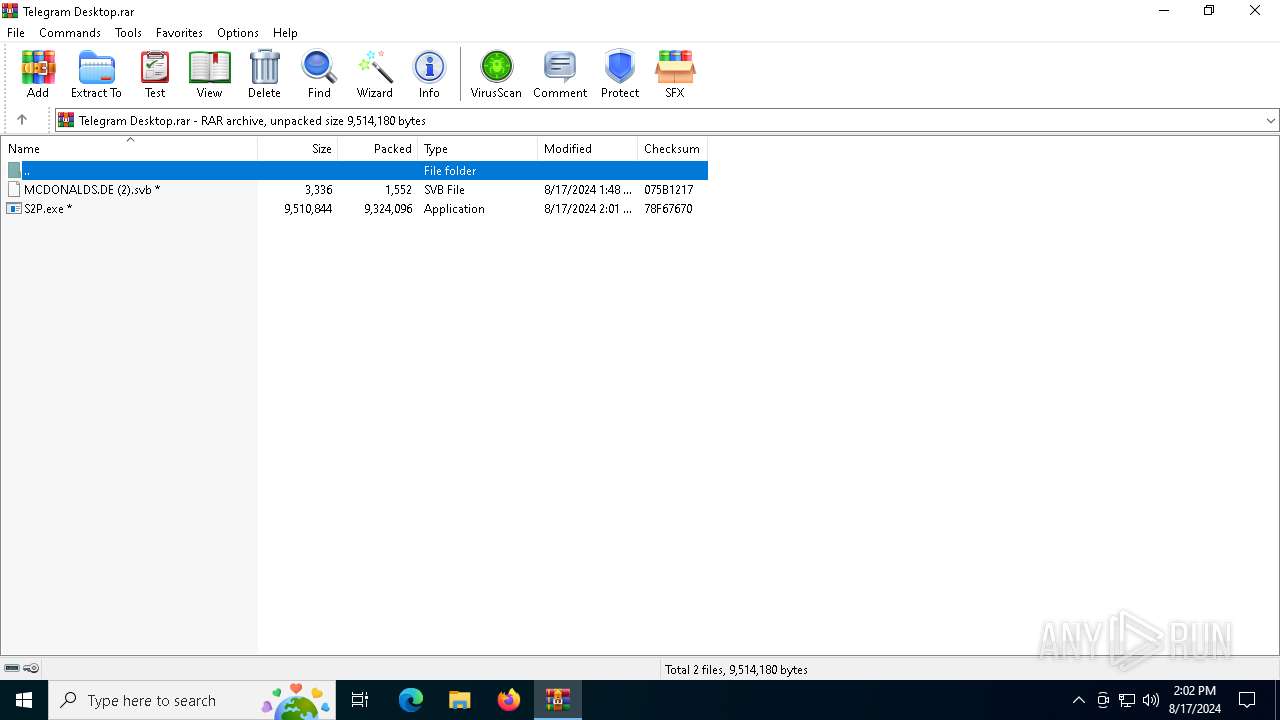
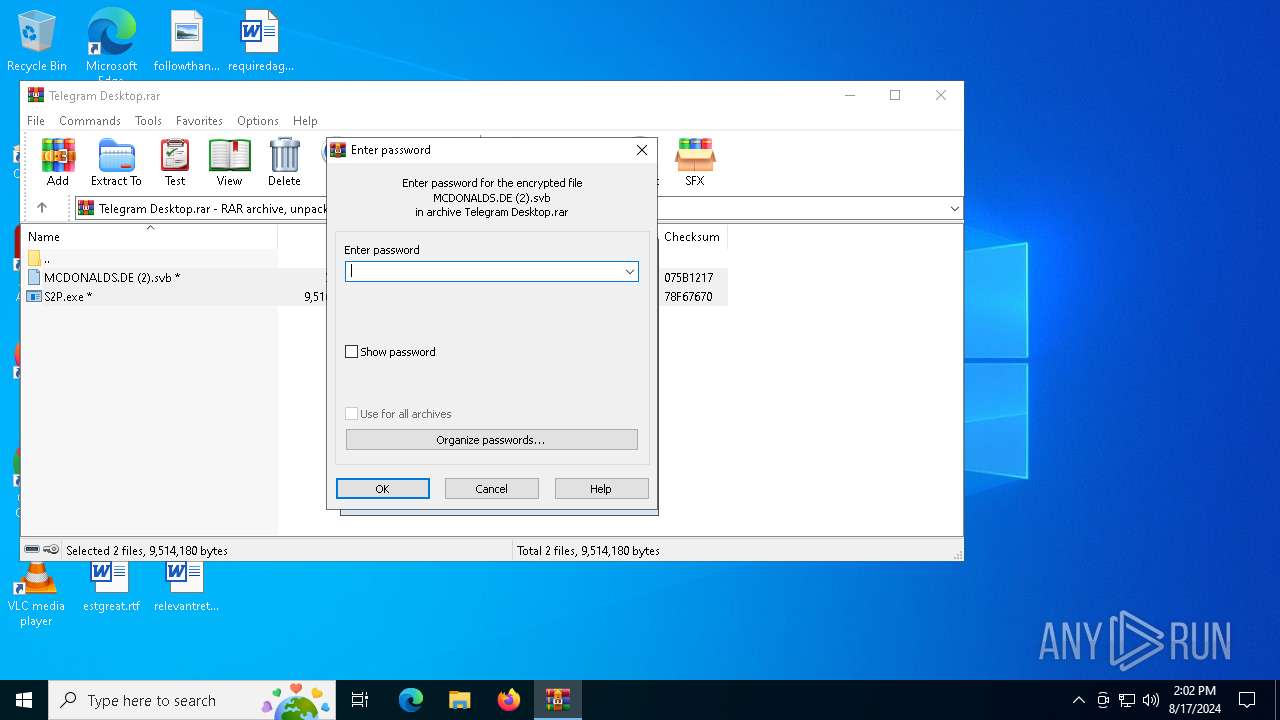
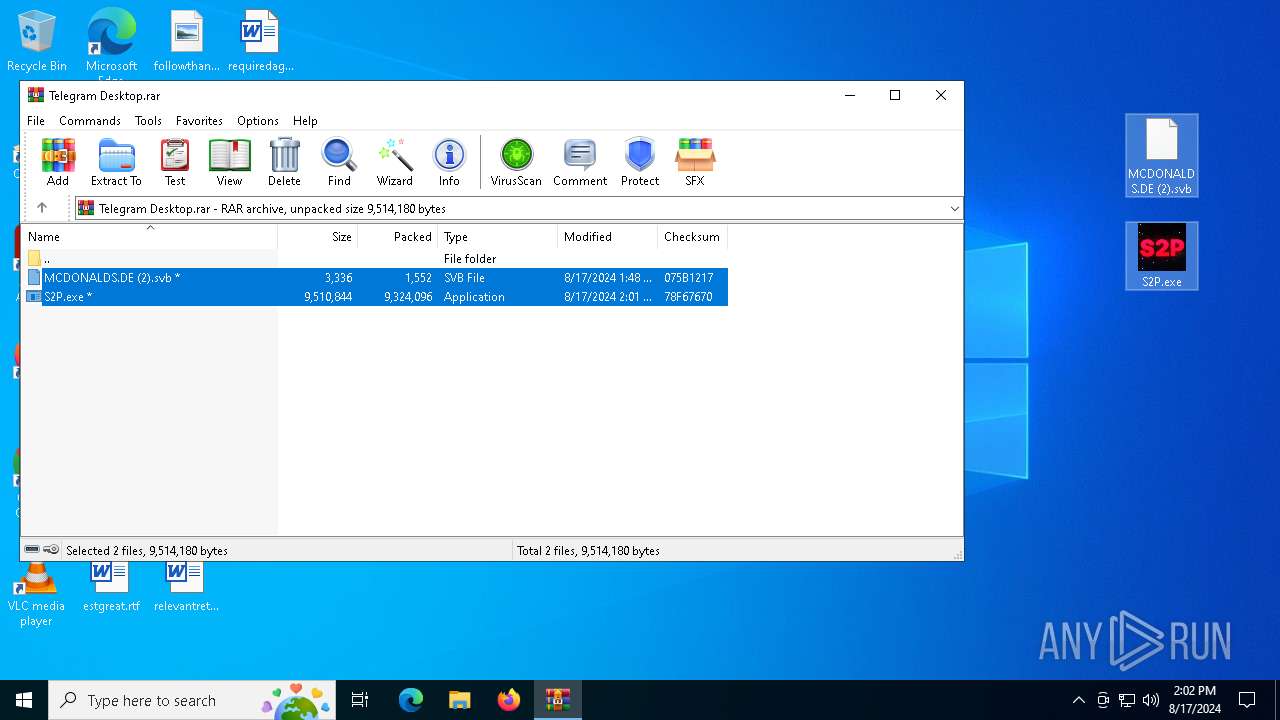
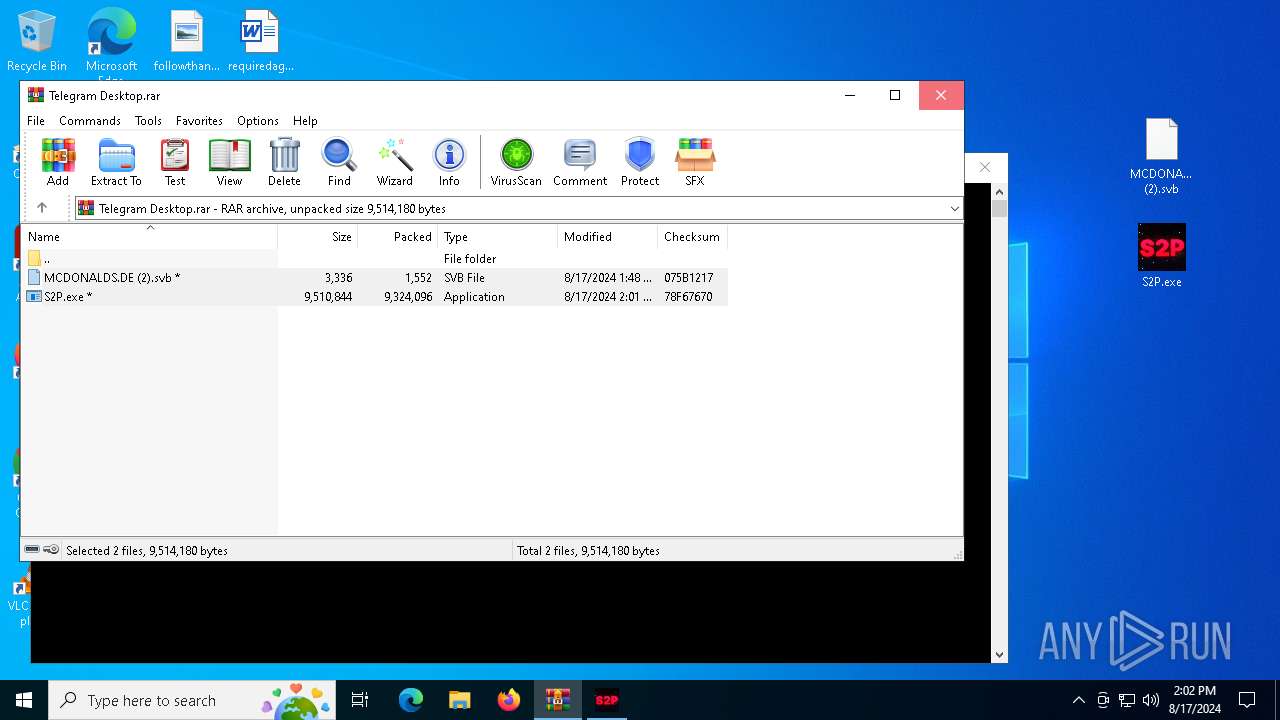
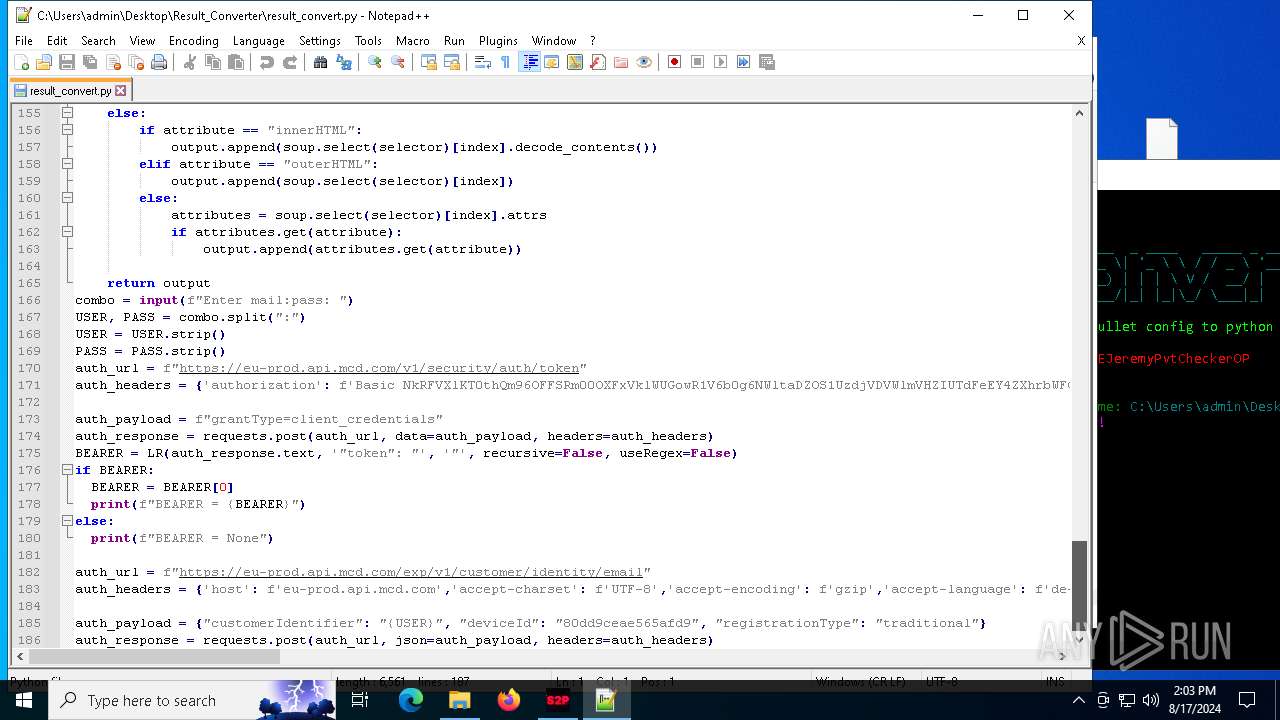
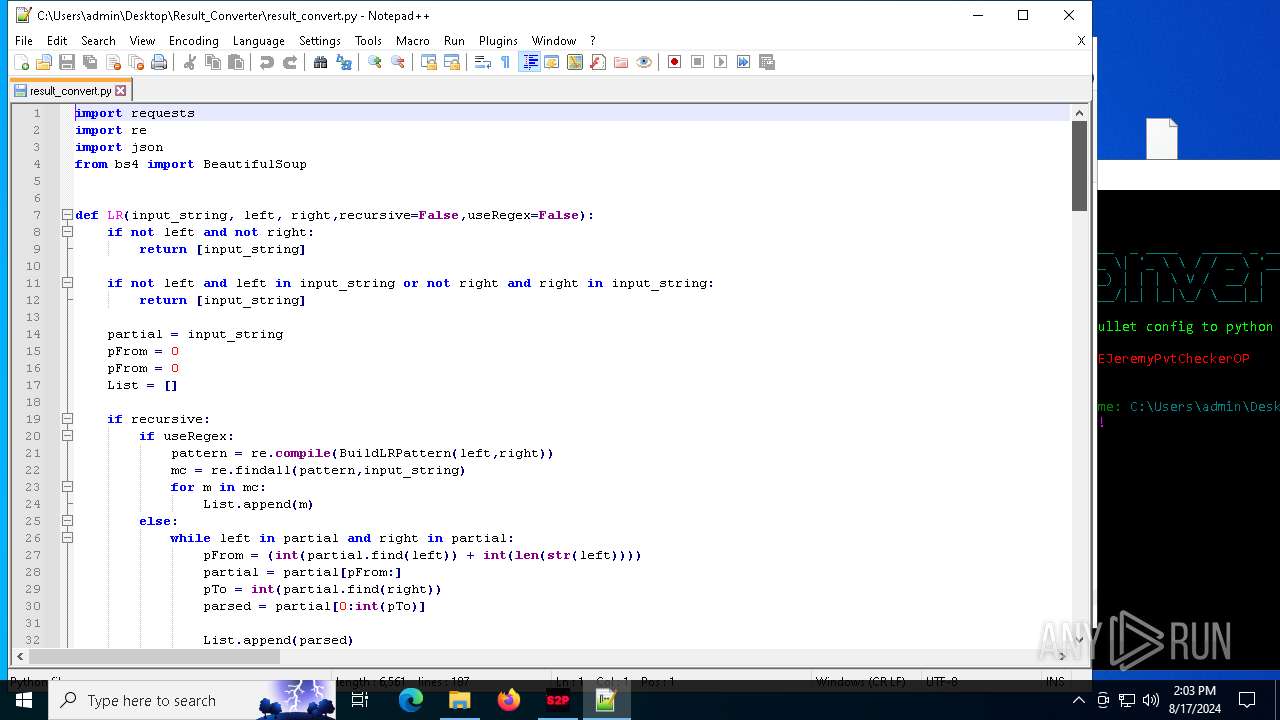
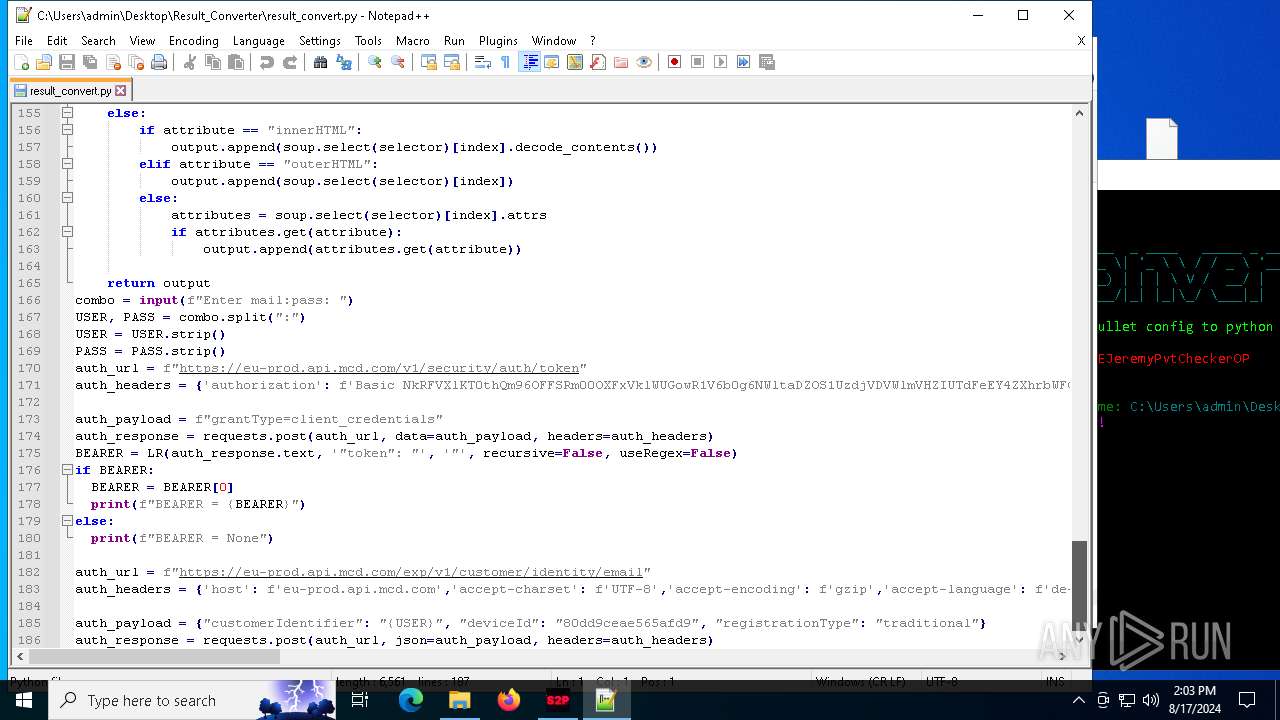
| File name: | Telegram Desktop.rar |
| Full analysis: | https://app.any.run/tasks/fe2b75a0-1f32-4da2-a21c-90ed821b0856 |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2024, 14:02:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DD991CFD0B635E4EE2C6BA4653FADF95 |
| SHA1: | 96BF402A4053C113BC0F4A6A4A2F57AD4CDA1ECC |
| SHA256: | 058BAA02BB6AC7735C6CC501ED304FB79A624B8447D1BAC122BC5CA6A3500F53 |
| SSDEEP: | 98304:m0qzWyMKxYgisKaFVInKtzqnApzRR3jJDur1yAyHeKCmJB/MiPM5bz51UEapM81M:lppVCmIj7fG81N39OGLVapjtuSN |
MALICIOUS
No malicious indicators.SUSPICIOUS
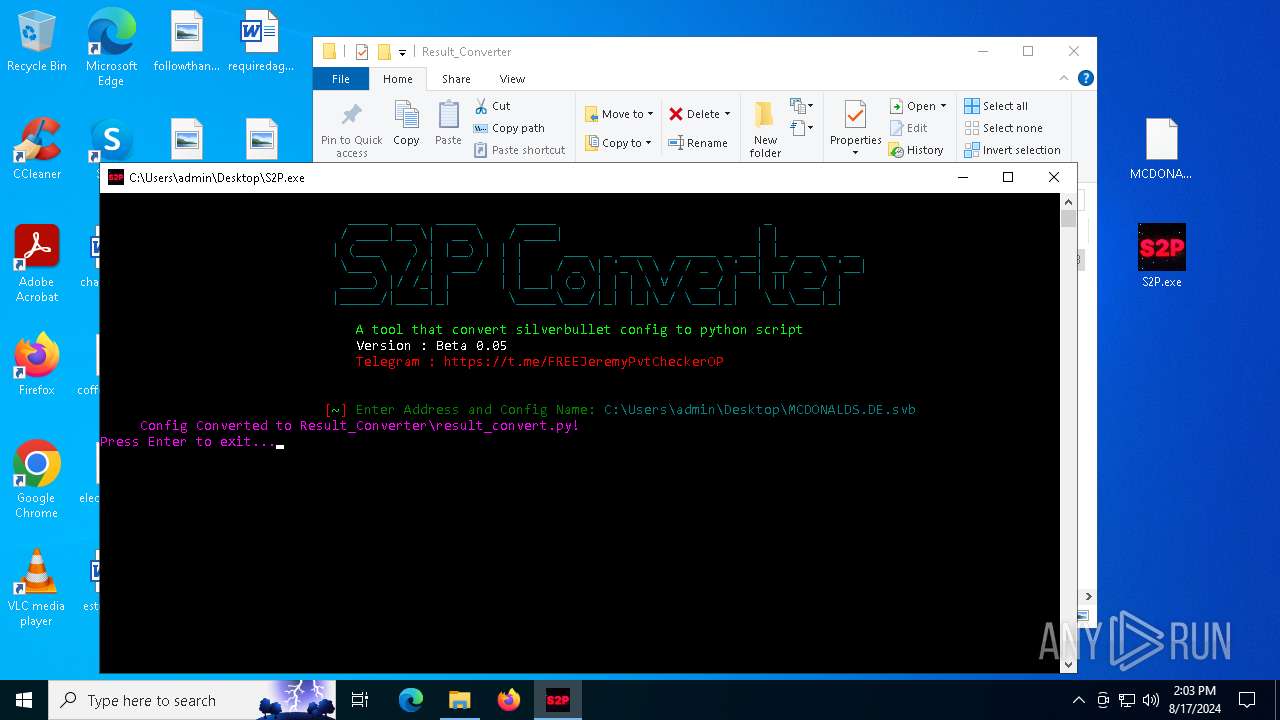
Process drops legitimate windows executable
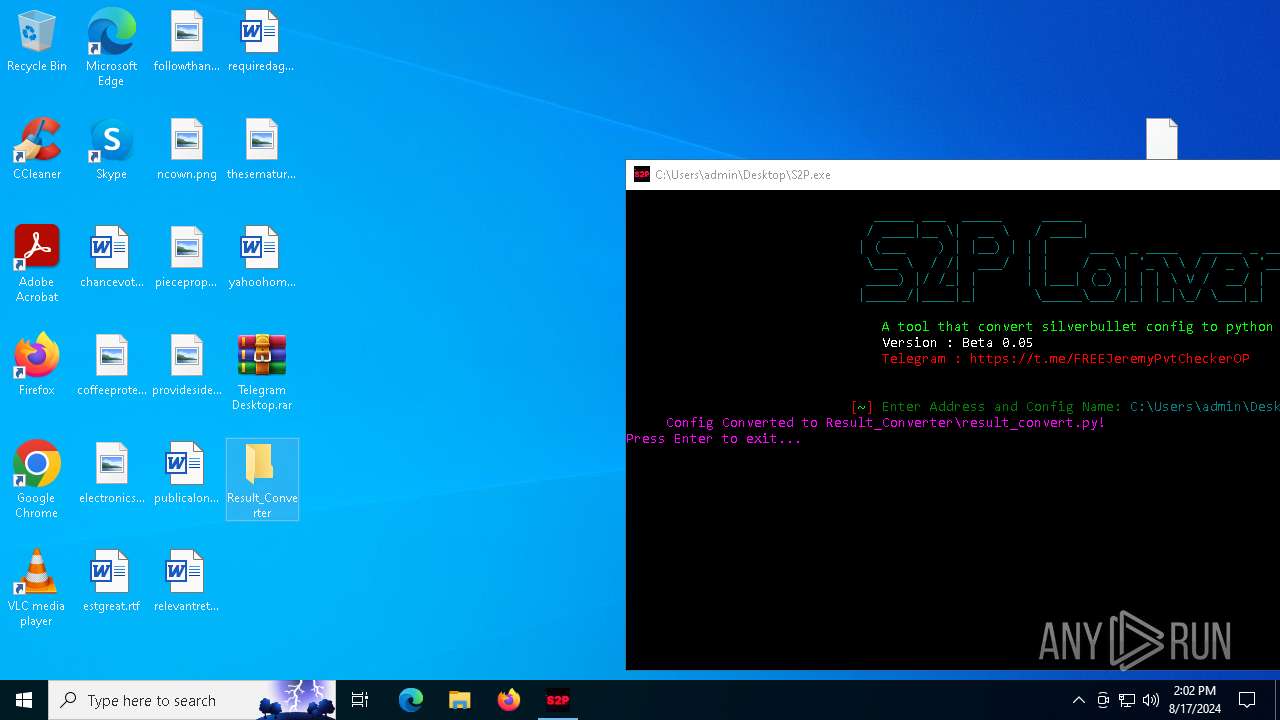
- S2P.exe (PID: 6716)
Executable content was dropped or overwritten
- S2P.exe (PID: 6716)
The process drops C-runtime libraries
- S2P.exe (PID: 6716)
Process drops python dynamic module
- S2P.exe (PID: 6716)
Application launched itself
- S2P.exe (PID: 6716)
Drops the executable file immediately after the start
- S2P.exe (PID: 6716)
Loads Python modules
- S2P.exe (PID: 6848)
Starts CMD.EXE for commands execution
- S2P.exe (PID: 6848)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6460)
Reads the computer name
- S2P.exe (PID: 6716)
- TextInputHost.exe (PID: 6824)
- identity_helper.exe (PID: 7784)
- S2P.exe (PID: 6848)
Manual execution by a user
- S2P.exe (PID: 6716)
- msedge.exe (PID: 2852)
- notepad++.exe (PID: 5500)
Create files in a temporary directory
- S2P.exe (PID: 6716)
Checks supported languages
- S2P.exe (PID: 6716)
- S2P.exe (PID: 6848)
- TextInputHost.exe (PID: 6824)
- identity_helper.exe (PID: 7784)
Reads Microsoft Office registry keys
- msedge.exe (PID: 2852)
- OpenWith.exe (PID: 6276)
Attempting to use file storage service
- msedge.exe (PID: 7144)
Reads Environment values
- identity_helper.exe (PID: 7784)
Application launched itself
- msedge.exe (PID: 2852)
PyInstaller has been detected (YARA)
- S2P.exe (PID: 6848)
- S2P.exe (PID: 6716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
181
Monitored processes
48
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1140 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5796 --field-trial-handle=2244,i,9519898949889180528,8441447879186365354,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1288 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4796 --field-trial-handle=2244,i,9519898949889180528,8441447879186365354,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1288 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=video_capture.mojom.VideoCaptureService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5476 --field-trial-handle=2244,i,9519898949889180528,8441447879186365354,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1292 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5660 --field-trial-handle=2244,i,9519898949889180528,8441447879186365354,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=5812 --field-trial-handle=2244,i,9519898949889180528,8441447879186365354,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5268 --field-trial-handle=2244,i,9519898949889180528,8441447879186365354,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2852 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2960 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x300,0x304,0x308,0x2f8,0x310,0x7fffd4775fd8,0x7fffd4775fe4,0x7fffd4775ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3044 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3508 --field-trial-handle=2244,i,9519898949889180528,8441447879186365354,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3700 --field-trial-handle=2244,i,9519898949889180528,8441447879186365354,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
14 801
Read events
14 675
Write events
123
Delete events
3
Modification events
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Telegram Desktop.rar | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0C00000050000000CC03000039020000 | |||
Executable files
78
Suspicious files
422
Text files
82
Unknown types
0
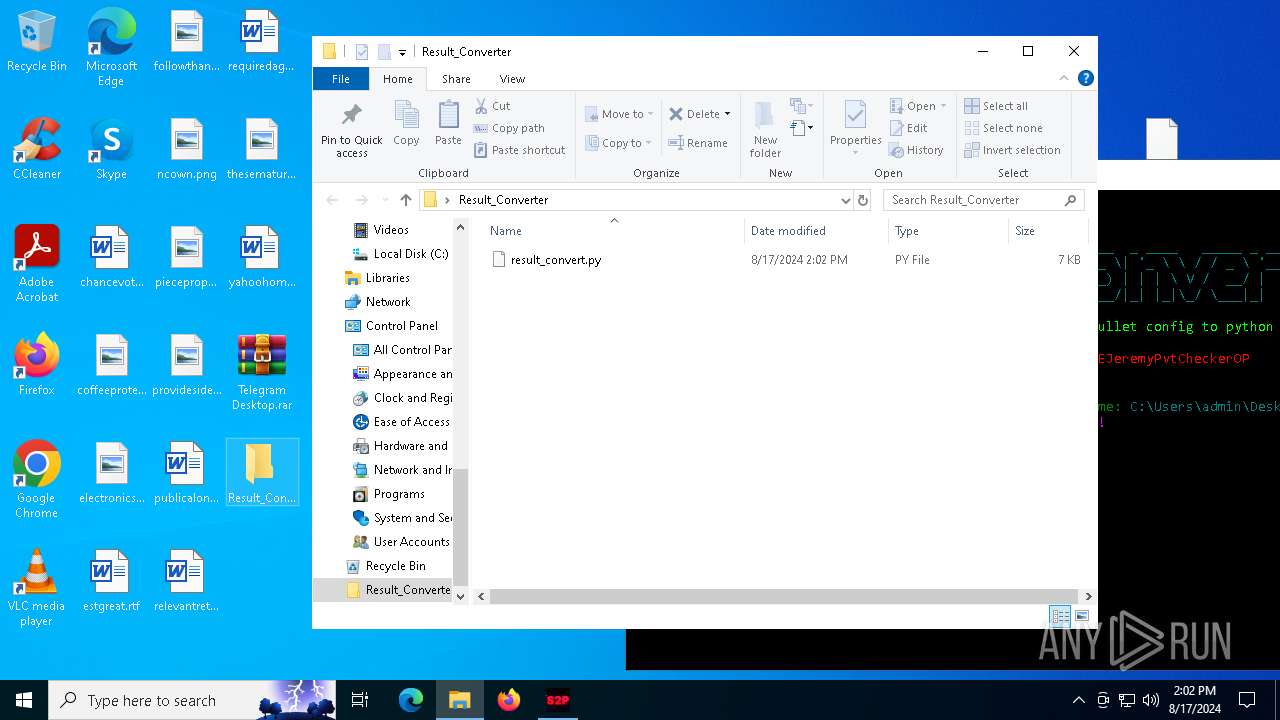
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:503107C27112EC911CFB4D9036E9BA2D | SHA256:F0662C9566EF712112A85A7FD11C96AD296A9571BD6953A756440186BAAADB9D | |||
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\_decimal.pyd | executable | |
MD5:33F721F1CBB413CD4F26FE0ED4A597E7 | SHA256:080D0FBBFF68D17B670110C95210347BE7B8AB7C385F956F123A66DC2F434AB3 | |||
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:9D57E52AE71ED1C5D43F34848E40E7CB | SHA256:3F4FCC14E6D126BB6EC6CCC1F91632039C884916F1D2E4C03CEDB6B6DD8EF85E | |||
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\_ssl.pyd | executable | |
MD5:0E9E6D6839D74AD40BB9F16CC6601B13 | SHA256:BCA1F490C9F7BA25CBBB4B39785DDA8AA651123E22D4E7EDC299B218C8157A81 | |||
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\_ctypes.pyd | executable | |
MD5:78DF76AA0FF8C17EDC60376724D206CD | SHA256:B75560DB79BA6FB56C393A4886EEDD72E60DF1E2F7F870FE2E356D08155F367B | |||
| 6460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6460.14696\S2P.exe | executable | |
MD5:7405A92735E43874408B4BD5B976E692 | SHA256:916B02281A402A3FE7C32AB0595B1282491FF7768B5E0FE8E351B93959F036D2 | |||
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\_lzma.pyd | executable | |
MD5:2AE2464BFCC442083424BC05ED9BE7D2 | SHA256:64BA475A28781DCA81180A1B8722A81893704F8D8FAC0B022C846FDCF95B15B9 | |||
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:EB957E8261032210713E41AD5B337D2E | SHA256:2EBF7BE5A6354058E59BFCC79B7EF6BCE71E7023F14C511CAAFE64554C23C9F4 | |||
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:F060BCB3C78C0CF55EC3785BC5883D23 | SHA256:203F3714E7D67970C7A31712D5CCD2FCD7B81806F33D35D214332AEBAB3B1860 | |||
| 6716 | S2P.exe | C:\Users\admin\AppData\Local\Temp\_MEI67162\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
132
DNS requests
114
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6244 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1344 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6960 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4692 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1860 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2876 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1860 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 92.123.104.47:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1344 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7144 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
7144 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Downloading from a file sharing service is observed |
7144 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|