| File name: | 4367890.vbs |
| Full analysis: | https://app.any.run/tasks/718edd74-57e1-4de9-b7b2-de0616269088 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 08:28:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | FDE6C67AEA146B55C1913F2A366298AB |
| SHA1: | 1770B686E86C85EC67651FA71CA2D1A145E6468C |
| SHA256: | 05B7BDDAB13B701AA80981AC648AD2946F89D557A81CE4CD90404F5551F30A5B |
| SSDEEP: | 192:2D/+o4XMLoUNF4pfAwb8MSaVN8fItX7P61yOe8ss/tUnh/K2E:2LroUNSrSm2md5dQwtK2E |
MALICIOUS
No malicious indicators.SUSPICIOUS
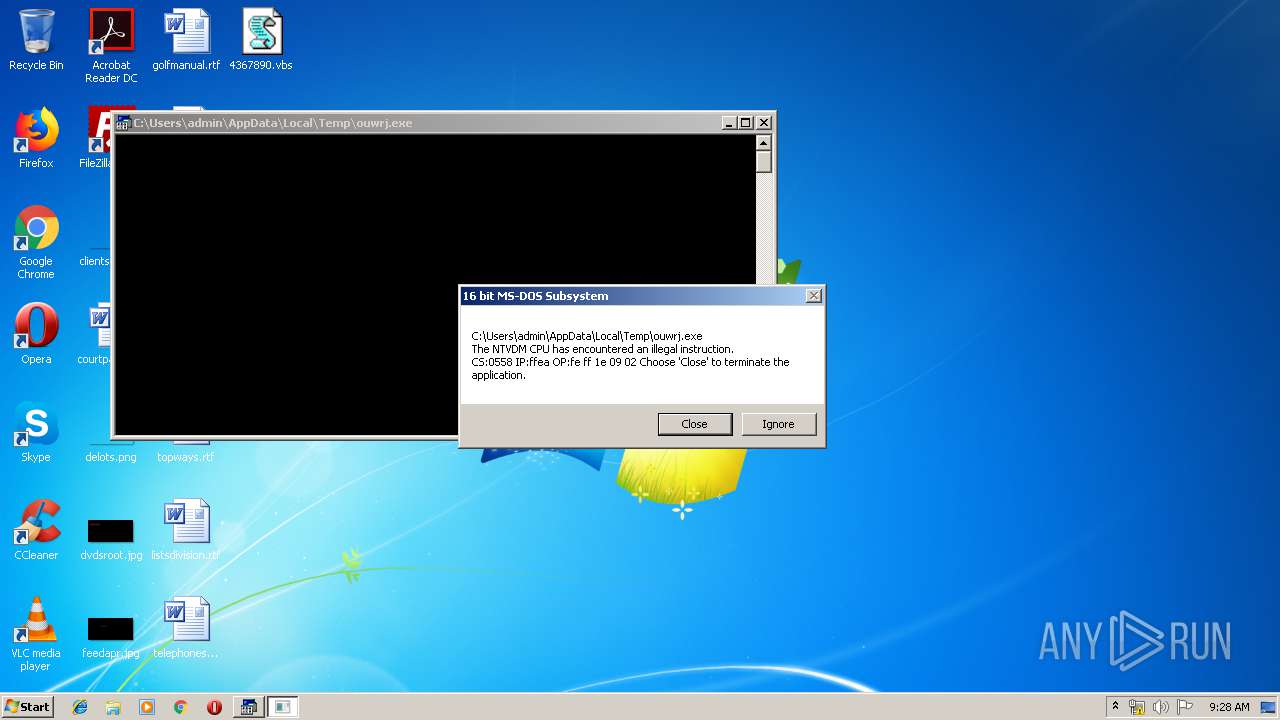
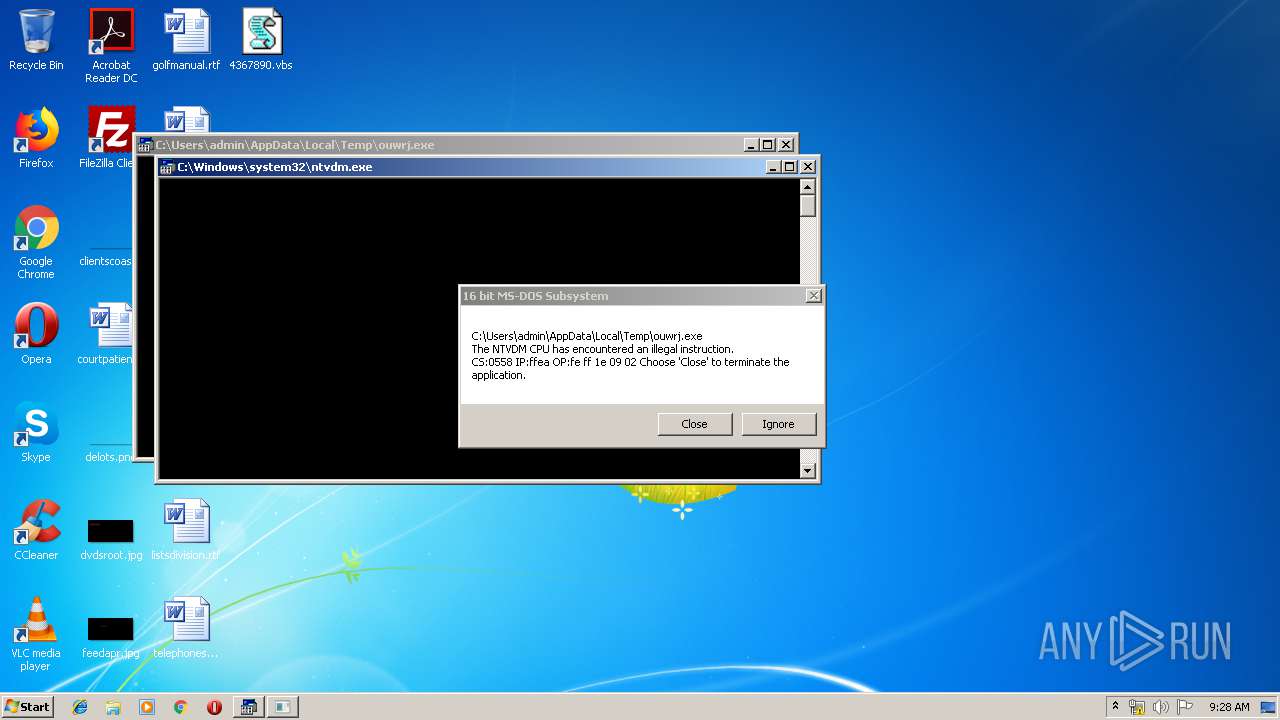
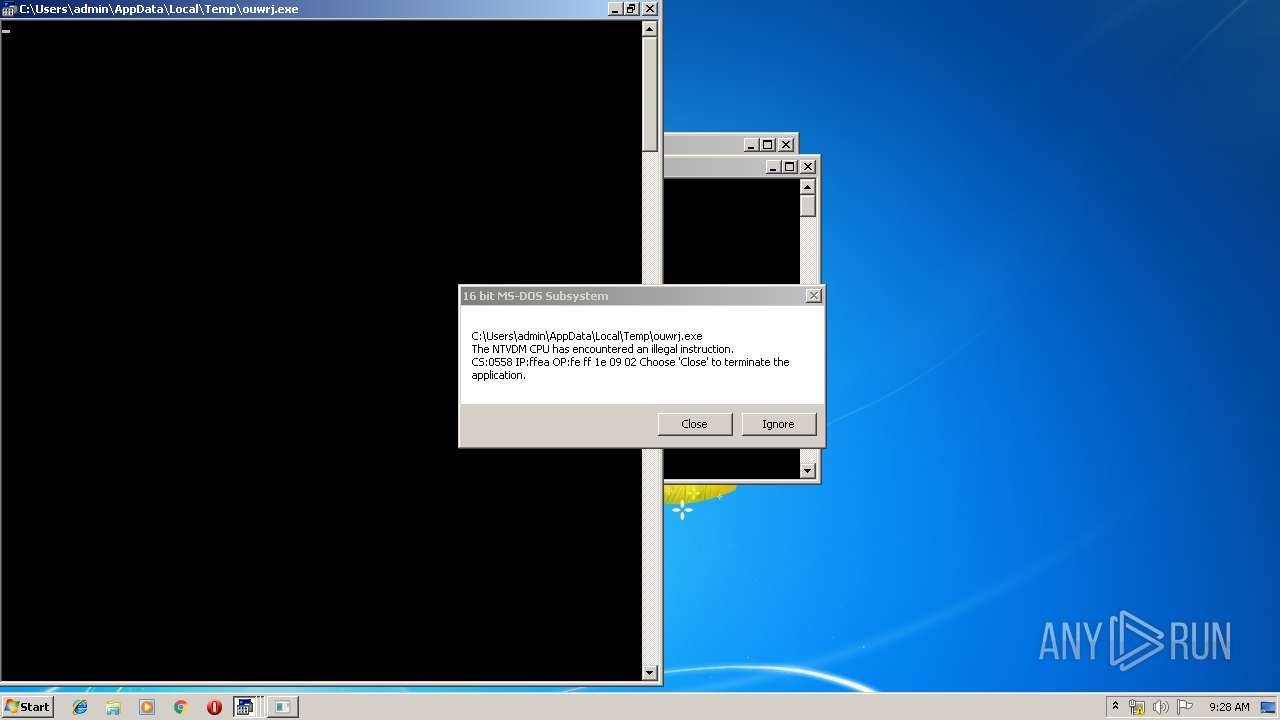
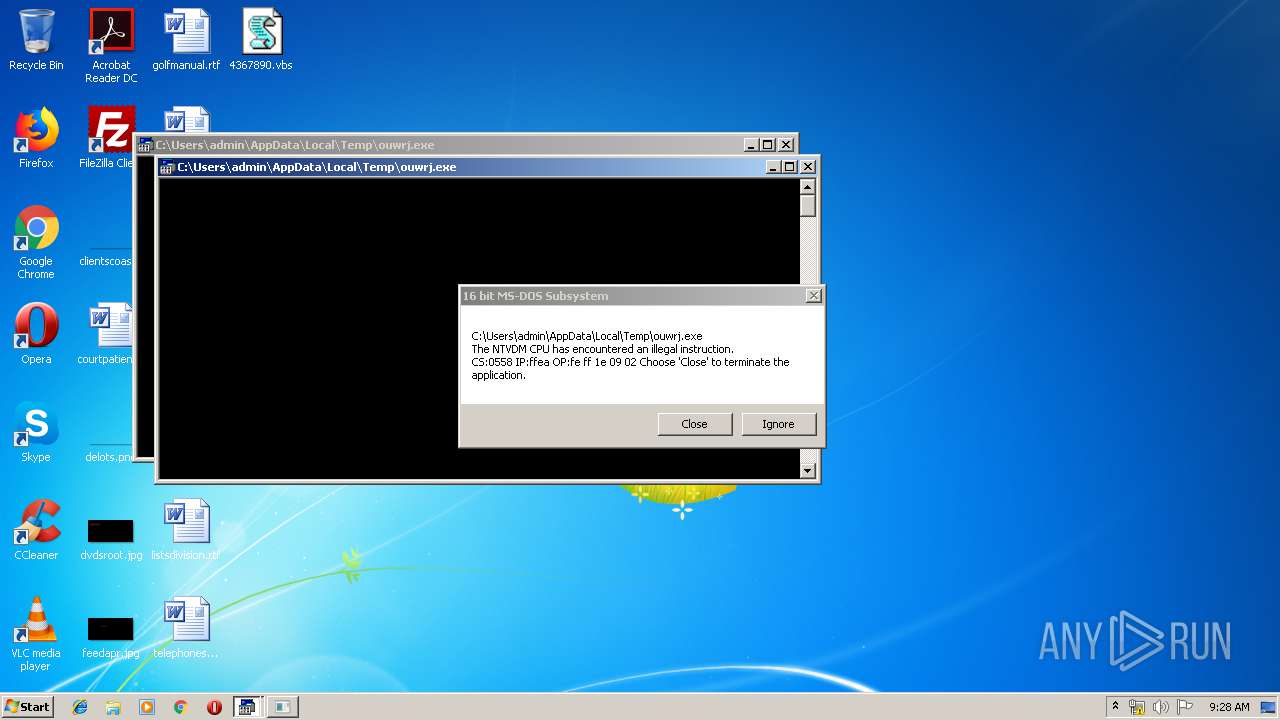
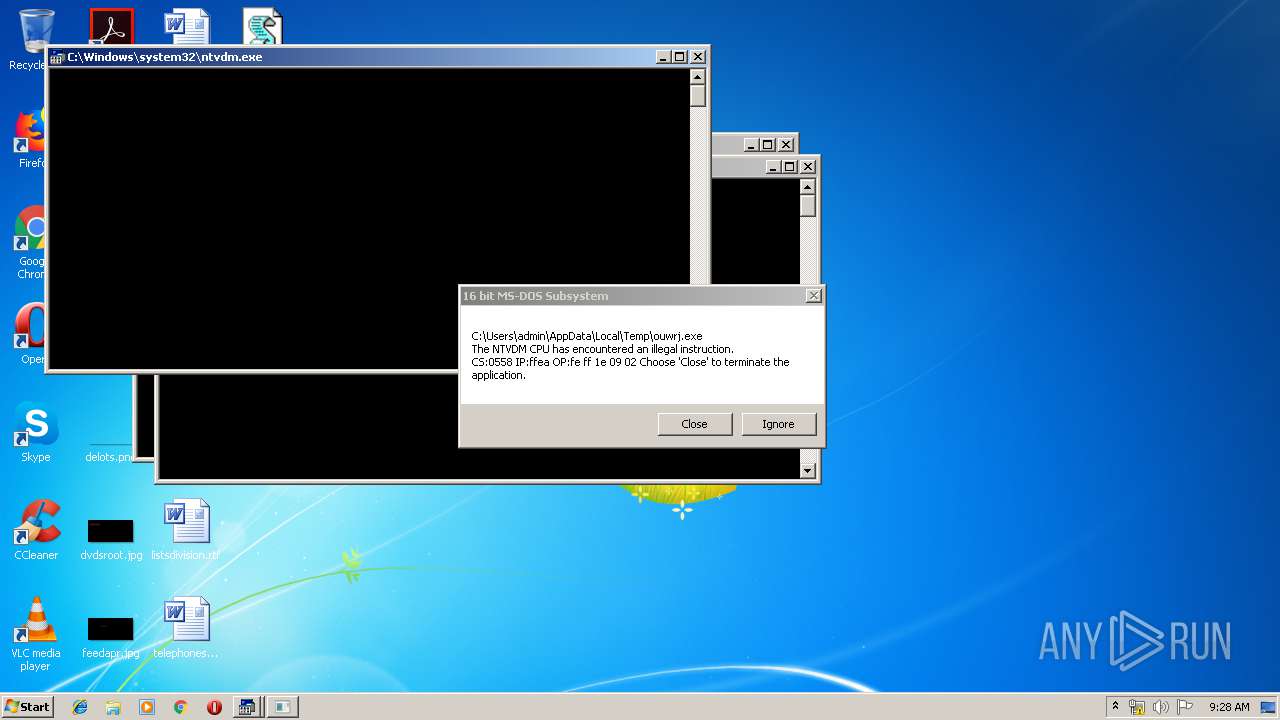
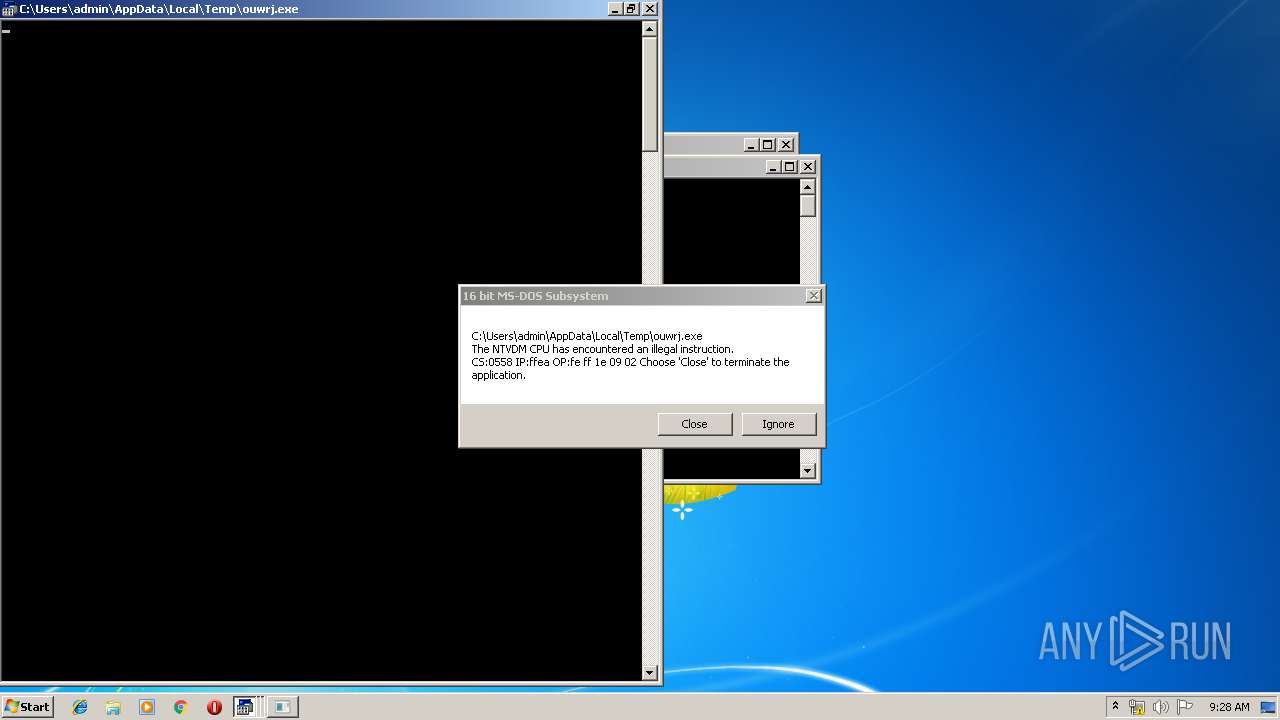
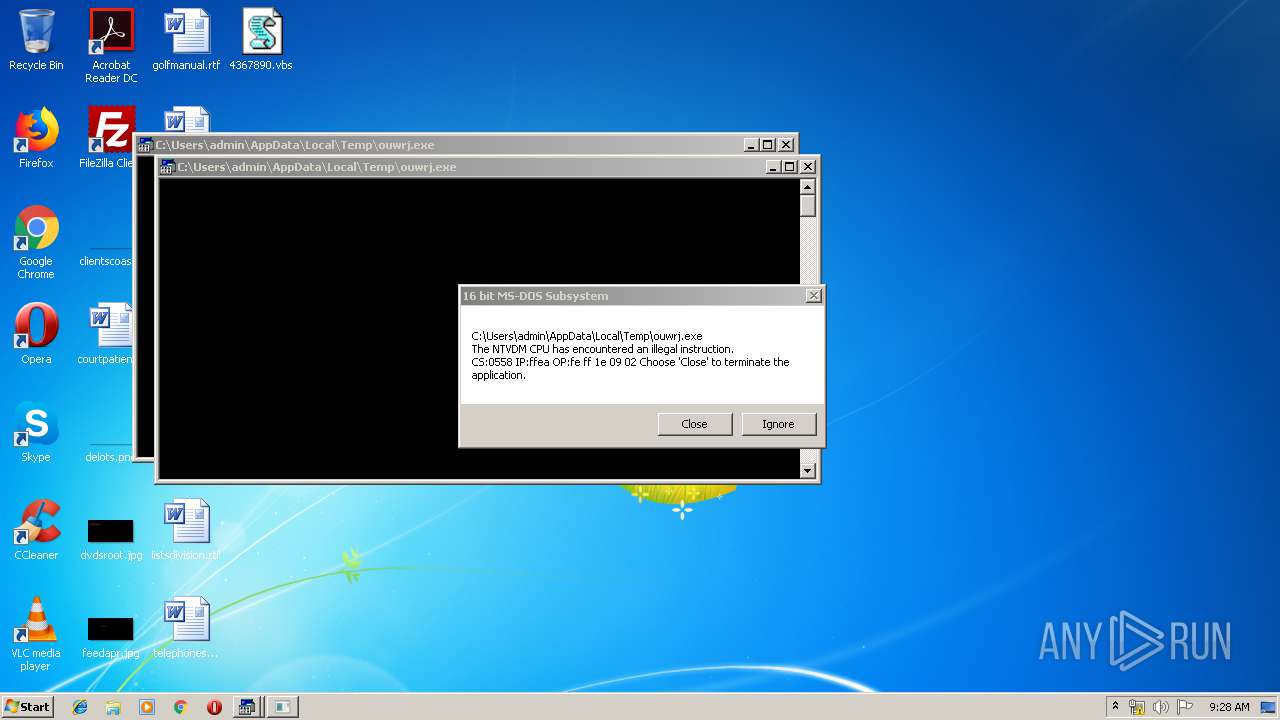
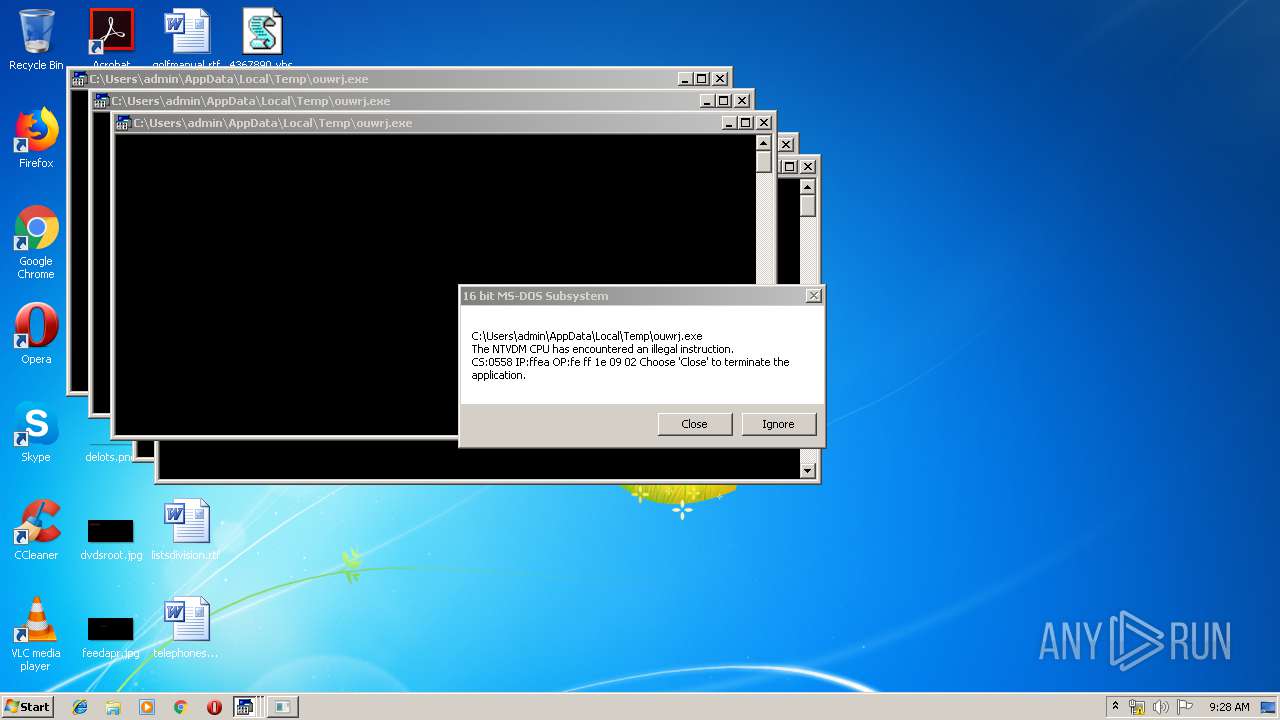
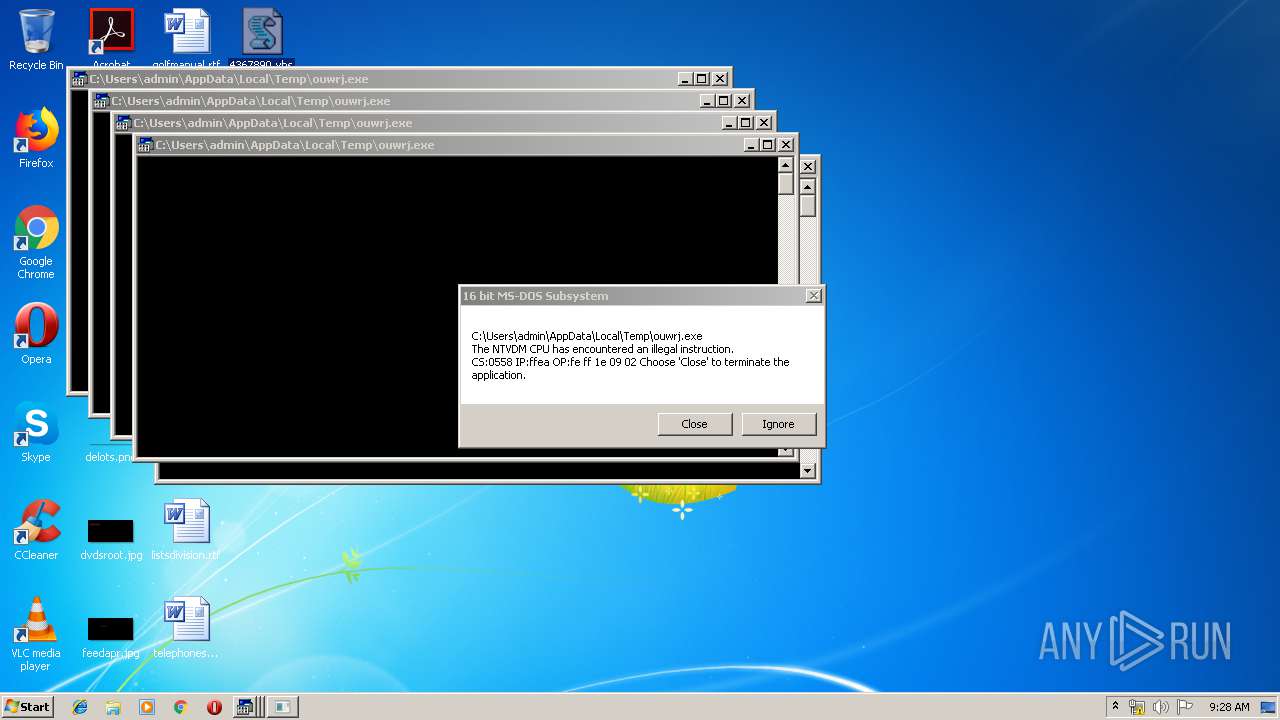
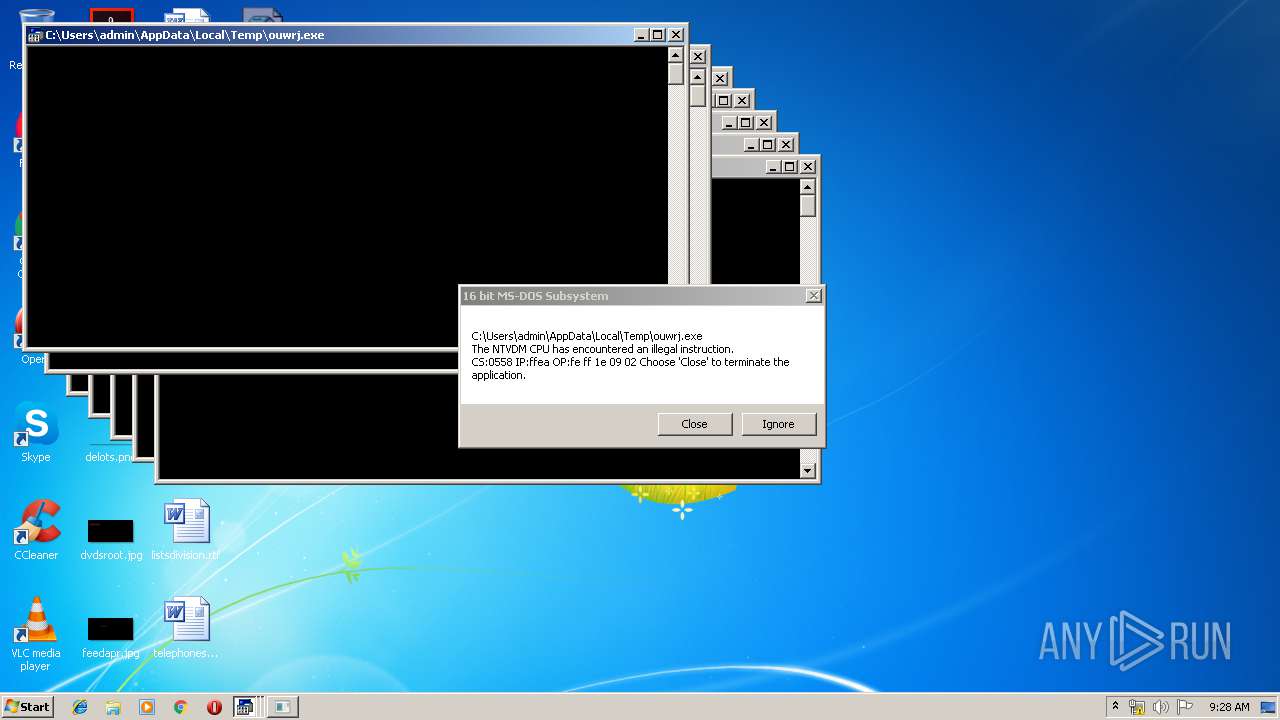
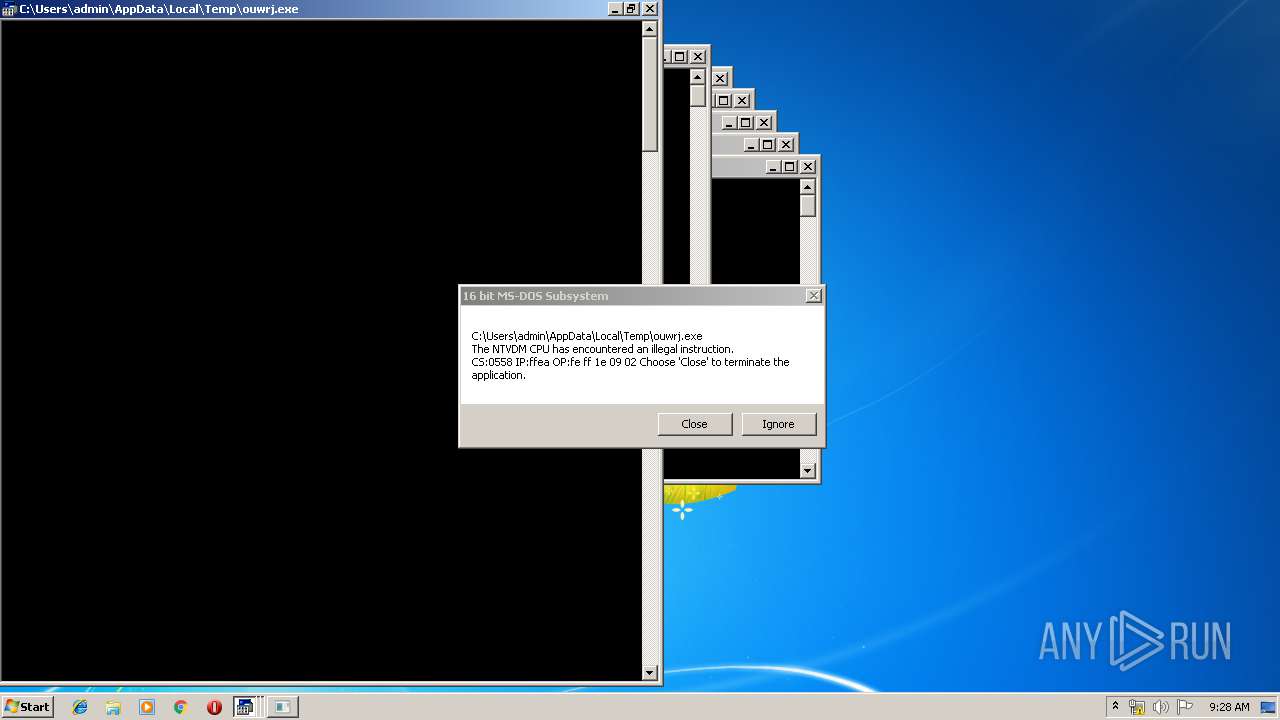
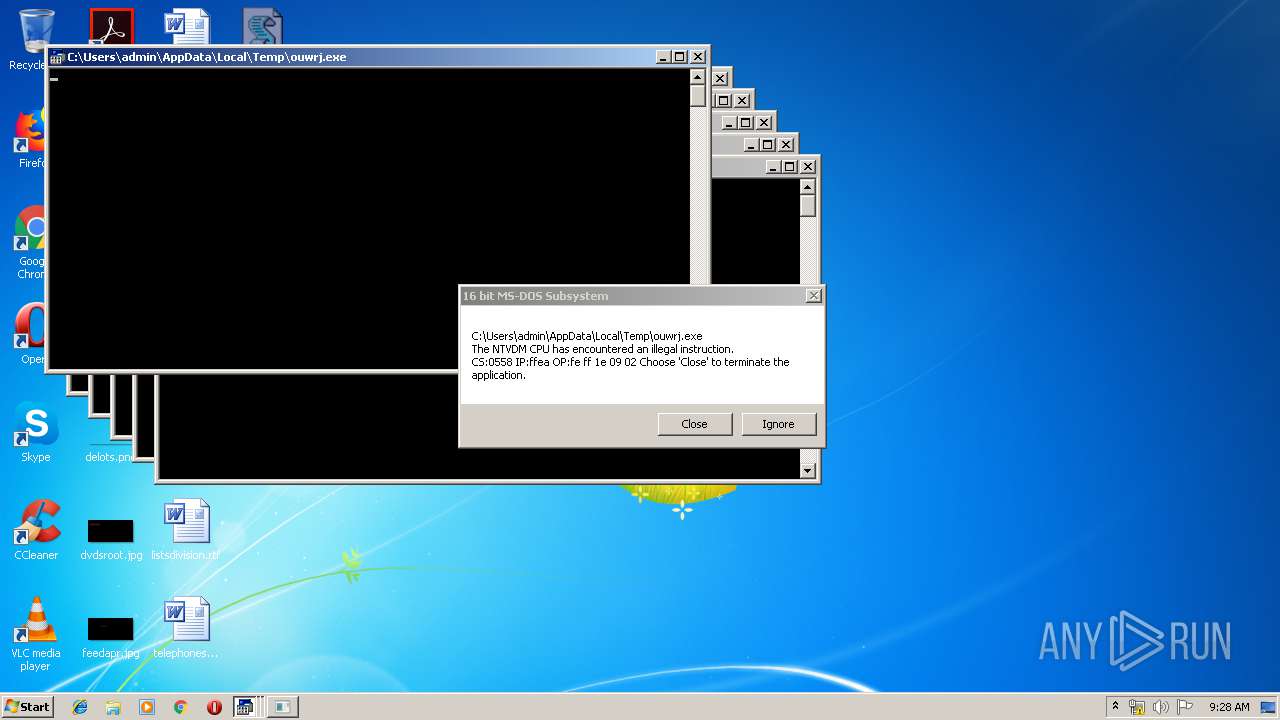
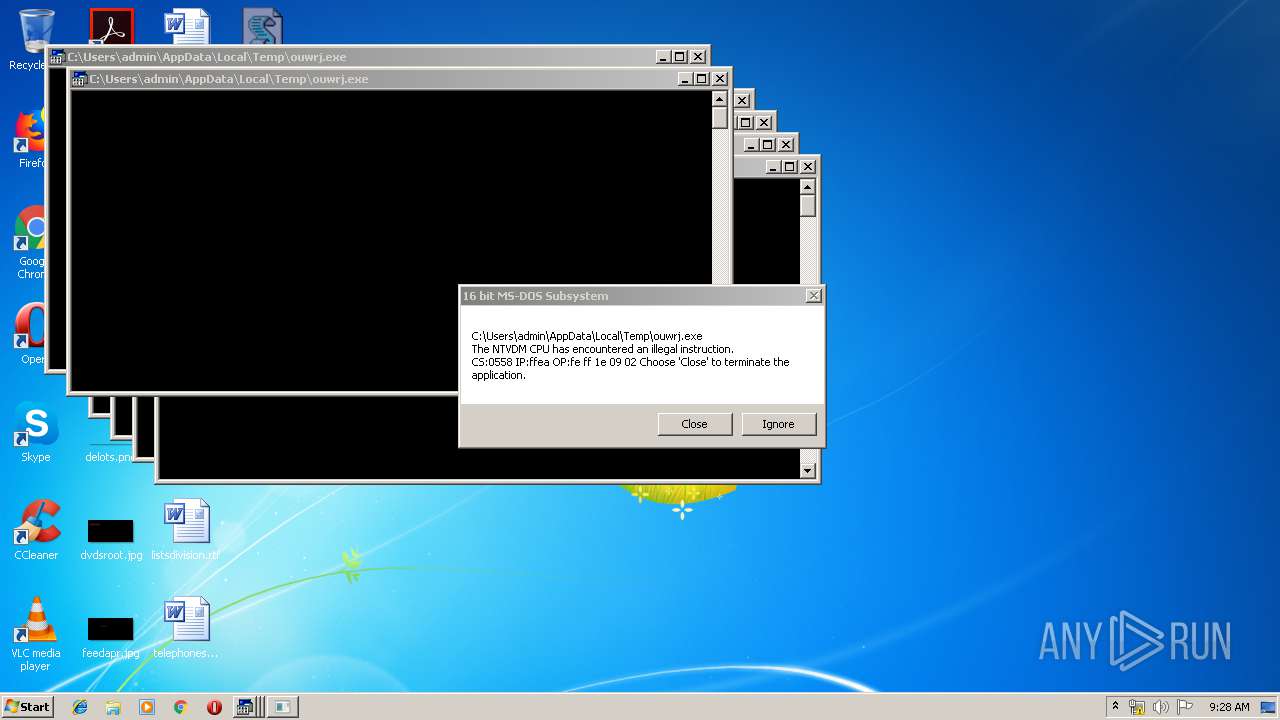
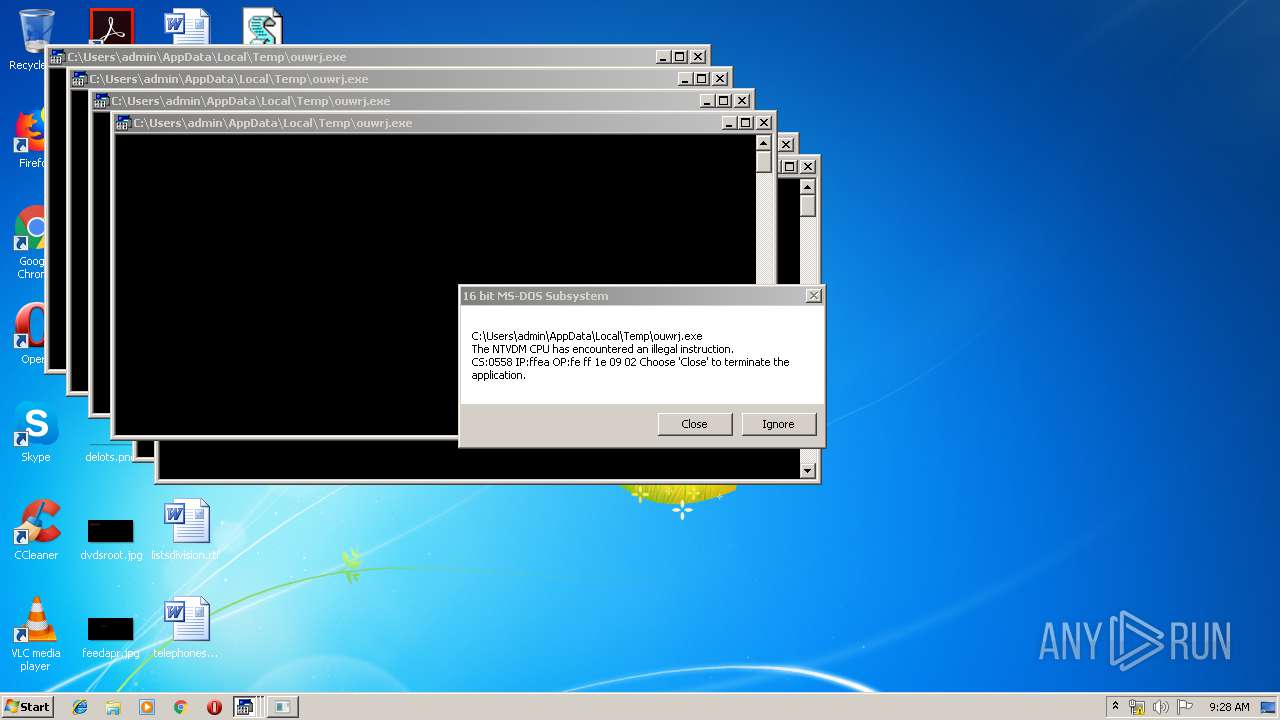
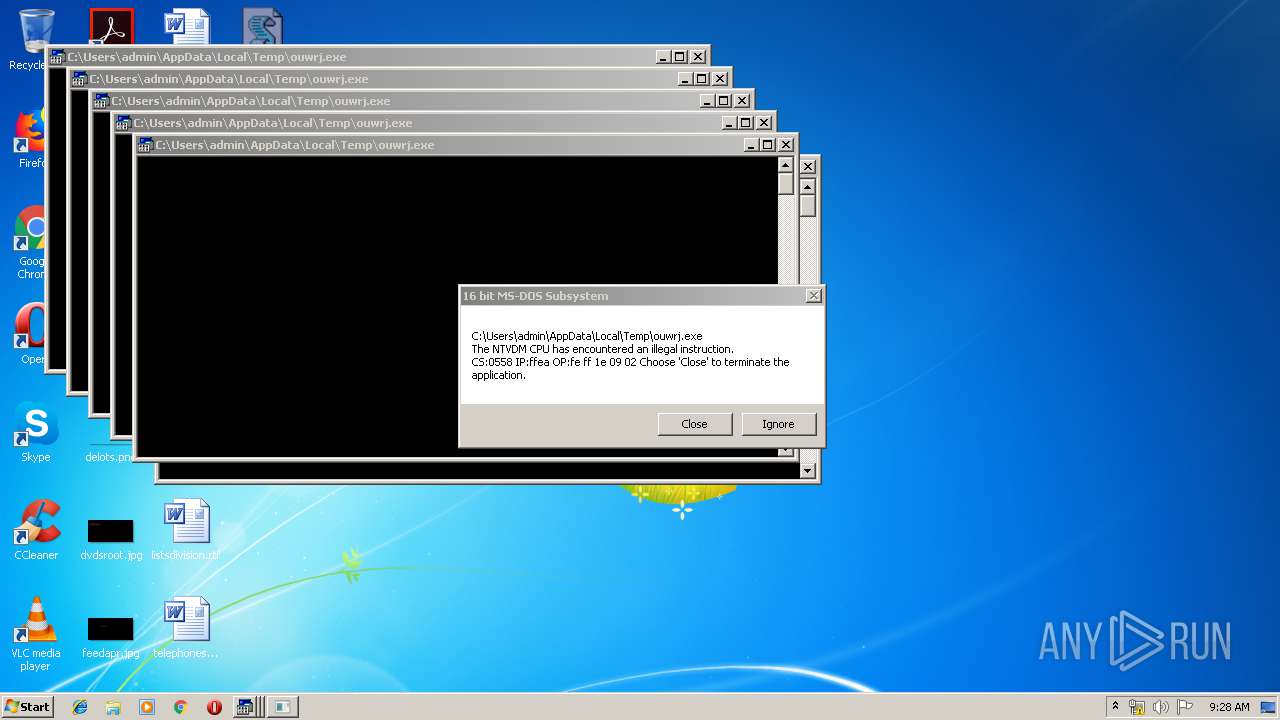
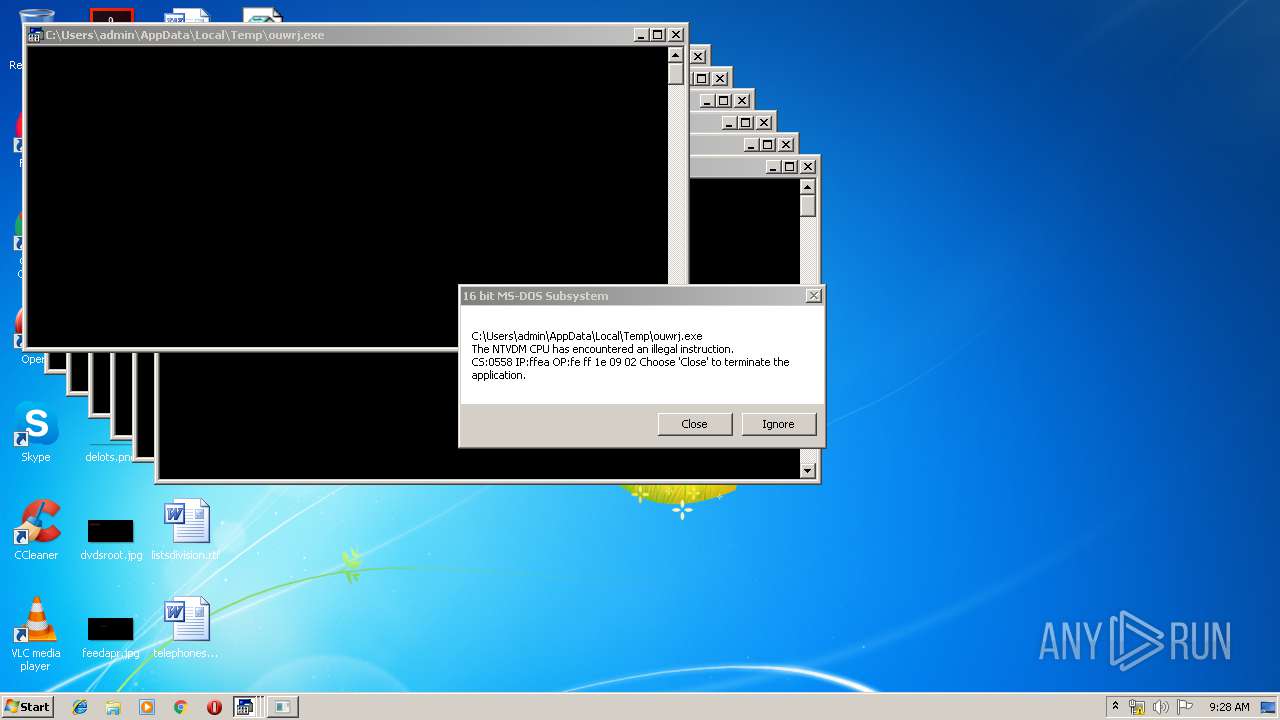
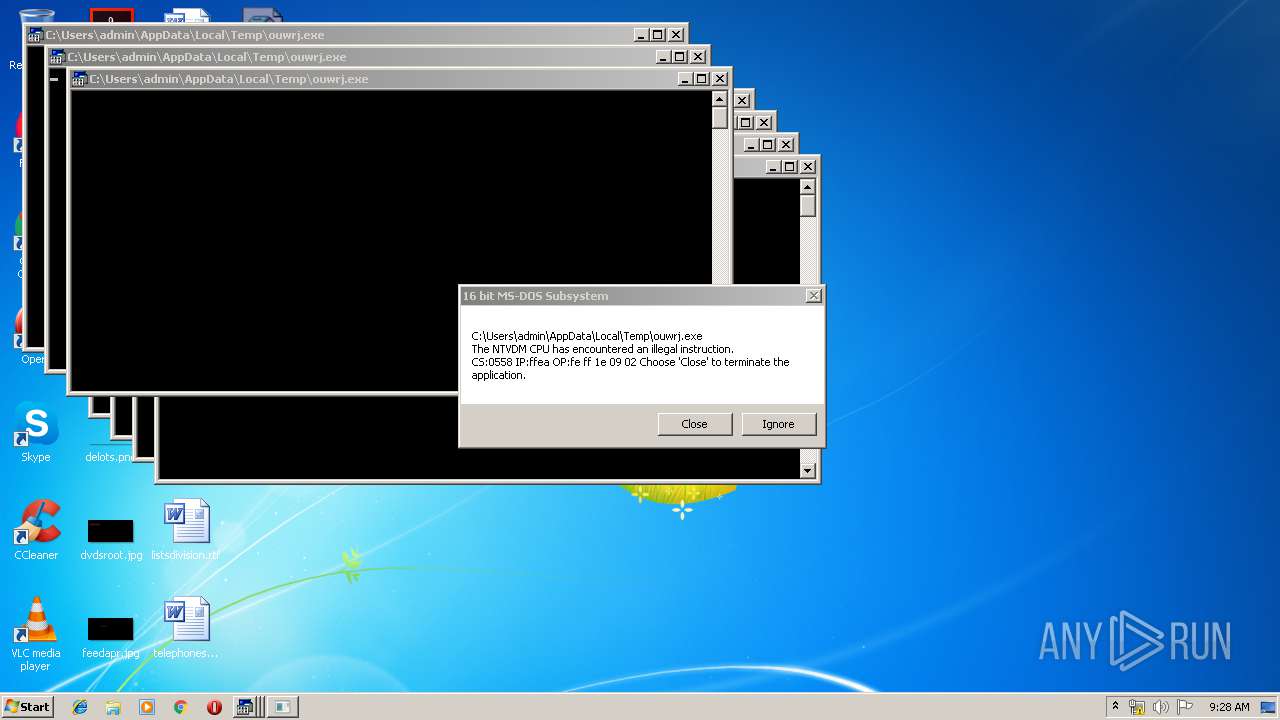
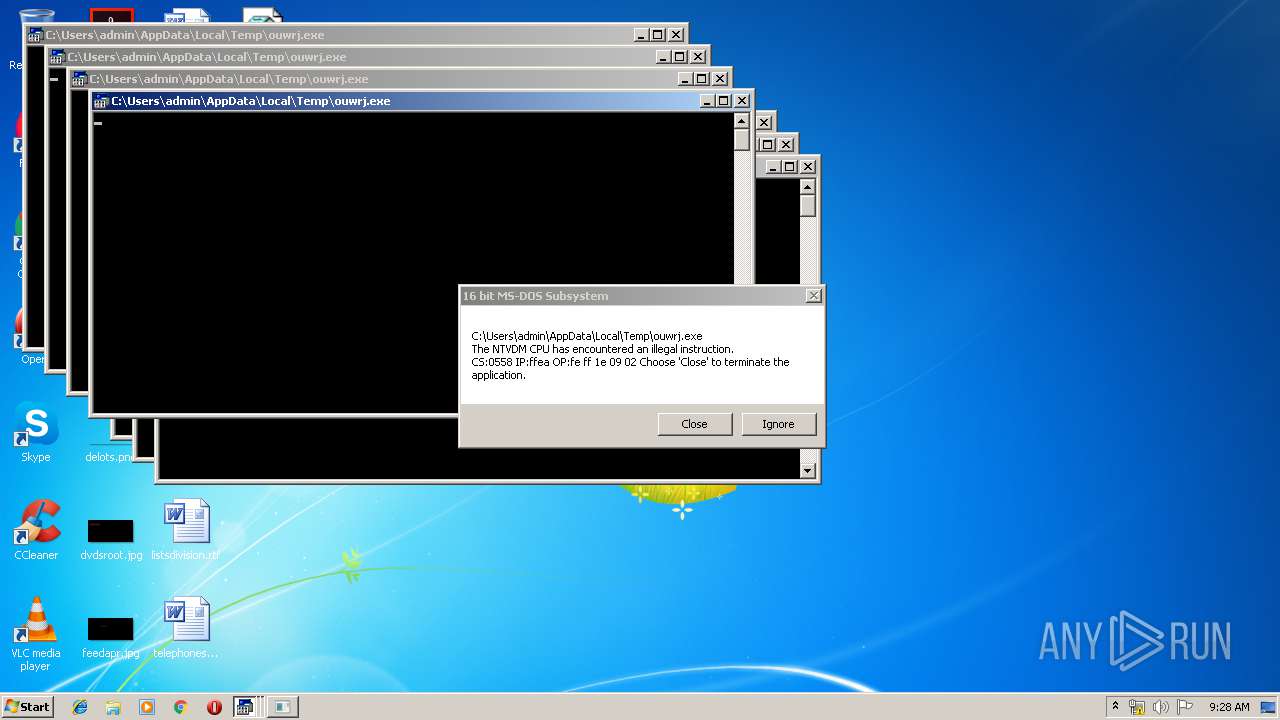
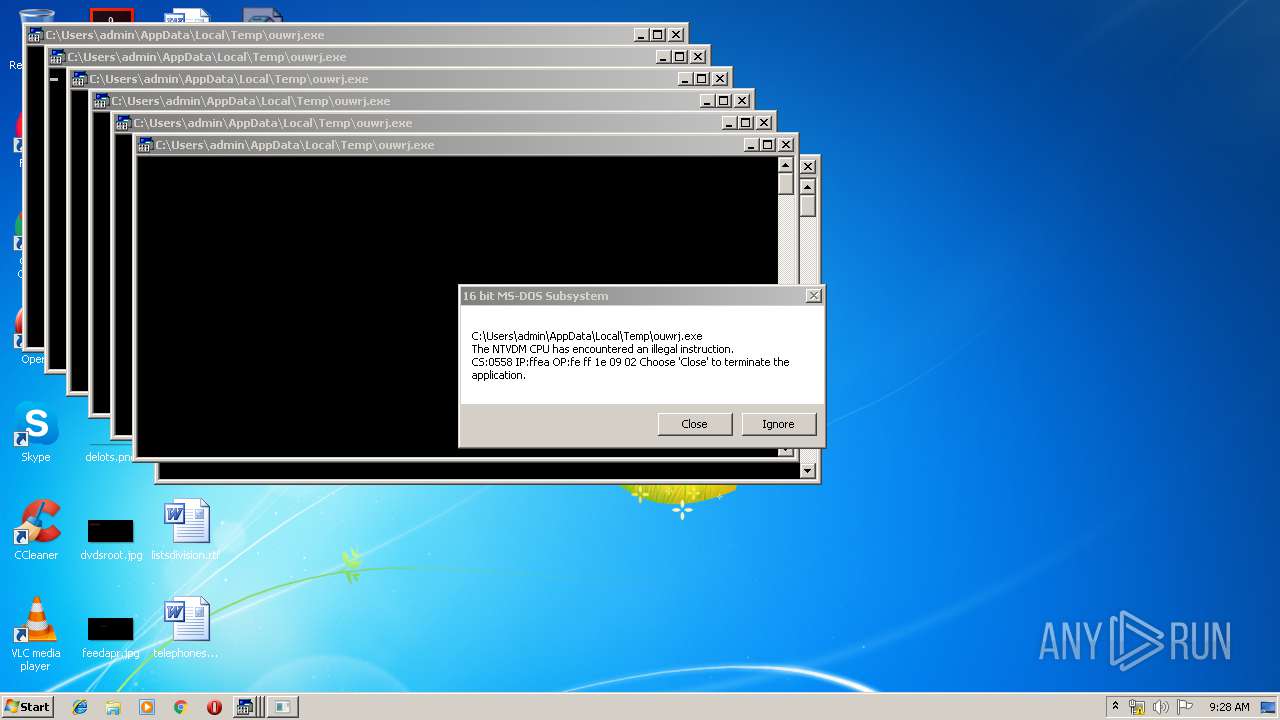
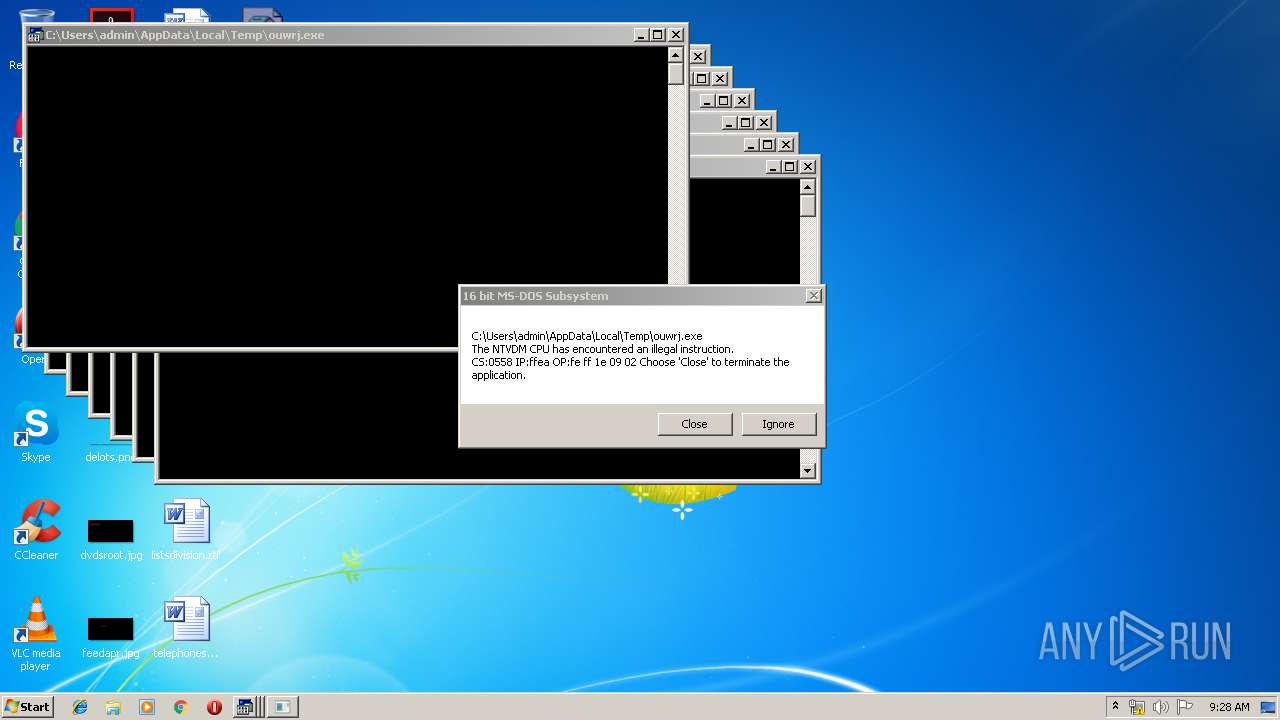
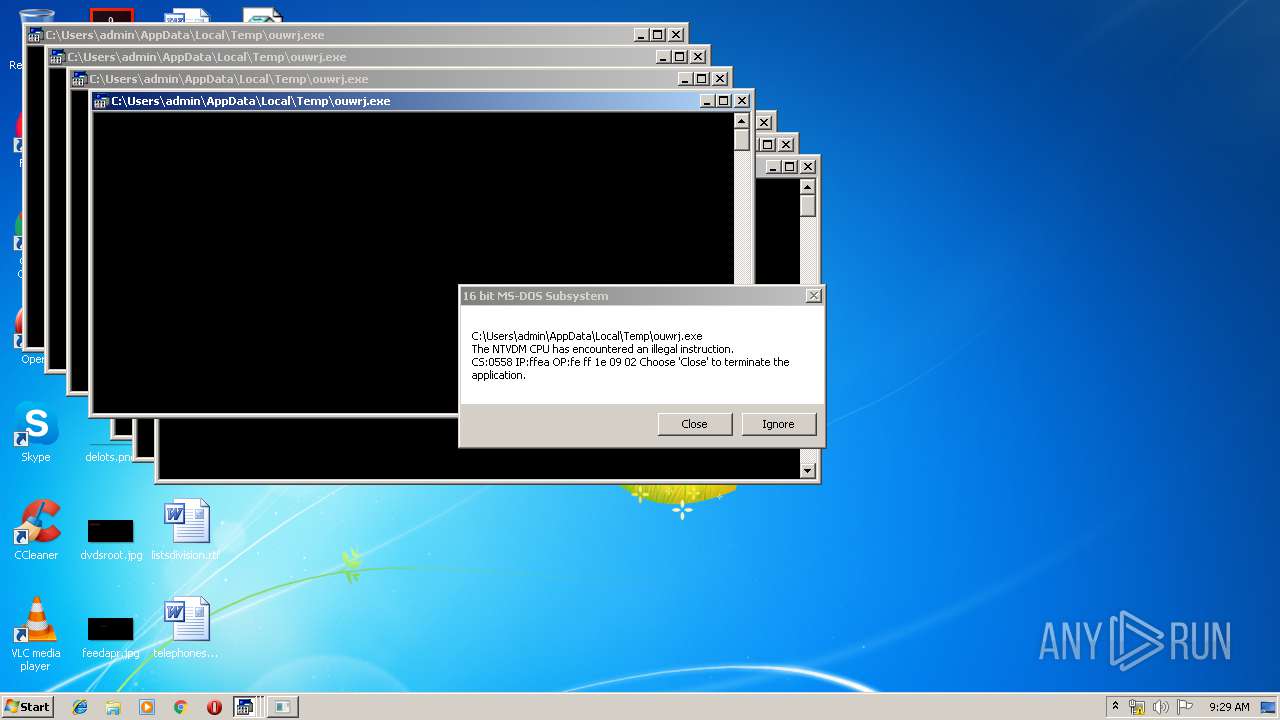
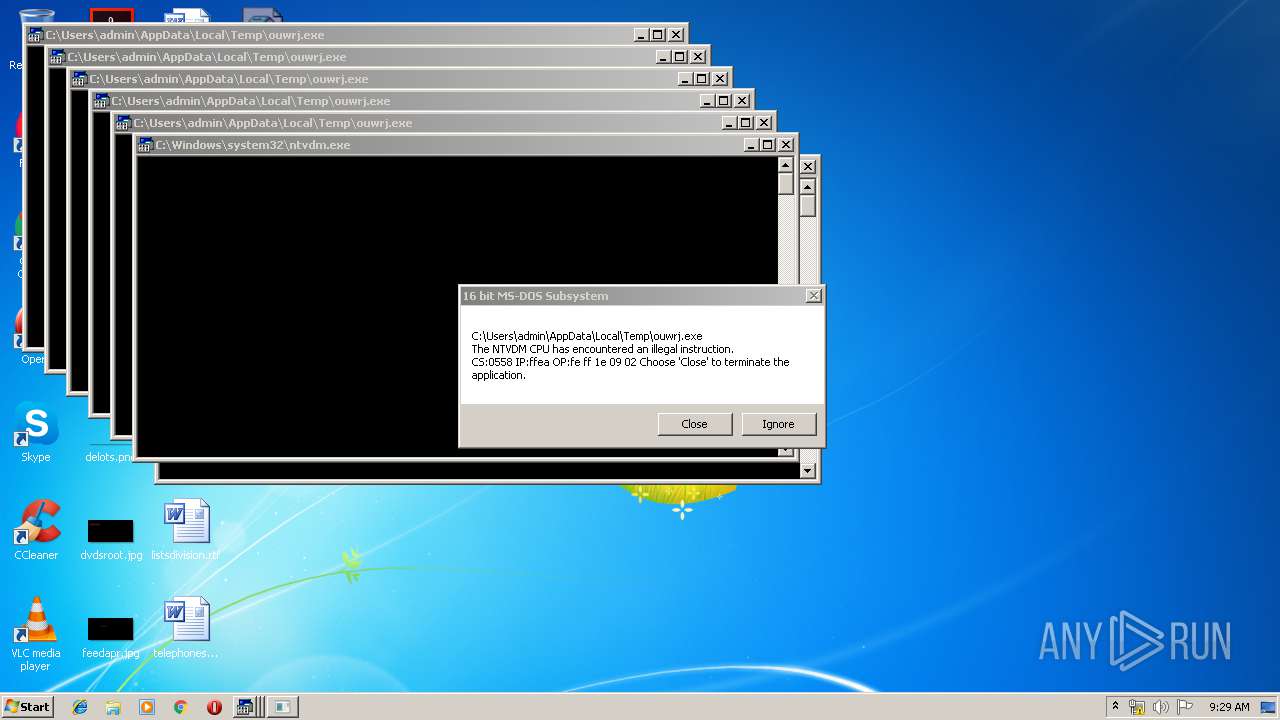
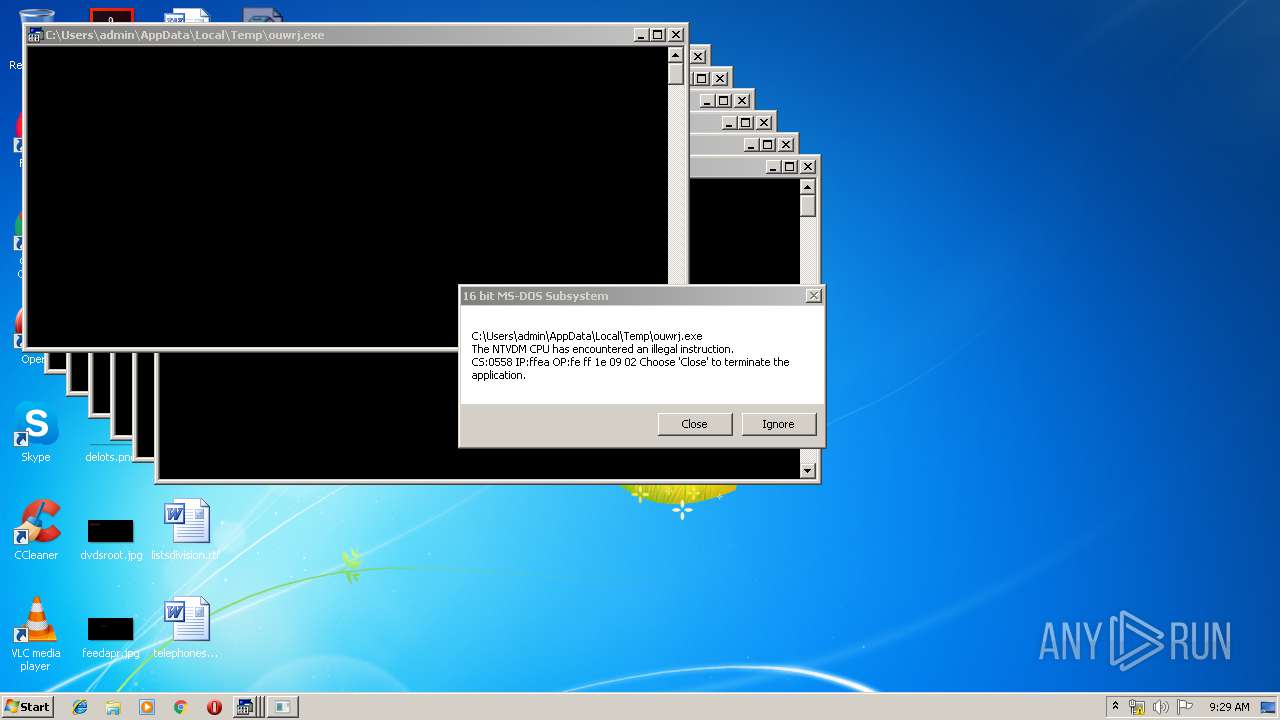
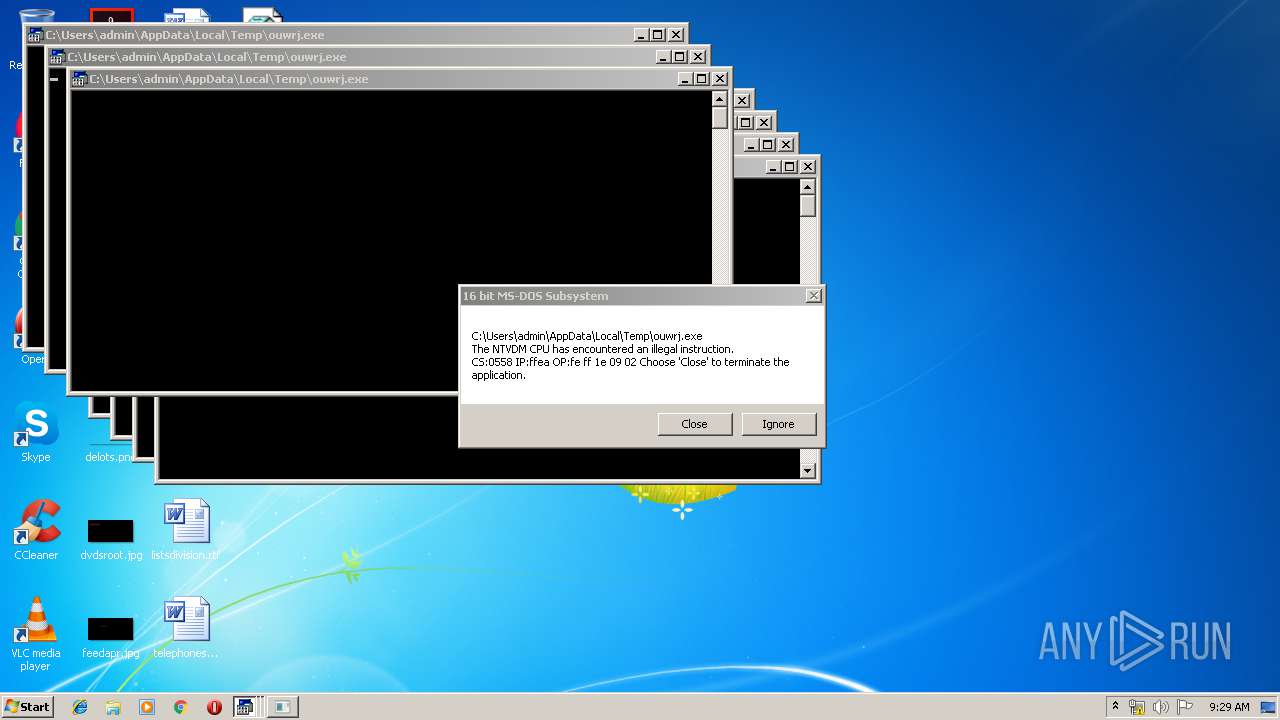
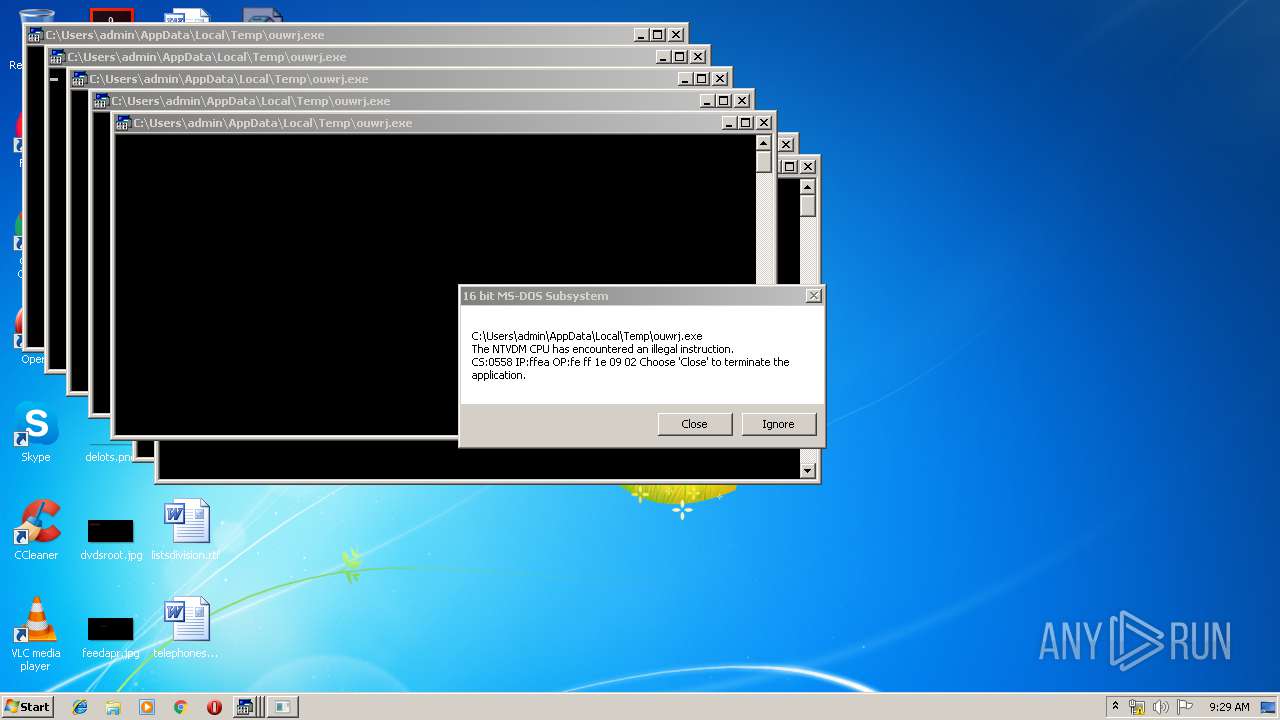
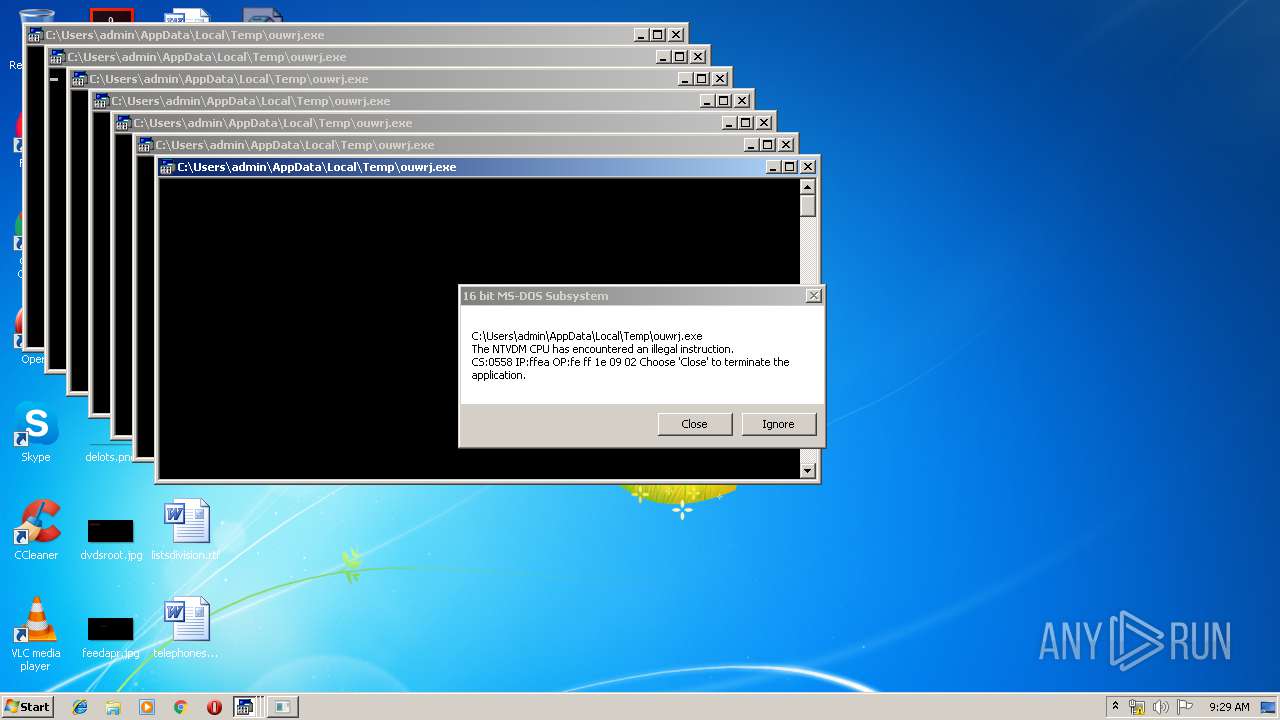
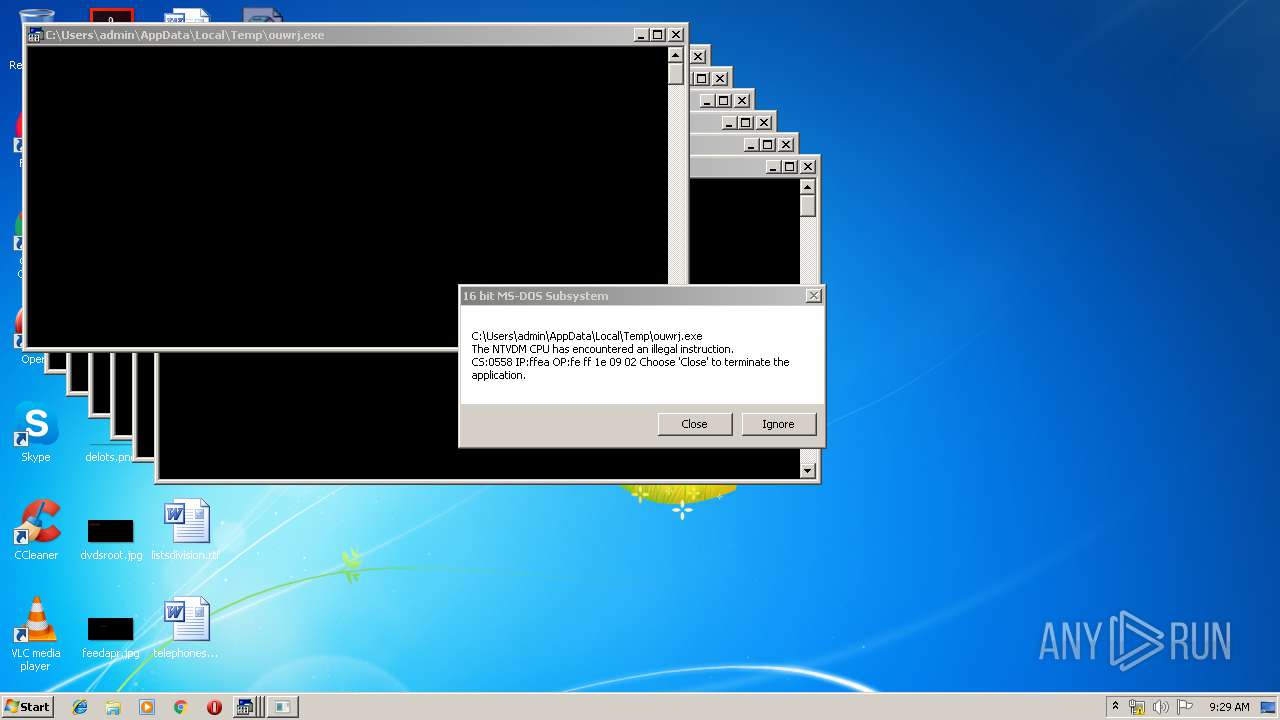
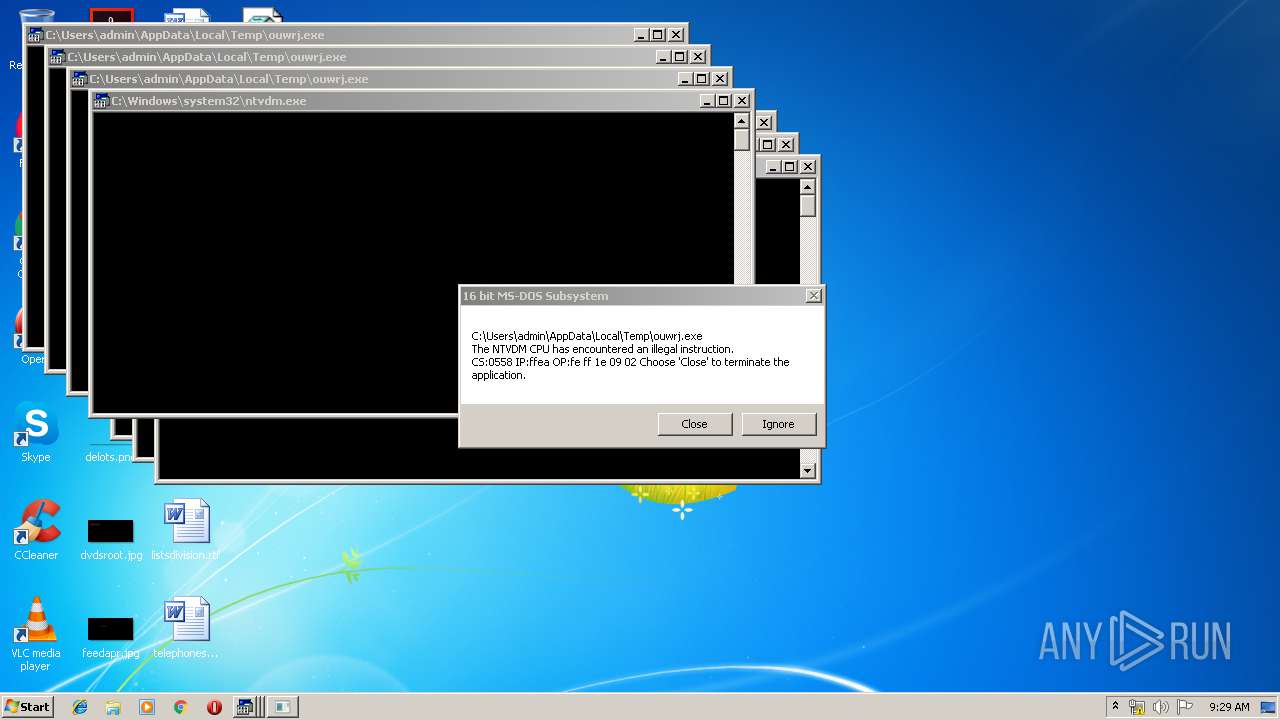
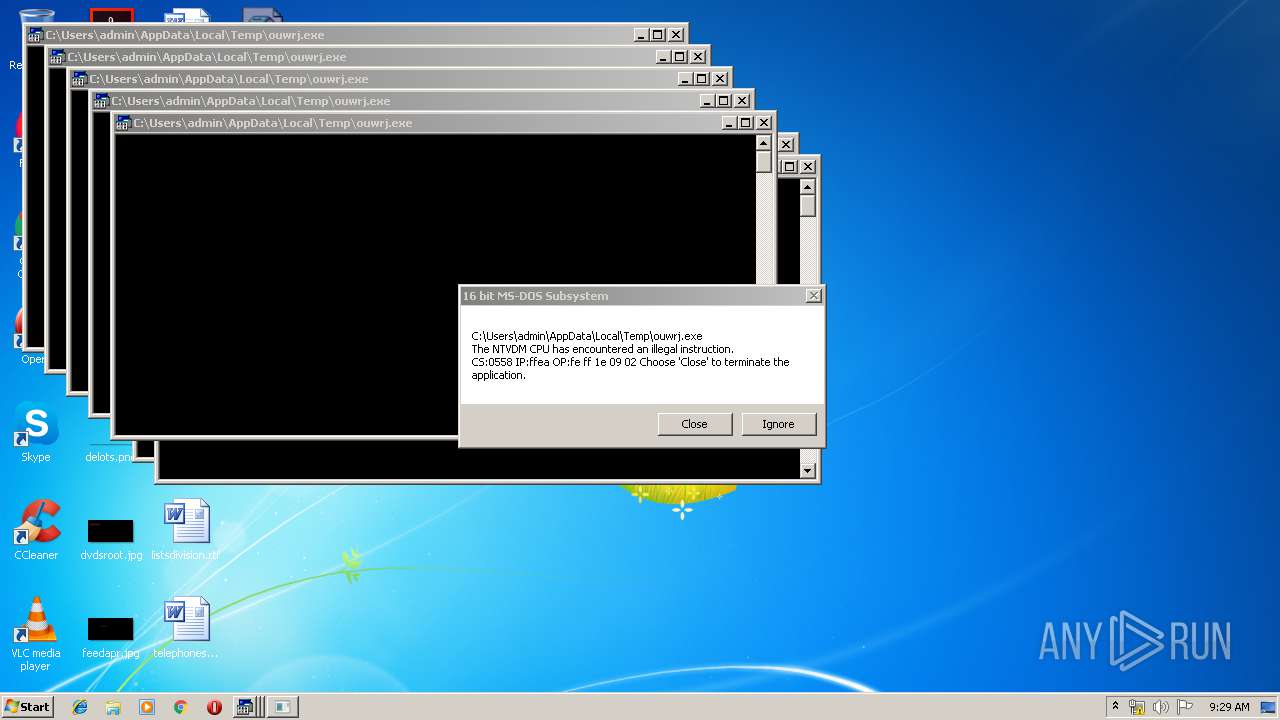
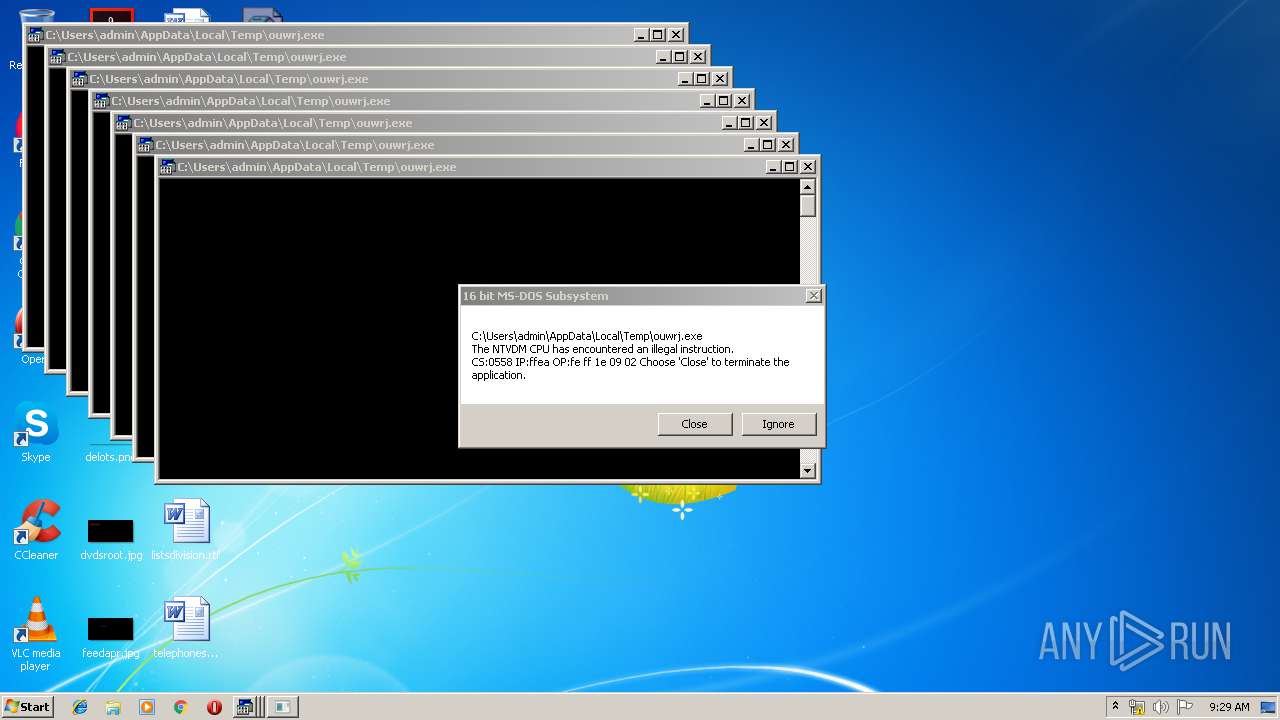
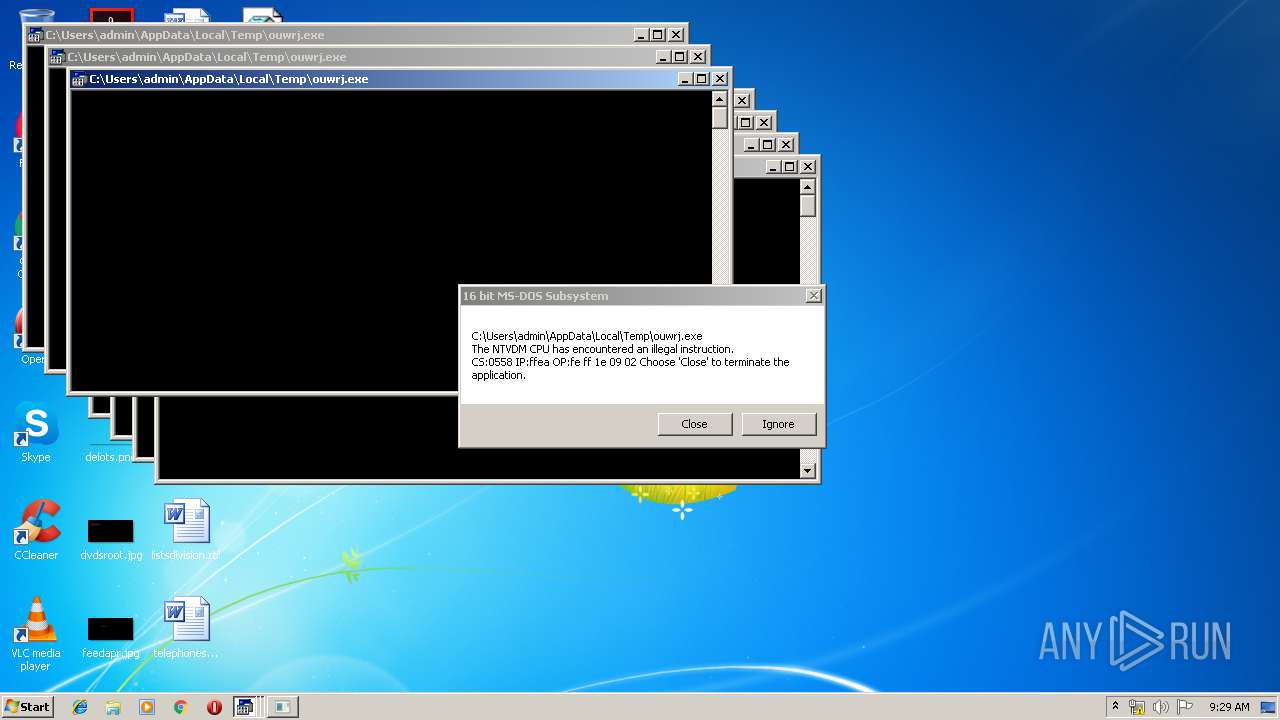
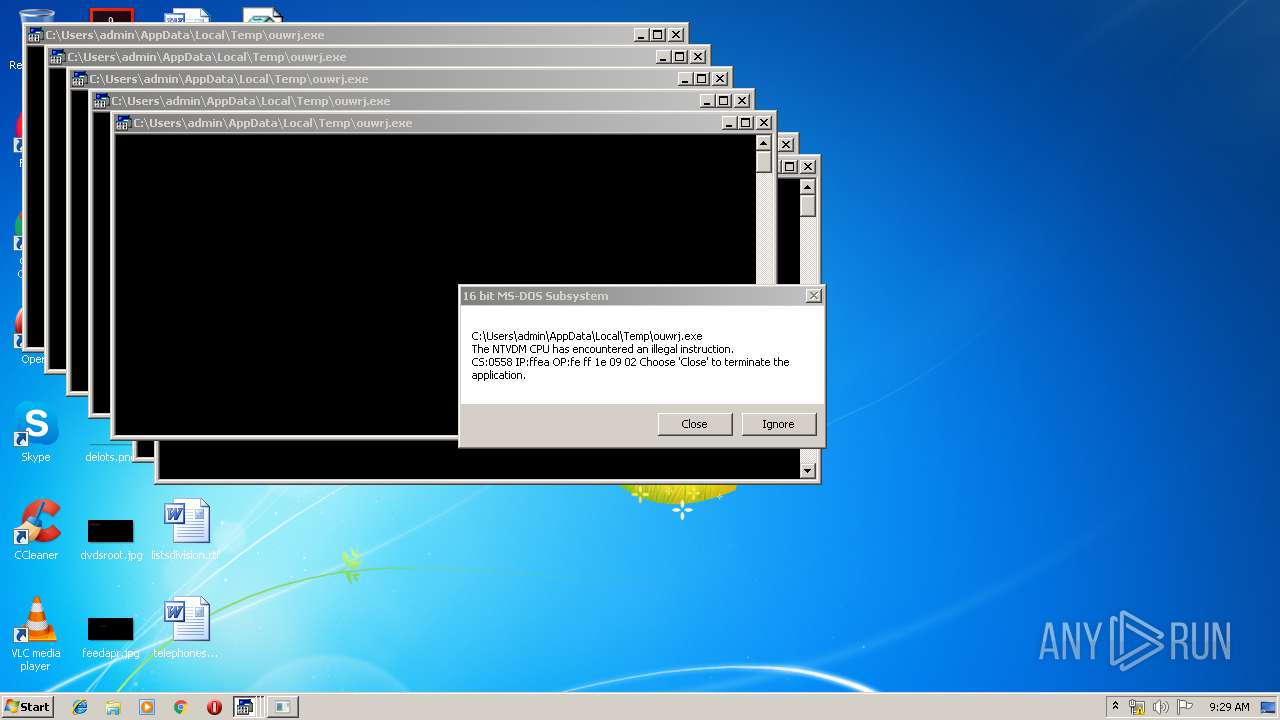
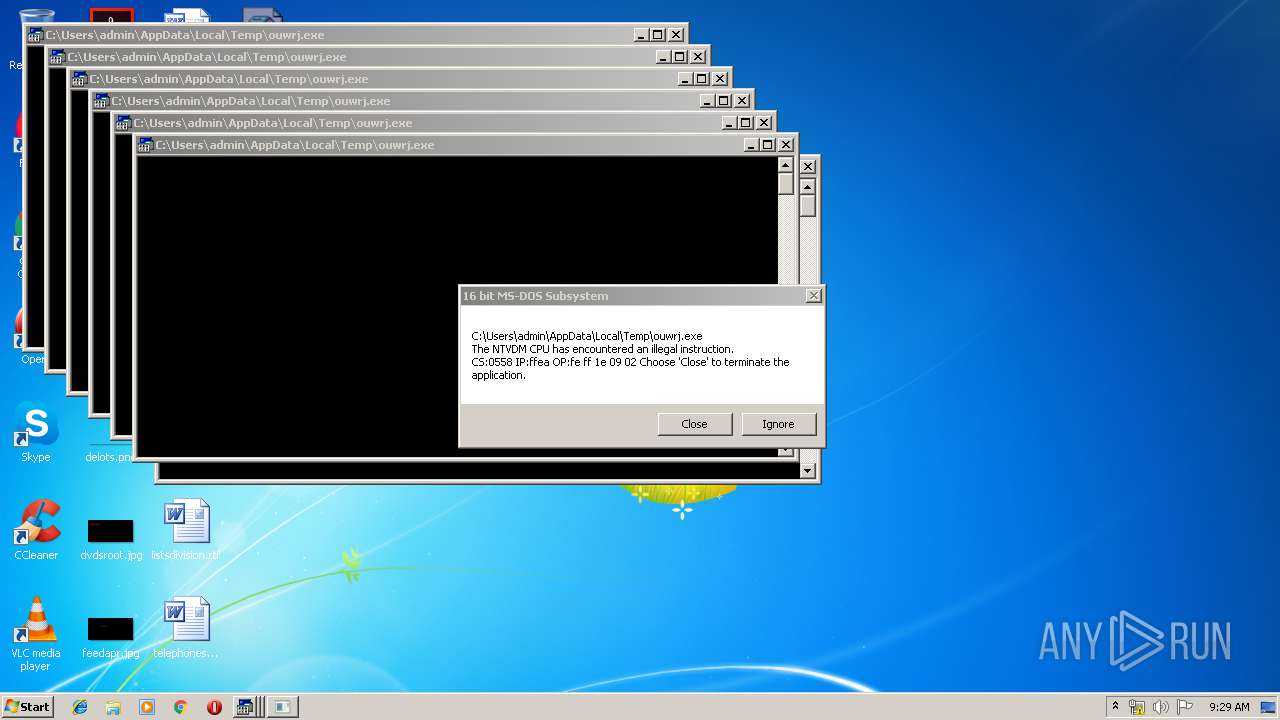
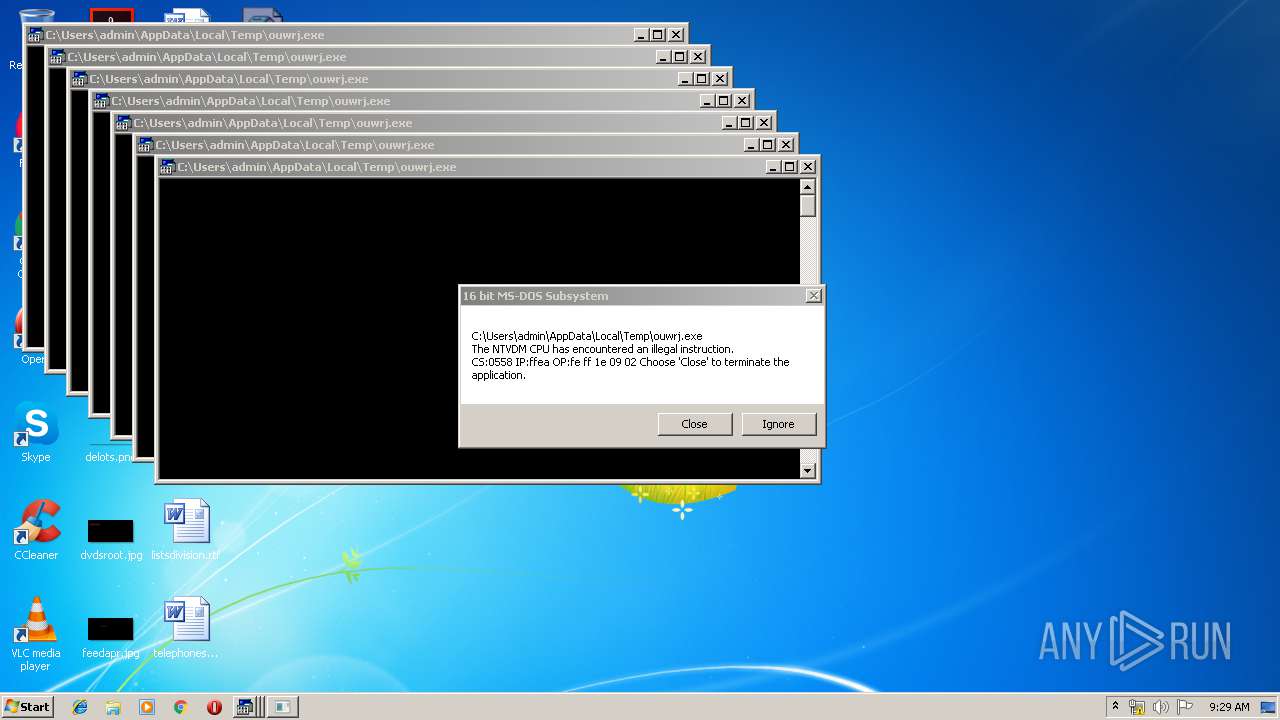
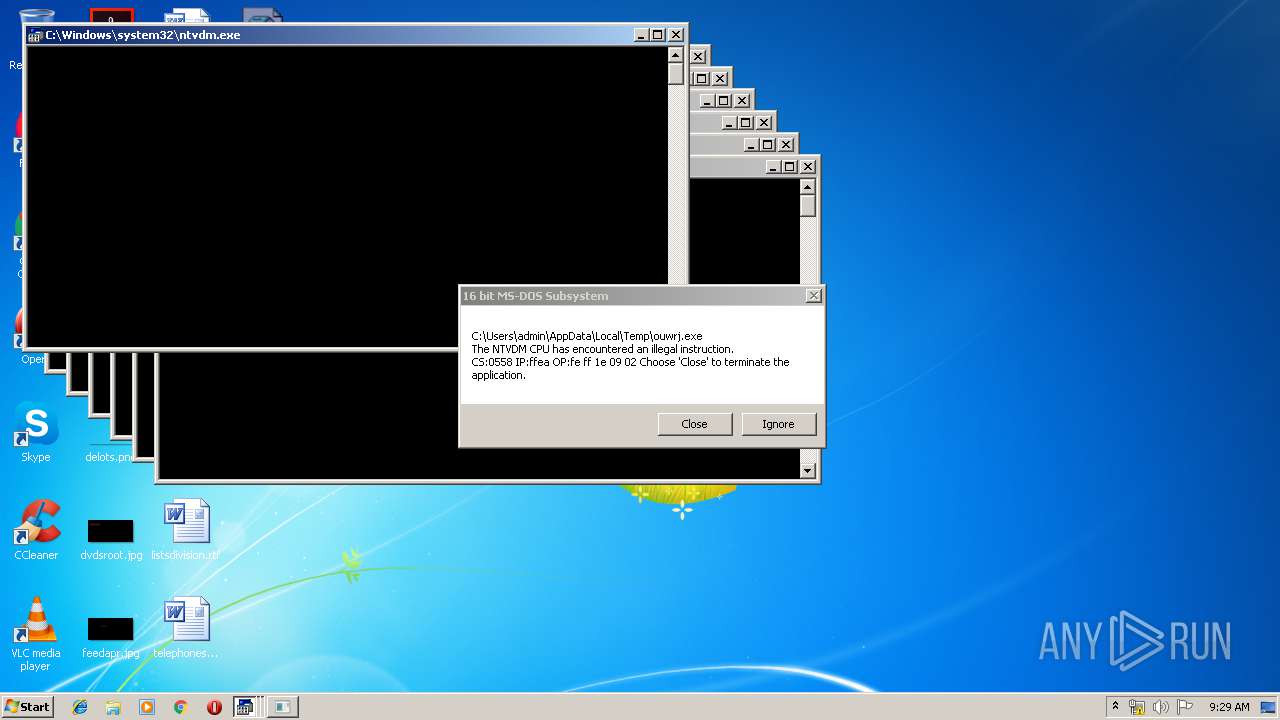
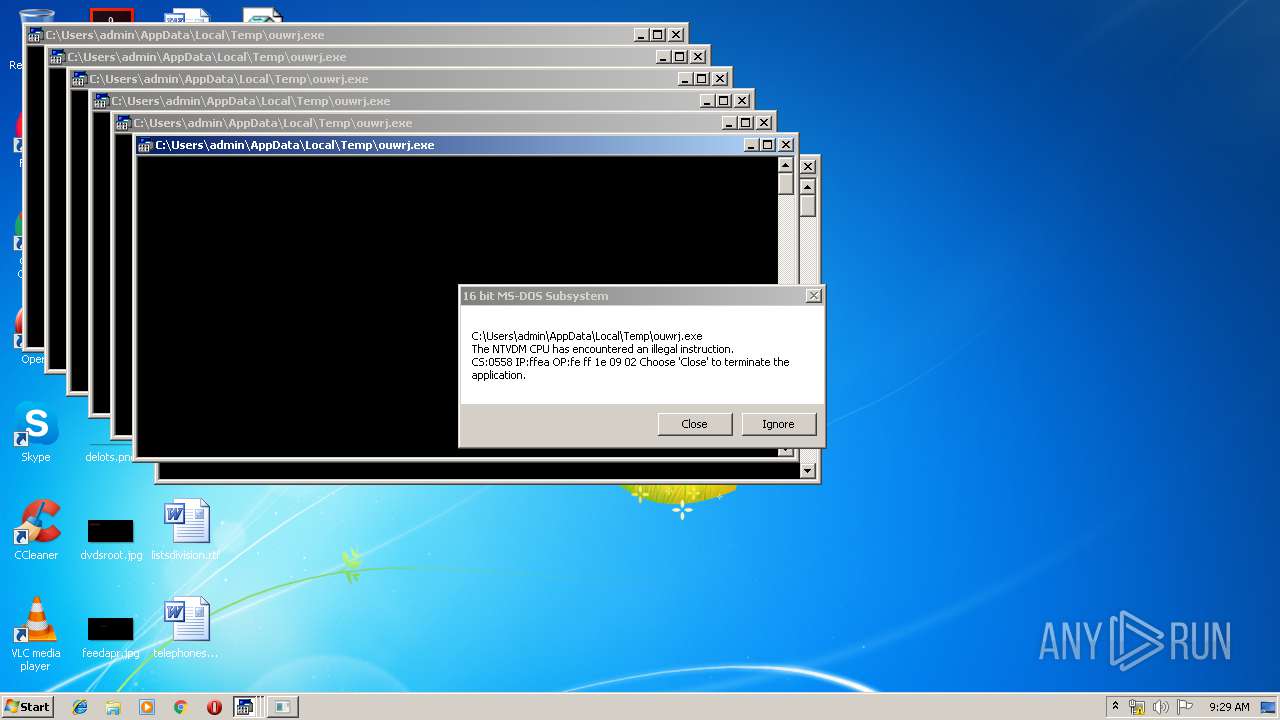
Executes application which crashes
- WScript.exe (PID: 2924)
- WScript.exe (PID: 2972)
- WScript.exe (PID: 3700)
- WScript.exe (PID: 2976)
- WScript.exe (PID: 3572)
- WScript.exe (PID: 3752)
- WScript.exe (PID: 4064)
- WScript.exe (PID: 2488)
- WScript.exe (PID: 2952)
- WScript.exe (PID: 3772)
- WScript.exe (PID: 656)
- WScript.exe (PID: 2260)
- WScript.exe (PID: 3464)
- WScript.exe (PID: 932)
- WScript.exe (PID: 3420)
- WScript.exe (PID: 3004)
- WScript.exe (PID: 696)
- WScript.exe (PID: 796)
- WScript.exe (PID: 3128)
- WScript.exe (PID: 1336)
- WScript.exe (PID: 3344)
- WScript.exe (PID: 312)
- WScript.exe (PID: 2892)
- WScript.exe (PID: 2864)
- WScript.exe (PID: 2152)
- WScript.exe (PID: 3436)
- WScript.exe (PID: 1484)
- WScript.exe (PID: 3500)
- WScript.exe (PID: 2932)
- WScript.exe (PID: 3824)
- WScript.exe (PID: 2712)
- WScript.exe (PID: 1656)
- WScript.exe (PID: 2720)
- WScript.exe (PID: 3248)
- WScript.exe (PID: 3856)
- WScript.exe (PID: 4004)
- WScript.exe (PID: 2840)
- WScript.exe (PID: 3092)
- WScript.exe (PID: 3820)
- WScript.exe (PID: 876)
- WScript.exe (PID: 3764)
- WScript.exe (PID: 3076)
- WScript.exe (PID: 2400)
- WScript.exe (PID: 2860)
- WScript.exe (PID: 3728)
- WScript.exe (PID: 3572)
- WScript.exe (PID: 2792)
- WScript.exe (PID: 3060)
- WScript.exe (PID: 3840)
- WScript.exe (PID: 6016)
- WScript.exe (PID: 5884)
- WScript.exe (PID: 5584)
- WScript.exe (PID: 4528)
- WScript.exe (PID: 3340)
- WScript.exe (PID: 4944)
- WScript.exe (PID: 5444)
- WScript.exe (PID: 4716)
- WScript.exe (PID: 5412)
- WScript.exe (PID: 5164)
- WScript.exe (PID: 5516)
- WScript.exe (PID: 6040)
- WScript.exe (PID: 5280)
- WScript.exe (PID: 5240)
- WScript.exe (PID: 6092)
- WScript.exe (PID: 5684)
- WScript.exe (PID: 5376)
INFO
Manual execution by user
- WScript.exe (PID: 3488)
- WScript.exe (PID: 4064)
- WScript.exe (PID: 2972)
- WScript.exe (PID: 2976)
- WScript.exe (PID: 3572)
- WScript.exe (PID: 2952)
- WScript.exe (PID: 3772)
- WScript.exe (PID: 2488)
- WScript.exe (PID: 3700)
- WScript.exe (PID: 2924)
- WScript.exe (PID: 2156)
- WScript.exe (PID: 2260)
- WScript.exe (PID: 656)
- WScript.exe (PID: 3420)
- WScript.exe (PID: 3004)
- WScript.exe (PID: 3464)
- WScript.exe (PID: 3108)
- WScript.exe (PID: 796)
- WScript.exe (PID: 932)
- WScript.exe (PID: 696)
- WScript.exe (PID: 3484)
- WScript.exe (PID: 2892)
- WScript.exe (PID: 1336)
- WScript.exe (PID: 3344)
- WScript.exe (PID: 312)
- WScript.exe (PID: 2224)
- WScript.exe (PID: 2864)
- WScript.exe (PID: 3128)
- WScript.exe (PID: 2152)
- WScript.exe (PID: 3436)
- WScript.exe (PID: 2932)
- WScript.exe (PID: 1484)
- WScript.exe (PID: 3500)
- WScript.exe (PID: 1656)
- WScript.exe (PID: 3824)
- WScript.exe (PID: 2720)
- WScript.exe (PID: 3856)
- WScript.exe (PID: 3248)
- WScript.exe (PID: 3340)
- WScript.exe (PID: 2712)
- WScript.exe (PID: 4004)
- WScript.exe (PID: 3092)
- WScript.exe (PID: 3820)
- WScript.exe (PID: 2840)
- WScript.exe (PID: 3764)
- WScript.exe (PID: 916)
- WScript.exe (PID: 2252)
- WScript.exe (PID: 876)
- WScript.exe (PID: 3808)
- WScript.exe (PID: 2400)
- WScript.exe (PID: 3076)
- WScript.exe (PID: 3728)
- WScript.exe (PID: 2860)
- WScript.exe (PID: 2792)
- WScript.exe (PID: 3572)
- WScript.exe (PID: 3060)
- WScript.exe (PID: 3840)
- WScript.exe (PID: 4100)
- WScript.exe (PID: 4812)
- WScript.exe (PID: 5884)
- WScript.exe (PID: 5584)
- WScript.exe (PID: 4976)
- WScript.exe (PID: 6016)
- WScript.exe (PID: 4528)
- WScript.exe (PID: 4944)
- WScript.exe (PID: 5444)
- WScript.exe (PID: 4924)
- WScript.exe (PID: 4716)
- WScript.exe (PID: 5412)
- WScript.exe (PID: 5164)
- WScript.exe (PID: 5164)
- WScript.exe (PID: 5708)
- WScript.exe (PID: 5008)
- WScript.exe (PID: 6040)
- WScript.exe (PID: 5516)
- WScript.exe (PID: 5280)
- WScript.exe (PID: 4720)
- WScript.exe (PID: 5240)
- WScript.exe (PID: 5684)
- WScript.exe (PID: 6092)
- WScript.exe (PID: 5376)
Reads settings of System Certificates
- WScript.exe (PID: 4812)
- WScript.exe (PID: 4720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
248
Monitored processes
148
Malicious processes
0
Suspicious processes
66
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\4367890.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 628 | "C:\Windows\system32\ntvdm.exe" -i25 | C:\Windows\system32\ntvdm.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 656 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\4367890.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 696 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\4367890.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 796 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\4367890.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 876 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\4367890.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 916 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\4367890.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 932 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\4367890.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 968 | "C:\Windows\system32\ntvdm.exe" -i23 | C:\Windows\system32\ntvdm.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | "C:\Windows\system32\ntvdm.exe" -i2a | C:\Windows\system32\ntvdm.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 427
Read events
4 267
Write events
160
Delete events
0
Modification events
| (PID) Process: | (3488) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2156) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3108) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3484) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2224) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2252) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (916) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3808) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4100) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4812) WScript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
0
Text files
79
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2916 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF751.tmp | — | |
MD5:— | SHA256:— | |||
| 2916 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF752.tmp | — | |
MD5:— | SHA256:— | |||
| 3376 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs868.tmp | — | |
MD5:— | SHA256:— | |||
| 3376 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs869.tmp | — | |
MD5:— | SHA256:— | |||
| 1816 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsABA.tmp | — | |
MD5:— | SHA256:— | |||
| 1816 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsACA.tmp | — | |
MD5:— | SHA256:— | |||
| 3700 | WScript.exe | C: | — | |
MD5:— | SHA256:— | |||
| 3164 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs19EC.tmp | — | |
MD5:— | SHA256:— | |||
| 3164 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs19FD.tmp | — | |
MD5:— | SHA256:— | |||
| 2976 | WScript.exe | C: | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
82
DNS requests
12
Threats
66
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3752 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://bjaoude.com/typical_solutions.php | US | xml | 345 b | malicious |
2488 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://ajjtech.com/promote.php | US | xml | 345 b | malicious |
3700 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://alemanautos.cl/audipromo.php | US | xml | 345 b | malicious |
3420 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://alemanautos.cl/audipromo.php | US | xml | 345 b | malicious |
2952 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://ajjtech.com/promote.php | US | xml | 345 b | malicious |
2972 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://bjaoude.com/typical_solutions.php | US | xml | 345 b | malicious |
3004 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://alkalbany.net/oracle_test.php | US | xml | 345 b | suspicious |
1336 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://alphatronic.com.my/googleInvesigations_89DE113109AA.php | US | xml | 345 b | malicious |
3572 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://alphatronic.com.my/googleInvesigations_89DE113109AA.php | US | xml | 345 b | malicious |
3464 | WScript.exe | GET | 404 | 67.23.226.159:80 | http://bjaoude.com/typical_solutions.php | US | xml | 345 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3752 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
4064 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
3700 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
2488 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
3488 | WScript.exe | 67.23.226.159:443 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
2972 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
2976 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
2924 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
3772 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
2952 | WScript.exe | 67.23.226.159:80 | bjaoude.com | HostDime.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bjaoude.com |
| malicious |
www.algehr.org |
| malicious |
alemanautos.cl |
| malicious |
ajjtech.com |
| malicious |
amafest.net |
| malicious |
alphatronic.com.my |
| malicious |
alcartgroup.com |
| malicious |
bizcraftindia.com |
| malicious |
aminvali.ca |
| malicious |
alkalbany.net |
| suspicious |
Threats
66 ETPRO signatures available at the full report