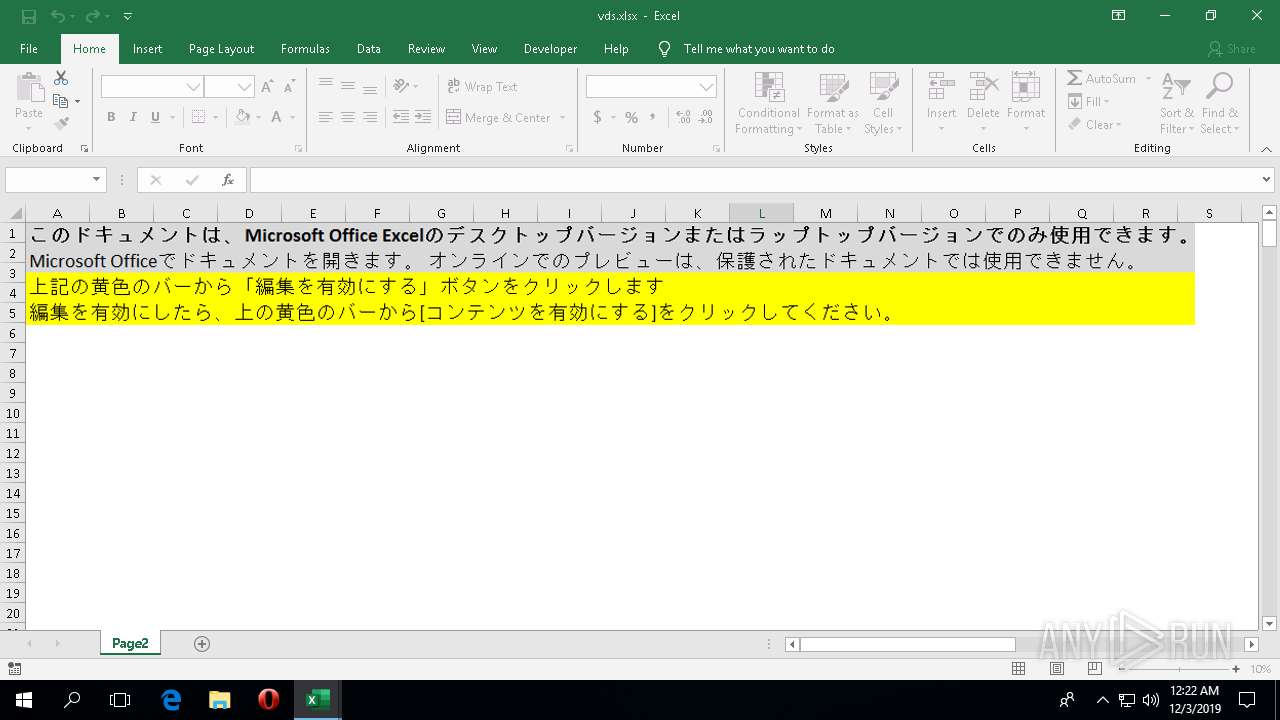
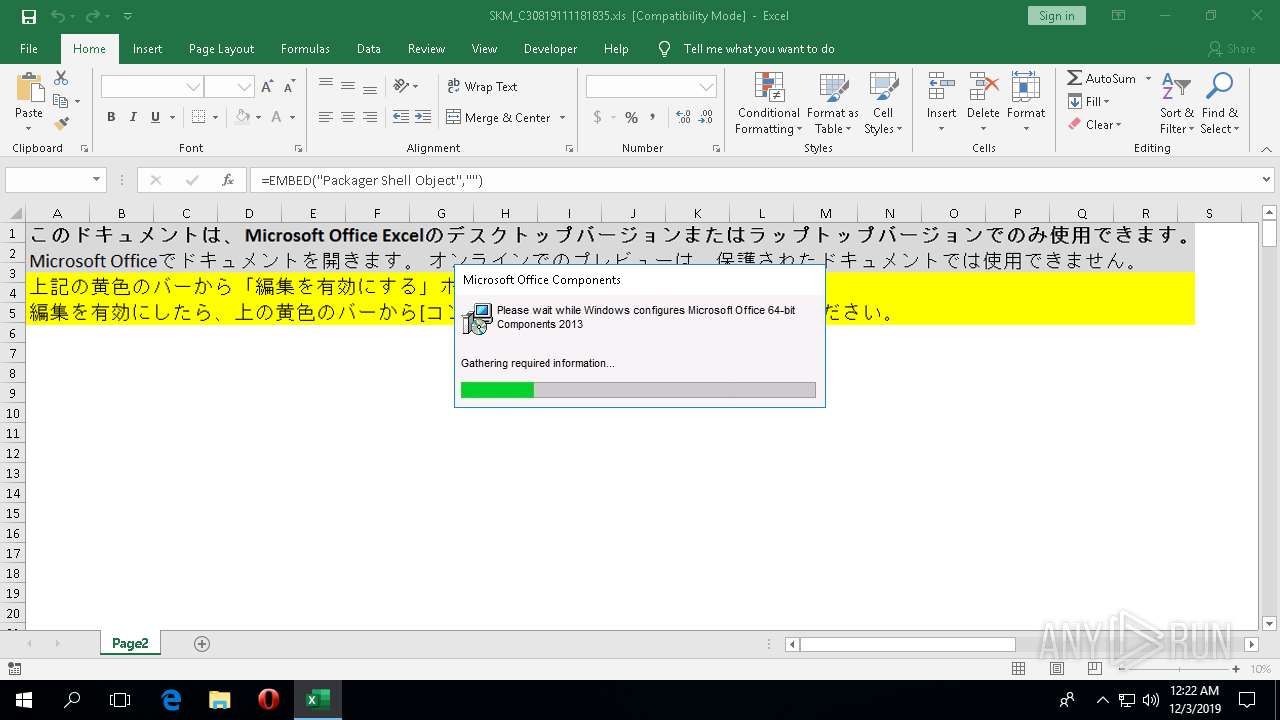
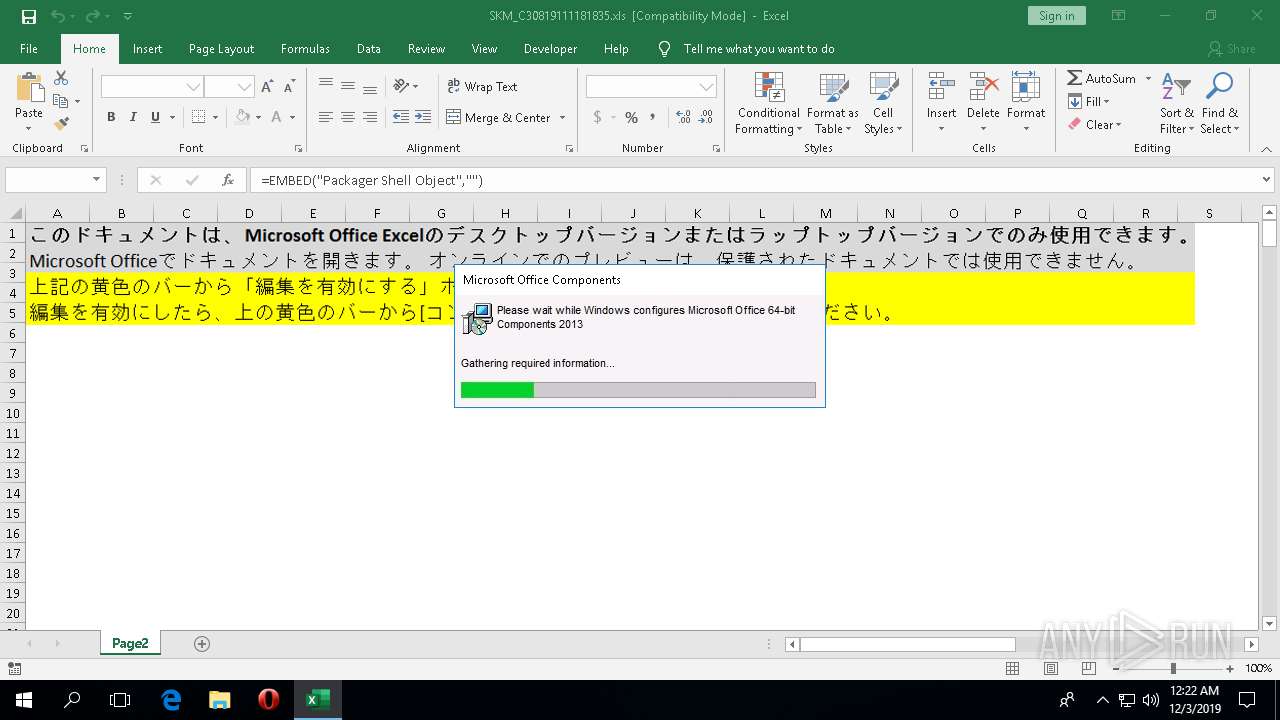
| File name: | SKM_C30819111181835.xls |
| Full analysis: | https://app.any.run/tasks/32683a2b-4a5c-4c28-986a-7b5e7f46b5e6 |
| Verdict: | Malicious activity |
| Analysis date: | December 03, 2019, 00:21:29 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.3, Code page: 1252, Title: CiBQd, Subject: N, Author: NYxaYK, Last Saved By: Administrator, Revision Number: 602, Name of Creating Application: Microsoft Excel, Total Editing Time: 1d+04:31:00, Create Time/Date: Fri Aug 30 10:14:50 2019, Last Saved Time/Date: Mon Dec 2 20:35:23 2019, Number of Pages: 2, Number of Words: 3929, Number of Characters: 7608, Security: 0 |
| MD5: | E64732DBBA7C812DE3CFD435B5F1F20B |
| SHA1: | 98F84376FE5E050C7783D1819FAB2E6369503066 |
| SHA256: | 04C6CE889C9D7E0B4C7D61ECB51F2FDECF3A37CE9892F7A4B6D5D458C8AB4DAF |
| SSDEEP: | 12288:6EB+Jx9Cjs/39lKf94sGg0SOMwItwmtSp+gW3:tcCjsnKG4wbmtcBE |
MALICIOUS
Scans artifacts that could help determine the target
- EXCEL.EXE (PID: 4208)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 4208)
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 4208)
Loads dropped or rewritten executable
- EXCEL.EXE (PID: 4208)
SUSPICIOUS
Reads Environment values
- EXCEL.EXE (PID: 4208)
INFO
Reads the software policy settings
- EXCEL.EXE (PID: 4208)
Reads the machine GUID from the registry
- EXCEL.EXE (PID: 4208)
Reads settings of System Certificates
- EXCEL.EXE (PID: 4208)
Creates files in the user directory
- EXCEL.EXE (PID: 4208)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 4208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 25 |
|---|---|
| CompObjUserType: | Microsoft Forms 2.0 Form |
| Title: | CiBQd |
| Subject: | N |
| Author: | NYxaYK |
| LastModifiedBy: | Administrator |
| RevisionNumber: | 602 |
| Software: | Microsoft Excel |
| TotalEditTime: | 1.2 days |
| CreateDate: | 2019:08:30 09:14:50 |
| ModifyDate: | 2019:12:02 20:35:23 |
| Pages: | 2 |
| Words: | 3929 |
| Characters: | 7608 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Bytes: | 12777 |
| Lines: | 230 |
| Paragraphs: | 36 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | Page2 |
| HeadingPairs: |
|
Total processes
99
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1240 | C:\WINDOWS\splwow64.exe 8192 | C:\WINDOWS\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4208 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\AppData\Local\Temp\SKM_C30819111181835.xls" | C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
Total events
2 113
Read events
1 701
Write events
358
Delete events
54
Modification events
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000284FFA2E01000000000000000400000000000000 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\EXCEL\4208 |
| Operation: | write | Name: | 0 |
Value: 0B0E103A6D74DCB9E66F4A83DB99A51B9CE2E0230046D999AEF0FAADEAEA016A0410240044FA5D64A89E01008500A907556E6B6E6F776EC9062E226D2B484F4D616659574A5464337373702B3165327141506A326C775347586F6C4A7635624B6E337449506B3D2200 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (4208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
5
Text files
4
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF901CDE733F9959AE.TMP | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GX40DJG9L5N7WTGHV33S.temp | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VB65E5.tmp | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VB65E4.tmp | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFA9806757755F8C1B.TMP | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\msohtmlclip1_PendingDelete | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\786D2000 | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF8BB14BC035E16D81.TMP | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~$vds.xlsx | — | |
MD5:— | SHA256:— | |||
| 4208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF174B2BFD28BB847C.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
31
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3472 | svchost.exe | POST | 400 | 40.90.22.184:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 210 b | whitelisted |
3472 | svchost.exe | POST | 400 | 40.90.22.184:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 210 b | whitelisted |
4208 | EXCEL.EXE | GET | 200 | 52.109.76.6:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.12026&crev=3 | IE | xml | 111 Kb | whitelisted |
4208 | EXCEL.EXE | POST | — | 172.104.91.16:443 | https://live-en.com/1111 | JP | — | — | malicious |
3472 | svchost.exe | POST | 400 | 40.90.22.184:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 210 b | whitelisted |
2660 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
4208 | EXCEL.EXE | GET | 200 | 52.109.52.36:443 | https://messaging.office.com/lifecycle/legacygetcustommessage16?app=1&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.12026&lc=en-US&platform=10%3A0%3A16299%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA044%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7BDC746D3A-E6B9-4A6F-83DB-99A51B9CE2E0%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofaa1msspvo2xw31%2Cofgg6vdq3anjh131%2Cof3ttwdwizkwt531%2Cofskuekmq22yki31%22%7D | JP | xml | 495 b | whitelisted |
2660 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | der | 555 b | whitelisted |
3472 | svchost.exe | POST | 200 | 40.90.22.184:443 | https://login.live.com/RST2.srf | US | xml | 1.29 Kb | whitelisted |
4208 | EXCEL.EXE | GET | 200 | 2.18.232.120:443 | https://fs.microsoft.com/fs/4.9/flatFontAssets.pkg | unknown | compressed | 381 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4208 | EXCEL.EXE | 52.109.76.6:443 | officeclient.microsoft.com | Microsoft Corporation | IE | whitelisted |
4208 | EXCEL.EXE | 2.18.232.120:443 | fs.microsoft.com | Akamai International B.V. | — | whitelisted |
4208 | EXCEL.EXE | 13.107.3.128:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
4208 | EXCEL.EXE | 172.104.91.16:443 | live-en.com | Linode, LLC | JP | malicious |
3472 | svchost.exe | 40.90.22.184:443 | login.live.com | Microsoft Corporation | US | malicious |
4208 | EXCEL.EXE | 52.109.52.36:443 | messaging.office.com | Microsoft Corporation | JP | unknown |
4208 | EXCEL.EXE | 52.109.76.31:443 | nexusrules.officeapps.live.com | Microsoft Corporation | IE | whitelisted |
2660 | svchost.exe | 2.21.38.54:80 | www.microsoft.com | GTT Communications Inc. | FR | malicious |
2660 | svchost.exe | 2.16.186.74:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
648 | svchost.exe | 40.90.22.190:443 | login.live.com | Microsoft Corporation | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
self.events.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
config.edge.skype.com |
| malicious |
login.live.com |
| whitelisted |
live-en.com |
| malicious |
messaging.office.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
dns.msftncsi.com |
| shared |