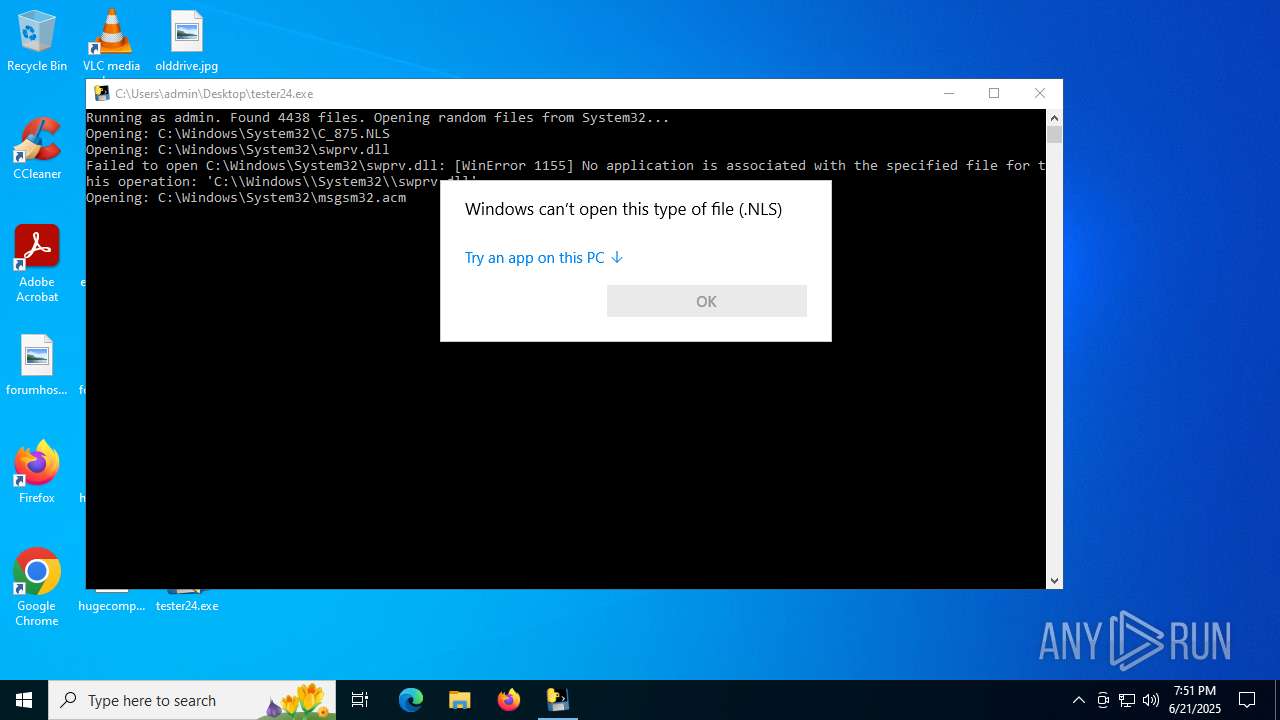
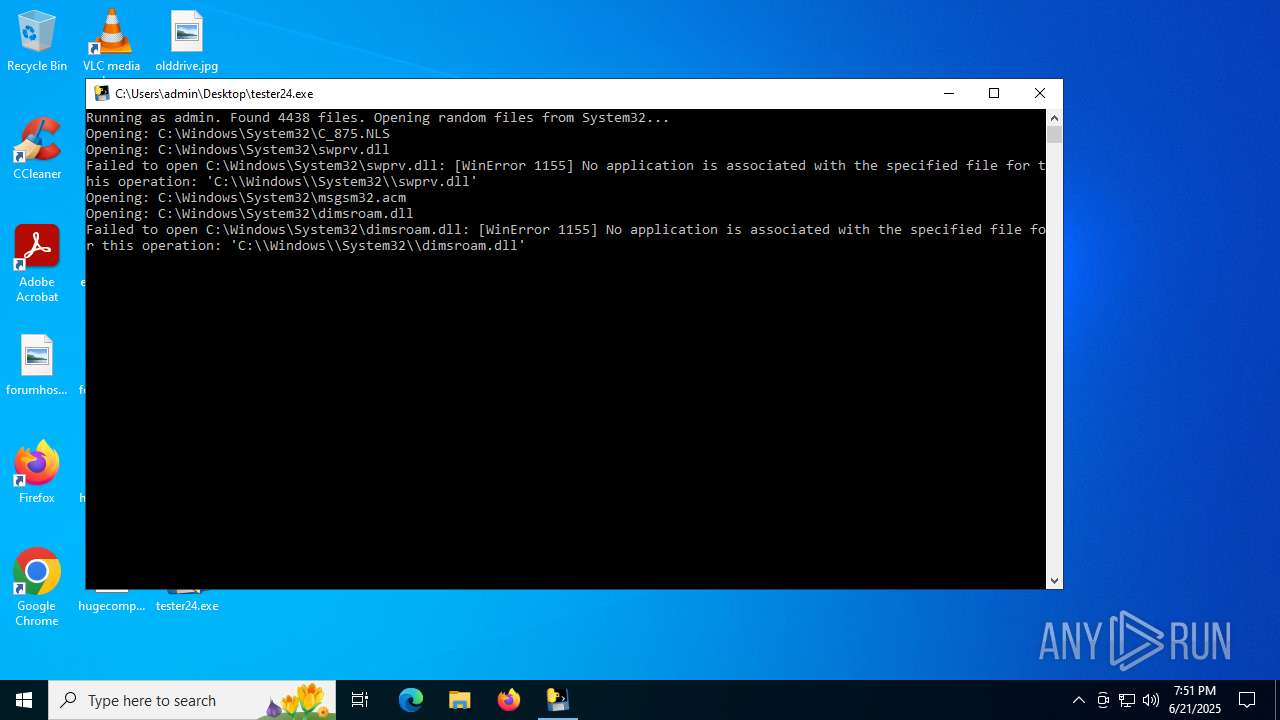
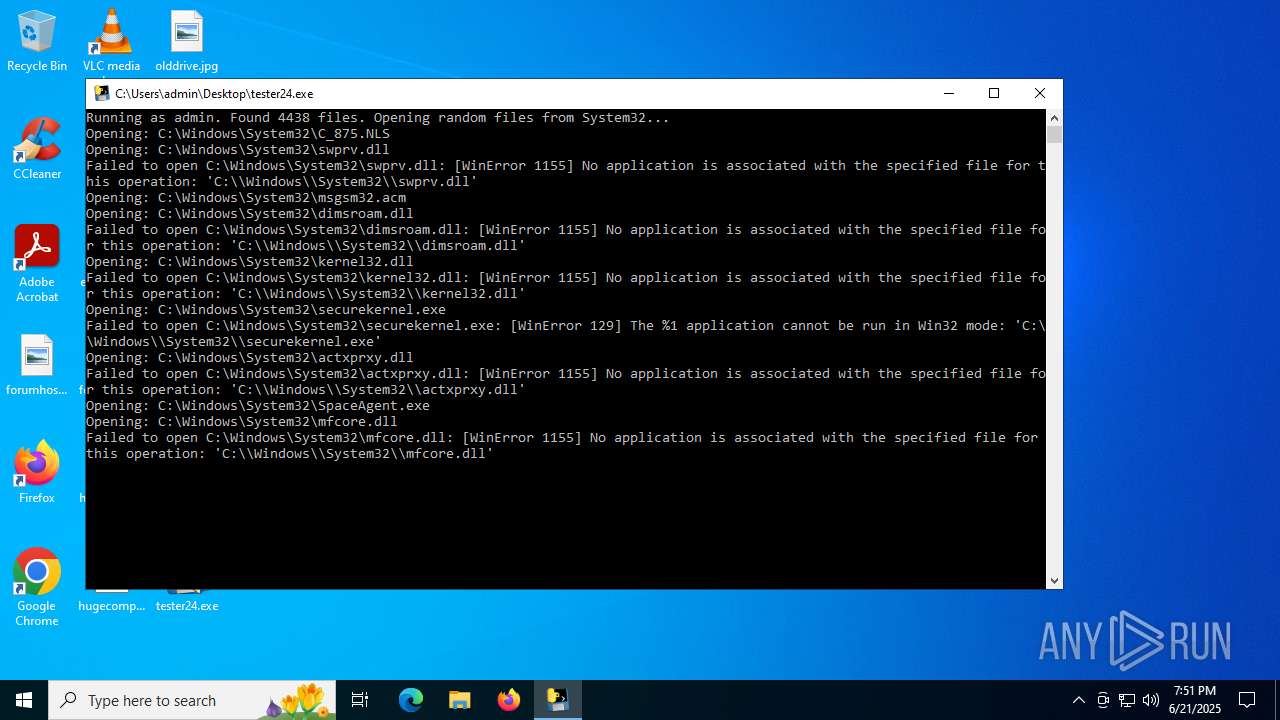
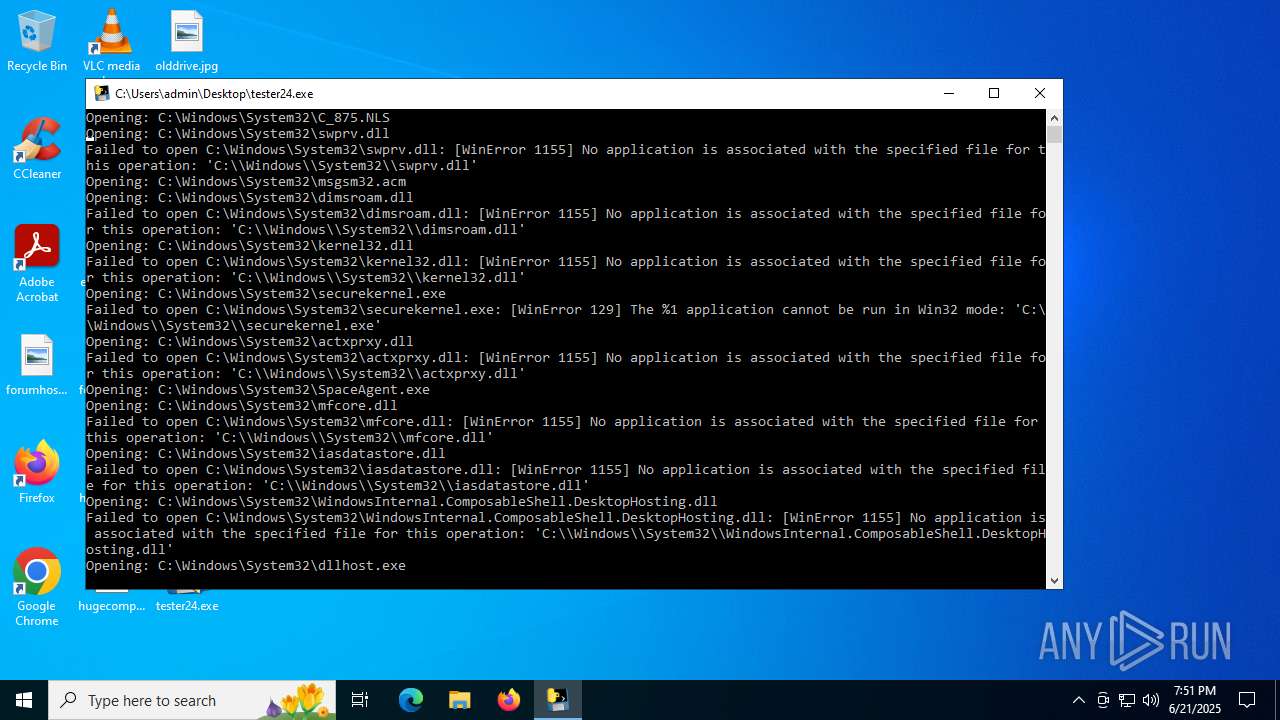
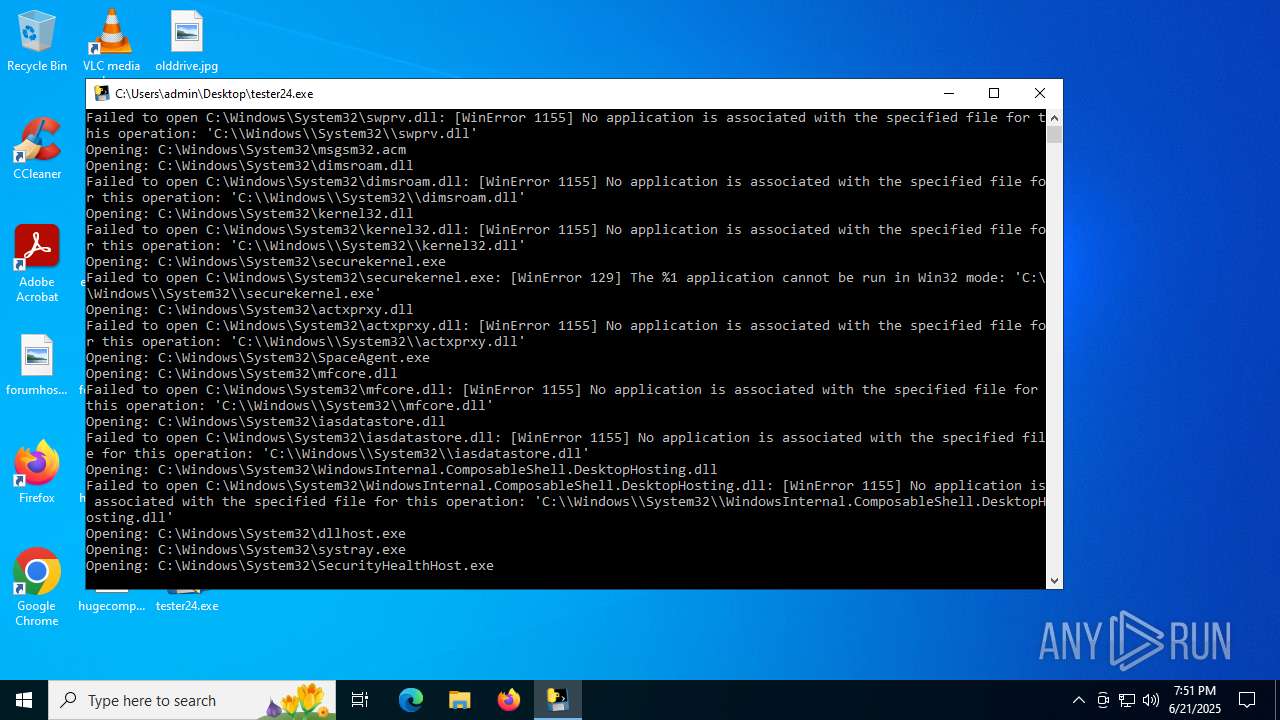
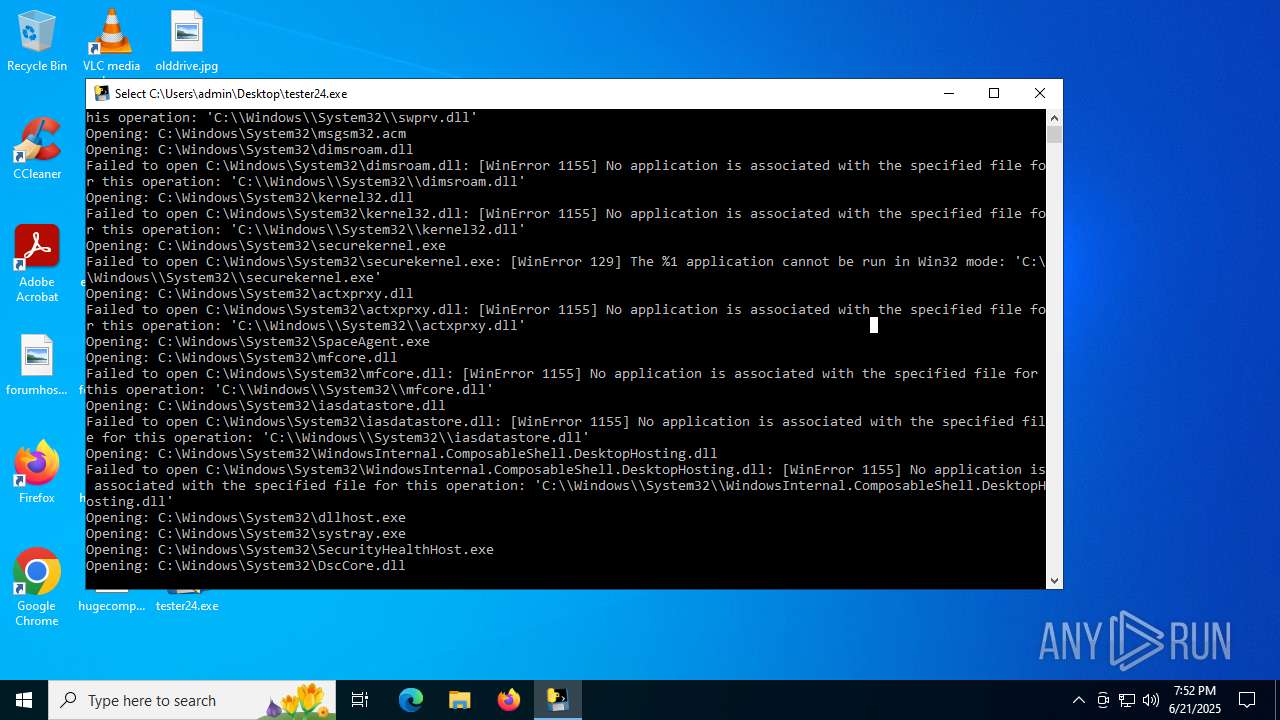
| File name: | tester24.exe |
| Full analysis: | https://app.any.run/tasks/897404d3-3848-4534-9978-a34f69ce6ef9 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 19:51:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 263DEEBFB107DBA1929A4FC98A83545B |
| SHA1: | 3359C38080E2A699A9A23C20FB6DC4835EF24617 |
| SHA256: | 06155B0426C0EDFEB8D2453C53CF10A8AC879399A69D32131DE73751FB8AA798 |
| SSDEEP: | 98304:LD/lyt8bKQdLKbLylu/ZUmTv4I9XLDbenkuA83wpYp2tw8Mne8YvBc1idV8/R9CQ:Fd0n881mwmNuEM491+jg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- tester24.exe (PID: 6772)
Executable content was dropped or overwritten
- tester24.exe (PID: 6772)
Process drops legitimate windows executable
- tester24.exe (PID: 6772)
The process drops C-runtime libraries
- tester24.exe (PID: 6772)
Application launched itself
- tester24.exe (PID: 6772)
Loads Python modules
- tester24.exe (PID: 3676)
Reads the date of Windows installation
- tester24.exe (PID: 3676)
Reads security settings of Internet Explorer
- tester24.exe (PID: 3676)
INFO
Checks supported languages
- tester24.exe (PID: 6772)
- tester24.exe (PID: 3676)
Create files in a temporary directory
- tester24.exe (PID: 6772)
Reads the computer name
- tester24.exe (PID: 6772)
- tester24.exe (PID: 3676)
The sample compiled with english language support
- tester24.exe (PID: 6772)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2192)
- OpenWith.exe (PID: 4320)
Process checks computer location settings
- tester24.exe (PID: 3676)
PyInstaller has been detected (YARA)
- tester24.exe (PID: 6772)
- tester24.exe (PID: 3676)
Checks proxy server information
- slui.exe (PID: 2764)
Reads the software policy settings
- slui.exe (PID: 2764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:21 19:50:15+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 179712 |
| InitializedDataSize: | 155136 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc650 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
146
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2128 | "C:\Windows\System32\securekernel.exe" | C:\Windows\System32\securekernel.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NT Secure Kernel Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2764 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | "C:\Windows\System32\SecurityHealthHost.exe" | C:\Windows\System32\SecurityHealthHost.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Security Health Host Exit code: 0 Version: 4.18.1907.16384 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3676 | "C:\Users\admin\Desktop\tester24.exe" | C:\Users\admin\Desktop\tester24.exe | — | tester24.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3864 | "C:\Users\admin\Desktop\tester24.exe" | C:\Users\admin\Desktop\tester24.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4320 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4684 | "C:\Windows\System32\SpaceAgent.exe" | C:\Windows\System32\SpaceAgent.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Storage Spaces Settings Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | "C:\Windows\System32\dllhost.exe" | C:\Windows\System32\dllhost.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6344 | "C:\Windows\System32\systray.exe" | C:\Windows\System32\systray.exe | — | tester24.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Systray .exe stub Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 135
Read events
5 135
Write events
0
Delete events
0
Modification events
Executable files
55
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\_decimal.pyd | executable | |
MD5:584652F877074FE71D7B1F8EEA1F849E | SHA256:E0F93185CD64F1DB3B9D1D20D620A691C5C453094B14D3B2BA2837F908F13304 | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\_hashlib.pyd | executable | |
MD5:692837EB1FCB73EF33A1474B18DFC7CD | SHA256:D674D53F7E2F906FBAF0D19AB871F9CFF53956D40B3CE003A2B4B44B549D4B92 | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\_ctypes.pyd | executable | |
MD5:429CB0177D5AB205F289D0CC830549FF | SHA256:6E804ED42CCA2EB401A896FE9542201D4D77DF22ACBD935A3C56DC68530DAE33 | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\api-ms-win-core-heap-l1-1-0.dll | executable | |
MD5:344A09B4BE069F86356A89482C156647 | SHA256:8F105771B236DBCB859DE271F0A6822CE1CB79C36988DD42C9E3F6F55C5F7EB9 | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:416AA8314222DB6CBB3760856BE13D46 | SHA256:39095F59C41D76EC81BB2723D646FDE4C148E7CC3402F4980D2ADE95CB9C84F9 | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:226A5983AE2CBBF0C1BDA85D65948ABC | SHA256:591358EB4D1531E9563EE0813E4301C552CE364C912CE684D16576EABF195DC3 | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\api-ms-win-core-kernel32-legacy-l1-1-1.dll | executable | |
MD5:0C1CC0A54D4B38885E1B250B40A34A84 | SHA256:A9B13A1CD1B8C19B0C6B4AFCD5BB0DD29C0E2288231AC9E6DB8510094CE68BA6 | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:CC228FF8D86B608E73026B1E9960B2F8 | SHA256:4CADBC0C39DA7C6722206FDCEBD670ABE5B8D261E7B041DD94F9397A89D1990D | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:9F45A47EBFD9D0629F4935764243DD5A | SHA256:1CA895ABA4E7435563A6B43E85EBA67A0F8C74AA6A6A94D0FC48FA35535E2585 | |||
| 6772 | tester24.exe | C:\Users\admin\AppData\Local\Temp\_MEI67722\_lzma.pyd | executable | |
MD5:0D549F688E0B2424B549AFCAC58D5FA7 | SHA256:80DF30ED0F2C532C07EA7FDC44836E40A8EBD9E7611365A1A26989147E1A4210 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
50
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4816 | RUXIMICS.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4816 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.66:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 40.126.32.133:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 504 | 40.126.32.134:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4816 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4816 | RUXIMICS.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |