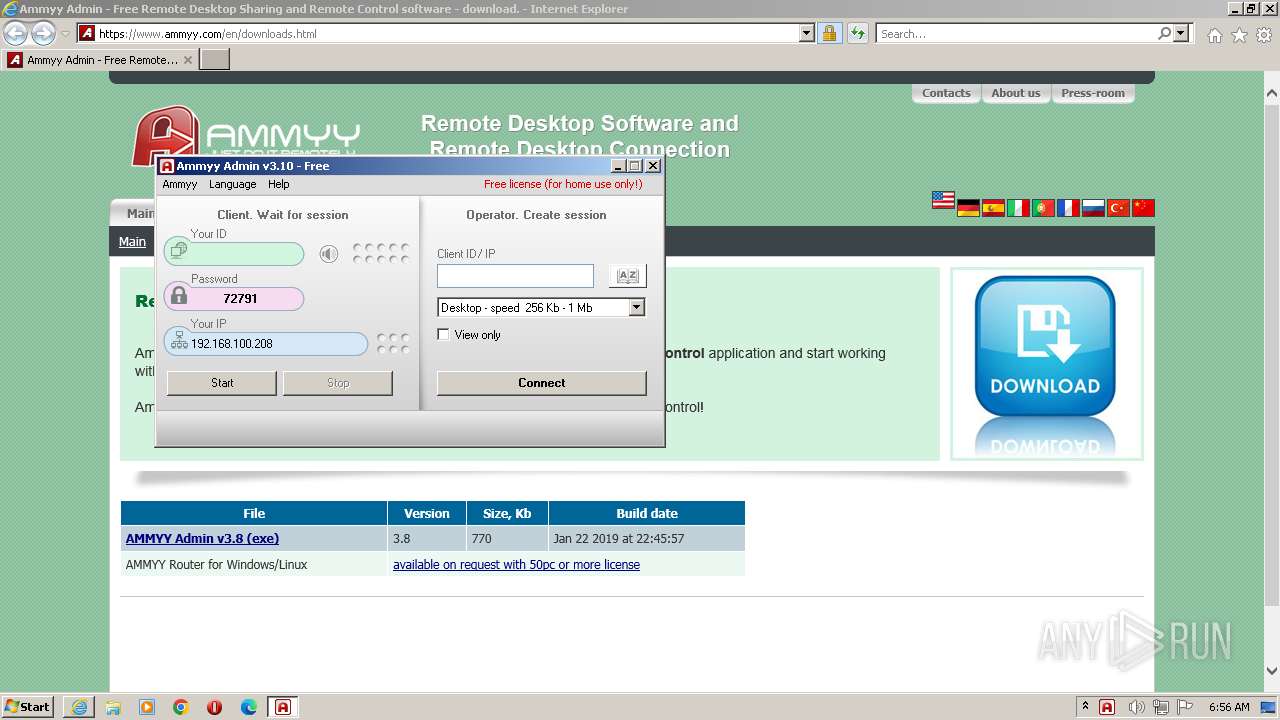
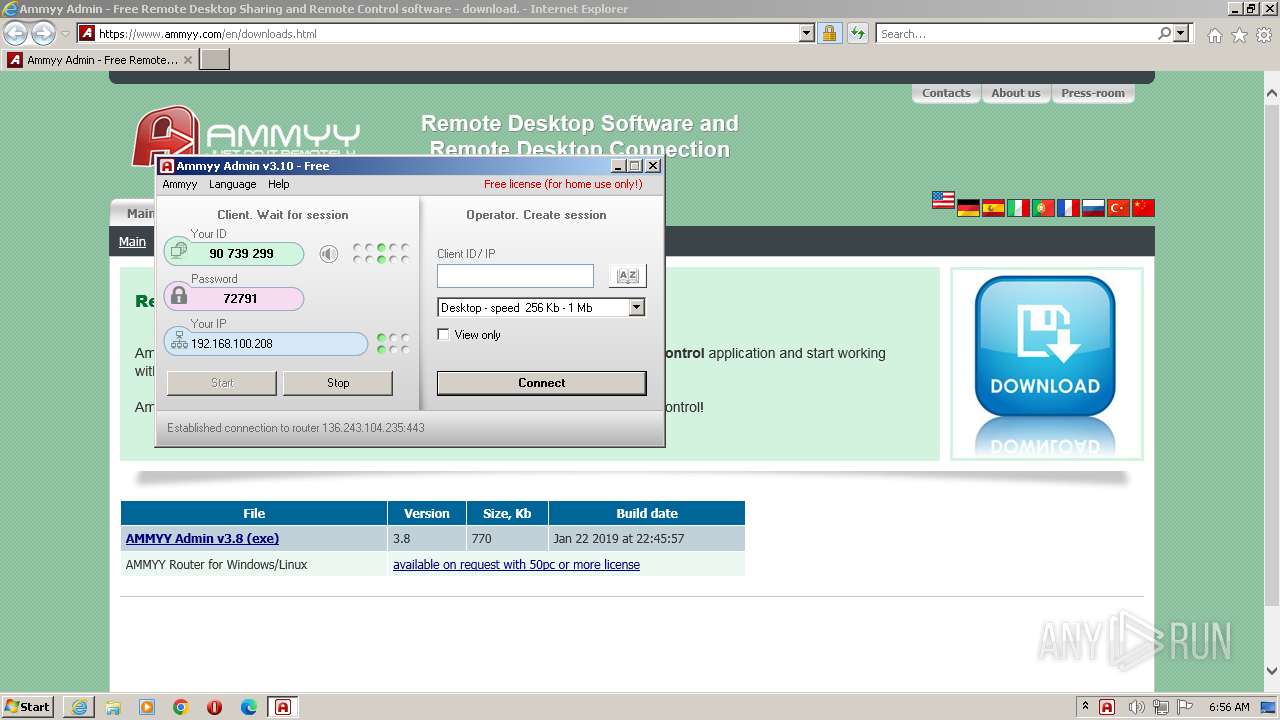
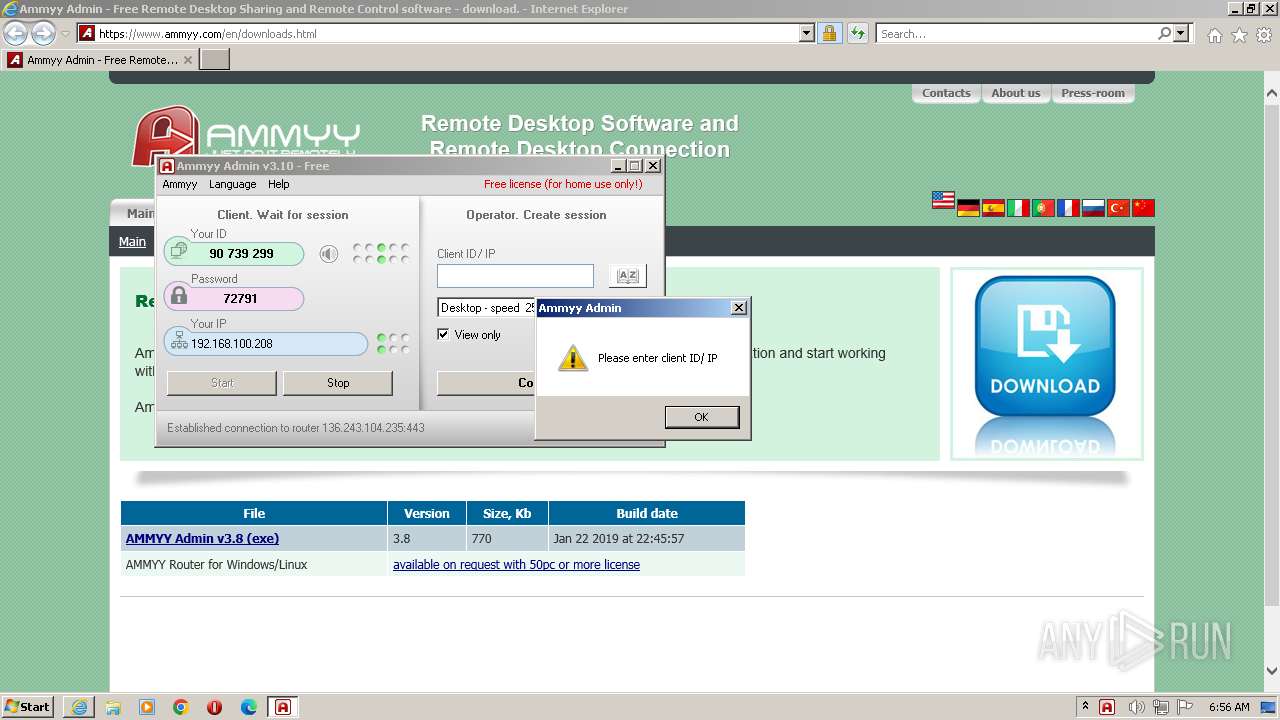
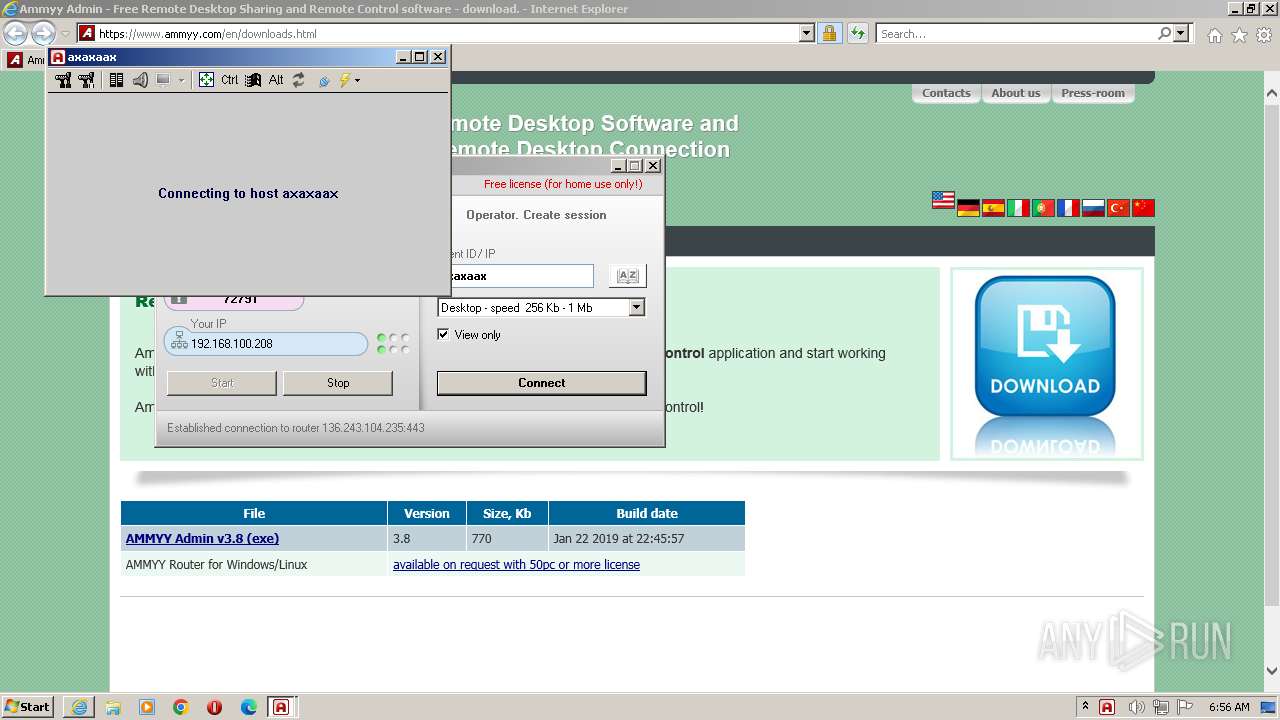
| URL: | https://www.ammyy.com/AA_v3.php?v=280566151 |
| Full analysis: | https://app.any.run/tasks/fbd54d35-3b28-429b-9d26-155d97df0f59 |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2023, 05:56:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FBB414B82D628AD9D90BF085F1AD4D26 |
| SHA1: | 3D7817989724CE8C07A0E78C205E86641B8DC55C |
| SHA256: | 0536EE8AC10175229BA70FFF33F5CD88D42DEB5B4C0C1AA6190374AC42584989 |
| SSDEEP: | 3:N8DSLuGK3ITWTtQU:2OLuGzWj |
MALICIOUS
Application was dropped or rewritten from another process
- AA_v3.exe (PID: 3024)
- AA_v3.exe (PID: 2468)
- AA_v3.exe (PID: 3944)
- AA_v3.exe (PID: 2080)
Deletes the SafeBoot registry key
- AA_v3.exe (PID: 2468)
Creates a writable file the system directory
- AA_v3.exe (PID: 2080)
Loads dropped or rewritten executable
- rundll32.exe (PID: 1032)
AMMYY was detected
- AA_v3.exe (PID: 2080)
SUSPICIOUS
Application launched itself
- AA_v3.exe (PID: 3024)
- AA_v3.exe (PID: 3944)
Reads the Internet Settings
- AA_v3.exe (PID: 3024)
Executes as Windows Service
- AA_v3.exe (PID: 3944)
Checks for external IP
- AA_v3.exe (PID: 2080)
Checks Windows Trust Settings
- AA_v3.exe (PID: 2080)
Adds/modifies Windows certificates
- AA_v3.exe (PID: 3944)
Executable content was dropped or overwritten
- AA_v3.exe (PID: 2080)
Uses RUNDLL32.EXE to load library
- AA_v3.exe (PID: 2080)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 2372)
- iexplore.exe (PID: 3484)
Application launched itself
- iexplore.exe (PID: 3484)
Checks supported languages
- AA_v3.exe (PID: 3024)
- AA_v3.exe (PID: 2468)
- AA_v3.exe (PID: 3944)
- AA_v3.exe (PID: 2080)
Reads the computer name
- AA_v3.exe (PID: 3024)
- AA_v3.exe (PID: 2468)
- AA_v3.exe (PID: 3944)
- AA_v3.exe (PID: 2080)
Checks proxy server information
- AA_v3.exe (PID: 3024)
The process uses the downloaded file
- iexplore.exe (PID: 3484)
- AA_v3.exe (PID: 3024)
Creates files in the program directory
- AA_v3.exe (PID: 3024)
- AA_v3.exe (PID: 2080)
Process checks computer location settings
- AA_v3.exe (PID: 2080)
Reads the machine GUID from the registry
- AA_v3.exe (PID: 2080)
Creates files or folders in the user directory
- AA_v3.exe (PID: 2080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1032 | rundll32.exe "C:\ProgramData\AMMYY\aa_nts.dll",run | C:\Windows\System32\rundll32.exe | — | AA_v3.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
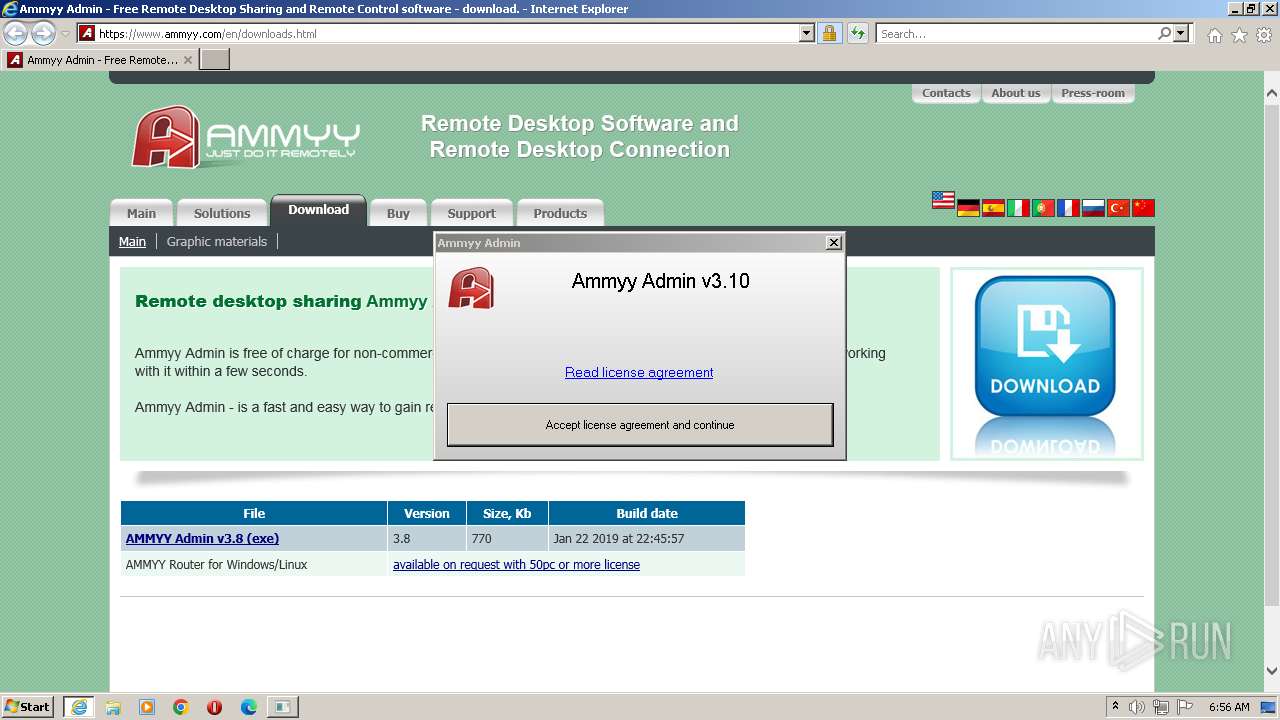
| 2080 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AA_v3.exe" -elevated | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AA_v3.exe | AA_v3.exe | ||||||||||||
User: SYSTEM Company: Ammyy LLC Integrity Level: SYSTEM Description: Ammyy Admin Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3484 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AA_v3.exe" -elevated | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AA_v3.exe | AA_v3.exe | ||||||||||||
User: admin Company: Ammyy LLC Integrity Level: HIGH Description: Ammyy Admin Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 3024 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AA_v3.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AA_v3.exe | — | iexplore.exe | |||||||||||
User: admin Company: Ammyy LLC Integrity Level: MEDIUM Description: Ammyy Admin Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 3484 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.ammyy.com/AA_v3.php?v=280566151" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3944 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AA_v3.exe" -service -lunch | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\AA_v3.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Ammyy LLC Integrity Level: SYSTEM Description: Ammyy Admin Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
Total events
24 006
Read events
23 896
Write events
105
Delete events
5
Modification events
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3484) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
29
Text files
41
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\downloads[1].htm | html | |
MD5:7E53FBDA60B21F46148B45078065FADF | SHA256:A9E3E2282763C2368C25C9EA8E39B21CE29697A3F019D60953971EE800E90034 | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8005.tmp | cat | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:24BE8A92460B5B7A555B1DA559296958 | SHA256:77A3CFE6B7EB676AF438D5DE88C7EFCB6ABCC494E0B65DA90201969E6D79B2A3 | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar8036.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8004.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab8035.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E311BDA85CA50E60B5894E5C8A6D118C | SHA256:742B26771C3627266FA2812C818B173C3A73C9FE455BD597630C5A0C0B7917BB | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5037AC1E573F140500110A0B67548B5E | der | |
MD5:6F8FCCCCEFFAB1CD6CE74AC119DA52DE | SHA256:A1E96A3F1CEDDBB0BD6CE4EB5C3666AD2F59F8E51AC641D4AC288B2DB857D036 | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5037AC1E573F140500110A0B67548B5E | binary | |
MD5:BB2FAA43EFC279EAF434769D7990C5B6 | SHA256:CB24A23091B81E8F8C697D74CD133282AF963B66C872EFDE620C79694BC9BD9B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
55
DNS requests
18
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2372 | iexplore.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a1812858e79438c5 | unknown | compressed | 4.66 Kb | unknown |
2372 | iexplore.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?80bf958c58d95605 | unknown | compressed | 61.6 Kb | unknown |
2372 | iexplore.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d3a29e5f0beeb90c | unknown | compressed | 4.66 Kb | unknown |
2372 | iexplore.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?33d3eed36c4585a3 | unknown | compressed | 61.6 Kb | unknown |
2372 | iexplore.exe | GET | 200 | 23.56.202.135:80 | http://x1.c.lencr.org/ | unknown | der | 717 b | unknown |
2372 | iexplore.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ae0c2afaac3e78ff | unknown | compressed | 61.6 Kb | unknown |
2372 | iexplore.exe | GET | 200 | 184.24.77.48:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQ7v4J%2FgaqUqpyZN7zZz%2ByuYw%3D%3D | unknown | der | 503 b | unknown |
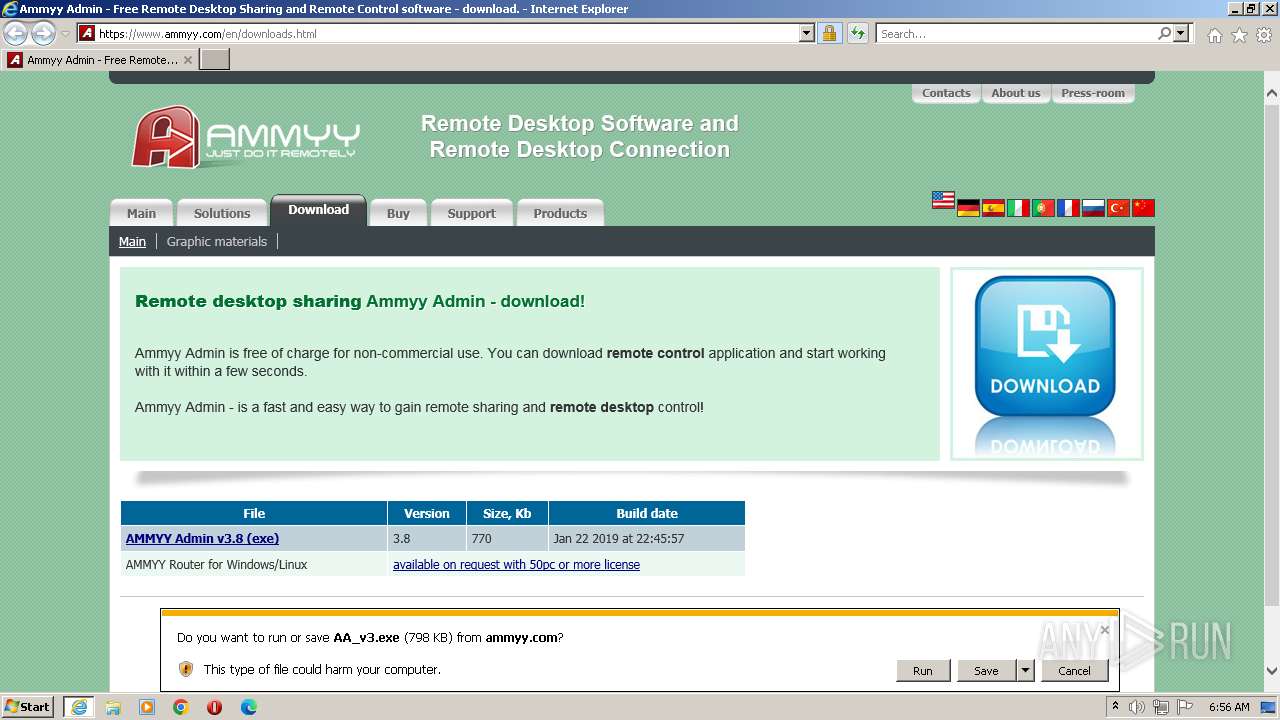
2372 | iexplore.exe | GET | 301 | 136.243.18.118:80 | http://www.ammyy.com/en/downloads.html | unknown | html | 325 b | unknown |
3484 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | unknown | der | 1.47 Kb | unknown |
2080 | AA_v3.exe | POST | 200 | 188.42.129.148:80 | http://rl.ammyy.com/ | unknown | text | 247 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2372 | iexplore.exe | 136.243.18.118:443 | www.ammyy.com | Hetzner Online GmbH | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2372 | iexplore.exe | 95.140.236.128:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2372 | iexplore.exe | 23.56.202.135:80 | x1.c.lencr.org | AKAMAI-AS | GB | unknown |
2372 | iexplore.exe | 184.24.77.48:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2372 | iexplore.exe | 136.243.18.118:80 | www.ammyy.com | Hetzner Online GmbH | DE | unknown |
2372 | iexplore.exe | 142.250.186.72:443 | ssl.google-analytics.com | GOOGLE | US | unknown |
2372 | iexplore.exe | 142.250.184.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3484 | iexplore.exe | 136.243.18.118:443 | www.ammyy.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.ammyy.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
ssl.google-analytics.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
rl.ammyy.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2080 | AA_v3.exe | Potential Corporate Privacy Violation | ET POLICY IP Check (rl. ammyy. com) |
1 ETPRO signatures available at the full report