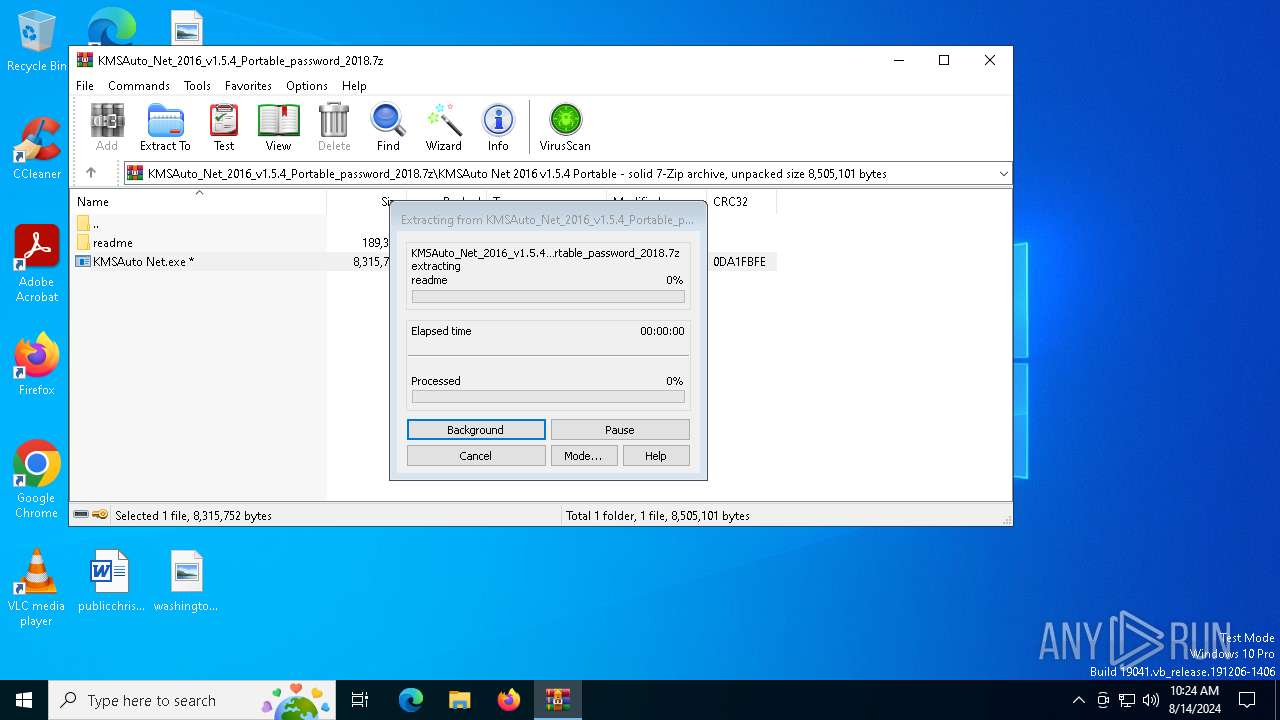
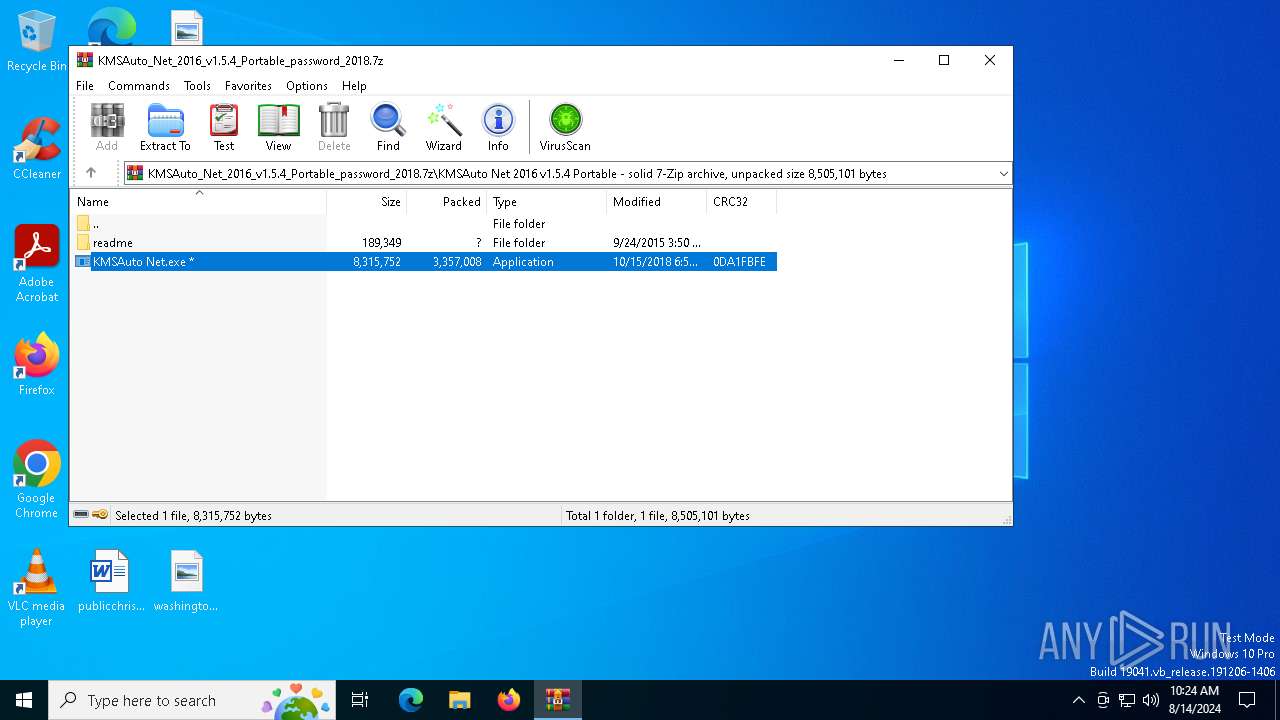
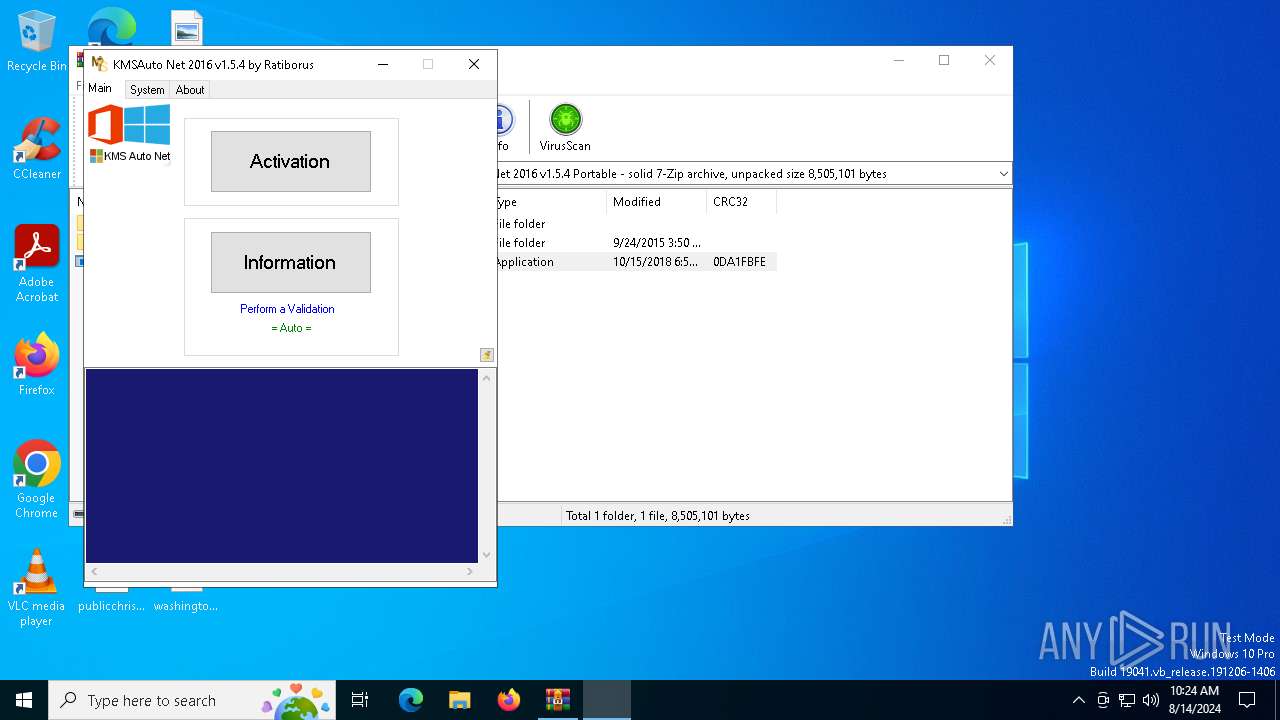
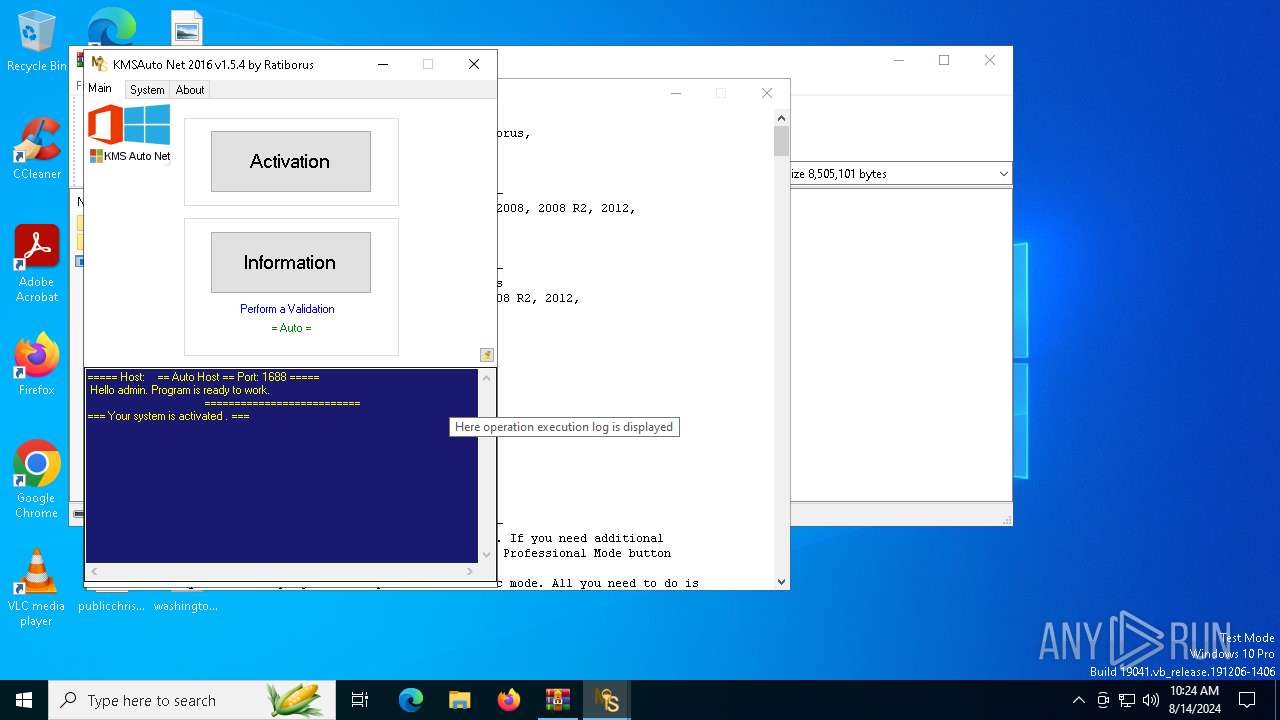
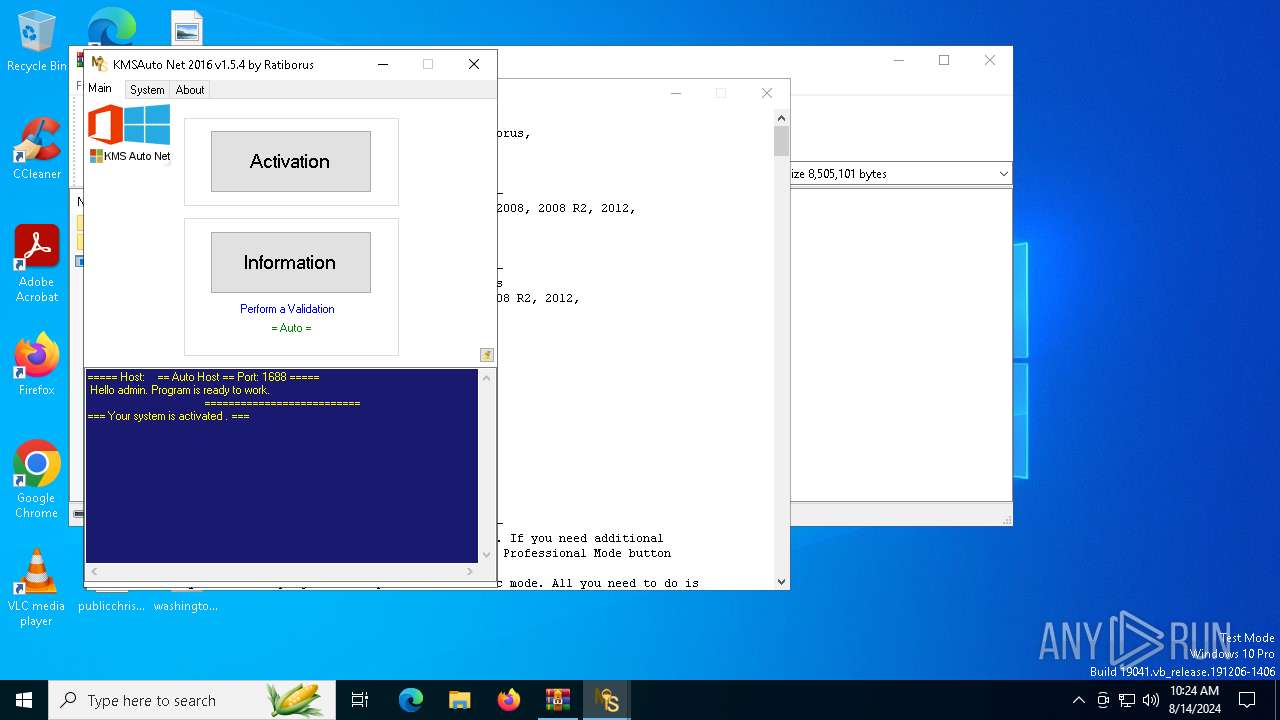
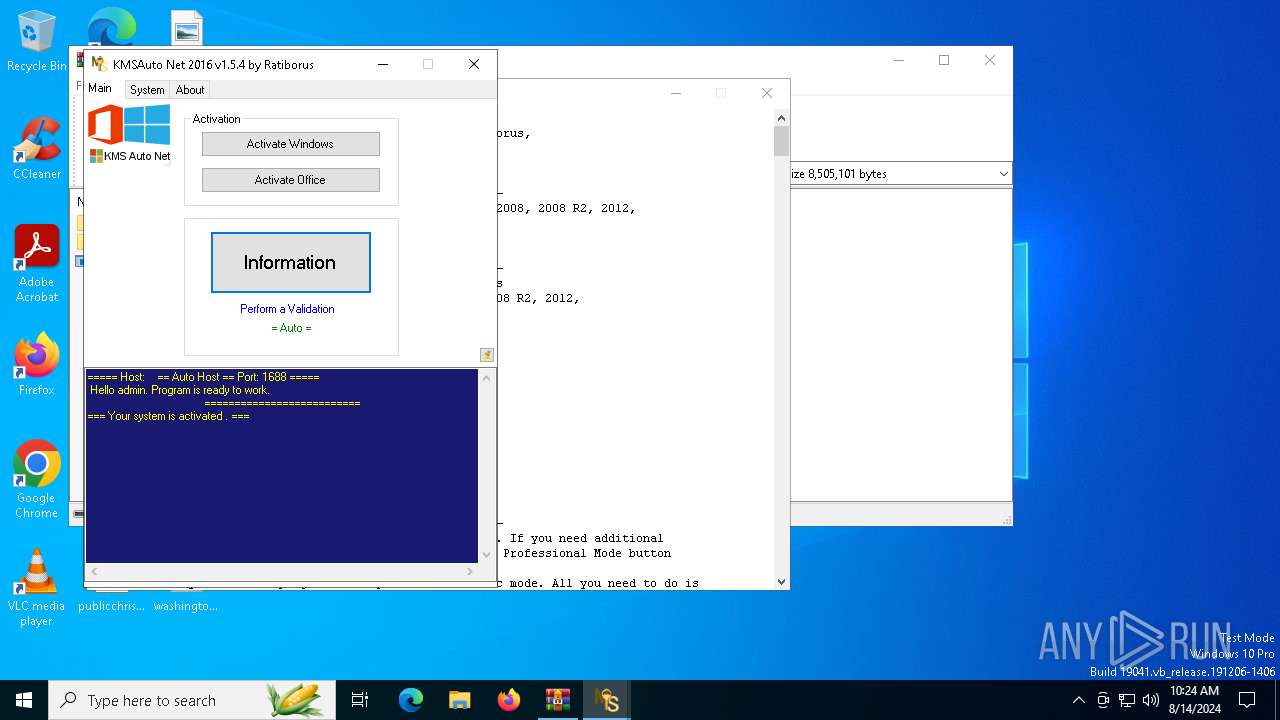
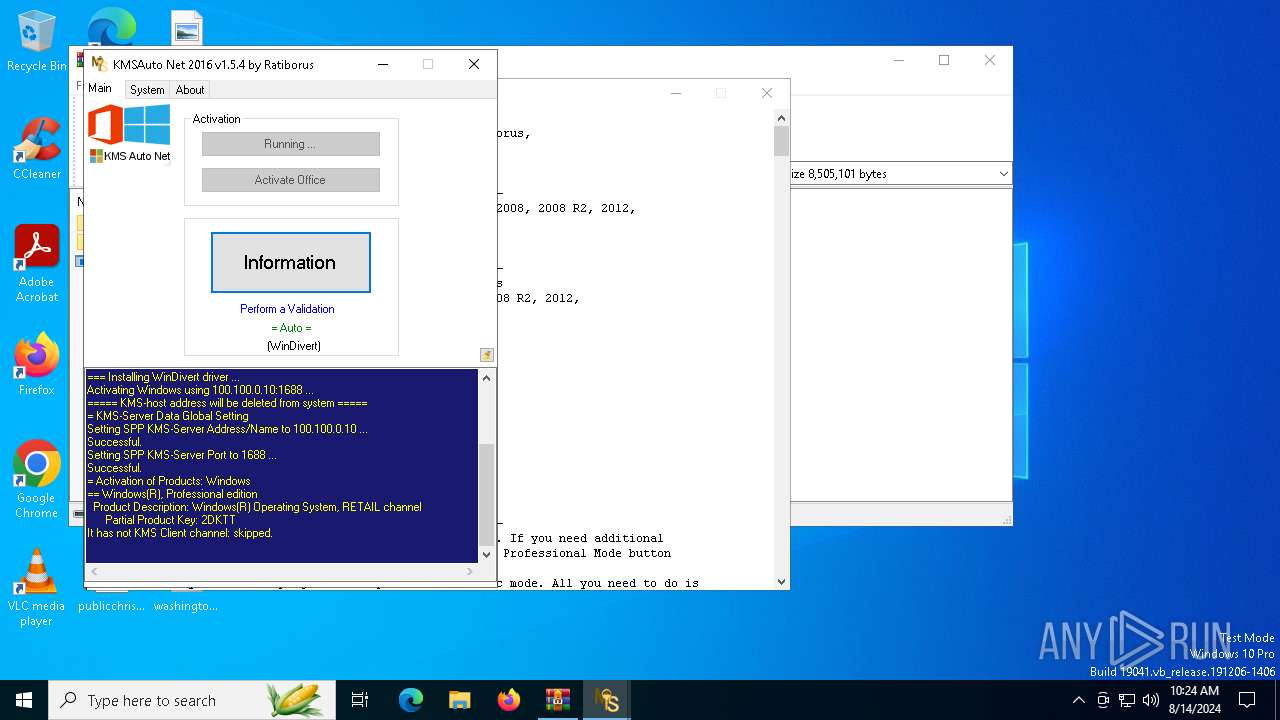
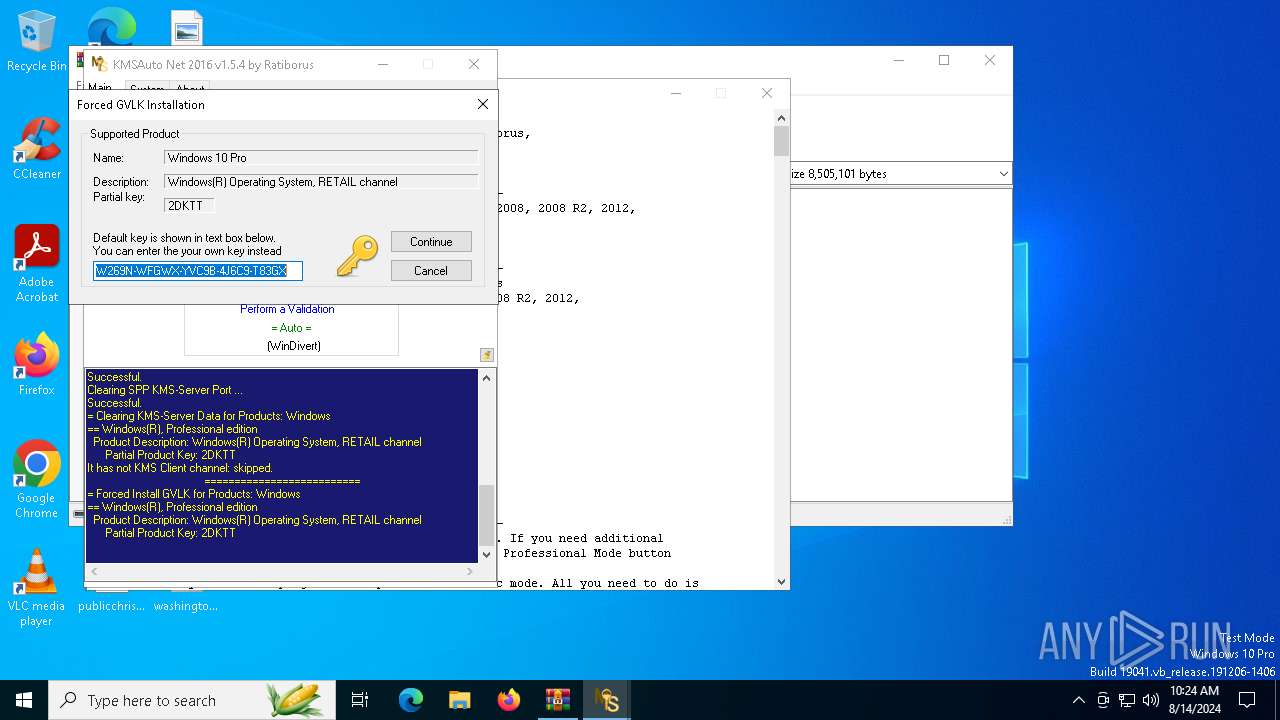
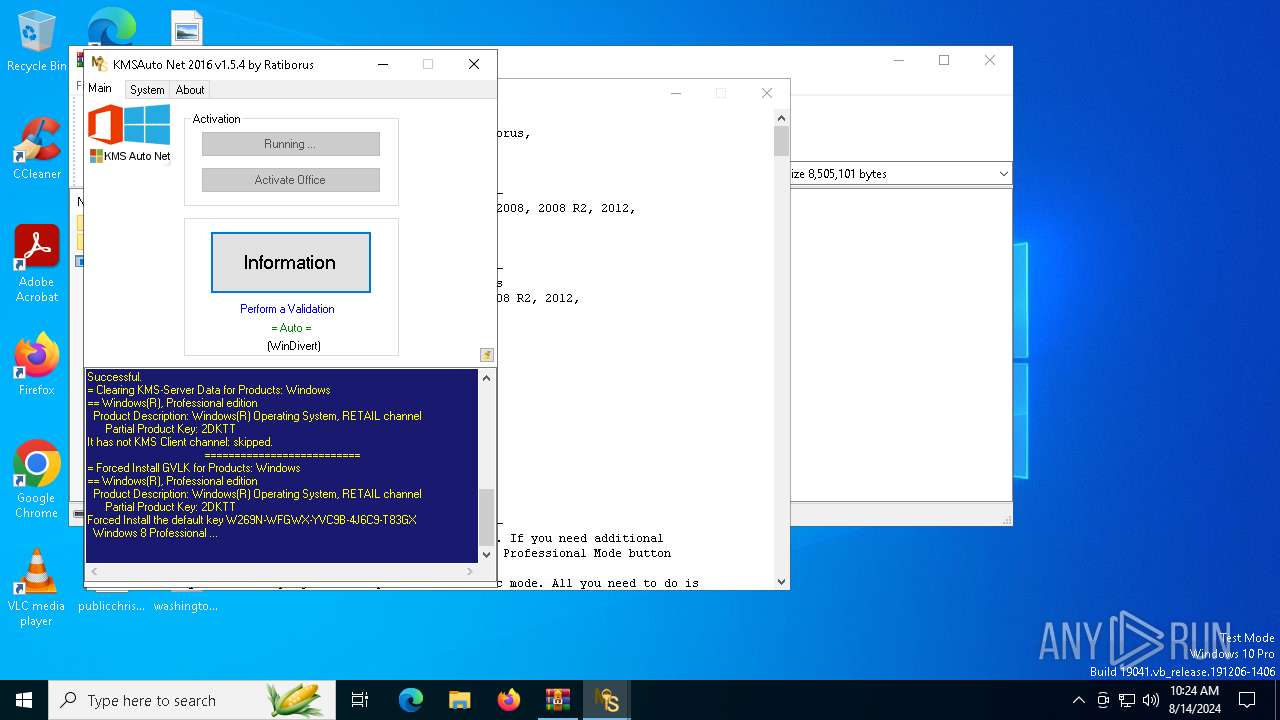
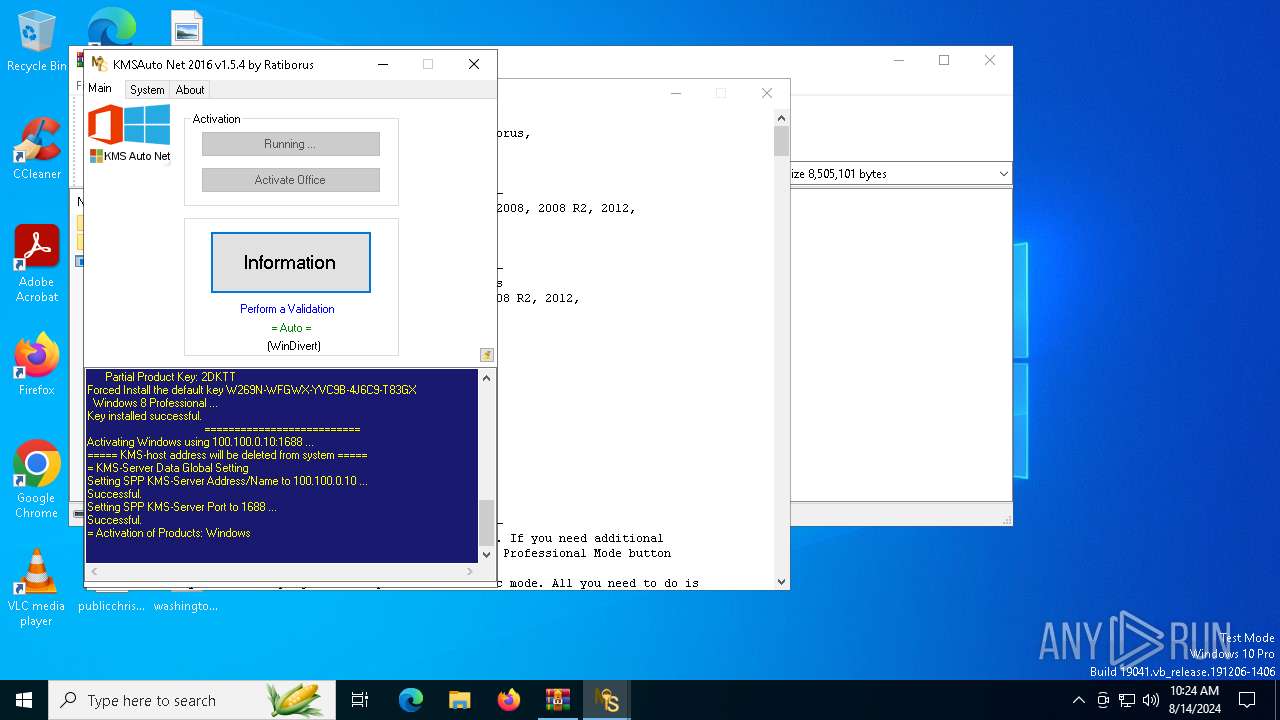
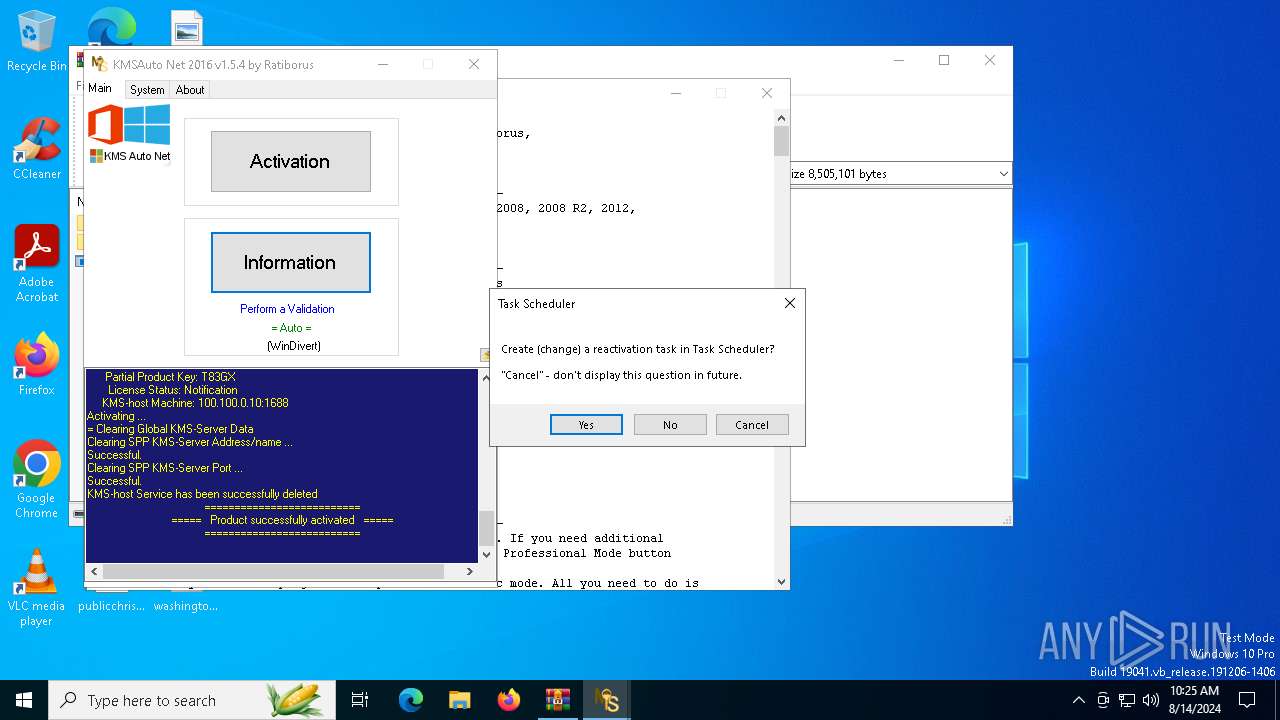
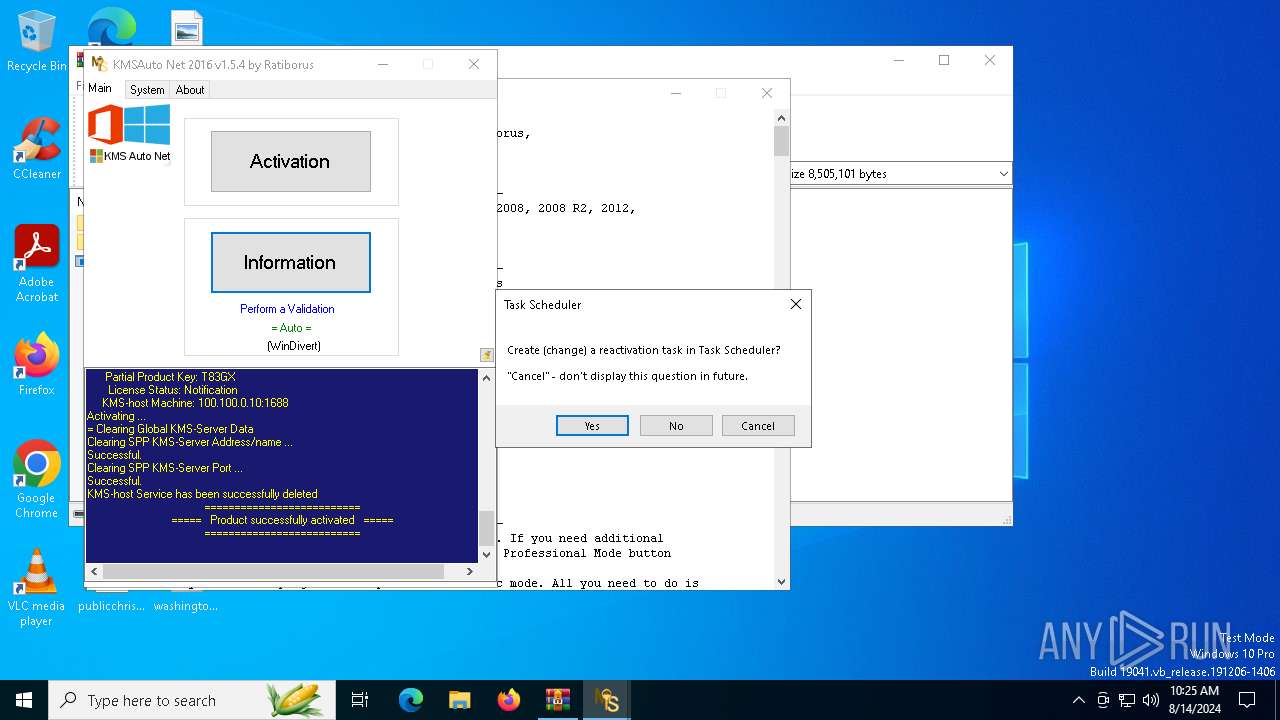
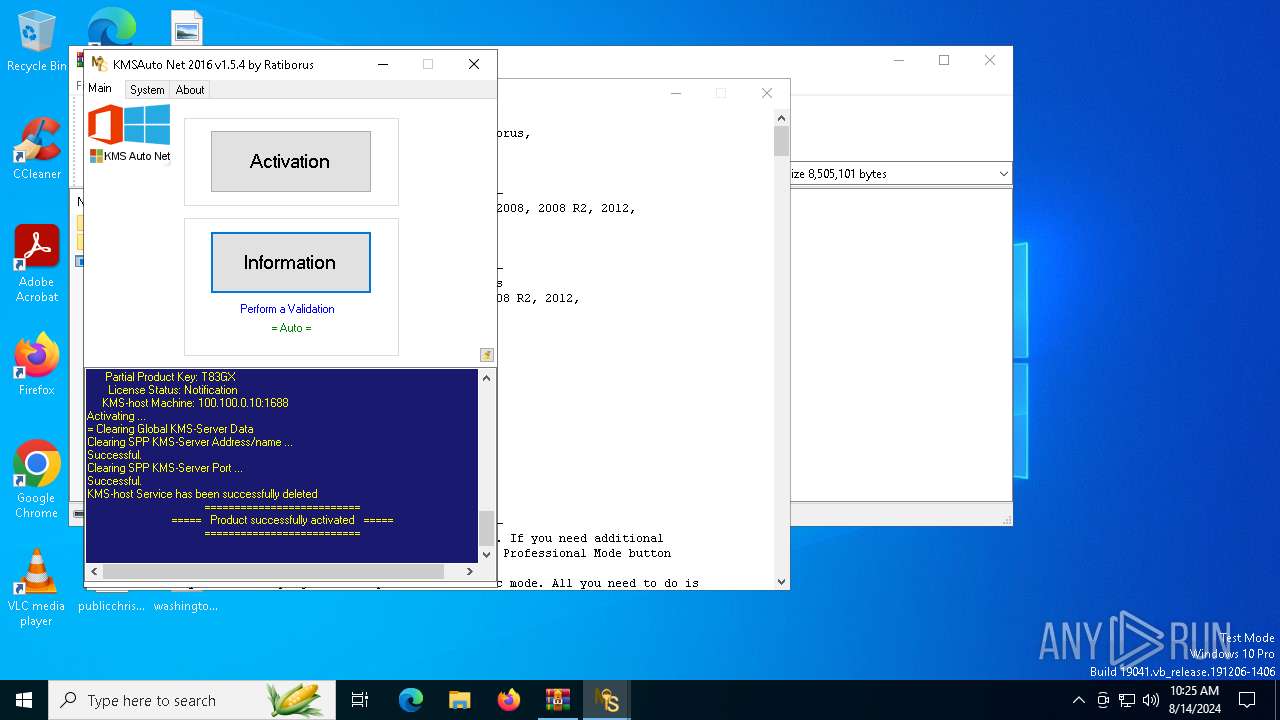
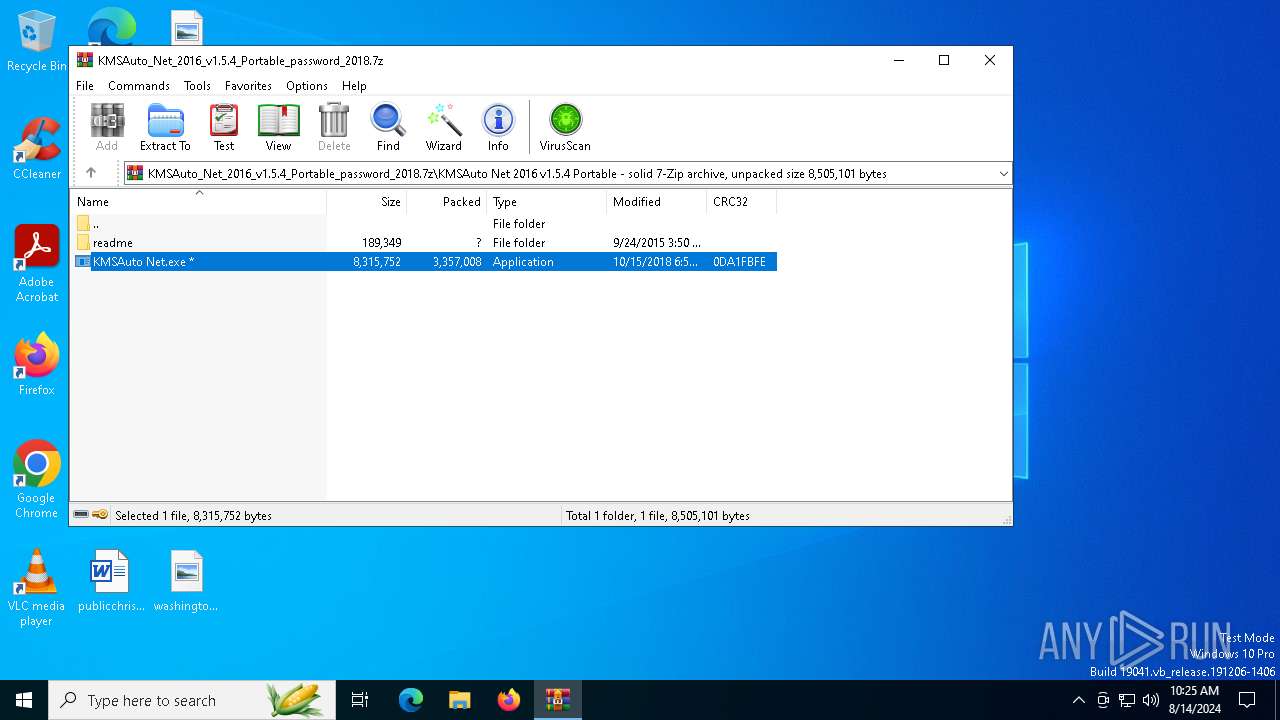
| File name: | KMSAuto_Net_2016_v1.5.4_Portable_password_2018.7z |
| Full analysis: | https://app.any.run/tasks/efc83ec5-6a13-47b7-a092-627d5658bf95 |
| Verdict: | Malicious activity |
| Analysis date: | August 14, 2024, 10:23:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | EE6EA04B058E3B0D38A716756597B4F8 |
| SHA1: | D59140C07BA68A8E0945CCD66746BD106FDED491 |
| SHA256: | 056684B471526B2CC044E2CB09E3C2B42CDA9FF1547617A43CF44890BE3030C5 |
| SSDEEP: | 98304:hnRrX1d8JMu3gerrZdZcWoSWvyE3GX/gQJ69l66tV2mA3f+zqxEin4PwpYDbw3VB:VnlXb/vaylg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6452)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 6876)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 6876)
- cmd.exe (PID: 1568)
Executable content was dropped or overwritten
- KMSAuto Net.exe (PID: 6876)
- bin.dat (PID: 644)
- bin_x64.dat (PID: 6152)
- AESDecoder.exe (PID: 2096)
- bin_x64.dat (PID: 4316)
- wzt.dat (PID: 4844)
Process drops legitimate windows executable
- wzt.dat (PID: 4844)
- bin_x64.dat (PID: 6152)
- bin_x64.dat (PID: 4316)
Drops the executable file immediately after the start
- bin.dat (PID: 644)
- KMSAuto Net.exe (PID: 6876)
- AESDecoder.exe (PID: 2096)
- bin_x64.dat (PID: 6152)
- bin_x64.dat (PID: 4316)
- wzt.dat (PID: 4844)
Adds/modifies Windows certificates
- certmgr.exe (PID: 1568)
- certmgr.exe (PID: 6028)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 6876)
Starts application with an unusual extension
- cmd.exe (PID: 3184)
- cmd.exe (PID: 6276)
- cmd.exe (PID: 3104)
- cmd.exe (PID: 840)
Drops a system driver (possible attempt to evade defenses)
- bin_x64.dat (PID: 6152)
- bin_x64.dat (PID: 4316)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 6876)
Application launched itself
- cmd.exe (PID: 1568)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 6876)
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 6876)
Executes as Windows Service
- KMSSS.exe (PID: 6228)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 6804)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6420)
Uses REG/REGEDIT.EXE to modify registry
- KMSAuto Net.exe (PID: 6876)
- cmd.exe (PID: 6564)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 5944)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6452)
Reads Environment values
- KMSAuto Net.exe (PID: 6876)
Reads the computer name
- KMSAuto Net.exe (PID: 6876)
- KMSSS.exe (PID: 6228)
- FakeClient.exe (PID: 3352)
Create files in a temporary directory
- cmd.exe (PID: 6992)
Checks supported languages
- KMSAuto Net.exe (PID: 6876)
- bin.dat (PID: 644)
- certmgr.exe (PID: 1568)
- certmgr.exe (PID: 6028)
- AESDecoder.exe (PID: 2096)
- bin_x64.dat (PID: 6152)
- KMSSS.exe (PID: 6228)
- bin_x64.dat (PID: 4316)
- FakeClient.exe (PID: 3352)
- wzt.dat (PID: 4844)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 6876)
Reads the machine GUID from the registry
- KMSAuto Net.exe (PID: 6876)
- KMSSS.exe (PID: 6228)
Reads product name
- KMSAuto Net.exe (PID: 6876)
Creates files in the program directory
- cmd.exe (PID: 6448)
- bin.dat (PID: 644)
- bin_x64.dat (PID: 6152)
- AESDecoder.exe (PID: 2096)
- KMSSS.exe (PID: 6228)
- bin_x64.dat (PID: 4316)
- KMSAuto Net.exe (PID: 6876)
- wzt.dat (PID: 4844)
UPX packer has been detected
- KMSAuto Net.exe (PID: 6876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
254
Monitored processes
114
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 32 | C:\WINDOWS\Sysnative\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0FF1CE15-A989-479D-AF46-F275C6370663" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 32 | "sc.exe" delete WinDivert1.1 | C:\Windows\SysWOW64\sc.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | bin.dat -y -pkmsauto | C:\ProgramData\KMSAuto\bin.dat | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 15.14 Modules
| |||||||||||||||
| 840 | C:\WINDOWS\Sysnative\cmd.exe /D /c wzt.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | reg.exe DELETE HKLM\SYSTEM\CurrentControlSet\Services\KMSEmulator /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | C:\WINDOWS\Sysnative\cmd.exe /D /c del /F /Q "bin_x64.dat" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | "sc.exe" start KMSEmulator | C:\Windows\SysWOW64\sc.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 448
Read events
16 401
Write events
39
Delete events
8
Modification events
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAuto_Net_2016_v1.5.4_Portable_password_2018.7z | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
28
Suspicious files
12
Text files
14
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6452.35728\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_ua.txt | text | |
MD5:304890B34C6E1277E6BD8B25F4080E64 | SHA256:B00BBCA133BDB04B2D89477288BFC13900415EC84C7E708A2DA926E799B24C01 | |||
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6452.35728\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_es.txt | text | |
MD5:12C9AEB3C00E3B094EBECF0D85BAC503 | SHA256:E5570A6208DCFE1D0F59F41B4410050614464DAE270A3EEEF27D1E3D3A970F56 | |||
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6452.35728\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_kms.txt | text | |
MD5:352709B6AED3902D4399F6615A7A7E70 | SHA256:D3BEF0FEF19603B33B86E1CA431A25CB8A6DF047058E073BBF8BB931533217AA | |||
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6452.35728\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_vi.txt | text | |
MD5:7F4691631E5D8D0E2677C4A770D9D78D | SHA256:60C17FD8F5F6D7C95360D523CEE81998DEFC3AE04C43CC7A7C9231A53C041B98 | |||
| 4844 | wzt.dat | C:\ProgramData\KMSAuto\wzt\wzteam.cer | binary | |
MD5:76B56D90E6F1DA030A8B85E64579F25A | SHA256:FD2D7DF0220DD65EE23D0090299DFCC356F6F8F7167BAE9ADF7D08CEFAF39D02 | |||
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6452.35728\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_fr.txt | text | |
MD5:4A8B83F2E300AD728DF3022B4090746C | SHA256:065F293D1F516C2723B56DD1E52F86DFD0008F474194FD51FFCB607796D24FEC | |||
| 6992 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6452.35728\KMSAuto Net 2016 v1.5.4 Portable\test.test | text | |
MD5:9F06243ABCB89C70E0C331C61D871FA7 | SHA256:837CCB607E312B170FAC7383D7CCFD61FA5072793F19A25E75FBACB56539B86B | |||
| 6876 | KMSAuto Net.exe | C:\Users\admin\AppData\Local\MSfree Inc\kmsauto.ini | text | |
MD5:AF6A20FD7DFADCD582CCF2B1BFAAF82B | SHA256:0BEE97833A70AA9BA271E93226DACE849836C64919FBFE15543D694E219D4AF2 | |||
| 6876 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\wzt.dat | executable | |
MD5:822DA2319294F2B768BFE9ED4EEBAC15 | SHA256:17B74D4EA905FAC0BA6857F78F47EE1E940675AF1BC27DED69FE2941318106EF | |||
| 644 | bin.dat | C:\ProgramData\KMSAuto\bin\KMSSS.exe.aes | binary | |
MD5:41E0D8AB5104DA2068739109EC3599F4 | SHA256:38D1DBDC7C7A64253E6D4B52225B0BFD7716405C731A107F0C6BA9573A73A77F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
46
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1948 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1948 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4692 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7164 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2064 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4088 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 184.86.251.17:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1948 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1948 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
FakeClient.exe | WdfCoInstaller: [08/14/2024 10:24.31.864] ReadComponents: WdfSection for Driver Service windivert using KMDF lib version Major 0x1, minor 0x9
|
FakeClient.exe | WdfCoInstaller: [08/14/2024 10:24.31.880] BootApplication: could not open service windivert, error error(1060) The specified service does not exist as an installed service.
|
FakeClient.exe | WdfCoInstaller: [08/14/2024 10:24.31.880] BootApplication: GetStartType error error(87) The parameter is incorrect.
Driver Service name windivert
|