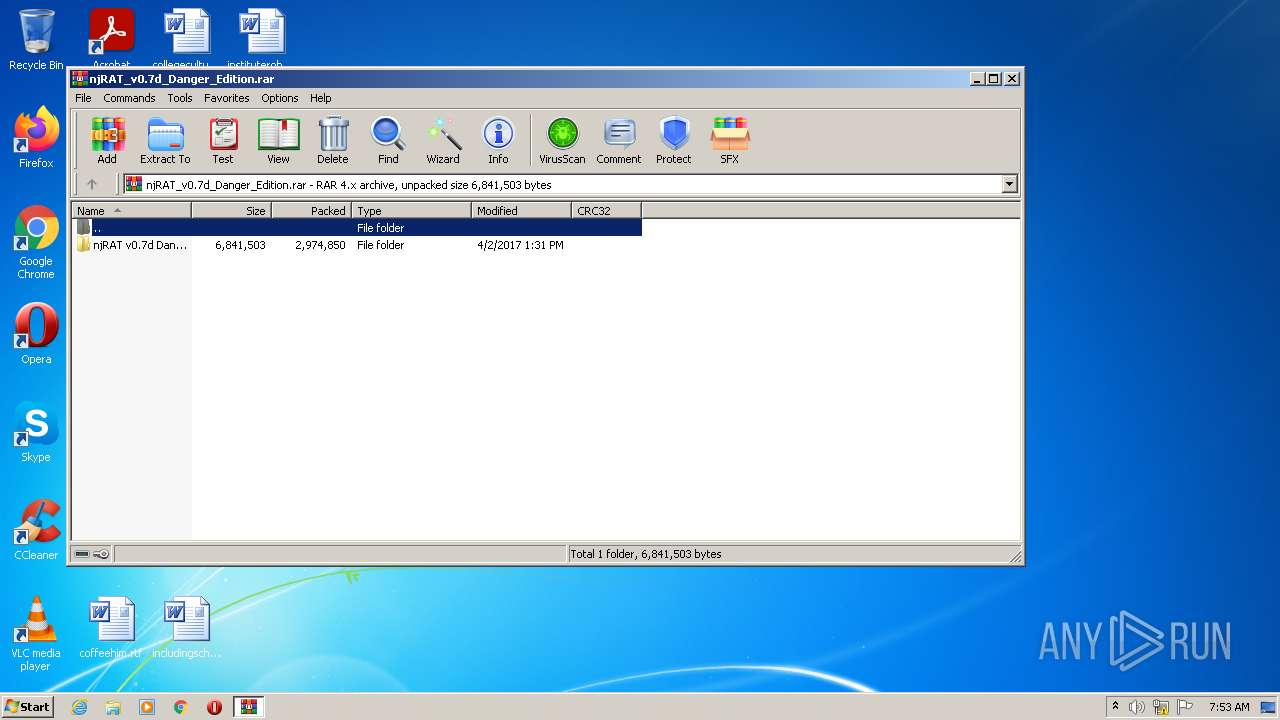
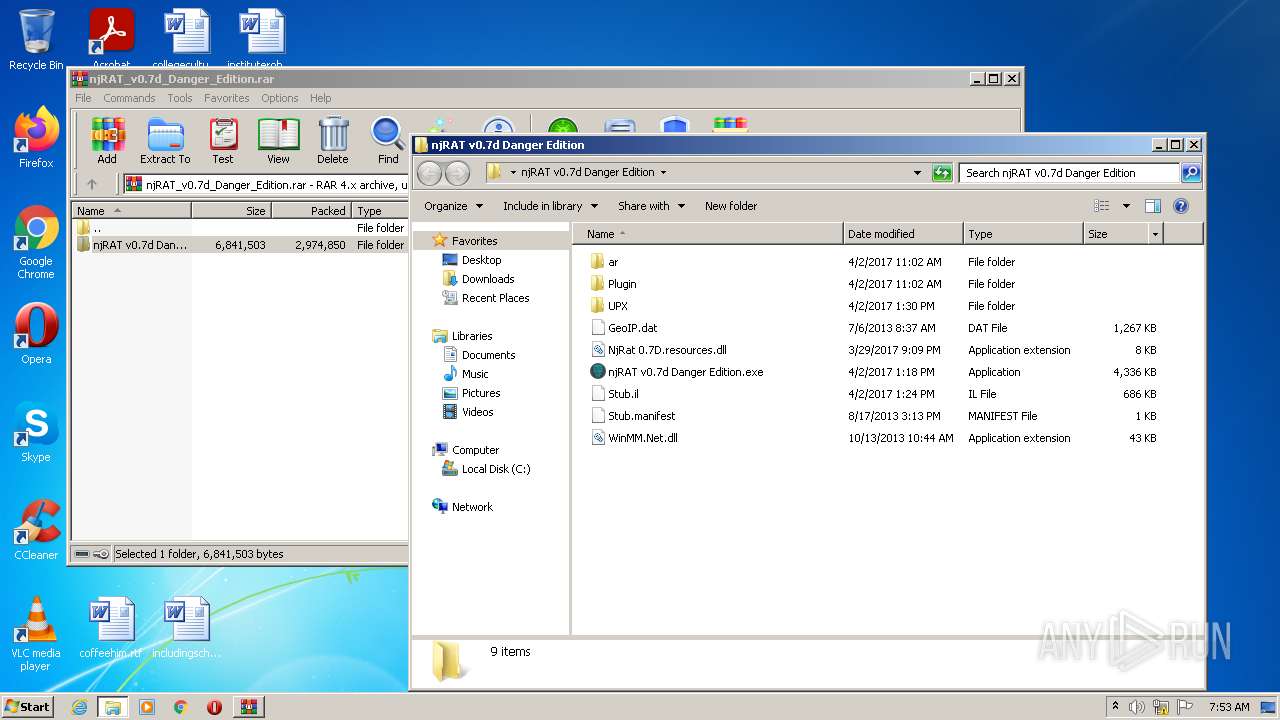
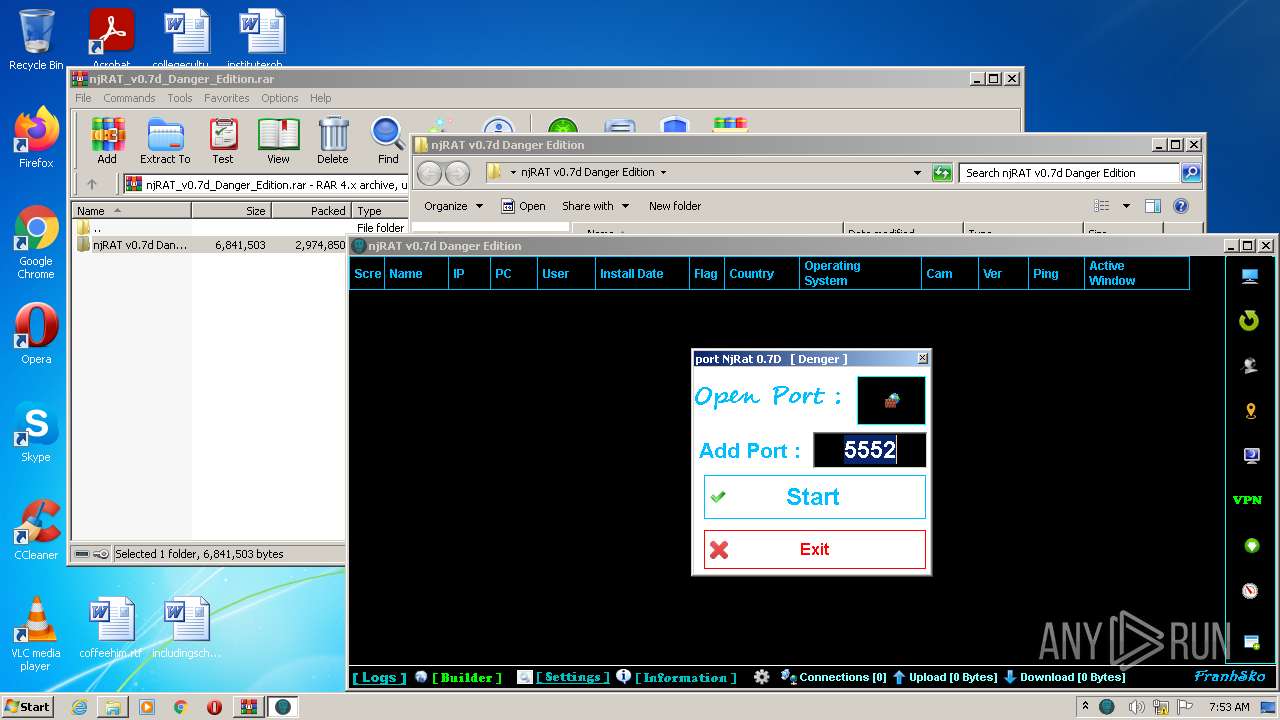
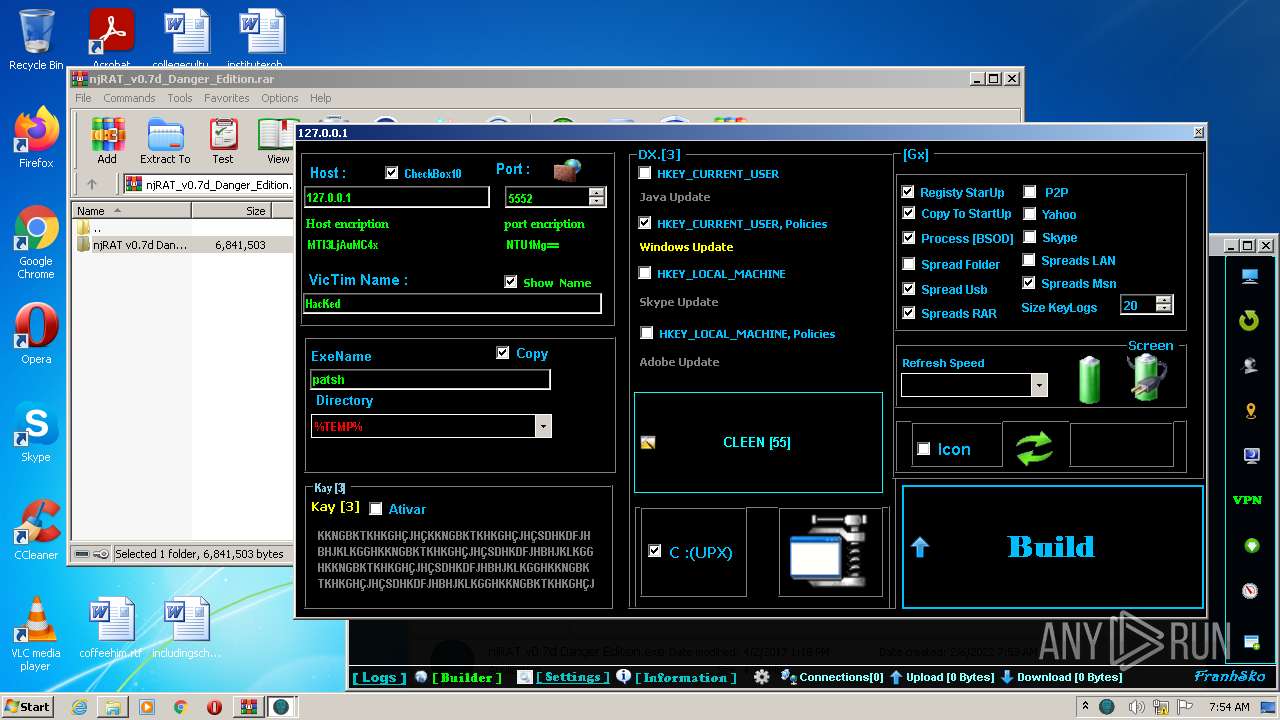
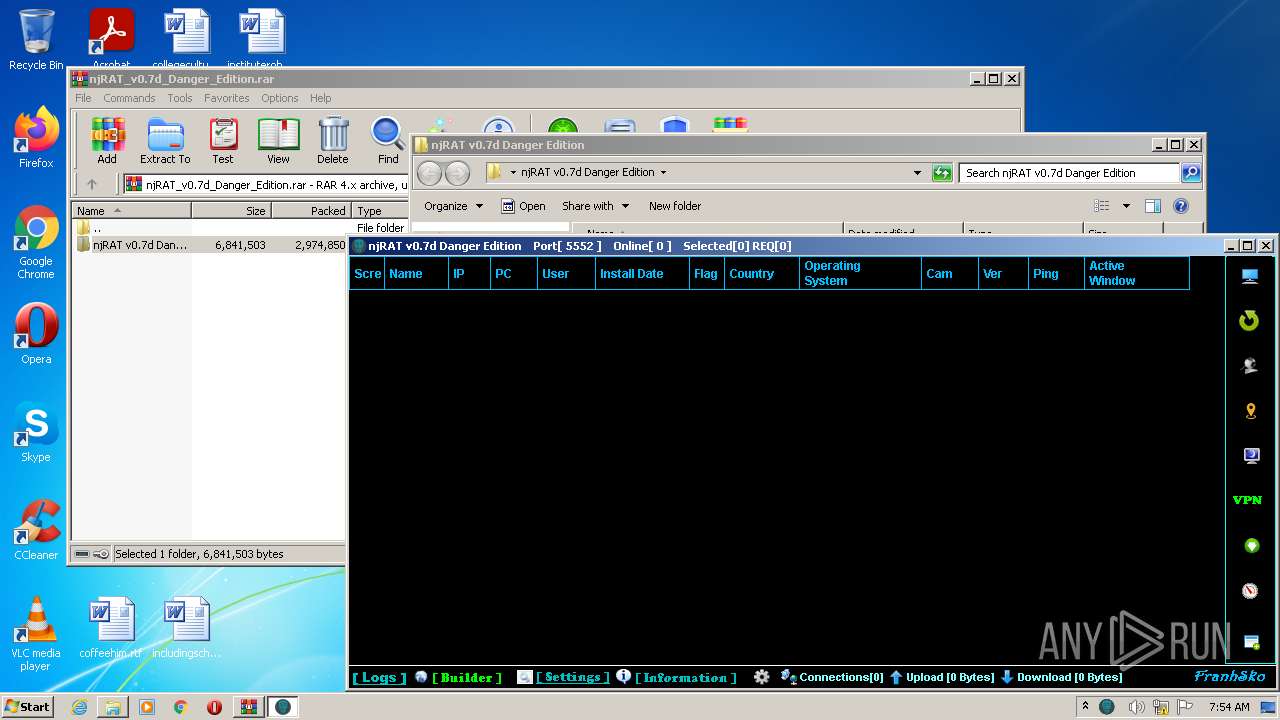
| File name: | njRAT_v0.7d_Danger_Edition.rar |
| Full analysis: | https://app.any.run/tasks/1e77afa9-84f3-49d4-aa6b-9808f12ab9e9 |
| Verdict: | Malicious activity |
| Analysis date: | February 06, 2022, 07:53:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 8C48650F82E9C160966BE4D9D2F85D68 |
| SHA1: | 1BCB277A541F5A7420BCA4D9EE18859A8AFD6965 |
| SHA256: | 0572B75E548423C3B3FEB5BFBF3A84135D4B8EC8A736F5E83951107D3D7518A2 |
| SSDEEP: | 49152:GOrKFD5fs/BGK1HJJSlQSQcOZWDo/NwpaHUD0gaeS4er21WL6AeHLEwBNdbb:GOrKjfN0eROAyNAaQ0gze7LMLzBN1 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3608)
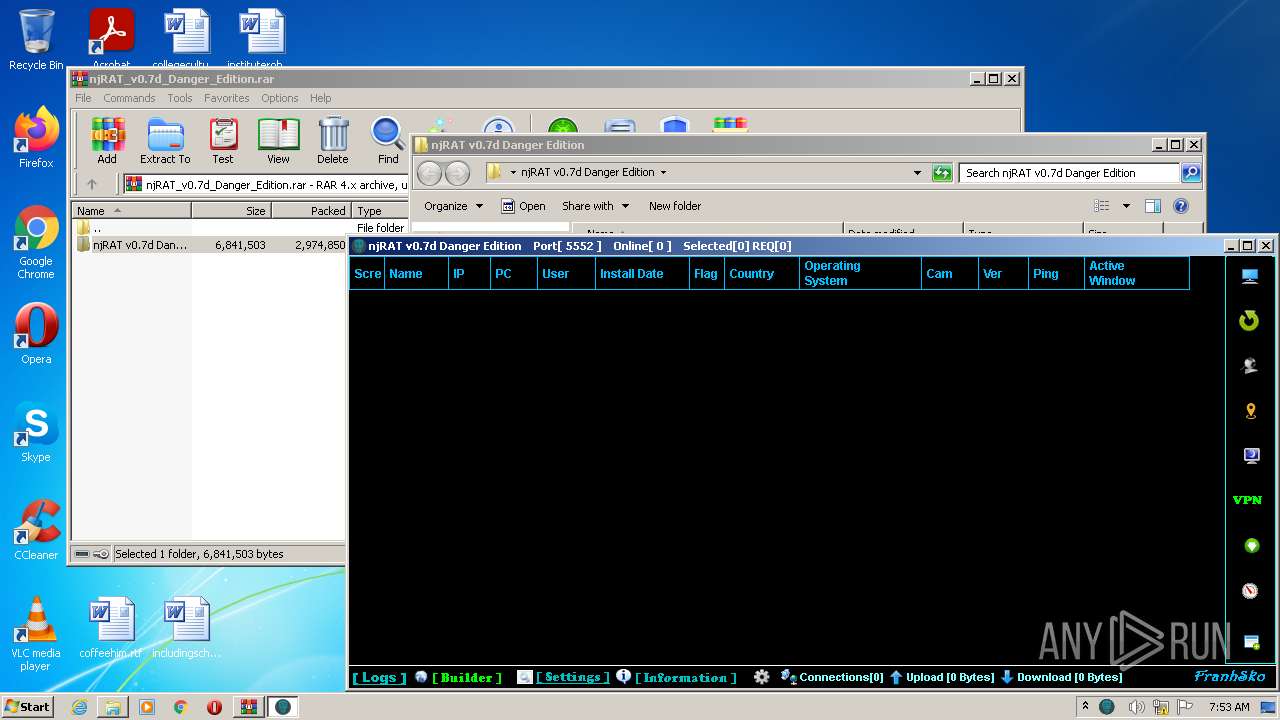
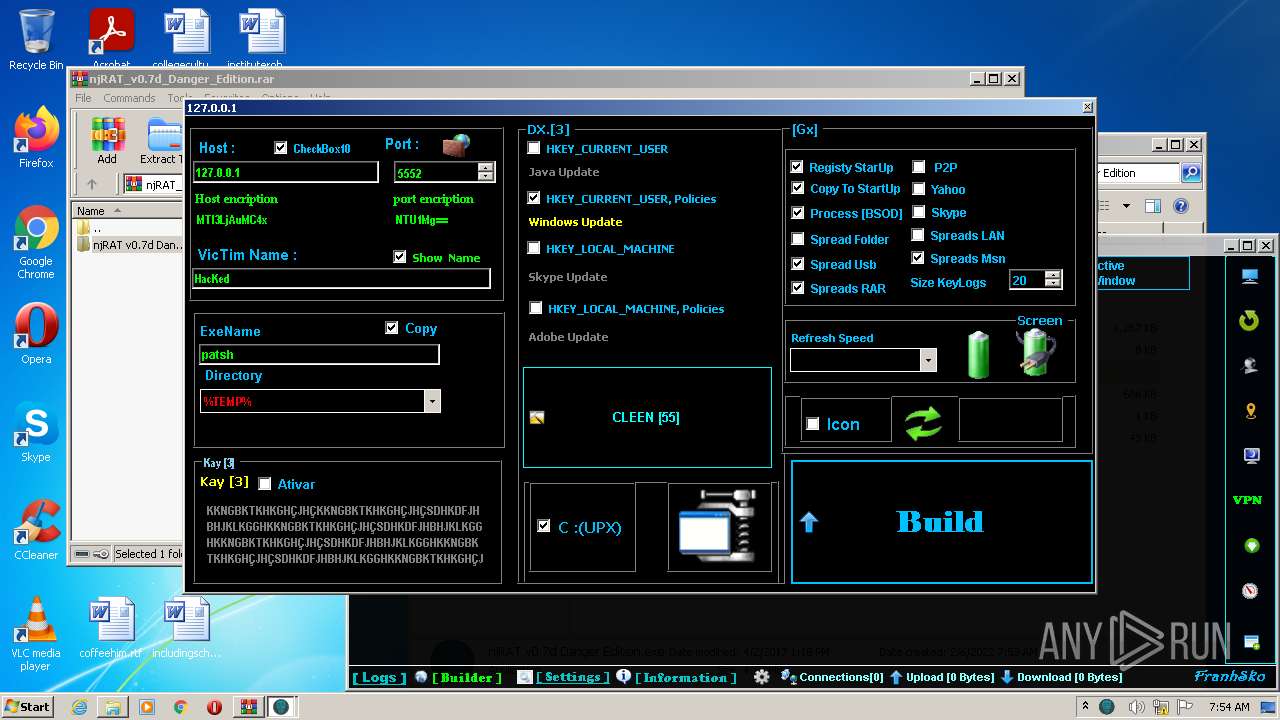
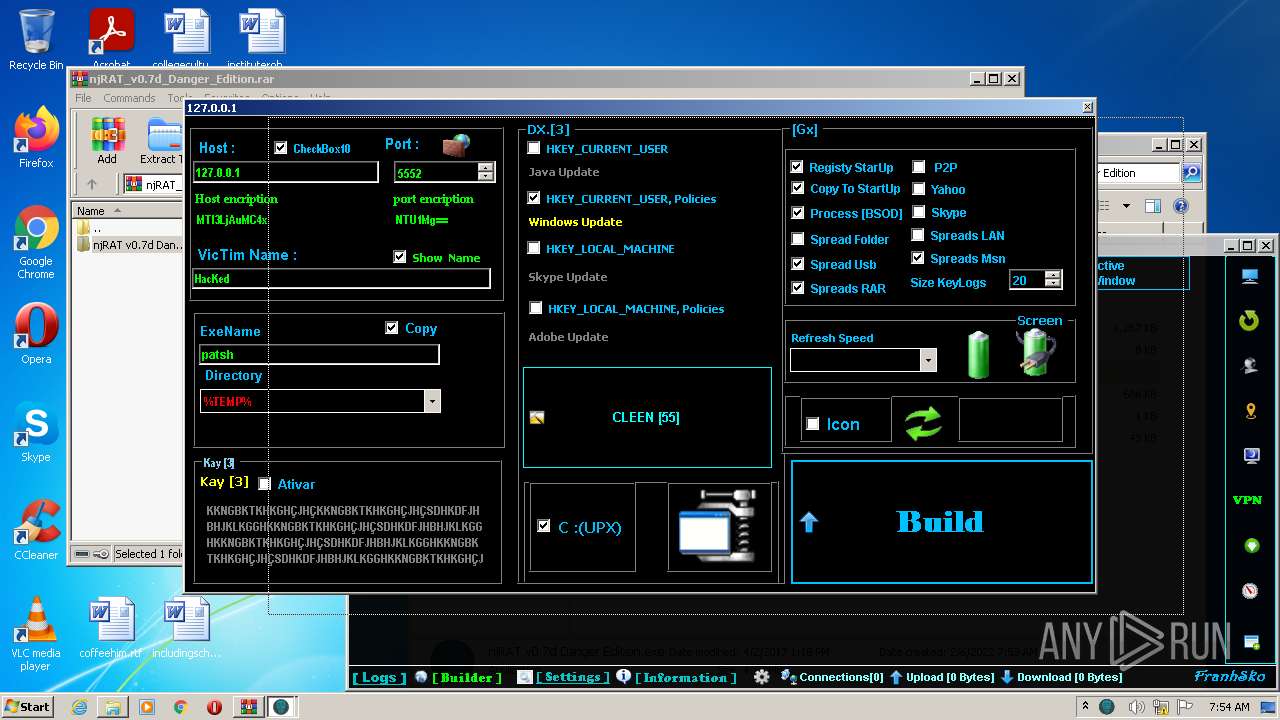
- njRAT v0.7d Danger Edition.exe (PID: 2956)
Application was dropped or rewritten from another process
- njRAT v0.7d Danger Edition.exe (PID: 2956)
SUSPICIOUS
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1380)
Checks supported languages
- WinRAR.exe (PID: 1380)
- njRAT v0.7d Danger Edition.exe (PID: 2956)
Reads the computer name
- WinRAR.exe (PID: 1380)
- njRAT v0.7d Danger Edition.exe (PID: 2956)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1380)
Reads Environment values
- njRAT v0.7d Danger Edition.exe (PID: 2956)
INFO
Manual execution by user
- njRAT v0.7d Danger Edition.exe (PID: 2956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | njRAT v0.7d Danger Edition\ar\NjRat 0.7D.resources.dll |
|---|---|
| PackingMethod: | Normal |
| ModifyDate: | 2017:04:01 19:30:20 |
| OperatingSystem: | Win32 |
| UncompressedSize: | 8192 |
| CompressedSize: | 1744 |
Total processes
37
Monitored processes
3
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1380 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\njRAT_v0.7d_Danger_Edition.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\Desktop\njRAT v0.7d Danger Edition\njRAT v0.7d Danger Edition.exe" | C:\Users\admin\Desktop\njRAT v0.7d Danger Edition\njRAT v0.7d Danger Edition.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3608 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
2 241
Read events
2 230
Write events
11
Delete events
0
Modification events
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\njRAT_v0.7d_Danger_Edition.rar | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1380) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
12
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\NjRat 0.7D.resources.dll | executable | |
MD5:87007C82A741E7F5E7AB4A7F55CBB65A | SHA256:808776A276F01826E3557D59E03513BA9F266FF69006B5CEEFF00C9D9EB7B44C | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\Plugin\mic.dll | executable | |
MD5:D4C5DDC00F27162FC0947830E0E762B7 | SHA256:B6FB6B66821E70A27A4750B0CD0393E4EE2603A47FEAC48D6A3D66D1C1CB56D5 | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\Plugin\cam.dll | executable | |
MD5:A73EDB60B80A2DFA86735D821BEA7B19 | SHA256:7A4977B024D048B71BCC8F1CC65FB06E4353821323F852DC6740B79B9AB75C98 | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\Plugin\ch.dll | executable | |
MD5:E747FA3339C1F138B6BFCE707B541D03 | SHA256:6E31148CC1B3235B71731C3944A7B06F861E104E978708D12C695EC09B5B3760 | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\njRAT v0.7d Danger Edition.exe | executable | |
MD5:85CFE00567DB5B2DF0648D8943D1CC94 | SHA256:AAF1D1465D24C051F9077FE5264C478E21FE3F62FF38196FE4622D09733B523E | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\Plugin\plg.dll | executable | |
MD5:0CBC2D9703FEEAD9783439E551C2B673 | SHA256:EA9ECF8723788FEEF6492BF938CDFAB1266A1558DFFE75E1F78A998320F96E39 | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\Plugin\sc2.dll | executable | |
MD5:19967E886EDCD2F22F8D4A58C8EA3773 | SHA256:3E5141C75B7746C0EB2B332082A165DEACB943CEF26BD84668E6B79B47BDFD93 | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\Stub.manifest | xml | |
MD5:4D18AC38A92D15A64E2B80447B025B7E | SHA256:835A00D6E7C43DB49AE7B3FA12559F23C2920B7530F4D3F960FD285B42B1EFB5 | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\ar\NjRat 0.7D.resources.dll | executable | |
MD5:EAC5655DAC58D912B4D5659621911503 | SHA256:7058F20403655057B6C9AE8EF520F817F950FEF281ACE567C43B80A90083C575 | |||
| 1380 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1380.18953\njRAT v0.7d Danger Edition\Stub.il | text | |
MD5:A44214201961678560414699F7490E11 | SHA256:801CA2B0C3066566B386FAAFA14133D93E84BD876445EF343EFA2EC29C042902 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report