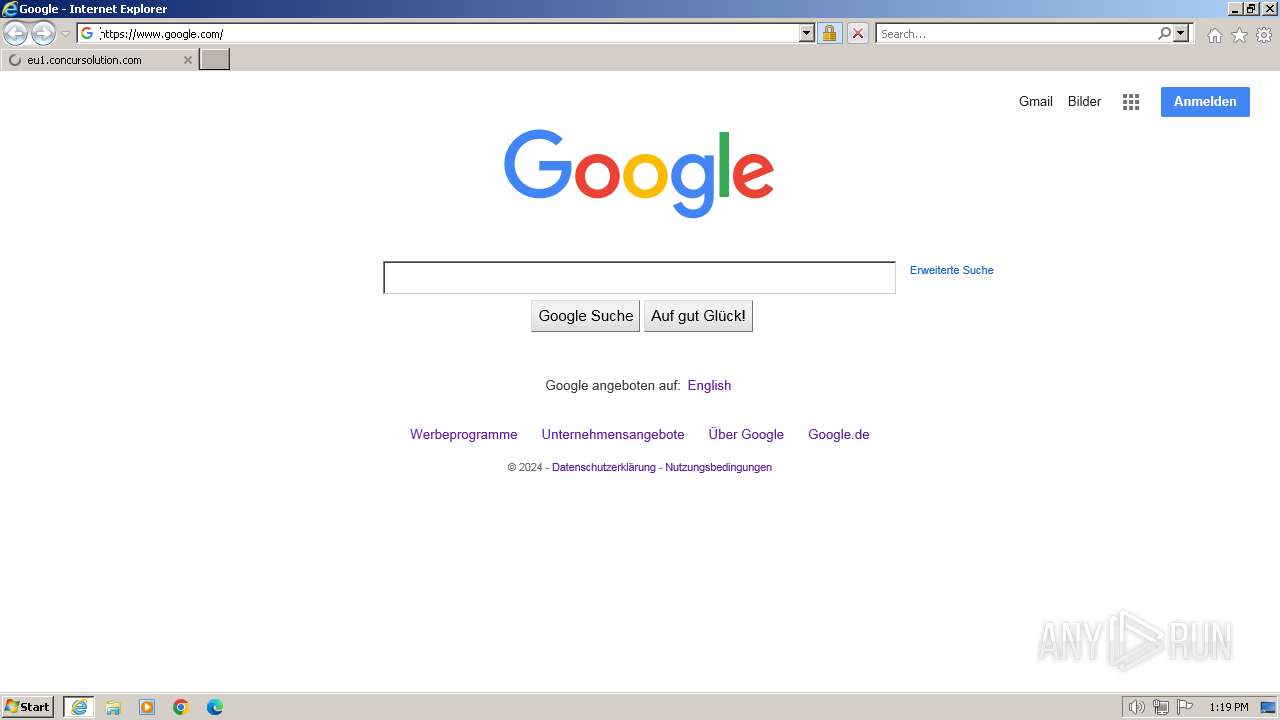
| URL: | https://google.com |
| Full analysis: | https://app.any.run/tasks/655a3b0f-0209-44b6-9035-5106d00821e8 |
| Verdict: | Malicious activity |
| Analysis date: | January 19, 2024, 13:18:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 99999EBCFDB78DF077AD2727FD00969F |
| SHA1: | 72FE95C5576EC634E214814A32AB785568EDA76A |
| SHA256: | 05046F26C83E8C88B3DDAB2EAB63D0D16224AC1E564535FC75CDCEEE47A0938D |
| SSDEEP: | 3:N8r3uK:2LuK |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
0
Suspicious processes
0
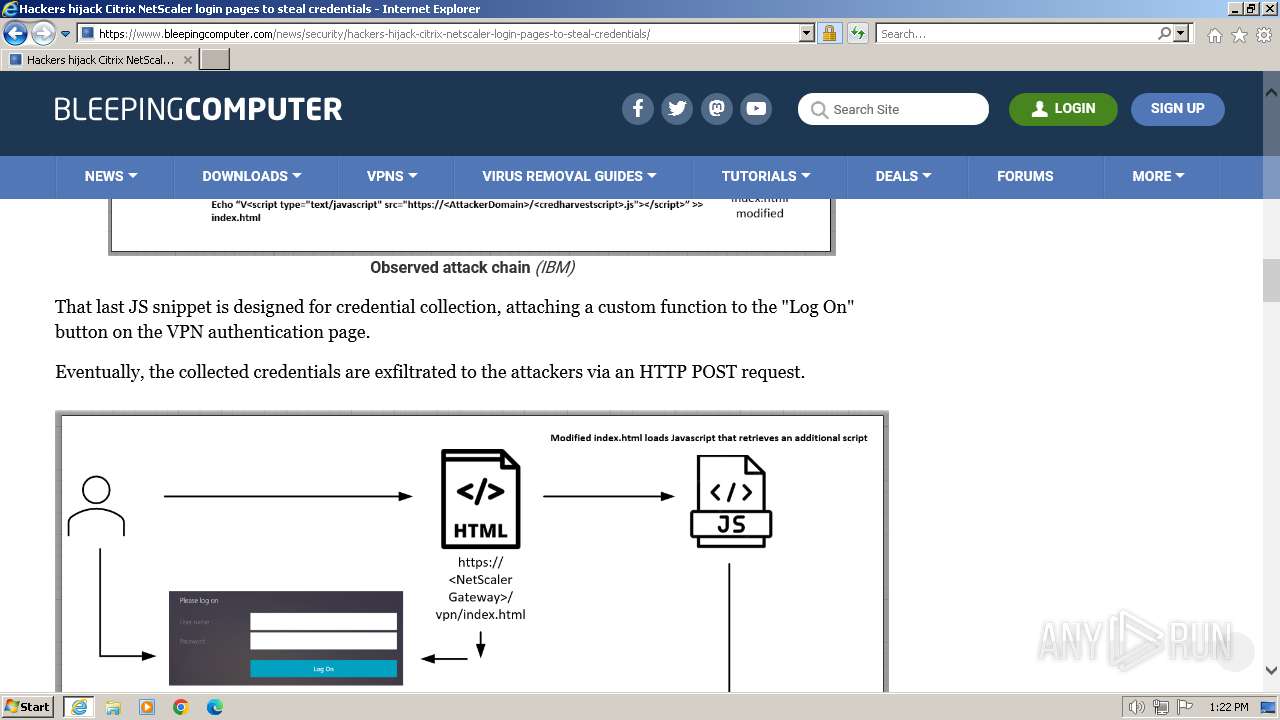
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://google.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:124 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
24 970
Read events
24 747
Write events
221
Delete events
2
Modification events
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
76
Text files
244
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:5E90FD4F239B0A4CC37DF3E3310B6CED | SHA256:97C84ECDF847C3E60107F1F75303EF81E13CD595FEB1F70D1E3F5E3A7F7FBF67 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\googlelogo_white_background_color_272x92dp[1].png | image | |
MD5:B593548AC0F25135C059A0AAE302AB4D | SHA256:44FC041CB8145B4EF97007F85BDB9ABDB9A50D744E258B0C4BB01F1D196BF105 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E87CE99F124623F95572A696C80EFCAF_ACE741CAE478F9E8195FFCECA66B0544 | binary | |
MD5:35385E00A17148E9839E929D316C7E5F | SHA256:C5D09610251554627D7CFC762A820F34EABCC146C75A1B7247282658A8C04B87 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:85F5248D6F554137CBBF0AD7ADE46FA3 | SHA256:55FD092C25EA288F42919A69A86A5EF3B464EE22AEF0966DB1C1FAD9094113E6 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E87CE99F124623F95572A696C80EFCAF_ACE741CAE478F9E8195FFCECA66B0544 | der | |
MD5:E7E55265CCFDDD060C81EA8D029B87CB | SHA256:1EF9D9F2683777642E7A361A2AB9E2786FE2F70E576F86D3F9D84C87AB69A088 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\CO2ZQRAV.txt | text | |
MD5:2EE0A05C1E782F8A42028BCAAD2F3449 | SHA256:CD200D909F466163B9AD6A5F7EDA364D4CFB5A044244AC01D1BFFC43952127D3 | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\NMO1EF4Y.htm | html | |
MD5:276BBB20C29087E88DB63899FD8F9129 | SHA256:5B61B0C2032B4AA9519D65CC98C6416C12415E02C7FBBAA1BE5121DC75162EDB | |||
| 2204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E87CE99F124623F95572A696C80EFCAF_F6683F4776D0303FB83B8F5DA6BFA751 | binary | |
MD5:511C2E989AD7D1EEA773F94E5F9D5903 | SHA256:84CC34D791BC9925A947D628D9E9AA660DA7527A6C6C68283608CC01BE4874DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
134
DNS requests
79
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2204 | iexplore.exe | GET | 200 | 23.53.40.56:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?608cb4ab6d3f68d3 | unknown | compressed | 4.66 Kb | unknown |
2204 | iexplore.exe | GET | 200 | 23.53.40.56:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f6bf34dbb61e71d7 | unknown | compressed | 4.66 Kb | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCc21SZGmxMgAqM79mihzX3 | unknown | binary | 472 b | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECbzjAowsPTyEMLulIc7EGw%3D | unknown | binary | 471 b | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCAPCRpfvazdAnzYNtm9aj3 | unknown | binary | 472 b | unknown |
124 | iexplore.exe | GET | 304 | 23.53.40.56:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d8f761b8c0f86c21 | unknown | — | — | unknown |
124 | iexplore.exe | GET | 304 | 23.53.40.56:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1a6e676fbb64f2cc | unknown | — | — | unknown |
2204 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDG7Gp%2BrTCD1hArSp%2FkcvFM | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2204 | iexplore.exe | 216.58.206.46:443 | google.com | GOOGLE | US | whitelisted |
2204 | iexplore.exe | 23.53.40.56:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2204 | iexplore.exe | 142.250.185.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2204 | iexplore.exe | 142.250.185.164:443 | www.google.com | GOOGLE | US | whitelisted |
2204 | iexplore.exe | 142.250.186.67:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
2204 | iexplore.exe | 142.250.186.35:443 | www.gstatic.com | GOOGLE | US | whitelisted |
124 | iexplore.exe | 142.250.185.164:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
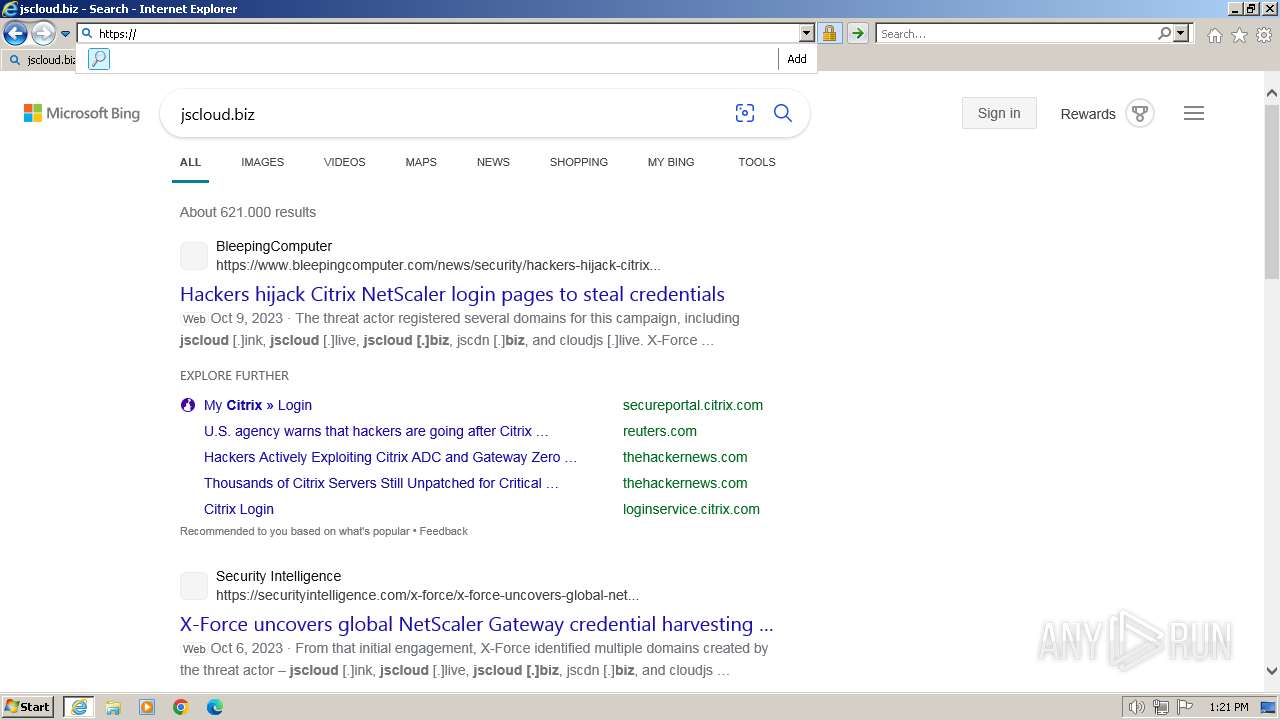
1080 | svchost.exe | A Network Trojan was detected | ET MALWARE Malicious Domain in DNS Lookup (jscloud .biz) |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2204 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |