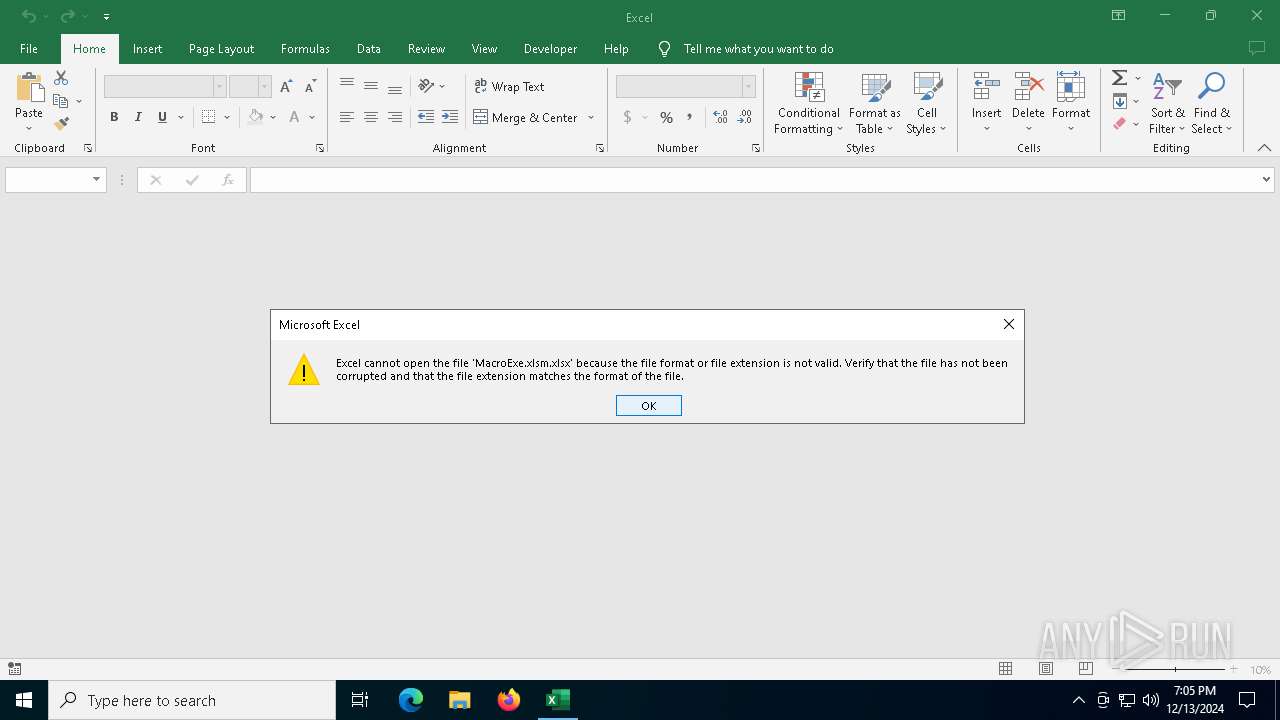
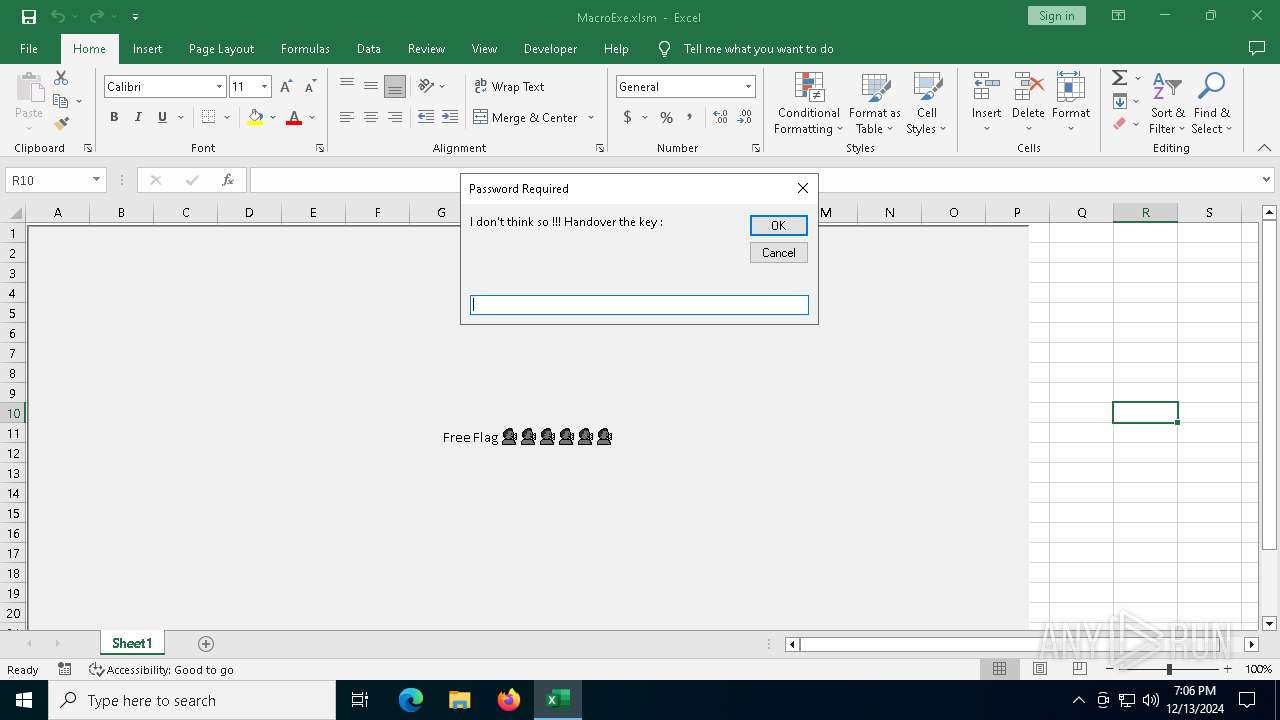
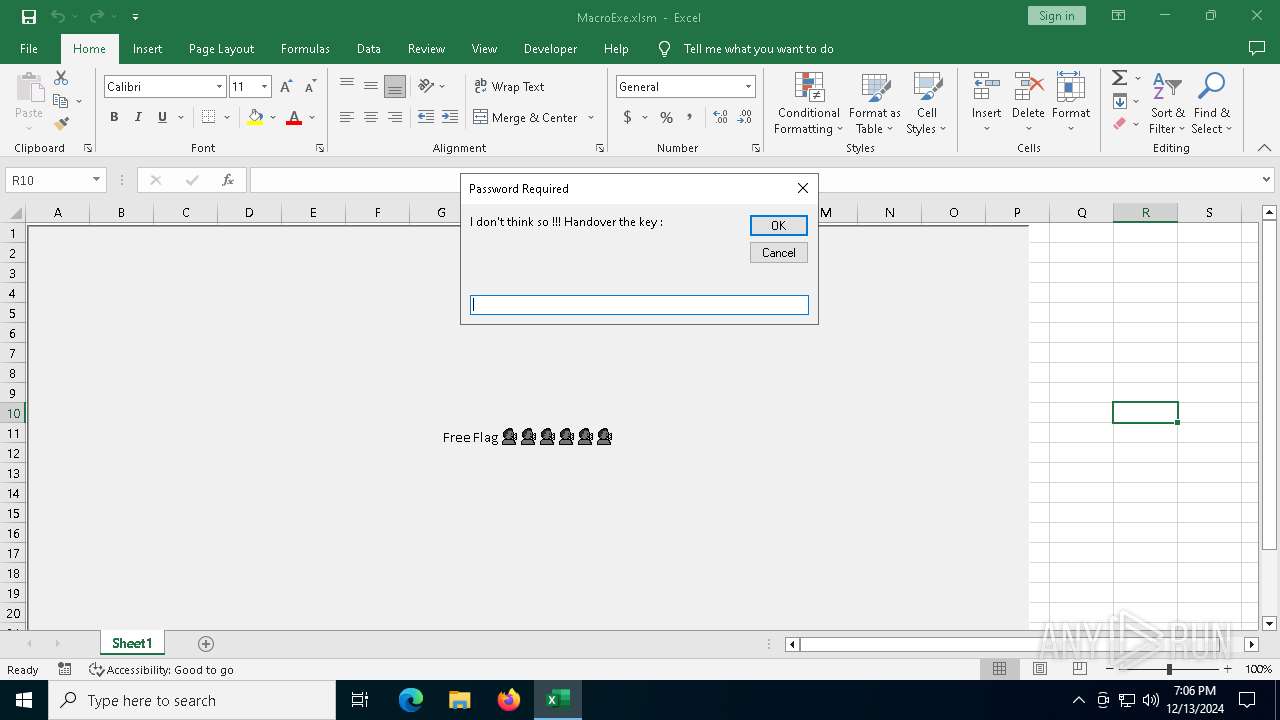
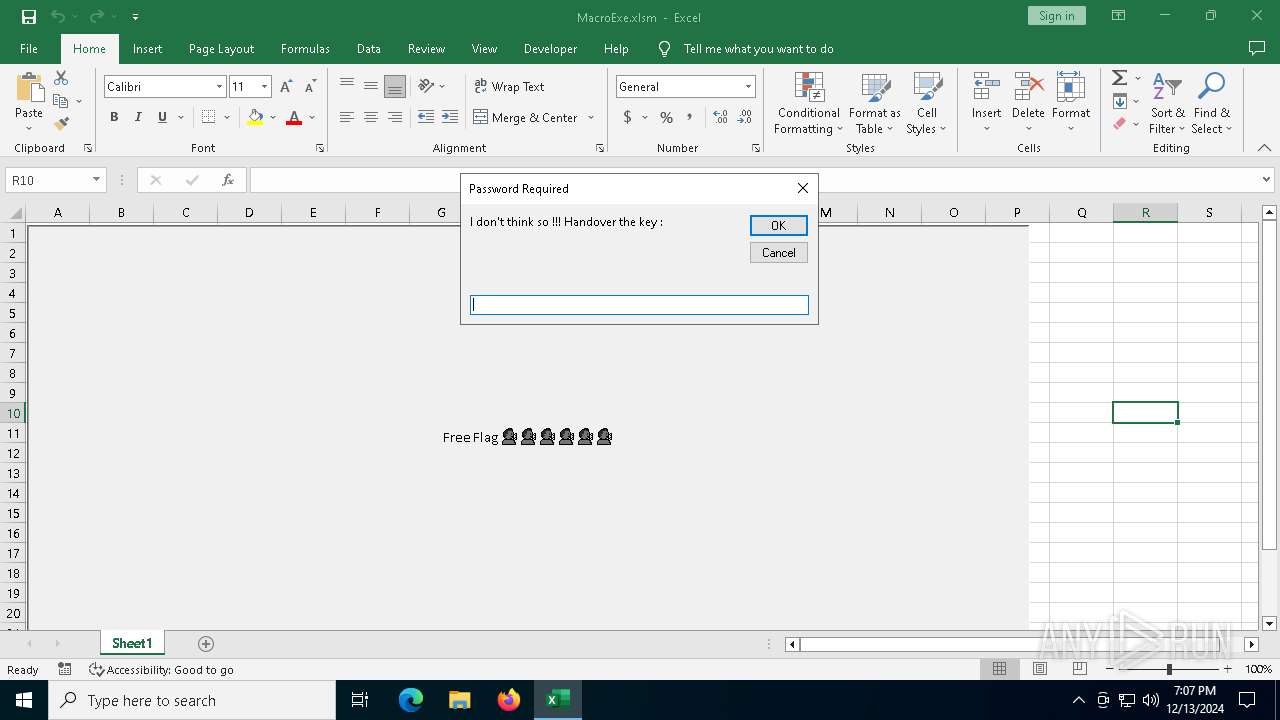
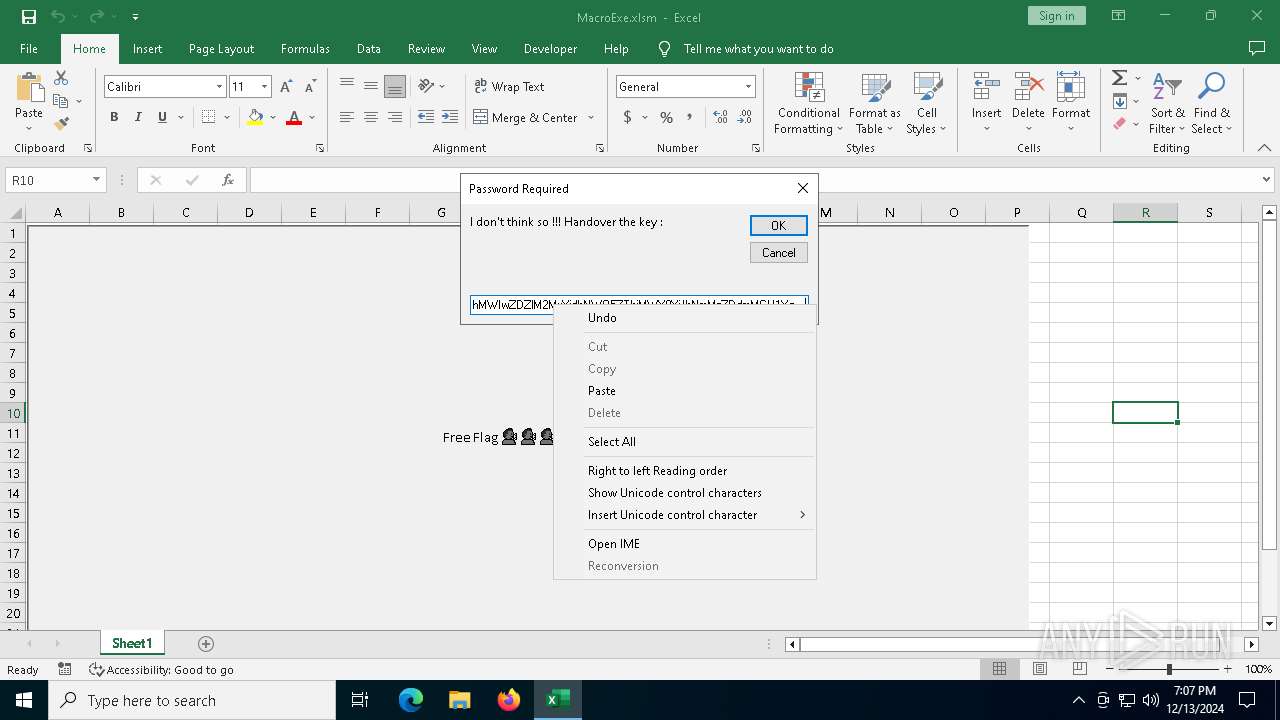
| File name: | MacroExe.xlsm |
| Full analysis: | https://app.any.run/tasks/e6cbbce3-faa1-4f3a-a969-6a3b127bb50e |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 19:05:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 4062325D51A3A8CD4286B25A90EBA9F3 |
| SHA1: | 6788B53F8C01CF96DA76A97990F6B4658318A281 |
| SHA256: | 05C61B17AB21CC5222D3EDFEBE467A930724ED5C64D0AE72396E39A58D3B2E37 |
| SSDEEP: | 3072:OUXvui7IZFBJY4wvgOMDbHHV+hG+Y0co9H9ZG9y2vaac5I:5XGZFXJwvqDzH6G+tco9HTG9y2yI |
MALICIOUS
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 4668)
Detects the decoding of a binary file from Base64 (SCRIPT)
- EXCEL.EXE (PID: 4668)
Uses base64 encoding (SCRIPT)
- EXCEL.EXE (PID: 4668)
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 4668)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 4668)
Unusual execution from MS Office
- EXCEL.EXE (PID: 4668)
SUSPICIOUS
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 236)
- EXCEL.EXE (PID: 4668)
Reads data from a binary Stream object (SCRIPT)
- EXCEL.EXE (PID: 4668)
Detected use of alternative data streams (AltDS)
- EXCEL.EXE (PID: 4668)
Runs shell command (SCRIPT)
- EXCEL.EXE (PID: 4668)
INFO
The process uses the downloaded file
- EXCEL.EXE (PID: 6184)
- EXCEL.EXE (PID: 4668)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 236)
Manual execution by a user
- EXCEL.EXE (PID: 4668)
Reads the time zone
- EXCEL.EXE (PID: 4668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlam | | | Excel Macro-enabled Open XML add-in (42.4) |
|---|---|---|
| .xlsm | | | Excel Microsoft Office Open XML Format document (with Macro) (29.2) |
| .xlsx | | | Excel Microsoft Office Open XML Format document (17.3) |
| .zip | | | Open Packaging Conventions container (8.9) |
| .zip | | | ZIP compressed archive (2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x6e9922cf |
| ZipCompressedSize: | 433 |
| ZipUncompressedSize: | 1551 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | openpyxl |
|---|---|
| Description: | 0ZTFrYTRfYTliM2Q3ZjVlMmM4ZjRhMWIwZDZlM2MyYjdhNWQ5ZThjMWY0YjJhNmMzZDdmMGU1Yg== |
XML
| LastModifiedBy: | Aayush Barhate |
|---|---|
| CreateDate: | 2024:12:08 10:25:05Z |
| ModifyDate: | 2024:12:08 10:53:04Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | Sheet1 |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16.03 |
Total processes
156
Monitored processes
27
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1412 | C:\Users\admin\AppData\Local\Temp\tfFNcTy18npI.exe | C:\Users\admin\AppData\Local\Temp\tfFNcTy18npI.exe | — | EXCEL.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 1760 | cmd /c del "C:\Users\admin\AppData\Local\Temp\tfFNcTy18npI.exe" /f /q | C:\Windows\System32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tfFNcTy18npI.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4544 | C:\Users\admin\AppData\Local\Temp\AK3FwgJ8KV7h.exe nite1ka4_a9b3d7f5e2c8f4a1b0d6e3c2b7a5d9e8c1f4b2a6c3d7f0e5b 0ZTFrYTRfYTliM2Q3ZjVlMmM4ZjRhMWIwZDZlM2MyYjdhNWQ5ZThjMWY0YjJhNmMzZDdmMGU1Yg== | C:\Users\admin\AppData\Local\Temp\AK3FwgJ8KV7h.exe | — | EXCEL.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 4624 | cmd /c del "C:\Users\admin\AppData\Local\Temp\AK3FwgJ8KV7h.exe" /f /q | C:\Windows\System32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4668 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\MacroExe.xlsm" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 874
Read events
12 598
Write events
1 146
Delete events
130
Modification events
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 1 | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 1 | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 1 | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ru-ru |
Value: 1 | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | tr-tr |
Value: 1 | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | v%+ |
Value: 76252B002818000001000000000000007A9B0C08924DDB0100000000 | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel |
| Operation: | write | Name: | ImmersiveWorkbookDirtySentinel |
Value: 0 | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel |
| Operation: | write | Name: | ExcelPreviousSessionId |
Value: {6E255CAA-1530-400D-8E08-62DA5D4C8E90} | |||
| (PID) Process: | (6184) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel |
| Operation: | write | Name: | FontInfoCache |
Value: 6000000060000000F5FFFFFF0000000000000000000000009001000000000000000000205400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000050000001B000000000000000D0000000B000000020000000200000000000000330000000000000000000000F5FFFFFF0000000000000000000000009001000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000001C000000000000000D0000000B000000020000000200000000000000330000000000000000000000F5FFFFFF000000000000000000000000BC02000000000000000000205400610068006F006D006100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000600000020000000000000000D0000000B000000020000000200000000000000330000000000000000000000F3FFFFFF0000000000000000000000009001000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000002000000000000000100000000D000000030000000300000000000000330000000000000000000000F3FFFFFF000000000000000000000000E803000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000070000002600000000000000100000000D000000030000000300000000000000330000000000000000000000F1FFFFFF000000000000000000000000900100000000000000000000430061006C0069006200720069000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000001A00000000000000120000000E000000040000000300000000000000330000000000000000000000F3FFFFFF0000000000000000000000009001000000000000000000005300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000070000002100000000000000110000000E000000030000000400000000000000330000000000000000000000F3FFFFFF000000000000000000000000BC02000000000000000000005300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000002100000000000000110000000E000000030000000400000000000000330000000000000000000000F3FFFFFF0000000000000000000000009001000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000070000002100000000000000110000000E000000030000000400000000000000330000000000000000000000F3FFFFFF000000000000000000000000BC02000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000002100000000000000110000000E000000030000000400000000000000330000000000000000000000F5FFFFFF0000000000000000000000009001000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000001C000000000000000D0000000B000000020000000200000000000000330000000000000000000000F1FFFFFF000000000000000000000000900100000000000000000000430061006C0069006200720069000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000001A00000000000000120000000E000000040000000300000000000000330000000000000000000000F5FFFFFF0000000000000000000000009001000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000001C000000000000000D0000000B000000020000000200000000000000330000000000000000000000F5FFFFFF0000000000000000000000009001000000000000000000205400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000050000001B000000000000000D0000000B000000020000000200000000000000330000000000000000000000F5FFFFFF000000000000000000000000BC02000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000001C000000000000000D0000000B000000020000000200000000000000330000000000000000000000F1FFFFFF000000000000000000000000900100000000000000000000430061006C0069006200720069000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000001A00000000000000120000000E000000040000000300000000000000330000000000000000000000F3FFFFFF000000000000000000000000BC02000000000000000000005300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000002100000000000000110000000E000000030000000400000000000000330000000000000000000000 | |||
Executable files
7
Suspicious files
34
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Diagnostics\EXCEL\App1734116753385014700_6E255CAA-1530-400D-8E08-62DA5D4C8E90.log | — | |
MD5:— | SHA256:— | |||
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:3C57C1D3F6EE5398DA0FC582572972B1 | SHA256:7EDB45DD3E19D76CC1FCC7E1543BFF6144EDEB86733154AC550E9B4AD56FE0FA | |||
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\A242898C-4BEB-4040-8E4C-E84C8ECFBD2C | xml | |
MD5:BEDD1D4DC3707BB9953C528E2C92C43A | SHA256:A38420C939804218CB936DC6F6FE0EE91198E61DAACC0CA5976E68C91EE3DE3F | |||
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:15B99537AF2C9E91A00BD821702AFC36 | SHA256:91E10E038860CC697C2CF1B71493DE9EC413CC7CF760C9415F39B56549425E2F | |||
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:62979CE48BAD4824963D087CCE036F28 | SHA256:D0BC4407C8241B03CB1671EB065D321318A6D8EE50101A2DD95B1720C76AEF8C | |||
| 6184 | EXCEL.EXE | C:\Users\admin\Desktop\~$MacroExe.xlsm.xlsx | pgc | |
MD5:21E5D64E6DD2C94C577A61B0A25DE7A4 | SHA256:657F0604A7C1F6CFDC4E8A224F59BD6E1900A4A4DD8B3F61A20F67DEBE41F209 | |||
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Excel.Settings.json | binary | |
MD5:E4E83F8123E9740B8AA3C3DFA77C1C04 | SHA256:6034F27B0823B2A6A76FE296E851939FD05324D0AF9D55F249C79AF118B0EB31 | |||
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:8DCCF28E1B0CC642B556CC48720183AF | SHA256:B223A27CD56D757FA13E3F5E6A4EE0C3AFBC873586D49FBF46521B7553F9CB0E | |||
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:8DCCF28E1B0CC642B556CC48720183AF | SHA256:B223A27CD56D757FA13E3F5E6A4EE0C3AFBC873586D49FBF46521B7553F9CB0E | |||
| 6184 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_40.ttf | pi2 | |
MD5:4296A064B917926682E7EED650D4A745 | SHA256:E04E41C74D6C78213BA1588BACEE64B42C0EDECE85224C474A714F39960D8083 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
56
DNS requests
31
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6184 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3952 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6184 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3952 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4144 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4144 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5340 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |