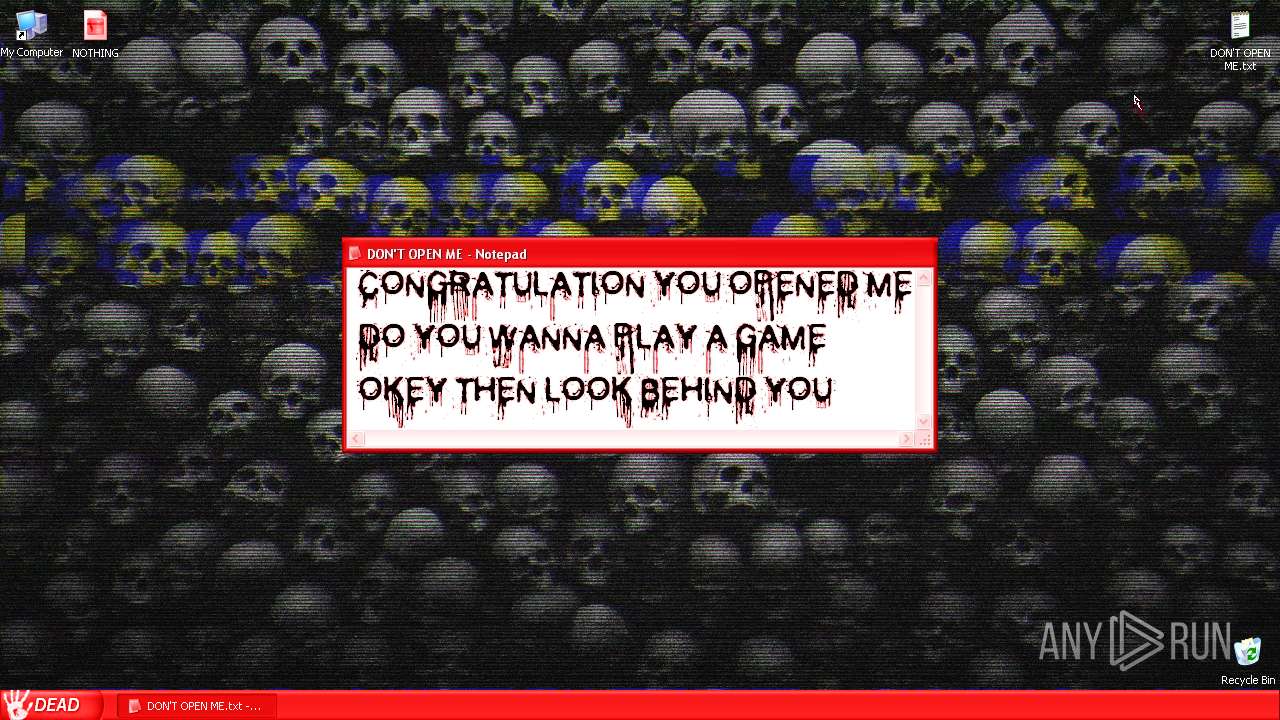
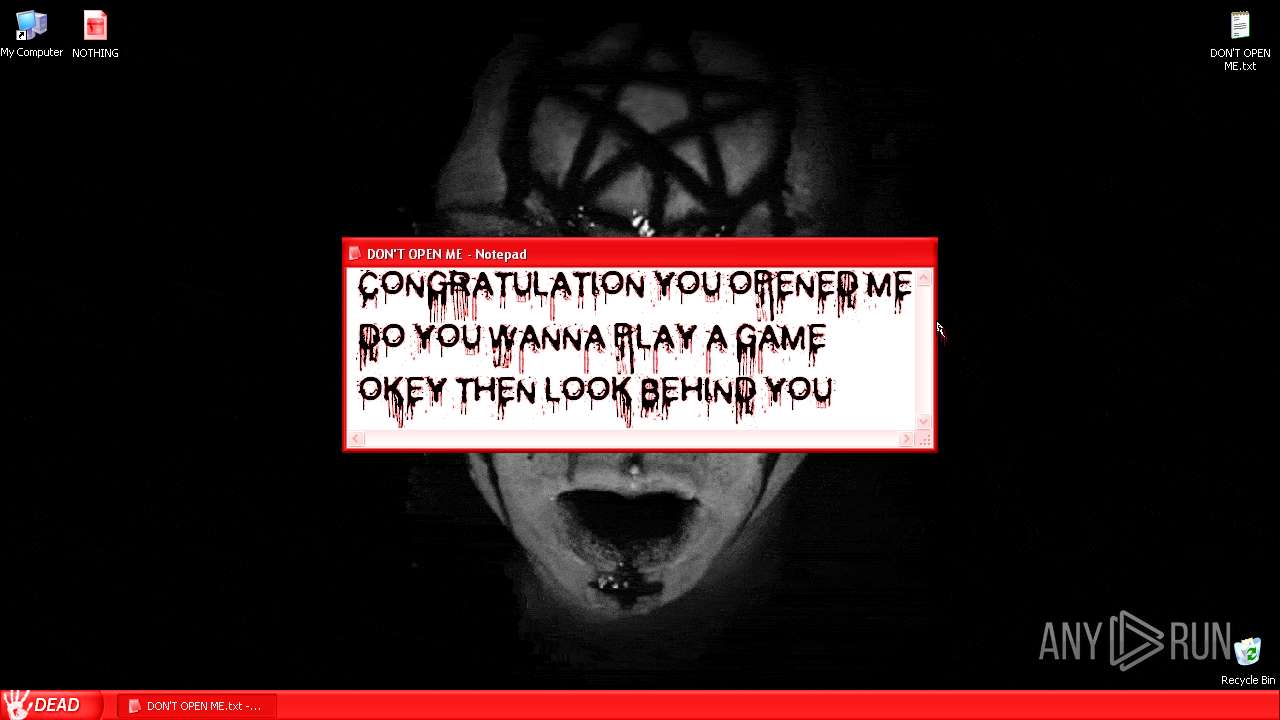
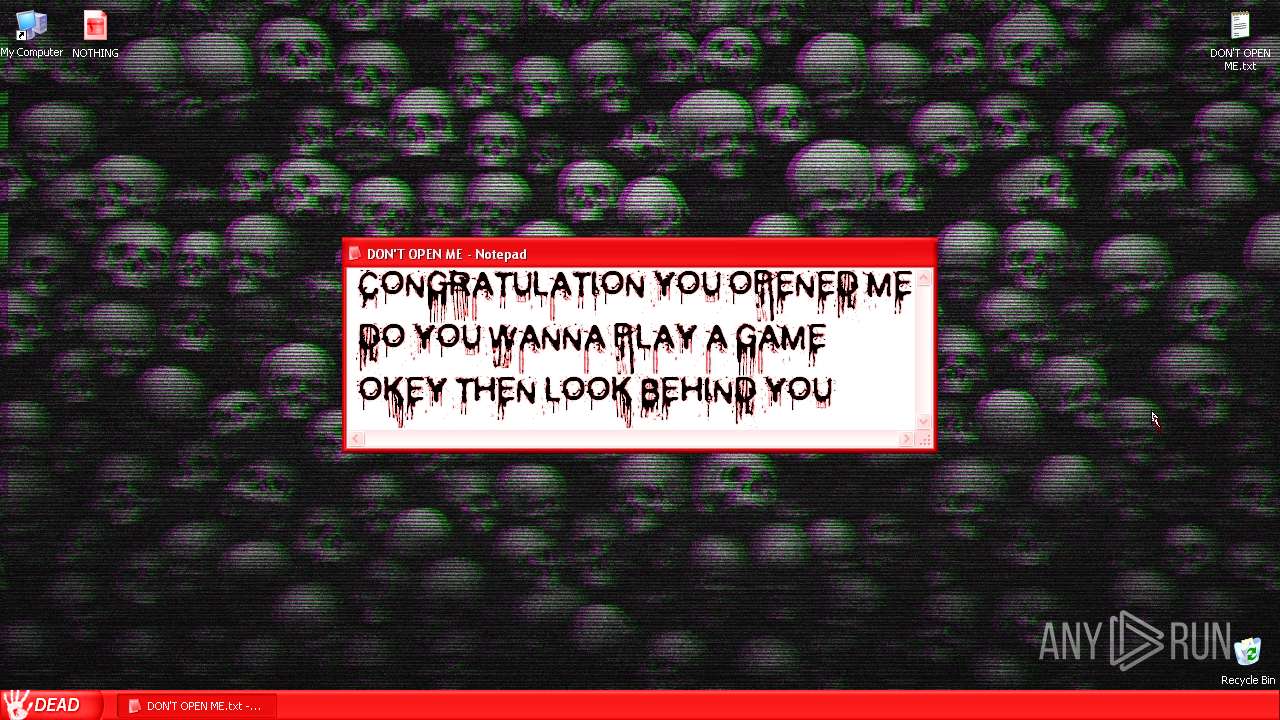
| URL: | https://archive.org/download/WinXP.Horror.DestructiveCreatedByWobbyChip_201811/WinXP.Horror.Destructive%20%20%28Created%20By%20WobbyChip%29.zip |
| Full analysis: | https://app.any.run/tasks/c42a94b3-b4b1-42f1-93ec-87a476ef6213 |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2022, 06:30:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 196BF5F8E3CA13D40F08F1D7BA04DFD3 |
| SHA1: | E025FAB70E949CF6C39BF9CDC2D0EB2AE72B9283 |
| SHA256: | 05295B561BC842E1EA2EF531BB65E20904E76DA83FFDF799077713DF470048B9 |
| SSDEEP: | 3:N8MFXJ2fL9B4HrQdKQE5ZH8V8VUW+I4HrQd1micAsVy0Un:2MFXML9B4LQTE5ZcC+C4LQLm/ATfn |
MALICIOUS
Changes the login/logoff helper path in the registry
- WinXP.Horror.Destructive (Created By WobbyChip).exe (PID: 3560)
UAC/LUA settings modification
- WinXP.Horror.Destructive (Created By WobbyChip).exe (PID: 3560)
Task Manager has been disabled (taskmgr)
- WinXP.Horror.Destructive (Created By WobbyChip).exe (PID: 3560)
Disables registry editing tools (regedit)
- WinXP.Horror.Destructive (Created By WobbyChip).exe (PID: 3560)
Disables the LogOff in Start menu
- WinXP.Horror.Destructive (Created By WobbyChip).exe (PID: 3560)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2812)
Checks supported languages
- WinRAR.exe (PID: 116)
- WinXP.Horror.Destructive (Created By WobbyChip).exe (PID: 3560)
Reads the computer name
- WinRAR.exe (PID: 116)
- WinXP.Horror.Destructive (Created By WobbyChip).exe (PID: 3560)
INFO
Reads the computer name
- iexplore.exe (PID: 2812)
- iexplore.exe (PID: 696)
Changes internet zones settings
- iexplore.exe (PID: 696)
Checks supported languages
- iexplore.exe (PID: 696)
- iexplore.exe (PID: 2812)
Checks Windows Trust Settings
- iexplore.exe (PID: 2812)
- iexplore.exe (PID: 696)
Application launched itself
- iexplore.exe (PID: 696)
Reads settings of System Certificates
- iexplore.exe (PID: 696)
- iexplore.exe (PID: 2812)
Reads internet explorer settings
- iexplore.exe (PID: 2812)
Creates files in the user directory
- iexplore.exe (PID: 696)
Modifies the phishing filter of IE
- iexplore.exe (PID: 696)
Reads the date of Windows installation
- iexplore.exe (PID: 696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\WinXP.Horror.Destructive (Created By WobbyChip).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 696 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://archive.org/download/WinXP.Horror.DestructiveCreatedByWobbyChip_201811/WinXP.Horror.Destructive%20%20%28Created%20By%20WobbyChip%29.zip" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:696 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2968 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa116.13793\WinXP.Horror.Destructive (Created By WobbyChip).exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa116.13793\WinXP.Horror.Destructive (Created By WobbyChip).exe | — | WinRAR.exe | |||||||||||
User: admin Company: WobbyCorp (C) 2017 Integrity Level: MEDIUM Description: Windows XP Horror Edition Exit code: 3221226540 Version: 6.6.6.0 Modules
| |||||||||||||||
| 3560 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa116.13793\WinXP.Horror.Destructive (Created By WobbyChip).exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa116.13793\WinXP.Horror.Destructive (Created By WobbyChip).exe | WinRAR.exe | ||||||||||||
User: admin Company: WobbyCorp (C) 2017 Integrity Level: HIGH Description: Windows XP Horror Edition Exit code: 0 Version: 6.6.6.0 Modules
| |||||||||||||||
Total events
16 761
Read events
16 563
Write events
193
Delete events
5
Modification events
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30963475 | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30963475 | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
12
Text files
16
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
| 696 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{B53BF19A-E306-11EC-B490-18C4897E77EE}.dat | binary | |
MD5:— | SHA256:— | |||
| 696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 696 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF66B08819446DA598.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\WinXP.Horror.Destructive%20%20(Created%20By%20WobbyChip)[1].zip | compressed | |
MD5:— | SHA256:— | |||
| 696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:— | SHA256:— | |||
| 696 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\CL22838S.txt | text | |
MD5:— | SHA256:— | |||
| 696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2812 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
2812 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
696 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
696 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2812 | iexplore.exe | GET | 200 | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e4425510b7c8ff5f | GB | compressed | 4.70 Kb | whitelisted |
2812 | iexplore.exe | GET | 200 | 95.140.236.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?990b70dac08a19f7 | GB | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2812 | iexplore.exe | 207.241.224.2:443 | archive.org | Internet Archive | US | malicious |
2812 | iexplore.exe | 95.140.236.0:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | GB | whitelisted |
2812 | iexplore.exe | 192.124.249.23:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
696 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
696 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2812 | iexplore.exe | 207.241.230.71:443 | ia800701.us.archive.org | Internet Archive | US | unknown |
696 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
696 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | Microsoft Corporation | US | whitelisted |
696 | iexplore.exe | 96.16.143.41:443 | go.microsoft.com | Akamai International B.V. | US | whitelisted |
696 | iexplore.exe | 204.79.197.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
archive.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
ia800701.us.archive.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |