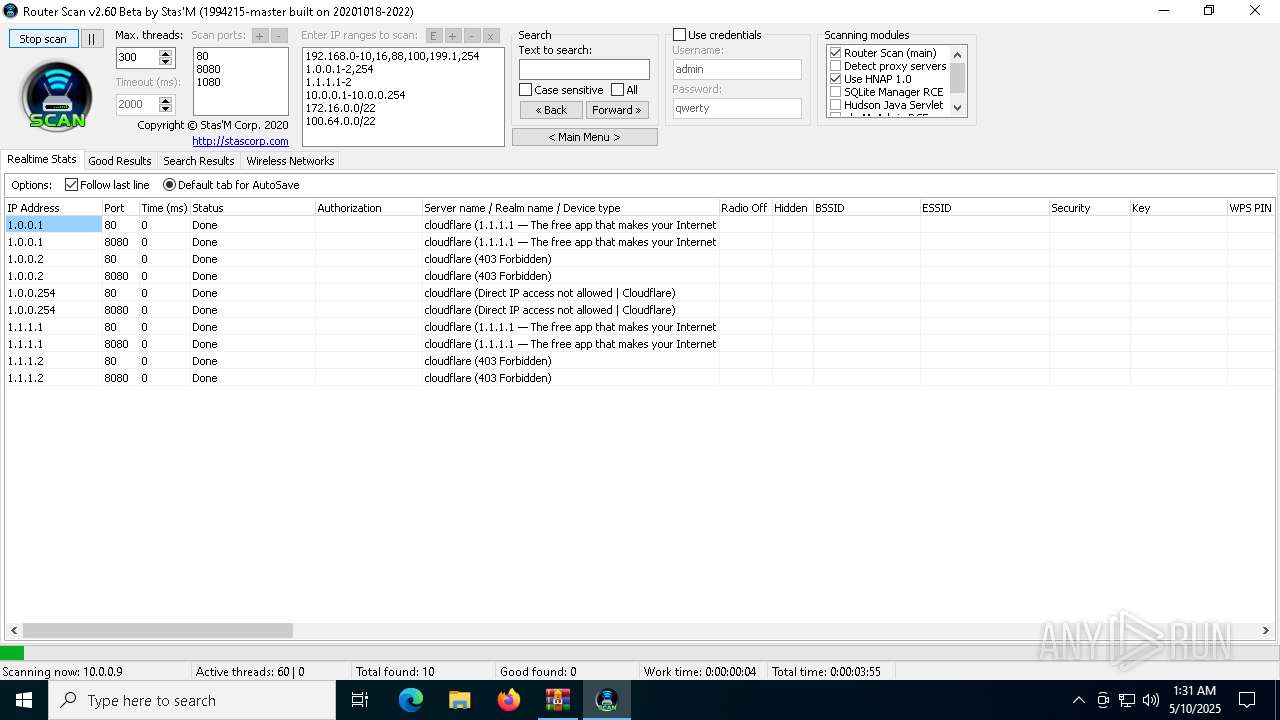
5124 | RouterScan.exe | GET | 301 | 1.0.0.1:80 | http://1.0.0.1/ | unknown | — | — | whitelisted |
5124 | RouterScan.exe | GET | 301 | 1.0.0.1:8080 | http://1.0.0.1:8080/ | unknown | — | — | whitelisted |
5124 | RouterScan.exe | GET | 301 | 1.0.0.2:80 | http://1.0.0.2/ | unknown | — | — | whitelisted |
5124 | RouterScan.exe | GET | 301 | 1.0.0.2:8080 | http://1.0.0.2:8080/ | unknown | — | — | whitelisted |
5124 | RouterScan.exe | GET | 403 | 1.0.0.254:80 | http://1.0.0.254/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5124 | RouterScan.exe | 134.0.119.34:443 | — | Domain names registrar REG.RU, Ltd | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5124 | RouterScan.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempting to network scan inside a home network |
5124 | RouterScan.exe | Misc activity | ET INFO Cloudflare DNS Over HTTPS Certificate Inbound |
5124 | RouterScan.exe | Misc activity | ET INFO Cloudflare DNS Over HTTPS Certificate Inbound |