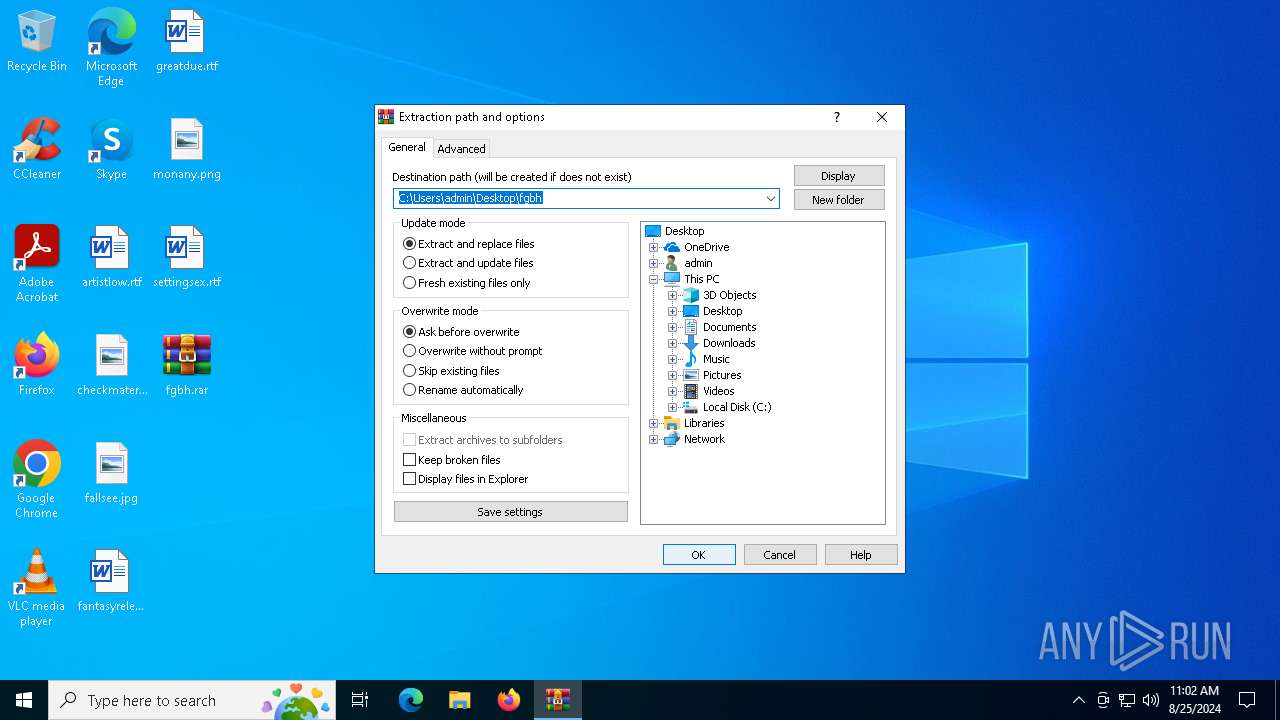
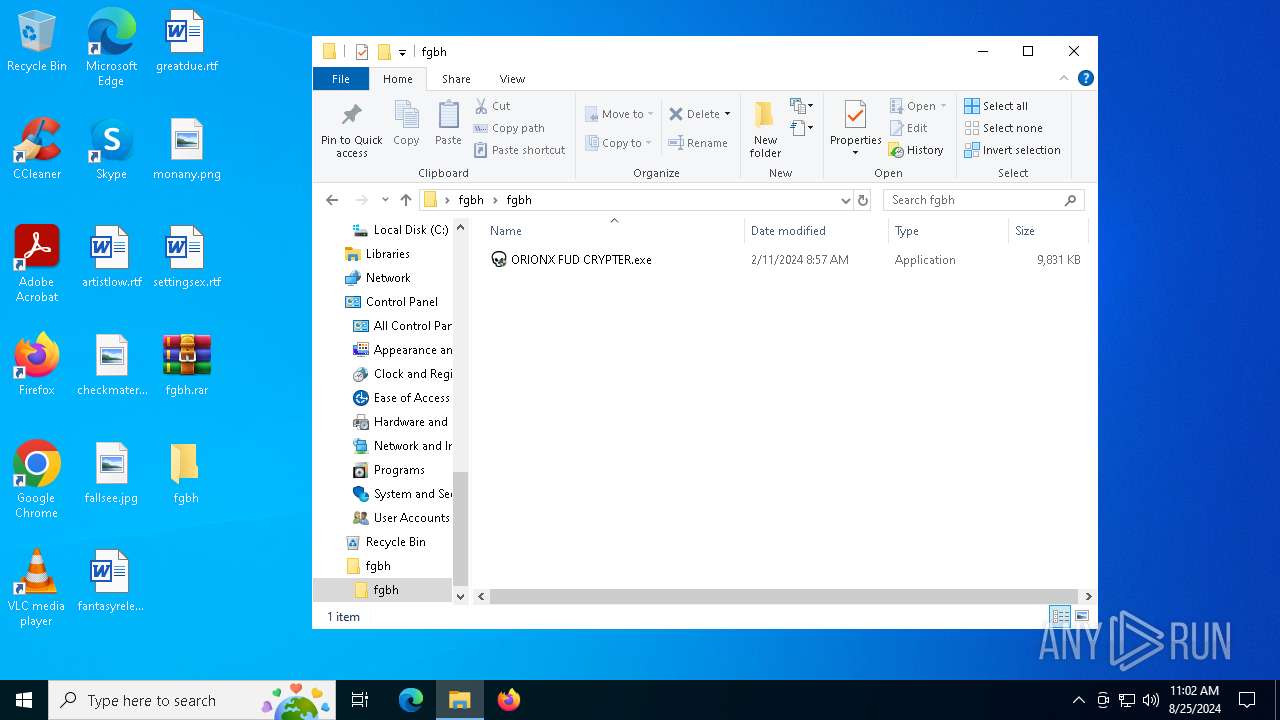
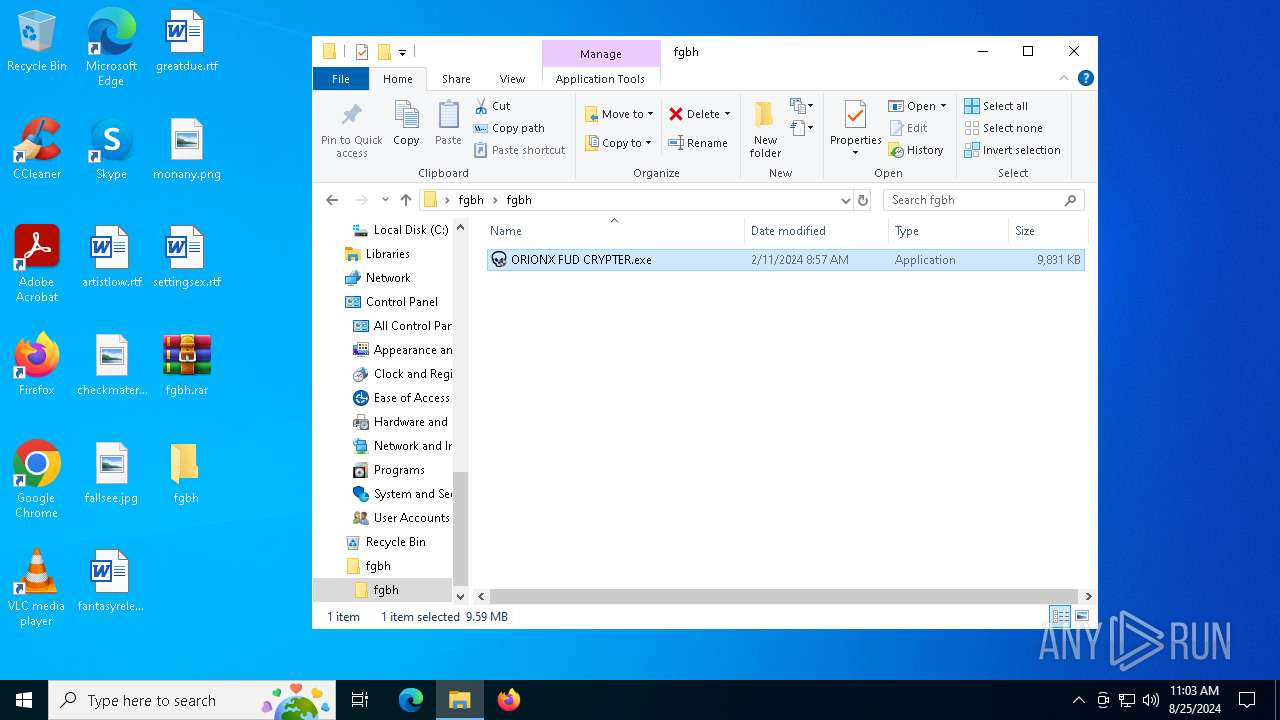
| File name: | fgbh.rar |
| Full analysis: | https://app.any.run/tasks/f1f7e582-b7d5-4a40-98b0-49c6172705ed |
| Verdict: | Malicious activity |
| Analysis date: | August 25, 2024, 11:02:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7391F9B2C60F3904817ED0D0AB88D59B |
| SHA1: | B6B192A9E5246E14C113B4CE2CA3583EF12E3E8D |
| SHA256: | 05F16A57FA8CFB84DE6C072919ECAC7882942564C1EB875151B9913A9E331195 |
| SSDEEP: | 98304:fFiIjMwrFrlHQ9Bt0BHp7FRJJNuoFo+7ondSFpSkFT9m5yPzCb81f061rpEynO6L:3bN3U8ThF |
MALICIOUS
No malicious indicators.SUSPICIOUS
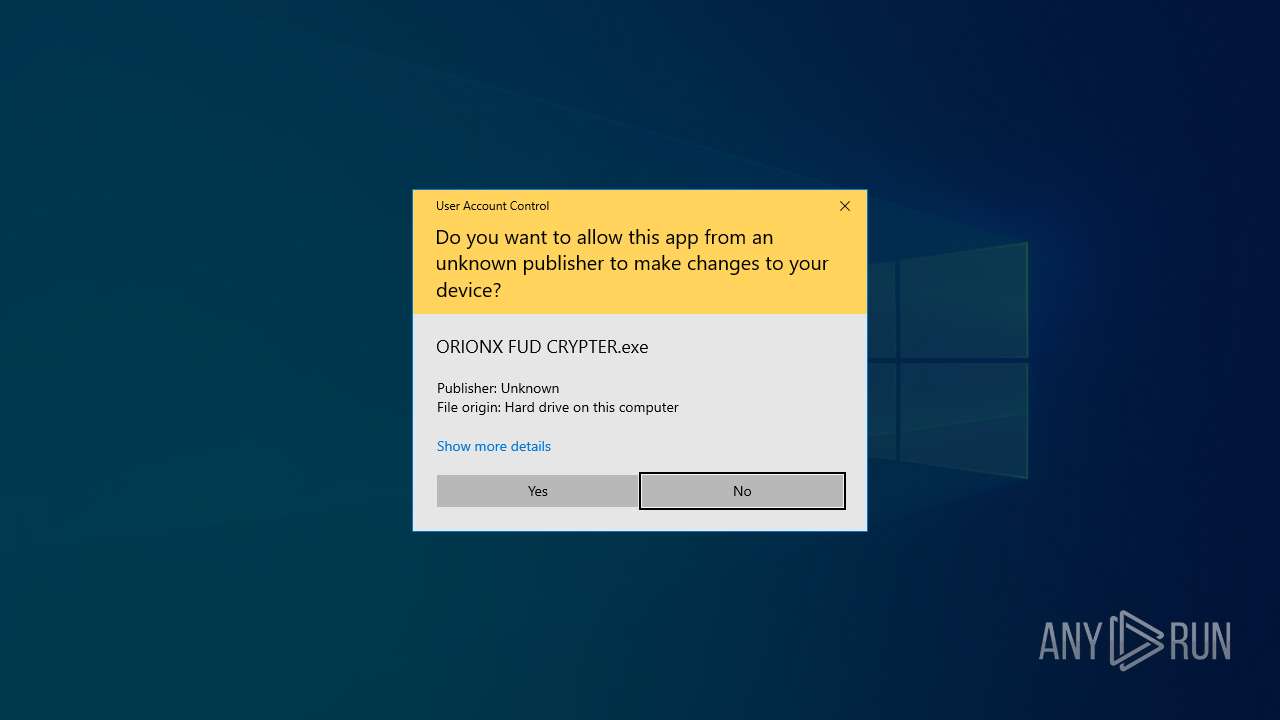
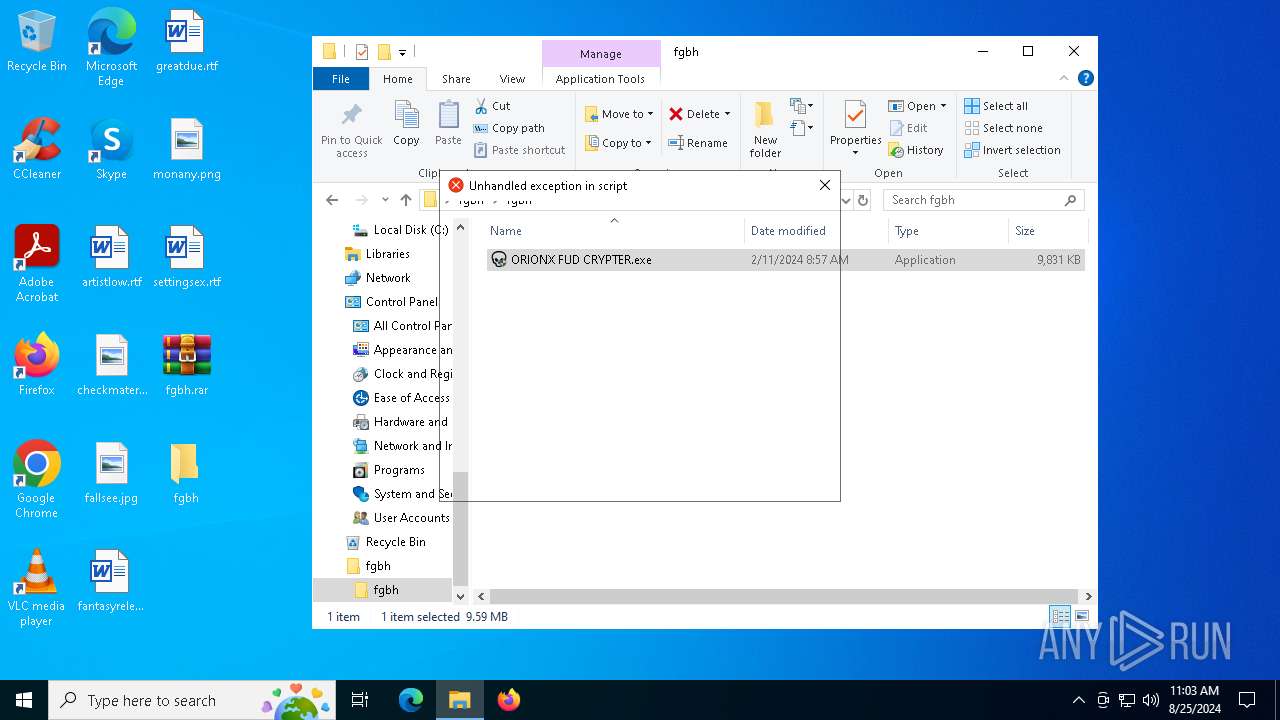
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6888)
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
The process drops C-runtime libraries
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
Process drops legitimate windows executable
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
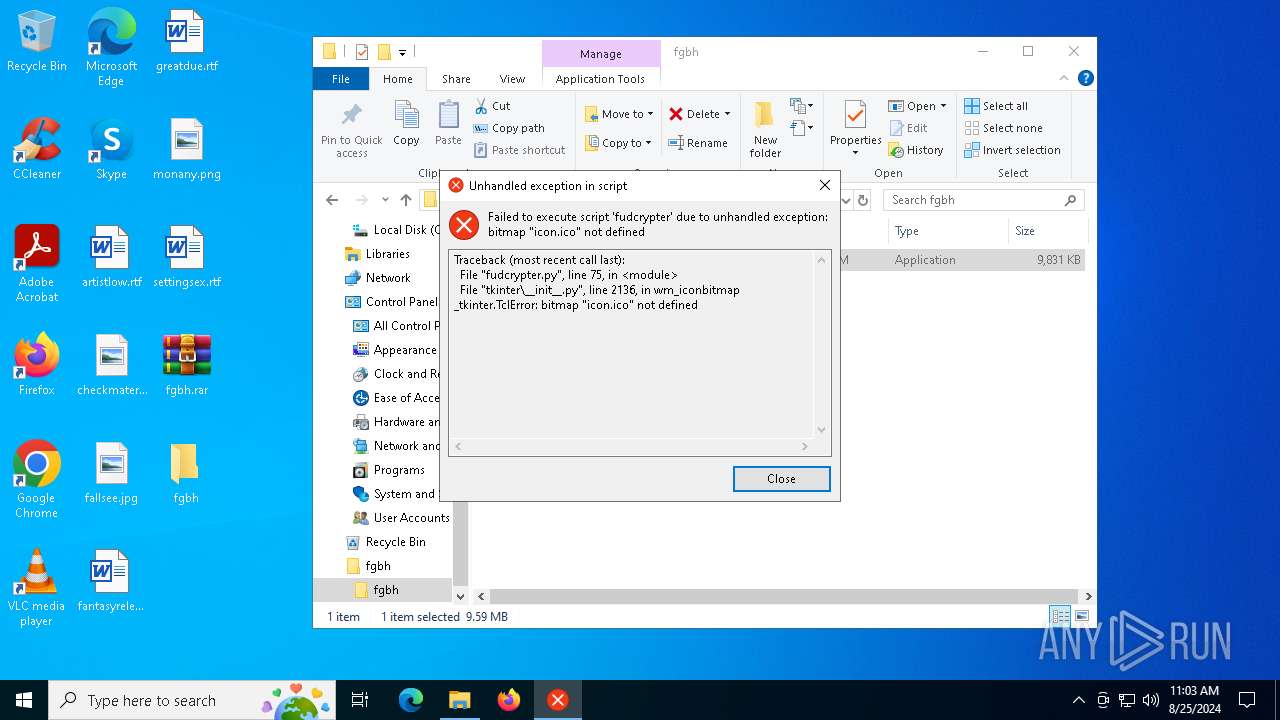
Process drops python dynamic module
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
Executable content was dropped or overwritten
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
Application launched itself
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
Loads Python modules
- ORIONX FUD CRYPTER.exe (PID: 7136)
- ORIONX FUD CRYPTER.exe (PID: 6404)
INFO
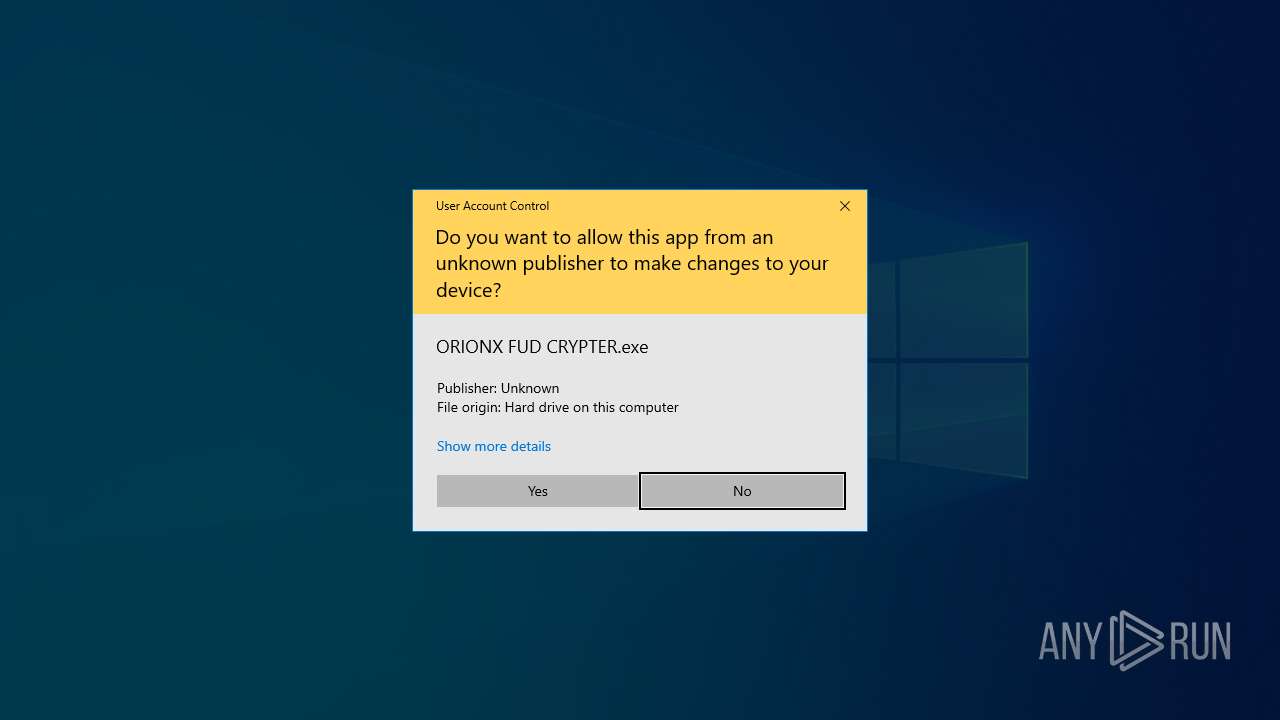
Manual execution by a user
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 6796)
- WinRAR.exe (PID: 7048)
- ORIONX FUD CRYPTER.exe (PID: 4084)
Checks supported languages
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
- ORIONX FUD CRYPTER.exe (PID: 6404)
- ORIONX FUD CRYPTER.exe (PID: 7136)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7048)
Reads the computer name
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
- ORIONX FUD CRYPTER.exe (PID: 6404)
- ORIONX FUD CRYPTER.exe (PID: 7136)
Create files in a temporary directory
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
PyInstaller has been detected (YARA)
- ORIONX FUD CRYPTER.exe (PID: 3184)
- ORIONX FUD CRYPTER.exe (PID: 4084)
- ORIONX FUD CRYPTER.exe (PID: 7136)
- ORIONX FUD CRYPTER.exe (PID: 6404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
131
Monitored processes
8
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3184 | "C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe" | C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 4084 | "C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe" | C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6404 | "C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe" | C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe | ORIONX FUD CRYPTER.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6456 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6796 | "C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe" | C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6888 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\fgbh.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7048 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\fgbh.rar" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7136 | "C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe" | C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe | ORIONX FUD CRYPTER.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
Total events
6 101
Read events
6 075
Write events
26
Delete events
0
Modification events
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\fgbh.rar | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6888) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
31
Suspicious files
6
Text files
1 840
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7048 | WinRAR.exe | C:\Users\admin\Desktop\fgbh\fgbh\ORIONX FUD CRYPTER.exe | executable | |
MD5:AF452C108FEE8530119D2534722238DD | SHA256:A1539F9996C040B18C34983D48B80A3592F00C93AB5A279BF015999CF1796E1B | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\_ssl.pyd | executable | |
MD5:AB0E4FBFFB6977D0196C7D50BC76CF2D | SHA256:680AD2DE8A6CFF927822C1D7DD22112A3E8A824E82A7958EE409A7B9CE45EC70 | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\_bz2.pyd | executable | |
MD5:A62207FC33140DE460444E191AE19B74 | SHA256:EBCAC51449F323AE3AE961A33843029C34B6A82138CCD9214CF99F98DD2148C2 | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\VCRUNTIME140.dll | executable | |
MD5:4585A96CC4EEF6AAFD5E27EA09147DC6 | SHA256:A8F950B4357EC12CFCCDDC9094CCA56A3D5244B95E09EA6E9A746489F2D58736 | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\_lzma.pyd | executable | |
MD5:0C7EA68CA88C07AE6B0A725497067891 | SHA256:F74AAF0AA08CF90EB1EB23A474CCB7CB706B1EDE7F911DAF7AE68480765BDF11 | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\_socket.pyd | executable | |
MD5:26DD19A1F5285712068B9E41808E8FA0 | SHA256:EAABF6B78840DAEAF96B5BDBF06ADF0E4E2994DFEEE5C5E27FEFD824DBDA5220 | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\_hashlib.pyd | executable | |
MD5:787B82D4466F393366657B8F1BC5F1A9 | SHA256:241322647BA9F94BDC3AE387413FFB57AE14C8CF88BD564A31FE193C6CA43E37 | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\libcrypto-1_1.dll | executable | |
MD5:9D7A0C99256C50AFD5B0560BA2548930 | SHA256:9B7B4A0AD212095A8C2E35C71694D8A1764CD72A829E8E17C8AFE3A55F147939 | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\libssl-1_1.dll | executable | |
MD5:BEC0F86F9DA765E2A02C9237259A7898 | SHA256:D74CE01319AE6F54483A19375524AA39D9F5FD91F06CF7DF238CA25E043130FD | |||
| 3184 | ORIONX FUD CRYPTER.exe | C:\Users\admin\AppData\Local\Temp\_MEI31842\_tkinter.pyd | executable | |
MD5:6352DB60D88705CE62B5665764529006 | SHA256:4536D9092A366426AA01E1800D9D4DE669928BBCB277F2363D54DF44DA096C31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
20
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5744 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1076 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1076 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3208 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5888 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5744 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5744 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |