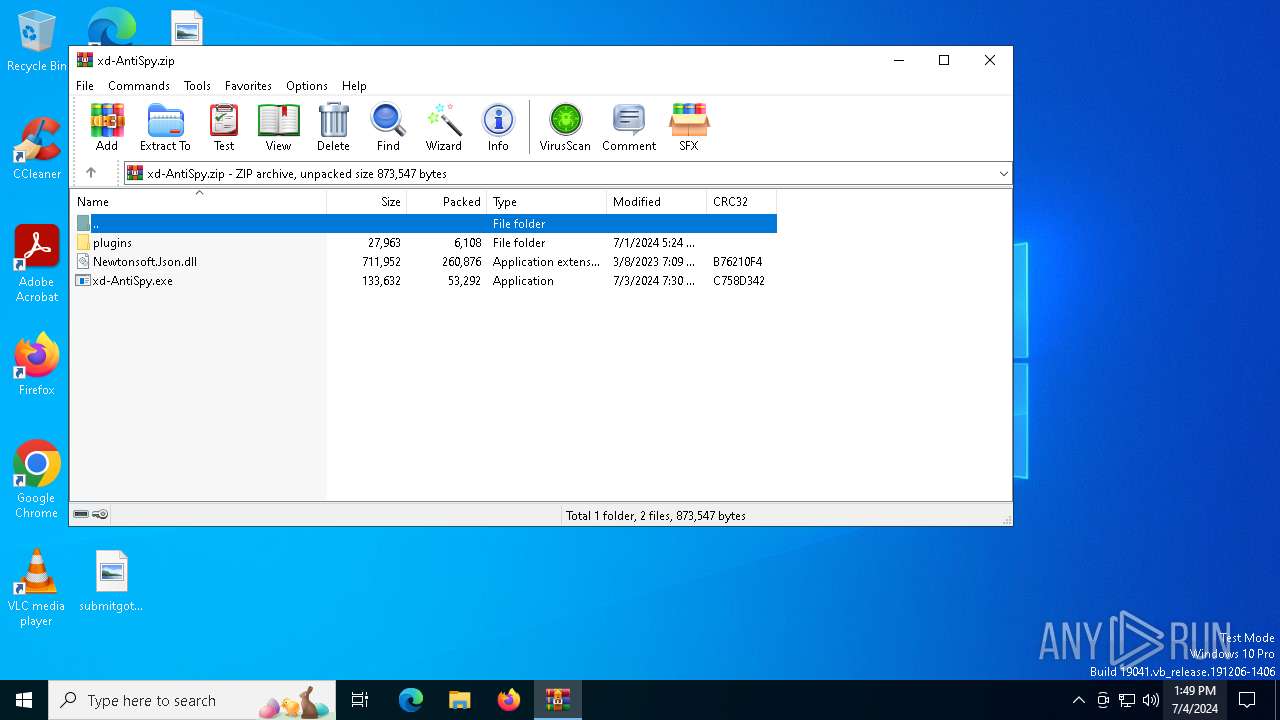
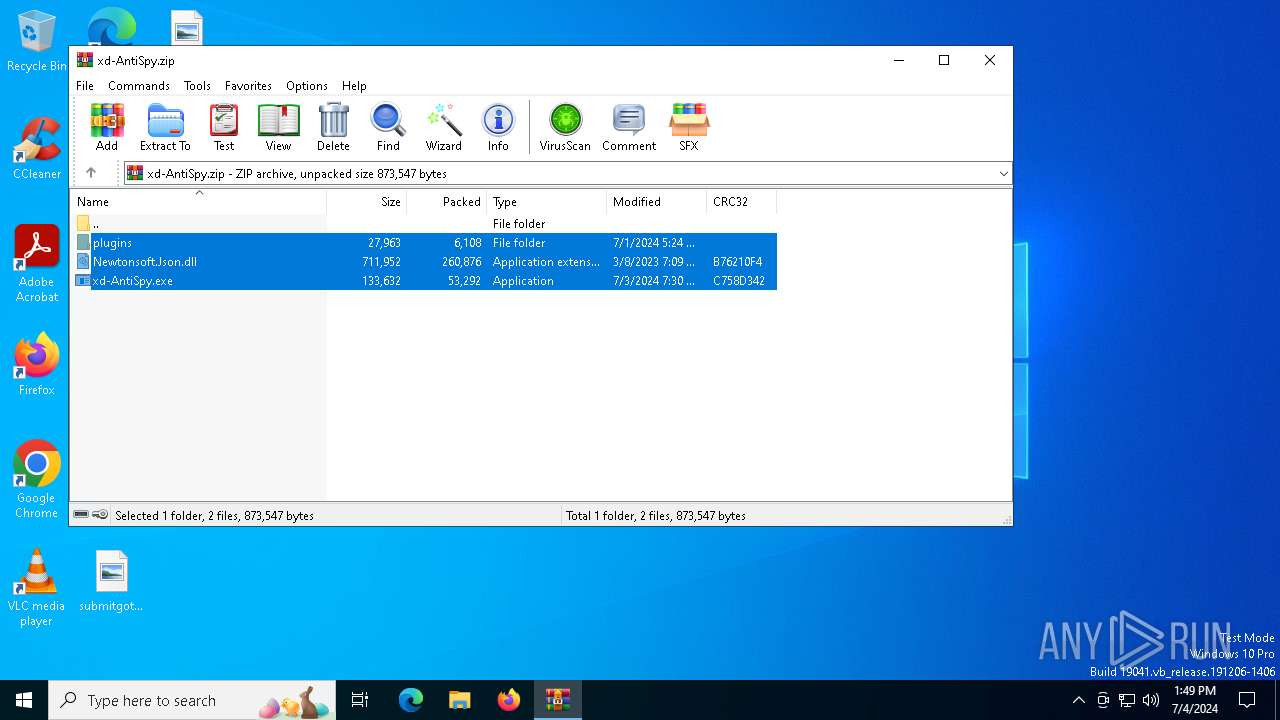
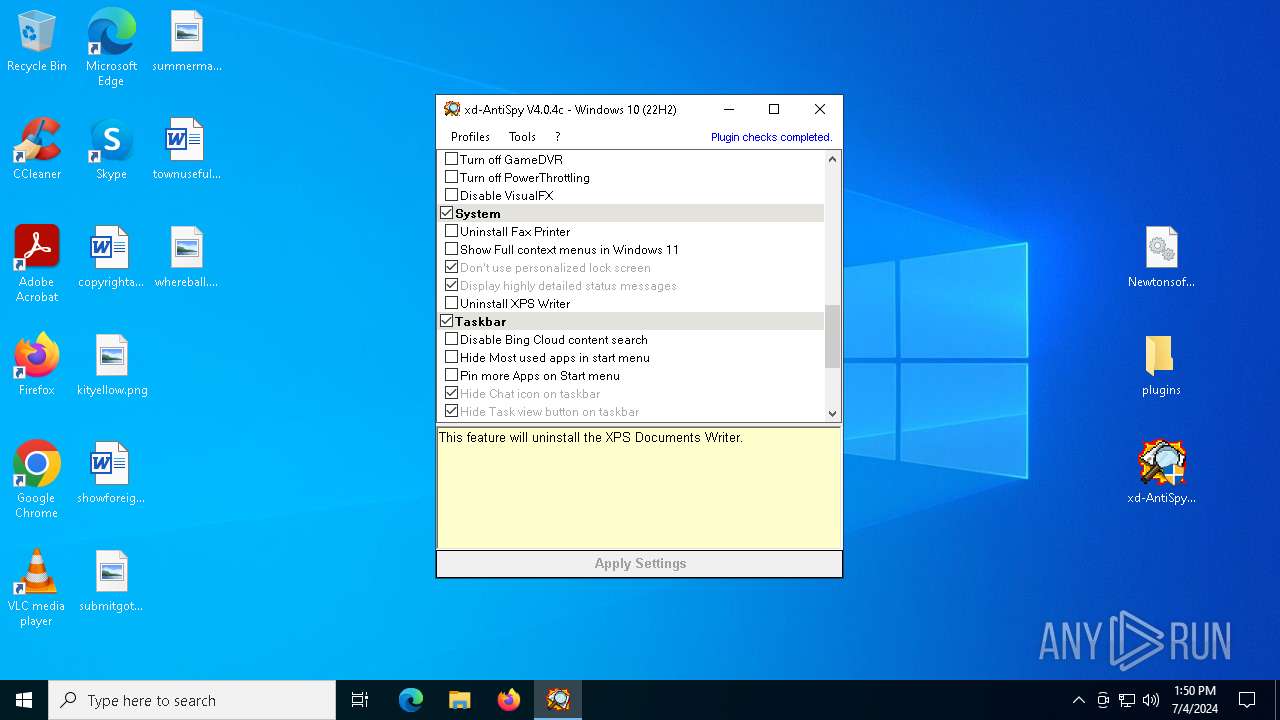
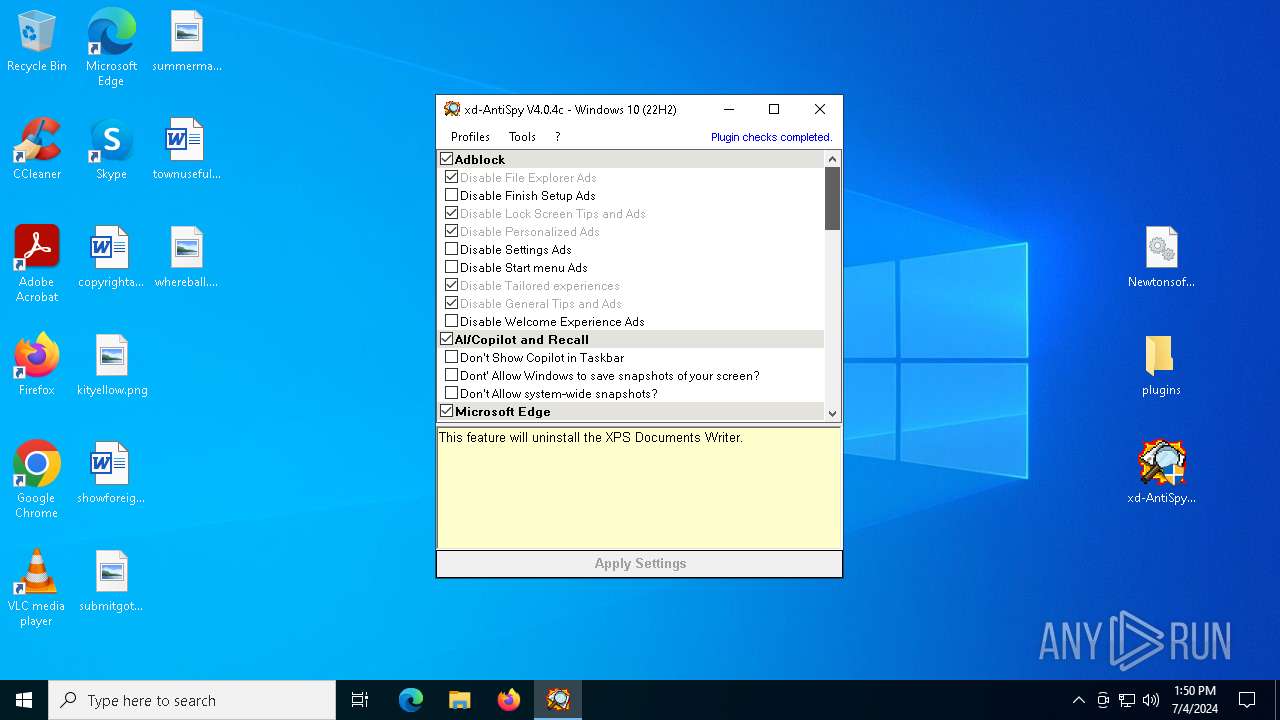
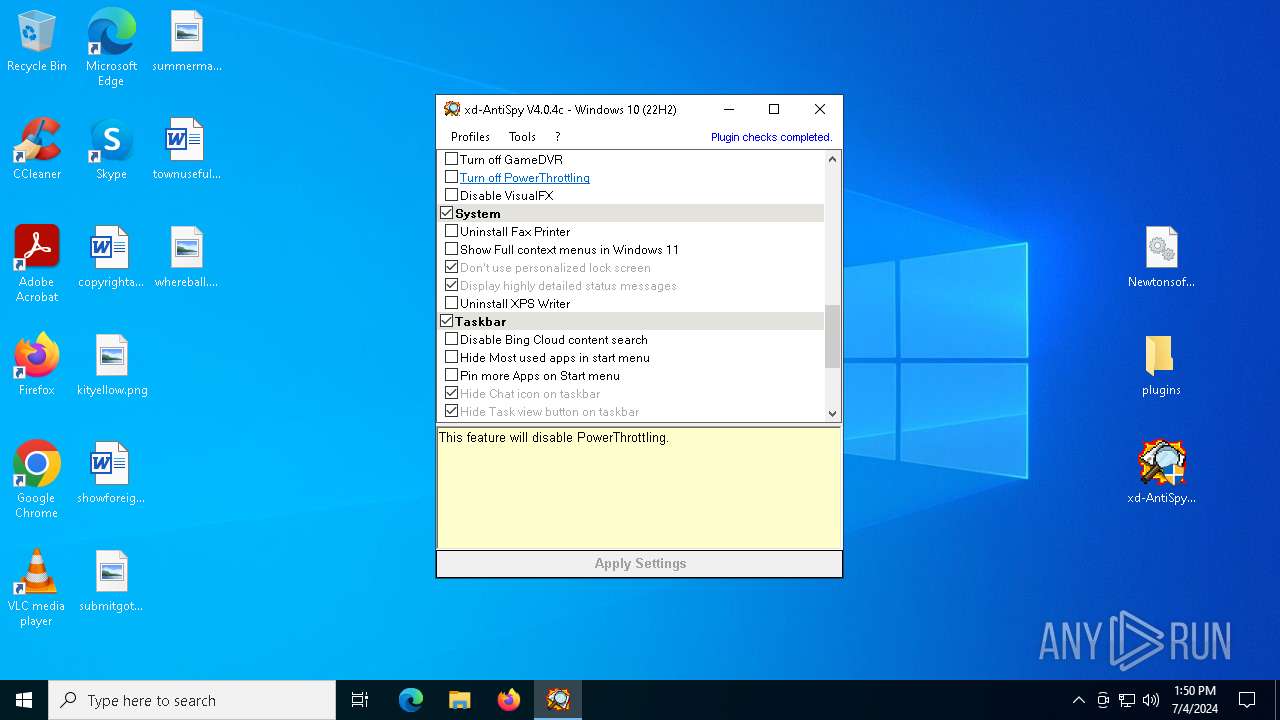
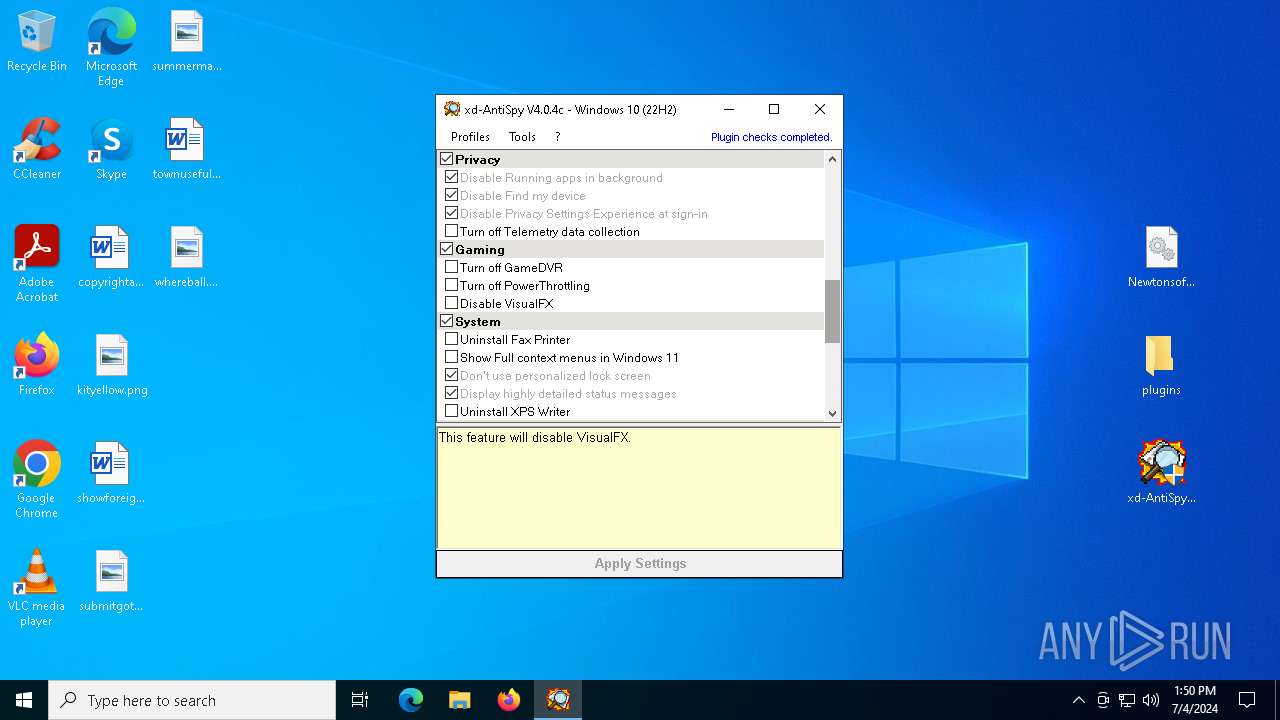
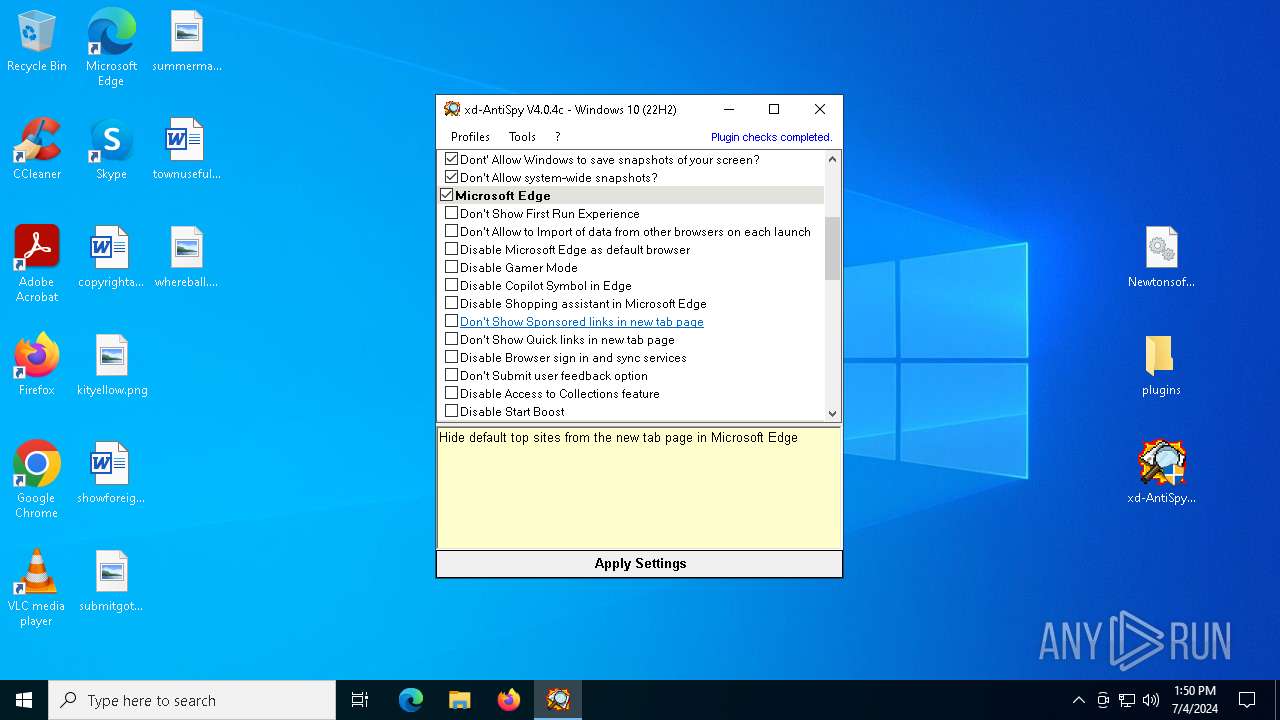
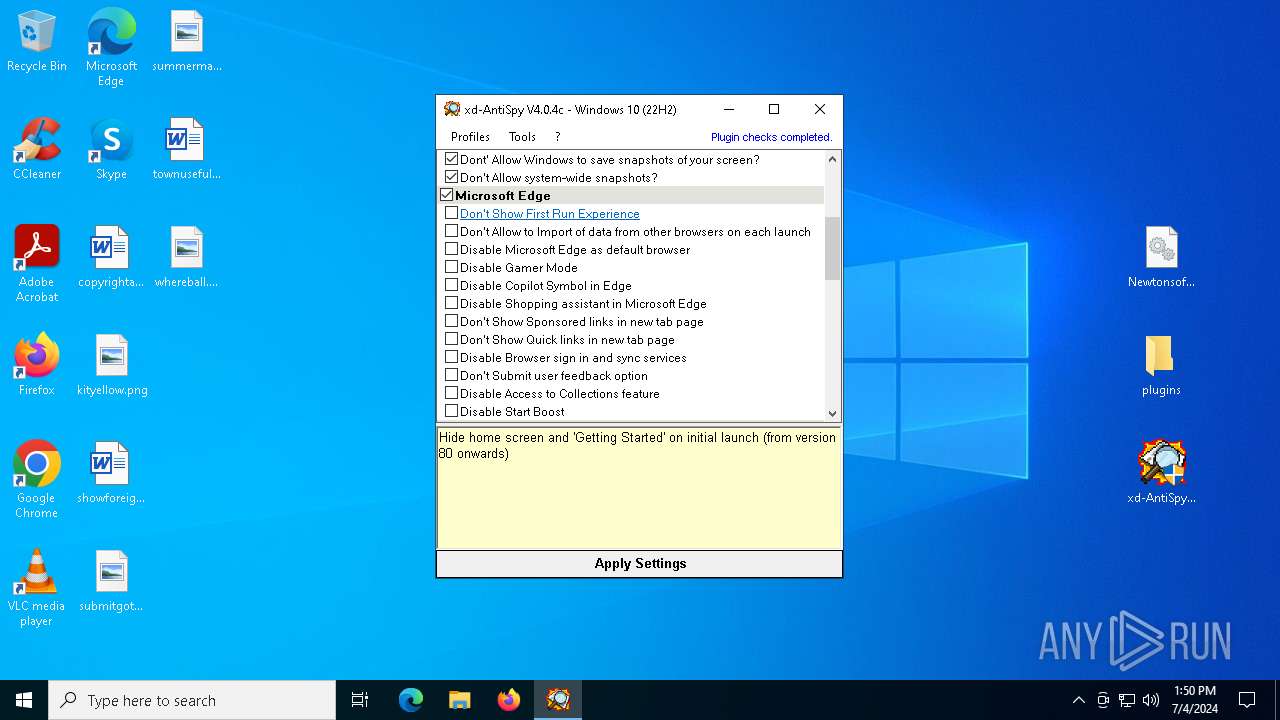
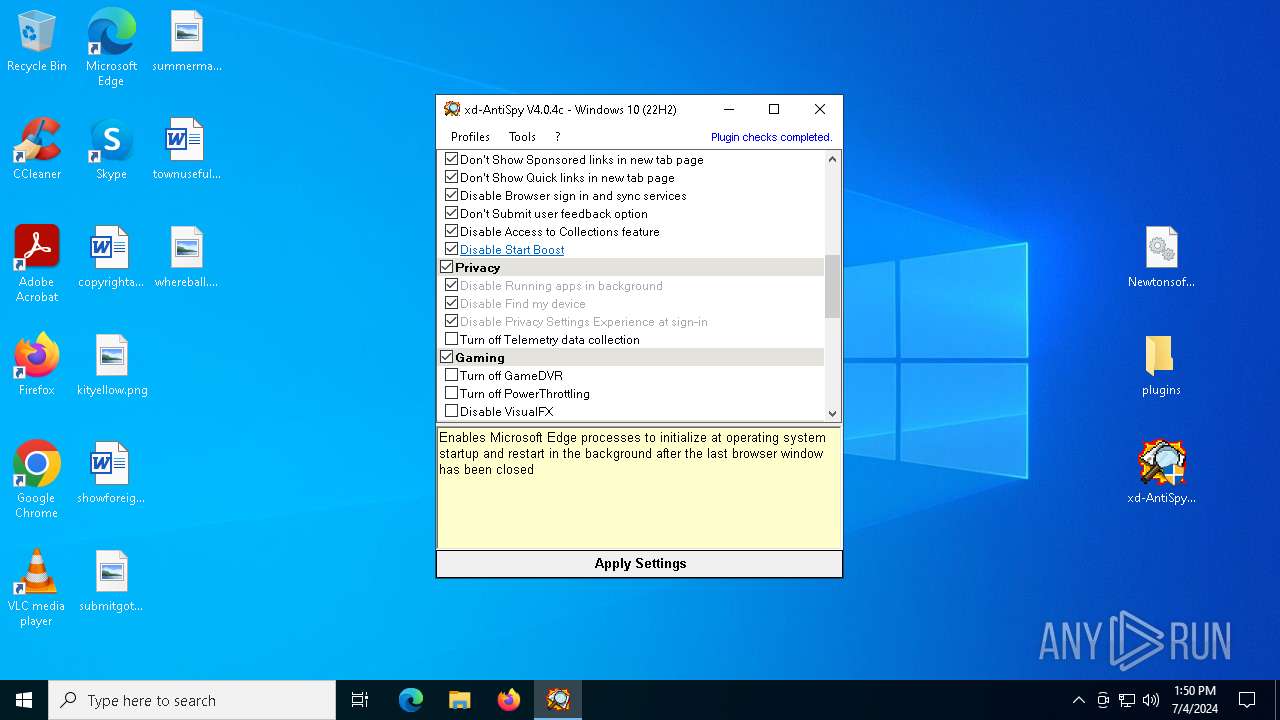
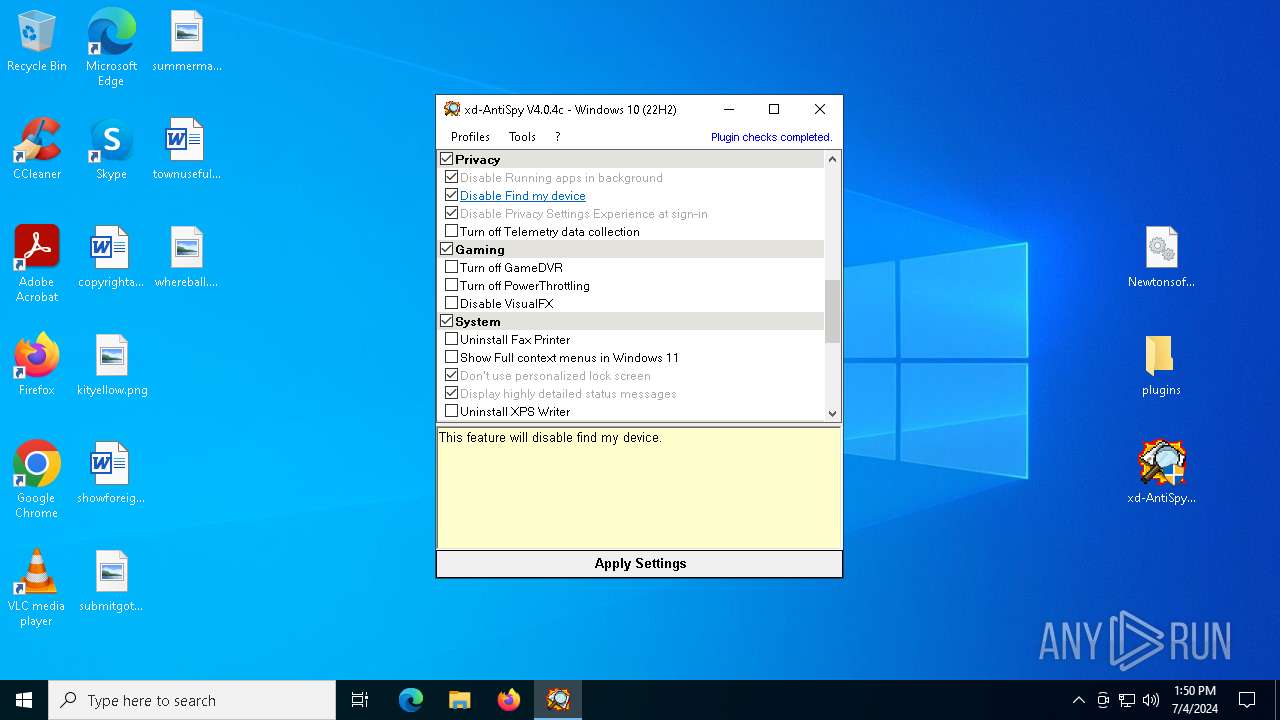
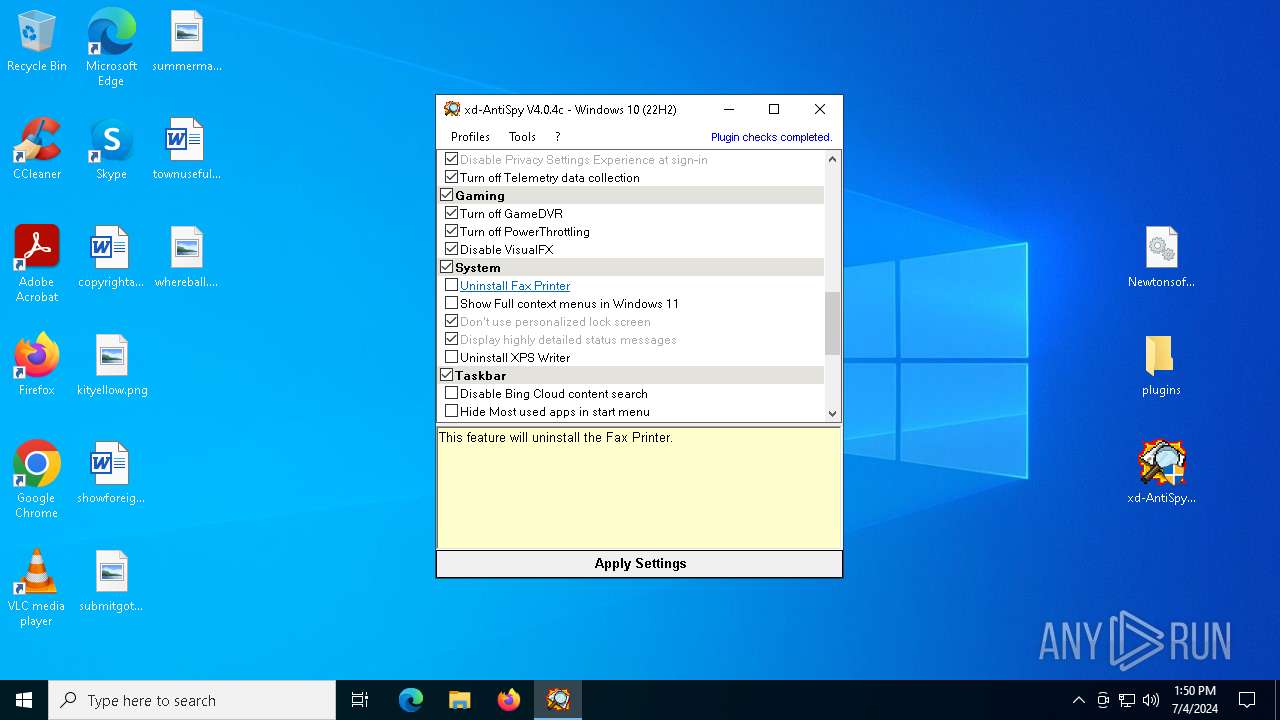
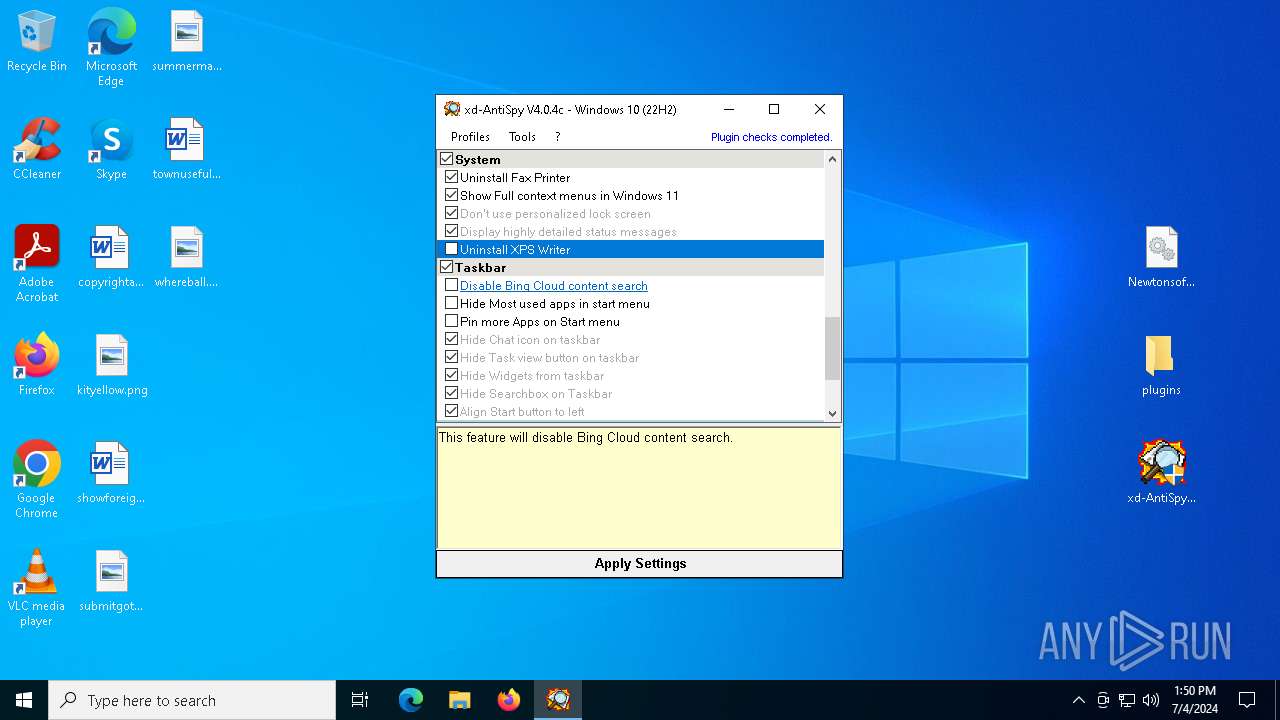
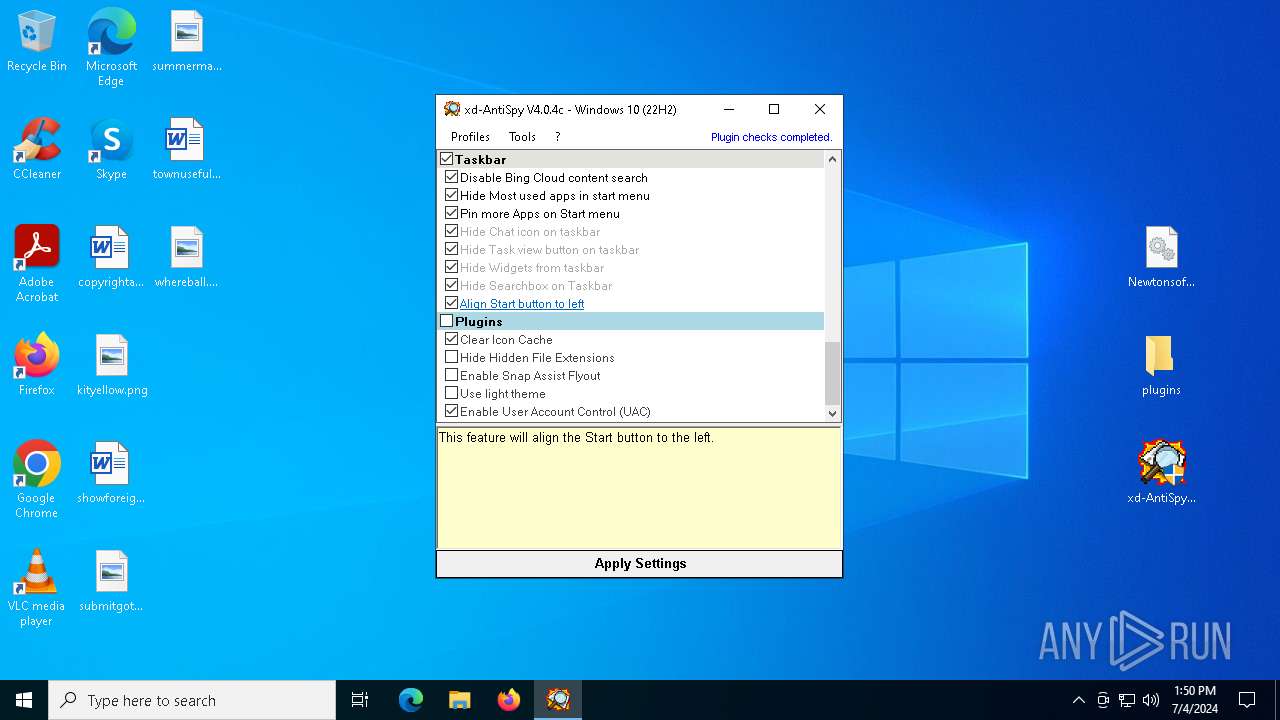
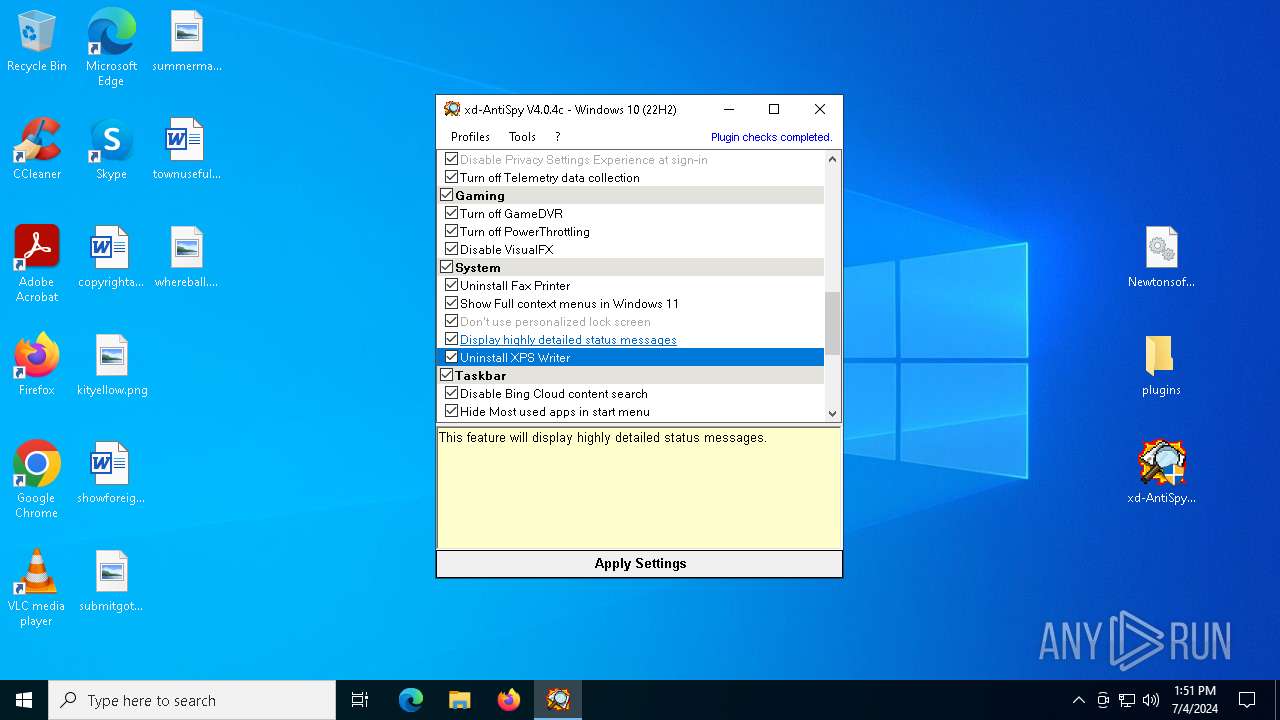
| File name: | xd-AntiSpy.zip |
| Full analysis: | https://app.any.run/tasks/b1f3b08a-ec79-4f19-8d1f-6c03955736e8 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2024, 13:49:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 59533DA83D5CDB60C849E0E9EC30A53C |
| SHA1: | FD0AEA950C4C48ECA7547E2027529EEDDADAA199 |
| SHA256: | 06145E4A9BF0F9E70D06329CBA0ABA6A90BD635D8E297574FB7118DA2FDFDA20 |
| SSDEEP: | 12288:T1K+HPEro7aDOimgk2s6rRKv3UjtNYWLkmzLD/Gk5qjGW:T1wro7wOijk2s6tKv3UzYWLkmvD/GkI7 |
MALICIOUS
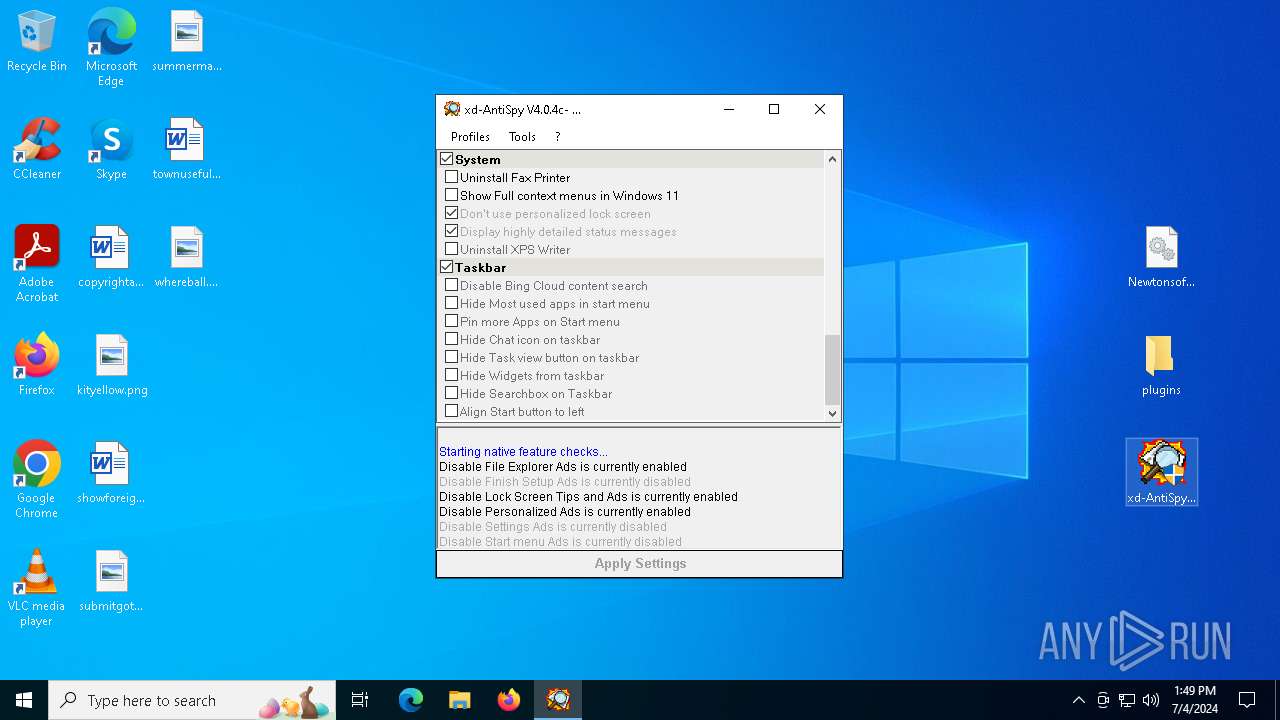
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3848)
- xd-AntiSpy.exe (PID: 2728)
SUSPICIOUS
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 2356)
- DismHost.exe (PID: 6192)
- DismHost.exe (PID: 652)
Process drops legitimate windows executable
- xd-AntiSpy.exe (PID: 2728)
Reads security settings of Internet Explorer
- xd-AntiSpy.exe (PID: 2728)
- StartMenuExperienceHost.exe (PID: 6340)
- GameBar.exe (PID: 4024)
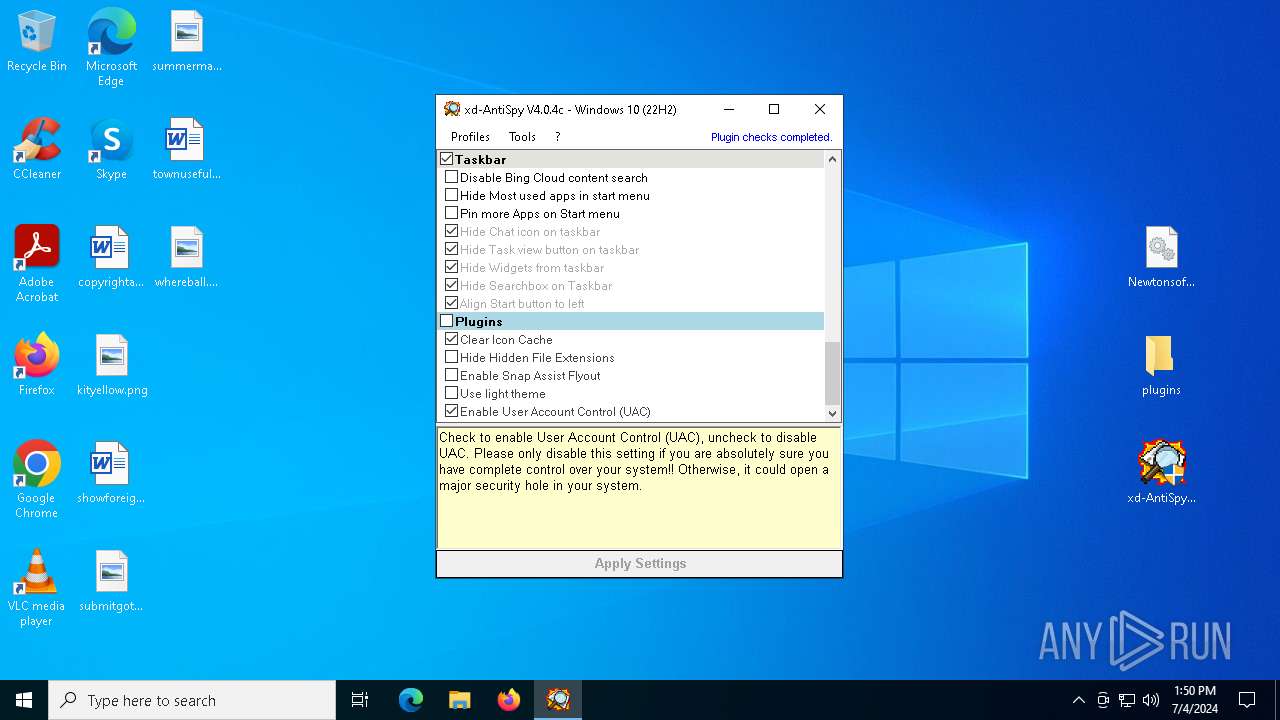
Checks Windows Trust Settings
- xd-AntiSpy.exe (PID: 2728)
Starts CMD.EXE for commands execution
- xd-AntiSpy.exe (PID: 2728)
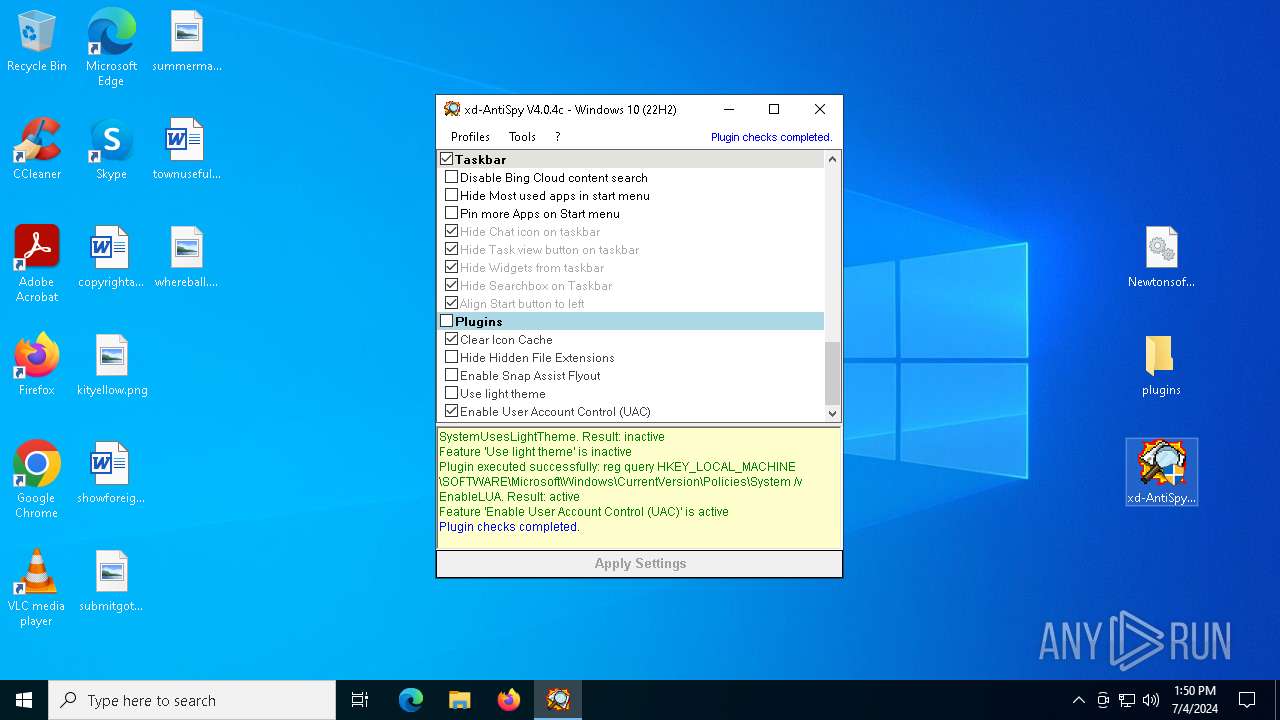
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6176)
- cmd.exe (PID: 6780)
- cmd.exe (PID: 6220)
- cmd.exe (PID: 1004)
- cmd.exe (PID: 4028)
Creates or modifies Windows services
- xd-AntiSpy.exe (PID: 2728)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7024)
The process executes via Task Scheduler
- explorer.exe (PID: 1160)
Executes as Windows Service
- VSSVC.exe (PID: 3188)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 6340)
Searches for installed software
- TiWorker.exe (PID: 5316)
The process creates files with name similar to system file names
- xd-AntiSpy.exe (PID: 2728)
Detected use of alternative data streams (AltDS)
- xd-AntiSpy.exe (PID: 2728)
Executable content was dropped or overwritten
- xd-AntiSpy.exe (PID: 2728)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3848)
Checks supported languages
- DismHost.exe (PID: 2356)
- xd-AntiSpy.exe (PID: 2728)
- DismHost.exe (PID: 6192)
- DismHost.exe (PID: 652)
- SearchApp.exe (PID: 1048)
- GameBar.exe (PID: 4024)
- StartMenuExperienceHost.exe (PID: 6340)
- TextInputHost.exe (PID: 7072)
Reads the computer name
- DismHost.exe (PID: 2356)
- xd-AntiSpy.exe (PID: 2728)
- DismHost.exe (PID: 6192)
- DismHost.exe (PID: 652)
- StartMenuExperienceHost.exe (PID: 6340)
- GameBar.exe (PID: 4024)
- TextInputHost.exe (PID: 7072)
- SearchApp.exe (PID: 1048)
Reads the machine GUID from the registry
- xd-AntiSpy.exe (PID: 2728)
- SearchApp.exe (PID: 1048)
Manual execution by a user
- xd-AntiSpy.exe (PID: 2728)
- xd-AntiSpy.exe (PID: 992)
Create files in a temporary directory
- xd-AntiSpy.exe (PID: 2728)
Reads Environment values
- DismHost.exe (PID: 6192)
- DismHost.exe (PID: 2356)
- DismHost.exe (PID: 652)
- SearchApp.exe (PID: 1048)
- xd-AntiSpy.exe (PID: 2728)
Changes appearance of the Explorer extensions
- reg.exe (PID: 7104)
- reg.exe (PID: 4928)
Reads Microsoft Office registry keys
- explorer.exe (PID: 1160)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1160)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 6340)
- SearchApp.exe (PID: 1048)
Creates files or folders in the user directory
- StartMenuExperienceHost.exe (PID: 6340)
Checks proxy server information
- SearchApp.exe (PID: 1048)
- explorer.exe (PID: 1160)
Process checks Internet Explorer phishing filters
- SearchApp.exe (PID: 1048)
Reads the software policy settings
- SearchApp.exe (PID: 1048)
- slui.exe (PID: 6868)
- xd-AntiSpy.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:03:08 09:09:56 |
| ZipCRC: | 0xb76210f4 |
| ZipCompressedSize: | 260876 |
| ZipUncompressedSize: | 711952 |
| ZipFileName: | Newtonsoft.Json.dll |
Total processes
219
Monitored processes
72
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | taskkill /f /im explorer.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | "cmd.exe" /c reg query HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Themes\Personalize /v AppsUseLightTheme | C:\Windows\System32\cmd.exe | — | xd-AntiSpy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 544 | "cmd.exe" /c reg query HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA | C:\Windows\System32\cmd.exe | — | xd-AntiSpy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 652 | C:\Users\admin\AppData\Local\Temp\8508881E-10F5-473E-985C-D314A6264E43\dismhost.exe {463CF80F-02EE-4835-91BE-8C3FE779811F} | C:\Users\admin\AppData\Local\Temp\8508881E-10F5-473E-985C-D314A6264E43\DismHost.exe | — | xd-AntiSpy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 992 | "C:\Users\admin\Desktop\xd-AntiSpy.exe" | C:\Users\admin\Desktop\xd-AntiSpy.exe | — | explorer.exe | |||||||||||
User: admin Company: A Belim app creation 2024 Integrity Level: MEDIUM Description: xd-AntiSpy Exit code: 3221226540 Version: 4.0.4 Modules
| |||||||||||||||
| 1004 | "cmd.exe" /c "reg add HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced /v ShowSuperHidden /t REG_DWORD /d 0 /f" | C:\Windows\System32\cmd.exe | — | xd-AntiSpy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 2 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | DrvInst.exe "5" "2" "C:\WINDOWS\System32\DriverStore\FileRepository\prnms001.inf_amd64_8bc1bda6cf47380c\prnms001.inf" "0" "4b7f4e337" "00000000000001D4" "WinSta0\Default" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 1160 | "C:\WINDOWS\explorer.exe" /NoUACCheck | C:\Windows\explorer.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
68 553
Read events
68 051
Write events
469
Delete events
33
Modification events
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\xd-AntiSpy.zip | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
152
Suspicious files
57
Text files
134
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.30416\plugins\File Extensions Visibility.json | binary | |
MD5:CA1243D201D273C2F2E5CABE09AD0B9F | SHA256:8C26DC45BFBA8FDC4940408A539E29261D79FC38A0C8A7FE7BD129F99E71ED31 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.30416\plugins\Restart Explorer.ps1 | text | |
MD5:2EBC3B277B6B0038B48F557507372A08 | SHA256:CE31D19E4B3C0A707053DC081E109A465487F57B5180FB470BE9EF75F391095D | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.30416\plugins\Snap Assist Flyout.json | binary | |
MD5:1F5420D9088C4BF71D52FC407C8D4485 | SHA256:83C8B51FA22E37B62253135FCEE3143FC293B97BE0A12A05415E237DA4597939 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.30416\plugins\Use light theme.json | binary | |
MD5:77FA56569685E559B47E56702254D04F | SHA256:69497B89C4FED794C28D05FCDF5785DF7482AACD0AA557238500254688B5831B | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.30416\plugins\toolDebloater.json | ini | |
MD5:999F24BE962A180CD720D6B20E779D61 | SHA256:062D12D99F51D8963DCFAB996A60FDF9491F1CA5C291927DEC752ACDFFC46698 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.30416\plugins\User Account Control.json | binary | |
MD5:D19364DC6D15AFFBC488D77B1D3F09F8 | SHA256:10C63BBE2C149F8B4B2927ACD993716CD890118A6AF7953CD6A92ABDE2C8927F | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.30416\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 2728 | xd-AntiSpy.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_31e5p1i5.xt1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2728 | xd-AntiSpy.exe | C:\WINDOWS\Logs\DISM\dism.log | text | |
MD5:2A4AEAD222F156BF488A89FF24B8C955 | SHA256:45A3299482FAFEABB056B29006E840744FB08EF210FE59758B94E55DD8BADDB4 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.30416\xd-AntiSpy.exe | executable | |
MD5:6495D3241FF331D2DED2A20D9D2CF6CA | SHA256:16615EFC42D24F5ABBB0BFC05B34C1A6E34B9E5770A3354017A3F714BDCF4F01 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
81
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2064 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2064 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
5968 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5220 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
5220 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
4632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
2476 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2336 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3676 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2064 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2064 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2064 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2064 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4656 | SearchApp.exe | 92.123.104.38:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
xd-AntiSpy.exe | PID=2728 TID=1324 DismApi.dll: API Version 6.2.19041.3758 - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 DismApi.dll: Parent process command line: "C:\Users\admin\Desktop\xd-AntiSpy.exe" - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 Enter DismInitializeInternal - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 Input parameters: LogLevel: 2, LogFilePath: C:\WINDOWS\Logs\DISM\dism.log, ScratchDirectory: (null) - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 DismApi.dll: - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 DismApi.dll: <----- Starting DismApi.dll session -----> - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 DismApi.dll: - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 DismApi.dll: Host machine information: OS Version=10.0.19045, Running architecture=amd64, Number of processors=4 - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 Initialized GlobalConfig - DismInitializeInternal
|
xd-AntiSpy.exe | PID=2728 TID=1324 Initialized SessionTable - DismInitializeInternal
|