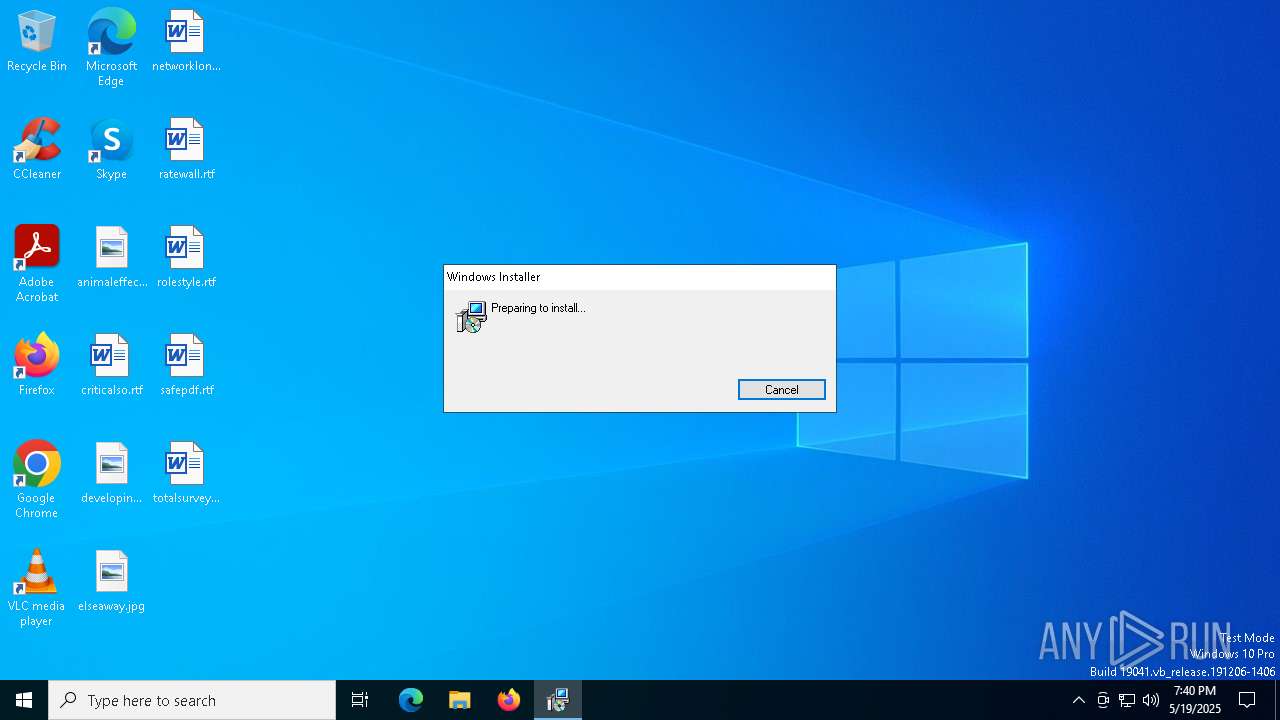
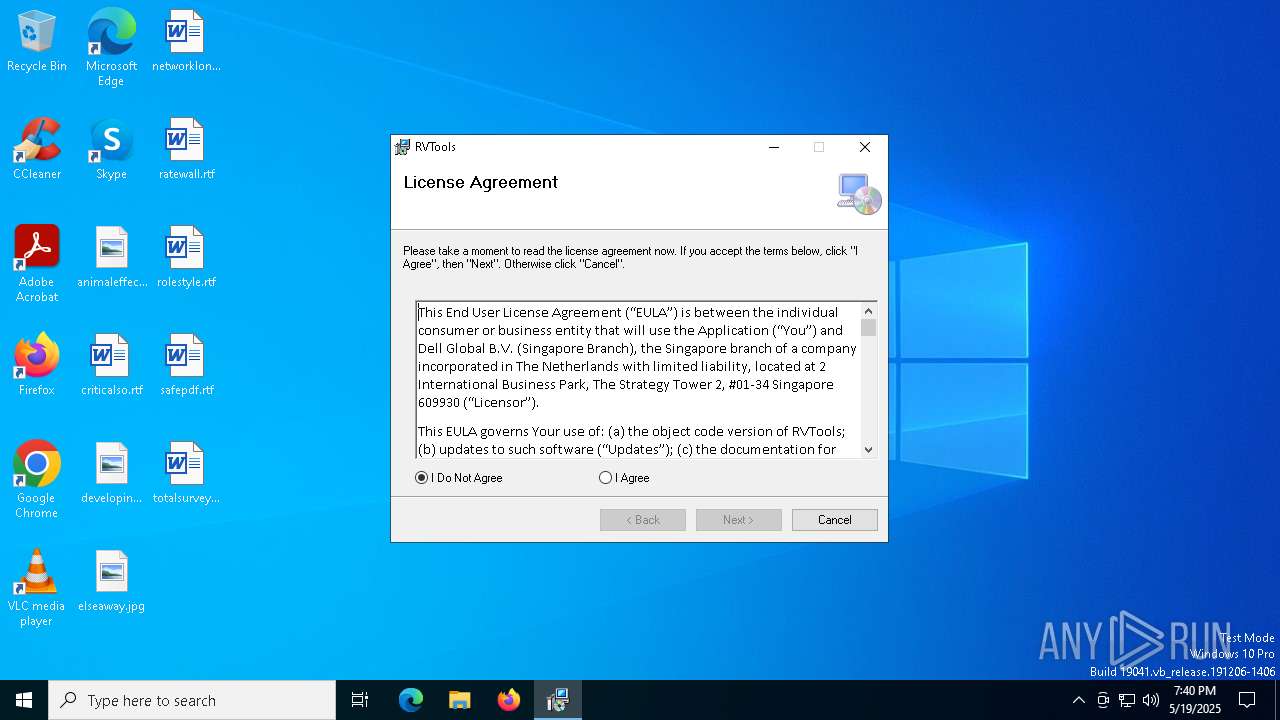
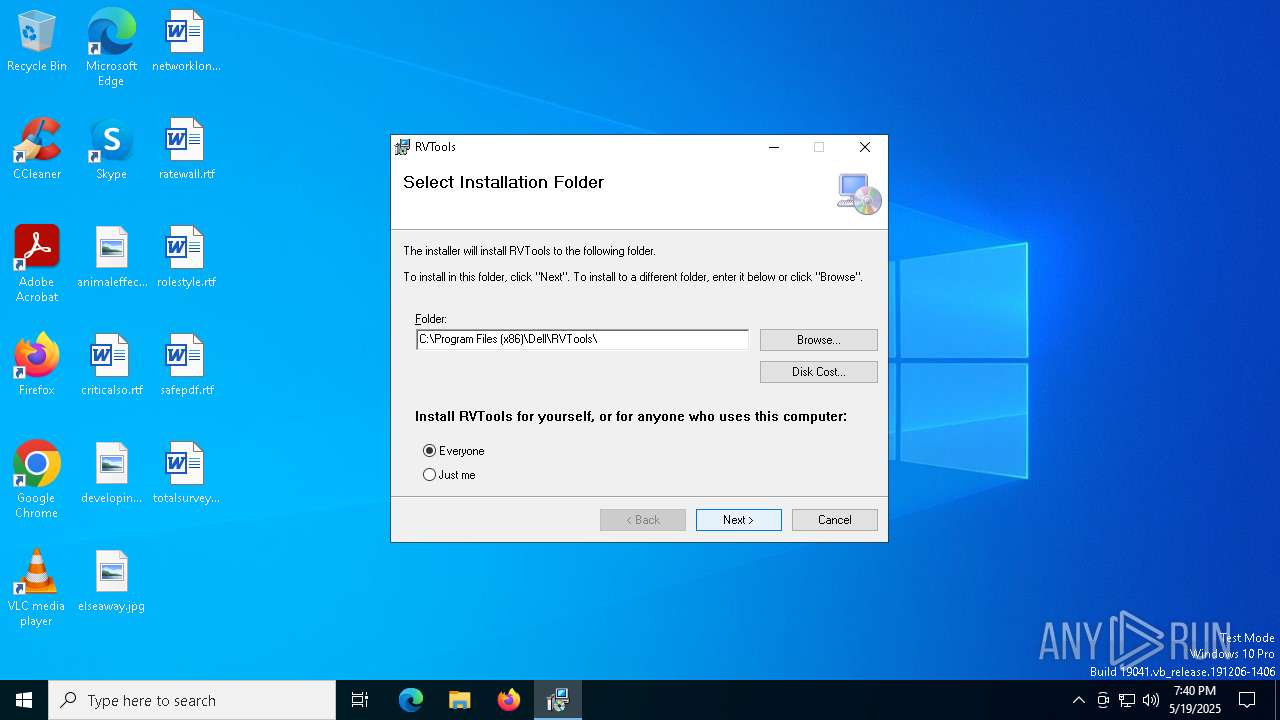
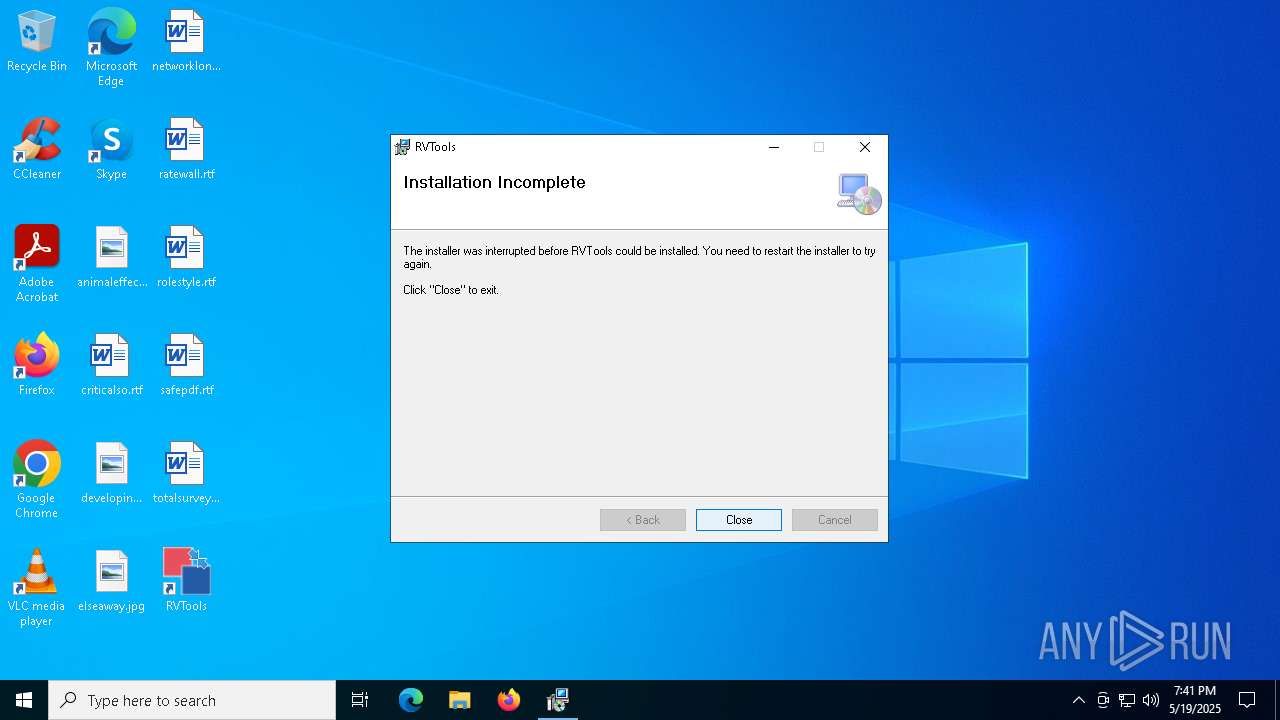
| File name: | RVTools4.7.1.msi |
| Full analysis: | https://app.any.run/tasks/a7db9ce6-43ad-484c-8c4c-b39695946b9f |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 19:40:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 07:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: Intel;1033, Number of Pages: 200, Revision Number: {5BFEF0CB-47D8-439A-BF55-F4EF29CF0340}, Title: RVTools, Author: Dell, Number of Words: 2, Last Saved Time/Date: Thu Oct 3 13:27:08 2024, Last Printed: Thu Oct 3 13:27:08 2024 |
| MD5: | 10610E3E81158E7F2A0C48E2B2F26D99 |
| SHA1: | 8BC692CB4478B317BBC74EE60771B1F723D85649 |
| SHA256: | 0506126BCBC4641D41C138E88D9EA9F10FB65F1EEAB3BFF90AD25330108B324C |
| SSDEEP: | 98304:qiRM4P2DvBKtFuBrvhJCTDOIMQ/DfIMLa0tZwYhwmcp9LANB4UXk53b+tsUlOHDI:tVdIbuH6vc6DYLt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 5968)
- msiexec.exe (PID: 2564)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6048)
Application launched itself
- msiexec.exe (PID: 6048)
Executes as Windows Service
- VSSVC.exe (PID: 1052)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5968)
The sample compiled with english language support
- msiexec.exe (PID: 5968)
- msiexec.exe (PID: 2564)
Reads the software policy settings
- msiexec.exe (PID: 5968)
Creates files or folders in the user directory
- msiexec.exe (PID: 5968)
Checks supported languages
- msiexec.exe (PID: 2564)
- msiexec.exe (PID: 6048)
Reads the computer name
- msiexec.exe (PID: 2564)
- msiexec.exe (PID: 6048)
Checks proxy server information
- msiexec.exe (PID: 5968)
Create files in a temporary directory
- msiexec.exe (PID: 6048)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5968)
- msiexec.exe (PID: 2564)
Process checks computer location settings
- msiexec.exe (PID: 6048)
Manages system restore points
- SrTasks.exe (PID: 5600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
| Pages: | 200 |
| RevisionNumber: | {5BFEF0CB-47D8-439A-BF55-F4EF29CF0340} |
| Title: | RVTools |
| Subject: | - |
| Author: | Dell |
| Keywords: | - |
| Comments: | - |
| Words: | 2 |
| ModifyDate: | 2024:10:03 13:27:08 |
| LastPrinted: | 2024:10:03 13:27:08 |
Total processes
142
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2564 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3676 | "C:\Windows\SysWOW64\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\RVTools4.7.1.msi" /qb! | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5400 | C:\Windows\syswow64\MsiExec.exe -Embedding 93223C7384554CF381FCE310F2997F5C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5600 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\RVTools4.7.1.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1603 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6048 | C:\Windows\syswow64\MsiExec.exe -Embedding 090088EB87831BB4EA3047C5880A0D92 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 542
Read events
7 221
Write events
304
Delete events
17
Modification events
| (PID) Process: | (6048) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings |
| Operation: | write | Name: | JITDebug |
Value: 0 | |||
| (PID) Process: | (2564) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000D96F23EFF5C8DB01040A000004020000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2564) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000D96F23EFF5C8DB01040A000004020000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2564) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000076C61EFF5C8DB01040A000004020000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2564) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000923666EFF5C8DB01040A000004020000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2564) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000A2085FEFF5C8DB01040A000004020000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2564) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000A2085FEFF5C8DB01040A000004020000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1052) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1052) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 48000000000000002556E9EFF5C8DB011C04000078070000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1052) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
Executable files
25
Suspicious files
26
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2564 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2564 | msiexec.exe | C:\Windows\Installer\1133af.msi | — | |
MD5:— | SHA256:— | |||
| 5968 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A37B8BA80004D3266CB4D93B2052DC10_EBDB5A7037F08CDFB408DBFC0D44B43D | binary | |
MD5:F29CD81482428A214BBC62837A2283C2 | SHA256:DF7A645C2CE9609700B4FC00B6A7E893FC5217182CD316415300E4E297187981 | |||
| 5968 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B44415D7D09A541D4434BC30A996B105_245D3F41BD5037E79C8ECB54E5253047 | binary | |
MD5:411386AEA4470577998809686C269A15 | SHA256:C352AC7A87FA0282AAD596C9AE213EF8286B725EDF8474A9F95E046AEA098EA6 | |||
| 5968 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\026A86A161D256DBB33076EDF20C0E5E_586120603910E6A9024E2F8513B0F104 | binary | |
MD5:8779070C3E17A56DE7B4BA5DB2046260 | SHA256:8DD0650B14667C7C02789034B4A09102AA772EA314B4344CF8FE943F381DE7A6 | |||
| 5968 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB807.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 5968 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB8C4.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 2564 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{28acb47e-d5c2-4166-b5e6-e4695367613e}_OnDiskSnapshotProp | binary | |
MD5:8B0B54A33E3844440139062829D7BD9A | SHA256:8B2B9D826841D84939AC1DB13F7F834AED82E444FA6CBE67BDBB45A6E9065743 | |||
| 2564 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:8B0B54A33E3844440139062829D7BD9A | SHA256:8B2B9D826841D84939AC1DB13F7F834AED82E444FA6CBE67BDBB45A6E9065743 | |||
| 2564 | msiexec.exe | C:\Windows\Installer\MSI38E0.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
27
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.179:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5968 | msiexec.exe | GET | 200 | 69.192.162.201:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCEE5A5DdU7eaMAAAAAFHTlH8%3D | unknown | — | — | whitelisted |
5968 | msiexec.exe | GET | 200 | 69.192.162.201:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRr2bwARTxMtEy9aspRAZg5QFhagQQUgrrWPZfOn89x6JI3r%2F2ztWk1V88CEHHvVXSvNVTDWixp9m9La80%3D | unknown | — | — | whitelisted |
5968 | msiexec.exe | GET | 200 | 69.192.162.201:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRRKiO2Poi0XFwdRr1PZXruPzTMZAQU75%2B6ebBz8iUeeJwDUpwbU4Teje0CEErhypfEK2Gwjfs6YRuPAPk%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4188 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4188 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.179:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5968 | msiexec.exe | 69.192.162.201:80 | ocsp.entrust.net | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.entrust.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |