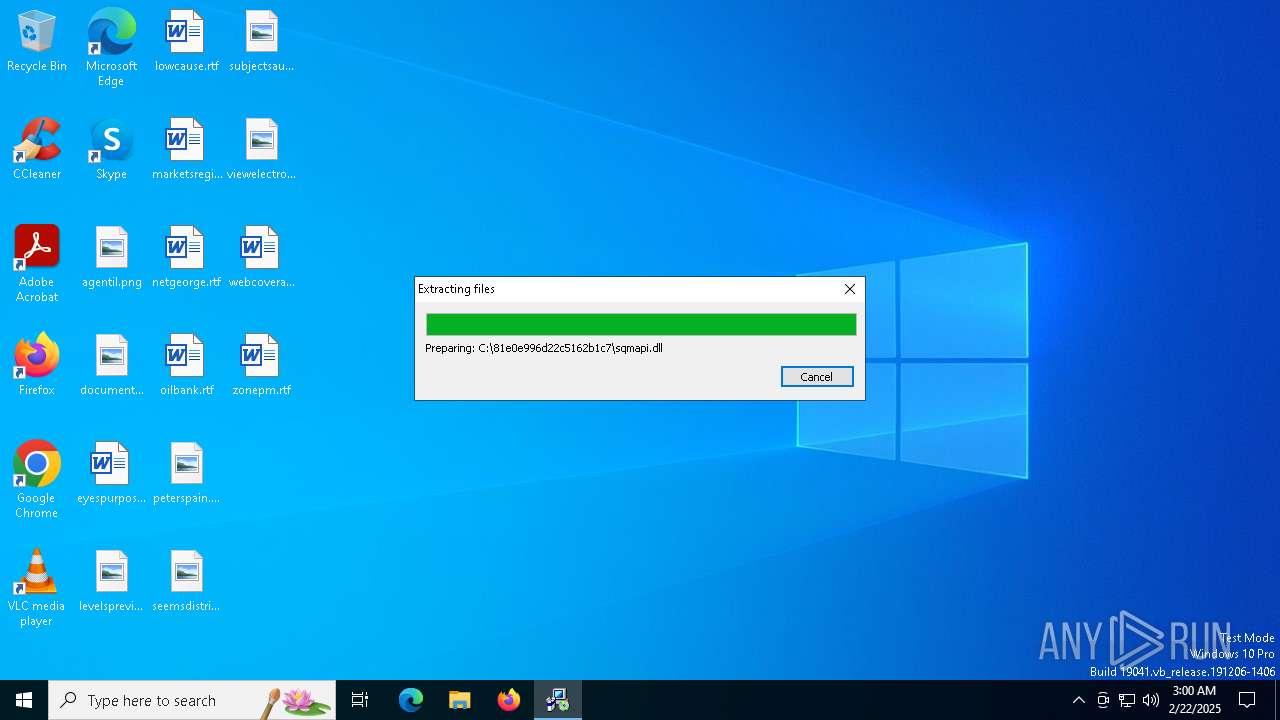
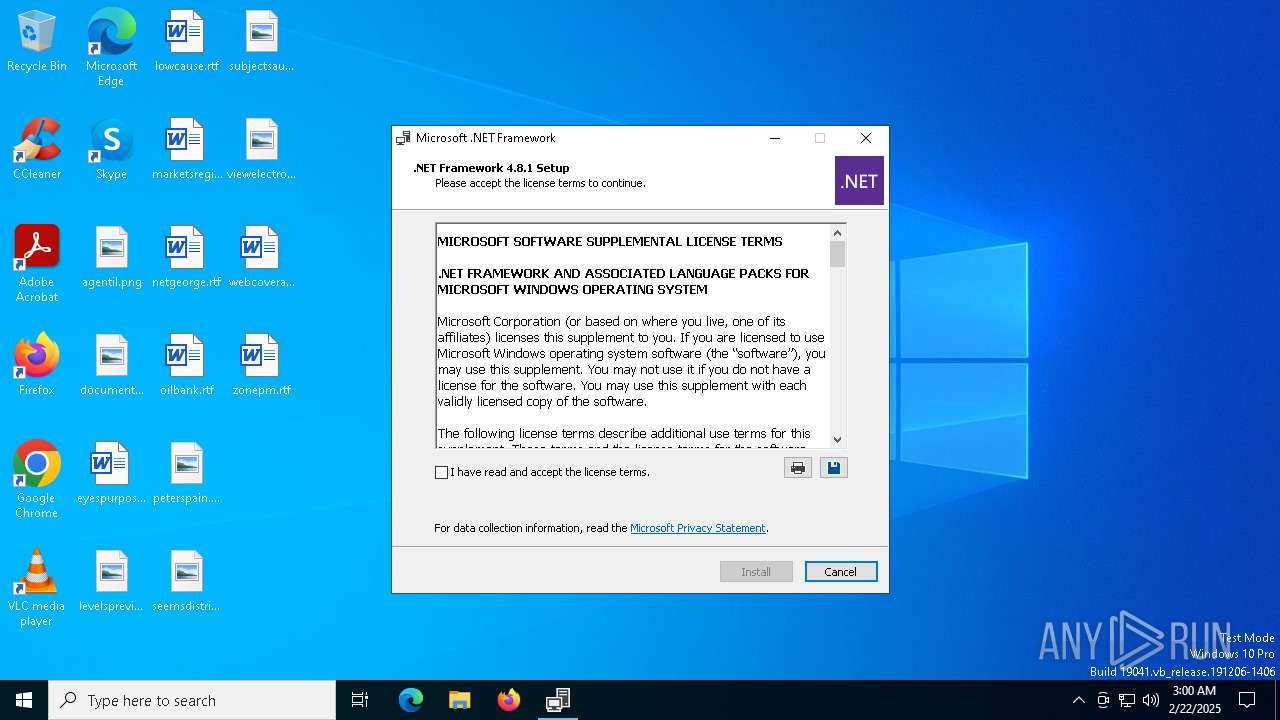
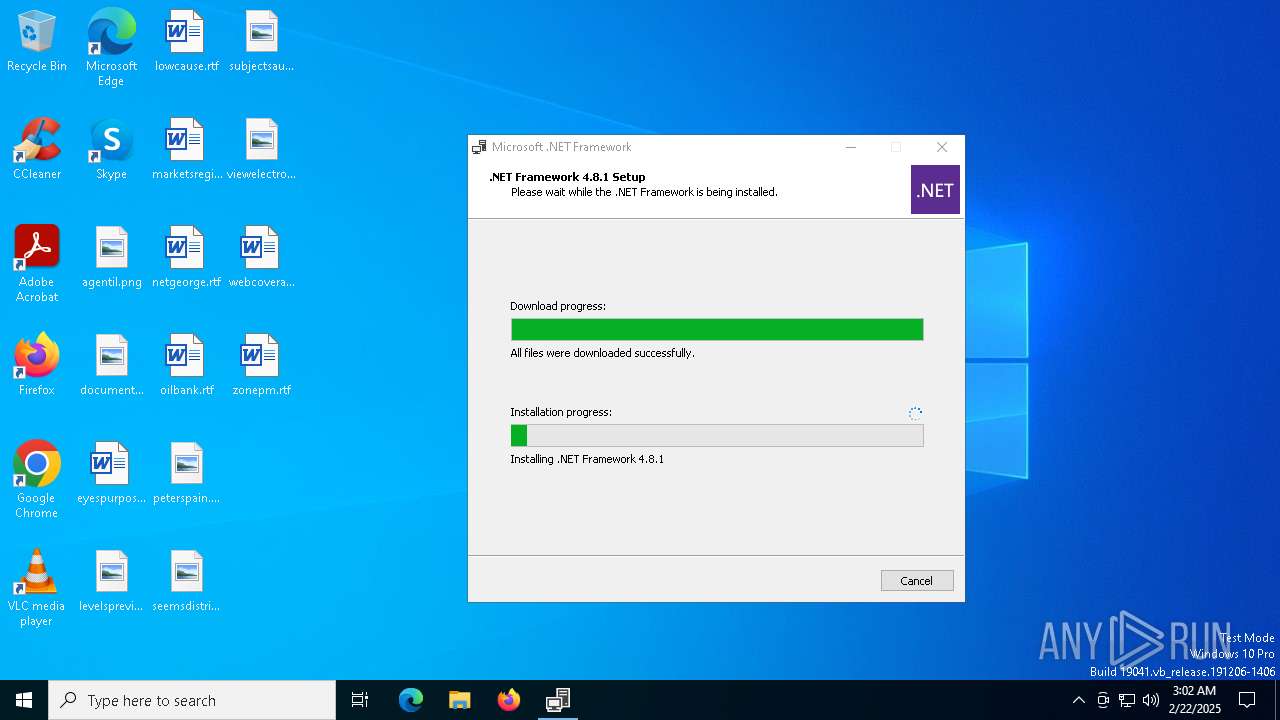
| File name: | NDP481-Web.exe |
| Full analysis: | https://app.any.run/tasks/1c9b3ee1-cda2-4269-ad25-1c845e6dd3af |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2025, 03:00:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 39304CE18D93EEEB6EFA488387ADAED8 |
| SHA1: | 22C974F3865CCE3F0EC385DD9C0B291CA045BC2C |
| SHA256: | 05E9ADA305FD0013A6844E7657F06ED330887093E3DF59C11CB528B86EFA3FBF |
| SSDEEP: | 49152:AIyyfl6pwuJlZ/koJ2LdbHDdEQwWiS4G1RlTnVVi93WTCdgJliViVXHGL4e8VZMM:9yiUmu7xR2LdbHDhwPsRlTVoGTHJlYaR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts a Microsoft application from unusual location
- NDP481-Web.exe (PID: 6548)
- NDP481-Web.exe (PID: 6704)
- DismHost.exe (PID: 6724)
Executable content was dropped or overwritten
- NDP481-Web.exe (PID: 6704)
- Dism.exe (PID: 5432)
- TiWorker.exe (PID: 5732)
Creates file in the systems drive root
- NDP481-Web.exe (PID: 6704)
Checks Windows Trust Settings
- Setup.exe (PID: 6800)
Process drops legitimate windows executable
- NDP481-Web.exe (PID: 6704)
- TiWorker.exe (PID: 5732)
Executes as Windows Service
- VSSVC.exe (PID: 2796)
The process creates files with name similar to system file names
- Dism.exe (PID: 5432)
Searches for installed software
- TiWorker.exe (PID: 5732)
The process drops C-runtime libraries
- TiWorker.exe (PID: 5732)
Reads security settings of Internet Explorer
- Setup.exe (PID: 6800)
INFO
The sample compiled with english language support
- NDP481-Web.exe (PID: 6704)
- Dism.exe (PID: 5432)
- TiWorker.exe (PID: 5732)
Reads the computer name
- NDP481-Web.exe (PID: 6704)
- Setup.exe (PID: 6800)
- SetupUtility.exe (PID: 6300)
- SetupUtility.exe (PID: 6496)
- DismHost.exe (PID: 6724)
Reads the machine GUID from the registry
- NDP481-Web.exe (PID: 6704)
- Setup.exe (PID: 6800)
The sample compiled with japanese language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with chinese language support
- NDP481-Web.exe (PID: 6704)
Create files in a temporary directory
- NDP481-Web.exe (PID: 6704)
- Setup.exe (PID: 6800)
- SetupUtility.exe (PID: 6300)
- Dism.exe (PID: 5432)
- TiWorker.exe (PID: 5732)
The sample compiled with czech language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with korean language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with arabic language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with russian language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with polish language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with portuguese language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with Italian language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with german language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with spanish language support
- NDP481-Web.exe (PID: 6704)
The sample compiled with turkish language support
- NDP481-Web.exe (PID: 6704)
Creates files or folders in the user directory
- Setup.exe (PID: 6800)
Checks supported languages
- Setup.exe (PID: 6800)
- NDP481-Web.exe (PID: 6704)
- SetupUtility.exe (PID: 6300)
- DismHost.exe (PID: 6724)
- SetupUtility.exe (PID: 6496)
Reads CPU info
- Setup.exe (PID: 6800)
Checks proxy server information
- Setup.exe (PID: 6800)
Reads the software policy settings
- Setup.exe (PID: 6800)
- TiWorker.exe (PID: 5732)
The sample compiled with swedish language support
- NDP481-Web.exe (PID: 6704)
Reads Environment values
- DismHost.exe (PID: 6724)
Manages system restore points
- SrTasks.exe (PID: 6340)
Manual execution by a user
- mspaint.exe (PID: 6576)
The sample compiled with french language support
- NDP481-Web.exe (PID: 6704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:07:16 21:09:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 160256 |
| InitializedDataSize: | 29184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x18ee7 |
| OSVersion: | 5.1 |
| ImageVersion: | 10 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.8.9195.10 |
| ProductVersionNumber: | 4.8.9195.10 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft .NET Framework 4.8.1 Setup |
| FileVersion: | 4.8.09195.10 |
| InternalName: | NDP481-Web.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | NDP481-Web.exe |
| ProductName: | Microsoft .NET Framework 4.8.1 |
| ProductVersion: | 4.8.09195.10 |
Total processes
146
Monitored processes
14
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2796 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3772 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5432 | dism.exe /quiet /norestart /online /add-package /packagepath:"C:\81e0e996d22c5162b1c7\Windows10.0-KB5011048-x64.cab" | C:\Windows\System32\Dism.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5732 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Dism.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6300 | SetupUtility.exe /aupause | C:\81e0e996d22c5162b1c7\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.8.9195.0 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6340 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | TiWorker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6496 | SetupUtility.exe /screboot | C:\81e0e996d22c5162b1c7\SetupUtility.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.5 Setup Exit code: 0 Version: 14.8.9195.0 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6548 | "C:\Users\admin\AppData\Local\Temp\NDP481-Web.exe" | C:\Users\admin\AppData\Local\Temp\NDP481-Web.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.8.1 Setup Exit code: 3221226540 Version: 4.8.09195.10 Modules
| |||||||||||||||
Total events
26 697
Read events
26 454
Write events
219
Delete events
24
Modification events
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31163606 | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 162652246 | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS\ServicingStackVersions |
| Operation: | write | Name: | 10.0.19041.3989 (WinBuild.160101.0800) |
Value: 2025/2/22:3:1:18.667 10.0.19041.3989 (WinBuild.160101.0800) | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingXmlIdentifier |
Value: | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PoqexecFailure |
Value: | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | ExecutionState |
Value: | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | RepairTransactionPended |
Value: | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqTime |
Value: 0 | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqCount |
Value: 0 | |||
| (PID) Process: | (5732) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | PoqTime |
Value: 0 | |||
Executable files
544
Suspicious files
18
Text files
293
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\Graphics\Setup.ico | image | |
MD5:6125F32AA97772AFDFF2649BD403419B | SHA256:A0C7B4B17A69775E1D94123DFCEEC824744901D55B463BA9DCA9301088F12EA5 | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\header.bmp | image | |
MD5:41C22EFA84CA74F0CE7076EB9A482E38 | SHA256:255025A0D79EF2DAC04BD610363F966EF58328400BF31E1F8915E676478CD750 | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\Graphics\Rotate10.ico | image | |
MD5:0CCA04A3468575FDCEFEE9957E32F904 | SHA256:B94E68C711B3B06D9A63C80AD013C7C7BBDB5F8E82CBC866B246FF22D99B03FE | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\Graphics\Rotate2.ico | image | |
MD5:F824905E5501603E6720B784ADD71BDD | SHA256:D15A6F1EEFEFE4F9CD51B7B22E9C7B07C7ACAD72FD53E5F277E6D4E0976036C3 | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\Graphics\Rotate8.ico | image | |
MD5:E7A252C763CE259F800183FD9DD1F512 | SHA256:FDE052EFE70C27D8023065F0859627FC88BF86E166016E9CB00185C21DE52742 | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\watermark.bmp | image | |
MD5:B0075CEE80173D764C0237E840BA5879 | SHA256:AB18374B3AAB10E5979E080D0410579F9771DB888BA1B80A5D81BA8896E2D33A | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\SplashScreen.bmp | image | |
MD5:BC32088BFAA1C76BA4B56639A2DEC592 | SHA256:B05141DBC71669A7872A8E735E5E43A7F9713D4363B7A97543E1E05DCD7470A7 | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\Graphics\Save.ico | image | |
MD5:C66BBE8F84496EF85F7AF6BED5212CEC | SHA256:1372C7F132595DDAD210C617E44FEDFF7A990A9E8974CC534CA80D897DD15ABD | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\Graphics\Rotate4.ico | image | |
MD5:267B198FEF022D3B1D44CCA7FE589373 | SHA256:303989B692A57FE34B47BB2F926B91AC605F288AE6C9479B33EAF15A14EB33AC | |||
| 6704 | NDP481-Web.exe | C:\81e0e996d22c5162b1c7\Graphics\Rotate9.ico | image | |
MD5:8853DA1F831CAE28E59D45F5E51885AC | SHA256:0203C7D678464641C016DC3D658ABA0A68F20B9A141D6E3EE1820C5B8B6401DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
44
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4328 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6800 | Setup.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6800 | Setup.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6684 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4328 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6800 | Setup.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5880 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4328 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4328 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=5432 TID=6776 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=5432 TID=6776 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5432 TID=6776 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5432 TID=6776 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5432 TID=6776 Loading Provider from location C:\WINDOWS\system32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5432 TID=6776 Connecting to the provider located at C:\WINDOWS\system32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |