| File name: | 05477cb5a3eccd620474e839fbae597bdda3d4fd5db3646fd83242f2d6f5f43emagis-video.apk |
| Full analysis: | https://app.any.run/tasks/feeafe21-4e07-4cae-83cb-d81e483d07e2 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 03:30:15 |
| OS: | Android 14 |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=deflate |
| MD5: | 760F7CEC2615F31F33A9ACB8FABFED30 |
| SHA1: | 0D6D04F46EA8E96B74E3B16DD29A7E46724FE082 |
| SHA256: | 05477CB5A3ECCD620474E839FBAE597BDDA3D4FD5DB3646FD83242F2D6F5F43E |
| SSDEEP: | 196608:xEHETdIrZdQQ0rTjl7WxTyM2qDfn+ZDI9TZx2R1MkN4TfZWI0Tr/dHhUaKBawvuv:xEH4arZdPQOT/2IaD+zKMkOoITa+ba |
MALICIOUS
Executes system commands or scripts
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
SUSPICIOUS
Retrieves a list of running application processes
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Retrieves installed applications on device
- app_process64 (PID: 2265)
Accesses system-level resources
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Detects Xposed framework for modifications
- app_process64 (PID: 2265)
Uses encryption API functions
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Accesses memory information
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Detects Cydia Substrate modification platform
- app_process64 (PID: 2265)
Reads device MAC address fingerprint
- app_process64 (PID: 2265)
Establishing a connection
- app_process64 (PID: 2265)
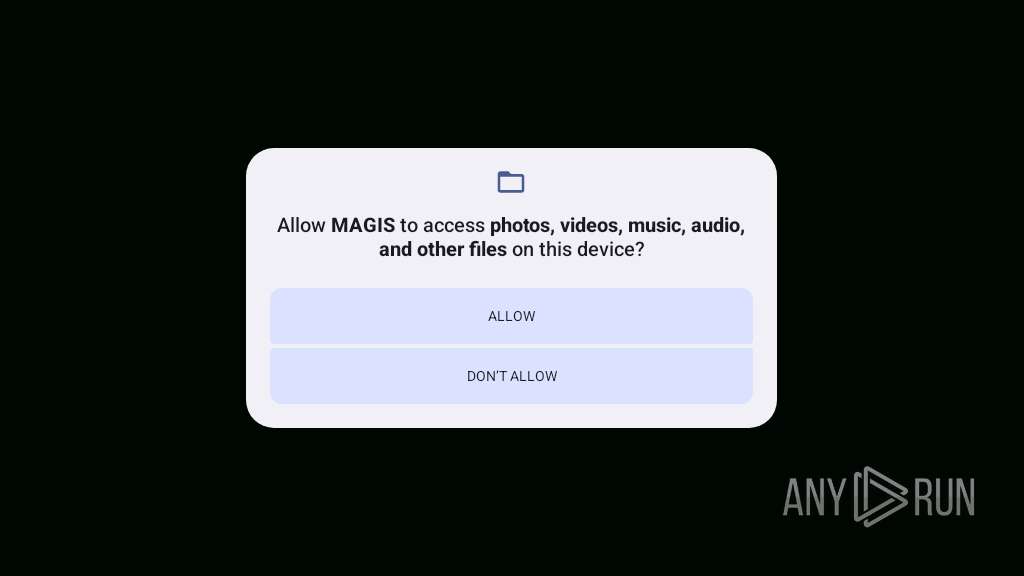
Accesses external device storage files
- app_process64 (PID: 2265)
Returns the name of the current network operator
- app_process64 (PID: 2265)
Launches a new activity
- app_process64 (PID: 2265)
INFO
Loads a native library into the application
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Returns elapsed time since boot
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Verifies whether the device is connected to the internet
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Stores data using SQLite database
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Listens for connection changes
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Dynamically registers broadcast event listeners
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Gets file name without full path
- app_process64 (PID: 2265)
Retrieves the value of a secure system setting
- app_process64 (PID: 2265)
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2265)
- app_process64 (PID: 2564)
Detects device power status
- app_process64 (PID: 2265)
Handles throwable exceptions in the app
- app_process64 (PID: 2265)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jar | | | Java Archive (78.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (21.6) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x181a1675 |
| ZipCompressedSize: | 56 |
| ZipUncompressedSize: | 63 |
| ZipFileName: | META-INF/AdvertLib_release.kotlin_module |
Total processes
143
Monitored processes
18
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2265 | com.android.mgstv | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2302 | getprop debug.dns.enable | /system/bin/toolbox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 15 | ||||
| 2304 | getprop debug.dns.filter | /system/bin/toolbox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 15 | ||||
| 2366 | ps | /system/bin/toybox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2419 | cat /proc/version | /system/bin/toybox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 256 | ||||
| 2451 | cat proc/cpuinfo | /system/bin/toybox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2475 | com.android.mgstv | /system/bin/app_process64 | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2479 | getprop ro.product.model | /system/bin/toolbox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2480 | getprop ro.product.brand | /system/bin/toolbox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2481 | getprop ro.system.build.id | /system/bin/toolbox | — | app_process64 |
User: u0_a109 Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
168
Text files
100
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2265 | app_process64 | /data/user/0/com.android.mgstv/files/PersistedInstallation2256677038265006879tmp | binary | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/shared_prefs/com.google.android.gms.appid.xml | xml | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/files/PersistedInstallation.W0RFRkFVTFRd+MTo2NDg1Njg3Njg1Mzg6YW5kcm9pZDoxMDJjNjljMWY4ZDU5MGExZjcyOWEz.json | binary | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/shared_prefs/com.google.android.gms.measurement.prefs.xml | xml | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/shared_prefs/FirebaseAppHeartBeat.xml | xml | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/shared_prefs/umeng_common_config.xml | — | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/files/.com.google.firebase.crashlytics-ndk/6856276503AA000108D9B058D5ECB618/session.json | binary | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/files/.com.google.firebase.crashlytics-ndk/6856276503AA000108D9B058D5ECB618/app.json | binary | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/shared_prefs/com.google.firebase.crashlytics.xml | xml | |
MD5:— | SHA256:— | |||
| 2265 | app_process64 | /data/user/0/com.android.mgstv/files/.com.google.firebase.crashlytics-ndk/6856276503AA000108D9B058D5ECB618/os.json | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
58
DNS requests
345
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.181.227:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
— | — | GET | 204 | 142.250.186.132:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
— | — | GET | 204 | 142.250.186.132:443 | https://www.google.com/generate_204 | unknown | — | — | unknown |
— | — | GET | 204 | 142.250.181.227:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.181.234:443 | https://firebaseinstallations.googleapis.com/v1/projects/mgs-free-e6046/installations | unknown | binary | 628 b | whitelisted |
— | — | GET | 200 | 142.250.185.227:443 | https://firebase-settings.crashlytics.com/spi/v2/platforms/android/gmp/1:648568768538:android:102c69c1f8d590a1f729a3/settings?instance=ea5b31c683dbf2fb67fe6cee33256e38b54f5eb2&build_version=42902&display_version=4.29.2&source=1 | unknown | binary | 743 b | whitelisted |
— | — | POST | 200 | 142.250.27.81:443 | https://staging-remoteprovisioning.sandbox.googleapis.com/v1:fetchEekChain | unknown | binary | 699 b | whitelisted |
— | — | POST | 200 | 104.21.32.1:443 | https://mds.yjda1lddfs.com/api/v2/dcs/getAddr | unknown | binary | 385 b | unknown |
— | — | POST | 200 | 104.21.66.254:443 | https://zpgxqa.gxudenhvk.com/api/portalCore/v3/snToken | unknown | binary | 68 b | unknown |
2265 | app_process64 | GET | 200 | 188.114.96.3:80 | http://pkrub.nhy74bgv.com/notice/api/get_notice?pkg=com.android.mgstv&v=42902&sn=&userId=&language=en | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
446 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 142.250.181.227:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.132:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.132:80 | www.google.com | GOOGLE | US | whitelisted |
— | — | 216.239.35.4:123 | time.android.com | — | — | whitelisted |
1748 | app_process64 | 142.250.27.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
573 | app_process64 | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
2265 | app_process64 | 172.217.16.202:443 | firebaseinstallations.googleapis.com | GOOGLE | US | whitelisted |
2265 | app_process64 | 142.250.185.227:443 | firebase-settings.crashlytics.com | GOOGLE | US | whitelisted |
2265 | app_process64 | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivitycheck.gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
google.com |
| whitelisted |
time.android.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
firebaseinstallations.googleapis.com |
| whitelisted |
firebase-settings.crashlytics.com |
| whitelisted |
time.google.com |
| whitelisted |
time.cloudflare.com |
| whitelisted |
time.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
— | — | Misc activity | ET INFO Android Device Connectivity Check |
— | — | Generic Protocol Command Decode | SURICATA HTTP gzip decompression failed |