| File name: | TCP-SetParam.exe |
| Full analysis: | https://app.any.run/tasks/c4e595b9-4789-41c6-881d-e7861b44a8de |
| Verdict: | Malicious activity |
| Analysis date: | July 01, 2024, 23:06:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CF2056FDEFAF254B0E2F22BD3672E89A |
| SHA1: | 6D8BE869A8E20692E22394C41C5FD6D96DBCCC56 |
| SHA256: | 04E1FBEBC75120E5BFEBF67940E7844E5D400EC72F52939EE31506B3CA2DF6EA |
| SSDEEP: | 12288:B3W7nePwZ4ckUlKEVuFxBlDtigjMN1CGBAp5HgtE+:BaePwybBpjMN1CKAp5H4 |
MALICIOUS
Drops the executable file immediately after the start
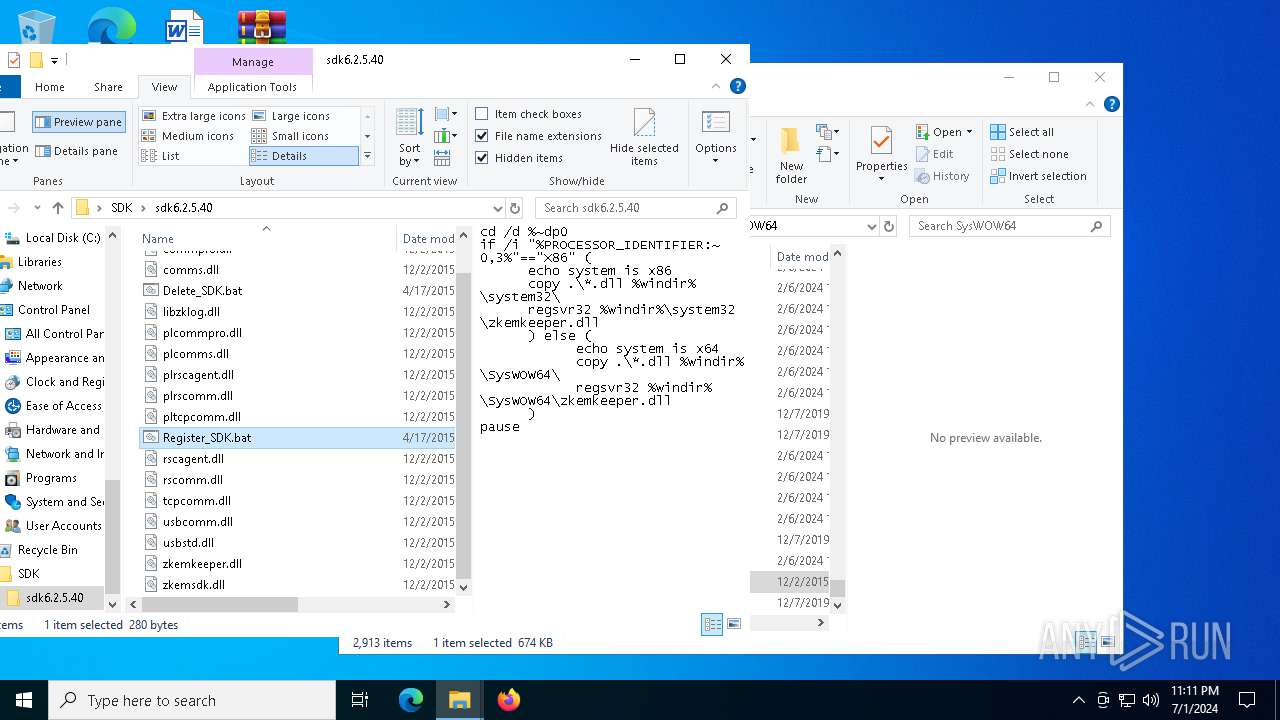
- TCP-SetParam.exe (PID: 3532)
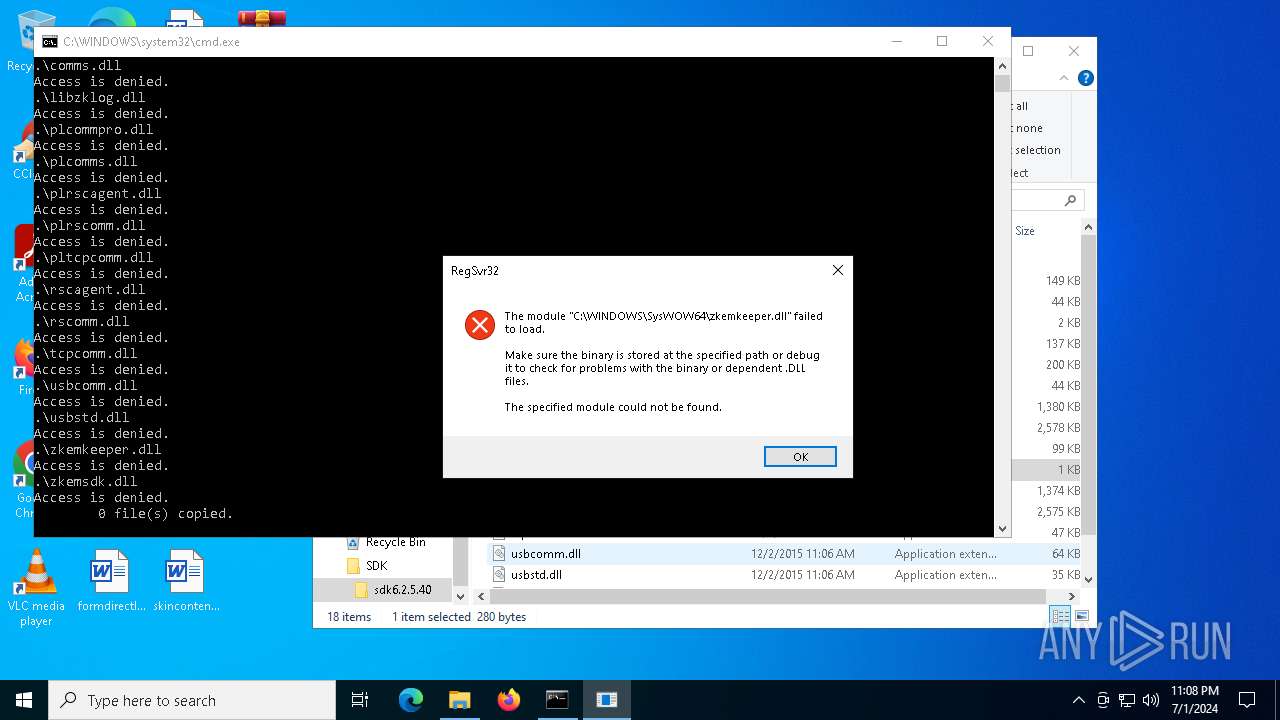
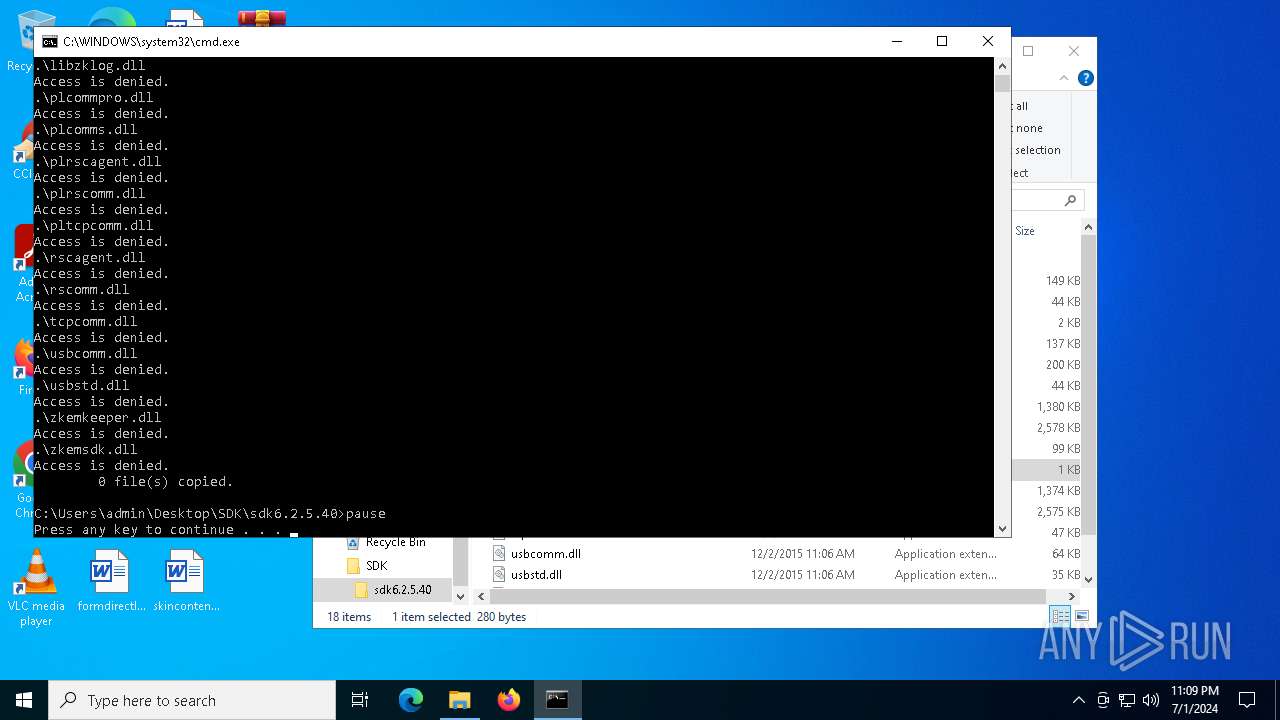
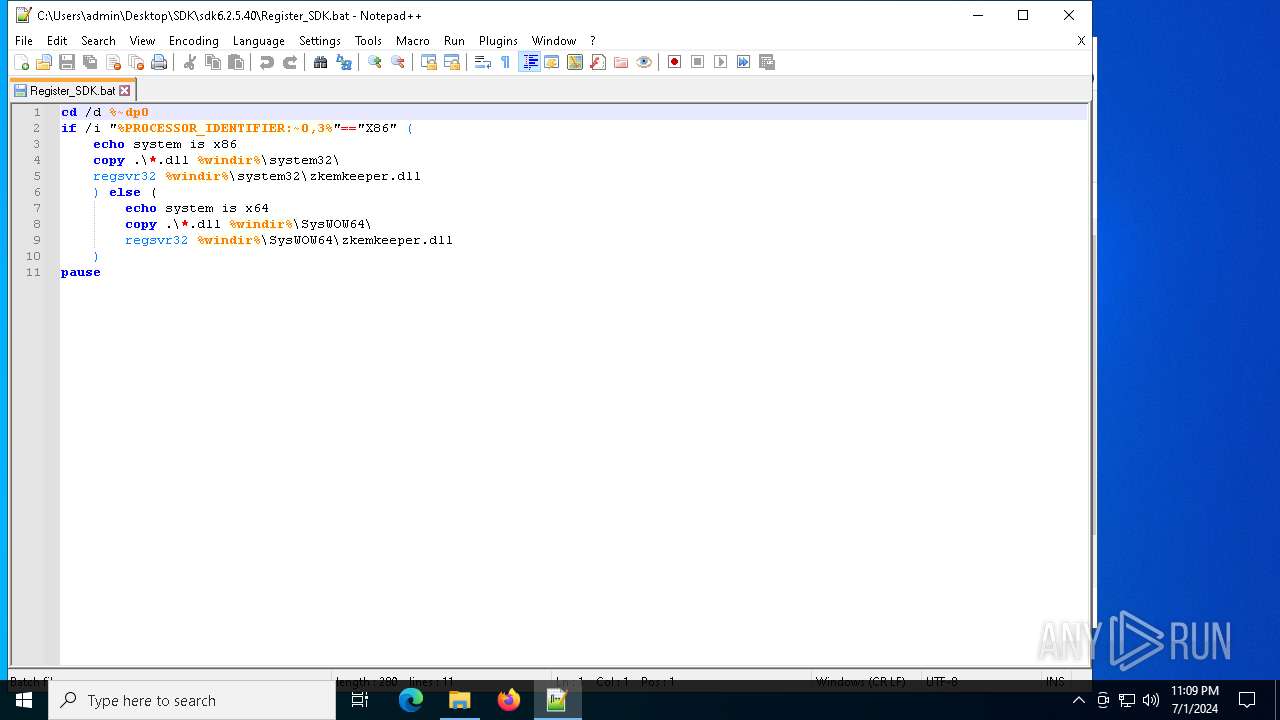
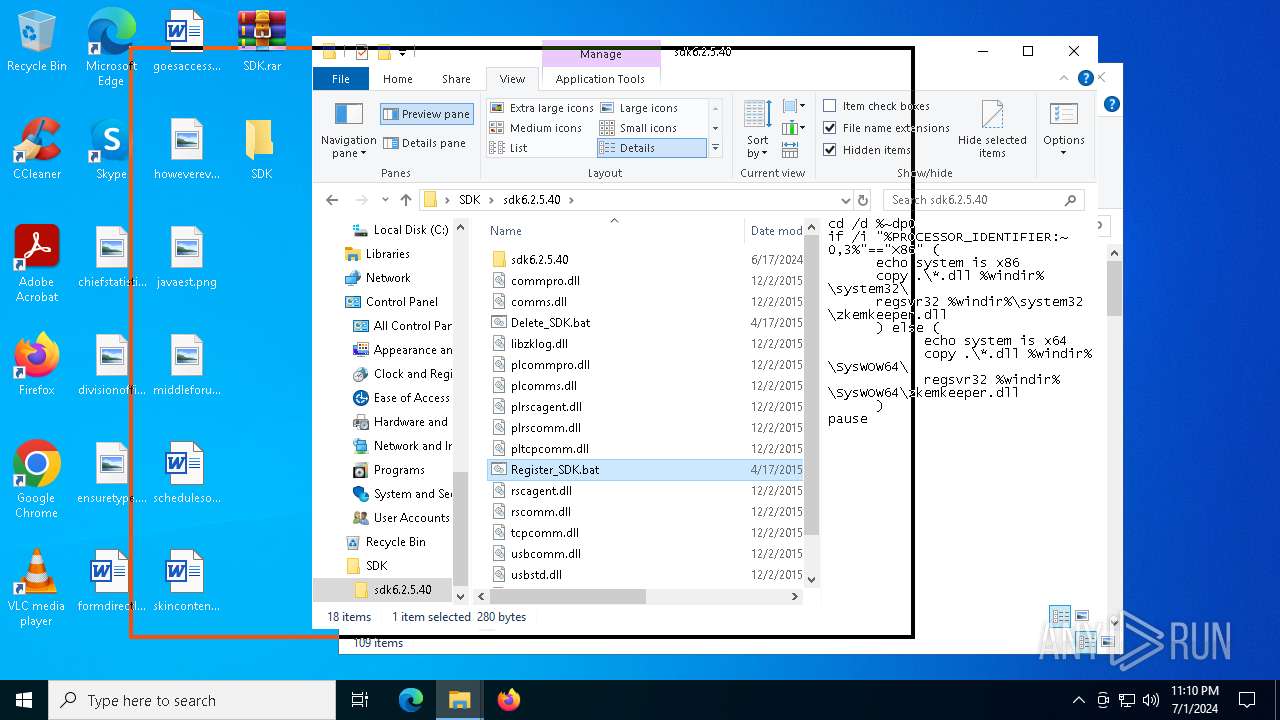
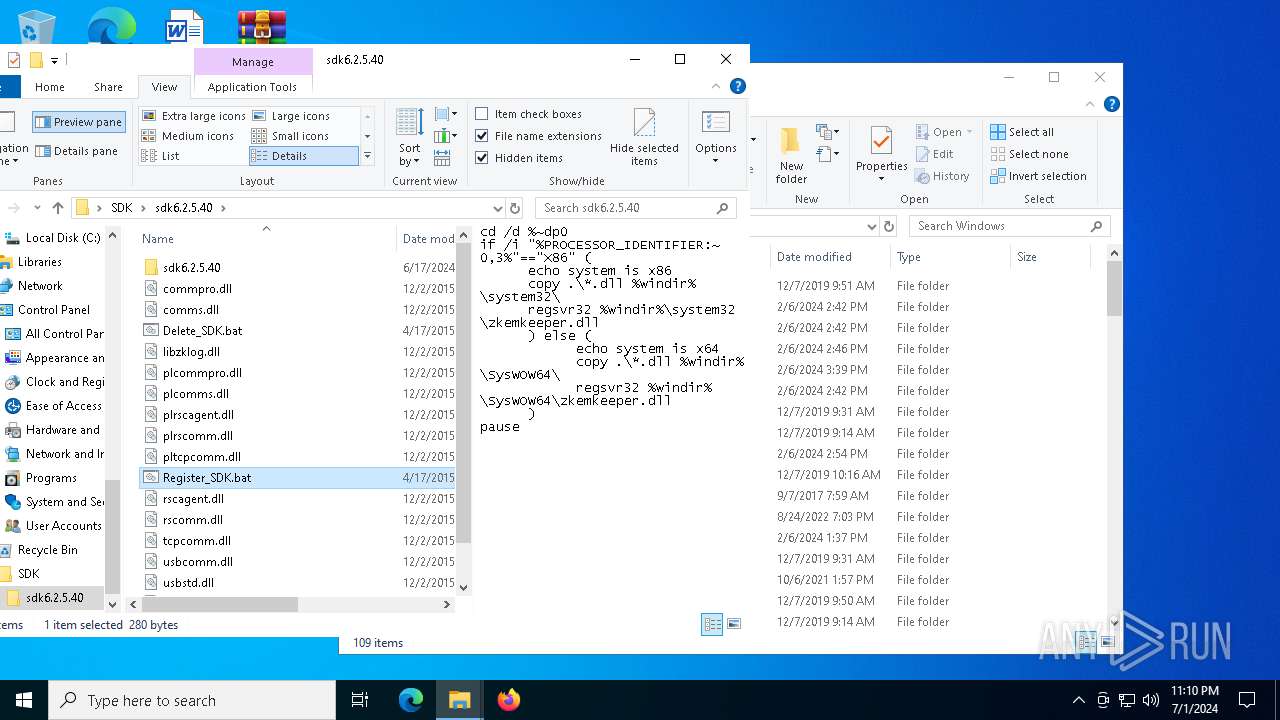
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 5956)
Creates a writable file in the system directory
- dllhost.exe (PID: 4648)
- dllhost.exe (PID: 5508)
SUSPICIOUS
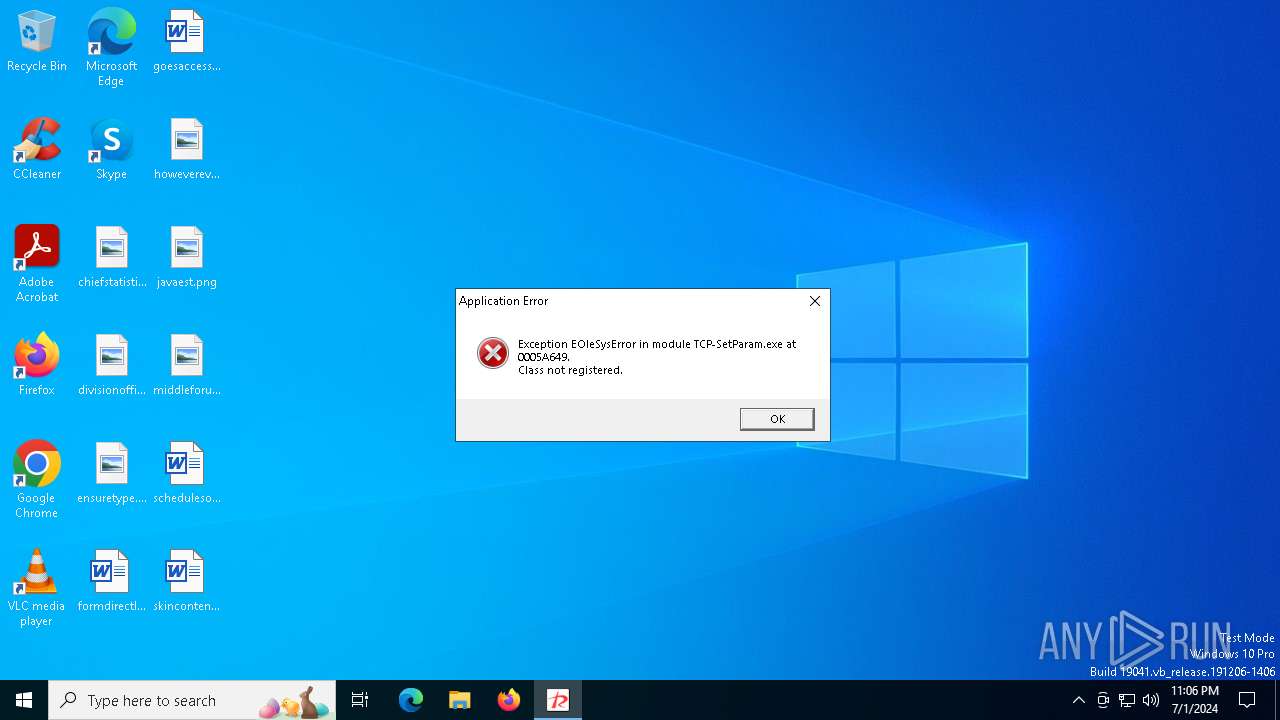
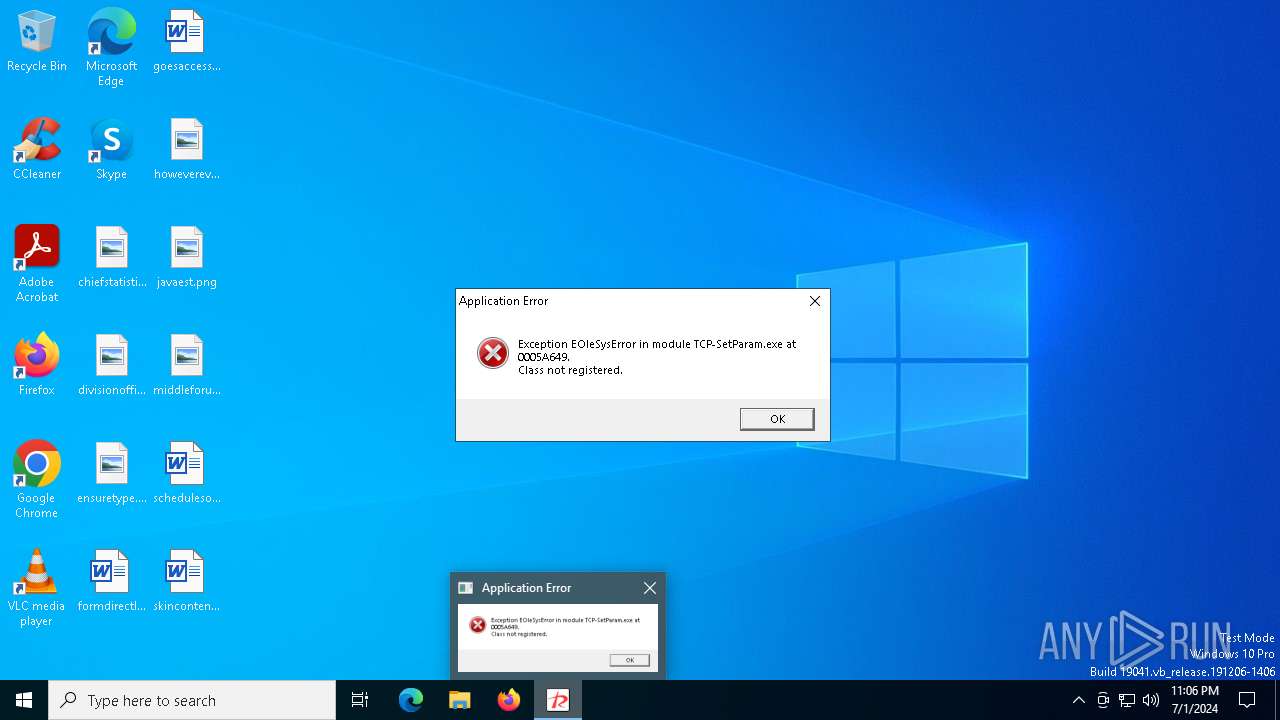
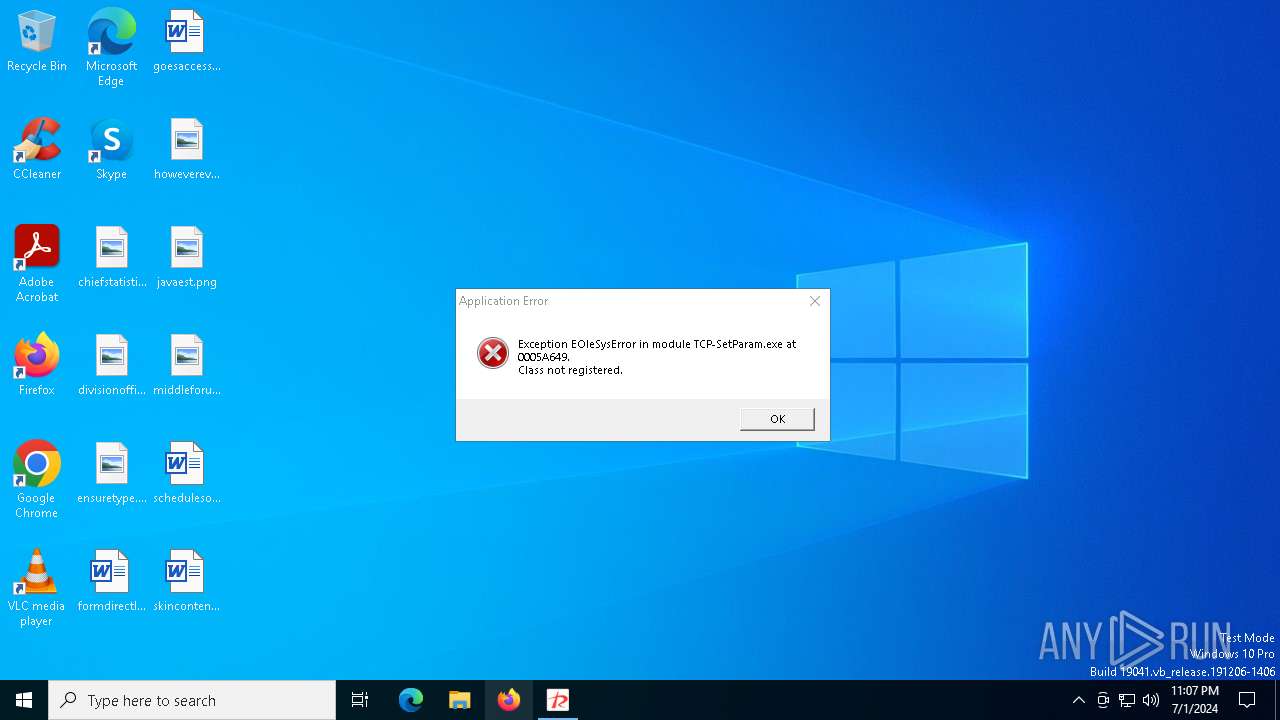
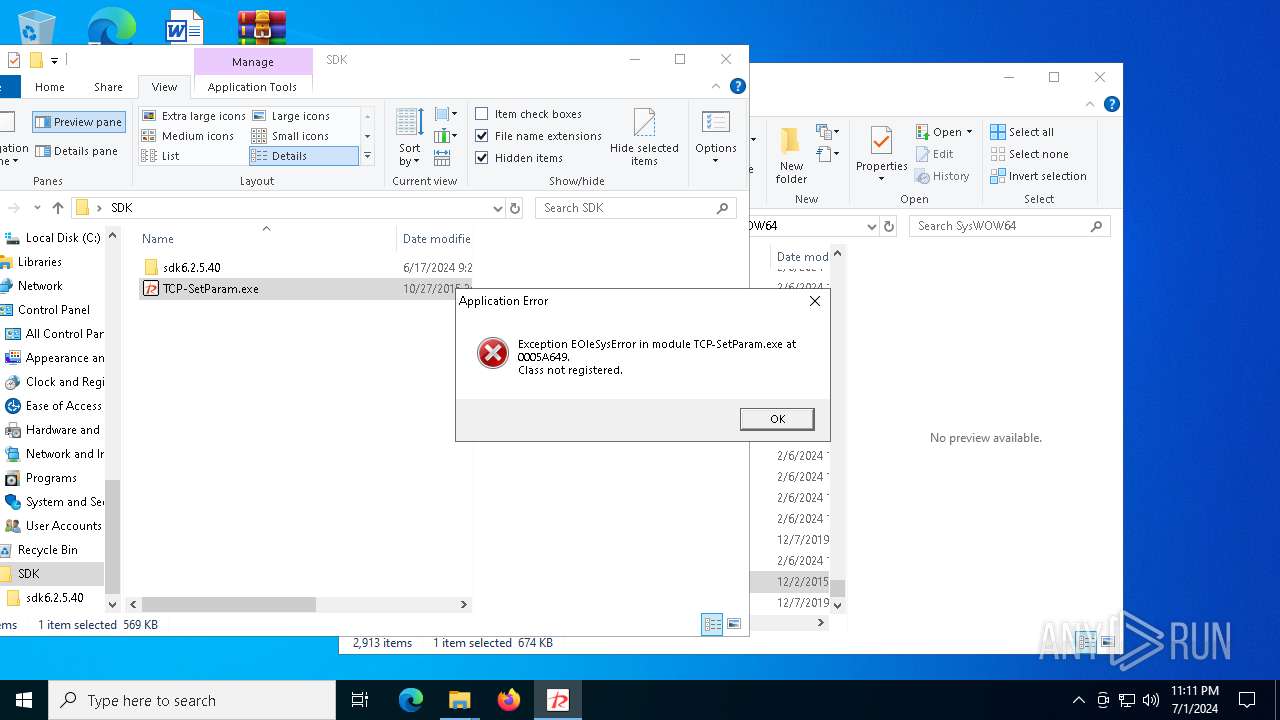
Executes application which crashes
- TCP-SetParam.exe (PID: 3532)
- TCP-SetParam.exe (PID: 4856)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 2648)
Executable content was dropped or overwritten
- dllhost.exe (PID: 4648)
- dllhost.exe (PID: 5508)
INFO
Reads the computer name
- TCP-SetParam.exe (PID: 3532)
- ShellExperienceHost.exe (PID: 2648)
- TCP-SetParam.exe (PID: 4856)
Checks supported languages
- TCP-SetParam.exe (PID: 3532)
- ShellExperienceHost.exe (PID: 2648)
- TCP-SetParam.exe (PID: 4856)
Creates files or folders in the user directory
- WerFault.exe (PID: 5060)
- WerFault.exe (PID: 3760)
Checks proxy server information
- WerFault.exe (PID: 5060)
- WerFault.exe (PID: 3760)
Reads the software policy settings
- WerFault.exe (PID: 5060)
- WerFault.exe (PID: 3760)
Manual execution by a user
- WinRAR.exe (PID: 2516)
- notepad++.exe (PID: 5968)
- cmd.exe (PID: 5956)
- TCP-SetParam.exe (PID: 4856)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2516)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 4648)
- dllhost.exe (PID: 5508)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2516)
- dllhost.exe (PID: 4648)
- dllhost.exe (PID: 5508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (31.9) |
|---|---|---|
| .scr | | | Windows screen saver (29.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (14.8) |
| .exe | | | Win32 Executable (generic) (10.1) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:03:03 10:01:51+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 479232 |
| InitializedDataSize: | 75264 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x75e78 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
162
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2112 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
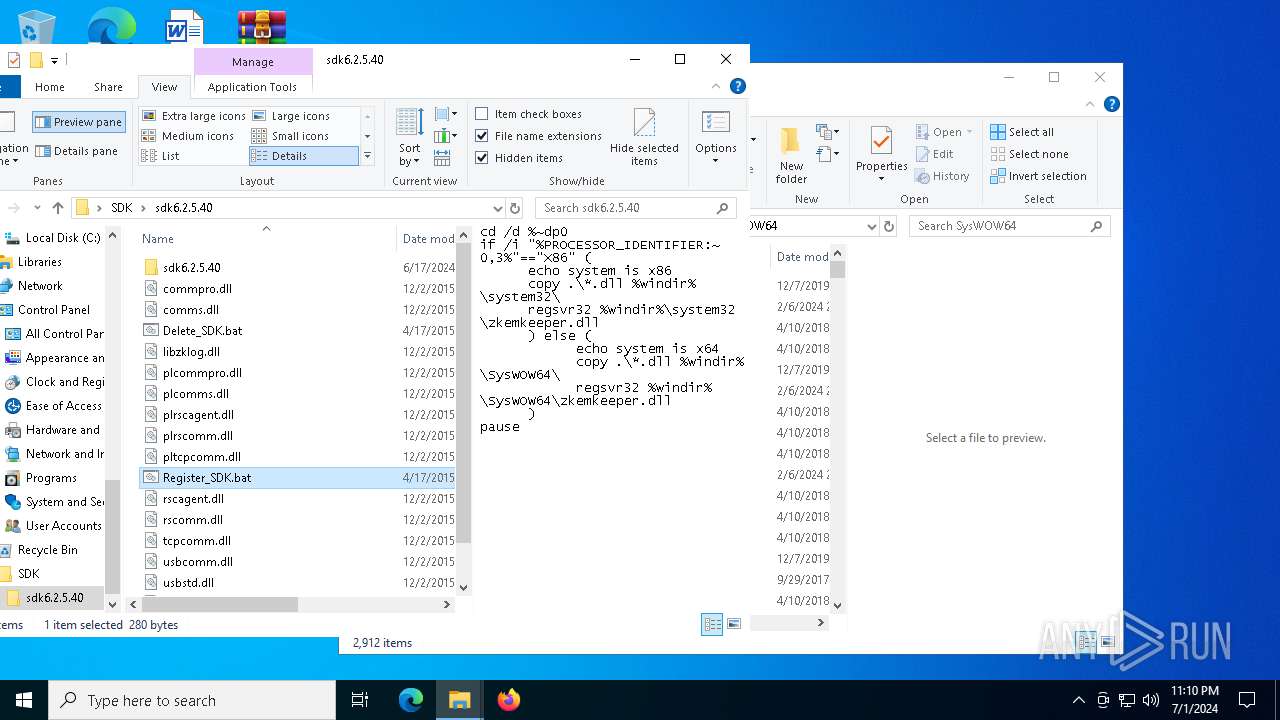
| 2140 | regsvr32 C:\WINDOWS\SysWOW64\zkemkeeper.dll | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\SDK.rar" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2648 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3532 | "C:\Users\admin\AppData\Local\Temp\TCP-SetParam.exe" | C:\Users\admin\AppData\Local\Temp\TCP-SetParam.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3720 | C:\WINDOWS\system32\prevhost.exe {914FEED8-267A-4BAA-B8AA-21E233792679} -Embedding | C:\Windows\System32\prevhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Preview Handler Surrogate Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3760 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4856 -s 704 | C:\Windows\SysWOW64\WerFault.exe | TCP-SetParam.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3948 | C:\WINDOWS\System32\rundll32.exe shell32.dll,SHCreateLocalServerRunDll {c82192ee-6cb5-4bc0-9ef0-fb818773790a} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4648 | C:\WINDOWS\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 424
Read events
12 418
Write events
6
Delete events
0
Modification events
| (PID) Process: | (2516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
18
Suspicious files
7
Text files
12
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5060 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_TCP-SetParam.exe_b922a8887e859a30f0859ea3ce963091f019a6d_1edb95ef_5d12fce8-e79d-486c-99b8-5e1aafc9366b\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5060 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD216.tmp.dmp | dmp | |
MD5:B53EA22558A4688F66821A824536FECC | SHA256:4F3386ACAFD260A32DB2A4DFF8E44EE9F9AC38F56F046B8FF9D5B5C106E3F80F | |||
| 5060 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:979F91388D4DF2F2D68497400C9830DD | SHA256:A9F27E26AA818BC97449D30D5707254EDCA571D21D36B4576C7CD9A56FB18BC5 | |||
| 5060 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD738.tmp.WERInternalMetadata.xml | xml | |
MD5:AF86A2BAFA6B62F880BE0CEF2D7F0E96 | SHA256:38D1085FAB9F326EA6094BB5824F940EBED1BA5FB6C6008381C8E325B5537BAA | |||
| 5060 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:40B1E9062BD6100D8770D6149715E195 | SHA256:DF3A7390BA08E112D32361CBB8664B8B2341F4419758CB1A89B18D91CD0AC7EC | |||
| 5060 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:CBA2426F2AAFE31899569ACE05E89796 | SHA256:A465FEBE8A024E3CDB548A3731B2EA60C7B2919E941A24B9A42890B2B039B85A | |||
| 5060 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD787.tmp.xml | xml | |
MD5:10703ACAE17227F52DEE5F885EC9EA91 | SHA256:73B849EE4A126425A00B6F7FACACF895872EBC9D8A943DB9EC8331613E3FF3ED | |||
| 5060 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\TCP-SetParam.exe.3532.dmp | binary | |
MD5:C251512B65E63C8F08FFD5BDF46540AA | SHA256:D31FE20E72519A135FE19E6F1E40F8DD5BEFECA599037EF95AD1E9E0310C878C | |||
| 5060 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:D634A2D5A3D9AABADE62611D1D4A90D9 | SHA256:4D11F6C5A946AD7FB22BCA36EBC14FFAD809730F68CEB77601A5FB732CFDFBFA | |||
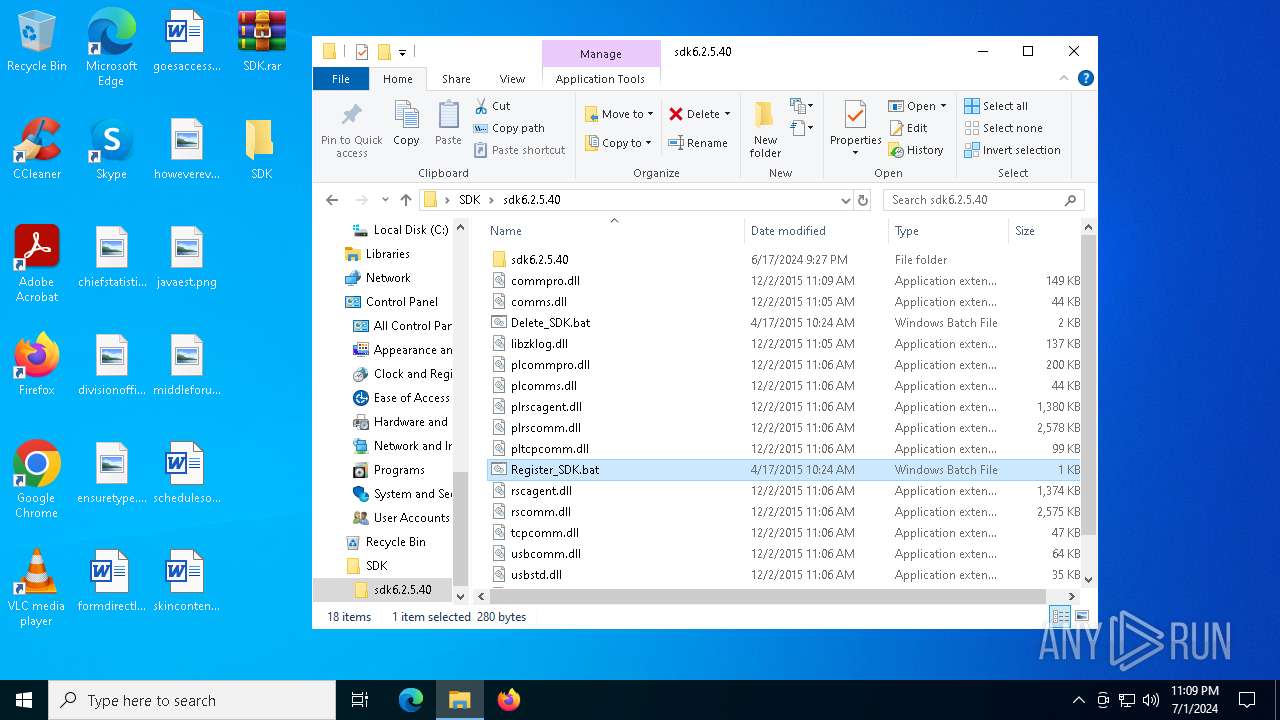
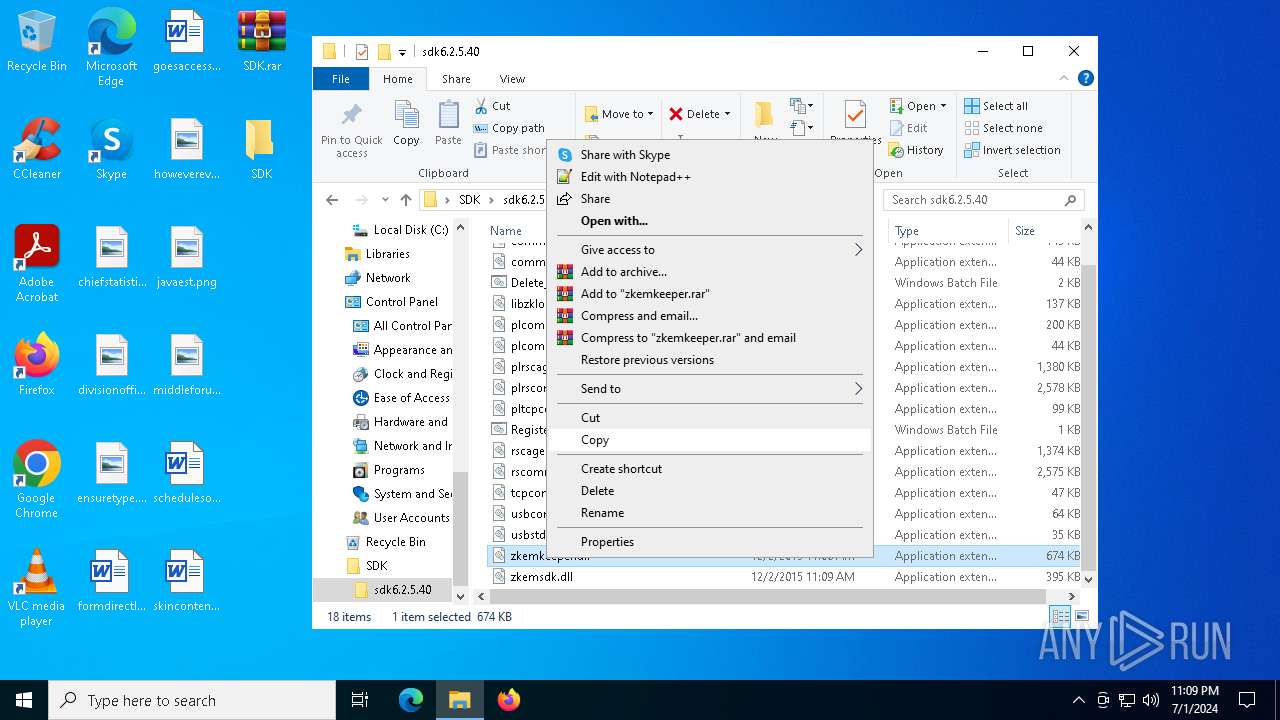
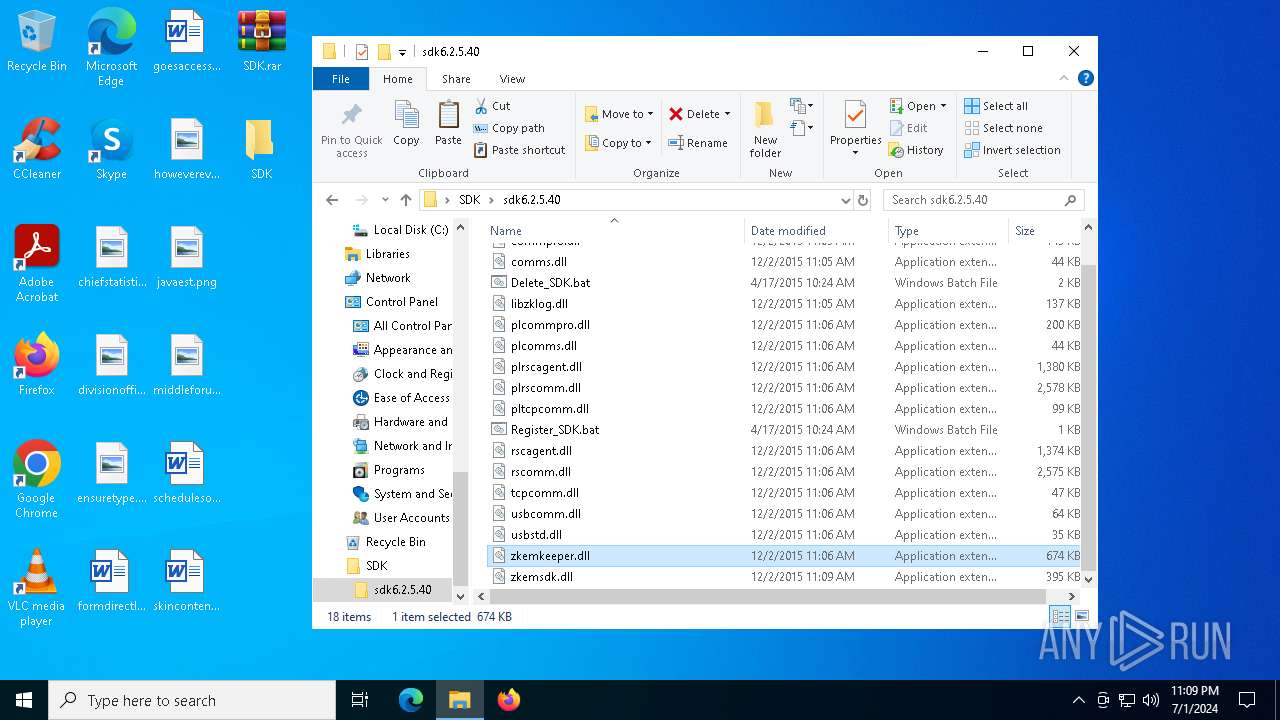
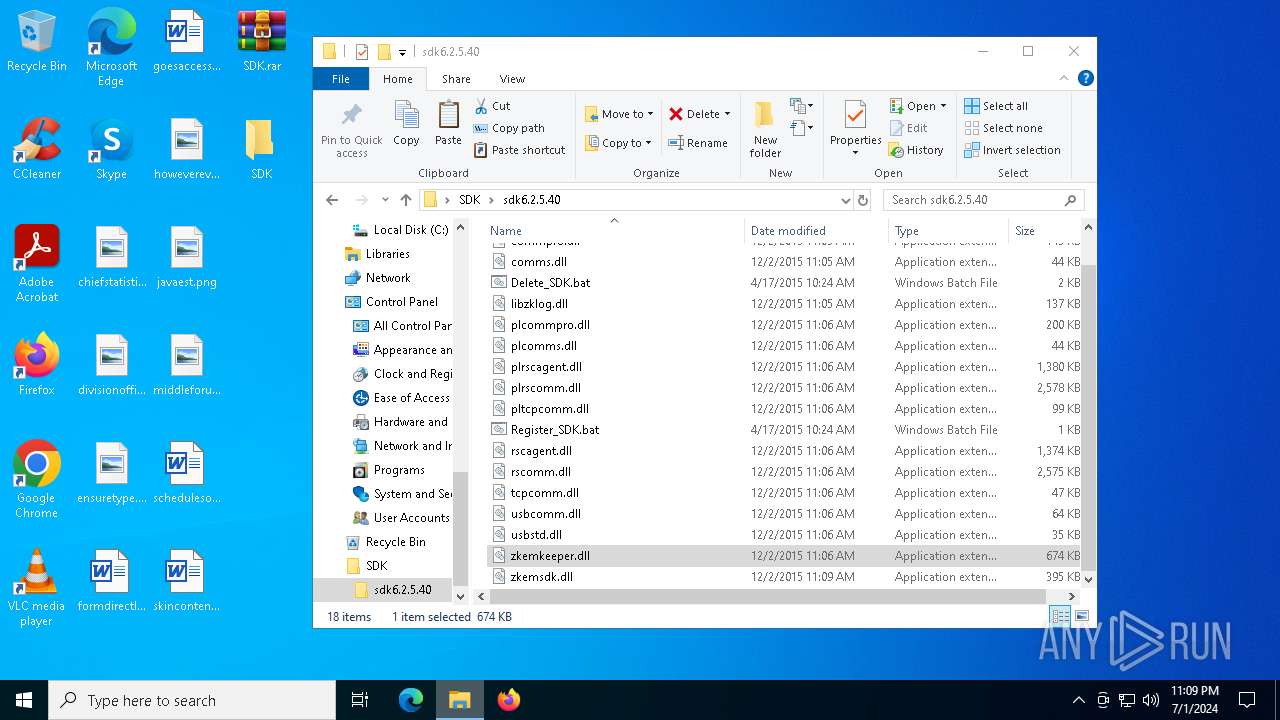
| 2516 | WinRAR.exe | C:\Users\admin\Desktop\SDK\sdk6.2.5.40\plcomms.dll | executable | |
MD5:B91A62F693B819BE25EDB7E25C482697 | SHA256:7C9329DA88943F704BD77A8E7E1924700ED45D0303542659705F50D92132F8BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
69
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5060 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5060 | WerFault.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
2872 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2872 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
2360 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2896 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
8 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
8 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3872 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3580 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2872 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5060 | WerFault.exe | 13.89.179.12:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5060 | WerFault.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5060 | WerFault.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4656 | SearchApp.exe | 104.126.37.162:443 | — | Akamai International B.V. | DE | unknown |
1544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|