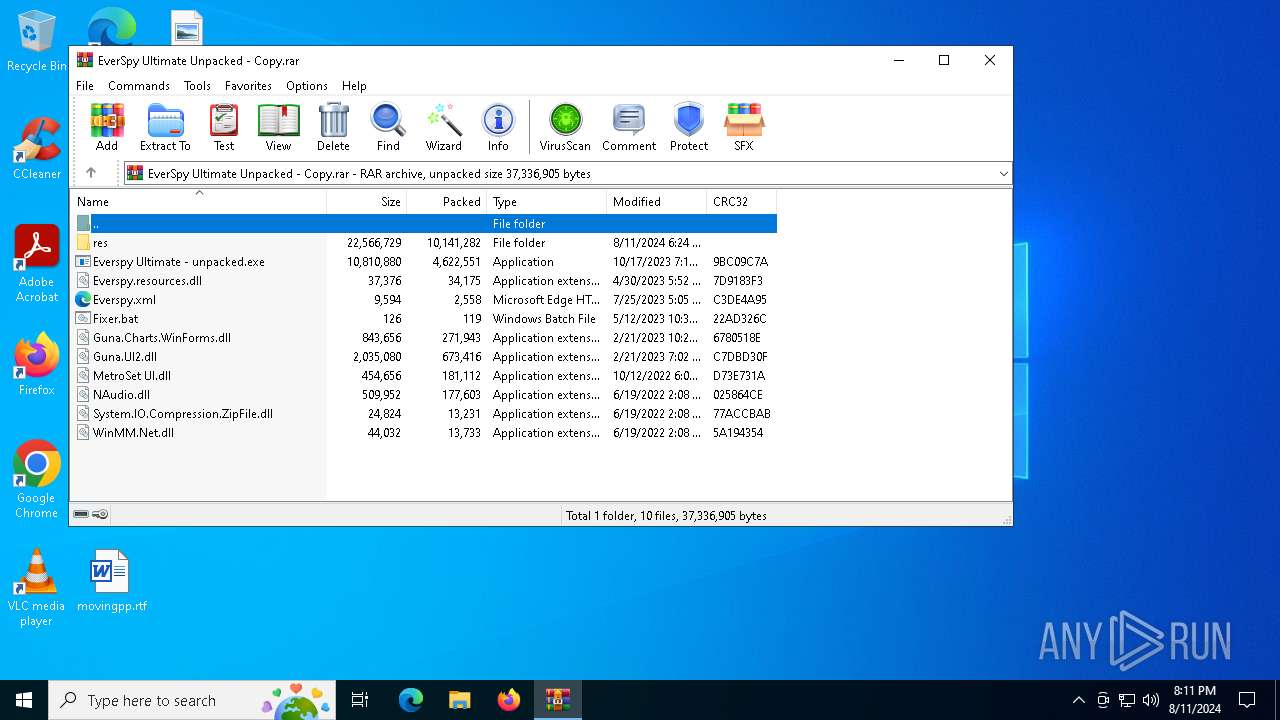
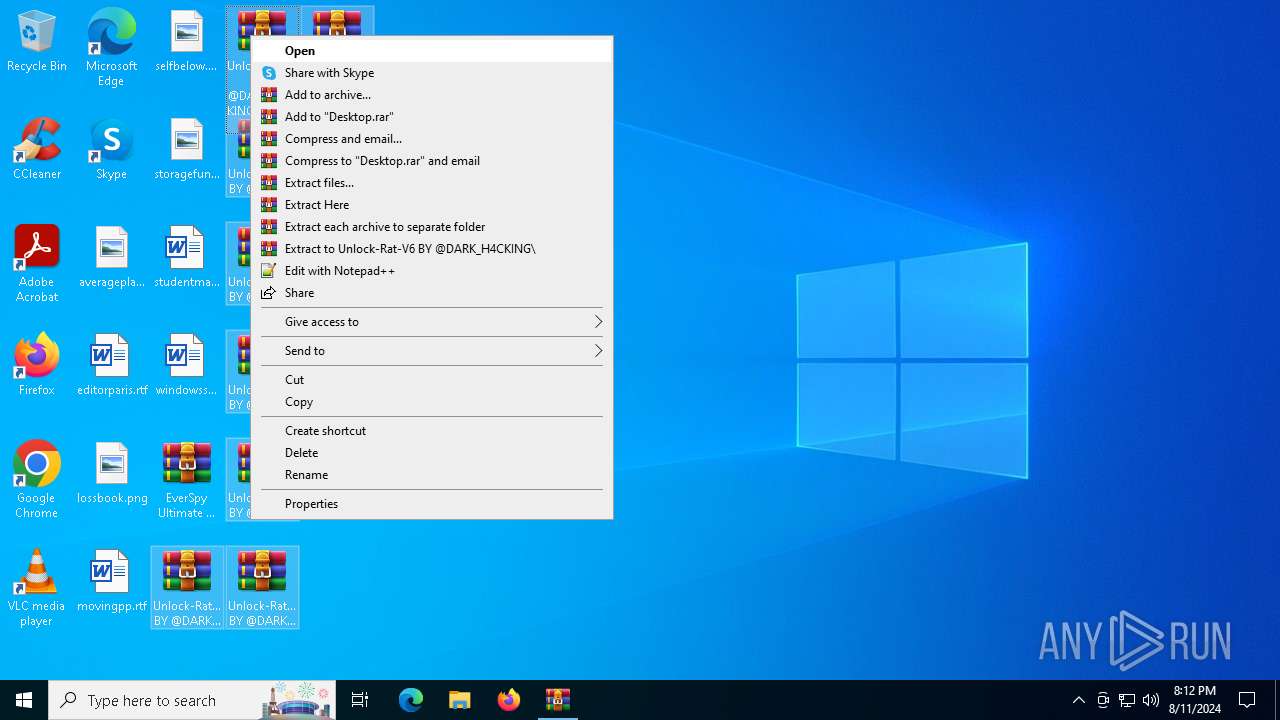
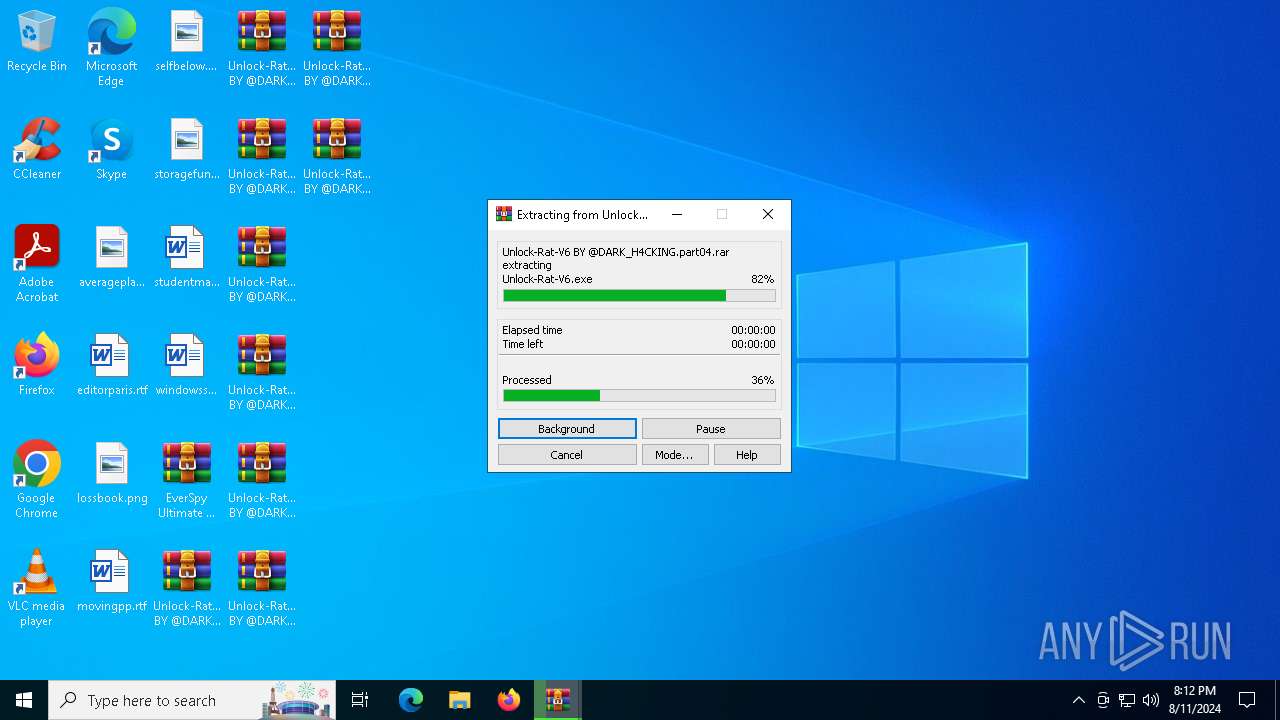
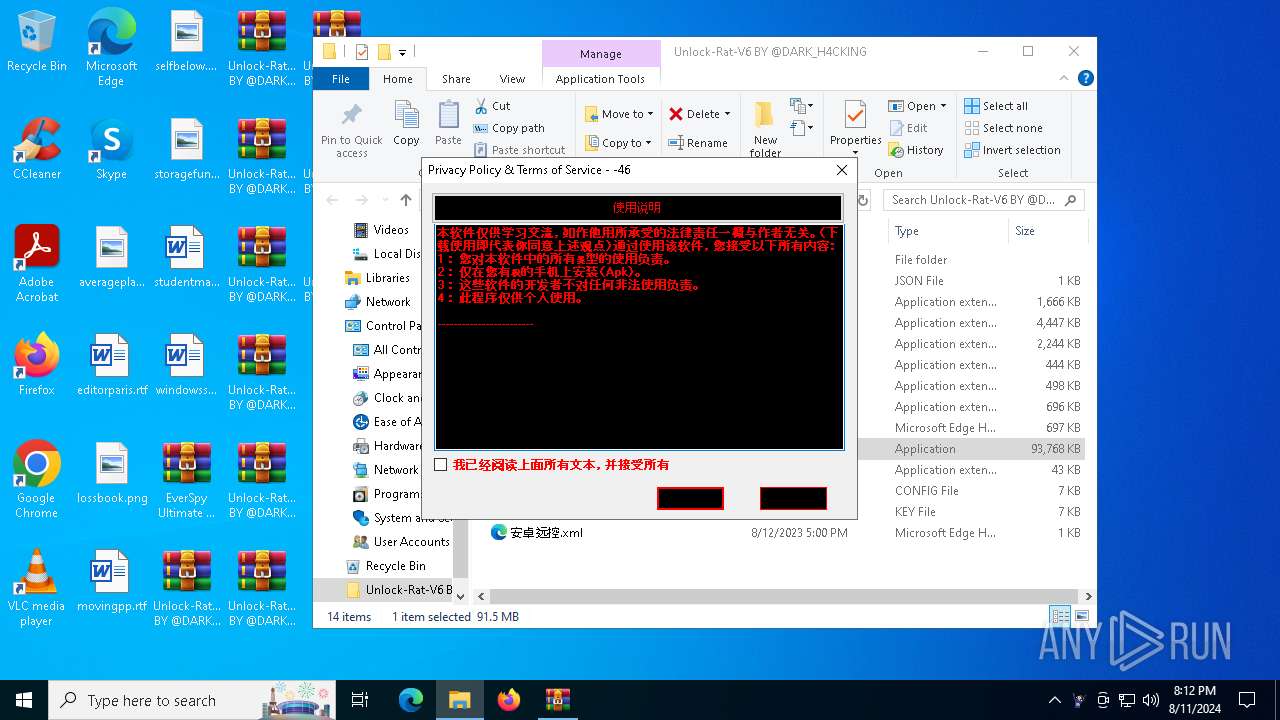
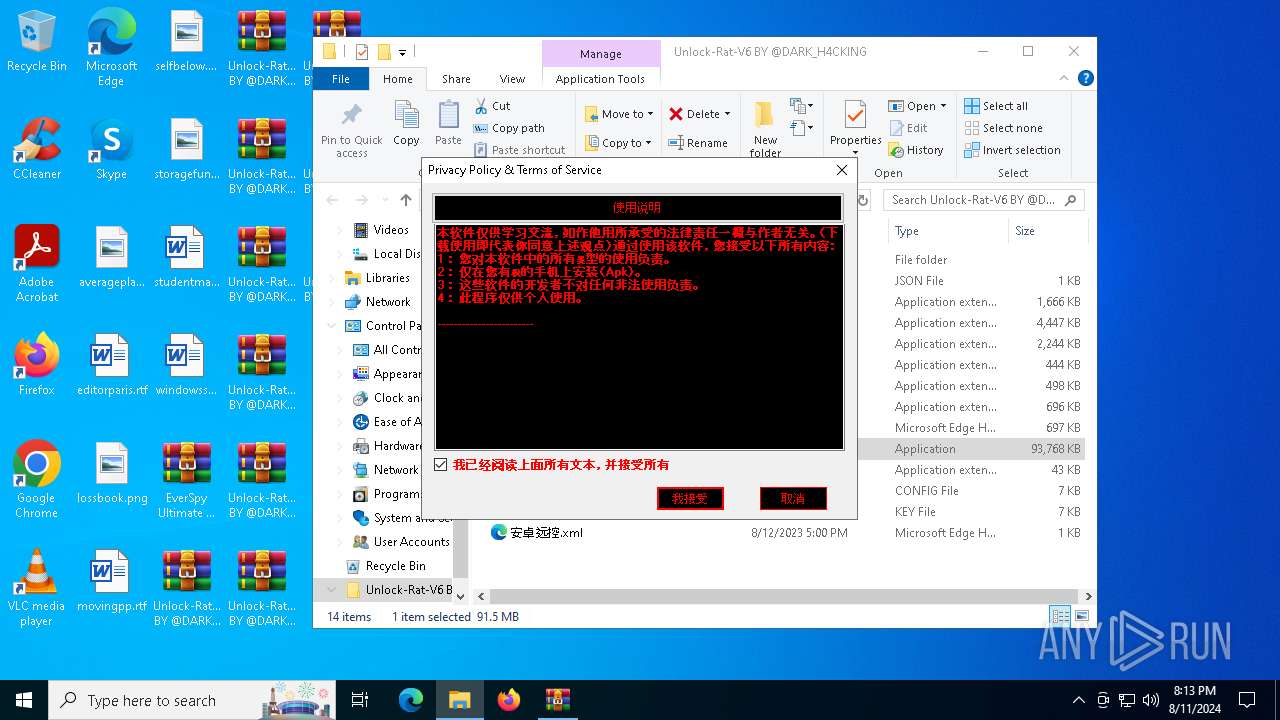
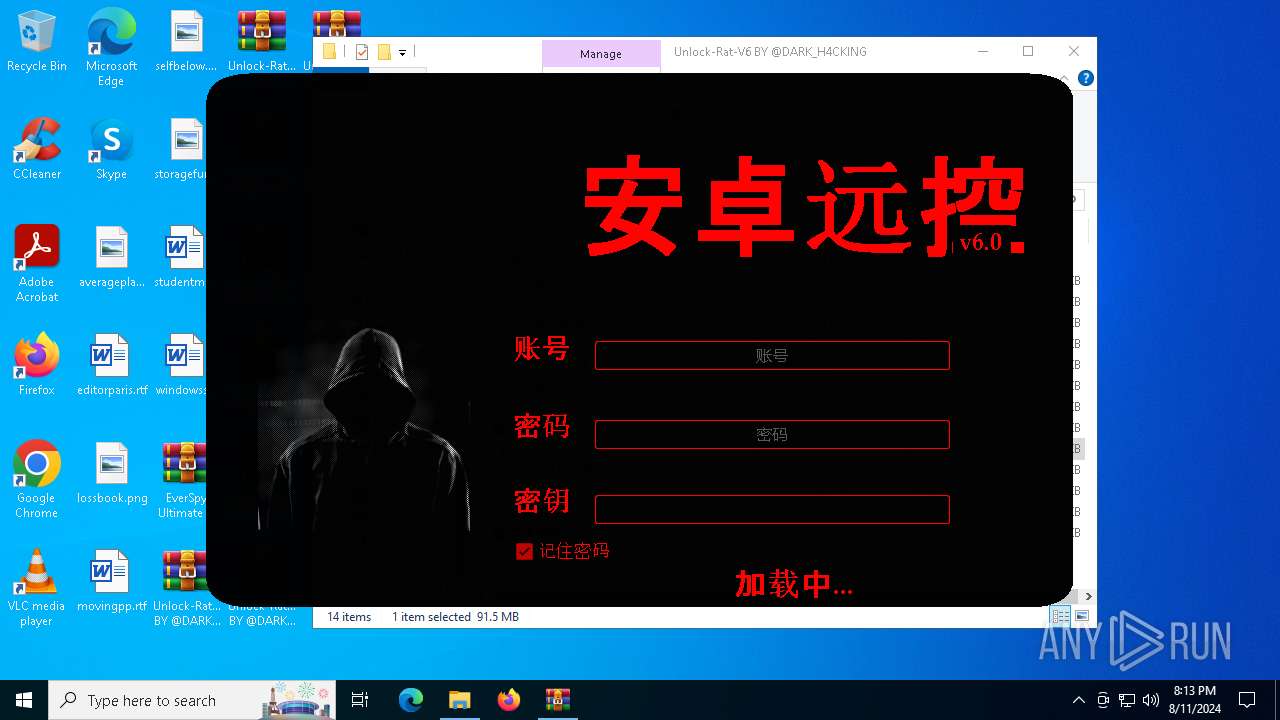
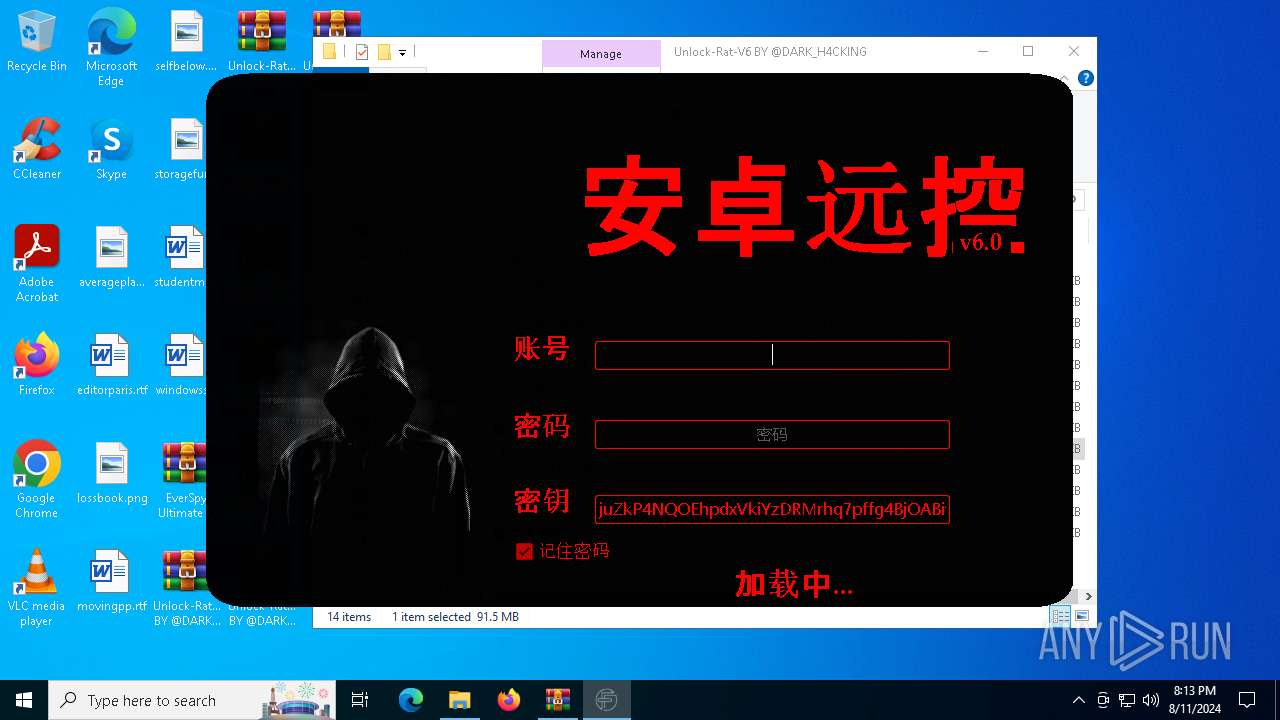
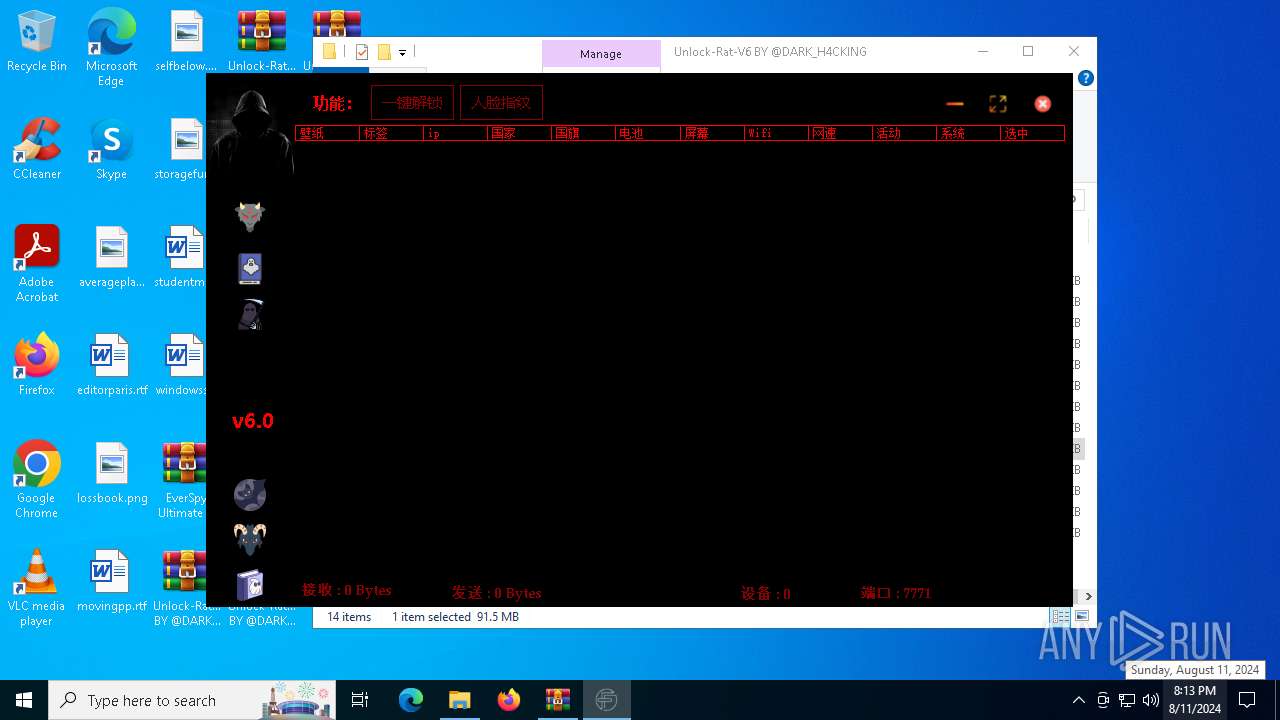
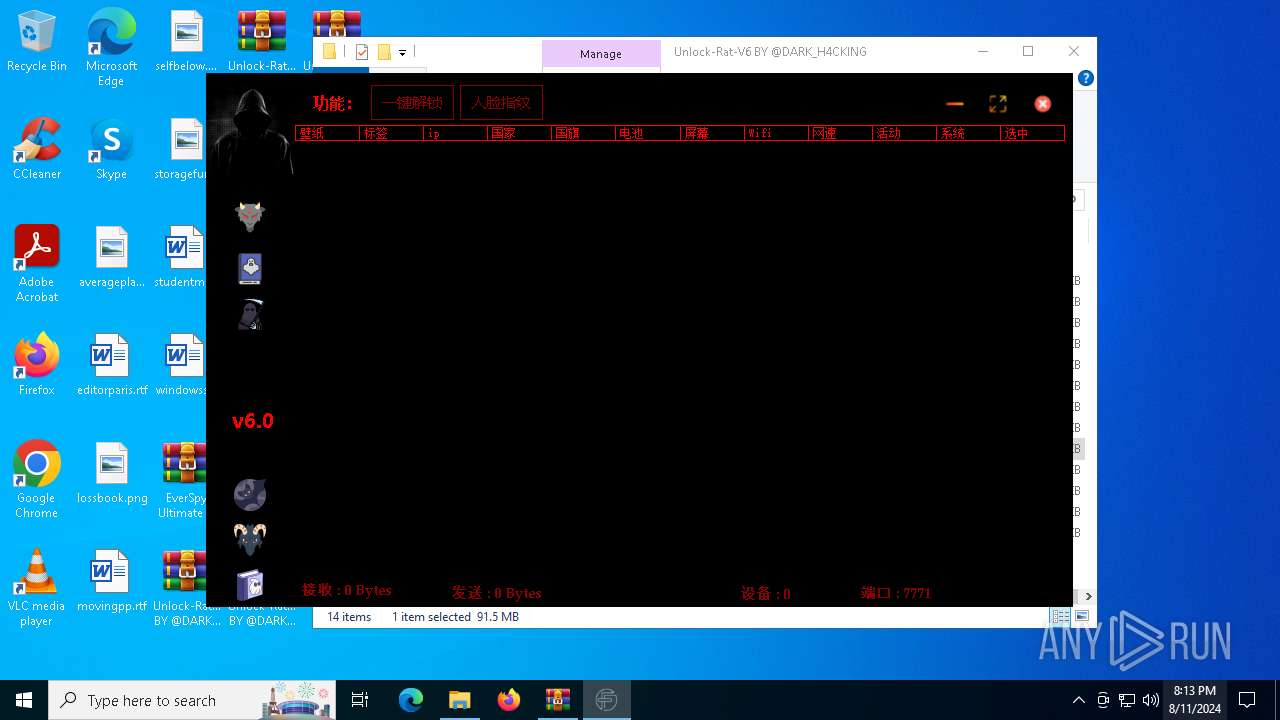
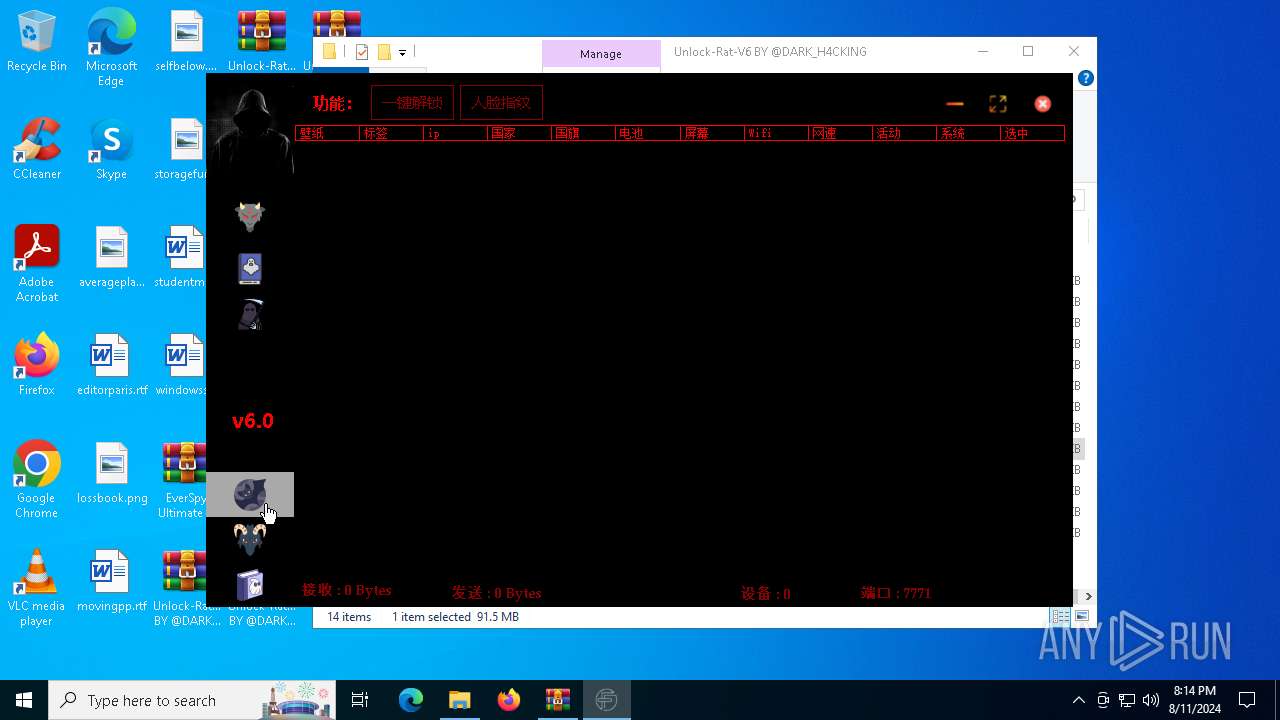
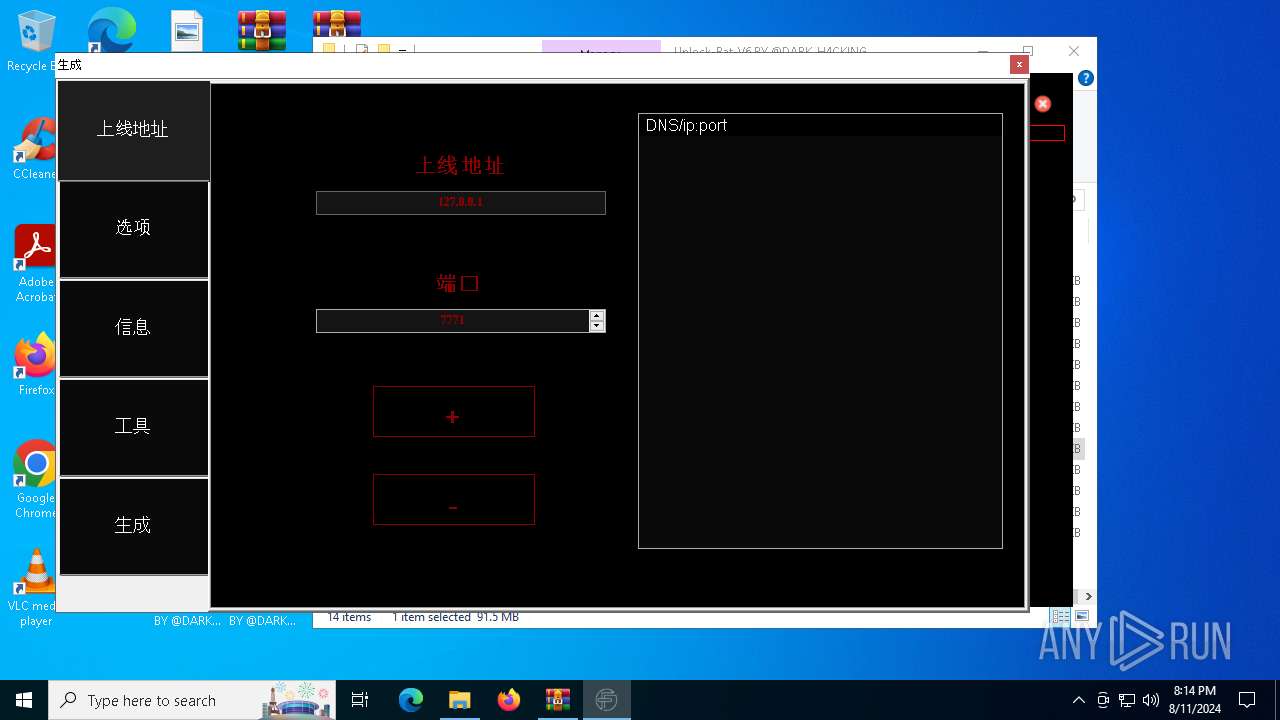
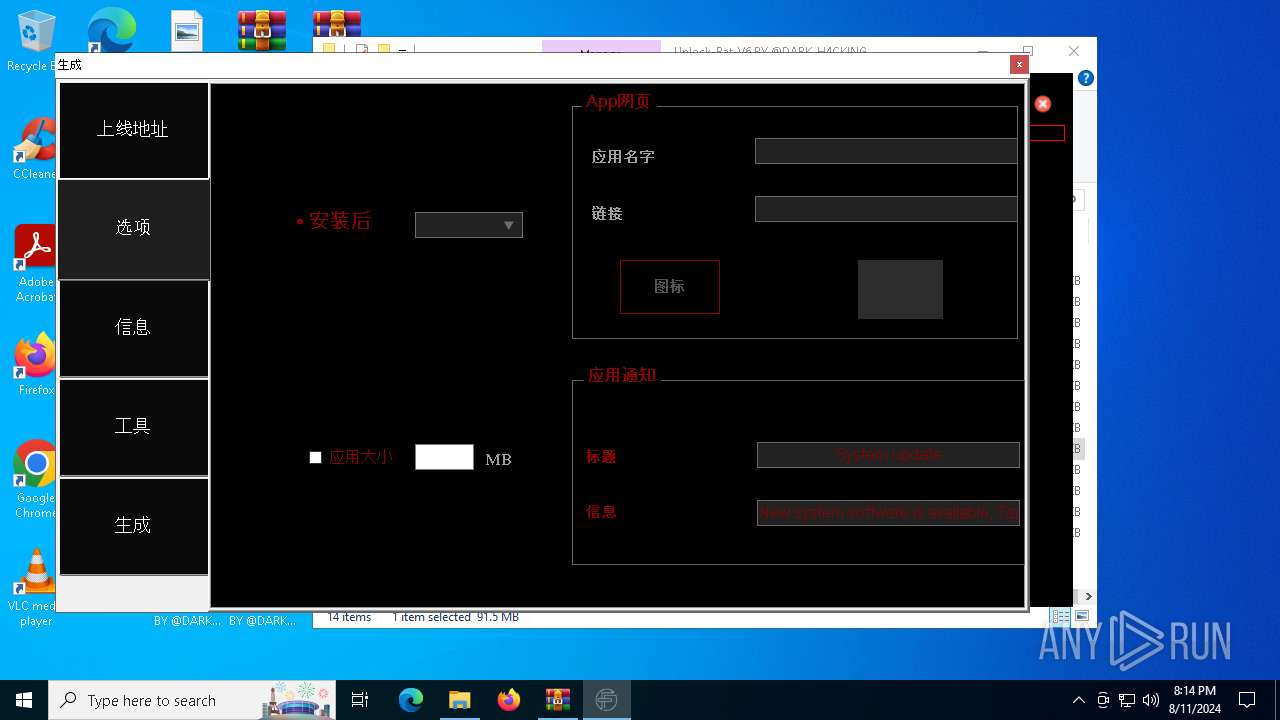
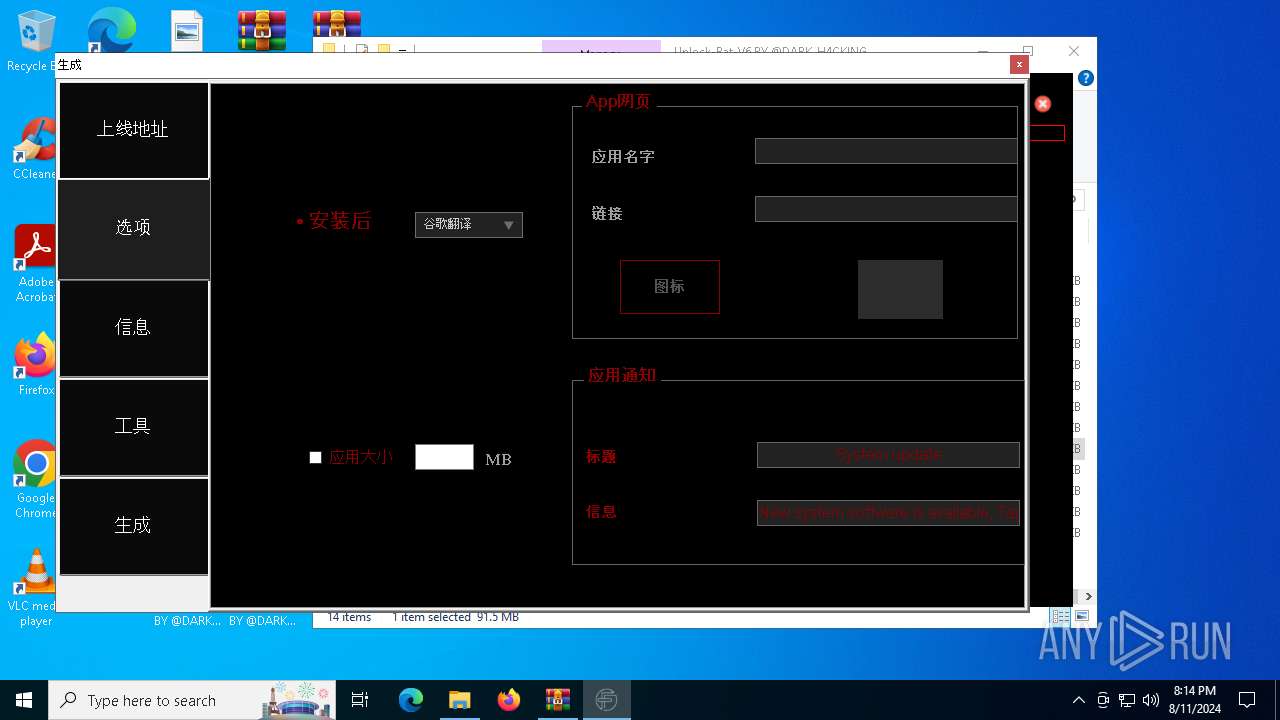
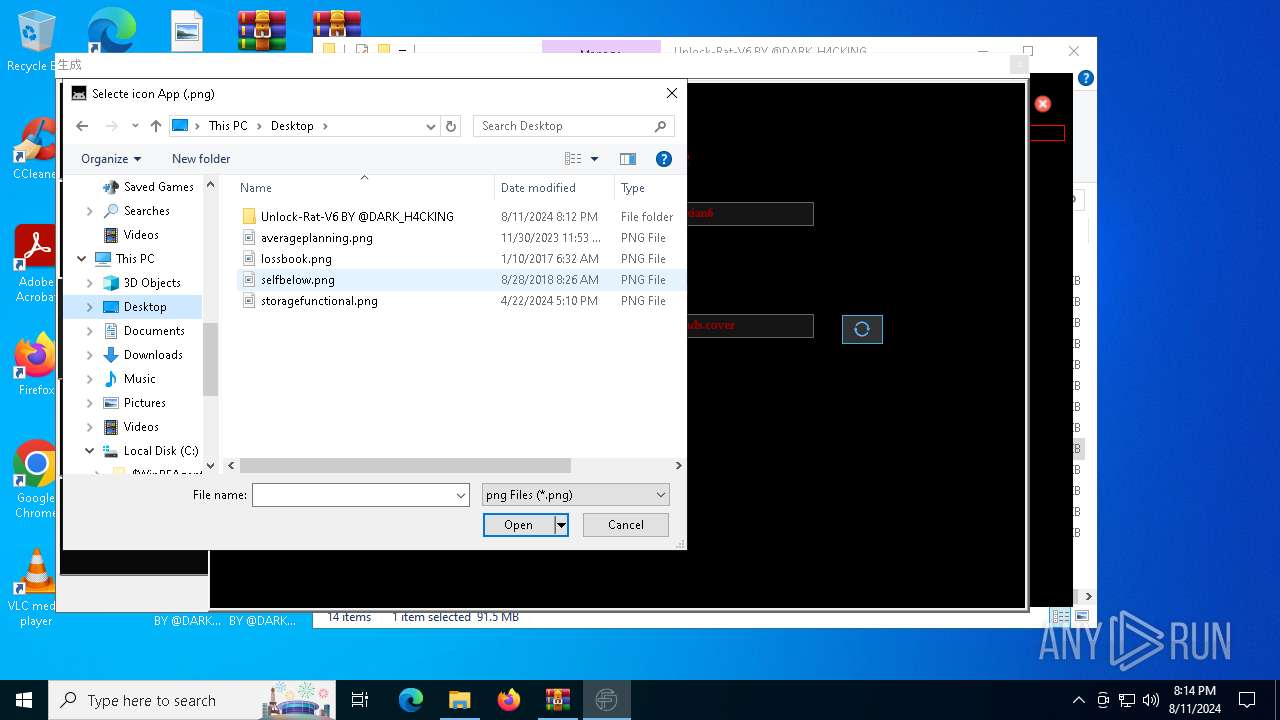
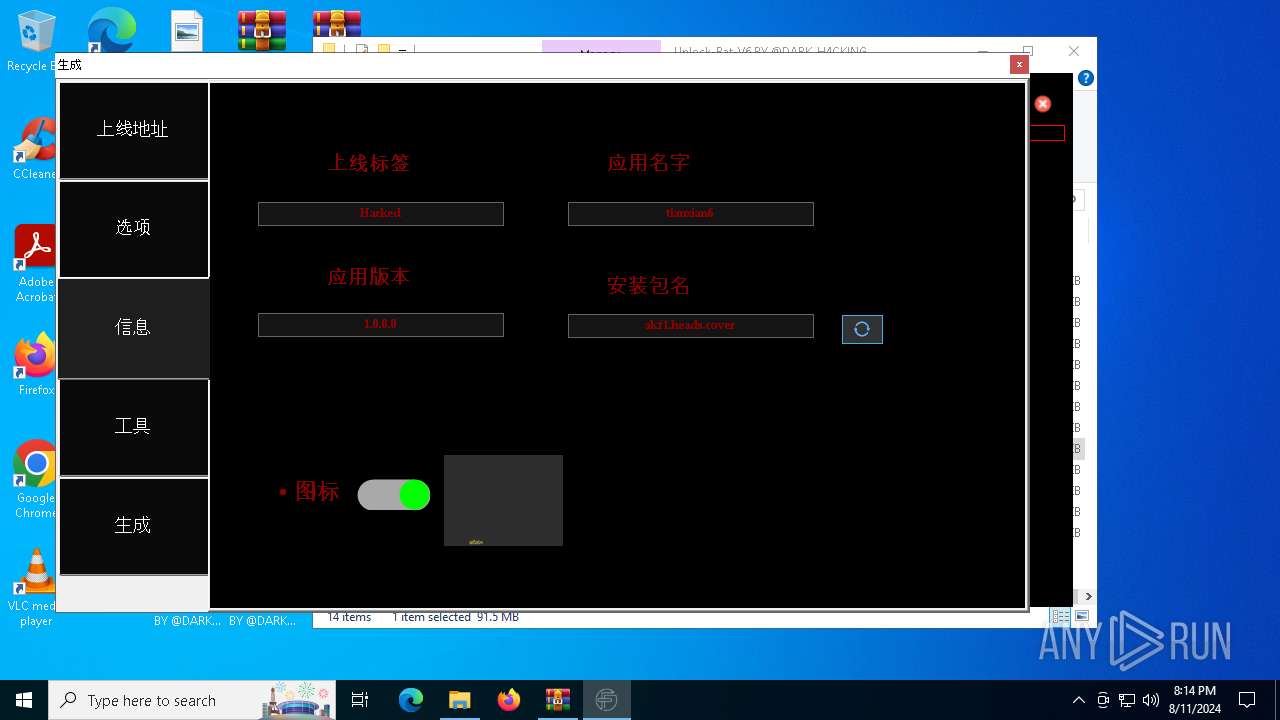
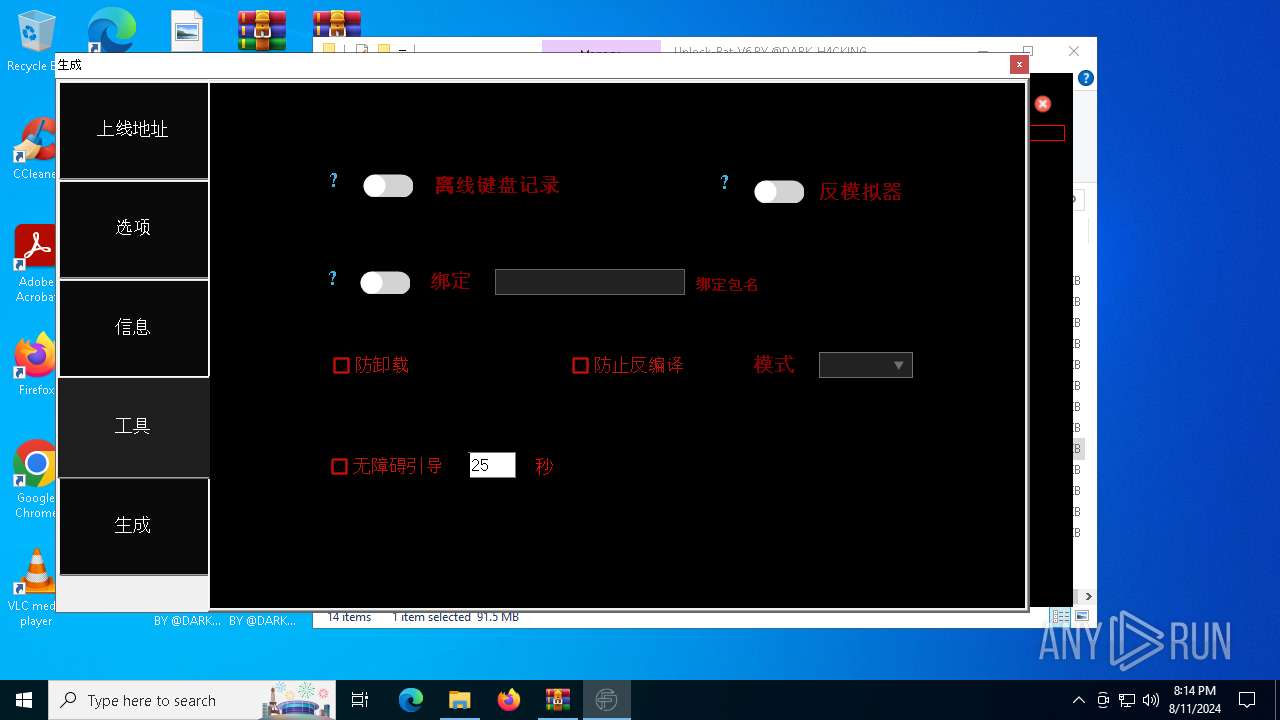
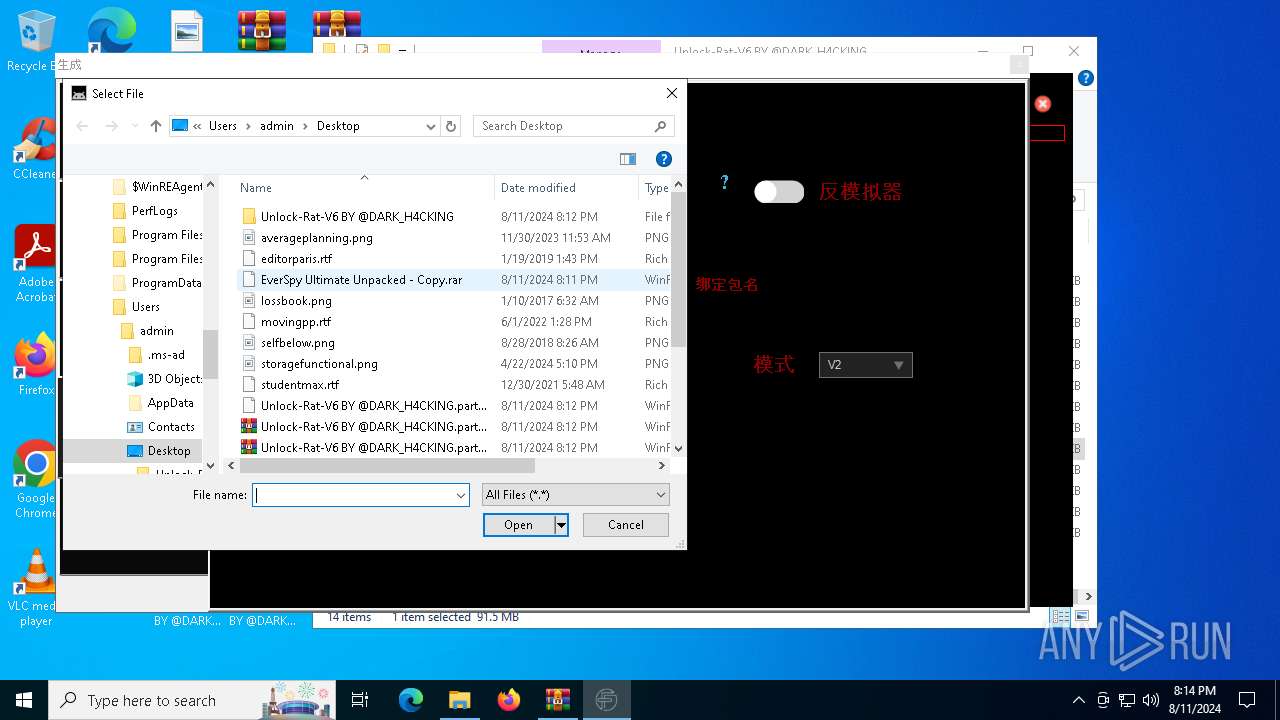
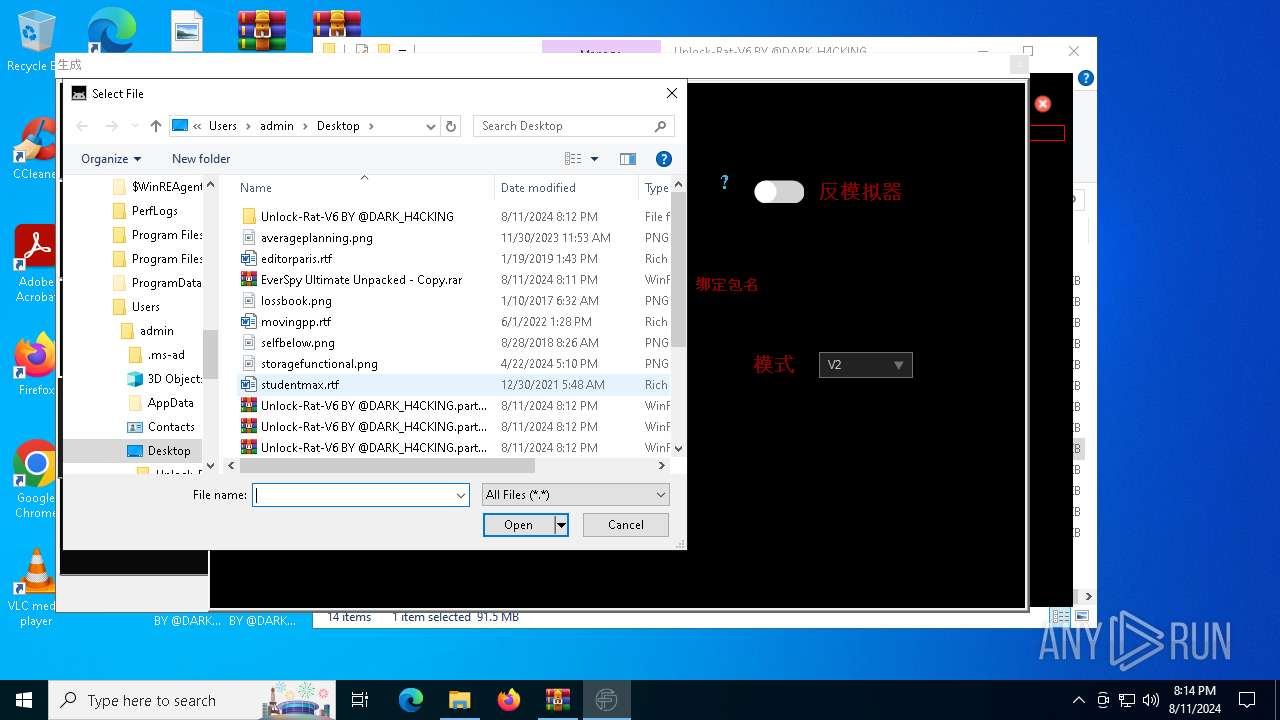
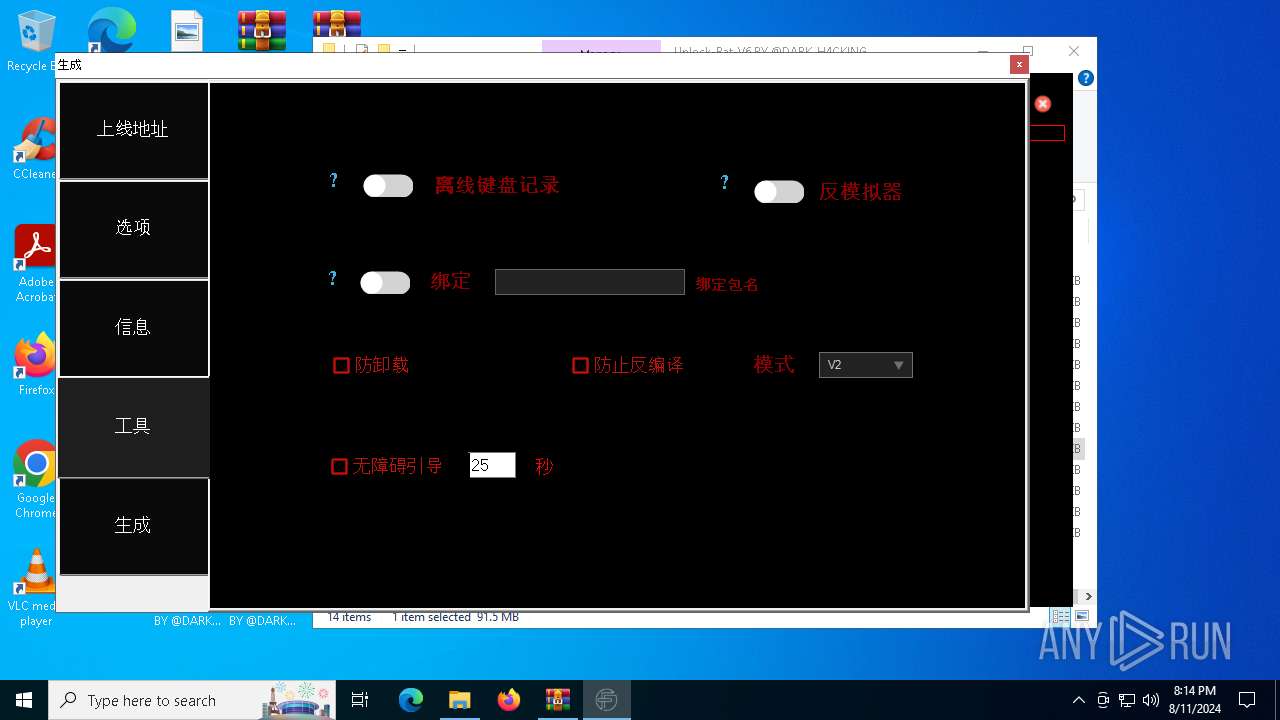
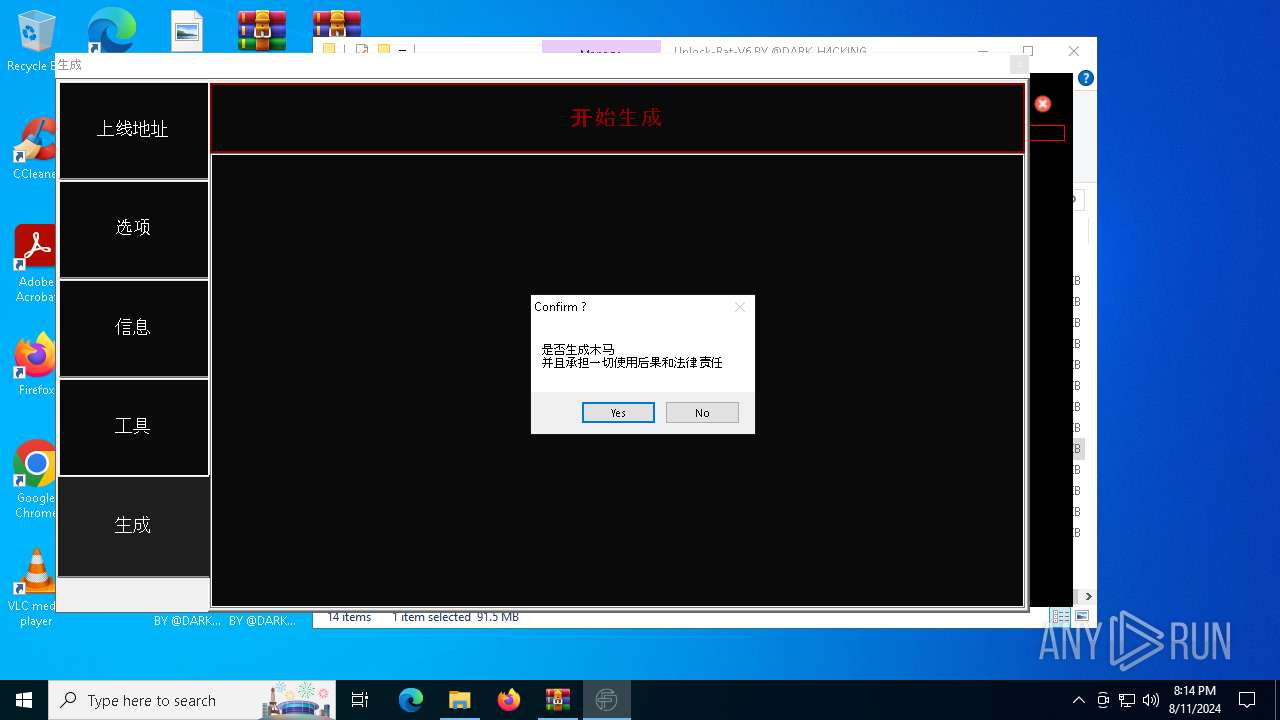
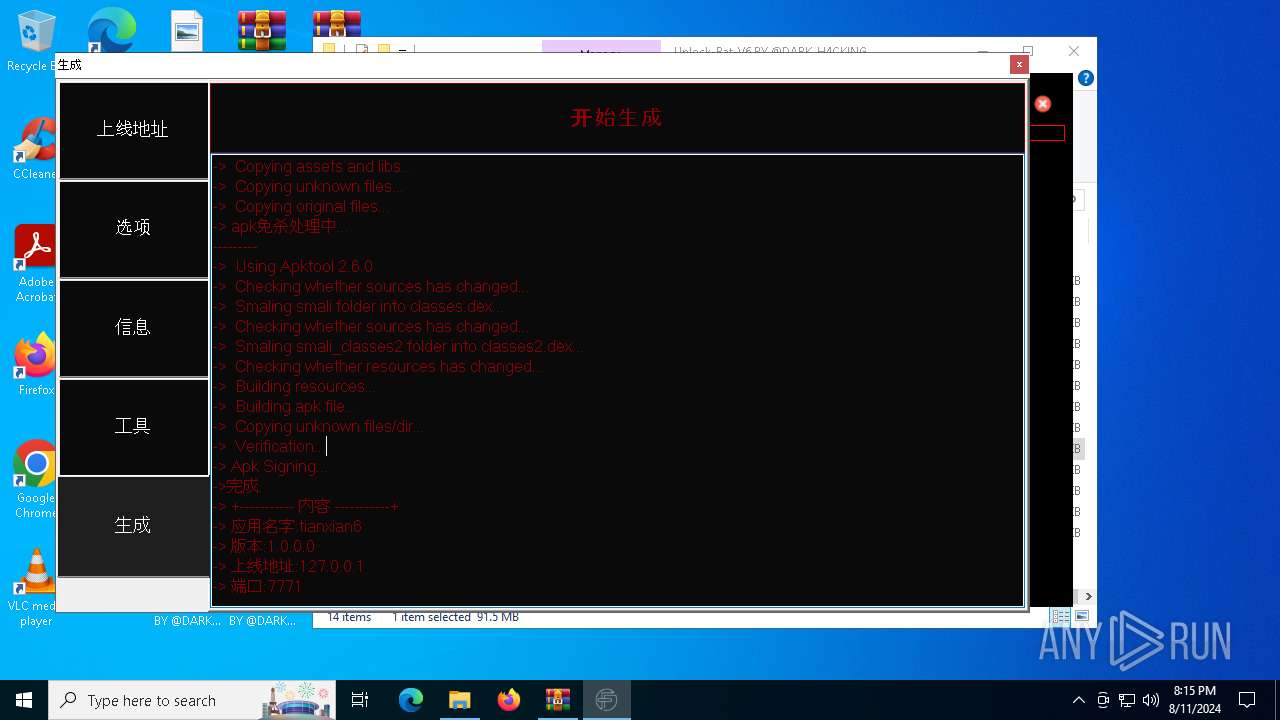
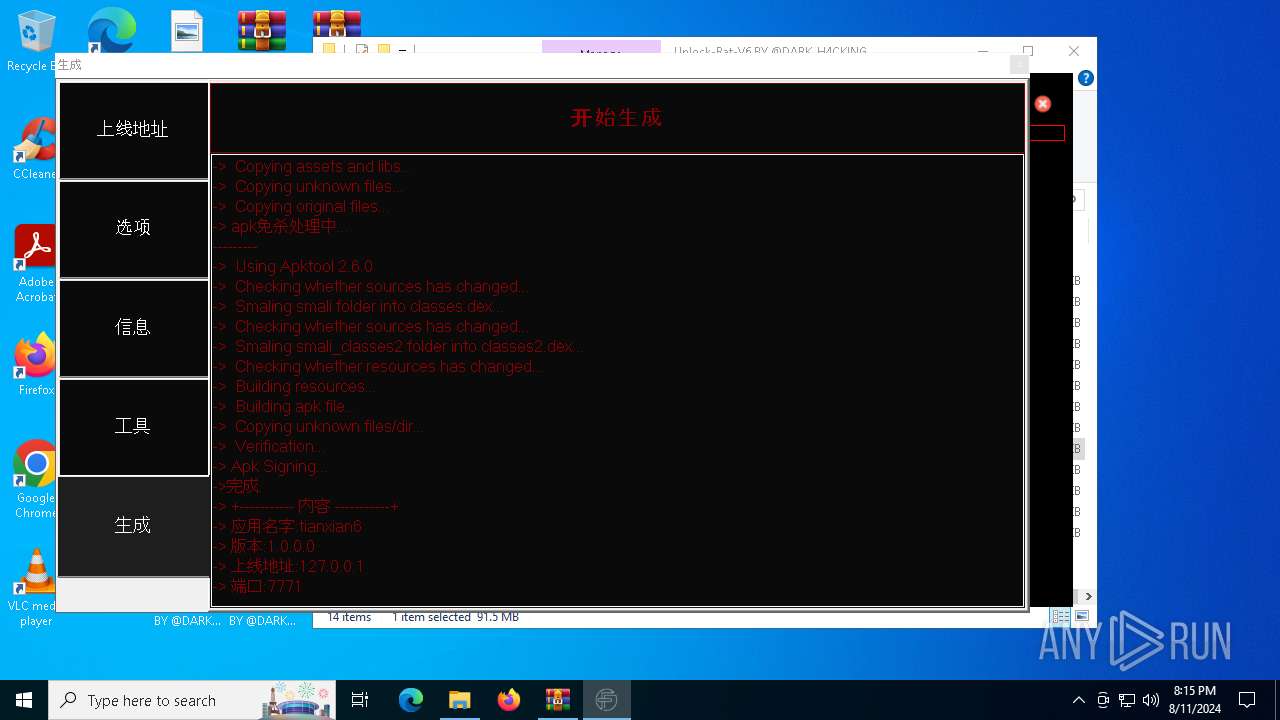
| File name: | EverSpy Ultimate Unpacked - Copy.rar |
| Full analysis: | https://app.any.run/tasks/abd51472-e279-4040-ac79-6f95a3975b2d |
| Verdict: | Malicious activity |
| Analysis date: | August 11, 2024, 20:11:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7CEA74158FFA610149B5B76B9CE29E5D |
| SHA1: | BD5BBD55F354B271015BE7B971DD3510064EE709 |
| SHA256: | 04D5C7486CF4962F52AC9173987C4AE53084A9329797F9E872D701943AF4A022 |
| SSDEEP: | 98304:/Ynz1/Hgu+4BNfWxWLFDou3biToRnoJF5j4GcvIhXWHhC320BIwXx3dyu4SJwbsk:DcFS50oBk3JJ7Rs63kuf2fN8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
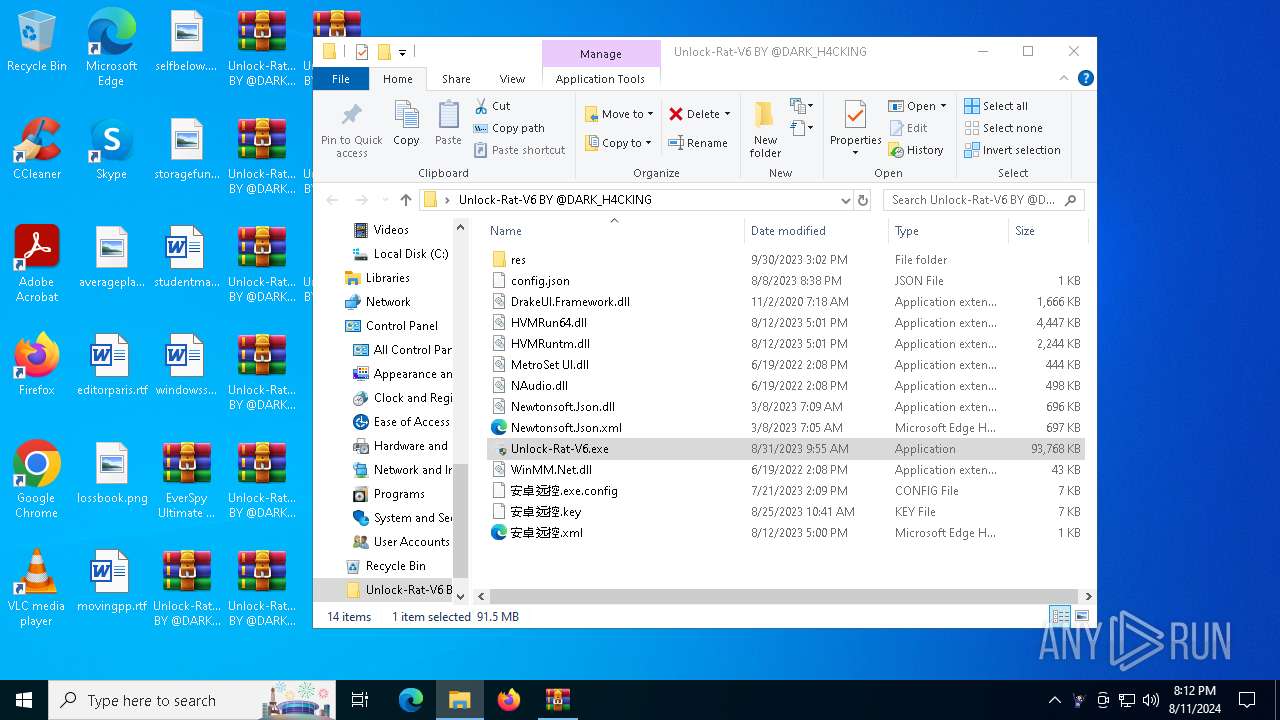
- Unlock-Rat-V6.exe (PID: 6928)
Starts CMD.EXE for commands execution
- Unlock-Rat-V6.exe (PID: 6928)
Creates file in the systems drive root
- Unlock-Rat-V6.exe (PID: 6928)
Executable content was dropped or overwritten
- java.exe (PID: 2212)
- Unlock-Rat-V6.exe (PID: 6928)
Drops the executable file immediately after the start
- java.exe (PID: 2212)
- Unlock-Rat-V6.exe (PID: 6928)
Starts application with an unusual extension
- java.exe (PID: 2212)
Reads security settings of Internet Explorer
- Unlock-Rat-V6.exe (PID: 6928)
Process drops legitimate windows executable
- Unlock-Rat-V6.exe (PID: 6928)
INFO
Manual execution by a user
- WinRAR.exe (PID: 6420)
- Unlock-Rat-V6.exe (PID: 1164)
- Unlock-Rat-V6.exe (PID: 6928)
Checks supported languages
- Unlock-Rat-V6.exe (PID: 6928)
- zipalign.exe (PID: 1432)
- java.exe (PID: 2212)
- java.exe (PID: 1984)
- brut_util_Jar_41112474085867589873911591747991064364.tmp (PID: 6400)
- java.exe (PID: 2852)
- java.exe (PID: 6484)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6420)
Create files in a temporary directory
- java.exe (PID: 6484)
- java.exe (PID: 2852)
- java.exe (PID: 2212)
- brut_util_Jar_41112474085867589873911591747991064364.tmp (PID: 6400)
- java.exe (PID: 1984)
Creates files or folders in the user directory
- java.exe (PID: 2852)
- Unlock-Rat-V6.exe (PID: 6928)
Reads the machine GUID from the registry
- Unlock-Rat-V6.exe (PID: 6928)
- java.exe (PID: 2852)
- java.exe (PID: 2212)
- java.exe (PID: 1984)
Reads the computer name
- Unlock-Rat-V6.exe (PID: 6928)
- java.exe (PID: 2212)
- java.exe (PID: 2852)
- java.exe (PID: 1984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
146
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
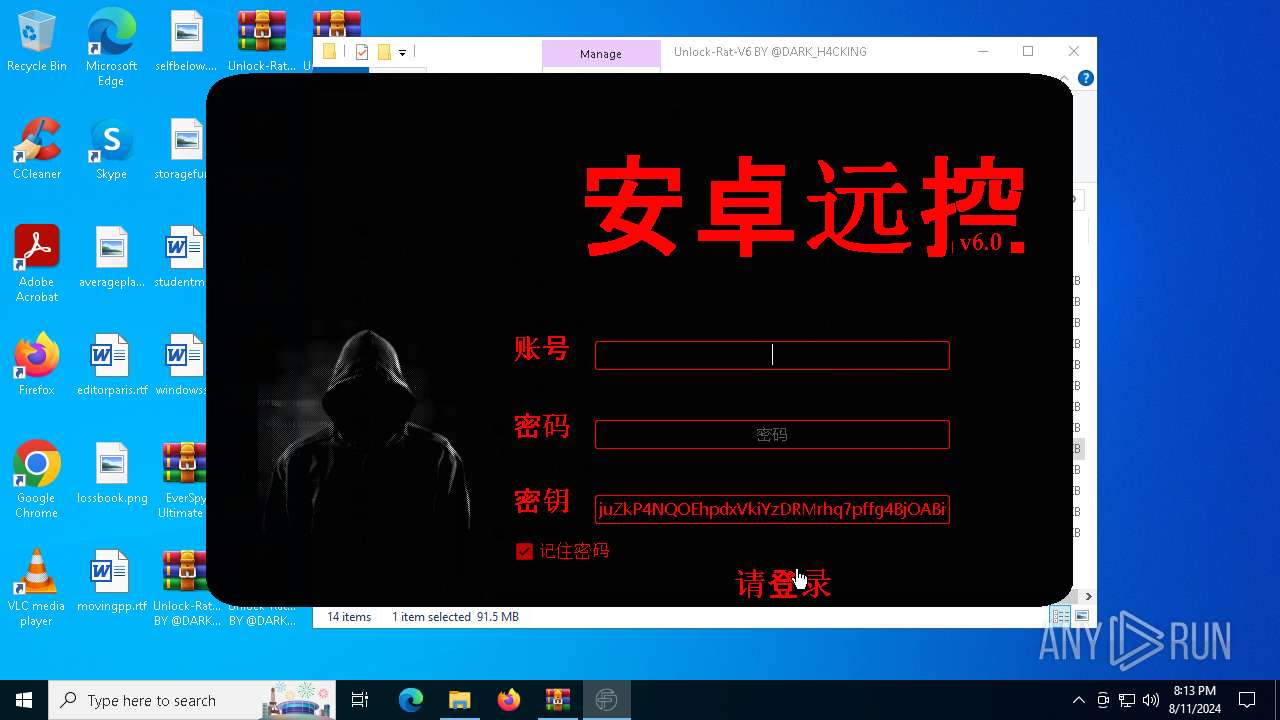
| 1164 | "C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\Unlock-Rat-V6.exe" | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\Unlock-Rat-V6.exe | — | explorer.exe | |||||||||||
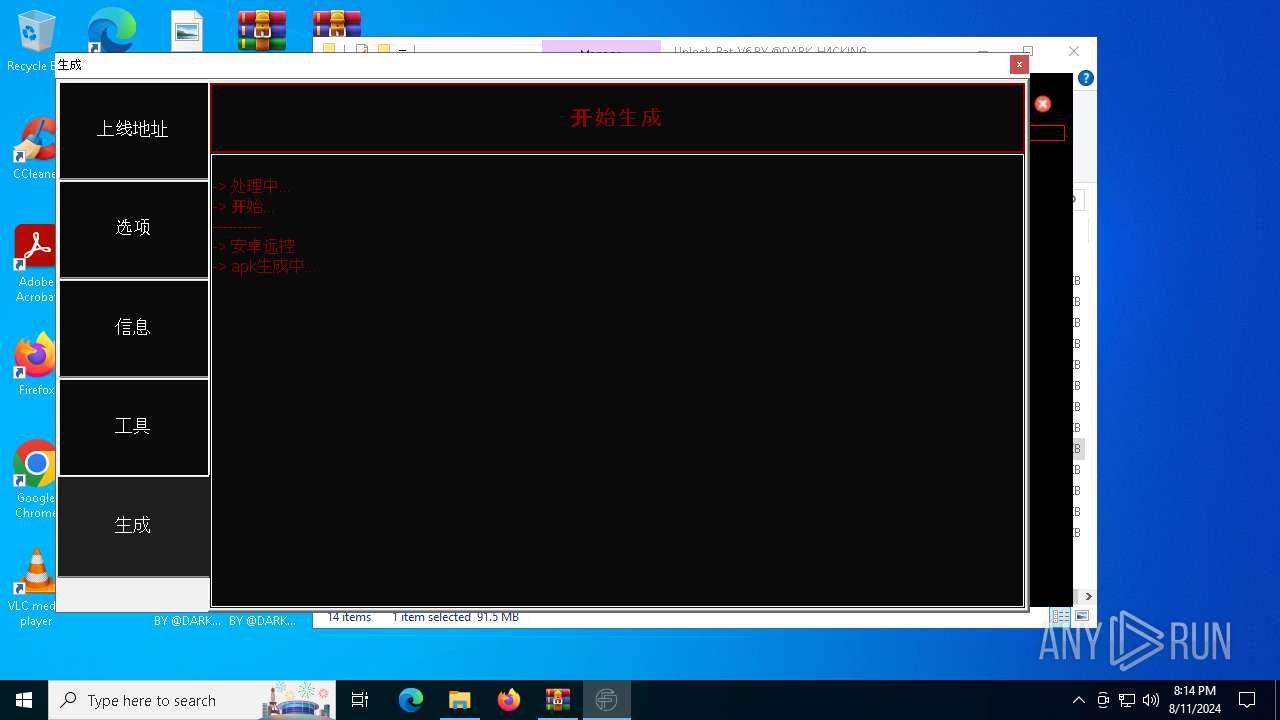
User: admin Company: 安卓远控 Integrity Level: MEDIUM Description: 安卓远控 Exit code: 3221226540 Version: 6.0 Modules
| |||||||||||||||
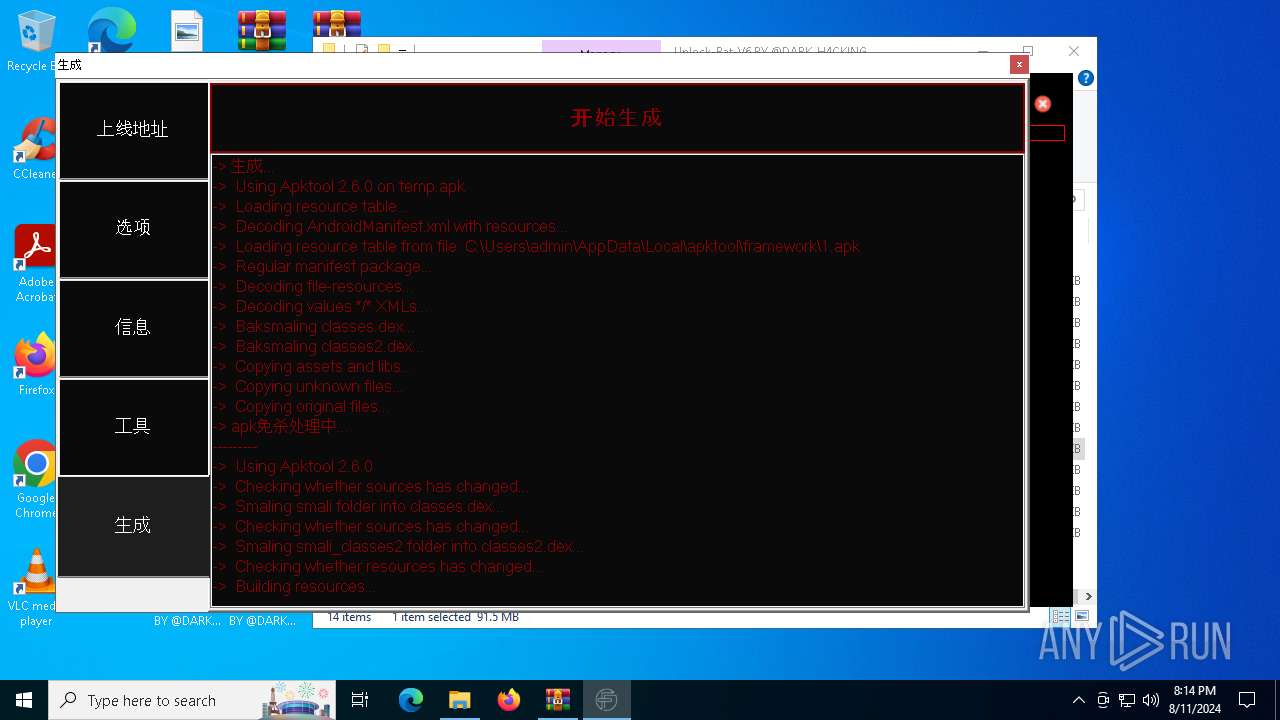
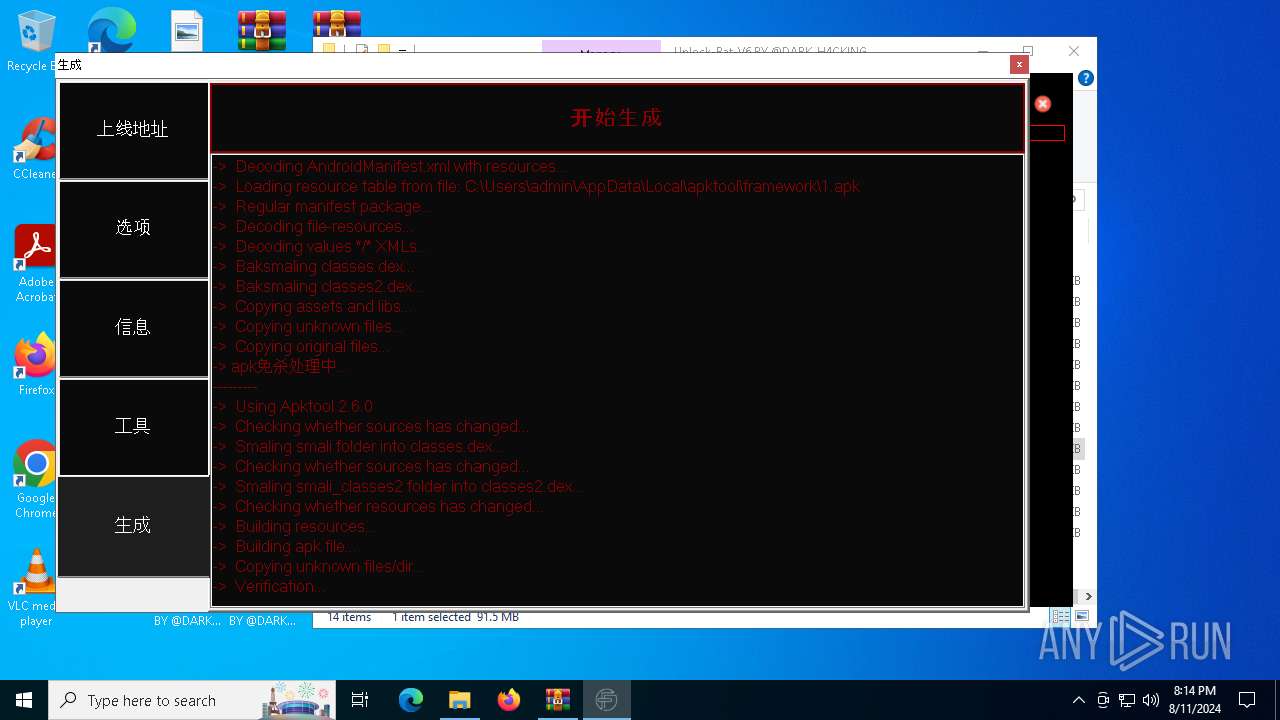
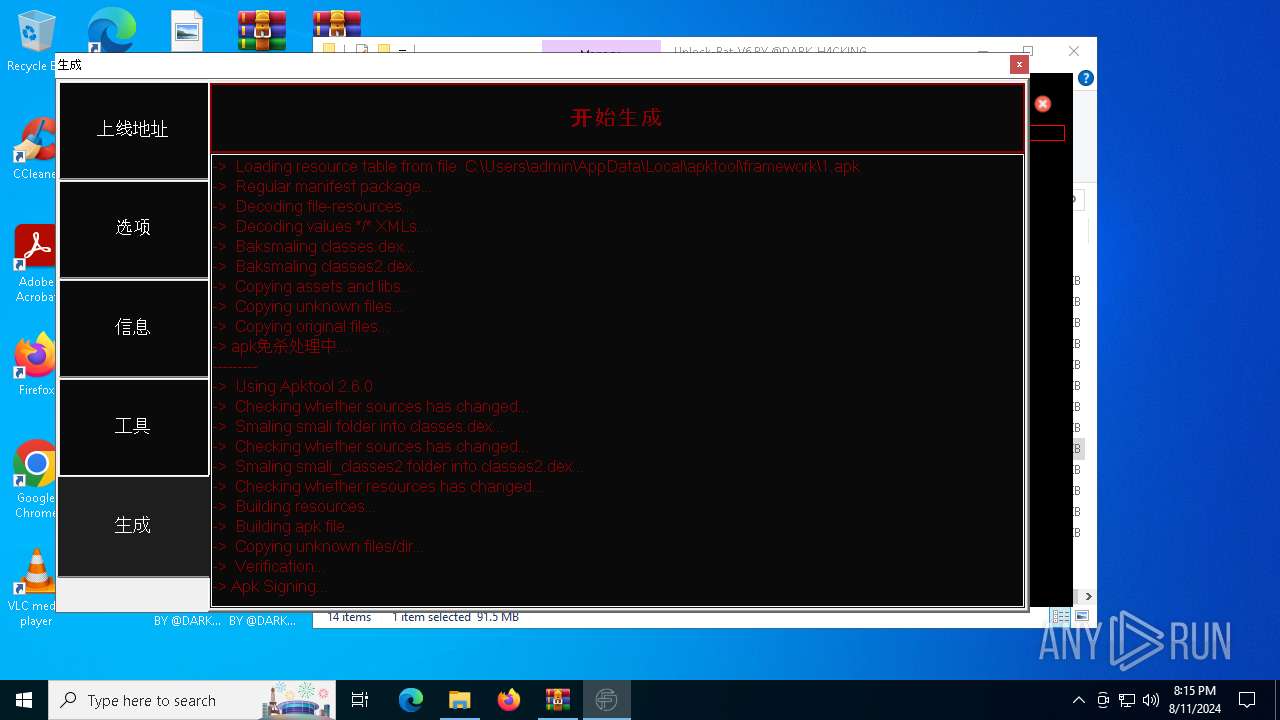
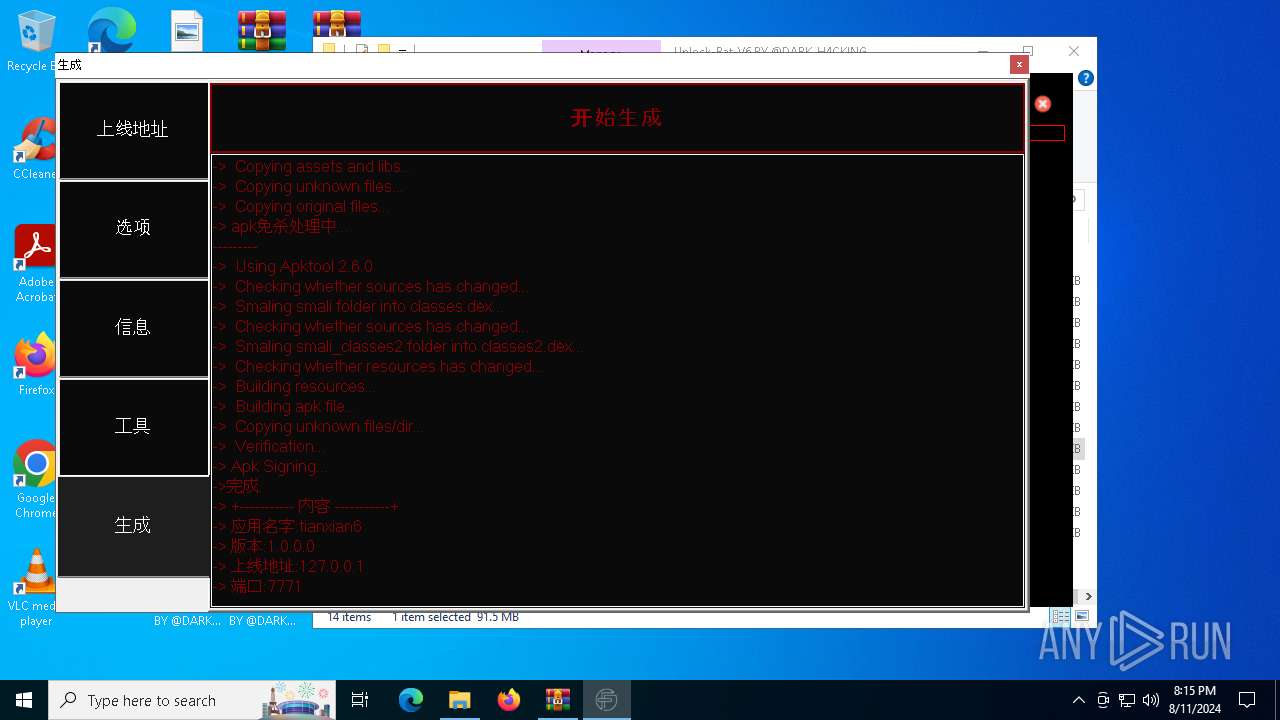
| 1432 | zipalign.exe -v 4 C:\tianxian_Builder\platformBinary64\bin\temp\dist\temp.apk C:\tianxian_Builder\platformBinary64\bin\temp\dist\tempzip.apk | C:\tianxian_Builder\platformBinary64\bin\zipalign.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
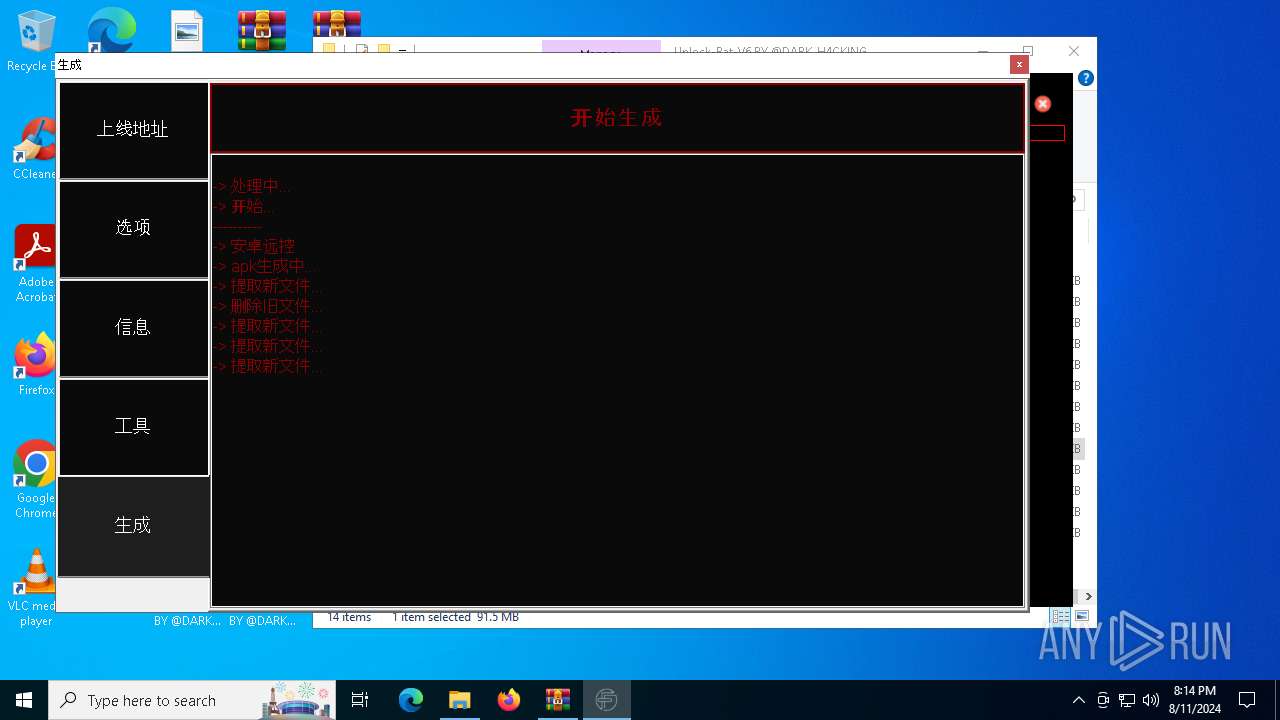
| 1984 | java -jar C:\tianxian_Builder\platformBinary64\bin\SignApk.jar sign --key C:\tianxian_Builder\platformBinary64\bin\key.pk8 --cert C:\tianxian_Builder\platformBinary64\bin\certificate.pem --v2-signing-enabled true --v3-signing-enabled true --out C:\tianxian_Builder\platformBinary64\bin\output\ready.apk C:\tianxian_Builder\platformBinary64\bin\temp\dist\temp.apk | C:\tianxian_Builder\platformBinary64\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: N/A Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 8.0.1520.1 Modules
| |||||||||||||||
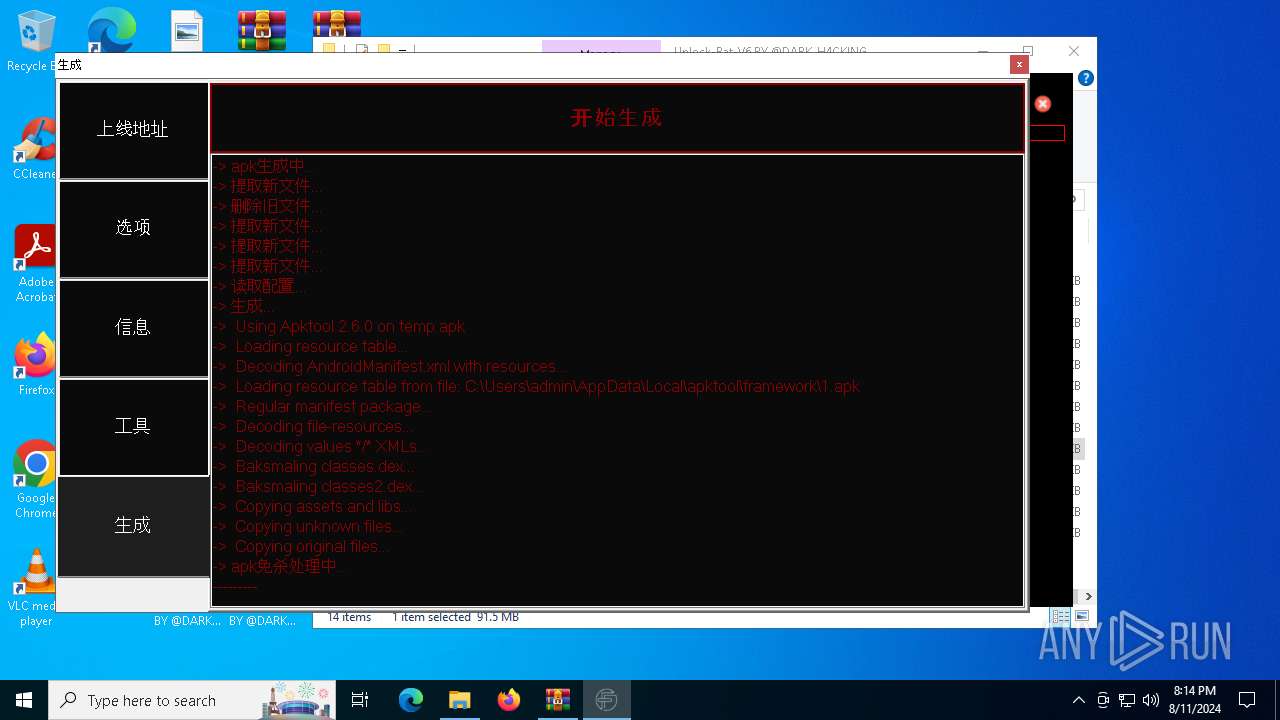
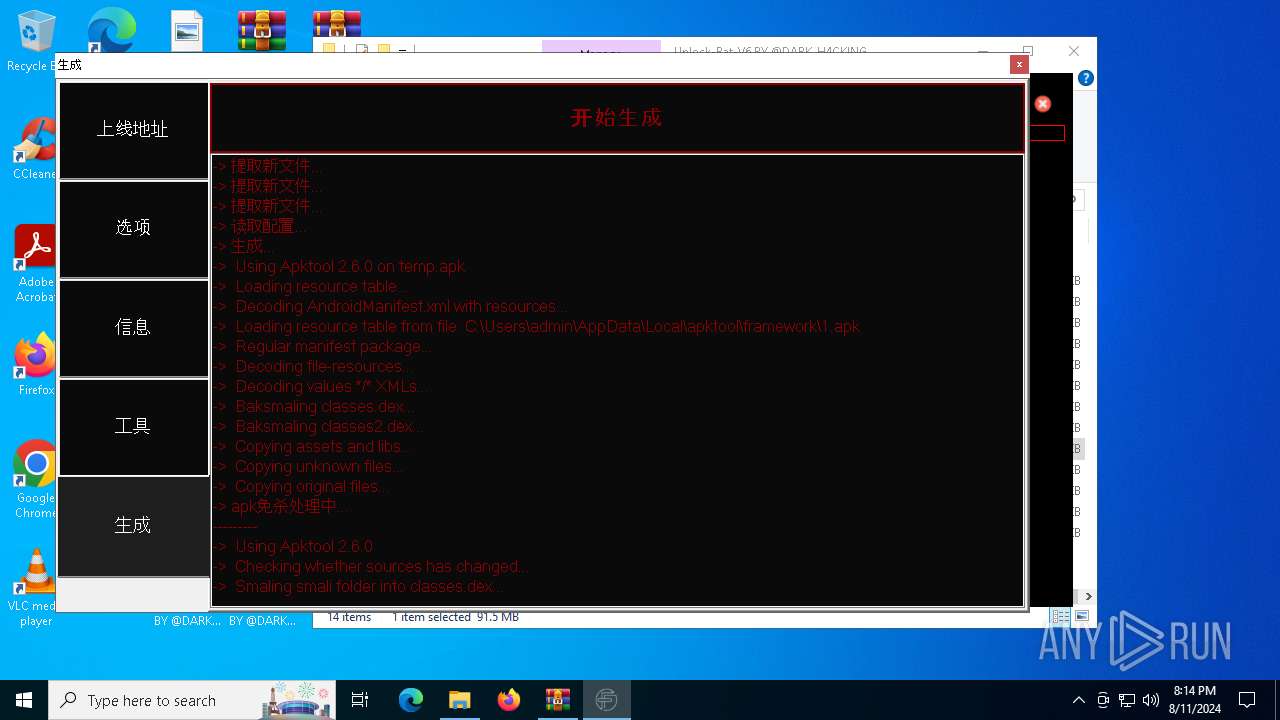
| 2212 | java -jar -Duser.language=en "C:\tianxian_Builder\platformBinary64\bin\\apktool.jar" b temp | C:\tianxian_Builder\platformBinary64\bin\java.exe | cmd.exe | ||||||||||||
User: admin Company: N/A Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 8.0.1520.1 Modules
| |||||||||||||||
| 2852 | java -jar -Duser.language=en "C:\tianxian_Builder\platformBinary64\bin\\apktool.jar" d temp.apk | C:\tianxian_Builder\platformBinary64\bin\java.exe | — | cmd.exe | |||||||||||
User: admin Company: N/A Integrity Level: HIGH Description: OpenJDK Platform binary Exit code: 0 Version: 8.0.1520.1 Modules
| |||||||||||||||
| 3812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5924 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\EverSpy Ultimate Unpacked - Copy.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6400 | C:\Users\admin\AppData\Local\Temp\brut_util_Jar_41112474085867589873911591747991064364.tmp p --forced-package-id 127 --min-sdk-version 23 --target-sdk-version 28 --version-code 1000 --version-name 1.0.0.0 --no-version-vectors -F C:\Users\admin\AppData\Local\Temp\APKTOOL1530726720742455262.tmp -e C:\Users\admin\AppData\Local\Temp\APKTOOL7428684883387620065.tmp -0 arsc -I C:\Users\admin\AppData\Local\apktool\framework\1.apk -S C:\tianxian_Builder\platformBinary64\bin\temp\res -M C:\tianxian_Builder\platformBinary64\bin\temp\AndroidManifest.xml | C:\Users\admin\AppData\Local\Temp\brut_util_Jar_41112474085867589873911591747991064364.tmp | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6420 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver "-anf=C:\Users\admin\AppData\Local\Temp\Rar$LS4552.47118" -scul -- "C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING.part02.rar" "C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6468 | "cmd.exe" | C:\Windows\SysWOW64\cmd.exe | — | Unlock-Rat-V6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 897
Read events
15 708
Write events
180
Delete events
9
Modification events
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\EverSpy Ultimate Unpacked - Copy.rar | |||
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5924) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
174
Suspicious files
63
Text files
1 662
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
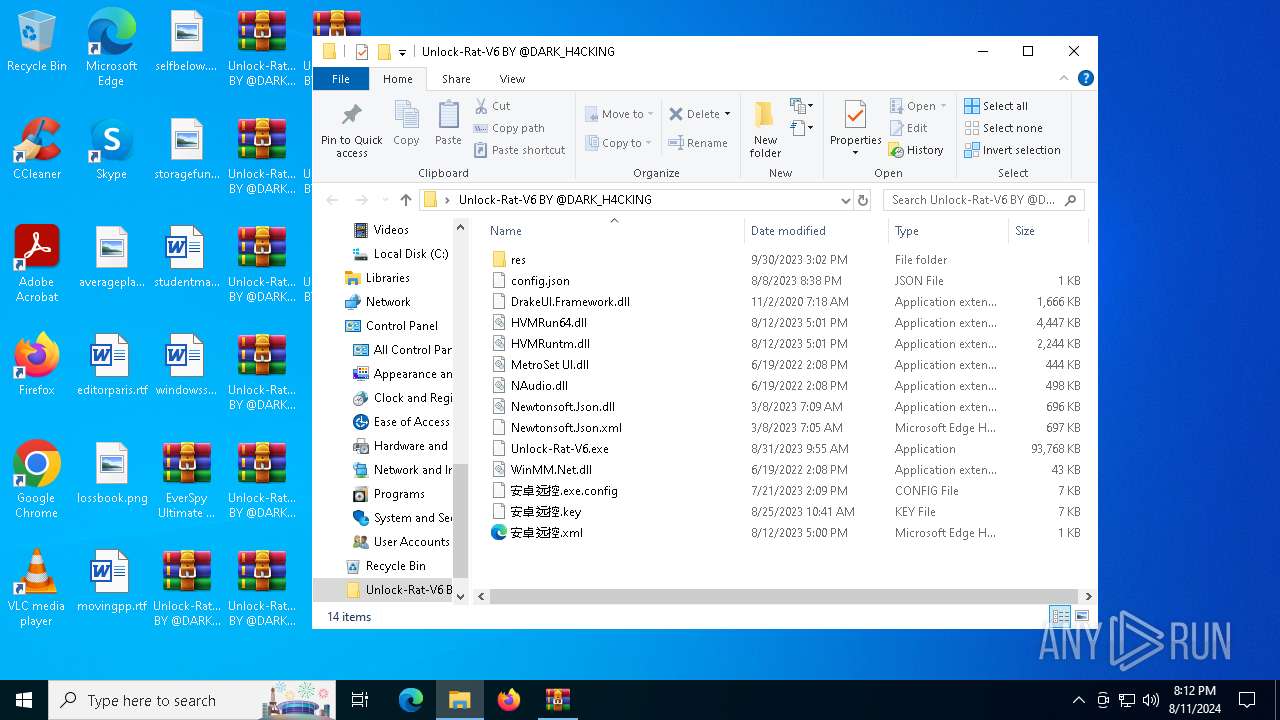
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\Unlock-Rat-V6.exe | — | |
MD5:— | SHA256:— | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\HVMRun64.dll | executable | |
MD5:21184C4444B13C67546C7ACF7F6AD8E3 | SHA256:14F61C269509EB27083883D5E8EDCF9ED14F3B62CFBFB69F4F7434D64A7FA924 | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\MetroSet UI.dll | binary | |
MD5:D99A97DE55B2561E57135433B44BB786 | SHA256:6288E559B0F34D56AB4601FFB2BA2289001C77CF7351D135DD93915034C56BBA | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\HVMRuntm.dll | executable | |
MD5:559F1A94D4FADBE42745200C5DEEB94C | SHA256:52CF690F3436C9E98A2AB13E2871CA95DA72C34EA5DD36D5C52ECCCFA78B5696 | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\res\Audio\2.wav | wav | |
MD5:9B15A3D6EA1205C555F91893859BDB7A | SHA256:40504BE5DA4002ABAD4B6B6B54DE0B966A3B9A5F4F24793B3AC9FC90E6CBE2CC | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\res\Audio\4.wav | wav | |
MD5:87F33DC8407B25DEAF98AC120E1883D6 | SHA256:A3B05031FC5D69766F5C59923495A1158D0624D4D168070BC74B7F315405B127 | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\res\Config\Pass.inf | text | |
MD5:F13C9FD7401845BCFACA535744744440 | SHA256:87C67159E71EF382BD47A763527C906C18A77F79FA66D9E18569D1ED0CBDD167 | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\res\Audio\5.wav | wav | |
MD5:33794366BB58C3AF5E464B0A974CC182 | SHA256:19DFFF92A123AC883F38BF617D530C6CD222ABF5540E3F215C9A44F6FCBA0D60 | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\res\Audio\3.wav | wav | |
MD5:269E4F85692280ED9C59CB1C40517007 | SHA256:258C0A0B95163A9379E6BD7E95CEA5F47B96CE2816692016DAB5DAFA73AA1FE9 | |||
| 6420 | WinRAR.exe | C:\Users\admin\Desktop\Unlock-Rat-V6 BY @DARK_H4CKING\res\Config\supported_text.inf | text | |
MD5:5D3B89E5C0D8B54971A1F81D175D5717 | SHA256:4C382A99B06A04BF3E5141FE9F4C6D1D40E7A2740740040156E1247C073FA8B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
40
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5540 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5540 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2128 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4080 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 184.86.251.28:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5540 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5540 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Unlock-Rat-V6.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |