| File name: | NDP481-Web.exe |
| Full analysis: | https://app.any.run/tasks/efc830b4-26f0-44c7-9e31-30c13ed11999 |
| Verdict: | Malicious activity |
| Analysis date: | September 24, 2024, 12:26:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 39304CE18D93EEEB6EFA488387ADAED8 |
| SHA1: | 22C974F3865CCE3F0EC385DD9C0B291CA045BC2C |
| SHA256: | 05E9ADA305FD0013A6844E7657F06ED330887093E3DF59C11CB528B86EFA3FBF |
| SSDEEP: | 49152:AIyyfl6pwuJlZ/koJ2LdbHDdEQwWiS4G1RlTnVVi93WTCdgJliViVXHGL4e8VZMM:9yiUmu7xR2LdbHDhwPsRlTVoGTHJlYaR |
MALICIOUS
No malicious indicators.SUSPICIOUS
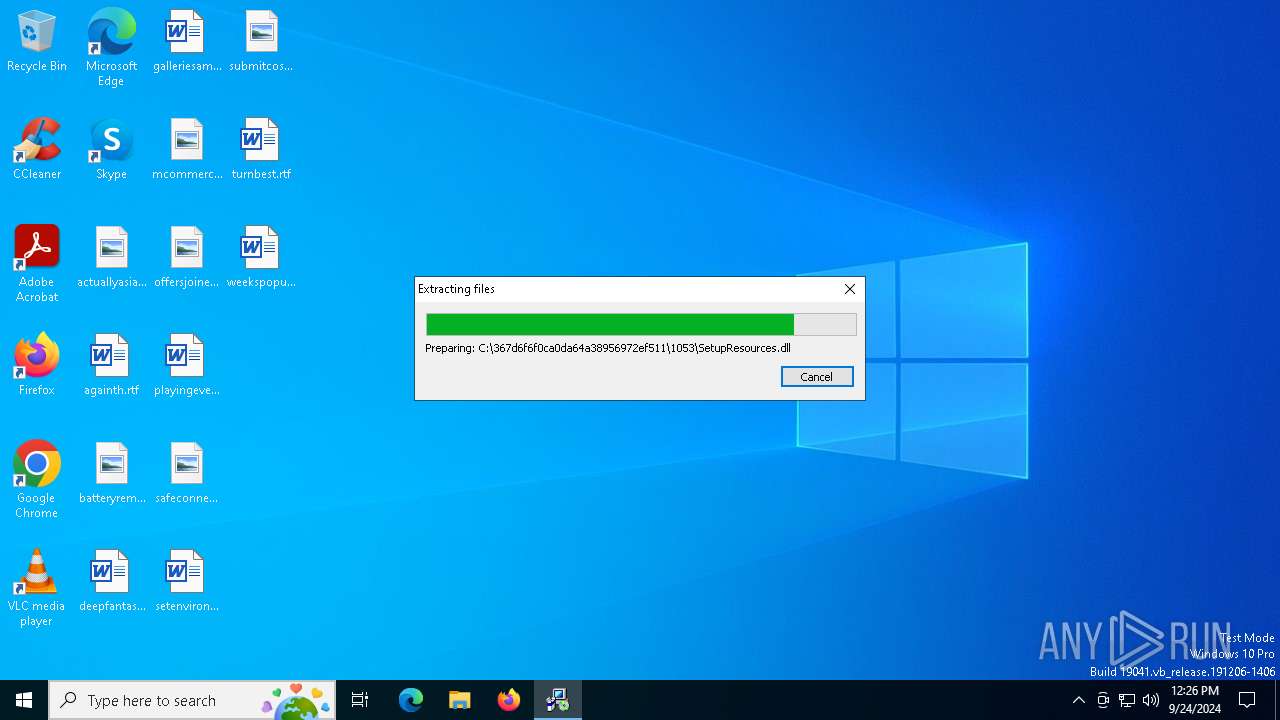
Executable content was dropped or overwritten
- NDP481-Web.exe (PID: 4060)
Process drops legitimate windows executable
- NDP481-Web.exe (PID: 4060)
Starts a Microsoft application from unusual location
- NDP481-Web.exe (PID: 5512)
- NDP481-Web.exe (PID: 4060)
Creates file in the systems drive root
- NDP481-Web.exe (PID: 4060)
Reads security settings of Internet Explorer
- Setup.exe (PID: 6340)
Checks Windows Trust Settings
- Setup.exe (PID: 6340)
INFO
Reads the machine GUID from the registry
- NDP481-Web.exe (PID: 4060)
- Setup.exe (PID: 6340)
Create files in a temporary directory
- NDP481-Web.exe (PID: 4060)
- Setup.exe (PID: 6340)
- SetupUtility.exe (PID: 6740)
Reads the computer name
- NDP481-Web.exe (PID: 4060)
- Setup.exe (PID: 6340)
- SetupUtility.exe (PID: 6740)
- SetupUtility.exe (PID: 6636)
Checks supported languages
- NDP481-Web.exe (PID: 4060)
- Setup.exe (PID: 6340)
- SetupUtility.exe (PID: 6636)
- SetupUtility.exe (PID: 6740)
Reads CPU info
- Setup.exe (PID: 6340)
Creates files or folders in the user directory
- Setup.exe (PID: 6340)
Checks proxy server information
- Setup.exe (PID: 6340)
Reads the software policy settings
- Setup.exe (PID: 6340)
Sends debugging messages
- Setup.exe (PID: 6340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:07:16 21:09:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 160256 |
| InitializedDataSize: | 29184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x18ee7 |
| OSVersion: | 5.1 |
| ImageVersion: | 10 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.8.9195.10 |
| ProductVersionNumber: | 4.8.9195.10 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft .NET Framework 4.8.1 Setup |
| FileVersion: | 4.8.09195.10 |
| InternalName: | NDP481-Web.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | NDP481-Web.exe |
| ProductName: | Microsoft .NET Framework 4.8.1 |
| ProductVersion: | 4.8.09195.10 |
Total processes
132
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4060 | "C:\Users\admin\AppData\Local\Temp\NDP481-Web.exe" | C:\Users\admin\AppData\Local\Temp\NDP481-Web.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.8.1 Setup Exit code: 1602 Version: 4.8.09195.10 Modules
| |||||||||||||||
| 5512 | "C:\Users\admin\AppData\Local\Temp\NDP481-Web.exe" | C:\Users\admin\AppData\Local\Temp\NDP481-Web.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.8.1 Setup Exit code: 3221226540 Version: 4.8.09195.10 Modules
| |||||||||||||||
| 6280 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 6308 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
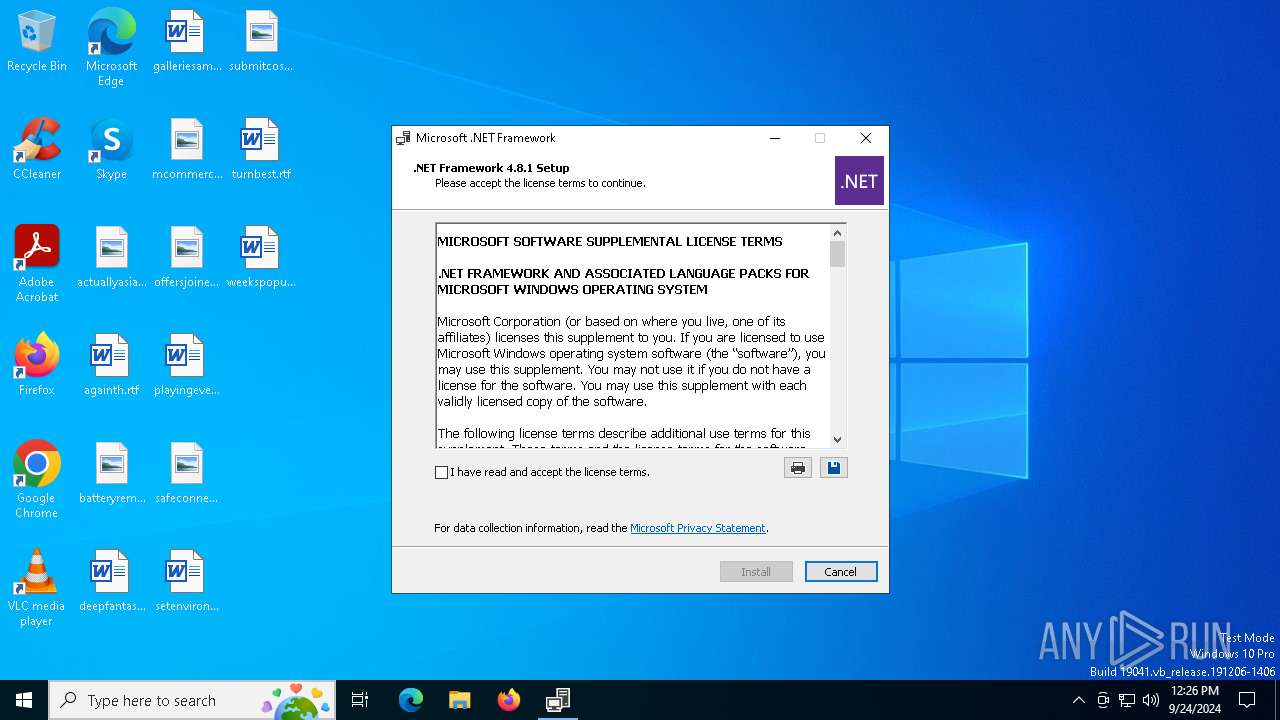
| 6340 | C:\367d6f6f0ca0da64a38956972ef511\\Setup.exe /x86 /x64 /web | C:\367d6f6f0ca0da64a38956972ef511\Setup.exe | NDP481-Web.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 1602 Version: 14.8.9195.0 built by: NET481REL1LAST_B Modules
| |||||||||||||||
| 6636 | SetupUtility.exe /screboot | C:\367d6f6f0ca0da64a38956972ef511\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.8.9195.0 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6740 | SetupUtility.exe /aupause | C:\367d6f6f0ca0da64a38956972ef511\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.8.9195.0 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 822
Read events
3 822
Write events
0
Delete events
0
Modification events
Executable files
29
Suspicious files
6
Text files
80
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\watermark.bmp | image | |
MD5:B0075CEE80173D764C0237E840BA5879 | SHA256:AB18374B3AAB10E5979E080D0410579F9771DB888BA1B80A5D81BA8896E2D33A | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\SplashScreen.bmp | image | |
MD5:BC32088BFAA1C76BA4B56639A2DEC592 | SHA256:B05141DBC71669A7872A8E735E5E43A7F9713D4363B7A97543E1E05DCD7470A7 | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\Graphics\Rotate1.ico | image | |
MD5:9B70C7FA81DCA6D3B992037D0C251D92 | SHA256:18226B9D56D2B1C070A2C606428892773CB00B5B4B95397E79D01DE26685CCD4 | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\header.bmp | image | |
MD5:41C22EFA84CA74F0CE7076EB9A482E38 | SHA256:255025A0D79EF2DAC04BD610363F966EF58328400BF31E1F8915E676478CD750 | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\Graphics\stop.ico | image | |
MD5:7D1BCCCE4F2EE7C824C6304C4A2F9736 | SHA256:BFB0332DF9FA20DEA30F0DB53CEAA389DF2722FD1ACF37F40AF954237717532D | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\Graphics\Rotate4.ico | image | |
MD5:267B198FEF022D3B1D44CCA7FE589373 | SHA256:303989B692A57FE34B47BB2F926B91AC605F288AE6C9479B33EAF15A14EB33AC | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\Graphics\Rotate8.ico | image | |
MD5:E7A252C763CE259F800183FD9DD1F512 | SHA256:FDE052EFE70C27D8023065F0859627FC88BF86E166016E9CB00185C21DE52742 | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\Graphics\Rotate10.ico | image | |
MD5:0CCA04A3468575FDCEFEE9957E32F904 | SHA256:B94E68C711B3B06D9A63C80AD013C7C7BBDB5F8E82CBC866B246FF22D99B03FE | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\Graphics\Rotate6.ico | image | |
MD5:5AC2B8E1A766C204F996D9CE33FB3DB4 | SHA256:EE387D9642DF93E4240361077AF6051C1B7E643C3CF110F43DA42E0EFE29A375 | |||
| 4060 | NDP481-Web.exe | C:\367d6f6f0ca0da64a38956972ef511\Graphics\SysReqMet.ico | image | |
MD5:889472312E724195D7B946EECAEA20C1 | SHA256:C9CA53F83A5CC10F726248D47FF82981B584B3FF62EE591229A8237C11340991 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
18
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4040 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6340 | Setup.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
6340 | Setup.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6340 | Setup.exe | GET | 200 | 2.21.20.133:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
6340 | Setup.exe | GET | 302 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net481Rel1Last_B&plcid=0x409&clcid=0x409&ar=09195.10&sar=amd64&o1=Windows10.0-KB5011048-x64.cab | unknown | — | — | whitelisted |
5376 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4040 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3032 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.79.189.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | JP | whitelisted |
4040 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4040 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6340 | Setup.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
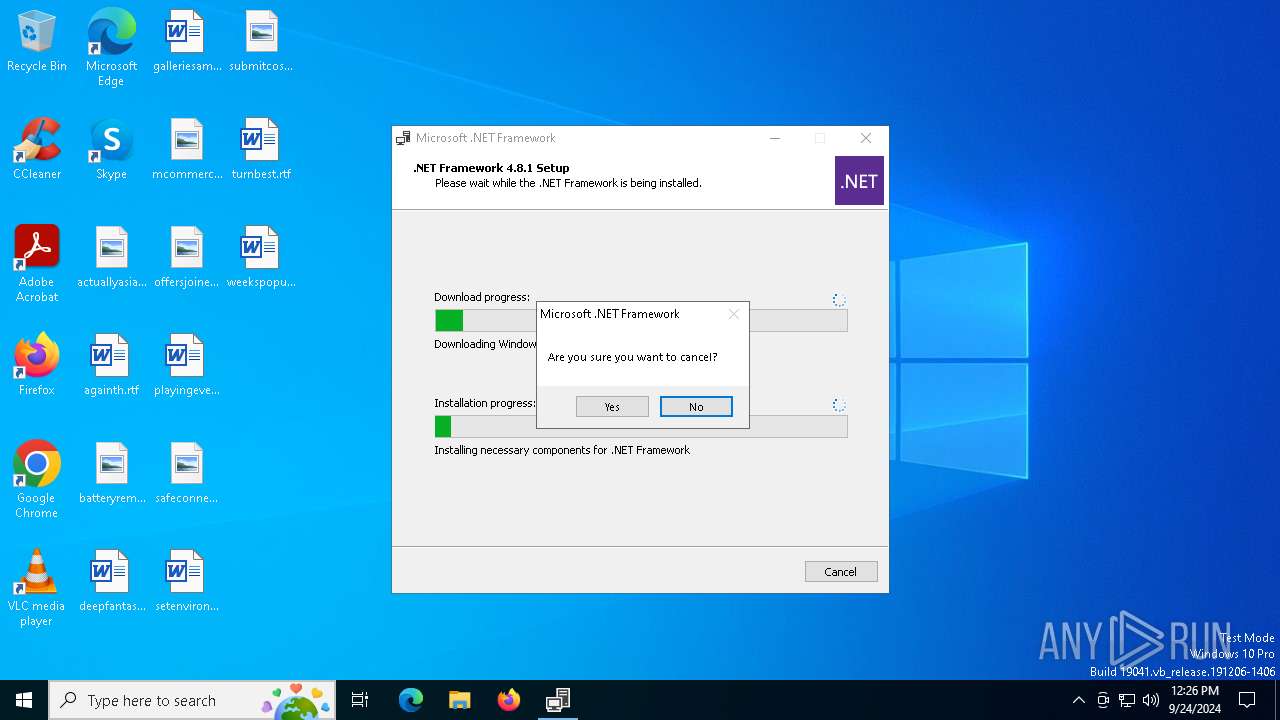
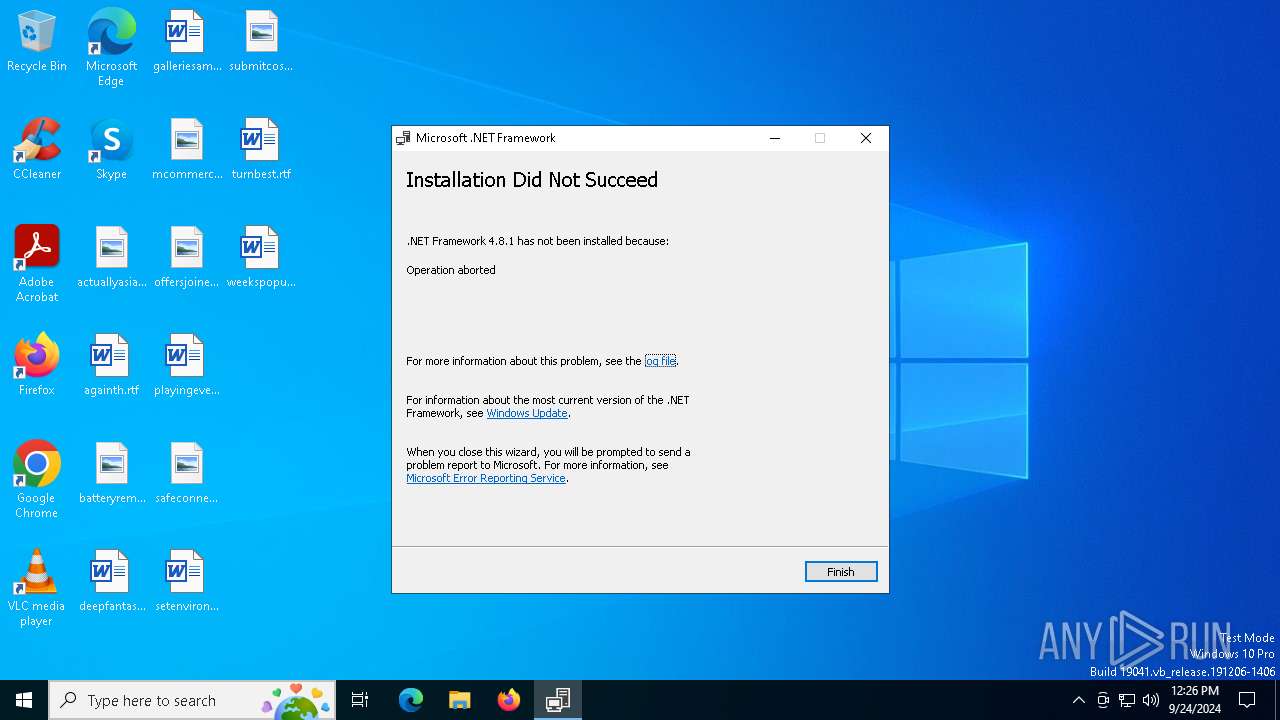
Setup.exe | User cancelled installation.
|