| File name: | Product.msi |
| Full analysis: | https://app.any.run/tasks/26cde5e1-a71a-48a4-96d4-e5572c440621 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 03:07:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
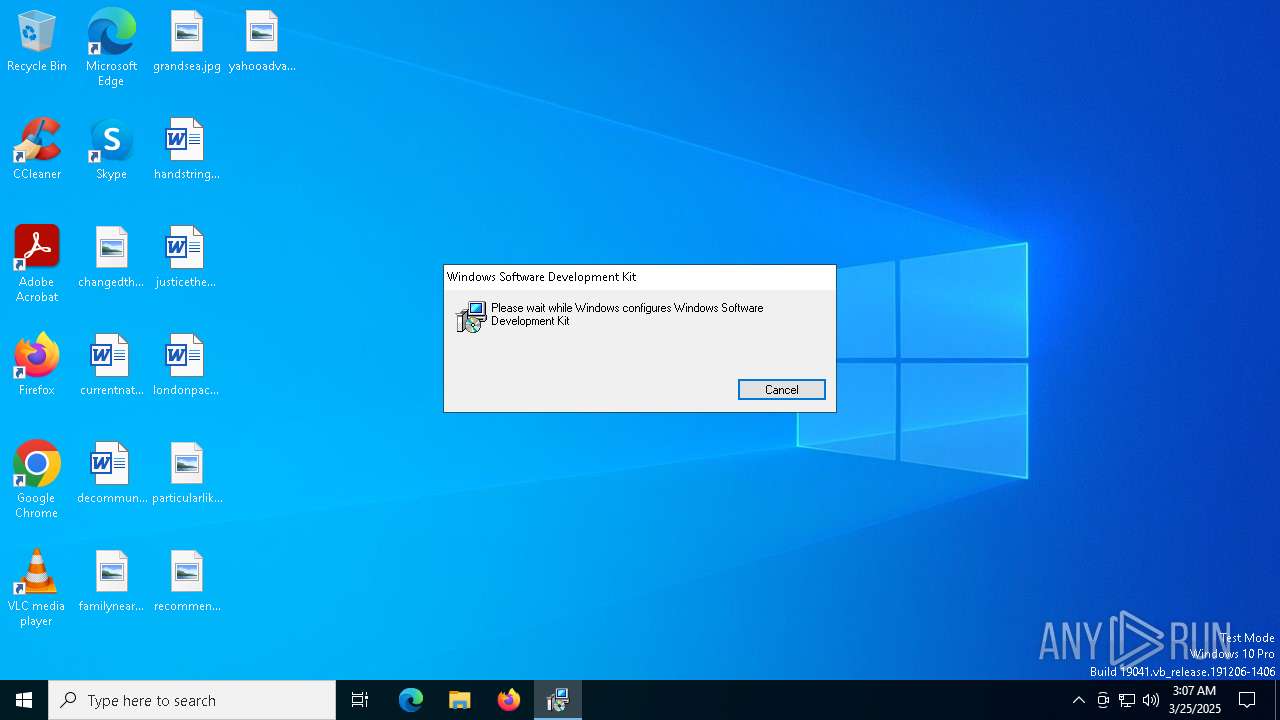
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Windows Software Development Kit 4.1.5.0 Installer, Author: Microsoft Corporation, Keywords: Installer, Comments: Windows Software Development Kit for Windows Store Apps, Template: Intel;1033, Revision Number: {26BAB16F-4FF3-486D-803F-A5ED6FF890A7}, Create Time/Date: Fri Mar 21 10:13:26 2025, Last Saved Time/Date: Fri Mar 21 10:13:26 2025, Number of Pages: 200, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.14.1.8722), Security: 2 |
| MD5: | 2FB80D73656ACA3D0E777311189E56A3 |
| SHA1: | 8E3A7D00997F331ECAF2530E96A4636228F34918 |
| SHA256: | 05BB855D9EBDBB0749113ACD50FDA0B03C3F050F97AFC5F5C4637C924D326F94 |
| SSDEEP: | 98304:nLagAHOVTjVXA74JQf/1sgvtbibnd+bi4r26MD/v2NA45jFeMCdB2YqerrHW16gt:nHUjRAy2Yk0kWqcEJWjxlMZ |
MALICIOUS
Generic archive extractor
- msiexec.exe (PID: 2236)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 5680)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6424)
Process drops python dynamic module
- msiexec.exe (PID: 6424)
Process drops legitimate windows executable
- msiexec.exe (PID: 6424)
The process drops C-runtime libraries
- msiexec.exe (PID: 6424)
Loads Python modules
- pythonw.exe (PID: 4880)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6424)
Reads security settings of Internet Explorer
- pythonw.exe (PID: 4880)
INFO
Reads the computer name
- msiexec.exe (PID: 6424)
- pythonw.exe (PID: 4880)
Checks supported languages
- msiexec.exe (PID: 6424)
- pythonw.exe (PID: 4880)
Manages system restore points
- SrTasks.exe (PID: 6032)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6424)
The sample compiled with english language support
- msiexec.exe (PID: 6424)
Python executable
- pythonw.exe (PID: 4880)
Creates a software uninstall entry
- msiexec.exe (PID: 6424)
Application launched itself
- Acrobat.exe (PID: 5416)
- AcroCEF.exe (PID: 7292)
Reads the machine GUID from the registry
- pythonw.exe (PID: 4880)
Reads the software policy settings
- pythonw.exe (PID: 4880)
Checks proxy server information
- pythonw.exe (PID: 4880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Windows Software Development Kit 4.1.5.0 Installer |
| Author: | Microsoft Corporation |
| Keywords: | Installer |
| Comments: | Windows Software Development Kit for Windows Store Apps |
| Template: | Intel;1033 |
| RevisionNumber: | {26BAB16F-4FF3-486D-803F-A5ED6FF890A7} |
| CreateDate: | 2025:03:21 10:13:26 |
| ModifyDate: | 2025:03:21 10:13:26 |
| Pages: | 200 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.14.1.8722) |
| Security: | Read-only recommended |
Total processes
150
Monitored processes
20
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | cmd.exe /C start "" "C:\Users\admin\AppData\Local\Hotfix\files\Password.pdf" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\Product.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\AppData\Local\Hotfix\files\pythonw.exe" "C:\Users\admin\AppData\Local\Hotfix\files\win_socks.py" | C:\Users\admin\AppData\Local\Hotfix\files\pythonw.exe | msiexec.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Version: 3.12.9 Modules
| |||||||||||||||
| 5408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5408 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\AppData\Local\Hotfix\files\Password.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5416 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\AppData\Local\Hotfix\files\Password.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | cmd.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5680 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6424 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 346
Read events
18 931
Write events
396
Delete events
19
Modification events
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000029389411339DDB011819000080100000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000029389411339DDB011819000080100000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000084A2F311339DDB011819000080100000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000084A2F311339DDB011819000080100000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000CD6AF811339DDB011819000080100000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000F5BAFA11339DDB011819000080100000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000A16D8612339DDB011819000080100000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000459A8C12339DDB0118190000D4150000E80300000100000000000000000000004C6E1B09B6EBC345BC6DE2D40EC460E700000000000000000000000000000000 | |||
| (PID) Process: | (5680) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000005D289812339DDB013016000088030000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
31
Suspicious files
199
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6424 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6424 | msiexec.exe | C:\Windows\Installer\1124ac.msi | — | |
MD5:— | SHA256:— | |||
| 6424 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:964F415401CDE768DBCAB2B51D28E1EF | SHA256:84A9858FC192FE7D00FF0645E4DF44F8251D04A7EDBF08A36F8B36D11EF2D91D | |||
| 6424 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:A9DDEAD5C4DB207DB6C911571BE03B37 | SHA256:E352526735AA03007299E60C595761F0689EFB552C00FFA9D54EDA3635976395 | |||
| 6424 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{091b6e4c-ebb6-45c3-bc6d-e2d40ec460e7}_OnDiskSnapshotProp | binary | |
MD5:964F415401CDE768DBCAB2B51D28E1EF | SHA256:84A9858FC192FE7D00FF0645E4DF44F8251D04A7EDBF08A36F8B36D11EF2D91D | |||
| 6424 | msiexec.exe | C:\Users\admin\AppData\Local\Hotfix\files\ordlookup\__pycache__\ws2_32.cpython-312.pyc | binary | |
MD5:1FC83CD95322875464E6BA68640F36FA | SHA256:D890632C1C600A7DDE942E398028CC0848241875F4DAD36D86892ACEEBD32CAC | |||
| 6424 | msiexec.exe | C:\Users\admin\AppData\Local\Hotfix\files\ordlookup\ws2_32.py | text | |
MD5:34E6BE9F69931AA8B9E1F655415188F9 | SHA256:832F959EBB7AC959B337CB1BA8B40449A370167676A238782EC880AB9203AEE0 | |||
| 6424 | msiexec.exe | C:\Users\admin\AppData\Local\Hotfix\files\python.exe | executable | |
MD5:EF26D0AE12E1C39269EFA78DF4107443 | SHA256:805FD29612C221EBEA570D372EC5ED46093C25A1033F1765DE9B2F8103868886 | |||
| 6424 | msiexec.exe | C:\Users\admin\AppData\Local\Hotfix\files\libssl-3.dll | executable | |
MD5:4FF168AAA6A1D68E7957175C8513F3A2 | SHA256:2E4D35B681A172D3298CAF7DC670451BE7A8BA27C26446EFC67470742497A950 | |||
| 6424 | msiexec.exe | C:\Windows\Temp\~DF88A25A63E406EFF6.TMP | binary | |
MD5:A9DDEAD5C4DB207DB6C911571BE03B37 | SHA256:E352526735AA03007299E60C595761F0689EFB552C00FFA9D54EDA3635976395 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
58
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
6192 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4220 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
4220 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
5416 | Acrobat.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6544 | svchost.exe | 20.190.160.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | unknown |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6192 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6192 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| unknown |
settings-win.data.microsoft.com |
| unknown |
crl.microsoft.com |
| unknown |
client.wns.windows.com |
| unknown |
login.live.com |
| unknown |
ocsp.digicert.com |
| unknown |
arc.msn.com |
| unknown |
go.microsoft.com |
| unknown |
slscr.update.microsoft.com |
| unknown |
www.microsoft.com |
| unknown |