| File name: | Co-Skip-Setup.exe |
| Full analysis: | https://app.any.run/tasks/4956a1b9-a5cb-4433-b425-d88913601c29 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2025, 08:05:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | 08ACC52CB06D4C65AF25F4974CA6BB3C |
| SHA1: | 66DAB737C4AA21C6418E3C797DD6C12606646554 |
| SHA256: | 05E583986A89C6EA8CDC6AEF6D07DC12DF628916F266CC7E9DDA4582234C4C12 |
| SSDEEP: | 196608:Z+P2Hirbekz9QdTPNy6YYgwC/4PP7Er8Fav:Z+uHi39RGPNpYYlC/4rlUv |
MALICIOUS
Changes Windows Defender settings
- Co-Skip-Setup.tmp (PID: 2580)
Adds path to the Windows Defender exclusion list
- Co-Skip-Setup.tmp (PID: 2580)
Changes powershell execution policy (Bypass)
- Co-Skip-Setup.tmp (PID: 2580)
Bypass execution policy to execute commands
- powershell.exe (PID: 4844)
SUSPICIOUS
Executable content was dropped or overwritten
- Co-Skip-Setup.exe (PID: 2292)
- Co-Skip-Setup.exe (PID: 7064)
- Co-Skip-Setup.tmp (PID: 2580)
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 892)
Reads security settings of Internet Explorer
- Co-Skip-Setup.tmp (PID: 2492)
- Co-Skip-Setup.tmp (PID: 2580)
- Co-Skip-Updater.exe (PID: 888)
Reads the Windows owner or organization settings
- Co-Skip-Setup.tmp (PID: 2580)
PSEXEC has been detected
- Co-Skip-Setup.tmp (PID: 2580)
Starts POWERSHELL.EXE for commands execution
- Co-Skip-Setup.tmp (PID: 2580)
Script adds exclusion path to Windows Defender
- Co-Skip-Setup.tmp (PID: 2580)
The process bypasses the loading of PowerShell profile settings
- Co-Skip-Setup.tmp (PID: 2580)
The process drops C-runtime libraries
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 892)
Reads the BIOS version
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 888)
- Co-Skip-Updater.exe (PID: 892)
- Co-Skip-Updater.exe (PID: 5236)
Process drops legitimate windows executable
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 892)
Process drops python dynamic module
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 892)
Application launched itself
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 888)
- Co-Skip-Updater.exe (PID: 892)
Loads Python modules
- Co-Skip-Updater.exe (PID: 888)
- Co-Skip-Updater.exe (PID: 5236)
Reads the date of Windows installation
- Co-Skip-Updater.exe (PID: 888)
INFO
Checks supported languages
- Co-Skip-Setup.exe (PID: 2292)
- Co-Skip-Setup.exe (PID: 7064)
- Co-Skip-Setup.tmp (PID: 2492)
- Co-Skip-Setup.tmp (PID: 2580)
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 888)
- Co-Skip-Updater.exe (PID: 892)
- Co-Skip-Updater.exe (PID: 5236)
Reads the computer name
- Co-Skip-Setup.tmp (PID: 2492)
- Co-Skip-Setup.tmp (PID: 2580)
- Co-Skip-Setup.exe (PID: 7064)
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 888)
- Co-Skip-Updater.exe (PID: 892)
- Co-Skip-Updater.exe (PID: 5236)
Create files in a temporary directory
- Co-Skip-Setup.exe (PID: 7064)
- Co-Skip-Setup.tmp (PID: 2580)
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 892)
- Co-Skip-Setup.exe (PID: 2292)
Process checks computer location settings
- Co-Skip-Setup.tmp (PID: 2492)
- Co-Skip-Setup.tmp (PID: 2580)
- Co-Skip-Updater.exe (PID: 888)
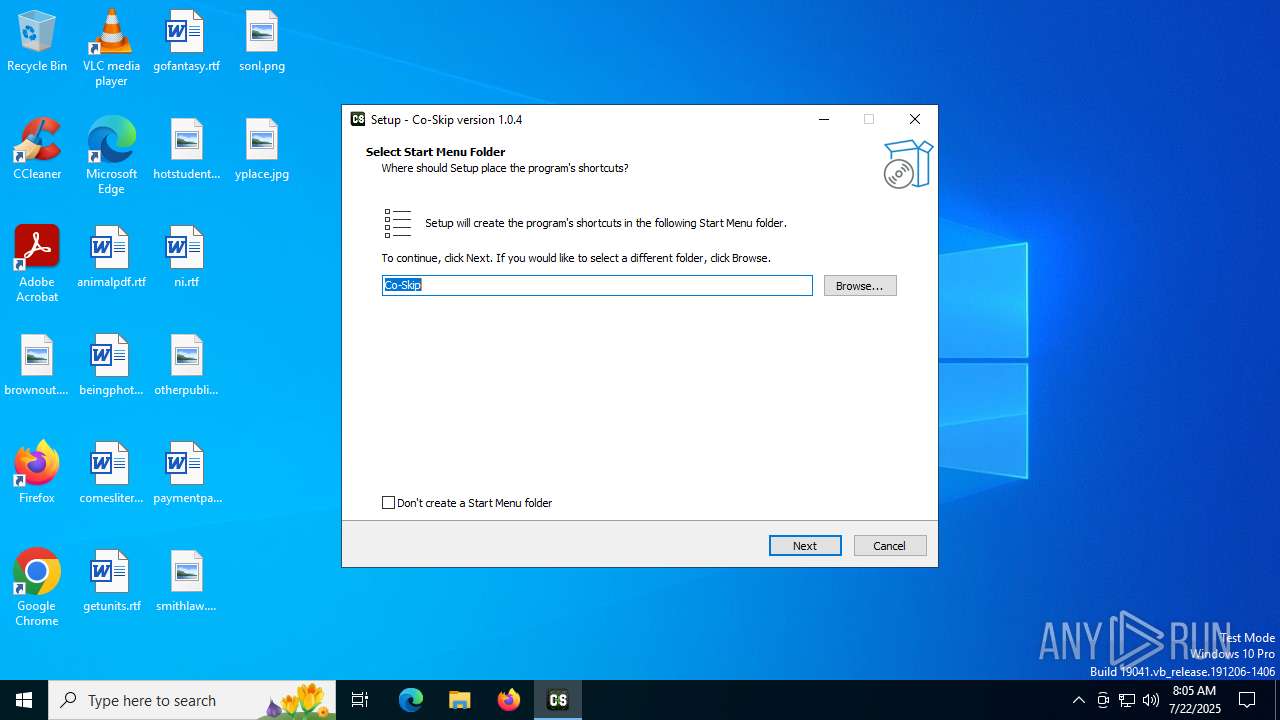
Creates a software uninstall entry
- Co-Skip-Setup.tmp (PID: 2580)
Compiled with Borland Delphi (YARA)
- Co-Skip-Setup.exe (PID: 2292)
- Co-Skip-Setup.tmp (PID: 2492)
Detects InnoSetup installer (YARA)
- Co-Skip-Setup.exe (PID: 2292)
- Co-Skip-Setup.tmp (PID: 2492)
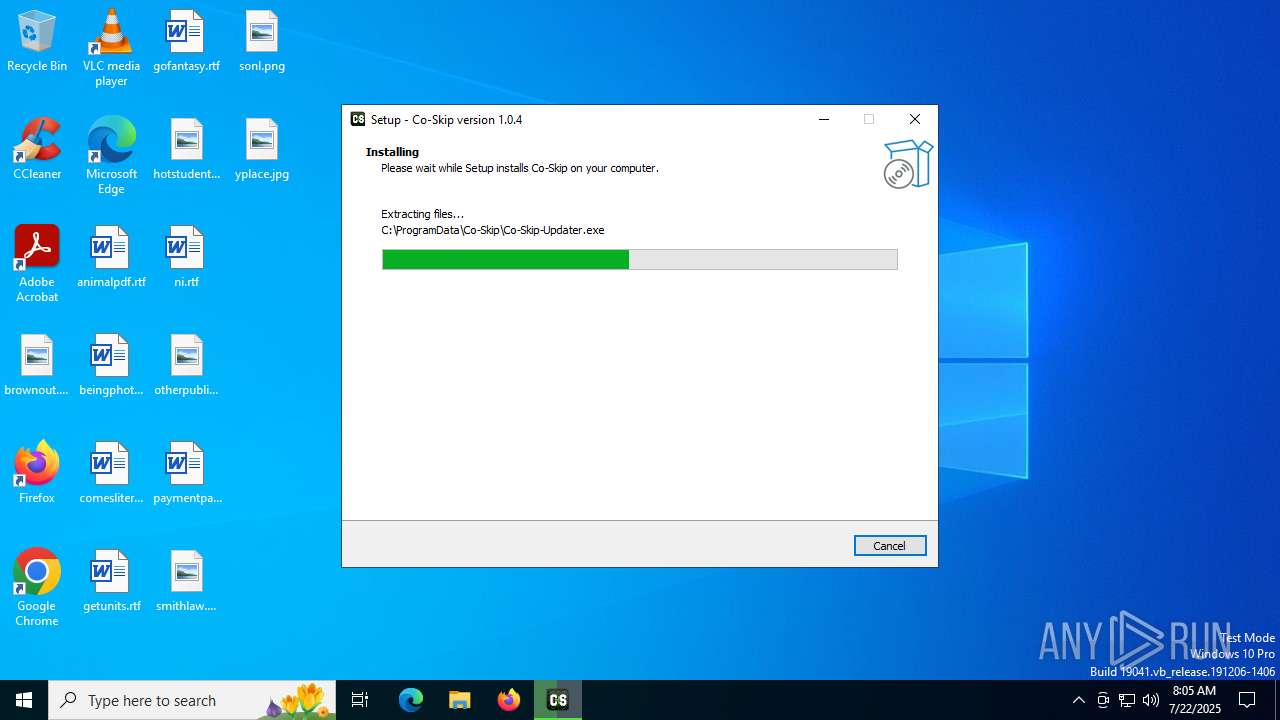
Creates files in the program directory
- Co-Skip-Setup.tmp (PID: 2580)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4844)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4844)
Manual execution by a user
- Co-Skip-Updater.exe (PID: 1944)
The sample compiled with english language support
- Co-Skip-Updater.exe (PID: 1944)
- Co-Skip-Updater.exe (PID: 892)
Process checks whether UAC notifications are on
- Co-Skip-Updater.exe (PID: 892)
- Co-Skip-Updater.exe (PID: 5236)
Checks proxy server information
- Co-Skip-Updater.exe (PID: 5236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:13 06:55:45+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 704512 |
| InitializedDataSize: | 240128 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xacfe0 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Co-Skip |
| FileDescription: | Co-Skip Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Co-Skip |
| ProductVersion: | 1.0.4 |
Total processes
151
Monitored processes
13
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | "C:\ProgramData\Co-Skip\Co-Skip-Updater.exe" | C:\ProgramData\Co-Skip\Co-Skip-Updater.exe | — | Co-Skip-Updater.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 892 | "C:\ProgramData\Co-Skip\Co-Skip-Updater.exe" | C:\ProgramData\Co-Skip\Co-Skip-Updater.exe | Co-Skip-Updater.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1944 | "C:\ProgramData\Co-Skip\Co-Skip-Updater.exe" | C:\ProgramData\Co-Skip\Co-Skip-Updater.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2292 | "C:\Users\admin\AppData\Local\Temp\Co-Skip-Setup.exe" | C:\Users\admin\AppData\Local\Temp\Co-Skip-Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Co-Skip Integrity Level: MEDIUM Description: Co-Skip Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2492 | "C:\Users\admin\AppData\Local\Temp\is-B8LD0.tmp\Co-Skip-Setup.tmp" /SL5="$9035A,14199915,945664,C:\Users\admin\AppData\Local\Temp\Co-Skip-Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-B8LD0.tmp\Co-Skip-Setup.tmp | — | Co-Skip-Setup.exe | |||||||||||
User: admin Company: Co-Skip Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\AppData\Local\Temp\is-G6RVE.tmp\Co-Skip-Setup.tmp" /SL5="$802DC,14199915,945664,C:\Users\admin\AppData\Local\Temp\Co-Skip-Setup.exe" /SPAWNWND=$90374 /NOTIFYWND=$9035A | C:\Users\admin\AppData\Local\Temp\is-G6RVE.tmp\Co-Skip-Setup.tmp | Co-Skip-Setup.exe | ||||||||||||
User: admin Company: Co-Skip Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Co-Skip-Updater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Co-Skip-Updater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -ExecutionPolicy Bypass -Command "Add-MpPreference -ExclusionPath 'C:\ProgramData\Co-Skip'" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | Co-Skip-Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | "C:\ProgramData\Co-Skip\Co-Skip-Updater.exe" | C:\ProgramData\Co-Skip\Co-Skip-Updater.exe | Co-Skip-Updater.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
Total events
7 089
Read events
7 062
Write events
27
Delete events
0
Modification events
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Co-Skip_is1 |
| Operation: | write | Name: | InstallDate |
Value: 20250722 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Co-Skip_is1 |
| Operation: | write | Name: | MajorVersion |
Value: 1 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Co-Skip_is1 |
| Operation: | write | Name: | MinorVersion |
Value: 0 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Co-Skip_is1 |
| Operation: | write | Name: | VersionMajor |
Value: 1 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Co-Skip_is1 |
| Operation: | write | Name: | VersionMinor |
Value: 0 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Co-Skip_is1 |
| Operation: | write | Name: | EstimatedSize |
Value: 16764 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsExec |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\PsExec64 |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Co-Skip_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.4.2 | |||
| (PID) Process: | (2580) Co-Skip-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Co-Skip_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\ProgramData\Co-Skip | |||
Executable files
135
Suspicious files
3
Text files
8
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7064 | Co-Skip-Setup.exe | C:\Users\admin\AppData\Local\Temp\is-G6RVE.tmp\Co-Skip-Setup.tmp | executable | |
MD5:E4AC724C01A0B574100DB256804D11BF | SHA256:409505018D12D0E442DF147414F7D6ABBB25E6FBFB9EC9AC9B5664491A0F7D4B | |||
| 2292 | Co-Skip-Setup.exe | C:\Users\admin\AppData\Local\Temp\is-B8LD0.tmp\Co-Skip-Setup.tmp | executable | |
MD5:E4AC724C01A0B574100DB256804D11BF | SHA256:409505018D12D0E442DF147414F7D6ABBB25E6FBFB9EC9AC9B5664491A0F7D4B | |||
| 2580 | Co-Skip-Setup.tmp | C:\ProgramData\Co-Skip\icon.ico | image | |
MD5:7E074328A012704BA88ED8FC381A23BC | SHA256:82AA79749ED3633159A24A46316625F5F3A9B7D05FFB9ADB4127DCBE552C296A | |||
| 2580 | Co-Skip-Setup.tmp | C:\ProgramData\Co-Skip\unins000.exe | executable | |
MD5:10BFBD594D47575231BCC938E53C28AC | SHA256:5A517562ABEE486E890B0C425E607F8244BFC61F972AD62F79C724C7F51EA1A6 | |||
| 2580 | Co-Skip-Setup.tmp | C:\Users\Public\Desktop\Co-Skip.lnk | lnk | |
MD5:B23D005050A9F6F8C3BDF2484E2B6EBE | SHA256:69921D54E9EDBB2E482B0D2D6AB7500E111B612335A627DA082B5A2341E6E7C4 | |||
| 2580 | Co-Skip-Setup.tmp | C:\ProgramData\Co-Skip\Co-Skip-Updater.exe | executable | |
MD5:78098ED0CE8F944EBFCEA50BEC0B0A19 | SHA256:857A22F8D50288B847D730D15CD3E76AF93A12BA2B849F71699E211ACFD4A244 | |||
| 2580 | Co-Skip-Setup.tmp | C:\ProgramData\Co-Skip\is-CA09D.tmp | image | |
MD5:7E074328A012704BA88ED8FC381A23BC | SHA256:82AA79749ED3633159A24A46316625F5F3A9B7D05FFB9ADB4127DCBE552C296A | |||
| 2580 | Co-Skip-Setup.tmp | C:\ProgramData\Co-Skip\is-PECTJ.tmp | executable | |
MD5:10BFBD594D47575231BCC938E53C28AC | SHA256:5A517562ABEE486E890B0C425E607F8244BFC61F972AD62F79C724C7F51EA1A6 | |||
| 2580 | Co-Skip-Setup.tmp | C:\ProgramData\Co-Skip\is-2473M.tmp | executable | |
MD5:78098ED0CE8F944EBFCEA50BEC0B0A19 | SHA256:857A22F8D50288B847D730D15CD3E76AF93A12BA2B849F71699E211ACFD4A244 | |||
| 4844 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2iu3cgop.3xv.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5644 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5368 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1964 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5644 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
co-skip-server.onrender.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Host dynamic web apps service (.onrender .com) |
2200 | svchost.exe | Misc activity | ET INFO DNS Query to Online Application Hosting Domain (onrender .com) |
5236 | Co-Skip-Updater.exe | Misc activity | ET INFO Observed Online Application Hosting Domain (onrender .com in TLS SNI) |