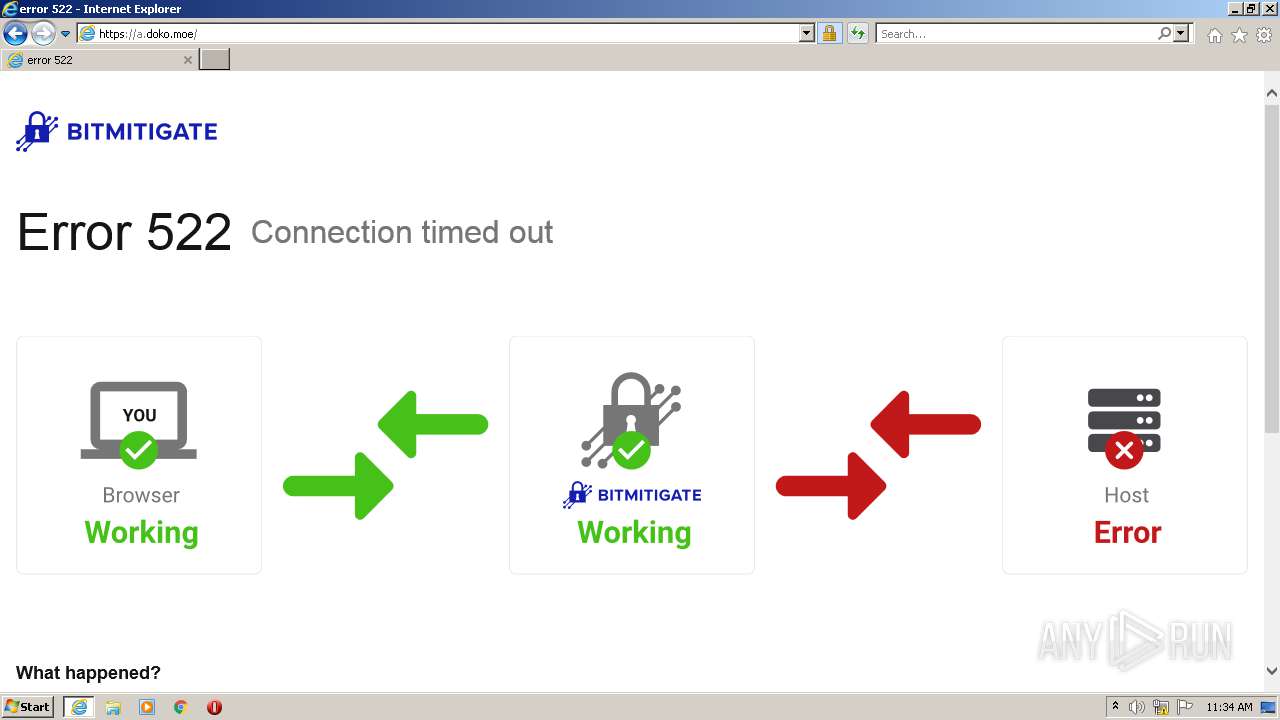
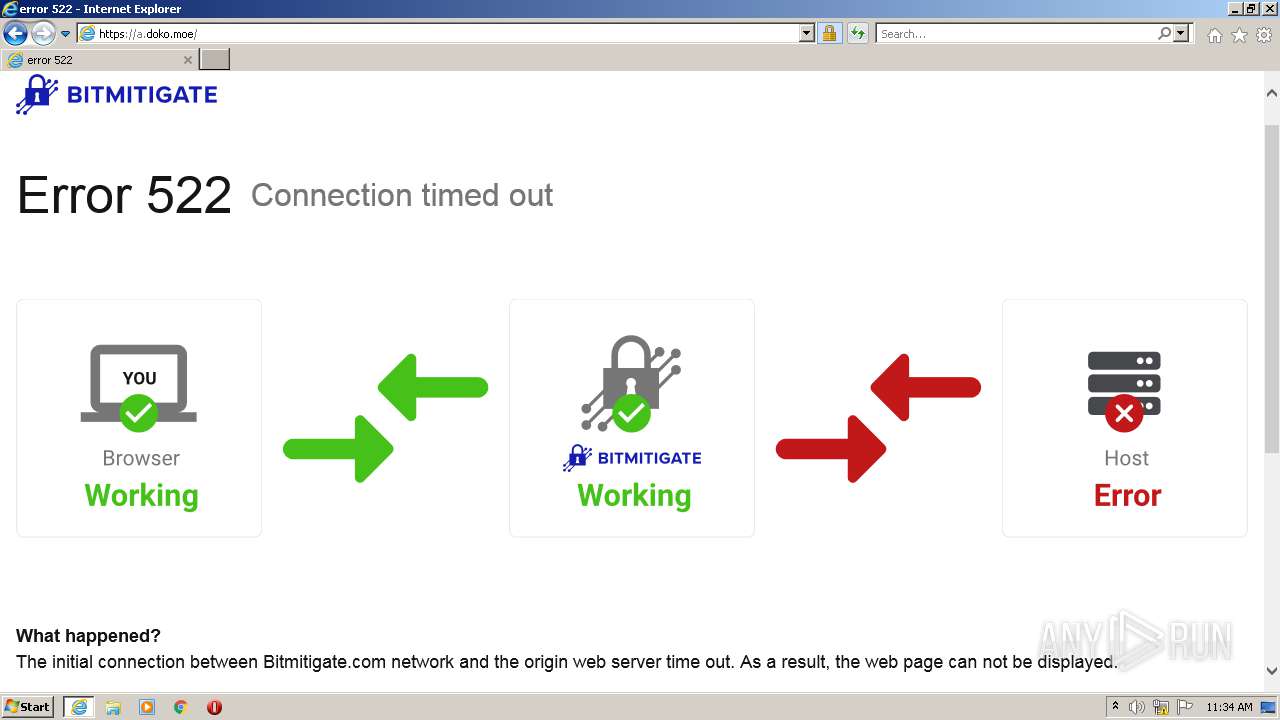
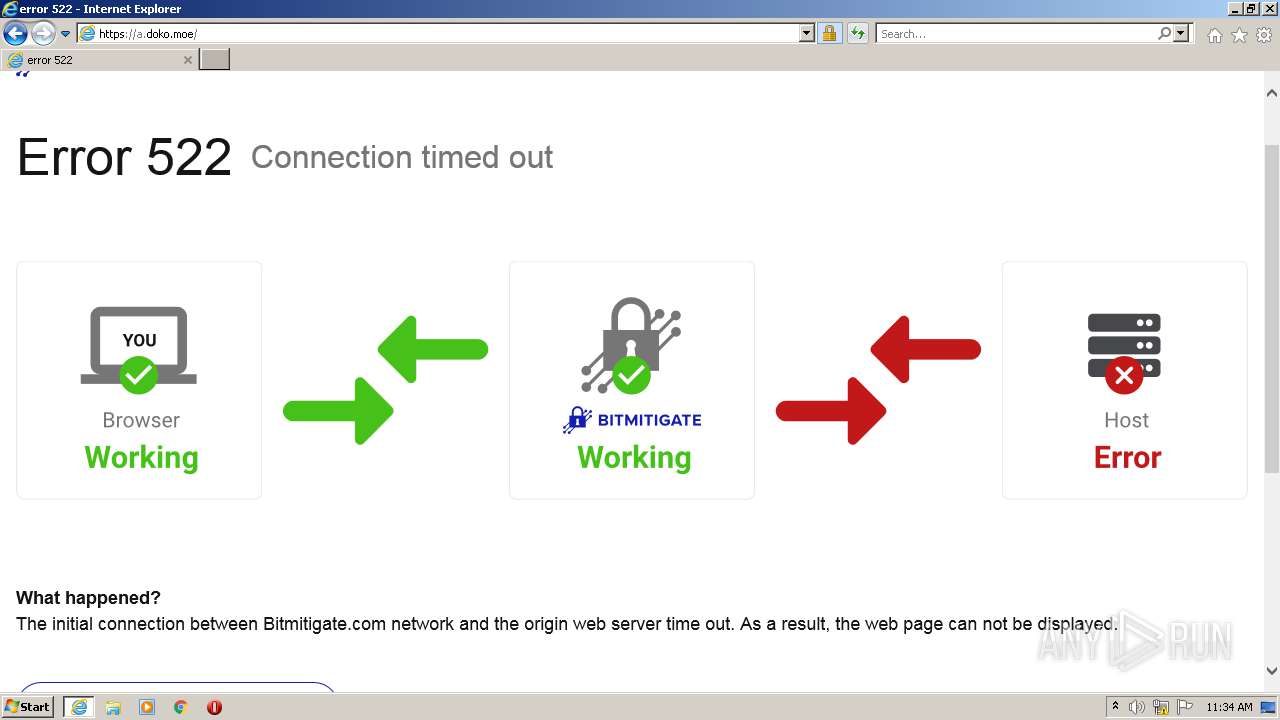
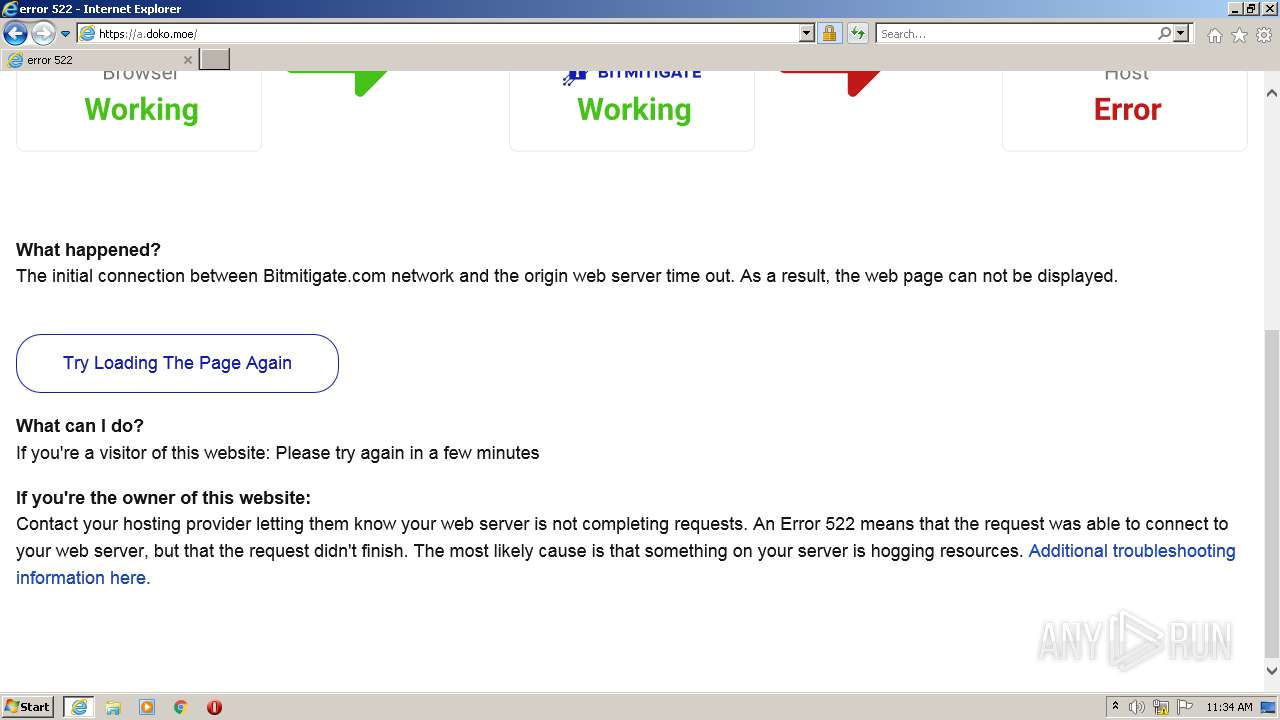
| URL: | http://a.doko.moe |
| Full analysis: | https://app.any.run/tasks/990bfd7e-34aa-44c8-aa72-24a4bc830356 |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2021, 10:33:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4A4AEB8F8AFF7D3EEBE0C9D4E225F691 |
| SHA1: | 9B7BFFF2FD8E91864DFABBE147D33AD3BB2B82AE |
| SHA256: | 056C2297BD7D7E744770B1C0AAACB9C8D8C7B59FDA7096FBFCD80EE86F43AE8A |
| SSDEEP: | 3:N1Kf1K6:C9K6 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2120)
Modifies files in Chrome extension folder
- chrome.exe (PID: 716)
INFO
Checks supported languages
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 2120)
- chrome.exe (PID: 1256)
- chrome.exe (PID: 292)
- chrome.exe (PID: 3812)
- chrome.exe (PID: 716)
- chrome.exe (PID: 828)
- chrome.exe (PID: 3708)
- chrome.exe (PID: 2692)
- chrome.exe (PID: 2016)
- chrome.exe (PID: 3044)
- chrome.exe (PID: 2228)
- chrome.exe (PID: 2880)
- chrome.exe (PID: 3264)
- chrome.exe (PID: 2956)
- chrome.exe (PID: 3272)
- chrome.exe (PID: 1696)
- chrome.exe (PID: 116)
- chrome.exe (PID: 2556)
- chrome.exe (PID: 3852)
- chrome.exe (PID: 2524)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 3584)
- chrome.exe (PID: 4084)
- chrome.exe (PID: 2692)
Reads the computer name
- chrome.exe (PID: 716)
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 2120)
- chrome.exe (PID: 1256)
- chrome.exe (PID: 828)
- chrome.exe (PID: 292)
- chrome.exe (PID: 3708)
- chrome.exe (PID: 2556)
Application launched itself
- iexplore.exe (PID: 3476)
- chrome.exe (PID: 716)
Changes internet zones settings
- iexplore.exe (PID: 3476)
Reads settings of System Certificates
- iexplore.exe (PID: 2120)
- iexplore.exe (PID: 3476)
- chrome.exe (PID: 1256)
Checks Windows Trust Settings
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 2120)
Reads internet explorer settings
- iexplore.exe (PID: 2120)
Reads the hosts file
- chrome.exe (PID: 716)
- chrome.exe (PID: 1256)
Manual execution by user
- chrome.exe (PID: 716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
59
Monitored processes
25
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,14776238890668202993,3769985874367936612,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3260 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1064,14776238890668202993,3769985874367936612,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1044 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 716 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --field-trial-handle=1064,14776238890668202993,3769985874367936612,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=audio --mojo-platform-channel-handle=3080 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1064,14776238890668202993,3769985874367936612,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1328 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,14776238890668202993,3769985874367936612,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2896 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,14776238890668202993,3769985874367936612,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2840 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3476 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,14776238890668202993,3769985874367936612,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3216 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2524 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1064,14776238890668202993,3769985874367936612,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3240 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
35 906
Read events
35 738
Write events
168
Delete events
0
Modification events
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 944387696 | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30901349 | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30901349 | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
43
Text files
169
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\compare_arrows_24px[1].svg | image | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\Logo[1].svg | image | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\app[1].css | text | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_A73D012718C94E81B9224F97262C7D1D | der | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\functions[1].js | text | |
MD5:— | SHA256:— | |||
| 2120 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5F6CFEFDA9005206F80593B3079304CC | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
61
DNS requests
30
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | iexplore.exe | GET | 200 | 23.55.163.73:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
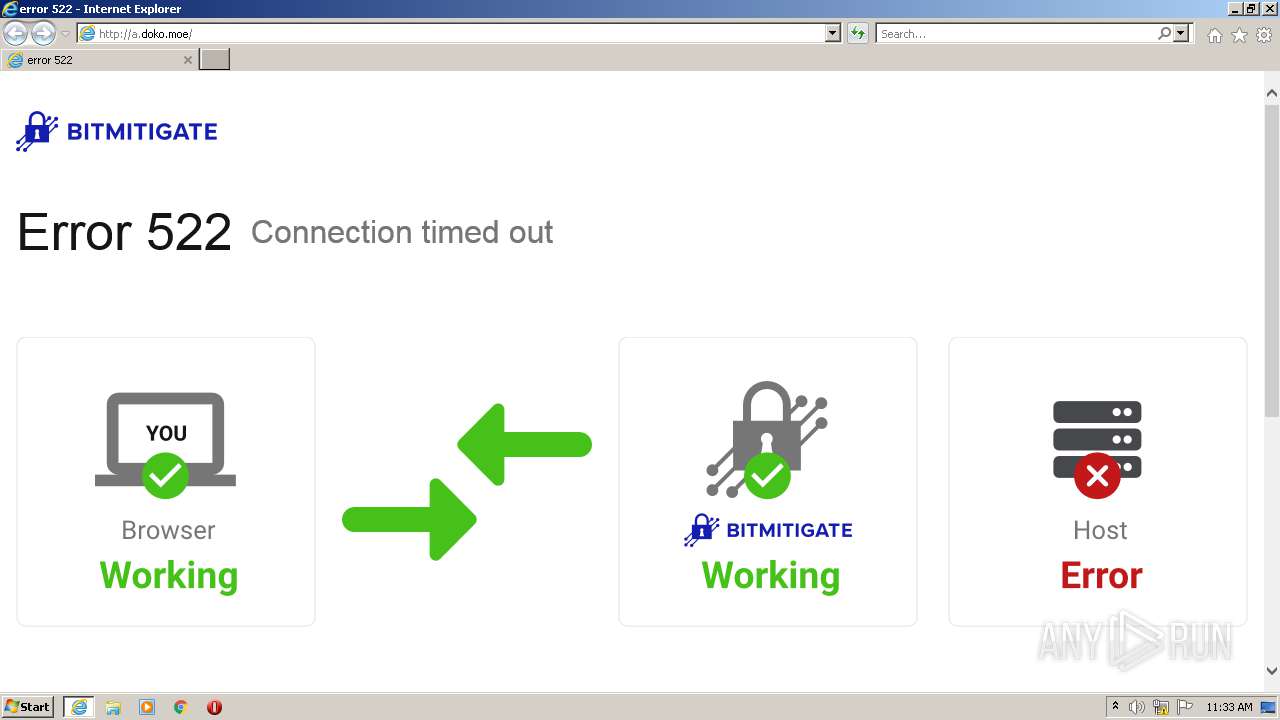
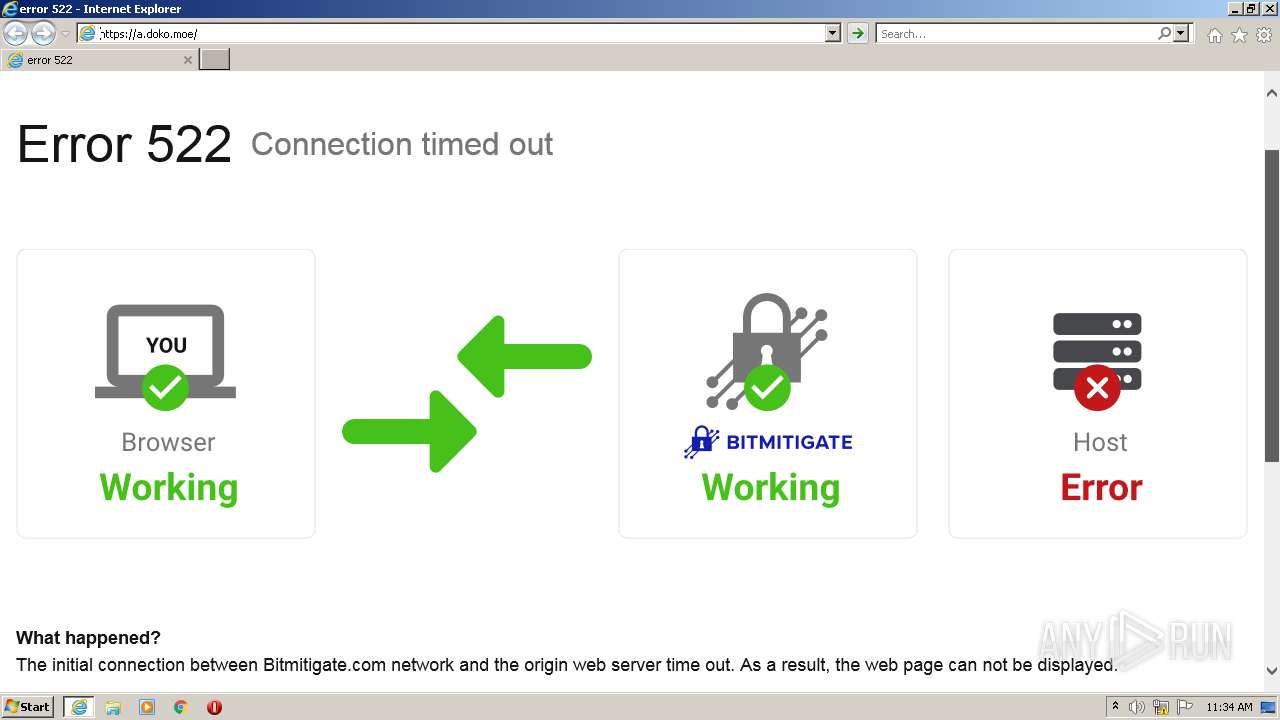
2120 | iexplore.exe | GET | 502 | 45.88.202.111:80 | http://a.doko.moe/ | unknown | html | 2.33 Kb | malicious |
2120 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEQDol4NJl4zPQyZl%2B4IS3XVD | US | der | 728 b | whitelisted |
2120 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
2120 | iexplore.exe | GET | 200 | 23.55.163.48:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNRPM2Uzd8z8YRd5Xo6vT4kfw%3D%3D | US | der | 503 b | shared |
3476 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2120 | iexplore.exe | GET | 200 | 2.16.186.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1e1d4d96bbacda66 | unknown | compressed | 4.70 Kb | whitelisted |
2120 | iexplore.exe | GET | 200 | 2.16.186.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2401b052d8460be5 | unknown | compressed | 4.70 Kb | whitelisted |
2120 | iexplore.exe | GET | 200 | 2.16.186.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3c690d9553e84248 | unknown | compressed | 4.70 Kb | whitelisted |
2120 | iexplore.exe | GET | 200 | 2.16.186.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4474a3cded3076de | unknown | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | iexplore.exe | 45.88.202.101:443 | bitmitigate.com | — | — | unknown |
2120 | iexplore.exe | 2.16.186.25:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3476 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2120 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
3476 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2120 | iexplore.exe | 104.117.200.9:80 | x1.c.lencr.org | TPG Telecom Limited | US | unknown |
2120 | iexplore.exe | 23.55.163.73:80 | crl.identrust.com | Akamai International B.V. | US | unknown |
— | — | 2.16.186.41:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
2120 | iexplore.exe | 23.55.163.48:80 | r3.o.lencr.org | Akamai International B.V. | US | unknown |
3476 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
a.doko.moe |
| unknown |
bitmitigate.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
dnencrypt.ocsp.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
Threats
2 ETPRO signatures available at the full report