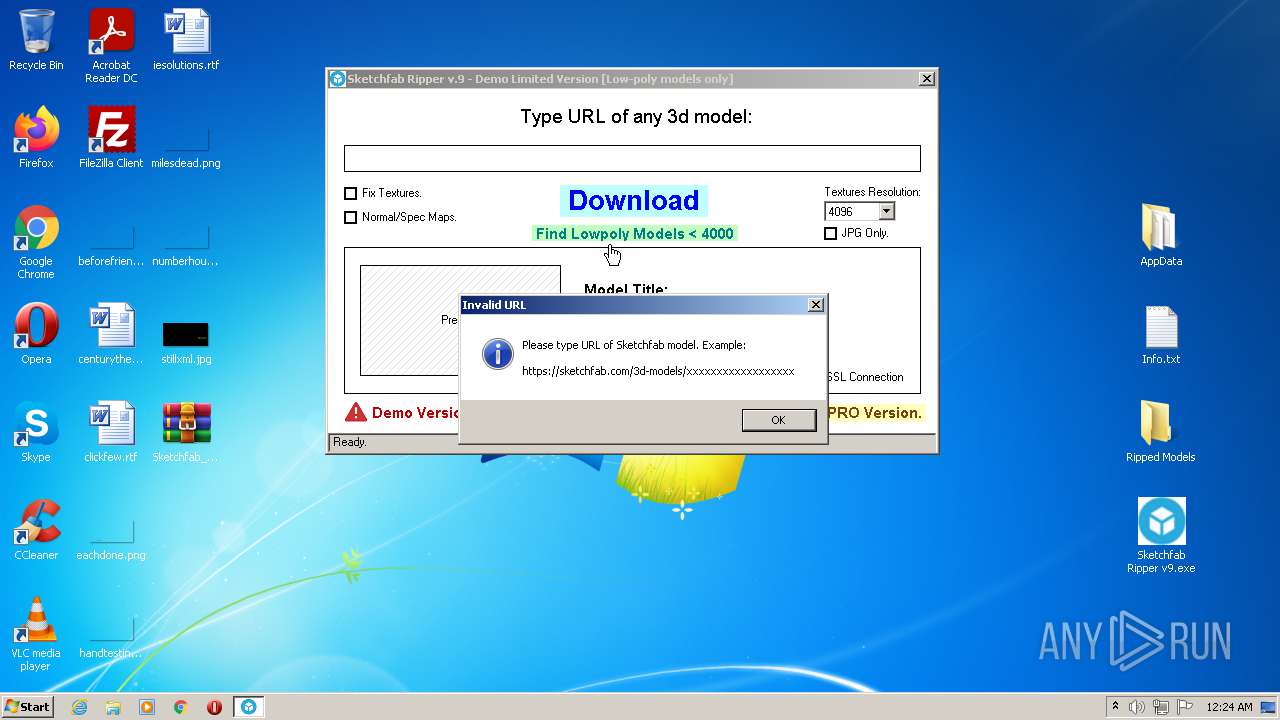
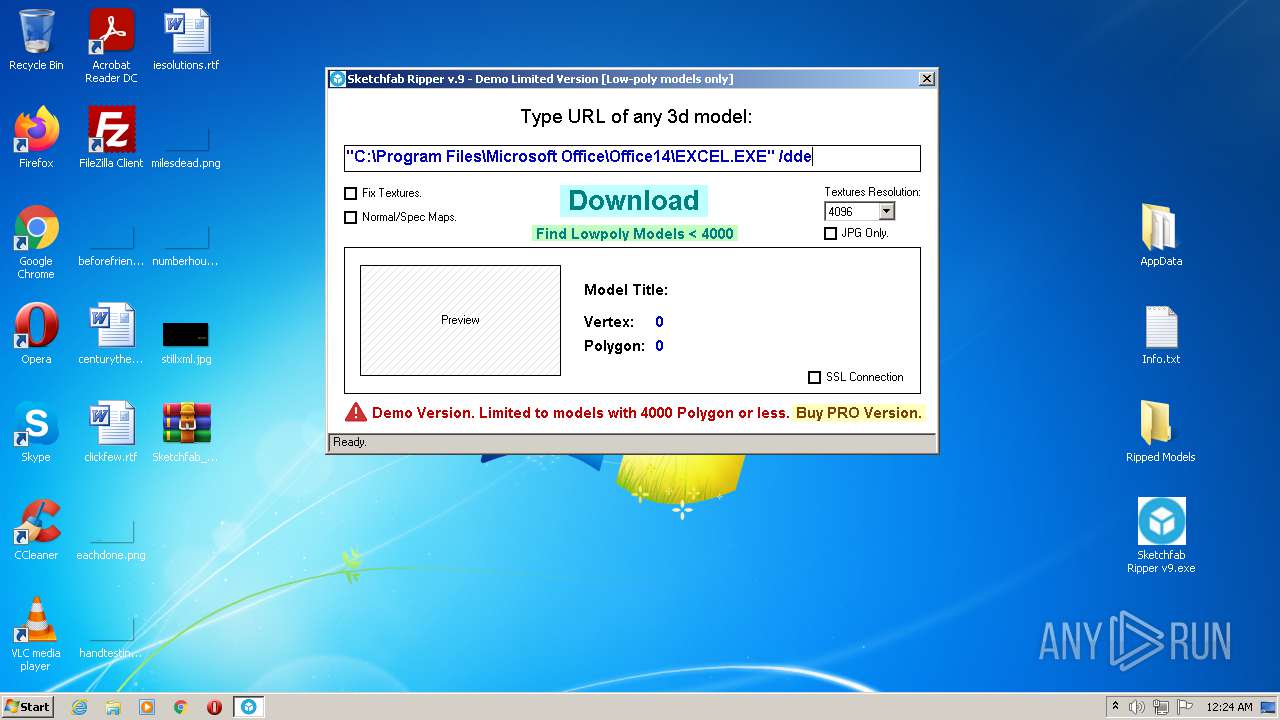
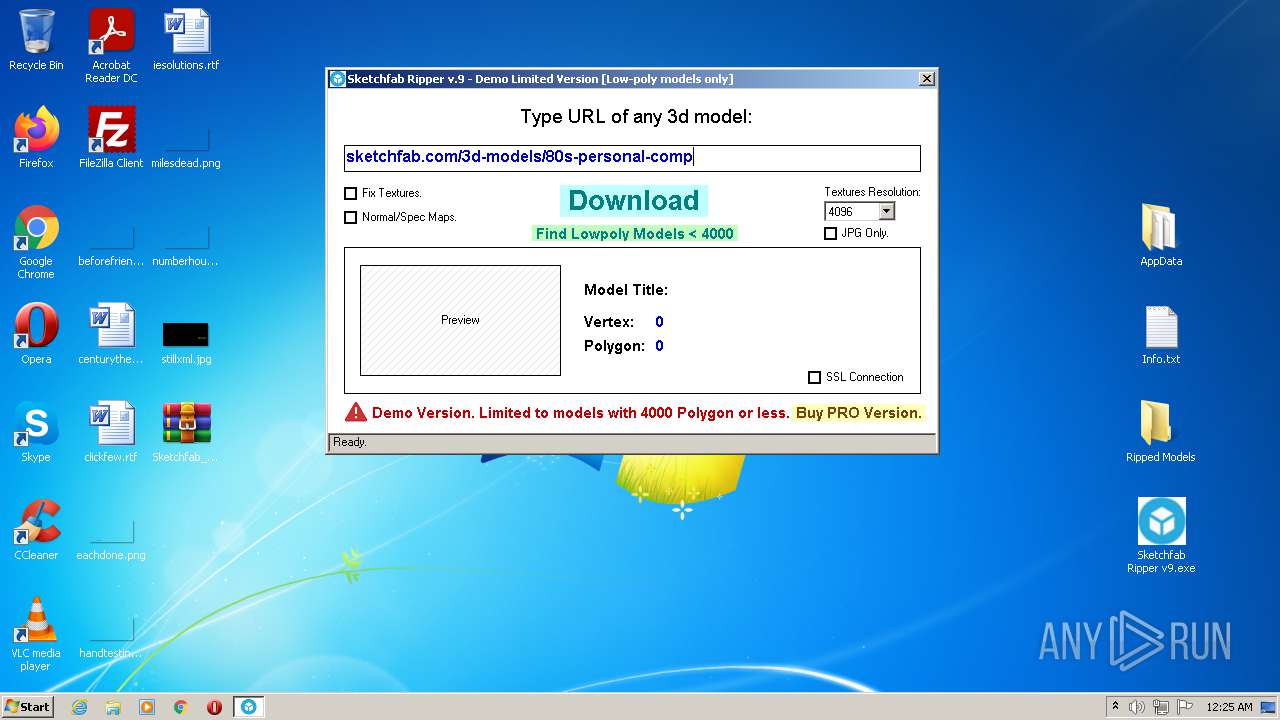
| File name: | Sketchfab_Ripper_v9.zip |
| Full analysis: | https://app.any.run/tasks/b50378c0-cffd-43de-8f80-9baa8aadc762 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2021, 23:23:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 3CF63D7CE8CC88273944EE9F4E87A880 |
| SHA1: | 6A61B4AA3E261AA62C20BFDA0E21770C79FD1D16 |
| SHA256: | 05ED4C8CFA17683AF3640C25080DF236EA8962734F01055FF2CF3898FCC6D454 |
| SSDEEP: | 196608:NLhj0S5YG0GTN9lrfJKX44NvFSnT1lUQRXI2fWqr0VToJkm35zju5Uv:NJjbvnLnT1OSpWqI0kU5zOUv |
MALICIOUS
Steals credentials from Web Browsers
- config.bat (PID: 552)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3396)
- sf_ripper.bat (PID: 2060)
Actions looks like stealing of personal data
- config.bat (PID: 552)
Application was dropped or rewritten from another process
- Sketchfab Ripper v9.exe (PID: 3512)
- config.bat (PID: 552)
- sf_ripper.bat (PID: 2060)
SUSPICIOUS
Drops a file with too old compile date
- WinRAR.exe (PID: 3828)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3828)
Reads the computer name
- WinRAR.exe (PID: 3828)
- config.bat (PID: 552)
- Sketchfab Ripper v9.exe (PID: 3512)
Checks supported languages
- Sketchfab Ripper v9.exe (PID: 3512)
- WinRAR.exe (PID: 3828)
- config.bat (PID: 552)
- sf_ripper.bat (PID: 2060)
Suspicious files were dropped or overwritten
- WinRAR.exe (PID: 3828)
- Sketchfab Ripper v9.exe (PID: 3512)
Starts application with an unusual extension
- Sketchfab Ripper v9.exe (PID: 3512)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3828)
- Sketchfab Ripper v9.exe (PID: 3512)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3828)
Executed via COM
- explorer.exe (PID: 2940)
- DllHost.exe (PID: 3192)
Creates files in the user directory
- config.bat (PID: 552)
Reads the date of Windows installation
- explorer.exe (PID: 2940)
Reads default file associations for system extensions
- explorer.exe (PID: 2940)
INFO
Manual execution by user
- Sketchfab Ripper v9.exe (PID: 3512)
Checks Windows Trust Settings
- Sketchfab Ripper v9.exe (PID: 3512)
Reads settings of System Certificates
- Sketchfab Ripper v9.exe (PID: 3512)
Reads the computer name
- explorer.exe (PID: 2940)
- Explorer.exe (PID: 2864)
- DllHost.exe (PID: 3192)
Checks supported languages
- DllHost.exe (PID: 3192)
- explorer.exe (PID: 2940)
- Explorer.exe (PID: 2864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | AppData/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:05:11 14:23:19 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
45
Monitored processes
8
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | AppData\config.bat | C:\Users\admin\Desktop\AppData\config.bat | Sketchfab Ripper v9.exe | ||||||||||||
User: admin Company: Synchronize Integrity Level: MEDIUM Description: Synchronize Exit code: 0 Version: 1.04.0008 Modules
| |||||||||||||||
| 2060 | sf_ripper.bat blank.blend -g -noaudio -noglsl -y -b -P 0000.py -P 0001.py | C:\Users\admin\Desktop\AppData\sf_ripper.bat | — | Sketchfab Ripper v9.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2864 | Explorer.exe Ripped Models\MundoPixelado\01- 80's Personal Computer Keyboard\ | C:\Windows\Explorer.exe | — | Sketchfab Ripper v9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2940 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3192 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3396 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
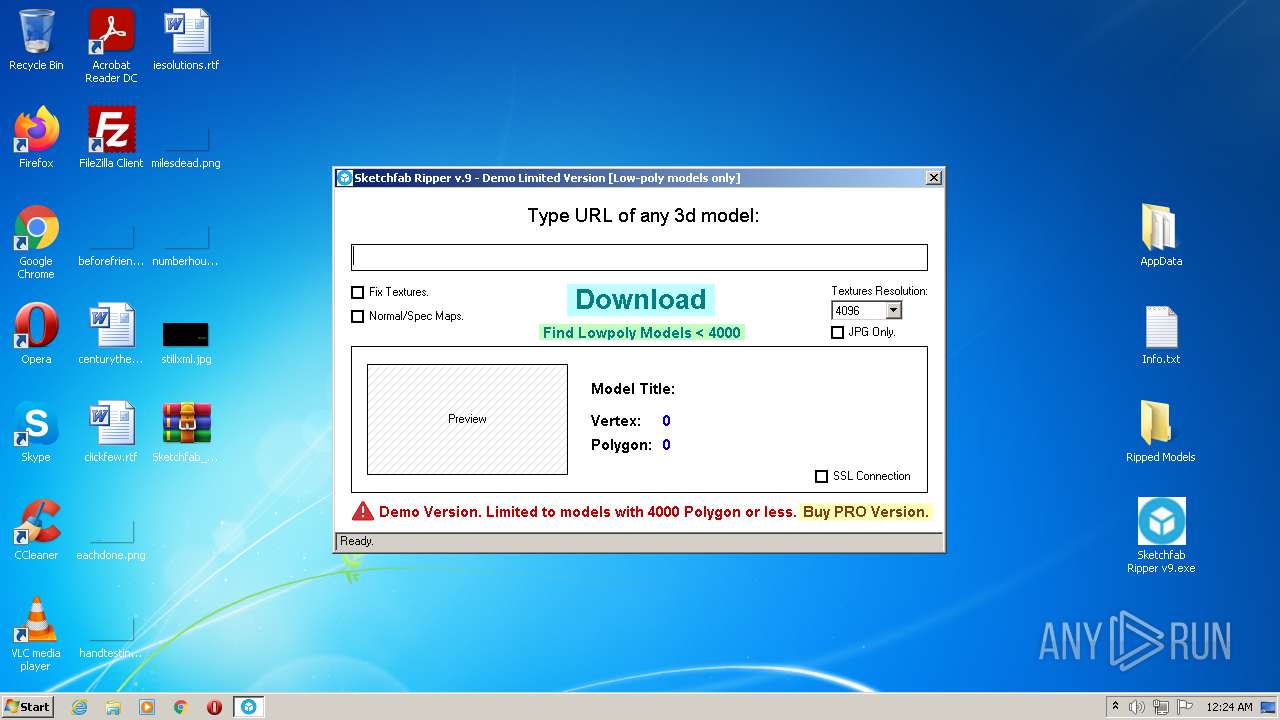
| 3512 | "C:\Users\admin\Desktop\Sketchfab Ripper v9.exe" | C:\Users\admin\Desktop\Sketchfab Ripper v9.exe | Explorer.EXE | ||||||||||||
User: admin Company: Sketchfab-Ripper.com Integrity Level: MEDIUM Description: Sketchfab-Ripper.com Exit code: 0 Version: 12.00 Modules
| |||||||||||||||
| 3828 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Sketchfab_Ripper_v9.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 295
Read events
9 892
Write events
390
Delete events
13
Modification events
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Sketchfab_Ripper_v9.zip | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
16
Suspicious files
11
Text files
64
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\Bpymenus | text | |
MD5:— | SHA256:— | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\export_obj.py | text | |
MD5:FF8A51622E8937DCE36A9D84E20E1146 | SHA256:FBA9A33A87B654C311A700C37A3296A4D9B966A25A4B5B3D13349FE859EB0376 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\bpymodules\BPyObject.py | text | |
MD5:C12A3042956DFE0B2D5E23962C12591A | SHA256:59A2F820E1A6C52520B098F8E677902121F74D70D7BAD7E2076565D83AD32319 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\newGameLib\myLibraries\myFunction.py | text | |
MD5:261BF7CD59653D40B94F59F2DEDE475B | SHA256:8609D084F0E3E6F2461FBDC118B9448B6A2C938E311E56D54D2472657C8F497F | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\bpymodules\BPySys.py | text | |
MD5:BB826670AD54708855637D84F1BA4D97 | SHA256:8DBAB6228272D8F7F7556CD8E4BA92E0ACF3C1C949931968E750329C13FE47D4 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\newGameLib\myLibraries\imageLib.py | text | |
MD5:DFBB7C07EBC3F060DFE6426B2EC6BF58 | SHA256:CFFF58BC2D2EE4BDF7EA8EB903EA2FA54D3571BF2766F3ED309B8A714295660C | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\newGameLib\myLibraries\actionLib.py | text | |
MD5:410EEA9BBCD270365C1AC7F1202E9174 | SHA256:6B5BC5CB21FC46BD6884A1AF8AF864FAA3F15DDEEE4C863C4E18F145C83232E3 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\newGameLib\myLibraries\binaresLib.py | text | |
MD5:9072082D81846D5C33EF324D68BFA27A | SHA256:5EE9A57C781B7B6789320FA67109B8BA5C20DEDBA23384FDA8272B3087D45F80 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\bpymodules\BPyMessages.py | text | |
MD5:653FC2E1E01F9073C2AC01AE6CFD4059 | SHA256:3E364197CDDCEF068A0BB78E6DDC423109BD9ABC2A5251BFB12DB88EBD711F98 | |||
| 3828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3828.7084\AppData\.blender\scripts\newGameLib\myLibraries\meshLib.py | text | |
MD5:AB373C04BA99EDCA34CBA6E3F820CB4D | SHA256:271B109A9F8DD9FFE8B3163DDEBC2D338F2AF215EAA18BF0DB8648D9A74B8FF5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
20
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3512 | Sketchfab Ripper v9.exe | GET | 200 | 13.225.84.145:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3512 | Sketchfab Ripper v9.exe | GET | 200 | 143.204.214.74:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAWSkQ%2FxfjBHjZi6MmhNbUA%3D | US | der | 471 b | whitelisted |
3512 | Sketchfab Ripper v9.exe | GET | 200 | 52.222.137.133:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
552 | config.bat | POST | 200 | 23.95.12.218:80 | http://coinbella.com/game/newgame.php?&rnd=6963.6 | US | text | 4 b | unknown |
552 | config.bat | POST | 200 | 23.95.12.218:80 | http://coinbella.com/game/newgame.php?&rnd=2349.4 | US | text | 4 b | unknown |
3512 | Sketchfab Ripper v9.exe | GET | 301 | 13.225.74.107:80 | http://media.sketchfab.com/models/5e400fbc21c34e72ab103640db42cde6/2bf5ae19b4aa496e8d343625a77b38c5/files/515a66bccdcc4e84bb88eb8e869a435e/model_file_wireframe.bin.gz | US | html | 183 b | whitelisted |
3512 | Sketchfab Ripper v9.exe | GET | 200 | 8.253.95.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?88e7a13e2898fbc0 | US | compressed | 4.70 Kb | whitelisted |
3512 | Sketchfab Ripper v9.exe | GET | 200 | 13.225.84.97:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
552 | config.bat | POST | 200 | 23.95.12.218:80 | http://coinbella.com/game/newgame.php?&rnd=8933.6 | US | text | 4 b | unknown |
3512 | Sketchfab Ripper v9.exe | GET | 200 | 107.172.10.124:80 | http://rigmodels.com/exporter/sf_rip_v2.php?rnd=137&uid=Free_Trial&hash=53-101-52-48-48-102-98-99-50-49-99-51-52-101-55-50-97-98-49-48-51-54-52-48-100-98-52-50-99-100-101-54-&pc=97100109105110 | US | text | 53 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3512 | Sketchfab Ripper v9.exe | 13.224.195.71:443 | sketchfab.com | — | US | suspicious |
3512 | Sketchfab Ripper v9.exe | 13.224.195.71:80 | sketchfab.com | — | US | suspicious |
552 | config.bat | 23.95.12.218:80 | coinbella.com | ColoCrossing | US | unknown |
3512 | Sketchfab Ripper v9.exe | 143.204.214.74:80 | ocsp.sca1b.amazontrust.com | — | US | whitelisted |
3512 | Sketchfab Ripper v9.exe | 107.172.10.124:80 | rigmodels.com | ColoCrossing | US | unknown |
3512 | Sketchfab Ripper v9.exe | 13.225.74.107:80 | media.sketchfab.com | — | US | unknown |
3512 | Sketchfab Ripper v9.exe | 13.225.84.145:80 | ocsp.rootca1.amazontrust.com | — | US | whitelisted |
3512 | Sketchfab Ripper v9.exe | 52.222.137.133:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
3512 | Sketchfab Ripper v9.exe | 8.253.95.121:80 | ctldl.windowsupdate.com | Global Crossing | US | suspicious |
3512 | Sketchfab Ripper v9.exe | 13.225.84.97:80 | o.ss2.us | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
coinbella.com |
| unknown |
sketchfab.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
media.sketchfab.com |
| whitelisted |
rigmodels.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
552 | config.bat | Generic Protocol Command Decode | SURICATA STREAM Last ACK with wrong seq |