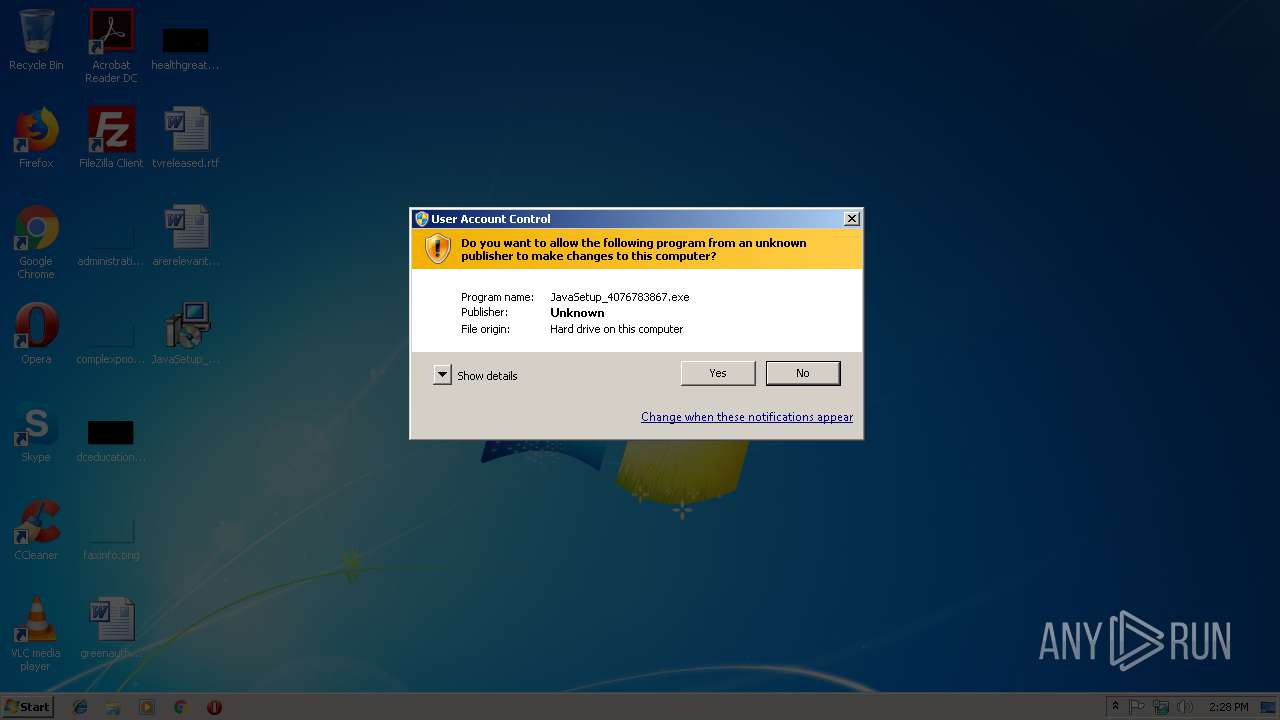
| File name: | JavaSetup_4076783867.exe |
| Full analysis: | https://app.any.run/tasks/2dc82564-6525-4061-b76a-92b6531976c7 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | January 11, 2019, 14:27:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6D5B63D532751510E0131154B5B4A4AF |
| SHA1: | D67F3B753C8AB50B137DC6100639A2401135A893 |
| SHA256: | 052F28BC9CD5590975E2E569E4DA8BAB0F09AAA41B4A7CDEF0C1C89F8B347511 |
| SSDEEP: | 49152:lIRCHh/o4LgytcHTFE9Y3JlQKjoFv4Qq2WxH/1/5gOShgsqq:6REhjU7TFE0JlQQQqjFd5xsqq |
MALICIOUS
INSTALLCORE was detected
- JavaSetup_4076783867.exe (PID: 3784)
Connects to CnC server
- JavaSetup_4076783867.exe (PID: 3784)
Application was dropped or rewritten from another process
- bspatch.exe (PID: 3352)
SUSPICIOUS
Executable content was dropped or overwritten
- JavaSetup_4076783867.exe (PID: 3712)
- installer.exe (PID: 2672)
- msiexec.exe (PID: 3800)
Reads internet explorer settings
- JavaSetup_4076783867.exe (PID: 3784)
- JavaSetup.exe (PID: 280)
Application launched itself
- JavaSetup_4076783867.exe (PID: 3784)
Starts Internet Explorer
- JavaSetup_4076783867.exe (PID: 3784)
Reads Environment values
- JavaSetup_4076783867.exe (PID: 3784)
Creates files in the program directory
- installer.exe (PID: 2672)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3628)
Application was dropped or rewritten from another process
- JavaSetup_4076783867.tmp (PID: 2848)
Reads internet explorer settings
- iexplore.exe (PID: 2068)
Creates a software uninstall entry
- msiexec.exe (PID: 3800)
Application launched itself
- iexplore.exe (PID: 3628)
- msiexec.exe (PID: 3800)
Creates files in the program directory
- msiexec.exe (PID: 3800)
Creates files in the user directory
- iexplore.exe (PID: 2068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.6.2.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Popecepo Setup |
| FileVersion: | 2.6.2.0 |
| LegalCopyright: | Con |
| ProductName: | Popecepo |
| ProductVersion: | 4.5.9 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | - |
| FileDescription: | Popecepo Setup |
| FileVersion: | 2.6.2.0 |
| LegalCopyright: | Con |
| ProductName: | Popecepo |
| ProductVersion: | 4.5.9 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x00009D30 | 0x00009E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.60951 |
DATA | 0x0000B000 | 0x00000250 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.75182 |
BSS | 0x0000C000 | 0x00000E8C | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0000D000 | 0x00000950 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.43073 |
.tls | 0x0000E000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0000F000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.204488 |
.reloc | 0x00010000 | 0x000008C4 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0 |
.rsrc | 0x00011000 | 0x00002C00 | 0x00002C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 4.54261 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.11919 | 1512 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 3.47151 | 1384 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 3.91708 | 744 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.91366 | 2216 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4089 | 3.21823 | 754 | UNKNOWN | UNKNOWN | RT_STRING |
4090 | 3.31515 | 780 | UNKNOWN | UNKNOWN | RT_STRING |
4091 | 3.25024 | 718 | UNKNOWN | UNKNOWN | RT_STRING |
4093 | 2.86149 | 104 | UNKNOWN | UNKNOWN | RT_STRING |
4094 | 3.20731 | 180 | UNKNOWN | UNKNOWN | RT_STRING |
4095 | 3.04592 | 174 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
52
Monitored processes
12
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Users\admin\AppData\Local\Temp\jds1764187.tmp\JavaSetup.exe" | C:\Users\admin\AppData\Local\Temp\jds1764187.tmp\JavaSetup.exe | JavaSetup.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.1110.14 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3628 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\Desktop\JavaSetup_4076783867.exe" /SPAWNWND=$20116 /NOTIFYWND=$20110 /_ShowProgress /PrTxt:TG9hZGluZy4uLg== /mnl | C:\Users\admin\Desktop\JavaSetup_4076783867.exe | — | JavaSetup_4076783867.exe | |||||||||||
User: admin Company: Integrity Level: HIGH Description: Popecepo Setup Exit code: 259 Version: 2.6.2.0 Modules
| |||||||||||||||
| 2640 | C:\Windows\system32\MsiExec.exe -Embedding DD99DBDFA7768512DC54CE5EDFD97DAD | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Java\jre1.8.0_111\installer.exe" /s INSTALLDIR="C:\Program Files\Java\jre1.8.0_111\\" SPONSORS=0 REPAIRMODE=0 ProductCode={26A24AE4-039D-4CA4-87B4-2F32180111F0} | C:\Program Files\Java\jre1.8.0_111\installer.exe | msiexec.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.1110.14 Modules
| |||||||||||||||
| 2692 | "C:\Users\admin\Downloads\JavaSetup.exe" | C:\Users\admin\Downloads\JavaSetup.exe | — | JavaSetup_4076783867.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.1110.14 Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\AppData\Local\Temp\is-L645V.tmp\JavaSetup_4076783867.tmp" /SL5="$20110,2189564,56832,C:\Users\admin\Desktop\JavaSetup_4076783867.exe" | C:\Users\admin\AppData\Local\Temp\is-L645V.tmp\JavaSetup_4076783867.tmp | — | JavaSetup_4076783867.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3352 | "bspatch.exe" baseimagefam8 newimage diff | C:\ProgramData\Oracle\Java\installcache\1790578.tmp\bspatch.exe | — | installer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3628 | "C:\Program Files\Internet Explorer\iexplore.exe" http://ic-dc.clearcontentbinaries.com/pr/519d1546-8bc5-11e6-b7fc-0695da005429/typ_2.html | C:\Program Files\Internet Explorer\iexplore.exe | JavaSetup_4076783867.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3712 | "C:\Users\admin\Desktop\JavaSetup_4076783867.exe" | C:\Users\admin\Desktop\JavaSetup_4076783867.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Popecepo Setup Exit code: 0 Version: 2.6.2.0 Modules
| |||||||||||||||
Total events
1 264
Read events
1 042
Write events
219
Delete events
3
Modification events
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\JavaSetup_4076783867_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\JavaSetup_4076783867_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\JavaSetup_4076783867_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\JavaSetup_4076783867_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\JavaSetup_4076783867_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\JavaSetup_4076783867_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3784) JavaSetup_4076783867.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\JavaSetup_4076783867_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
3
Suspicious files
9
Text files
240
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\0019ACA1.log | — | |
MD5:— | SHA256:— | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\csshover3.htc | html | |
MD5:52FA0DA50BF4B27EE625C80D36C67941 | SHA256:E37E99DDFC73AC7BA774E23736B2EF429D9A0CB8C906453C75B14C029BDD5493 | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\form.bmp.Mask | binary | |
MD5:D2FC989F9C2043CD32332EC0FAD69C70 | SHA256:27DD029405CBFB0C3BF8BAC517BE5DB9AA83E981B1DC2BD5C5D6C549FA514101 | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\css\main.css | text | |
MD5:CD50C111BCB785F12306BB72C5E926E2 | SHA256:86DD1310F16A1DAF0DCF0A05FE0C7937432A889B43D440BC1548C49314F9F05F | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\css\ie6_main.css | text | |
MD5:AD234E6A62580F62019C78B2A718DE00 | SHA256:C4F2684F16C8E4553CC29C604A2F505399039638A34E652A7A1ACDEB157A0861 | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\css\_functions.scss | text | |
MD5:8F7259DE64F6DDF352BF461F44D34A81 | SHA256:80EDC9D67172BC830D68D33F4547735FB072CADF3EF25AAB37A10B50DB87A069 | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\css\helpers\_border-radius.scss | text | |
MD5:6BDF3FD89410E39D33F8137E04AD4A16 | SHA256:2C6B98CB19C3E3A0E37472767C53DF213243AE92BC80EF9A7F5BAA17F7B6FA31 | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\css\helpers\_colors.scss | text | |
MD5:2DA278FBB61E370E0CC9F548E8154E1C | SHA256:857A73FC1DA7CF54525048AA60EC9E2F07328EE1D718A66E3B17186170BB5B5B | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\css\helpers\_display.scss | text | |
MD5:7FC18252C6212F1EBB349B5F7F429217 | SHA256:1B1F774D3B163C1BA9C86CAD87D4B594FBA588A364132121F8A234F149816429 | |||
| 3784 | JavaSetup_4076783867.exe | C:\Users\admin\AppData\Local\Temp\inH168259362006\css\main.scss | text | |
MD5:A85DEB7E401725C73E02464106F6501F | SHA256:3B5A044EF2BFF26A7D09AF66A3B8E102CF669BEDEEE65C127B46C4DC21EC344D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
19
DNS requests
9
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3784 | JavaSetup_4076783867.exe | HEAD | 200 | 199.201.110.78:80 | http://cdnus.laboratoryconecpttoday.com/app/softjug/javaSetup.exe | US | — | — | malicious |
3784 | JavaSetup_4076783867.exe | GET | — | 199.201.110.78:80 | http://cdnus.laboratoryconecpttoday.com/app/softjug/javaSetup.exe | US | — | — | malicious |
2068 | iexplore.exe | GET | — | 52.222.146.105:80 | http://ic-dc.clearcontentbinaries.com/pr/public/js/jquery.min.js | US | — | — | whitelisted |
3784 | JavaSetup_4076783867.exe | POST | 200 | 52.214.73.247:80 | http://ww4.fawari-viwad.com/ | IE | — | — | malicious |
3784 | JavaSetup_4076783867.exe | GET | — | 199.201.110.78:80 | http://cdnus.laboratoryconecpttoday.com/app/softjug/javaSetup.exe | US | — | — | malicious |
3784 | JavaSetup_4076783867.exe | GET | — | 199.201.110.78:80 | http://cdnus.laboratoryconecpttoday.com/app/softjug/javaSetup.exe | US | — | — | malicious |
3784 | JavaSetup_4076783867.exe | GET | 200 | 85.159.237.103:80 | http://ww42.fawari-viwad.com/app/softjug/java_32.png | NL | image | 1.83 Kb | malicious |
3784 | JavaSetup_4076783867.exe | POST | 200 | 52.214.73.247:80 | http://ww4.fawari-viwad.com/ | IE | — | — | malicious |
3784 | JavaSetup_4076783867.exe | GET | — | 199.201.110.78:80 | http://cdnus.laboratoryconecpttoday.com/app/softjug/javaSetup.exe | US | — | — | malicious |
3784 | JavaSetup_4076783867.exe | POST | — | 52.209.41.250:80 | http://support.fawari-viwad.com/softjug/ | IE | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3784 | JavaSetup_4076783867.exe | 52.214.73.247:80 | ww4.fawari-viwad.com | Amazon.com, Inc. | IE | malicious |
3784 | JavaSetup_4076783867.exe | 34.251.155.7:80 | web.fawari-viwad.com | Amazon.com, Inc. | IE | whitelisted |
3784 | JavaSetup_4076783867.exe | 85.159.237.103:80 | ww42.fawari-viwad.com | NForce Entertainment B.V. | NL | malicious |
3628 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
280 | JavaSetup.exe | 184.31.87.231:443 | javadl-esd-secure.oracle.com | Akamai International B.V. | NL | whitelisted |
3784 | JavaSetup_4076783867.exe | 52.209.41.250:80 | support.fawari-viwad.com | Amazon.com, Inc. | IE | malicious |
2068 | iexplore.exe | 52.222.146.105:80 | ic-dc.clearcontentbinaries.com | Amazon.com, Inc. | US | unknown |
3784 | JavaSetup_4076783867.exe | 199.201.110.78:80 | cdnus.laboratoryconecpttoday.com | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ww4.fawari-viwad.com |
| malicious |
web.fawari-viwad.com |
| malicious |
ww42.fawari-viwad.com |
| malicious |
support.fawari-viwad.com |
| malicious |
cdnus.laboratoryconecpttoday.com |
| malicious |
cdn.fawari-viwad.com |
| malicious |
ic-dc.clearcontentbinaries.com |
| whitelisted |
www.bing.com |
| whitelisted |
javadl-esd-secure.oracle.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3784 | JavaSetup_4076783867.exe | Misc activity | ADWARE [PTsecurity] PUP.Optional.InstallCore Artifact M2 |
3784 | JavaSetup_4076783867.exe | Misc activity | ADWARE [PTsecurity] PUP.Optional.InstallCore Artifact M1 |
3784 | JavaSetup_4076783867.exe | Misc activity | ADWARE [PTsecurity] PUP.Optional.InstallCore Artifact M3 |
3784 | JavaSetup_4076783867.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Possible threat - .exe downloading with HEAD option |
3784 | JavaSetup_4076783867.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3784 | JavaSetup_4076783867.exe | Misc activity | ADWARE [PTsecurity] PUP.Optional.InstallCore Artifact M4 |
1 ETPRO signatures available at the full report