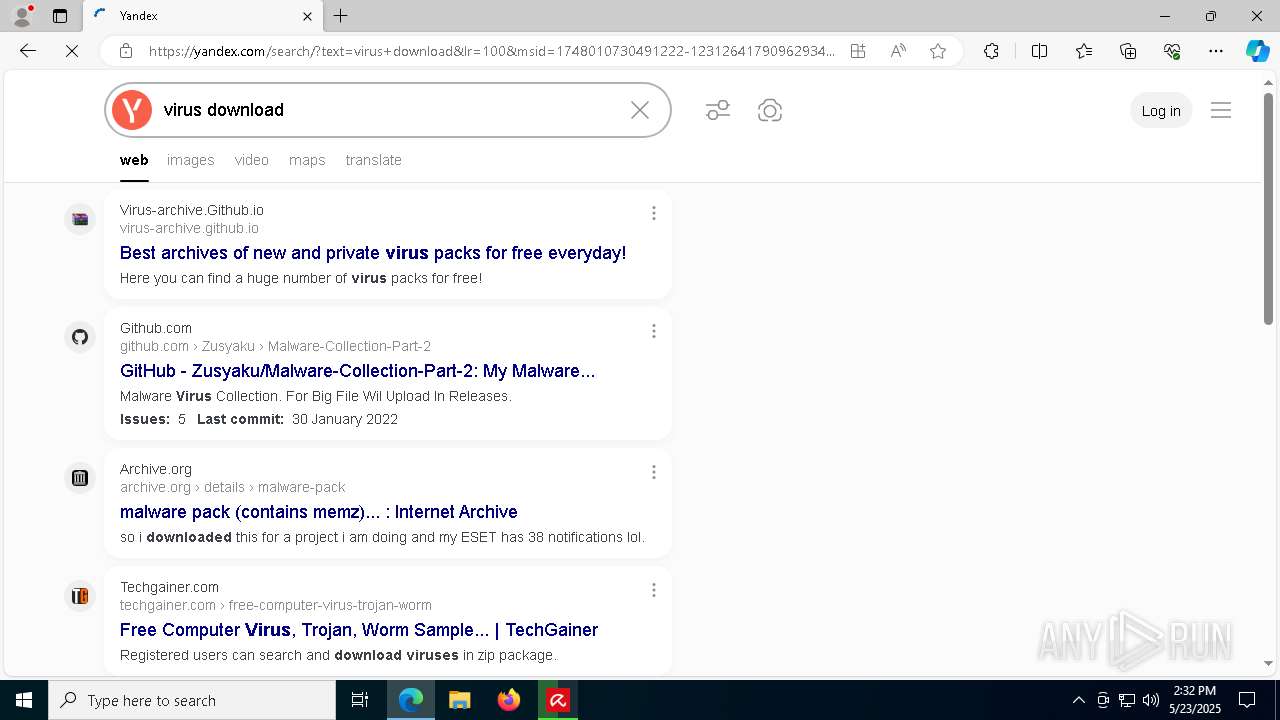
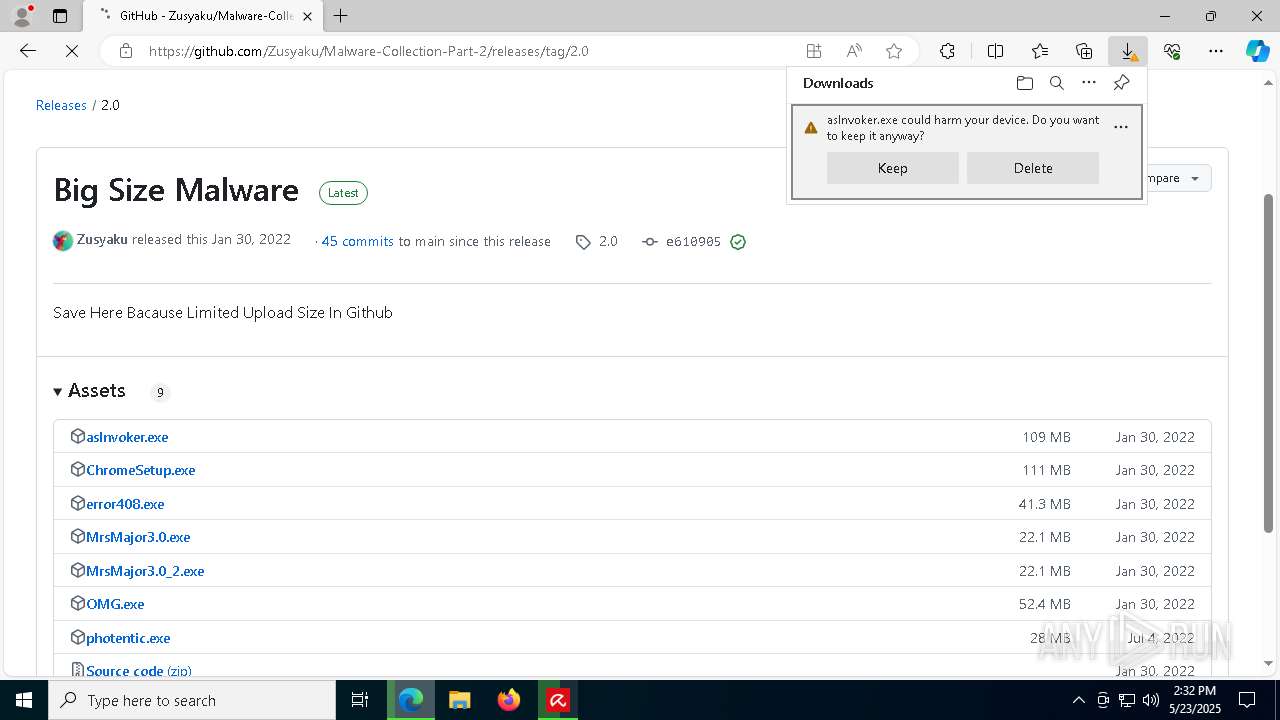
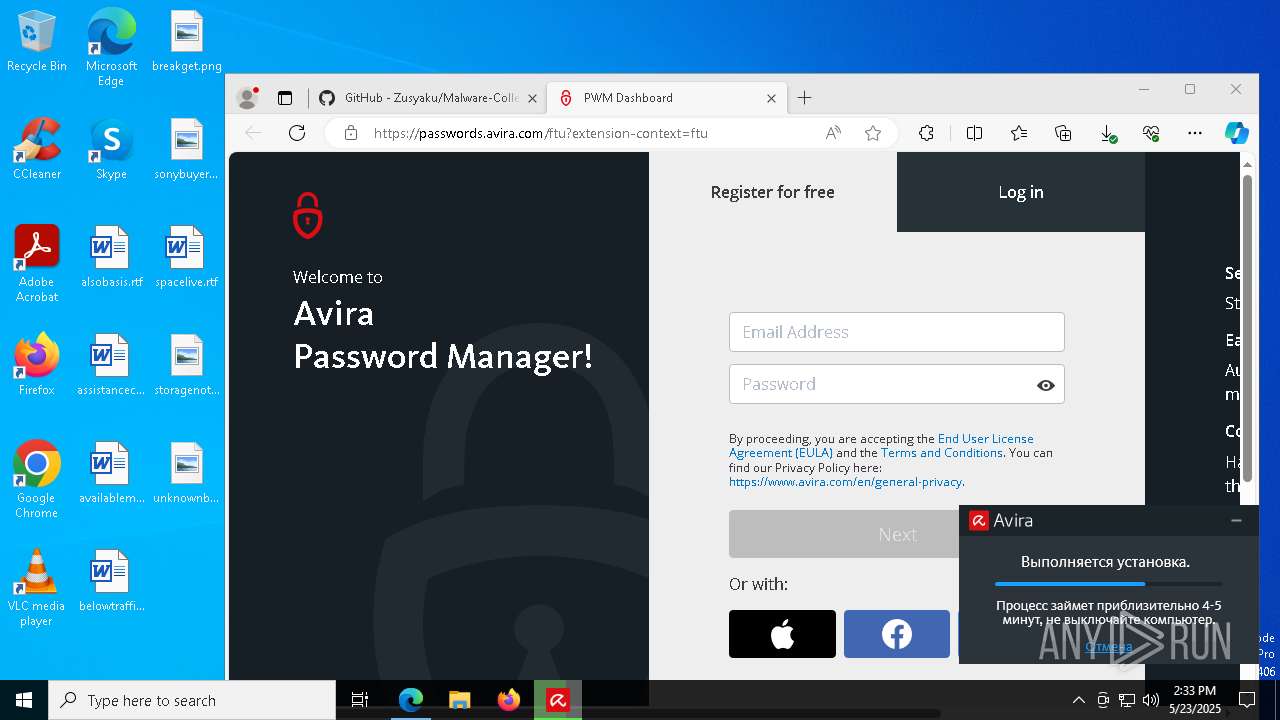
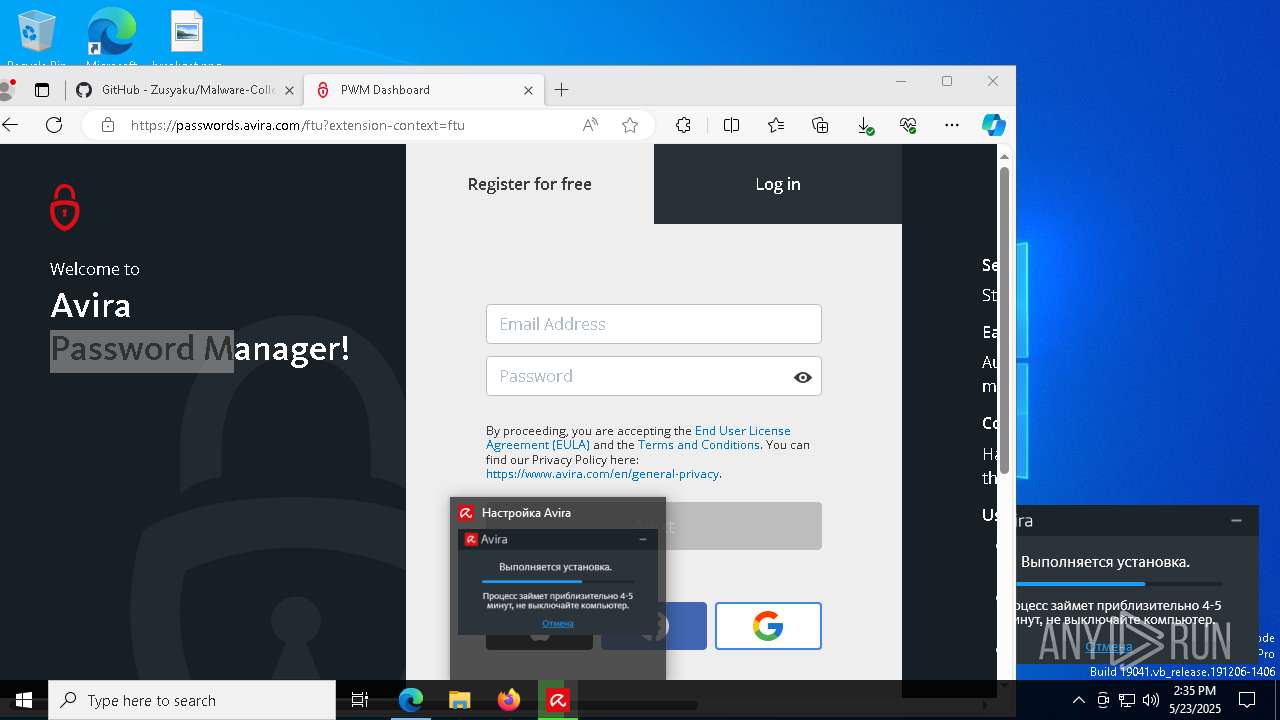
| File name: | avira_ru_sptl1_7a027e278ef14d44__phpws.exe |
| Full analysis: | https://app.any.run/tasks/1ae81e6d-e2bf-4256-85b8-b64b0e4b4c1a |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2025, 14:30:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 32386A910280A99BBE25E16220524102 |
| SHA1: | CBA149A5EF79F809E1B2E0C37F91B6F52609D4AA |
| SHA256: | 0581ED64B9049A56EBE2445412DD827D72210448C3D5DFE028EA0D6AC50E485D |
| SSDEEP: | 98304:iJEWOATmyqtAs+3js0168Ivhki/NWmU8MkbwvMV5gGUIuWWsxI6+PFIY03JGOVdb:zUJKCF |
MALICIOUS
Uses Task Scheduler to run other applications
- avira_ru_sptl1_7a027e278ef14d44__phpws.exe (PID: 5868)
SUSPICIOUS
The process creates files with name similar to system file names
- avira_ru_sptl1_7a027e278ef14d44__phpws.exe (PID: 5868)
Executable content was dropped or overwritten
- avira_ru_sptl1_7a027e278ef14d44__phpws.exe (PID: 5868)
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 2236)
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 8308)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 6136)
Searches for installed software
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
Reads security settings of Internet Explorer
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
- MicrosoftEdgeUpdate.exe (PID: 7796)
Adds/modifies Windows certificates
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
The process verifies whether the antivirus software is installed
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
There is functionality for taking screenshot (YARA)
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 2236)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 6136)
- MicrosoftEdgeUpdate.exe (PID: 7796)
- MicrosoftEdgeUpdate.exe (PID: 8464)
Disables SEHOP
- MicrosoftEdgeUpdate.exe (PID: 7796)
Process drops legitimate windows executable
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 2236)
- MicrosoftEdgeUpdate.exe (PID: 7796)
- MicrosoftEdgeUpdate.exe (PID: 8464)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 6136)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 2320)
INFO
Reads the machine GUID from the registry
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
Create files in a temporary directory
- avira_ru_sptl1_7a027e278ef14d44__phpws.exe (PID: 5868)
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
Reads the computer name
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
- MicrosoftEdgeUpdate.exe (PID: 7796)
- identity_helper.exe (PID: 7208)
Checks supported languages
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
- avira_ru_sptl1_7a027e278ef14d44__phpws.exe (PID: 5868)
- ACSSIGNEDIC.EXE (PID: 1852)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 2236)
- MicrosoftEdgeUpdate.exe (PID: 7796)
- identity_helper.exe (PID: 7208)
Disables trace logs
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
Creates files in the program directory
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 2236)
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
The sample compiled with english language support
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 2236)
- MicrosoftEdgeUpdate.exe (PID: 7796)
- MicrosoftEdgeUpdate.exe (PID: 8464)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 6136)
Reads the software policy settings
- slui.exe (PID: 6080)
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
- MicrosoftEdgeUpdate.exe (PID: 7796)
Manual execution by a user
- msedge.exe (PID: 300)
- firefox.exe (PID: 7520)
Application launched itself
- msedge.exe (PID: 300)
- firefox.exe (PID: 7520)
- firefox.exe (PID: 8108)
Checks proxy server information
- AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE (PID: 1128)
- MicrosoftEdgeUpdate.exe (PID: 7796)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 7796)
- identity_helper.exe (PID: 7208)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 7796)
Executable content was dropped or overwritten
- msedge.exe (PID: 4844)
- msedge.exe (PID: 300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:07 07:16:48+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 335360 |
| InitializedDataSize: | 6500864 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2ab00 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.52.783 |
| ProductVersionNumber: | 1.0.52.783 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Avira Operations GmbH |
| FileDescription: | Avira Security |
| FileVersion: | 1.0.52.783 |
| InternalName: | avira.exe |
| LegalCopyright: | Copyright © 2025 Avira Operations GmbH and its Licensors |
| OriginalFileName: | avira.exe |
| ProductName: | Avira Security |
| ProductVersion: | 1.0.52.783 |
Total processes
244
Monitored processes
104
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 444 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5688 --field-trial-handle=2456,i,109631197482032811,17129939915702862282,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 496 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=52 --mojo-platform-channel-handle=6840 --field-trial-handle=2456,i,109631197482032811,17129939915702862282,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 720 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7500 --field-trial-handle=2456,i,109631197482032811,17129939915702862282,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 744 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AVIRA.SPOTLIGHT.BOOTSTRAPPER.REPORTINGTOOL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1004 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5744 --field-trial-handle=2456,i,109631197482032811,17129939915702862282,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5208 --field-trial-handle=2456,i,109631197482032811,17129939915702862282,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x300,0x304,0x308,0x2f8,0x310,0x7ffc89795fd8,0x7ffc89795fe4,0x7ffc89795ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1128 | "C:\Users\admin\AppData\Local\Temp\.CR.14396\Avira.Spotlight.Bootstrapper.exe" "C:\Users\admin\AppData\Local\Temp\.CR.14396\Avira.Spotlight.Bootstrapper.exe" OriginalFileName=avira_ru_sptl1_7a027e278ef14d44__phpws.exe | C:\Users\admin\AppData\Local\Temp\.CR.14396\AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | avira_ru_sptl1_7a027e278ef14d44__phpws.exe | ||||||||||||
User: admin Company: Avira Operations GmbH Integrity Level: HIGH Description: Avira Security Version: 1.0.52.783 Modules
| |||||||||||||||
Total events
95 844
Read events
95 081
Write events
743
Delete events
20
Modification events
| (PID) Process: | (5868) avira_ru_sptl1_7a027e278ef14d44__phpws.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\Avira.Spotlight.Bootstrapper.exe |
| Operation: | write | Name: | NoStartPage |
Value: | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\{80b8c23c-16e0-4cd8-bbc3-cecec9a78b79} |
| Operation: | write | Name: | telemetry |
Value: d7279172f64146a7b3051f6c1bce8f0f160b233c | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | F40042E2E5F7E8EF8189FED15519AECE42C3BFA2 |
Value: | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\F40042E2E5F7E8EF8189FED15519AECE42C3BFA2 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000BE954F16012122448CA8BC279602ACF50F000000010000003000000041CE925678DFE0CCAA8089263C242B897CA582089D14E5EB685FCA967F36DBD334E97E81FD0E64815F851F914ADE1A1E030000000100000014000000F40042E2E5F7E8EF8189FED15519AECE42C3BFA21D0000000100000010000000E78921F81CEA4D4105D2B5F4AFAE0C78140000000100000014000000C87ED26A852A1BCA1998040727CF50104F68A8A2090000000100000016000000301406082B0601050507030306082B060105050703086200000001000000200000005367F20C7ADE0E2BCA790915056D086B720C33C1FA2A2661ACF787E3292E12700B00000001000000800000004D006900630072006F0073006F006600740020004900640065006E007400690074007900200056006500720069006600690063006100740069006F006E00200052006F006F007400200043006500720074006900660069006300610074006500200041007500740068006F0072006900740079002000320030003200300000001900000001000000100000009F687581F7EF744ECFC12B9CEE6238F12000000001000000D0050000308205CC308203B4A00302010202105498D2D1D45B1995481379C811C08799300D06092A864886F70D01010C05003077310B3009060355040613025553311E301C060355040A13154D6963726F736F667420436F72706F726174696F6E314830460603550403133F4D6963726F736F6674204964656E7469747920566572696669636174696F6E20526F6F7420436572746966696361746520417574686F726974792032303230301E170D3230303431363138333631365A170D3435303431363138343434305A3077310B3009060355040613025553311E301C060355040A13154D6963726F736F667420436F72706F726174696F6E314830460603550403133F4D6963726F736F6674204964656E7469747920566572696669636174696F6E20526F6F7420436572746966696361746520417574686F72697479203230323030820222300D06092A864886F70D01010105000382020F003082020A0282020100B3912A07830667FD9E9DE0C7C0B7A4E642047F0FA6DB5FFBD55AD745A0FB770BF080F3A66D5A4D7953D8A08684574520C7A254FBC7A2BF8AC76E35F3A215C42F4EE34A8596490DFFBE99D814F6BC2707EE429B2BF50B9206E4FD691365A89172F29884EB833D0EE4D771124821CB0DEDF64749B79BF9C9C717B6844FFFB8AC9AD773674985E386BD3740D02586D4DEB5C26D626AD5A978BC2D6F49F9E56C1414FD14C7D3651637DECB6EBC5E298DFD629B152CD605E6B9893233A362C7D7D6526708C42EF4562B9E0B87CCECA7B4A6AAEB05CD1957A53A0B04271C91679E2D622D2F1EBEDAC020CB0419CA33FB89BE98E272A07235BE79E19C836FE46D176F90F33D008675388ED0E0499ABBDBD3F830CAD55788684D72D3BF6D7F71D8FDBD0DAE926448B75B6F7926B5CD9B952184D1EF0F323D7B578CF345074C7CE05E180E35768B6D9ECB3674AB05F8E0735D3256946797250AC6353D9497E7C1448B80FDC1F8F47419E530F606FB21573E061C8B6B158627497B8293CA59E87547E83F38F4C75379A0B6B4E25C51EFBD5F38C113E6780C955A2EC5405928CC0F24C0ECBA0977239938A6B61CDAC7BA20B6D737D87F37AF08E33B71DB6E731B7D9972B0E486335974B516007B506DC68613DAFDC439823D24009A60DABA94C005512C34AC50991387BBB30580B24D30025CB826835DB46373EFAE23954F6028BE37D55BA50203010001A3543052300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF301D0603551D0E04160414C87ED26A852A1BCA1998040727CF50104F68A8A2301006092B06010401823715010403020100300D06092A864886F70D01010C05000382020100AF6ADDE619E72D9443194ECBE9509564A50391028BE236803B15A252C21619B66A5A5D744330F49BFF607409B1211E90166DC5248F5C668863F44FCC7DF2124C40108B019FDAA9C8AEF2951BCF9D05EB493E74A0685BE5562C651C827E53DA56D94617799245C4103608522917CB2FA6F27ED469248A1E8FB0730DCC1C4AABB2AAEDA79163016422A832B87E3228B367732D91B4DC31010BF7470AA6F1D74AED5660C42C08A37B40B0BC74275287D6BE88DD378A896E67881DF5C95DA0FEB6AB3A80D71A973C173622411EAC4DD583E63C38BD4F30E954A9D3B604C3327661BBB018C52B18B3C080D5B795B05E514D22FCEC58AAE8D894B4A52EED92DEE7187C2157DD5563F7BF6DCD1FD2A6772870C7E25B3A5B08D25B4EC80096B3E18336AF860A655C74F6EAEC7A6A74A0F04BEEEF94A3AC50F287EDD73A3083C9FB7D57BEE5E3F841CAE564AEB3A3EC58EC859ACCEFB9EAF35618B95C739AAFC577178359DB371A187254A541D2B62375A3439AE5777C9679B7418DBFECDC80A09FD17775585F3513E0251A670B7DCE25FA070AE46121D8D41CE507C63699F496D0C615FE4ECDD7AE8B9DDB16FD04C692BDD488E6A9A3AABBF764383B5FCC0CD035BE741903A6C5AA4CA26136823E1DF32BBC975DDB4B783B2DF53BEF6023E8F5EC0B233695AF9866BF53D37BB8694A2A966669C494C6F45F6EAC98788880065CA2B2EDA2 | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\F40042E2E5F7E8EF8189FED15519AECE42C3BFA2 |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000001000001900000001000000100000009F687581F7EF744ECFC12B9CEE6238F10B00000001000000800000004D006900630072006F0073006F006600740020004900640065006E007400690074007900200056006500720069006600690063006100740069006F006E00200052006F006F007400200043006500720074006900660069006300610074006500200041007500740068006F0072006900740079002000320030003200300000006200000001000000200000005367F20C7ADE0E2BCA790915056D086B720C33C1FA2A2661ACF787E3292E1270090000000100000016000000301406082B0601050507030306082B06010505070308140000000100000014000000C87ED26A852A1BCA1998040727CF50104F68A8A21D0000000100000010000000E78921F81CEA4D4105D2B5F4AFAE0C78030000000100000014000000F40042E2E5F7E8EF8189FED15519AECE42C3BFA20F000000010000003000000041CE925678DFE0CCAA8089263C242B897CA582089D14E5EB685FCA967F36DBD334E97E81FD0E64815F851F914ADE1A1E040000000100000010000000BE954F16012122448CA8BC279602ACF52000000001000000D0050000308205CC308203B4A00302010202105498D2D1D45B1995481379C811C08799300D06092A864886F70D01010C05003077310B3009060355040613025553311E301C060355040A13154D6963726F736F667420436F72706F726174696F6E314830460603550403133F4D6963726F736F6674204964656E7469747920566572696669636174696F6E20526F6F7420436572746966696361746520417574686F726974792032303230301E170D3230303431363138333631365A170D3435303431363138343434305A3077310B3009060355040613025553311E301C060355040A13154D6963726F736F667420436F72706F726174696F6E314830460603550403133F4D6963726F736F6674204964656E7469747920566572696669636174696F6E20526F6F7420436572746966696361746520417574686F72697479203230323030820222300D06092A864886F70D01010105000382020F003082020A0282020100B3912A07830667FD9E9DE0C7C0B7A4E642047F0FA6DB5FFBD55AD745A0FB770BF080F3A66D5A4D7953D8A08684574520C7A254FBC7A2BF8AC76E35F3A215C42F4EE34A8596490DFFBE99D814F6BC2707EE429B2BF50B9206E4FD691365A89172F29884EB833D0EE4D771124821CB0DEDF64749B79BF9C9C717B6844FFFB8AC9AD773674985E386BD3740D02586D4DEB5C26D626AD5A978BC2D6F49F9E56C1414FD14C7D3651637DECB6EBC5E298DFD629B152CD605E6B9893233A362C7D7D6526708C42EF4562B9E0B87CCECA7B4A6AAEB05CD1957A53A0B04271C91679E2D622D2F1EBEDAC020CB0419CA33FB89BE98E272A07235BE79E19C836FE46D176F90F33D008675388ED0E0499ABBDBD3F830CAD55788684D72D3BF6D7F71D8FDBD0DAE926448B75B6F7926B5CD9B952184D1EF0F323D7B578CF345074C7CE05E180E35768B6D9ECB3674AB05F8E0735D3256946797250AC6353D9497E7C1448B80FDC1F8F47419E530F606FB21573E061C8B6B158627497B8293CA59E87547E83F38F4C75379A0B6B4E25C51EFBD5F38C113E6780C955A2EC5405928CC0F24C0ECBA0977239938A6B61CDAC7BA20B6D737D87F37AF08E33B71DB6E731B7D9972B0E486335974B516007B506DC68613DAFDC439823D24009A60DABA94C005512C34AC50991387BBB30580B24D30025CB826835DB46373EFAE23954F6028BE37D55BA50203010001A3543052300E0603551D0F0101FF040403020186300F0603551D130101FF040530030101FF301D0603551D0E04160414C87ED26A852A1BCA1998040727CF50104F68A8A2301006092B06010401823715010403020100300D06092A864886F70D01010C05000382020100AF6ADDE619E72D9443194ECBE9509564A50391028BE236803B15A252C21619B66A5A5D744330F49BFF607409B1211E90166DC5248F5C668863F44FCC7DF2124C40108B019FDAA9C8AEF2951BCF9D05EB493E74A0685BE5562C651C827E53DA56D94617799245C4103608522917CB2FA6F27ED469248A1E8FB0730DCC1C4AABB2AAEDA79163016422A832B87E3228B367732D91B4DC31010BF7470AA6F1D74AED5660C42C08A37B40B0BC74275287D6BE88DD378A896E67881DF5C95DA0FEB6AB3A80D71A973C173622411EAC4DD583E63C38BD4F30E954A9D3B604C3327661BBB018C52B18B3C080D5B795B05E514D22FCEC58AAE8D894B4A52EED92DEE7187C2157DD5563F7BF6DCD1FD2A6772870C7E25B3A5B08D25B4EC80096B3E18336AF860A655C74F6EAEC7A6A74A0F04BEEEF94A3AC50F287EDD73A3083C9FB7D57BEE5E3F841CAE564AEB3A3EC58EC859ACCEFB9EAF35618B95C739AAFC577178359DB371A187254A541D2B62375A3439AE5777C9679B7418DBFECDC80A09FD17775585F3513E0251A670B7DCE25FA070AE46121D8D41CE507C63699F496D0C615FE4ECDD7AE8B9DDB16FD04C692BDD488E6A9A3AABBF764383B5FCC0CD035BE741903A6C5AA4CA26136823E1DF32BBC975DDB4B783B2DF53BEF6023E8F5EC0B233695AF9866BF53D37BB8694A2A966669C494C6F45F6EAC98788880065CA2B2EDA2 | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\{80b8c23c-16e0-4cd8-bbc3-cecec9a78b79} |
| Operation: | write | Name: | SessionId |
Value: ab4c7518dbc04d6b873ad7f8c8964906 | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\{80b8c23c-16e0-4cd8-bbc3-cecec9a78b79} |
| Operation: | write | Name: | Action |
Value: Install | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Avira\Bootstrapper |
| Operation: | write | Name: | MixpanelCommonProperties |
Value: AAEAAAD/////AQAAAAAAAAAEAQAAAOIBU3lzdGVtLkNvbGxlY3Rpb25zLkdlbmVyaWMuRGljdGlvbmFyeWAyW1tTeXN0ZW0uU3RyaW5nLCBtc2NvcmxpYiwgVmVyc2lvbj00LjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPWI3N2E1YzU2MTkzNGUwODldLFtTeXN0ZW0uT2JqZWN0LCBtc2NvcmxpYiwgVmVyc2lvbj00LjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPWI3N2E1YzU2MTkzNGUwODldXQQAAAAHVmVyc2lvbghDb21wYXJlcghIYXNoU2l6ZQ1LZXlWYWx1ZVBhaXJzAAMAAwiSAVN5c3RlbS5Db2xsZWN0aW9ucy5HZW5lcmljLkdlbmVyaWNFcXVhbGl0eUNvbXBhcmVyYDFbW1N5c3RlbS5TdHJpbmcsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV1dCOYBU3lzdGVtLkNvbGxlY3Rpb25zLkdlbmVyaWMuS2V5VmFsdWVQYWlyYDJbW1N5c3RlbS5TdHJpbmcsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV0sW1N5c3RlbS5PYmplY3QsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV1dW10TAAAACQIAAAAlAAAACQMAAAAEAgAAAJIBU3lzdGVtLkNvbGxlY3Rpb25zLkdlbmVyaWMuR2VuZXJpY0VxdWFsaXR5Q29tcGFyZXJgMVtbU3lzdGVtLlN0cmluZywgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5XV0AAAAABwMAAAAAAQAAABMAAAAD5AFTeXN0ZW0uQ29sbGVjdGlvbnMuR2VuZXJpYy5LZXlWYWx1ZVBhaXJgMltbU3lzdGVtLlN0cmluZywgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5XSxbU3lzdGVtLk9iamVjdCwgbXNjb3JsaWIsIFZlcnNpb249NC4wLjAuMCwgQ3VsdHVyZT1uZXV0cmFsLCBQdWJsaWNLZXlUb2tlbj1iNzdhNWM1NjE5MzRlMDg5XV0E/P///+QBU3lzdGVtLkNvbGxlY3Rpb25zLkdlbmVyaWMuS2V5VmFsdWVQYWlyYDJbW1N5c3RlbS5TdHJpbmcsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV0sW1N5c3RlbS5PYmplY3QsIG1zY29ybGliLCBWZXJzaW9uPTQuMC4wLjAsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49Yjc3YTVjNTYxOTM0ZTA4OV1dAgAAAANrZXkFdmFsdWUBAgYFAAAAAyRvcwYGAAAAB1dpbmRvd3MB+f////z///8GCAAAAAskb3NfdmVyc2lvbgYJAAAACjEwLjAuMTkwNDUB9v////z///8GCwAAAAtPcyBMYW5ndWFnZQYMAAAABWVuLVVTAfP////8////Bg4AAAALT3MgUGxhdGZvcm0GDwAAAAN4NjQB8P////z///8GEQAAAAxzaGEyX3N1cHBvcnQIAQEB7v////z///8GEwAAABYuTkVUIEZyYW1ld29yayBWZXJzaW9uCRQAAAAB6/////z///8GFgAAAApQcm9jZXNzIElECAhoBAAAAen////8////BhgAAAASQ29tcGF0aWJpbGl0eSBNb2RlCRkAAAAB5v////z///8GGwAAAAthY3Nfc3VwcG9ydAgBAQHk/////P///wYdAAAADUV4cGVyaW1lbnRJZHMJHgAAAAHh/////P///wYgAAAAEEV4cGVyaW1lbnRHcm91cHMJIQAAAAHe/////P///wYjAAAAD0Rvd25sb2FkIFNvdXJjZQYkAAAABXBocHdzAdv////8////BiYAAAAJQnVuZGxlIElEBicAAAAFc3B0bDEB2P////z///8GKQAAABRCb290c3RyYXBwZXIgVmVyc2lvbgYqAAAACjEuMC41Mi43ODMB1f////z///8GLAAAAAZBY3Rpb24GLQAAAAdJbnN0YWxsAdL////8////Bi8AAAAHUnVuTW9kZQYwAAAAB0RlZmF1bHQBz/////z///8GMgAAAAZTaWxlbnQIAQABzf////z///8GNAAAAApTZXNzaW9uIElEBjUAAAAgYWI0Yzc1MThkYmMwNGQ2Yjg3M2FkN2Y4Yzg5NjQ5MDYByv////z///8GNwAAABJTcG90bGlnaHQgTGFuZ3VhZ2UGOAAAAAVydS1SVQQUAAAADlN5c3RlbS5WZXJzaW9uBAAAAAZfTWFqb3IGX01pbm9yBl9CdWlsZAlfUmV2aXNpb24AAAAACAgICAQAAAAIAAAA//////////8RGQAAAAIAAAAGOQAAABJEZXRlY3RvcnNBcHBIZWFsdGgGOgAAAAlJbnN0YWxsZXIRHgAAAAEAAAAGOwAAAAlzcG90bGlnaHQRIQAAAAEAAAAGPAAAAAdkZWZhdWx0Cw== | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Avira_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1128) AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Avira_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
351
Suspicious files
937
Text files
248
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1128 | AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | C:\Users\admin\AppData\Local\Temp\.CR.14396\d03008cd-76cd-431f-8a58-18209b579ece\7f3ca2e2-4dfb-4600-915d-9747796db4a0.tmp | — | |
MD5:— | SHA256:— | |||
| 1128 | AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | C:\Users\admin\AppData\Local\Temp\.CR.14396\d03008cd-76cd-431f-8a58-18209b579ece\MicrosoftEdgeWebView2RuntimeInstallerX64.exe | — | |
MD5:— | SHA256:— | |||
| 1128 | AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | C:\Users\admin\AppData\Local\Temp\.CR.14396\386a1a0c-0449-42a8-965c-327e5eef144b\avira_spotlight_setup_phpws.exe | — | |
MD5:— | SHA256:— | |||
| 1128 | AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | C:\Users\admin\AppData\Local\Temp\.CR.14396\cb0276e4-1014-46a3-85cc-74c1ed30a89c\8f30da97-8e61-4450-8238-21ff1a2c9d9f.tmp | — | |
MD5:— | SHA256:— | |||
| 1128 | AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | C:\Users\admin\AppData\Local\Temp\.CR.14396\cb0276e4-1014-46a3-85cc-74c1ed30a89c\avira_system_speedup.exe | — | |
MD5:— | SHA256:— | |||
| 5868 | avira_ru_sptl1_7a027e278ef14d44__phpws.exe | C:\Users\admin\AppData\Local\Temp\.CR.31292\Avira.Spotlight.Bootstrapper.Runner.exe.config | xml | |
MD5:58410F4F50391A09970644AC99DC692C | SHA256:CDDC4ED76E18D72D144809A86CADE27F7B5AA1833B7900E40739B59852999245 | |||
| 300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF11fb84.TMP | — | |
MD5:— | SHA256:— | |||
| 300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF11fb84.TMP | — | |
MD5:— | SHA256:— | |||
| 300 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
202
DNS requests
233
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7356 | wermgr.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7660 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/51cb2782-01e8-472e-b29c-e0305135c81e?P1=1748436608&P2=404&P3=2&P4=lbKUjwK0s3CYAEpK72ojAcfR13bXwsjQOSO8OU%2bEXiw0fDrpCmtriDF9fQxjtECpu3vY4dpqywq0lSLXcUINmw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
1128 | AVIRA.SPOTLIGHT.BOOTSTRAPPER.EXE | 18.185.166.254:443 | dispatch.avira-update.com | AMAZON-02 | DE | unknown |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
dispatch.avira-update.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.my.avira.com |
| unknown |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4844 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |
4844 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |
4844 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |
4844 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Blob Storage (.blob .core .windows .net) |