| URL: | http://qttabbar.wikidot.com/ |
| Full analysis: | https://app.any.run/tasks/8abda25a-8c8a-4883-b598-6a55fef64416 |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2020, 00:48:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F4FA4C1AC26A06C48CC1EA329F41E264 |
| SHA1: | 76321066F1045BFFF1D9438229F71145502E2B7E |
| SHA256: | 064EED0605B44E0437680CC350743C60DF0480F4FF44BD4C64C33E4A80BAA8FA |
| SSDEEP: | 3:N1KP3EHeX8tGTK:C/E+X8tGTK |
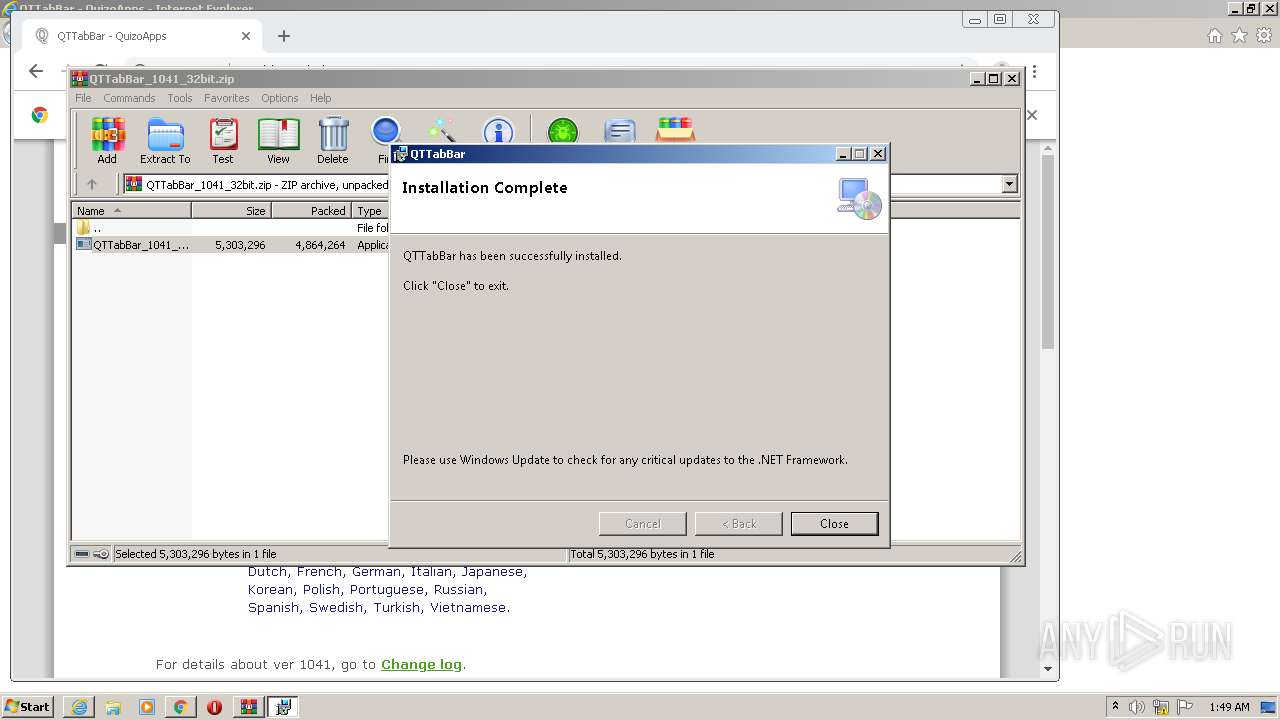
MALICIOUS
Application was dropped or rewritten from another process
- QTTabBar_1041_32bit.exe (PID: 1816)
- QTTabBar_1041_32bit.exe (PID: 1352)
Loads dropped or rewritten executable
- RegAsm.exe (PID: 3228)
- RegAsm.exe (PID: 2716)
- mscorsvw.exe (PID: 2288)
- mscorsvw.exe (PID: 3748)
- mscorsvw.exe (PID: 2144)
SUSPICIOUS
Starts Microsoft Installer
- QTTabBar_1041_32bit.exe (PID: 1352)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3528)
- msiexec.exe (PID: 3220)
- MSI4E01.tmp (PID: 3856)
- MSI892B.tmp (PID: 3524)
- mscorsvw.exe (PID: 3748)
- mscorsvw.exe (PID: 2288)
Creates files in the Windows directory
- msiexec.exe (PID: 3220)
- ngen.exe (PID: 308)
- ngen.exe (PID: 4068)
- mscorsvw.exe (PID: 3748)
- ngen.exe (PID: 952)
- ngen.exe (PID: 2948)
- mscorsvw.exe (PID: 2288)
Creates files in the user directory
- msiexec.exe (PID: 3220)
Creates COM task schedule object
- RegAsm.exe (PID: 3228)
- RegAsm.exe (PID: 2716)
Creates files in the program directory
- MSI4E01.tmp (PID: 3856)
Removes files from Windows directory
- mscorsvw.exe (PID: 2288)
- mscorsvw.exe (PID: 3748)
INFO
Application launched itself
- iexplore.exe (PID: 2976)
- chrome.exe (PID: 4008)
- msiexec.exe (PID: 3220)
Creates files in the user directory
- iexplore.exe (PID: 2928)
- iexplore.exe (PID: 2976)
Reads Internet Cache Settings
- iexplore.exe (PID: 2976)
- iexplore.exe (PID: 2928)
- chrome.exe (PID: 4008)
Changes internet zones settings
- iexplore.exe (PID: 2976)
Reads settings of System Certificates
- iexplore.exe (PID: 2976)
- iexplore.exe (PID: 2928)
- chrome.exe (PID: 2708)
Reads the hosts file
- chrome.exe (PID: 2708)
- chrome.exe (PID: 4008)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2976)
Reads internet explorer settings
- iexplore.exe (PID: 2928)
Manual execution by user
- chrome.exe (PID: 4008)
- explorer.exe (PID: 3132)
- explorer.exe (PID: 1864)
Changes settings of System certificates
- iexplore.exe (PID: 2976)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3636)
- MsiExec.exe (PID: 620)
- msiexec.exe (PID: 3220)
Searches for installed software
- msiexec.exe (PID: 3220)
Creates files in the program directory
- msiexec.exe (PID: 3220)
Application was dropped or rewritten from another process
- MSI4E01.tmp (PID: 3856)
- MSI892B.tmp (PID: 3524)
Creates a software uninstall entry
- msiexec.exe (PID: 3220)
Starts application with an unusual extension
- msiexec.exe (PID: 3220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
91
Monitored processes
42
Malicious processes
5
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe" "QTPluginLib, Version=1.0.0.0, Culture=neutral, PublicKeyToken=78a0cde69b47ca25" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | MSI4E01.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Common Language Runtime native compiler Exit code: 4294967295 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,2839903882629469616,13368469734850972820,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2111798716984684798 --mojo-platform-channel-handle=500 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 560 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\QTTabBar_zi1v12ub.p0l\QTTabBar Setup.msi" REINSTALL=ALL REINSTALLMODE=vamus | C:\Windows\System32\msiexec.exe | — | QTTabBar_1041_32bit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 620 | C:\Windows\system32\MsiExec.exe -Embedding 00A1C976AA17A081240E893922D017CF C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe" "QTPluginLib, Version=1.0.0.0, Culture=neutral, PublicKeyToken=78a0cde69b47ca25" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | MSI892B.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Common Language Runtime native compiler Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 968 | C:\Windows\system32\MsiExec.exe -Embedding 0DDC2DB2DBA48C1CA7E95922E461B78E | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,2839903882629469616,13368469734850972820,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9241186648287728544 --mojo-platform-channel-handle=1060 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,2839903882629469616,13368469734850972820,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=11853842260099654059 --mojo-platform-channel-handle=3932 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,2839903882629469616,13368469734850972820,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7400961020807380951 --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2608 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1352 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3528.29610\QTTabBar_1041_32bit.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3528.29610\QTTabBar_1041_32bit.exe | WinRAR.exe | ||||||||||||
User: admin Company: Quizo Integrity Level: HIGH Description: QTTabBar Installer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
6 164
Read events
4 889
Write events
1 201
Delete events
74
Modification events
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1655931644 | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30835486 | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
25
Suspicious files
71
Text files
202
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab68C8.tmp | — | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar68C9.tmp | — | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\8MZJJKOA.htm | html | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9FF67FB3141440EED32363089565AE60_444DE43FED932ACF85BE689919570420 | binary | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\FlickrGalleryModule[1].css | text | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\WIKIDOT.combined[1].js | text | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\2HJ7OU8Y.txt | — | |
MD5:— | SHA256:— | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\AMNBEVCC.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
69
TCP/UDP connections
77
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2928 | iexplore.exe | GET | 200 | 107.20.139.170:80 | http://qttabbar.wikidot.com/ | US | html | 5.08 Kb | whitelisted |
2928 | iexplore.exe | GET | 200 | 143.204.208.53:80 | http://d3g0gp89917ko0.cloudfront.net/v--3e3a6f7dbcc9/common--modules/js/wiki/image/FlickrGalleryModule.js | US | text | 1.11 Kb | whitelisted |
2928 | iexplore.exe | GET | 302 | 107.20.139.170:80 | http://qttabbar.wikidot.com/qttabbar/html/9401009bfaf8e3a6a32a12c0a81518a62d9bc185-52362084674610471 | US | compressed | 5.08 Kb | whitelisted |
2928 | iexplore.exe | GET | 200 | 107.20.139.176:80 | http://qttabbar.wdfiles.com/local--theme/currentbasedlocalizenosidebar/style.css | US | text | 89 b | suspicious |
2928 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2928 | iexplore.exe | GET | 200 | 107.20.139.176:80 | http://qttabbar.wdfiles.com/local--files/nav:top/twitter-ss.png | US | image | 1.50 Kb | suspicious |
2928 | iexplore.exe | GET | 200 | 107.20.139.176:80 | http://qttabbar.wdfiles.com/local--files/repository/qttabbar_top.png | US | image | 64.9 Kb | suspicious |
2928 | iexplore.exe | GET | 200 | 143.204.208.53:80 | http://d3g0gp89917ko0.cloudfront.net/v--3e3a6f7dbcc9/common--theme/localize/css/style.css | US | text | 1.29 Kb | whitelisted |
2928 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAQSqG2Vcy5VgVdz4Q5GOwg%3D | US | der | 280 b | whitelisted |
2928 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2928 | iexplore.exe | 143.204.208.53:80 | d3g0gp89917ko0.cloudfront.net | — | US | suspicious |
2928 | iexplore.exe | 107.20.139.176:80 | qttabbar.wdfiles.com | Amazon.com, Inc. | US | unknown |
2928 | iexplore.exe | 107.20.139.170:80 | qttabbar.wikidot.com | Amazon.com, Inc. | US | suspicious |
2928 | iexplore.exe | 173.194.76.155:80 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
2928 | iexplore.exe | 104.18.225.52:443 | cdn.onesignal.com | Cloudflare Inc | US | malicious |
2928 | iexplore.exe | 91.228.74.226:80 | edge.quantserve.com | Quantcast Corporation | GB | suspicious |
2928 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2976 | iexplore.exe | 107.20.139.170:80 | qttabbar.wikidot.com | Amazon.com, Inc. | US | suspicious |
2976 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2708 | chrome.exe | 172.217.18.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
qttabbar.wikidot.com |
| whitelisted |
d3g0gp89917ko0.cloudfront.net |
| whitelisted |
qttabbar.wdfiles.com |
| suspicious |
cdn.onesignal.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
edge.quantserve.com |
| whitelisted |
rules.quantcount.com |
| whitelisted |
pixel.quantserve.com |
| whitelisted |
api.bing.com |
| whitelisted |