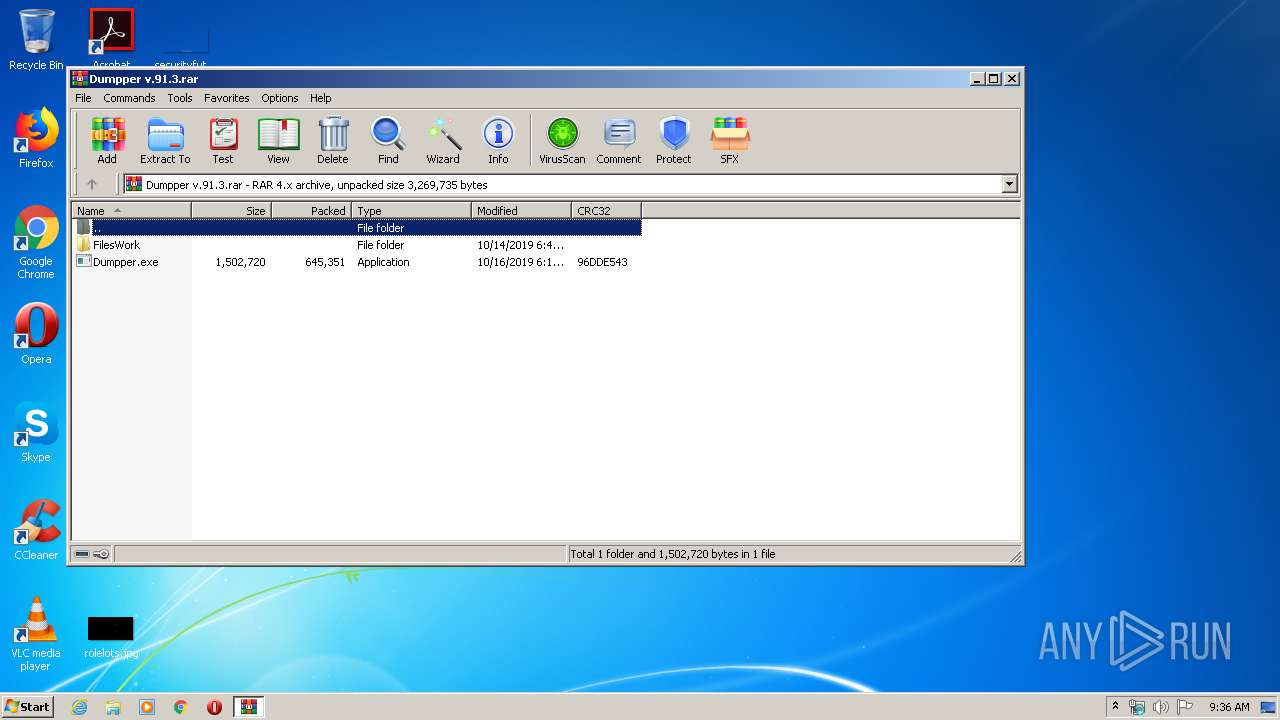
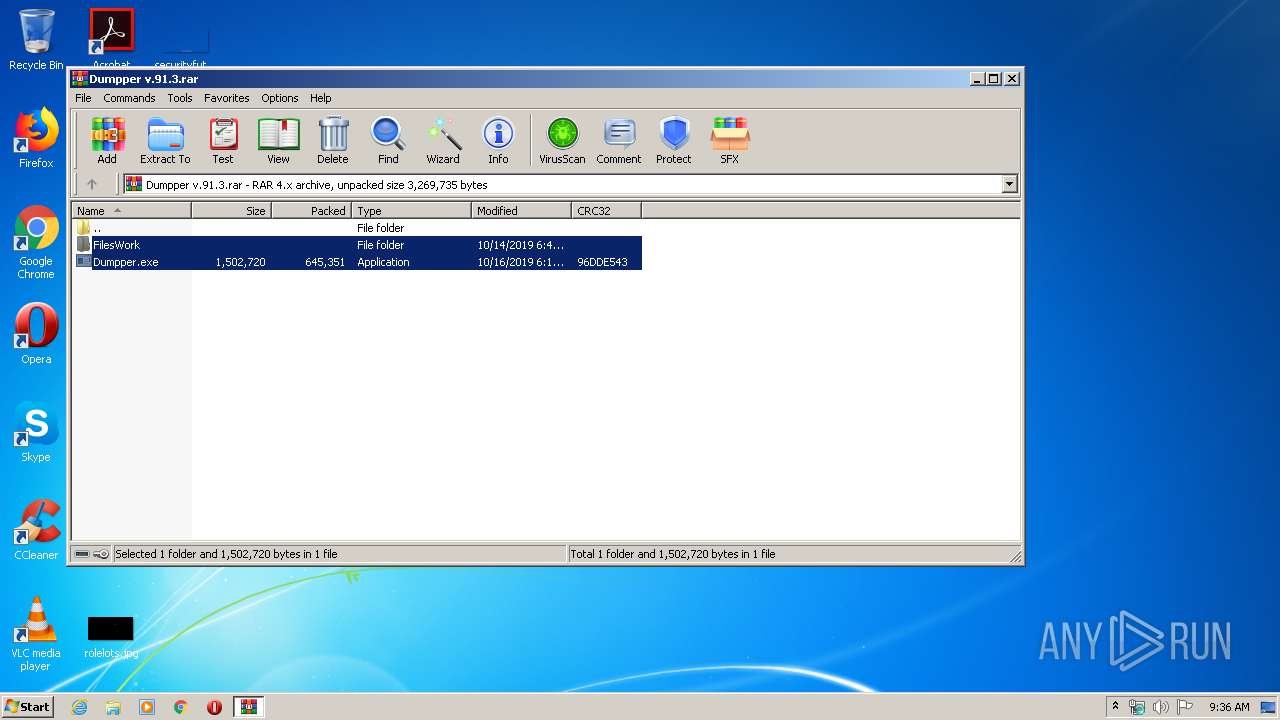
| File name: | Dumpper v.91.3.rar |
| Full analysis: | https://app.any.run/tasks/59d4f4b5-d333-4571-a286-2a100054f67f |
| Verdict: | Suspicious activity |
| Analysis date: | March 30, 2020, 08:36:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 5277AE0D59827F4CF3523BF6B3460E29 |
| SHA1: | 335AD31D2DBC4E4A03DDED528CA3306F86AFE134 |
| SHA256: | 05BFDB6922C3E7D681A8D48D697375B5DA5071546CCEC892F9EC2D46617FD5AA |
| SSDEEP: | 24576:BsN2+HT23E73P7XNu6aqXihQcUEtLnH2PyO1UO0lJrs3r:EBzrzDNFaqyhQcHdH2ao33r |
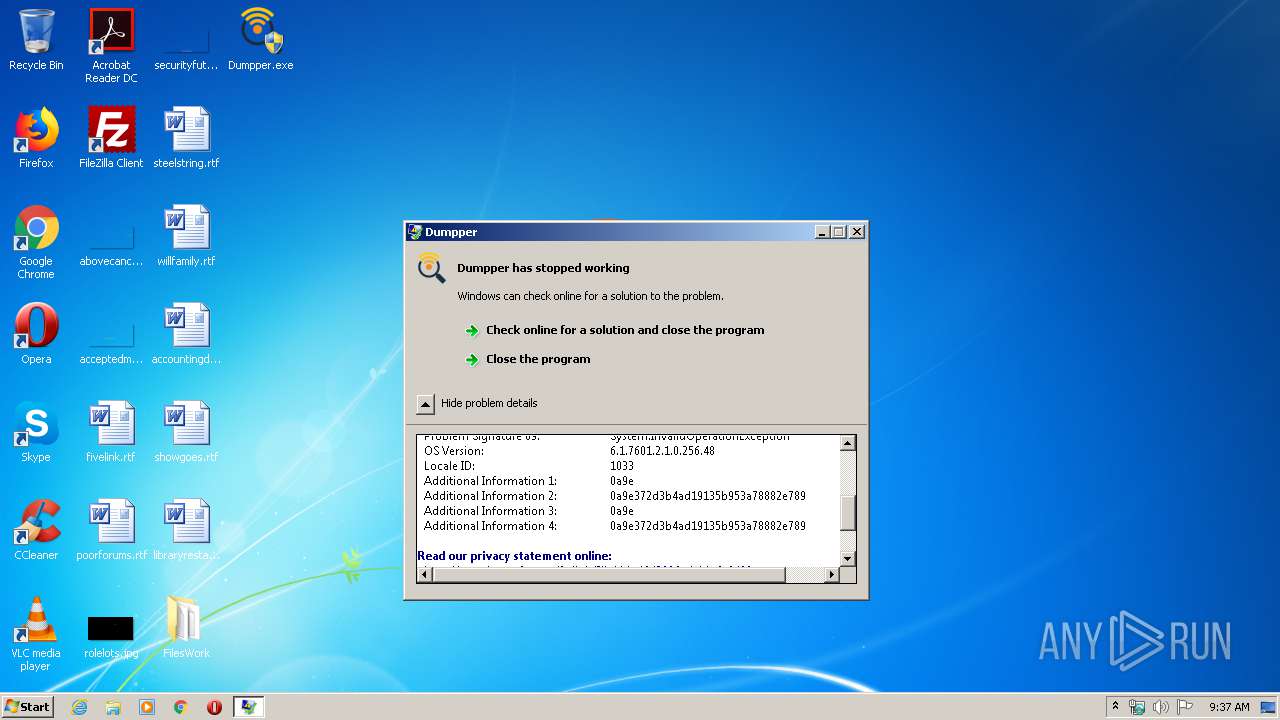
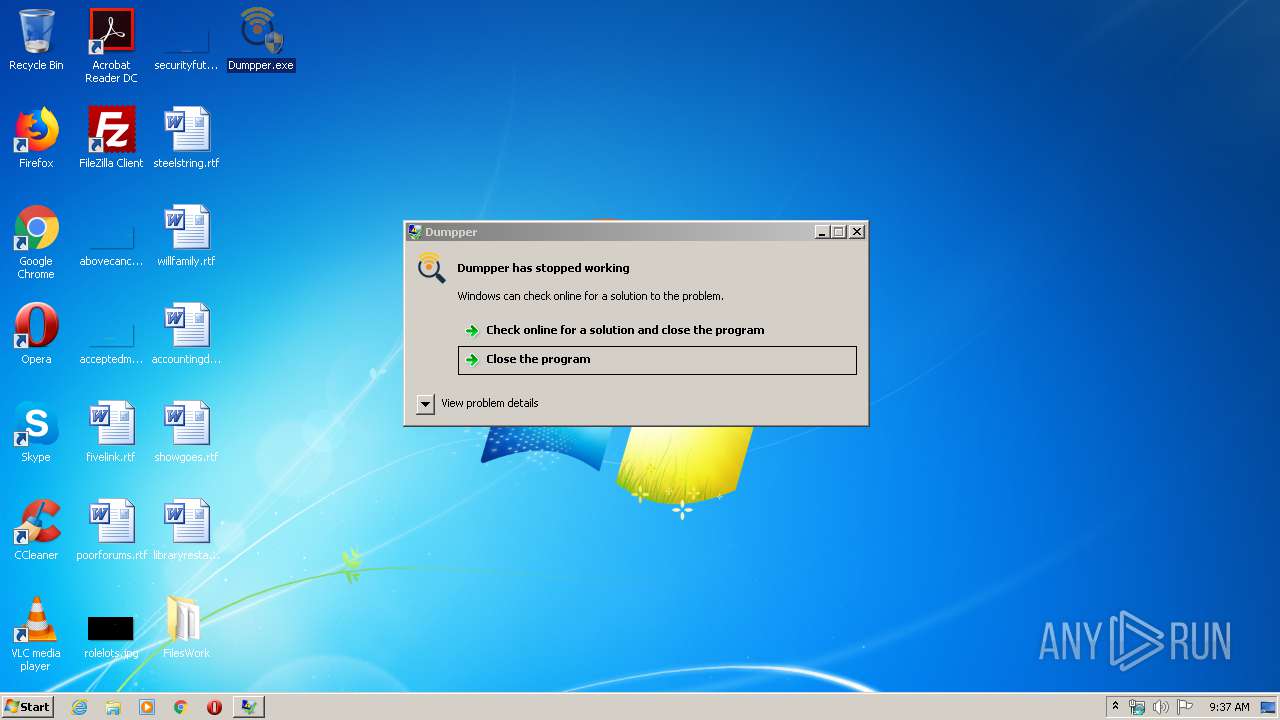
MALICIOUS
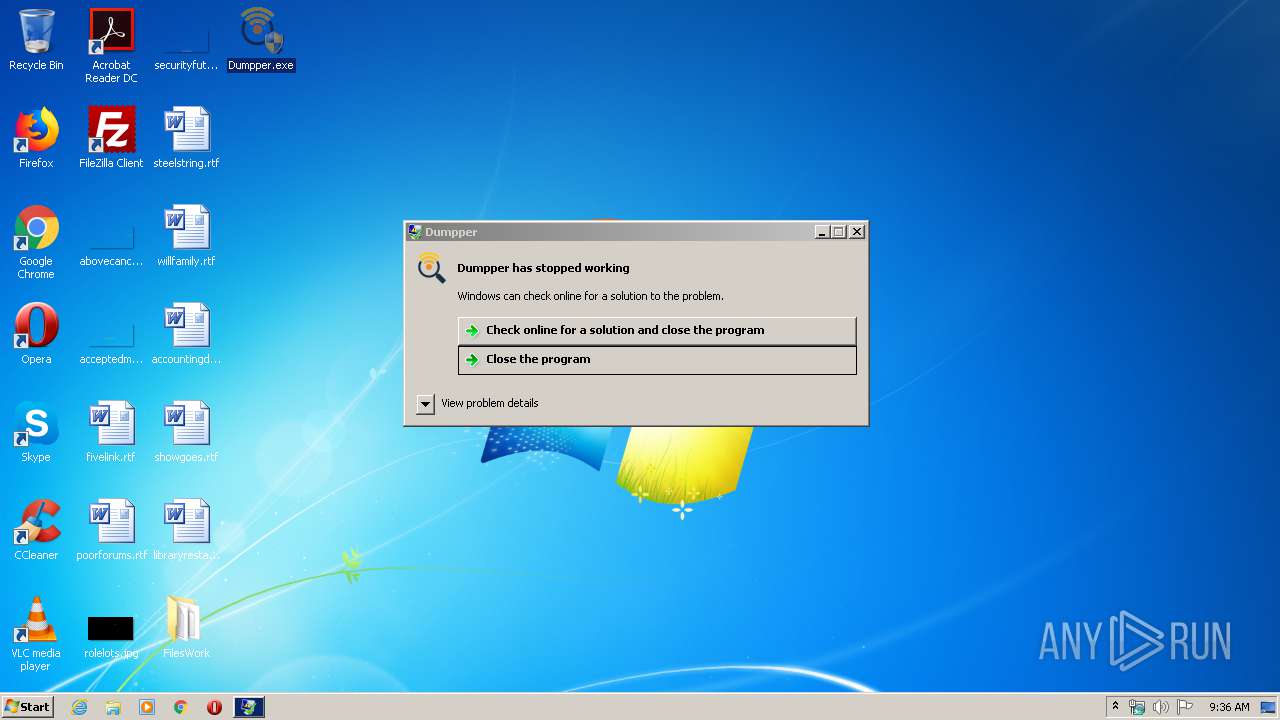
Application was dropped or rewritten from another process
- Dumpper.exe (PID: 1756)
- Dumpper.exe (PID: 2948)
- Dumpper.exe (PID: 2852)
- Dumpper.exe (PID: 2496)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3376)
INFO
Manual execution by user
- Dumpper.exe (PID: 2496)
- Dumpper.exe (PID: 2852)
- Dumpper.exe (PID: 2948)
- wermgr.exe (PID: 3852)
- Dumpper.exe (PID: 1756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 388940 |
|---|---|
| UncompressedSize: | 1646592 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:02:06 04:17:22 |
| PackingMethod: | Normal |
| ArchivedFileName: | FilesWork\JumpLittle.exe |
Total processes
49
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1756 | "C:\Users\admin\Desktop\Dumpper.exe" | C:\Users\admin\Desktop\Dumpper.exe | explorer.exe | ||||||||||||
User: admin Company: SkyTech Integrity Level: HIGH Description: Dumpper Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2496 | "C:\Users\admin\Desktop\Dumpper.exe" | C:\Users\admin\Desktop\Dumpper.exe | explorer.exe | ||||||||||||
User: admin Company: SkyTech Integrity Level: HIGH Description: Dumpper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\Desktop\Dumpper.exe" | C:\Users\admin\Desktop\Dumpper.exe | — | explorer.exe | |||||||||||
User: admin Company: SkyTech Integrity Level: MEDIUM Description: Dumpper Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2948 | "C:\Users\admin\Desktop\Dumpper.exe" | C:\Users\admin\Desktop\Dumpper.exe | — | explorer.exe | |||||||||||
User: admin Company: SkyTech Integrity Level: MEDIUM Description: Dumpper Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3376 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Dumpper v.91.3.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3852 | "C:\Windows\system32\wermgr.exe" "-outproc" "372" "3940" | C:\Windows\system32\wermgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
490
Read events
468
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Dumpper v.91.3.rar | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3376) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
3
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3376 | WinRAR.exe | C:\Users\admin\Desktop\FilesWork\PinList.txt | text | |
MD5:— | SHA256:— | |||
| 3376 | WinRAR.exe | C:\Users\admin\Desktop\Dumpper.exe | executable | |
MD5:— | SHA256:— | |||
| 3852 | wermgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\NonCritical_Dumpper.exe_785b5d2660d3c59e17653c1bf214fcfab6e6179_cab_0fab16a8\appcompat.txt | xml | |
MD5:— | SHA256:— | |||
| 3852 | wermgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\NonCritical_Dumpper.exe_785b5d2660d3c59e17653c1bf214fcfab6e6179_cab_0fab16a8\Report.wer | binary | |
MD5:— | SHA256:— | |||
| 3376 | WinRAR.exe | C:\Users\admin\Desktop\FilesWork\PerfilWps.bin | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
| 3852 | wermgr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\NonCritical_Dumpper.exe_785b5d2660d3c59e17653c1bf214fcfab6e6179_cab_0fab16a8\Tab15EE.tmp | text | |
MD5:A888880617592FACA7384726060482F4 | SHA256:812742C959B6752D300080FB56459B04332EF91CC895A0846C2333C8B0C15FD6 | |||
| 3376 | WinRAR.exe | C:\Users\admin\Desktop\FilesWork\JumpLittle.exe | executable | |
MD5:1E0FE724AC8EEE75461AA814C480705D | SHA256:177023C40080306164E32221C019B31DD91DF3F94DCE19A2416A74AE9061917F | |||
| 3376 | WinRAR.exe | C:\Users\admin\Desktop\FilesWork\WpsWin.exe | executable | |
MD5:D474EAEB9542D2BE2AC1853936BB774B | SHA256:93229A919E830257DC87BFD9EC11E5E1DDFBF18425484E4450DB7329E6D0C1D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
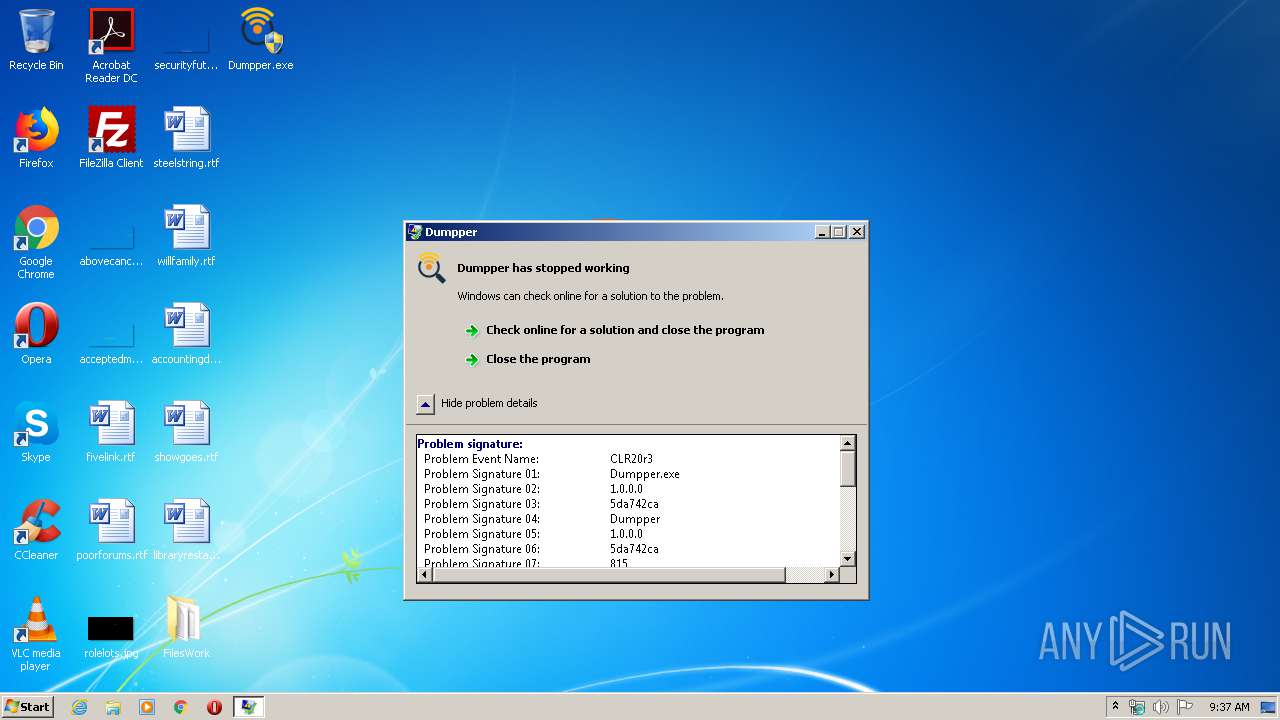
3800 | WerFault.exe | GET | — | 51.143.111.81:80 | http://watson.microsoft.com/StageOne/Generic/CLR20r3/Dumpper_exe/1_0_0_0/5da742ca/Dumpper/1_0_0_0/5da742ca/815/12/System_InvalidOperationException.htm?LCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=DELL&SPN=DELL&BV=DELL&MID=3ADE2C42-4AB9-49B7-B142-BE9AEEA69063 | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3800 | WerFault.exe | 51.143.111.81:80 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dumpper.exe | FTH: (2496): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|