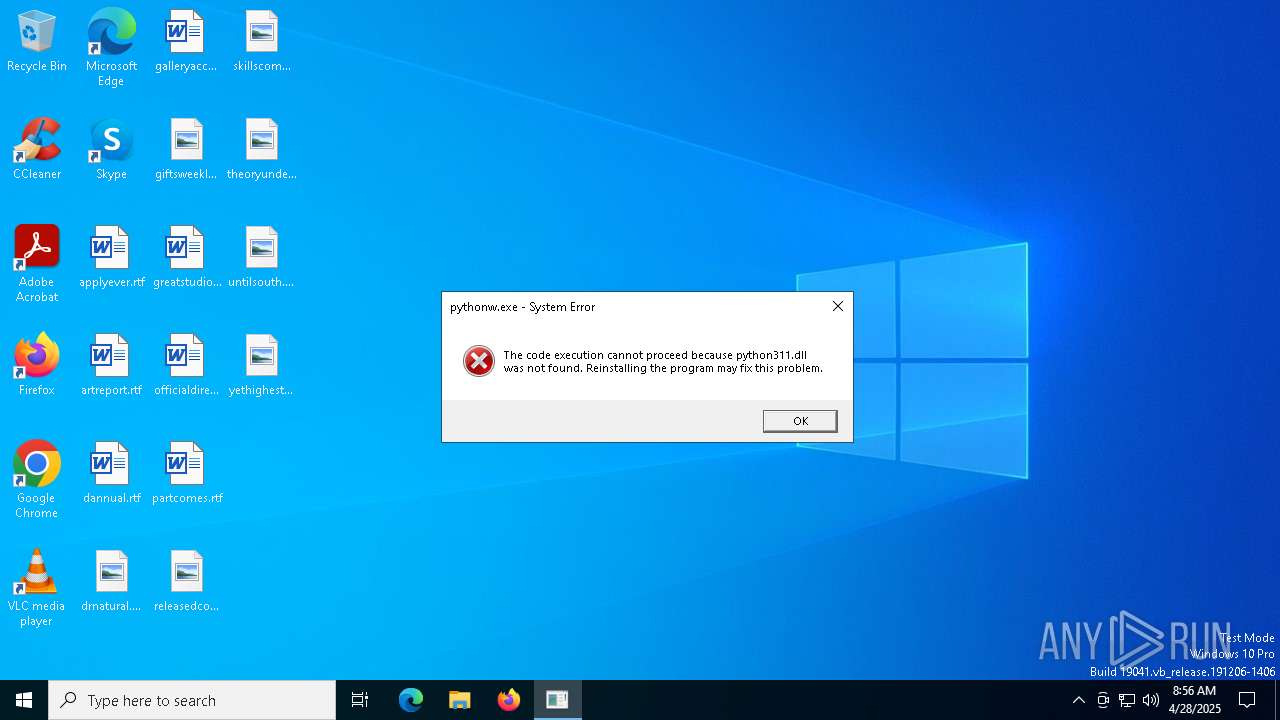
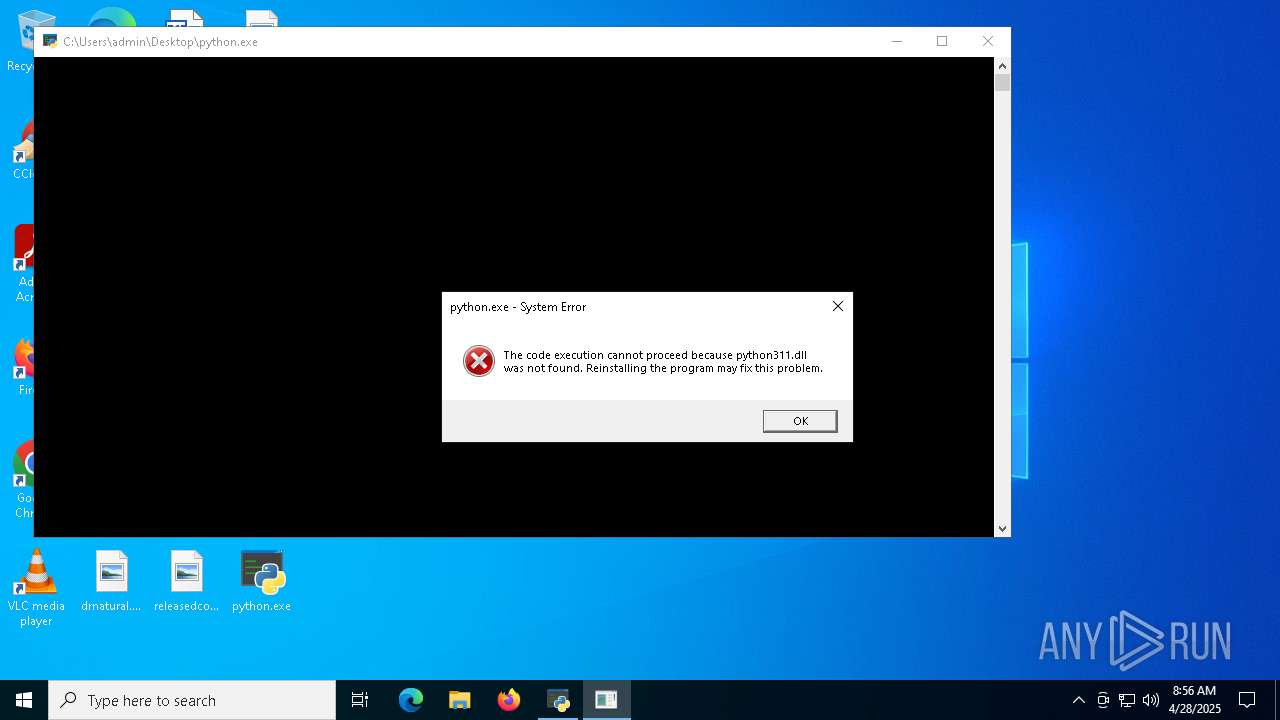
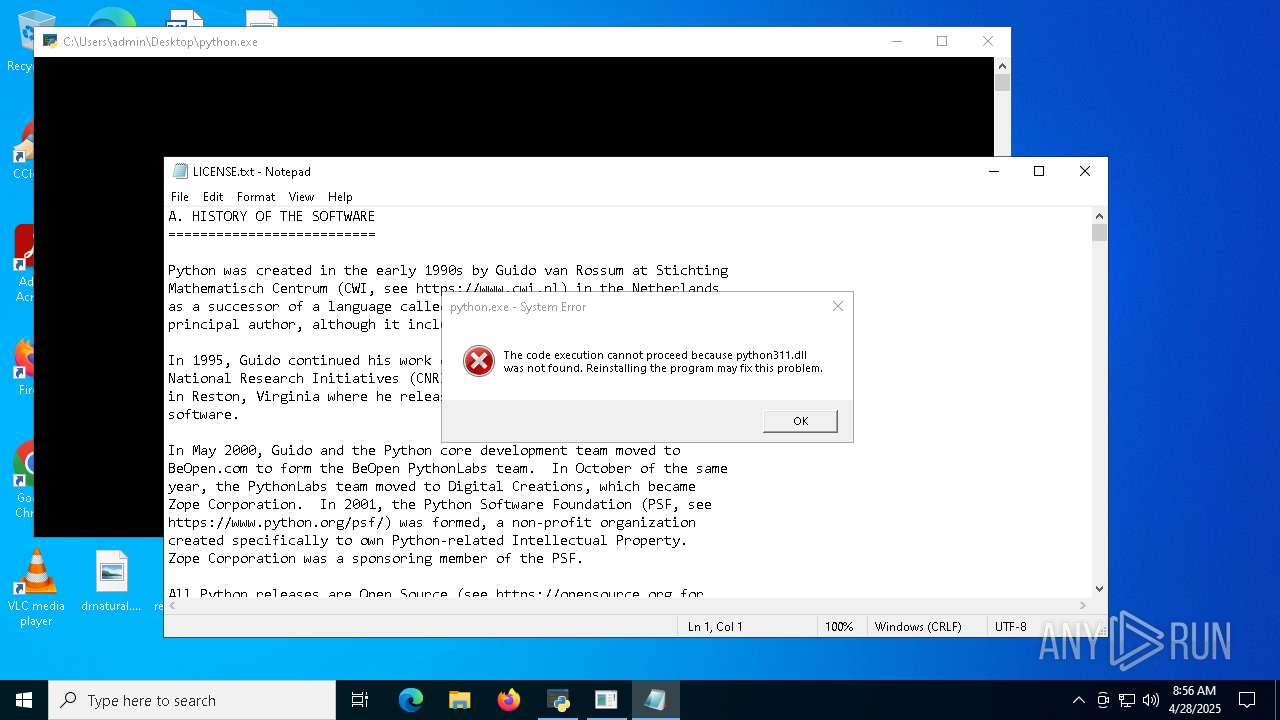
| File name: | 5307e6e80026ce038ec5d185c79aa840.exe |
| Full analysis: | https://app.any.run/tasks/6f5a819b-61be-4c57-9317-670f39e9cfdb |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2025, 08:55:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 15 sections |
| MD5: | 5307E6E80026CE038EC5D185C79AA840 |
| SHA1: | E098694951E00B047D1F262FF9E11142B2742341 |
| SHA256: | 054CB1E0B461069397D1FEBD61C464305BA0787920FCE8433E602D73EFADAE42 |
| SSDEEP: | 98304:Hsq6VdPIw06jRroLaOh3WuHjPue3/ZSCIBAaXoFmvGqcysFcgIEEpunrVgbKbuUC:2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
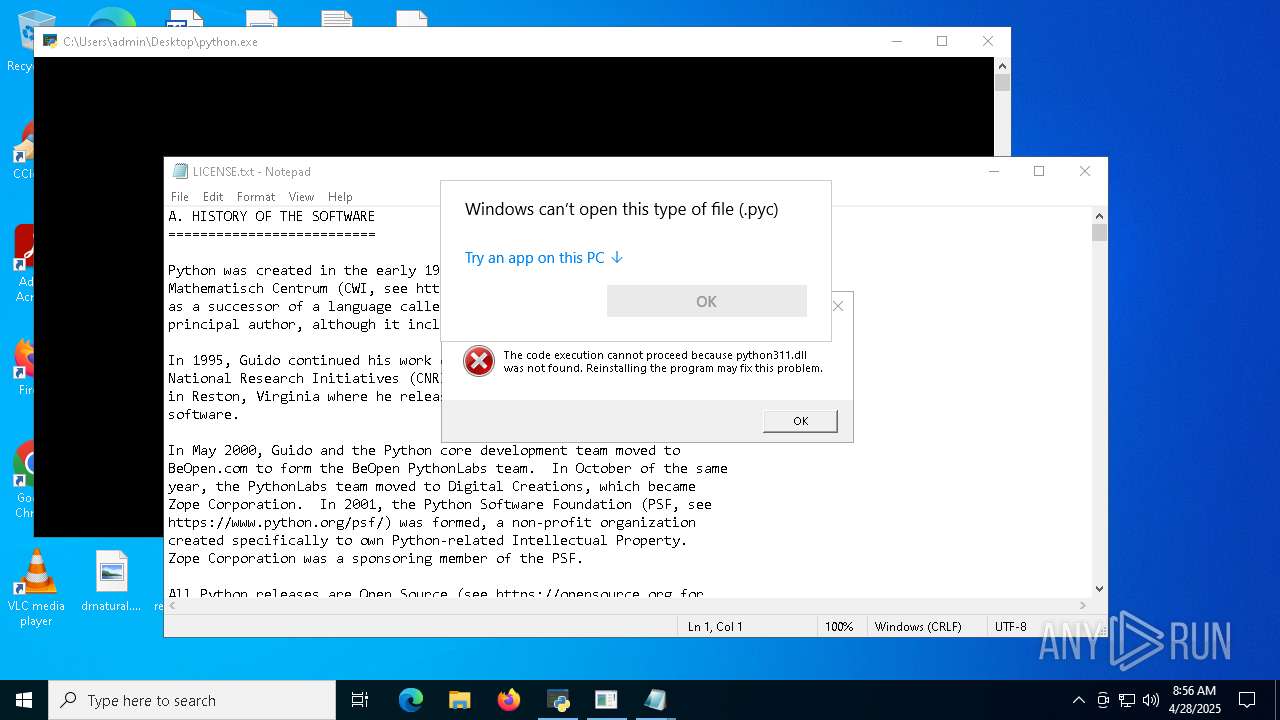
Process drops python dynamic module
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
Process drops legitimate windows executable
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
Executable content was dropped or overwritten
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
The process drops C-runtime libraries
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
INFO
Reads the software policy settings
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
- slui.exe (PID: 6944)
Creates files or folders in the user directory
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
Checks supported languages
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
Reads the machine GUID from the registry
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
Reads the computer name
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
The sample compiled with english language support
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
Attempting to use instant messaging service
- 5307e6e80026ce038ec5d185c79aa840.exe (PID: 3300)
Manual execution by a user
- OpenWith.exe (PID: 1280)
- notepad.exe (PID: 6824)
- OpenWith.exe (PID: 1052)
- OpenWith.exe (PID: 920)
- pythonw.exe (PID: 2772)
- notepad.exe (PID: 736)
- python.exe (PID: 5756)
- OpenWith.exe (PID: 7152)
- OpenWith.exe (PID: 6736)
- OpenWith.exe (PID: 1096)
- OpenWith.exe (PID: 5548)
- OpenWith.exe (PID: 1272)
- OpenWith.exe (PID: 960)
- OpenWith.exe (PID: 1312)
- OpenWith.exe (PID: 5720)
- OpenWith.exe (PID: 3784)
- OpenWith.exe (PID: 6828)
- OpenWith.exe (PID: 2384)
- OpenWith.exe (PID: 4424)
- OpenWith.exe (PID: 1388)
- OpenWith.exe (PID: 6136)
- OpenWith.exe (PID: 5384)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6824)
- notepad.exe (PID: 736)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 920)
- OpenWith.exe (PID: 1280)
- OpenWith.exe (PID: 6736)
- OpenWith.exe (PID: 7152)
- OpenWith.exe (PID: 5548)
- OpenWith.exe (PID: 2384)
- OpenWith.exe (PID: 1272)
- OpenWith.exe (PID: 960)
- OpenWith.exe (PID: 1096)
- OpenWith.exe (PID: 1312)
- OpenWith.exe (PID: 5720)
- OpenWith.exe (PID: 3784)
- OpenWith.exe (PID: 6828)
- OpenWith.exe (PID: 1052)
- OpenWith.exe (PID: 4424)
- OpenWith.exe (PID: 5384)
- OpenWith.exe (PID: 6136)
- OpenWith.exe (PID: 1388)
Python executable
- pythonw.exe (PID: 2772)
- python.exe (PID: 5756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2530304 |
| InitializedDataSize: | 252928 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x73e60 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
Total processes
155
Monitored processes
27
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\LICENSE.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\__init__.pyc | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\README | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | python.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\sre_parse.pyc | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\__init__.pyc | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\fetch_macholib | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\cElementTree.pyc | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1312 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\log.pyc | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\__init__.pyc | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 070
Read events
13 070
Write events
0
Delete events
0
Modification events
Executable files
30
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\_bz2.pyd | executable | |
MD5:3859239CED9A45399B967EBCE5A6BA23 | SHA256:A4DD883257A7ACE84F96BCC6CD59E22D843D0DB080606DEFAE32923FC712C75A | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\winsound.pyd | executable | |
MD5:1C856FABFF6967DD21ADE8338E15D637 | SHA256:63ED931F692B63A8D6D7948BD8EF3B6C678B57C0C0574BF649F783C602B4E7E4 | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\_asyncio.pyd | executable | |
MD5:79F71C92C850B2D0F5E39128A59054F1 | SHA256:0237739399DB629FDD94DE209F19AC3C8CD74D48BEBE40AD8EA6AC7556A51980 | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\LICENSE.txt | text | |
MD5:EBCF45A479F291A0D965EA60B5F1C30B | SHA256:616FA565945ECA2F0E0A5440B3973FED7D5291622B90849212077FE68E27DCB0 | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\select.pyd | executable | |
MD5:C97A587E19227D03A85E90A04D7937F6 | SHA256:C4AA9A106381835CFB5F9BADFB9D77DF74338BC66E69183757A5A3774CCDACCF | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\pyexpat.pyd | executable | |
MD5:9C21A5540FC572F75901820CF97245EC | SHA256:2FF8CD82E7CC255E219E7734498D2DEA0C65A5AB29DC8581240D40EB81246045 | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\vcruntime140_1.dll | executable | |
MD5:7E668AB8A78BD0118B94978D154C85BC | SHA256:E4B533A94E02C574780E4B333FCF0889F65ED00D39E32C0FBBDA2116F185873F | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\python3.dll | executable | |
MD5:B711598FC3ED0FE4CF2C7F3E0877979E | SHA256:520169AA6CF49D7EE724D1178DE1BE0E809E4BDCF671E06F3D422A0DD5FD294A | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\python.exe | executable | |
MD5:B6EF5717317F6300D663ED9559EE9967 | SHA256:4FB049EEDDD221E5470CD33177299DD13F85EBA25BEEF7ACED7A0890AD85181F | |||
| 3300 | 5307e6e80026ce038ec5d185c79aa840.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\pythonw.exe | executable | |
MD5:9D0F19A3FDF077FC90CB1055018669FD | SHA256:695EC4080F596F485E4E36DE383A32F18042BC13620CF93BA5708EC354B6CA0D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
26
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1812 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1812 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3300 | 5307e6e80026ce038ec5d185c79aa840.exe | 151.101.0.223:443 | www.python.org | FASTLY | US | whitelisted |
3300 | 5307e6e80026ce038ec5d185c79aa840.exe | 162.159.129.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.python.org |
| whitelisted |
cdn.discordapp.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
3300 | 5307e6e80026ce038ec5d185c79aa840.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |