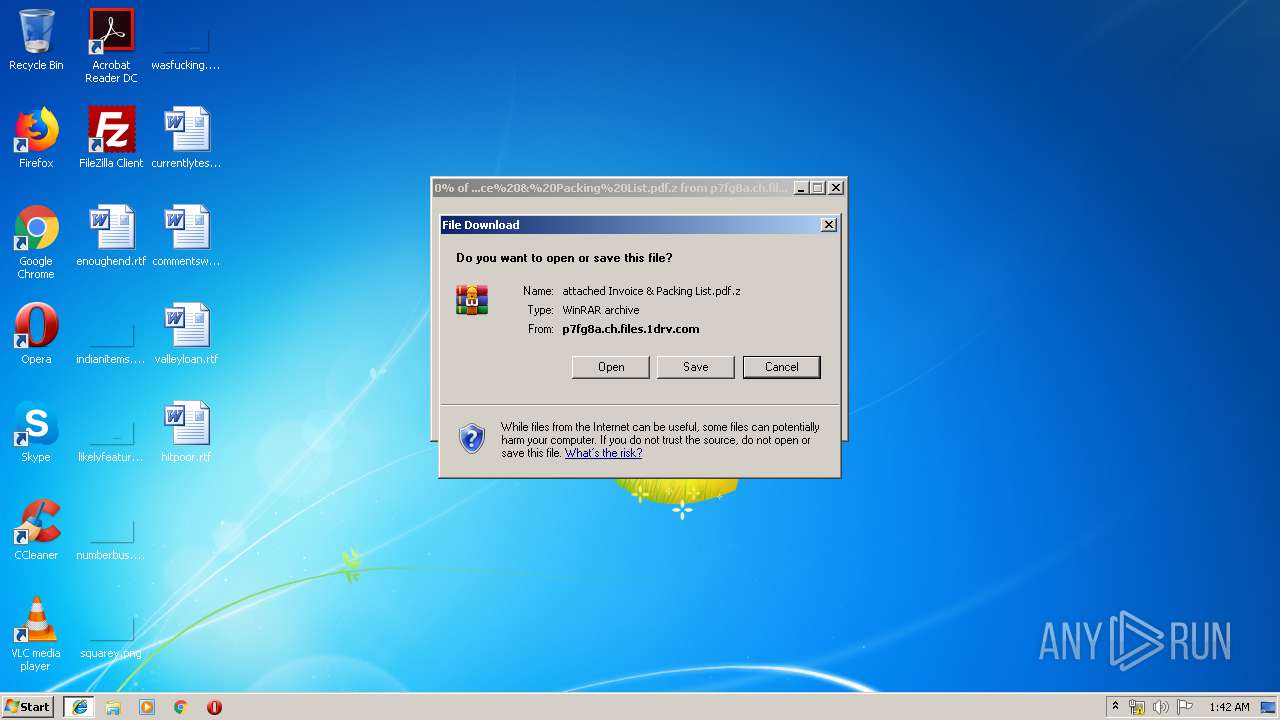
| URL: | https://p7fg8a.ch.files.1drv.com/y4md9A3nDOsrzJWeHDlS6FWFCsN87EbIclCkqny2qxEy5ACsGJadyDx_loNeajKxoDQ0y57NrcrWs2Bw6QeajcbMLyl4ymyZFwxdev2aafSspqXXFtsOO5q-VYBLq3V0M0ZjJ5Y0cKLcyV00M4B3c0AP_g8NfC9eP3MSDtOEXEfdu1sNoBxKgQkoc3xz8CfuXfx9wpTKzGmgmP1eceU0Ms6vQ/attached%20Invoice%20%26%20Packing%20List.pdf.z?download&psid=1 |
| Full analysis: | https://app.any.run/tasks/8f38e7ed-0023-458b-9e0d-4bc74796d7df |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2019, 00:42:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 2479DFF2970174F1CD6F4B0527957750 |
| SHA1: | 5549139AFCD66806F929989B868CF99F43F52821 |
| SHA256: | 06457B3A502AD58592784FE867C88DCC5563D8BF3C2677E960C4A7BA47FA6838 |
| SSDEEP: | 6:2WHy5ahq4fhTjoHDpc6dMT6hnXjnOwCPj287ZRqgCmOEztjVVok1WAzGPtrDuK4F:2KygJ5IVfOGXjOvfZMgC5Eztj/rWBDu7 |
MALICIOUS
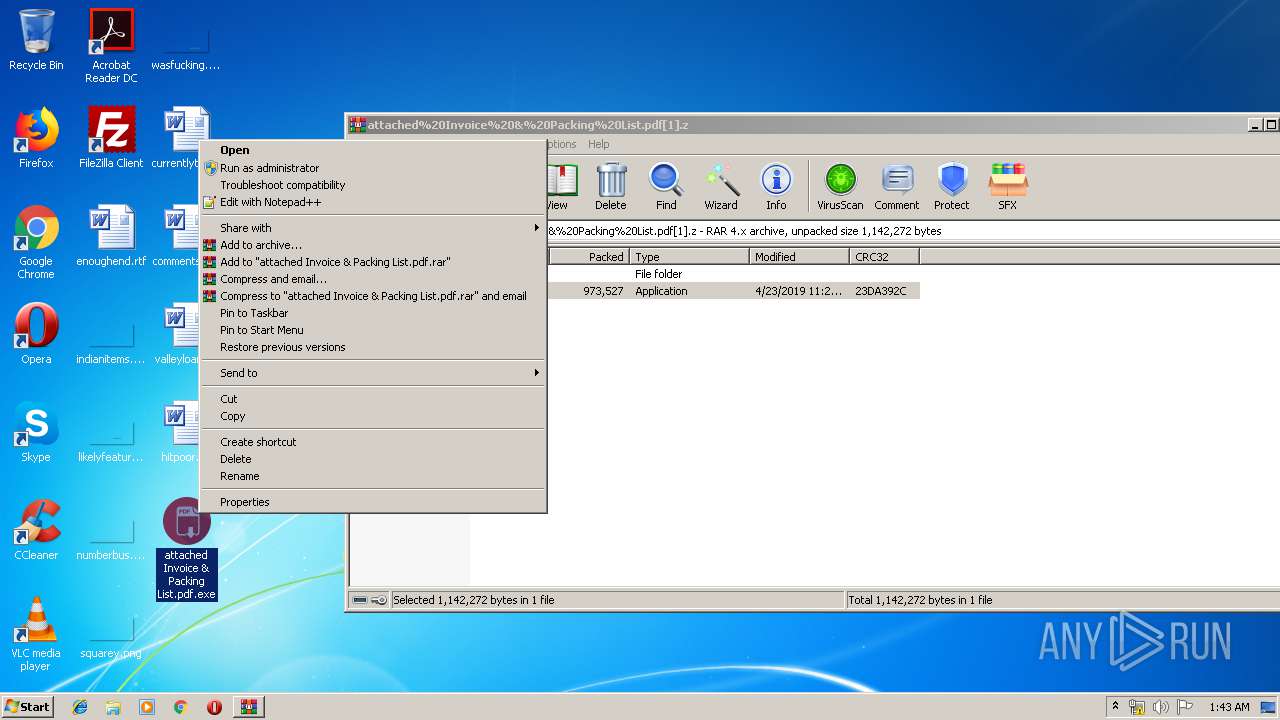
Application was dropped or rewritten from another process
- attached Invoice & Packing List.pdf.exe (PID: 2192)
- attached Invoice & Packing List.pdf.exe (PID: 760)
- attached Invoice & Packing List.pdf.exe (PID: 3936)
- attached Invoice & Packing List.pdf.exe (PID: 2180)
- attached Invoice & Packing List.pdf.exe (PID: 2148)
- attached Invoice & Packing List.pdf.exe (PID: 3200)
Writes to a start menu file
- attached Invoice & Packing List.pdf.exe (PID: 3936)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2300)
- attached Invoice & Packing List.pdf.exe (PID: 3936)
Creates files in the user directory
- attached Invoice & Packing List.pdf.exe (PID: 3936)
- notepad++.exe (PID: 3884)
Application launched itself
- attached Invoice & Packing List.pdf.exe (PID: 2192)
- attached Invoice & Packing List.pdf.exe (PID: 760)
INFO
Application launched itself
- iexplore.exe (PID: 2308)
Changes internet zones settings
- iexplore.exe (PID: 2308)
Reads Internet Cache Settings
- iexplore.exe (PID: 3616)
- iexplore.exe (PID: 2308)
Changes settings of System certificates
- iexplore.exe (PID: 2308)
Creates files in the user directory
- iexplore.exe (PID: 3616)
Reads settings of System Certificates
- iexplore.exe (PID: 2308)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
11
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 760 | "C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe" | C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe | — | explorer.exe | |||||||||||
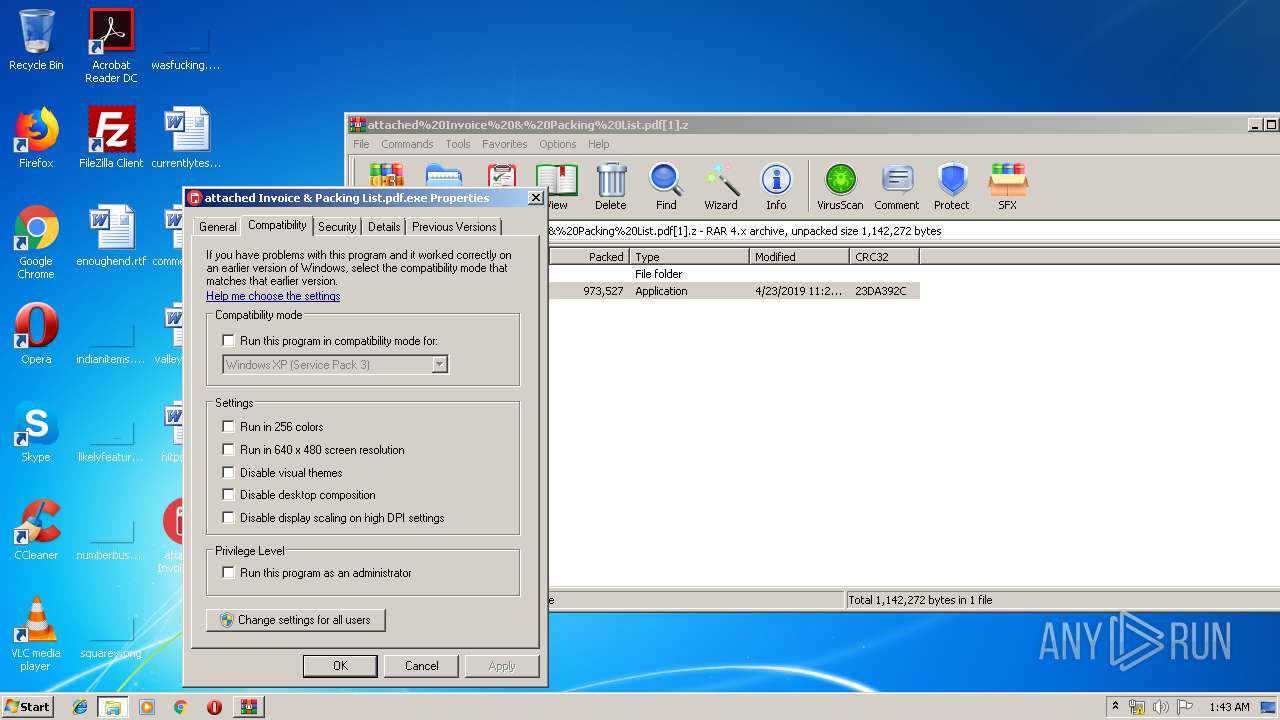
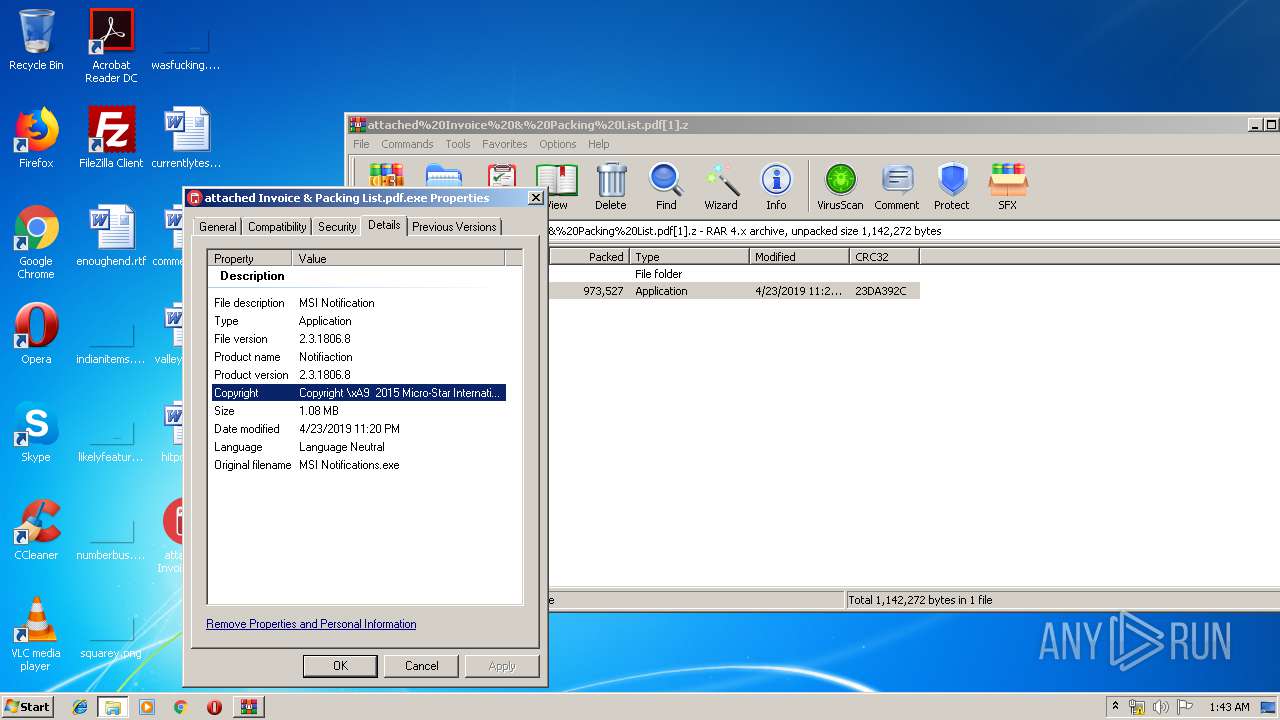
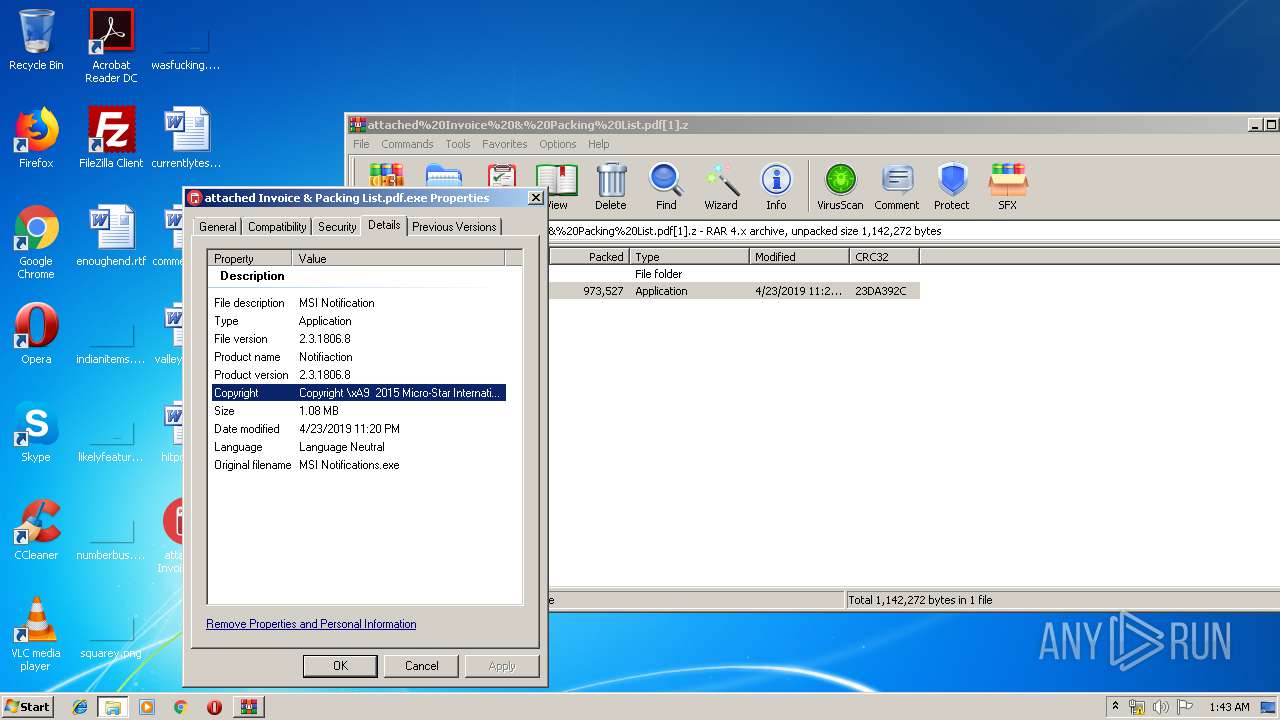
User: admin Company: Micro-Star International Co., Ltd. Integrity Level: MEDIUM Description: MSI Notification Exit code: 0 Version: 2.3.1806.8 Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe" | C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe | explorer.exe | ||||||||||||
User: admin Company: Micro-Star International Co., Ltd. Integrity Level: HIGH Description: MSI Notification Exit code: 0 Version: 2.3.1806.8 Modules
| |||||||||||||||
| 2180 | "C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe" | C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe | — | attached Invoice & Packing List.pdf.exe | |||||||||||
User: admin Company: Micro-Star International Co., Ltd. Integrity Level: MEDIUM Description: MSI Notification Exit code: 0 Version: 2.3.1806.8 Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2300.9036\attached Invoice & Packing List.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2300.9036\attached Invoice & Packing List.pdf.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Micro-Star International Co., Ltd. Integrity Level: MEDIUM Description: MSI Notification Exit code: 0 Version: 2.3.1806.8 Modules
| |||||||||||||||
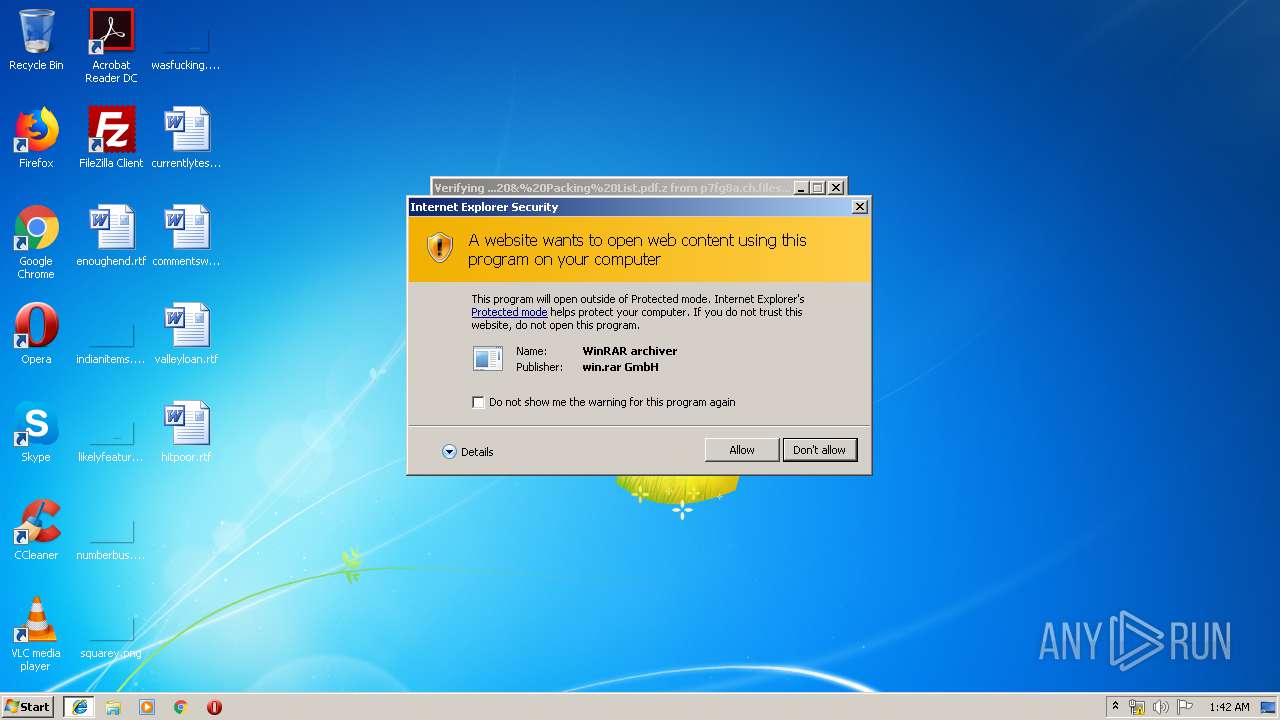
| 2300 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\B6AKU5BF\attached%20Invoice%20&%20Packing%20List.pdf[1].z" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3200 | "C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe" | C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe | — | explorer.exe | |||||||||||
User: admin Company: Micro-Star International Co., Ltd. Integrity Level: MEDIUM Description: MSI Notification Exit code: 0 Version: 2.3.1806.8 Modules
| |||||||||||||||
| 3236 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 3616 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2308 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3884 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\attached Invoice & Packing List.pdf.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
Total events
1 526
Read events
1 431
Write events
91
Delete events
4
Modification events
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {E24ABF37-6629-11E9-A09E-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (2308) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30704000300180000002A003200B500 | |||
Executable files
3
Suspicious files
2
Text files
16
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2308 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF2BD988B7B8773799.TMP | — | |
MD5:— | SHA256:— | |||
| 2308 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF28AE2FDCA8B17768.TMP | — | |
MD5:— | SHA256:— | |||
| 2308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{E24ABF37-6629-11E9-A09E-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\B6AKU5BF\attached%20Invoice%20&%20Packing%20List.pdf[1].z | compressed | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\97863QZ6\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019042420190425\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2300.9036\attached Invoice & Packing List.pdf.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2308 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
— | — | GET | 200 | 195.138.255.24:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | DE | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2308 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3616 | iexplore.exe | 13.107.42.12:443 | p7fg8a.ch.files.1drv.com | Microsoft Corporation | US | suspicious |
3236 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
— | — | 195.138.255.24:80 | isrg.trustid.ocsp.identrust.com | AS33891 Netzbetrieb GmbH | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
p7fg8a.ch.files.1drv.com |
| whitelisted |
notepad-plus-plus.org |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|