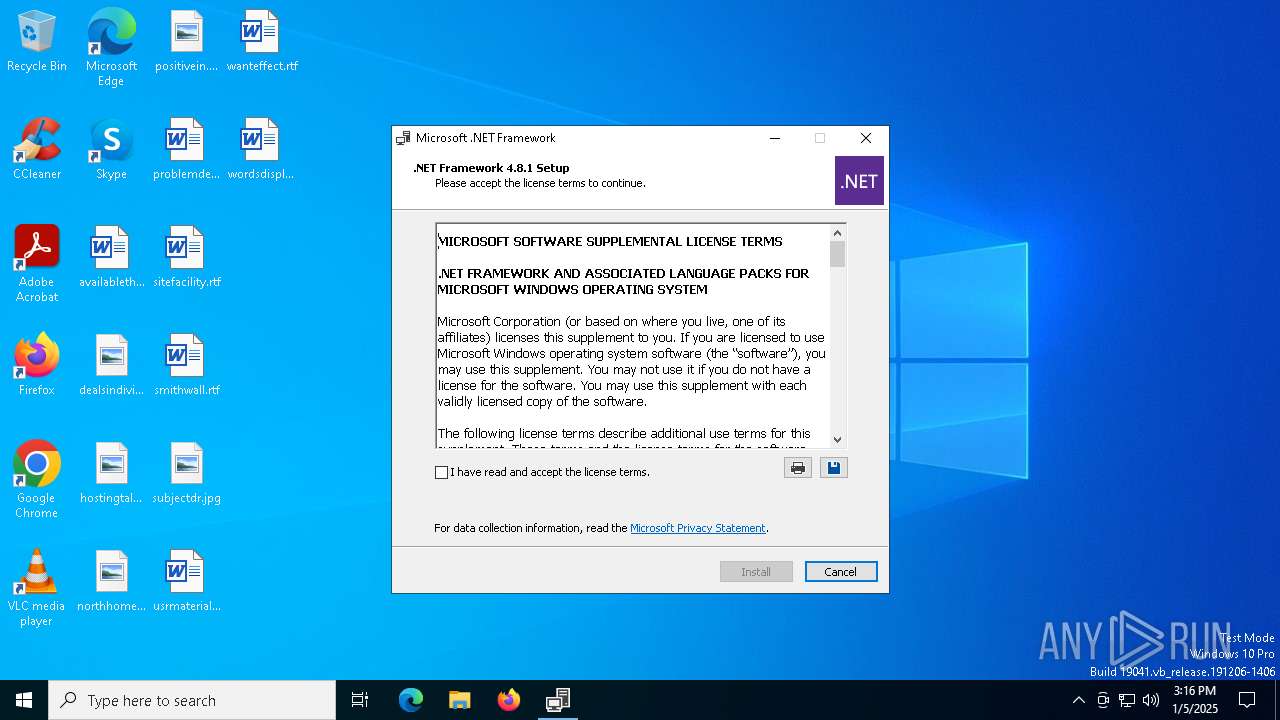
| File name: | NDP481-Web (1).exe |
| Full analysis: | https://app.any.run/tasks/57955a57-196c-45cf-a4a8-415324e7942b |
| Verdict: | Malicious activity |
| Analysis date: | January 05, 2025, 15:15:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 39304CE18D93EEEB6EFA488387ADAED8 |
| SHA1: | 22C974F3865CCE3F0EC385DD9C0B291CA045BC2C |
| SHA256: | 05E9ADA305FD0013A6844E7657F06ED330887093E3DF59C11CB528B86EFA3FBF |
| SSDEEP: | 49152:AIyyfl6pwuJlZ/koJ2LdbHDdEQwWiS4G1RlTnVVi93WTCdgJliViVXHGL4e8VZMM:9yiUmu7xR2LdbHDhwPsRlTVoGTHJlYaR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- NDP481-Web (1).exe (PID: 6280)
Starts a Microsoft application from unusual location
- NDP481-Web (1).exe (PID: 6280)
- NDP481-Web (1).exe (PID: 1580)
Executable content was dropped or overwritten
- NDP481-Web (1).exe (PID: 6280)
Creates file in the systems drive root
- NDP481-Web (1).exe (PID: 6280)
INFO
Reads the computer name
- NDP481-Web (1).exe (PID: 6280)
- Setup.exe (PID: 6404)
The sample compiled with english language support
- NDP481-Web (1).exe (PID: 6280)
Checks supported languages
- NDP481-Web (1).exe (PID: 6280)
- Setup.exe (PID: 6404)
The sample compiled with chinese language support
- NDP481-Web (1).exe (PID: 6280)
Create files in a temporary directory
- NDP481-Web (1).exe (PID: 6280)
- Setup.exe (PID: 6404)
The sample compiled with korean language support
- NDP481-Web (1).exe (PID: 6280)
Reads the machine GUID from the registry
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with japanese language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with portuguese language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with arabic language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with Italian language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with russian language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with swedish language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with polish language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with czech language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with german language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with spanish language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with french language support
- NDP481-Web (1).exe (PID: 6280)
The sample compiled with turkish language support
- NDP481-Web (1).exe (PID: 6280)
Reads CPU info
- Setup.exe (PID: 6404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:07:16 21:09:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 160256 |
| InitializedDataSize: | 29184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x18ee7 |
| OSVersion: | 5.1 |
| ImageVersion: | 10 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.8.9195.10 |
| ProductVersionNumber: | 4.8.9195.10 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft .NET Framework 4.8.1 Setup |
| FileVersion: | 4.8.09195.10 |
| InternalName: | NDP481-Web.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | NDP481-Web.exe |
| ProductName: | Microsoft .NET Framework 4.8.1 |
| ProductVersion: | 4.8.09195.10 |
Total processes
129
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1580 | "C:\Users\admin\AppData\Local\Temp\NDP481-Web (1).exe" | C:\Users\admin\AppData\Local\Temp\NDP481-Web (1).exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.8.1 Setup Exit code: 3221226540 Version: 4.8.09195.10 Modules
| |||||||||||||||
| 6280 | "C:\Users\admin\AppData\Local\Temp\NDP481-Web (1).exe" | C:\Users\admin\AppData\Local\Temp\NDP481-Web (1).exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.8.1 Setup Version: 4.8.09195.10 Modules
| |||||||||||||||
| 6404 | C:\90f0f0fb33aef269aa\\Setup.exe /x86 /x64 /web | C:\90f0f0fb33aef269aa\Setup.exe | — | NDP481-Web (1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Version: 14.8.9195.0 built by: NET481REL1LAST_B Modules
| |||||||||||||||
Total events
223
Read events
223
Write events
0
Delete events
0
Modification events
Executable files
29
Suspicious files
0
Text files
78
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\Graphics\Rotate1.ico | image | |
MD5:9B70C7FA81DCA6D3B992037D0C251D92 | SHA256:18226B9D56D2B1C070A2C606428892773CB00B5B4B95397E79D01DE26685CCD4 | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\Graphics\Rotate2.ico | image | |
MD5:F824905E5501603E6720B784ADD71BDD | SHA256:D15A6F1EEFEFE4F9CD51B7B22E9C7B07C7ACAD72FD53E5F277E6D4E0976036C3 | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\SplashScreen.bmp | image | |
MD5:BC32088BFAA1C76BA4B56639A2DEC592 | SHA256:B05141DBC71669A7872A8E735E5E43A7F9713D4363B7A97543E1E05DCD7470A7 | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\Graphics\Rotate3.ico | image | |
MD5:0ADE6BE0DF29400E5534AA71ABFA03F6 | SHA256:C2F6FAA18B16F728AE5536D5992CC76A4B83530A1EA74B9D11BEBDF871CF3B4E | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\watermark.bmp | image | |
MD5:B0075CEE80173D764C0237E840BA5879 | SHA256:AB18374B3AAB10E5979E080D0410579F9771DB888BA1B80A5D81BA8896E2D33A | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\DisplayIcon.ico | image | |
MD5:F9657D290048E169FFABBBB9C7412BE0 | SHA256:B74AD253B9B8F9FCADE725336509143828EE739CC2B24782BE3ECFF26F229160 | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\header.bmp | image | |
MD5:41C22EFA84CA74F0CE7076EB9A482E38 | SHA256:255025A0D79EF2DAC04BD610363F966EF58328400BF31E1F8915E676478CD750 | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\Graphics\Rotate10.ico | image | |
MD5:0CCA04A3468575FDCEFEE9957E32F904 | SHA256:B94E68C711B3B06D9A63C80AD013C7C7BBDB5F8E82CBC866B246FF22D99B03FE | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\Graphics\Rotate5.ico | image | |
MD5:25F0D572761CB610BDAD6DD980C46CC7 | SHA256:CE2AFC0AA52B3D459D6D8D7C551F7B8FBF323E2260326908C37A13F21FEE423E | |||
| 6280 | NDP481-Web (1).exe | C:\90f0f0fb33aef269aa\Graphics\Print.ico | image | |
MD5:D39BAD9DDA7B91613CB29B6BD55F0901 | SHA256:D80FFEB020927F047C11FC4D9F34F985E0C7E5DFEA9FB23F2BC134874070E4E6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6876 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6876 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5432 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3884 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |