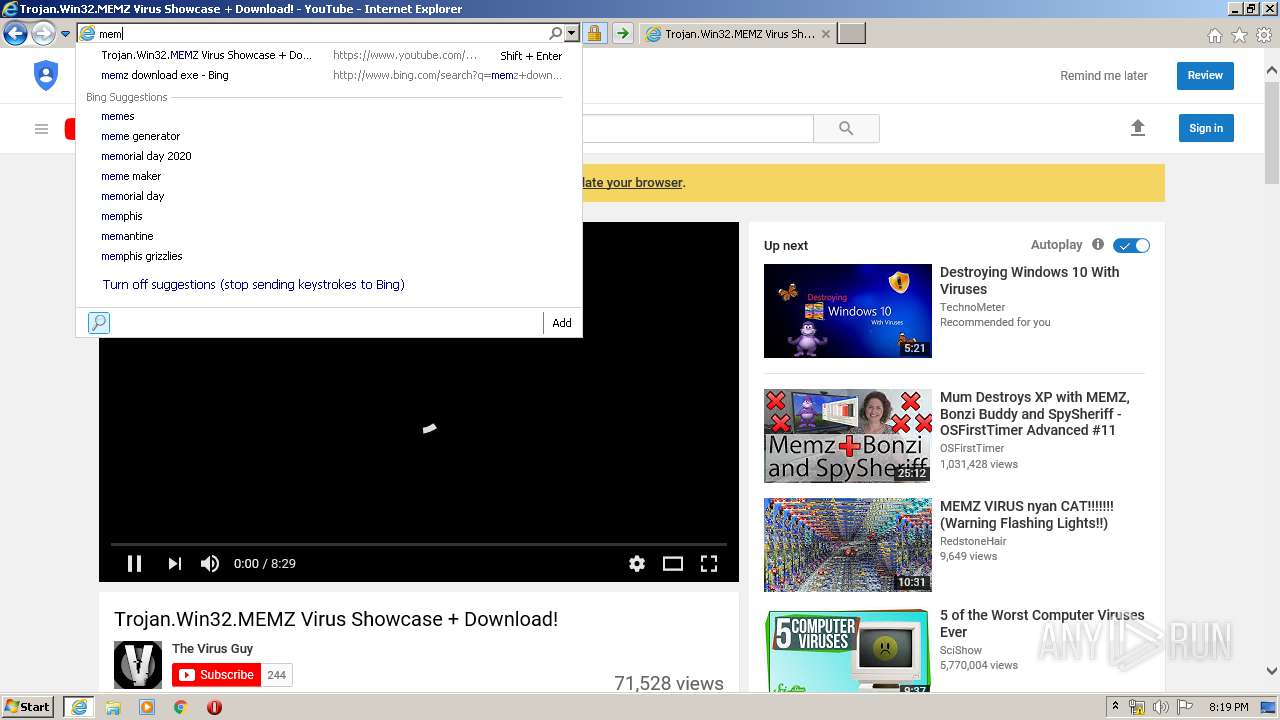
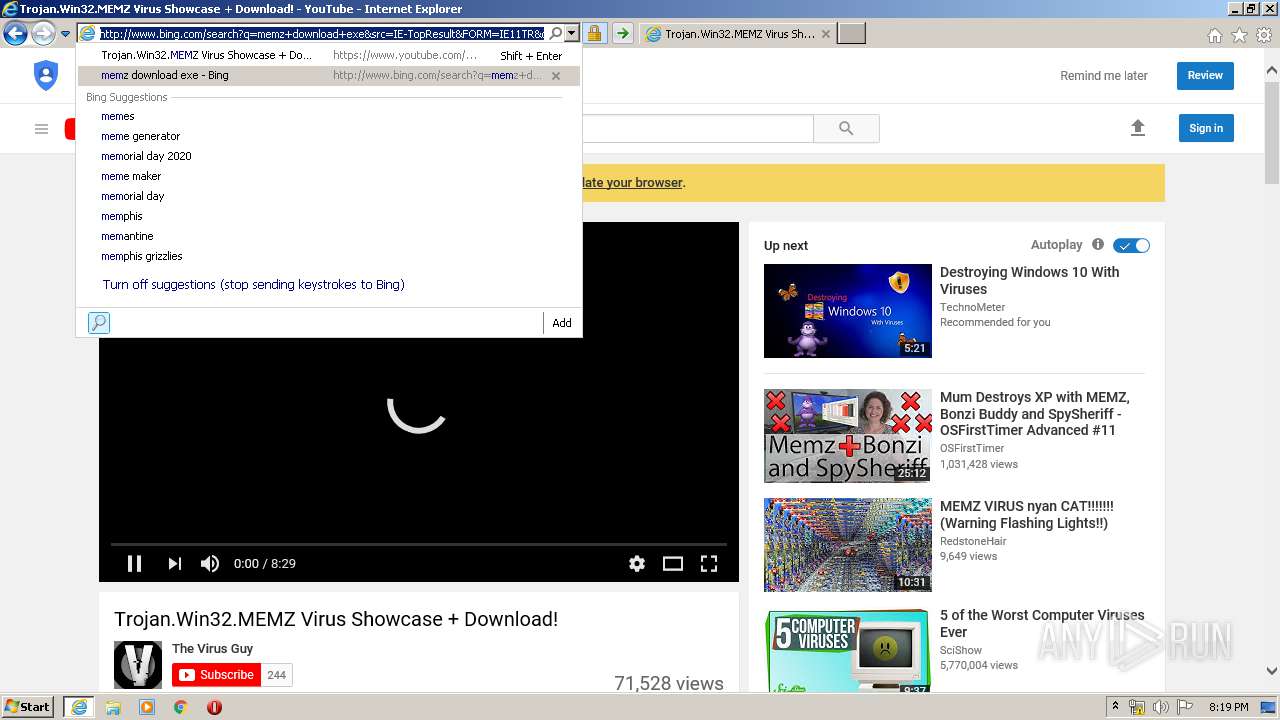
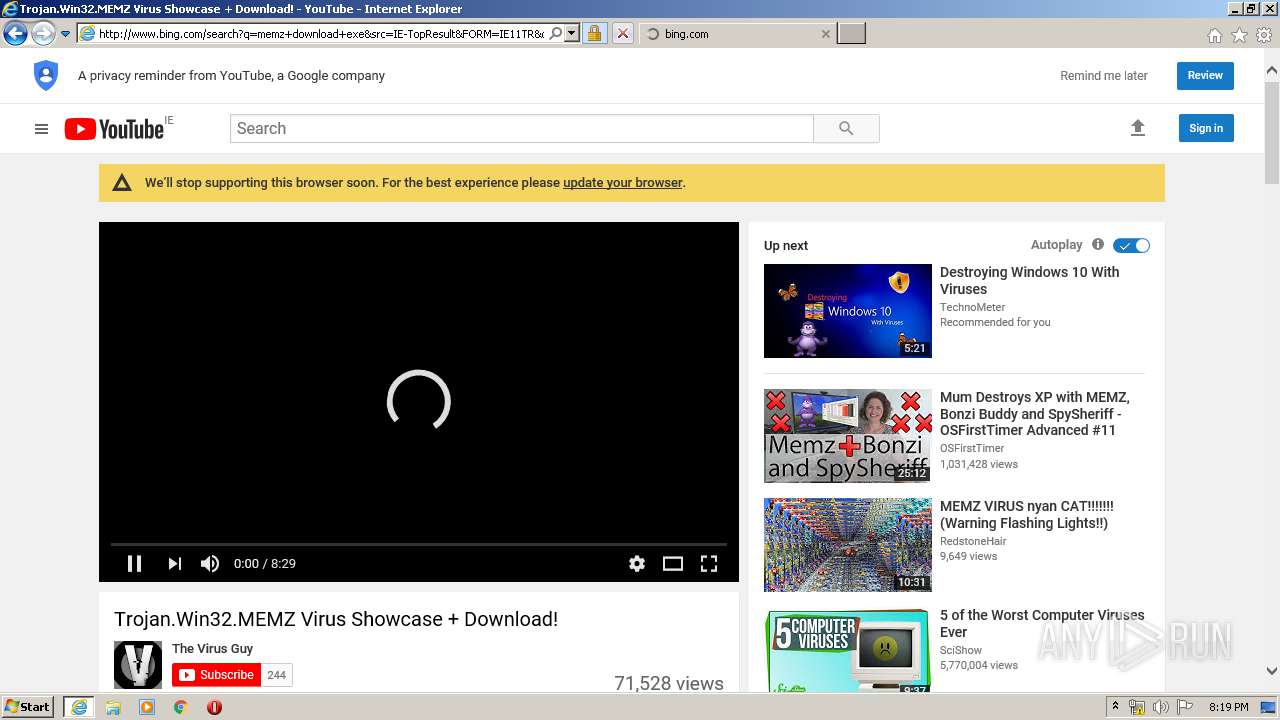
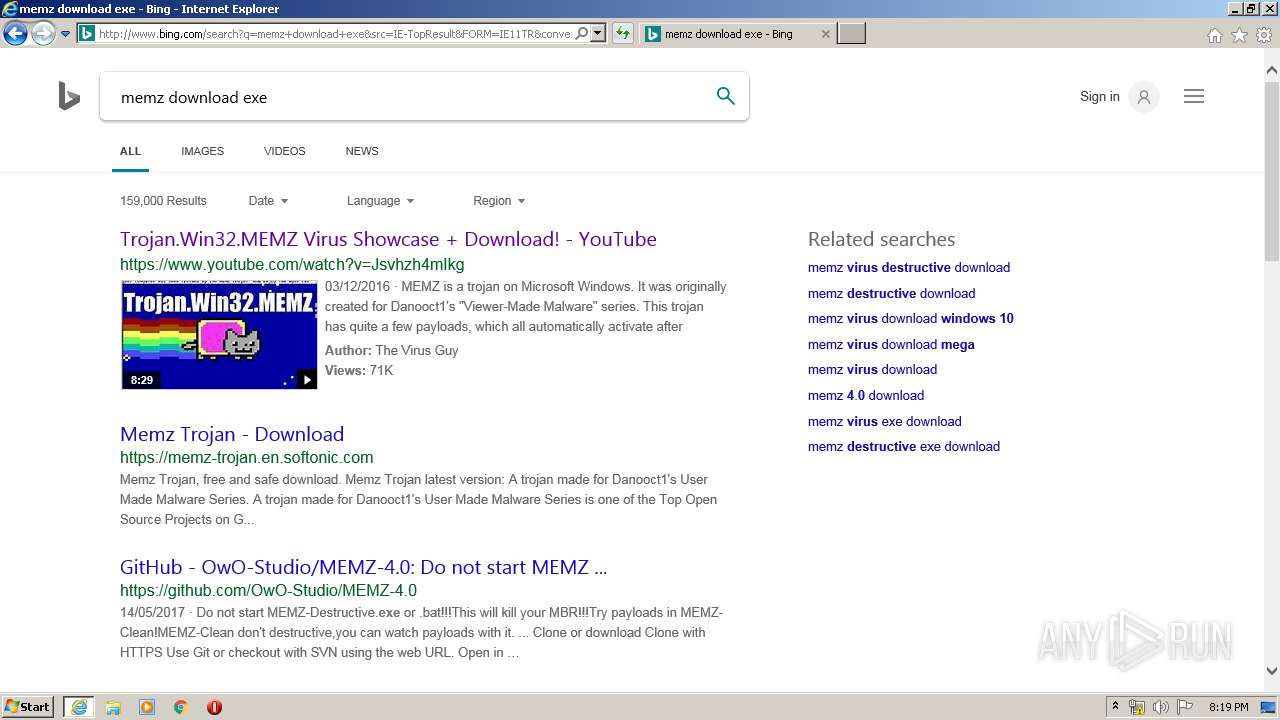
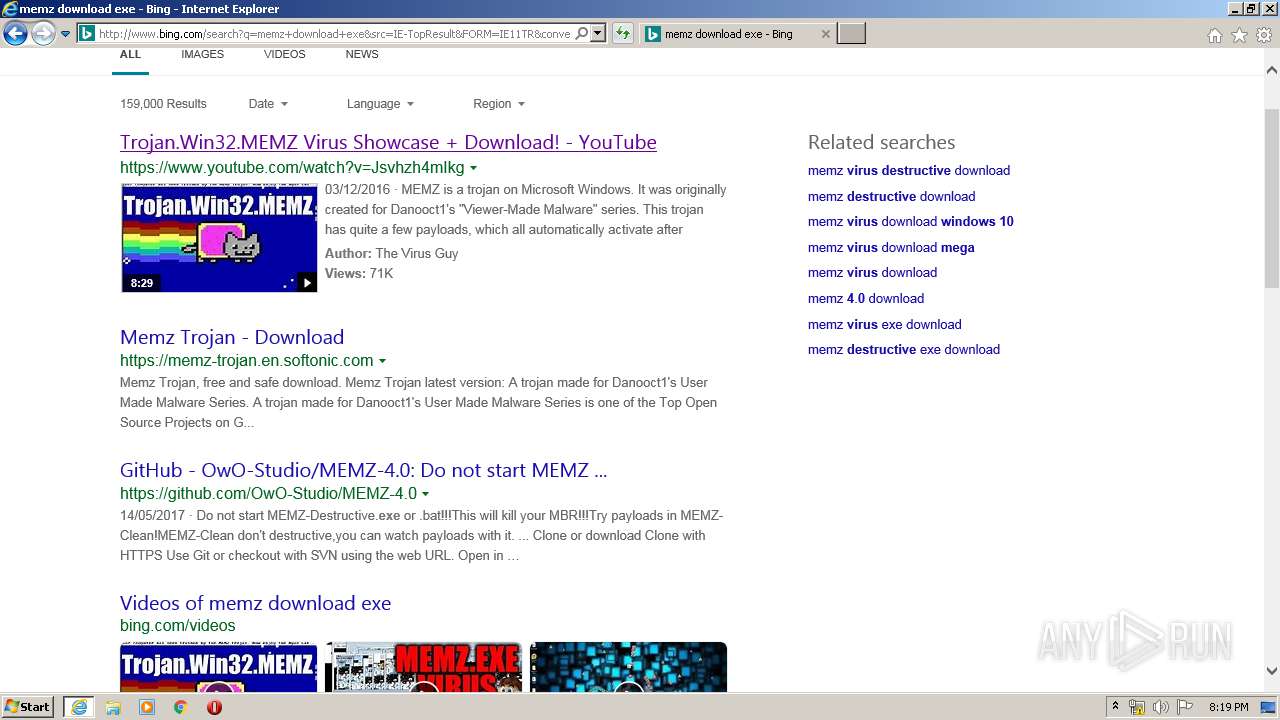
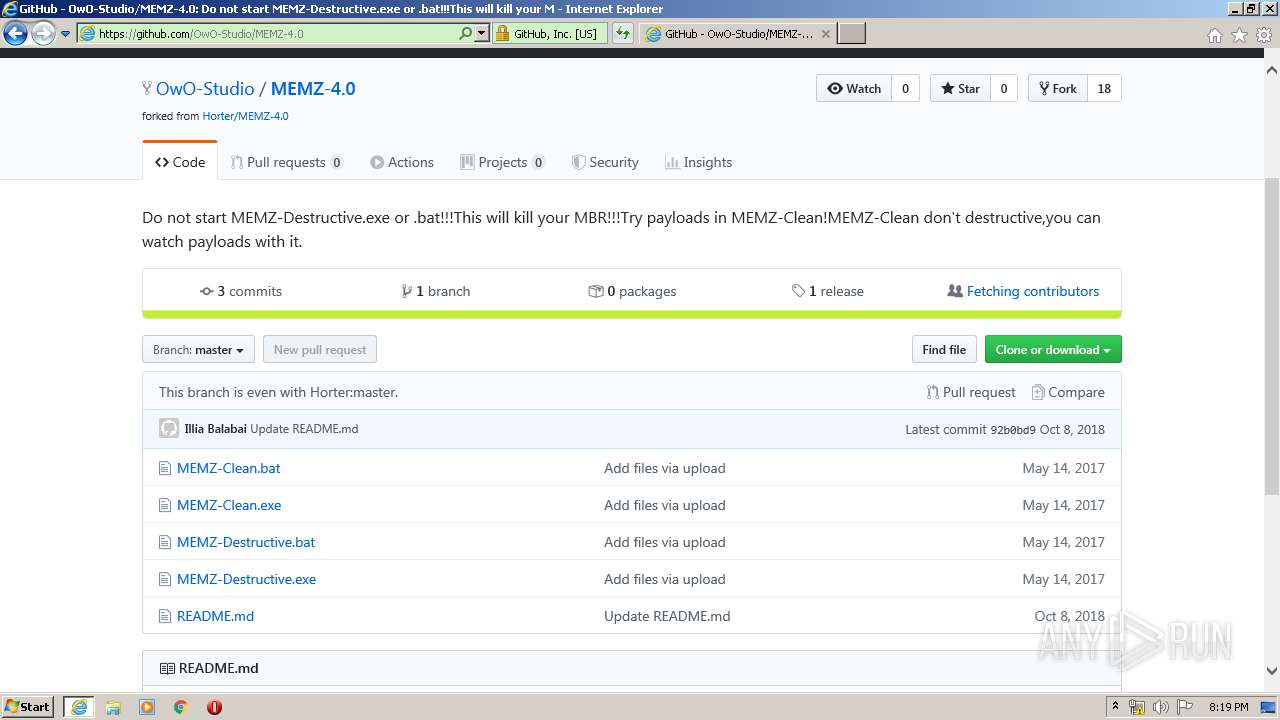
| URL: | https://google.com |
| Full analysis: | https://app.any.run/tasks/ada98101-e42c-4fef-9f63-5120c35d6d16 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 19:18:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 99999EBCFDB78DF077AD2727FD00969F |
| SHA1: | 72FE95C5576EC634E214814A32AB785568EDA76A |
| SHA256: | 05046F26C83E8C88B3DDAB2EAB63D0D16224AC1E564535FC75CDCEEE47A0938D |
| SSDEEP: | 3:N8r3uK:2LuK |
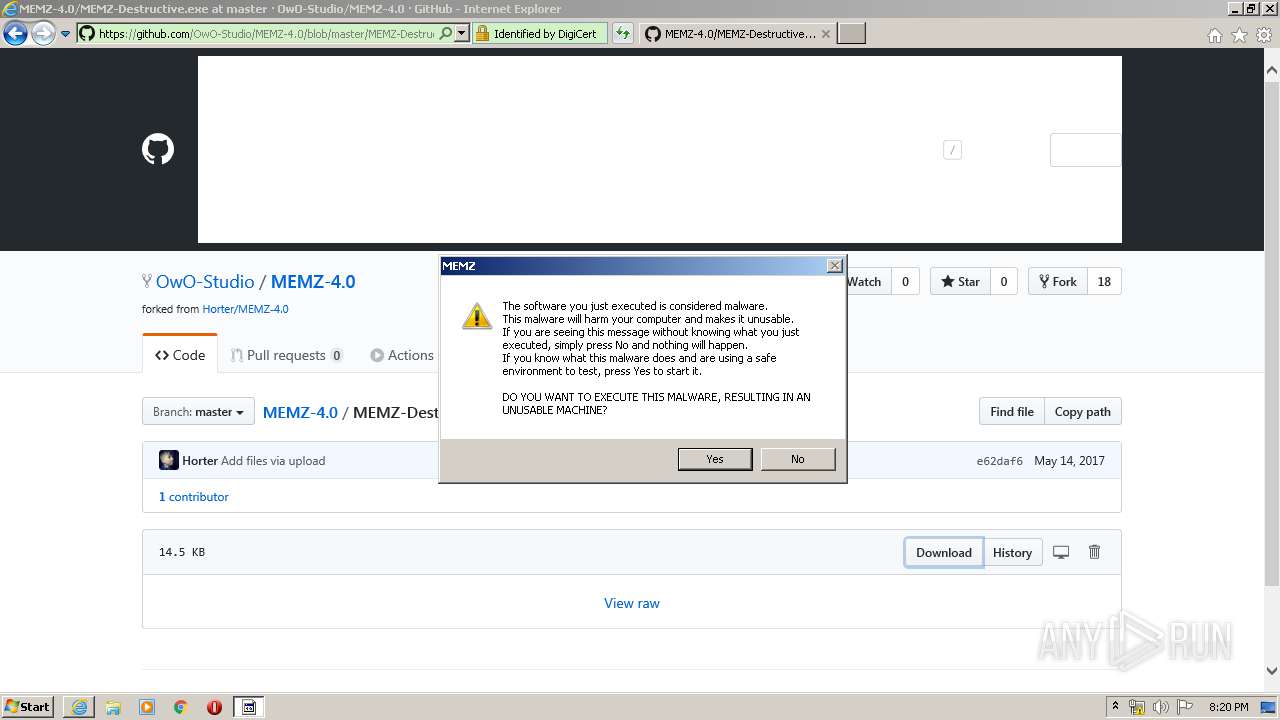
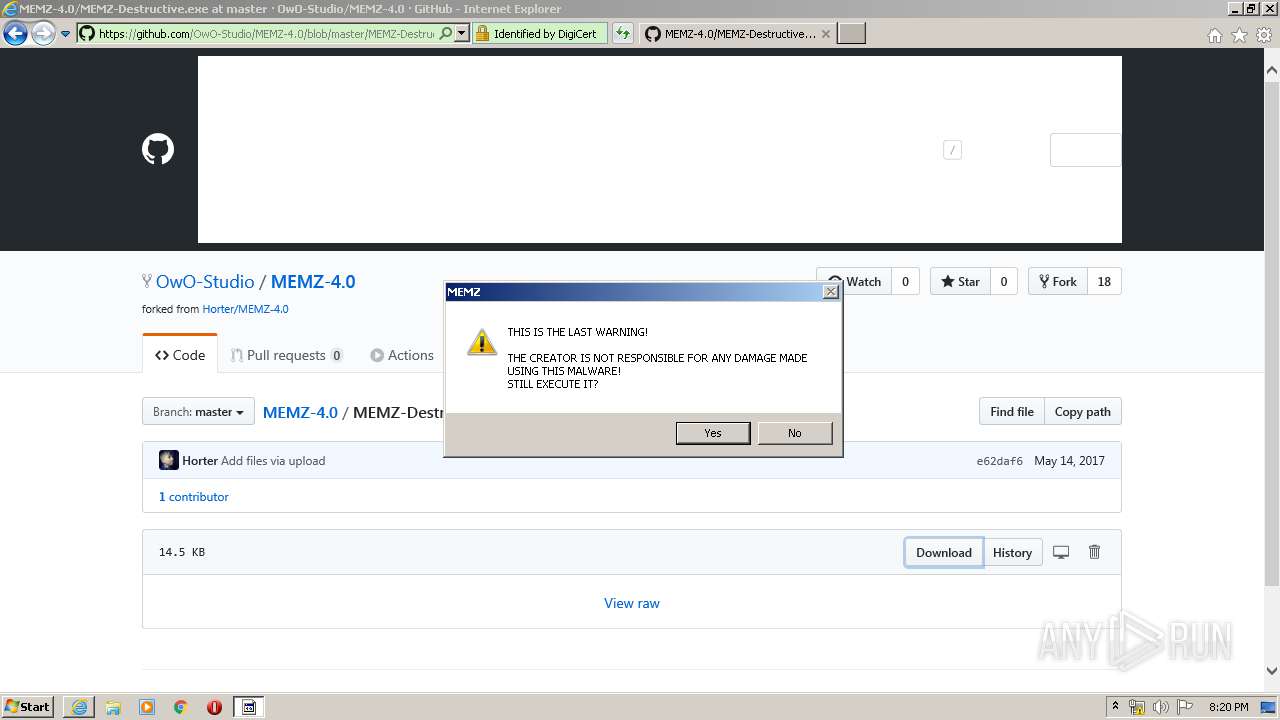
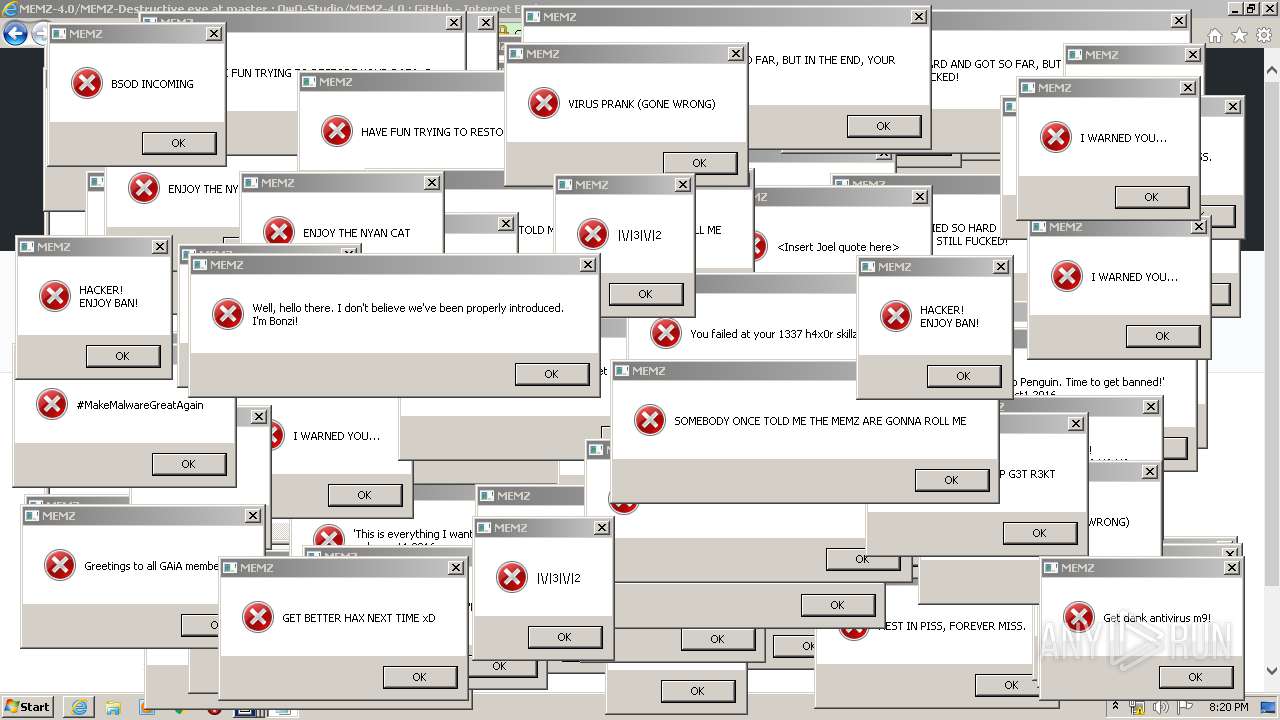
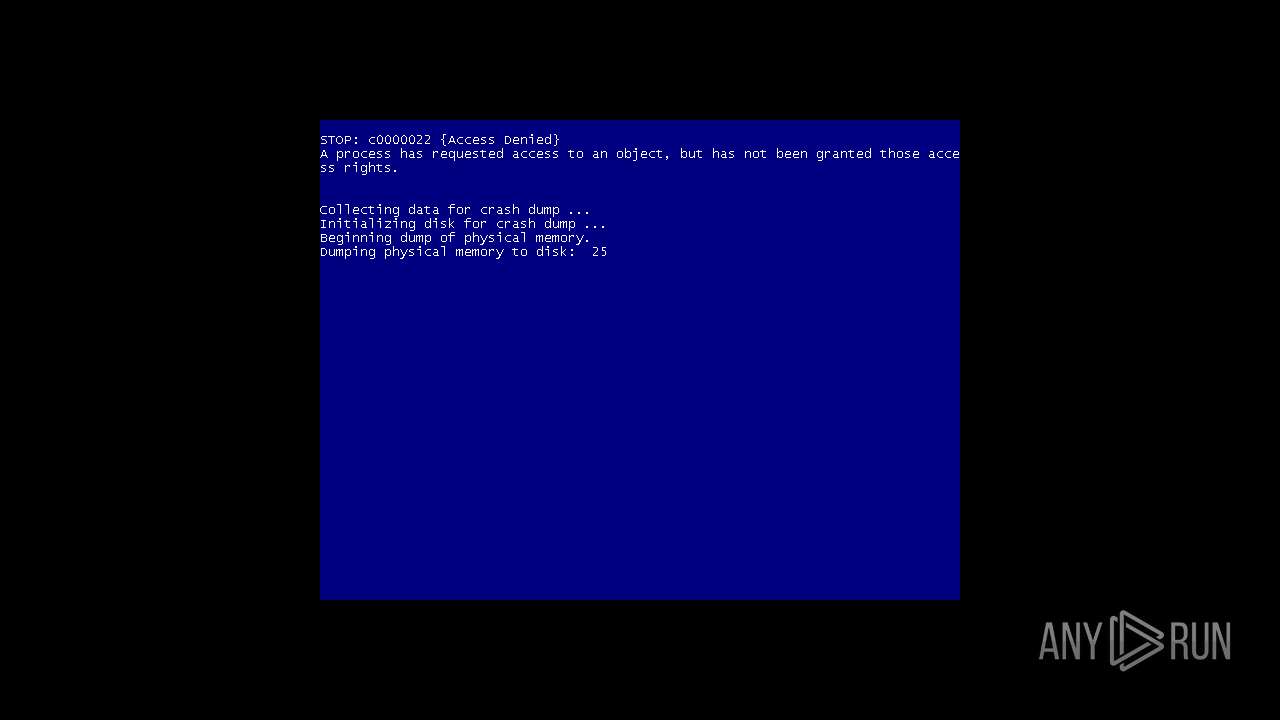
MALICIOUS
Application was dropped or rewritten from another process
- MEMZ-Destructive.exe (PID: 2440)
- MEMZ-Destructive.exe (PID: 3960)
- MEMZ-Destructive.exe (PID: 912)
- MEMZ-Destructive.exe (PID: 2628)
- MEMZ-Destructive.exe (PID: 2952)
- MEMZ-Destructive.exe (PID: 2296)
- MEMZ-Destructive.exe (PID: 2932)
- MEMZ-Destructive.exe (PID: 580)
Low-level write access rights to disk partition
- MEMZ-Destructive.exe (PID: 580)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3012)
- iexplore.exe (PID: 3044)
Application launched itself
- MEMZ-Destructive.exe (PID: 3960)
Low-level read access rights to disk partition
- MEMZ-Destructive.exe (PID: 580)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 3044)
- iexplore.exe (PID: 3012)
- iexplore.exe (PID: 1248)
Changes internet zones settings
- iexplore.exe (PID: 3044)
Reads internet explorer settings
- iexplore.exe (PID: 3012)
- iexplore.exe (PID: 1248)
Application launched itself
- iexplore.exe (PID: 3044)
Reads settings of System Certificates
- iexplore.exe (PID: 1248)
- iexplore.exe (PID: 3012)
- iexplore.exe (PID: 3044)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3012)
Creates files in the user directory
- iexplore.exe (PID: 1248)
- iexplore.exe (PID: 3044)
- iexplore.exe (PID: 3012)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3044)
Changes settings of System certificates
- iexplore.exe (PID: 3044)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
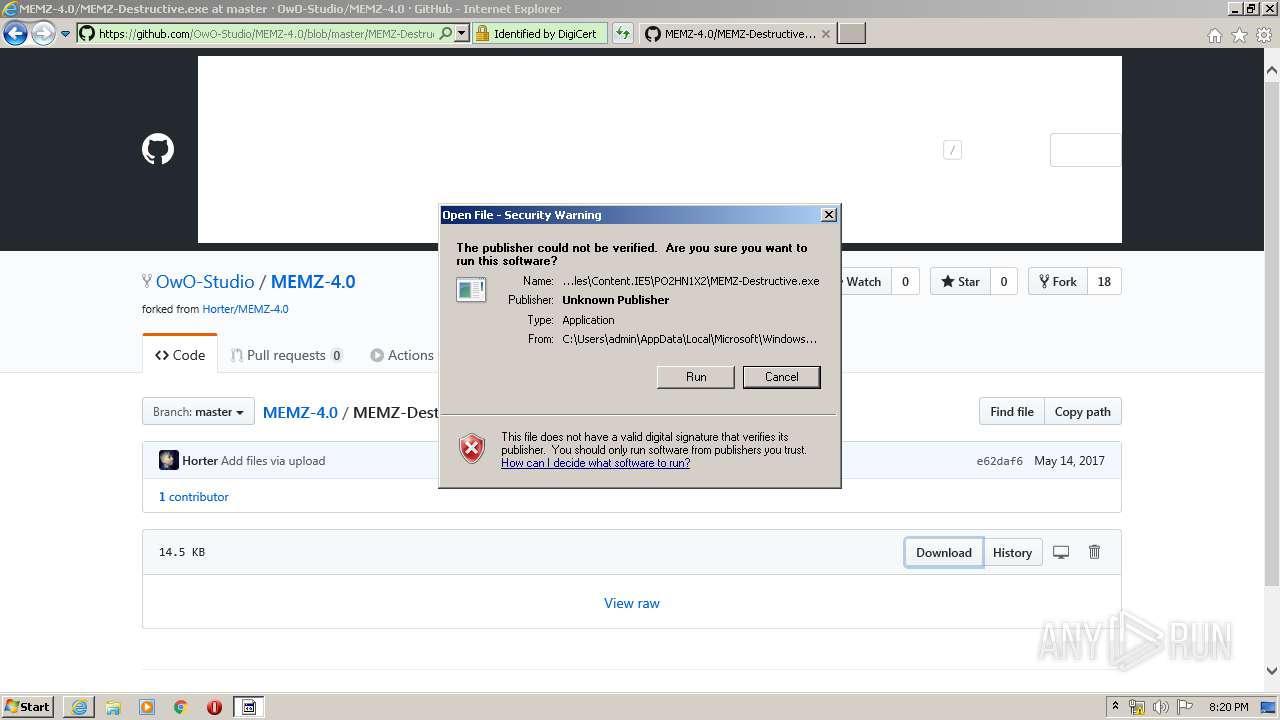
| 580 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe" /main | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe | MEMZ-Destructive.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 912 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3044 CREDAT:3544352 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1900 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\System32\notepad.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2296 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2440 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2628 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2932 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ-Destructive.exe | — | MEMZ-Destructive.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3012 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3044 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
10 572
Read events
2 124
Write events
5 689
Delete events
2 759
Modification events
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 147234574 | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803656 | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
78
Text files
179
Unknown types
36
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\PGXAICWX.txt | — | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\3PCSQWH5.txt | — | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BFNULQTW.txt | — | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\X7GO6VZI.txt | — | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\search[1].htm | html | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ZMCKX417.txt | text | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\D8nShhiaHwwY7S6Dowtg0f0NCMg[1].js | text | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:— | SHA256:— | |||
| 3012 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\th[1].jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
97
TCP/UDP connections
121
DNS requests
51
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3012 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=memz&maxwidth=32765&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 222 b | whitelisted |
3012 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/search?q=memz+download+exe&src=IE-TopResult&FORM=IE11TR&conversationid= | US | html | 67.1 Kb | whitelisted |
3012 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/th?id=OVP.UvZbuPsrMHy2ot4cPrExJQEsDh:OVP.vHzB4B2sHjfLgaSlueoSygHgFo&w=197&h=110&c=7&rs=1&qlt=90&pid=1.7&bw=3&bc=ffffff | US | image | 16.2 Kb | whitelisted |
3012 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/rb/14/cj,nj/-nK5HAtc03YD_-fIE4Q-t8DnnZY.js?bu=DiovZHR5fHFnarMBtQEvoAEv | US | text | 7.65 Kb | whitelisted |
3012 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/rs/6g/16F/cj,nj/JOVKK9CwtlLttGBW-c2T2aVxX_U.js | US | text | 297 b | whitelisted |
3012 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/rs/2Z/2r/cj,nj/GTd5evTp2v9quFX_8_4U14MoprA.js | US | text | 816 b | whitelisted |
3012 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/rb/5g/cj,nj/D8nShhiaHwwY7S6Dowtg0f0NCMg.js?bu=EpMhqyHMINcgqQXrIO0guyHcIPYg-iClIakhnCH6H5gfmh-JIA | US | text | 5.38 Kb | whitelisted |
3012 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/rs/3P/pq/cj,nj/lwQdVqXdJk4a1F5YBjGkU_5t-WY.js | US | text | 425 b | whitelisted |
3012 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/rs/3P/dn/cj,nj/MMEgsTPmgL4RSsDZTuQZxkynWYQ.js | US | text | 2.20 Kb | whitelisted |
3044 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3012 | iexplore.exe | 172.217.21.238:443 | google.com | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 13.107.5.80:80 | api.bing.com | Microsoft Corporation | US | whitelisted |
3044 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3012 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 13.107.5.80:80 | api.bing.com | Microsoft Corporation | US | whitelisted |
3012 | iexplore.exe | 40.126.1.130:443 | login.microsoftonline.com | Microsoft Corporation | US | malicious |
3012 | iexplore.exe | 172.217.18.163:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3012 | iexplore.exe | 104.18.25.243:80 | ocsp.msocsp.com | Cloudflare Inc | US | shared |
3012 | iexplore.exe | 172.217.22.98:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
login.live.com |
| whitelisted |
www2.bing.com |
| whitelisted |
a4.bing.com |
| whitelisted |
www.youtube.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3012 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |