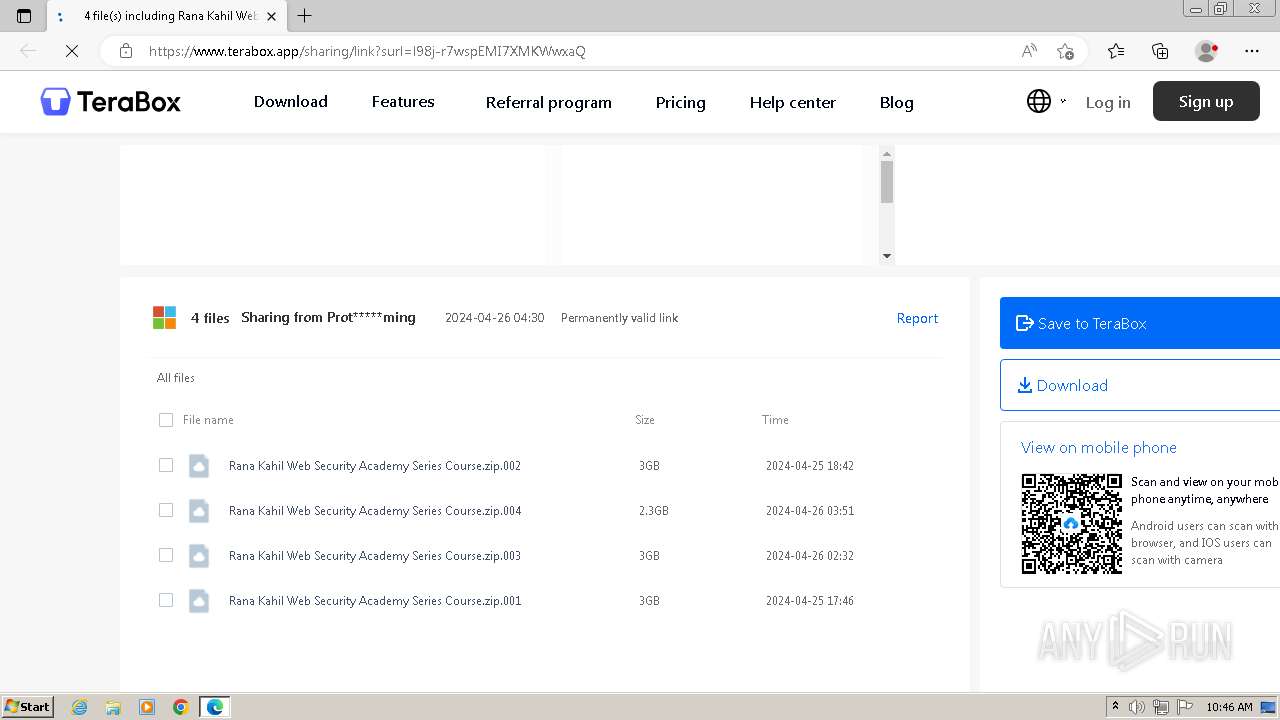
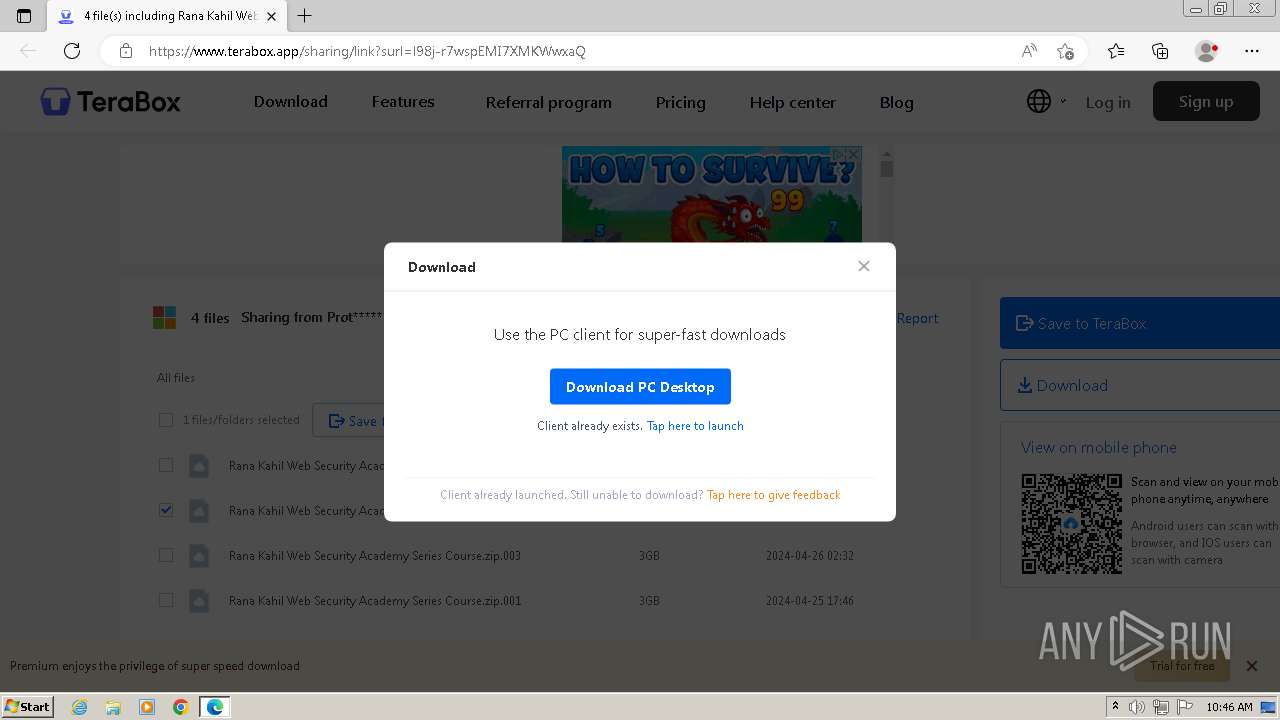
| URL: | https://teraboxapp.com/s/1l98j-r7wspEMI7XMKWwxaQ |
| Full analysis: | https://app.any.run/tasks/1b1455c8-bc1c-4e6f-864d-90e09bd2a0c1 |
| Verdict: | Malicious activity |
| Analysis date: | May 07, 2024, 09:45:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4338949736855B3CDADDFDA0F23D9530 |
| SHA1: | 40CE5574E136FF9E96254B1856543571173B05ED |
| SHA256: | 049B68FE9545C7CEA8B5ED9ED5B70FF8EAD6F17D21FF5740A06EDAB9CCB85498 |
| SSDEEP: | 3:N8IUqWljlFyudn:2IVQSA |
MALICIOUS
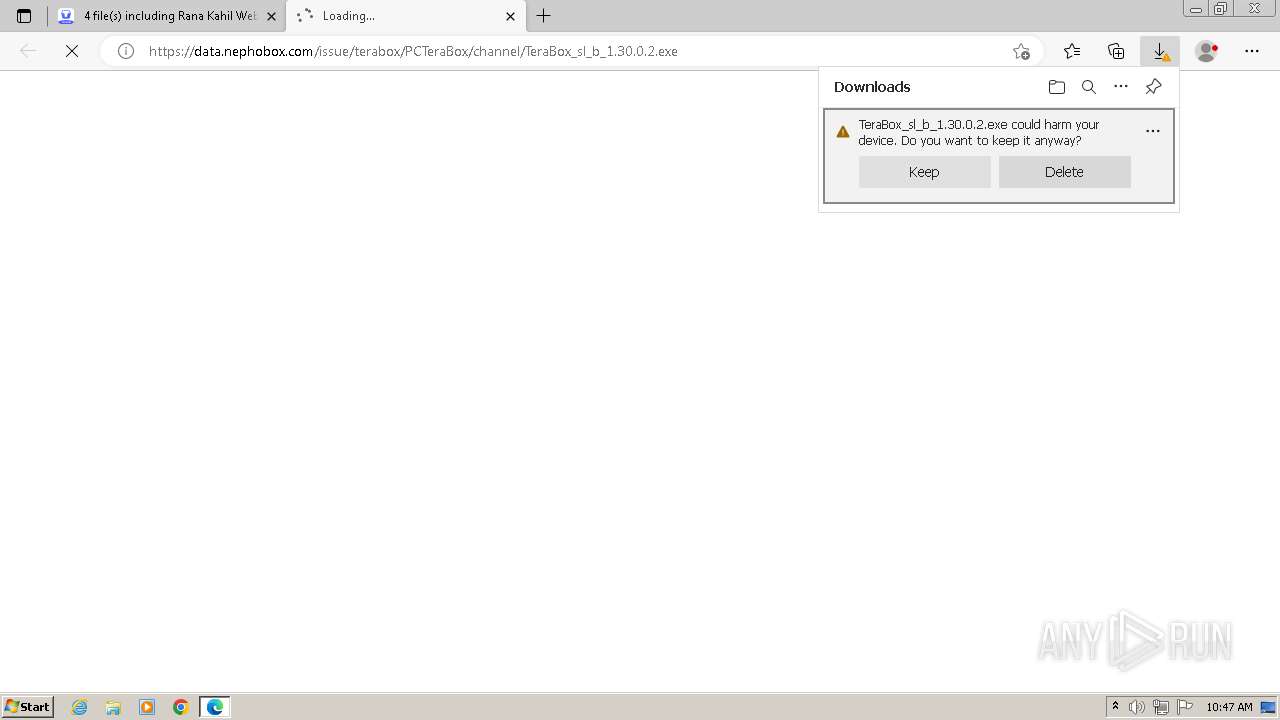
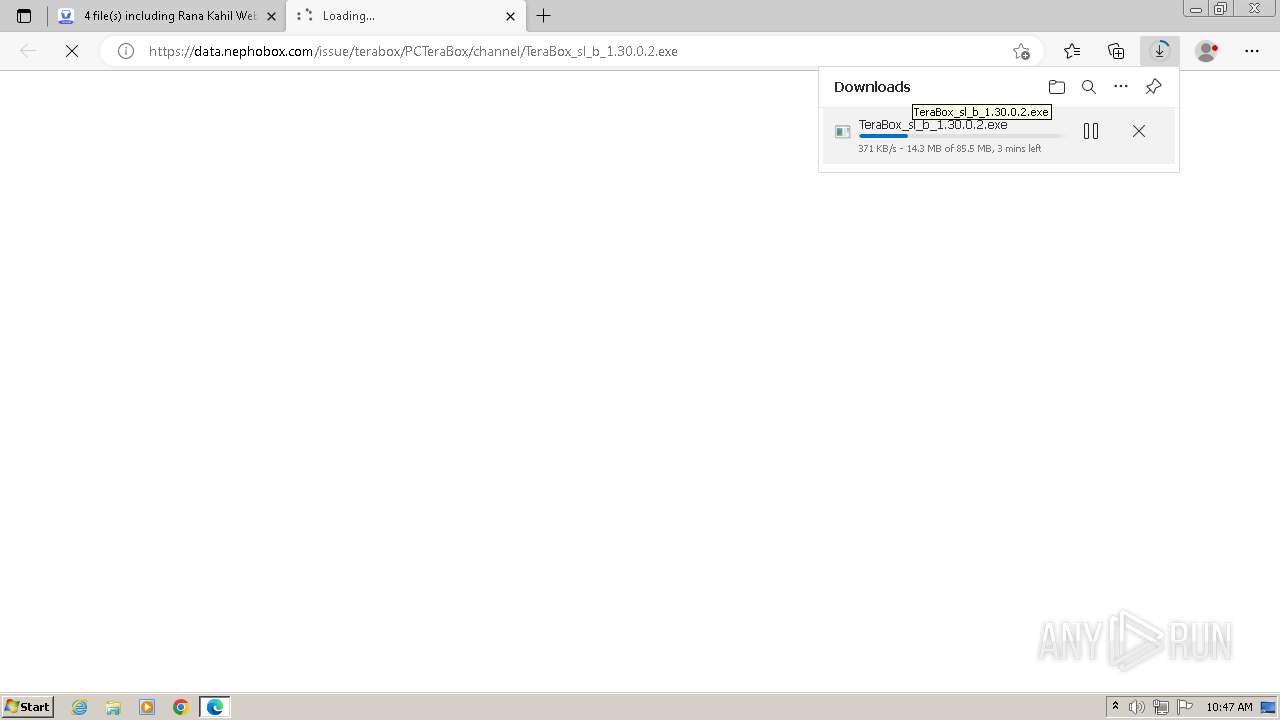
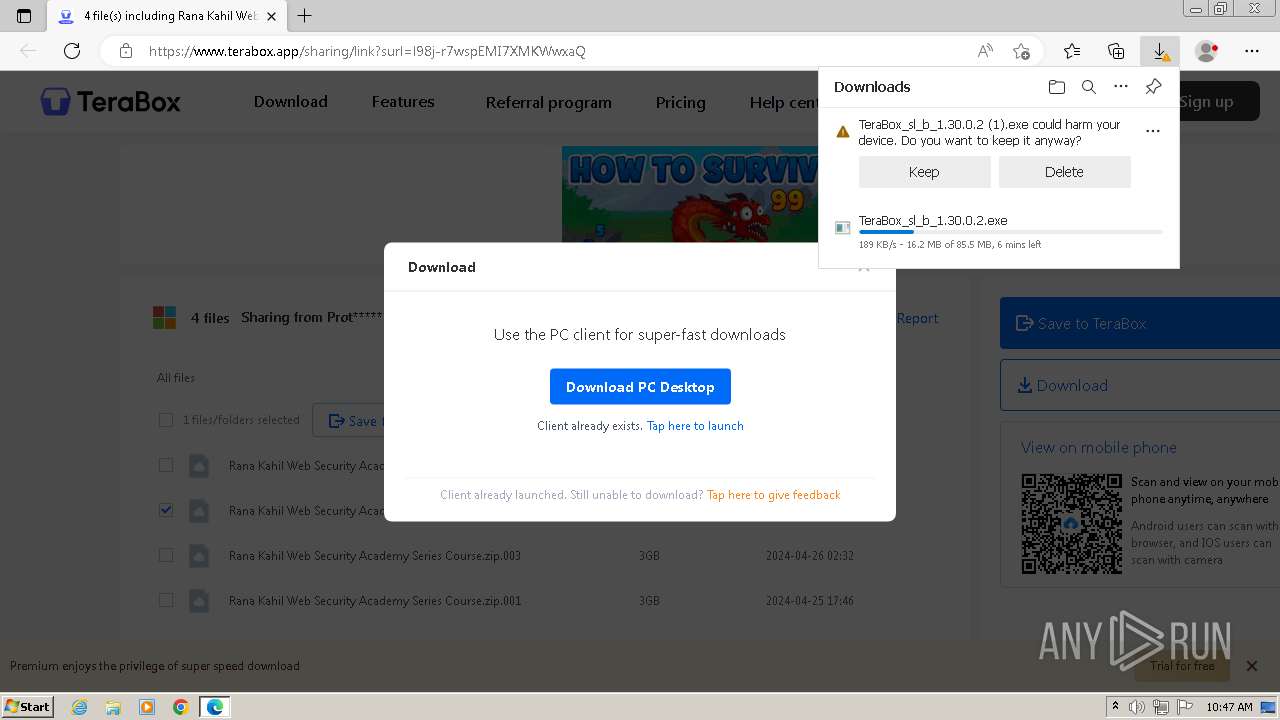
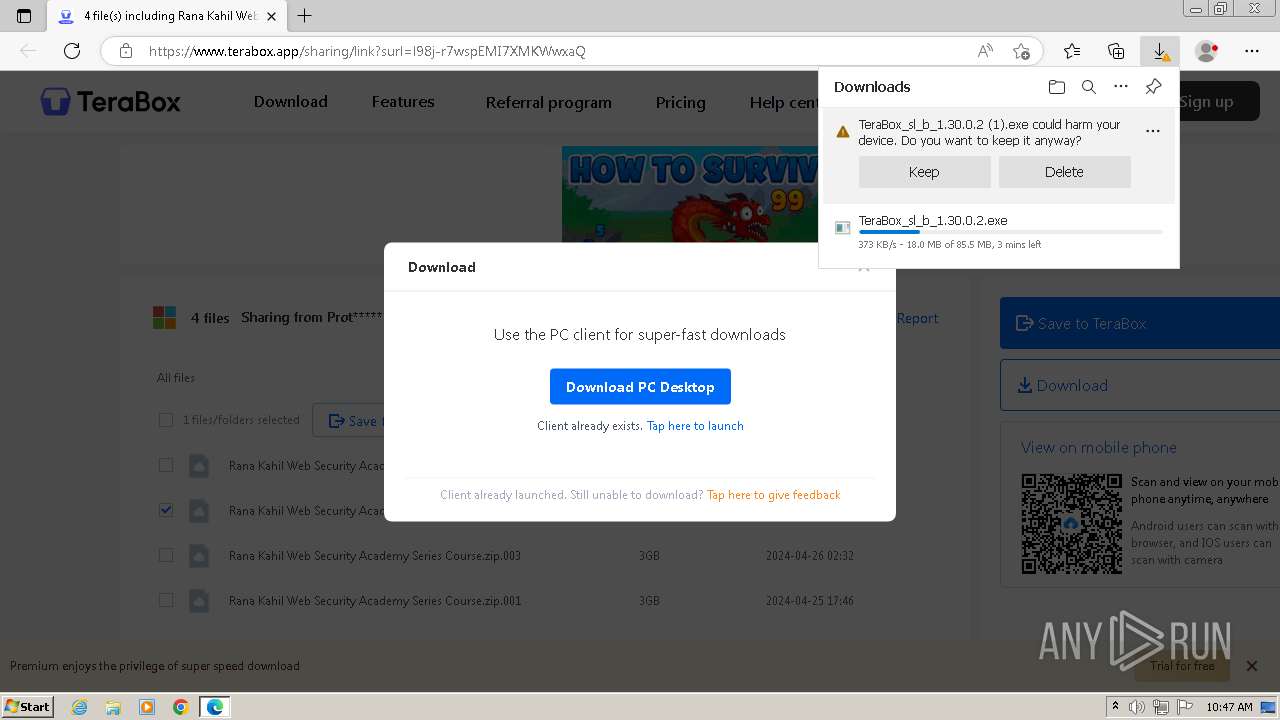
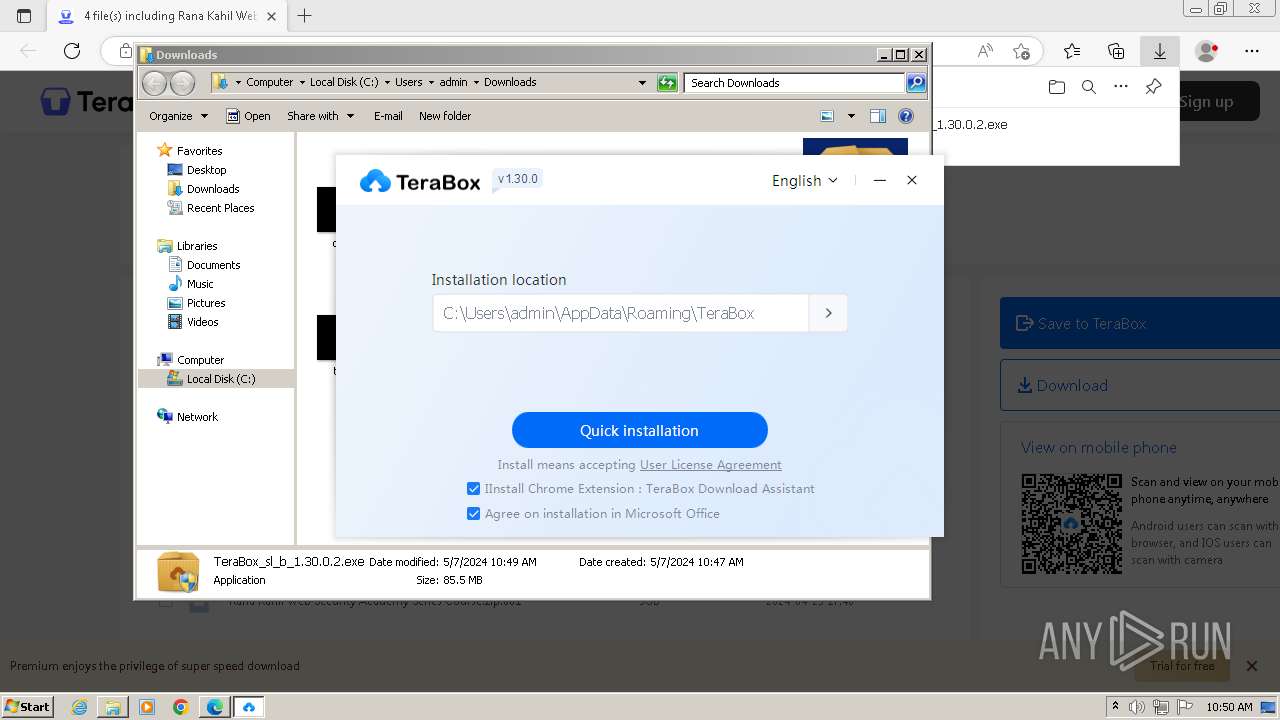
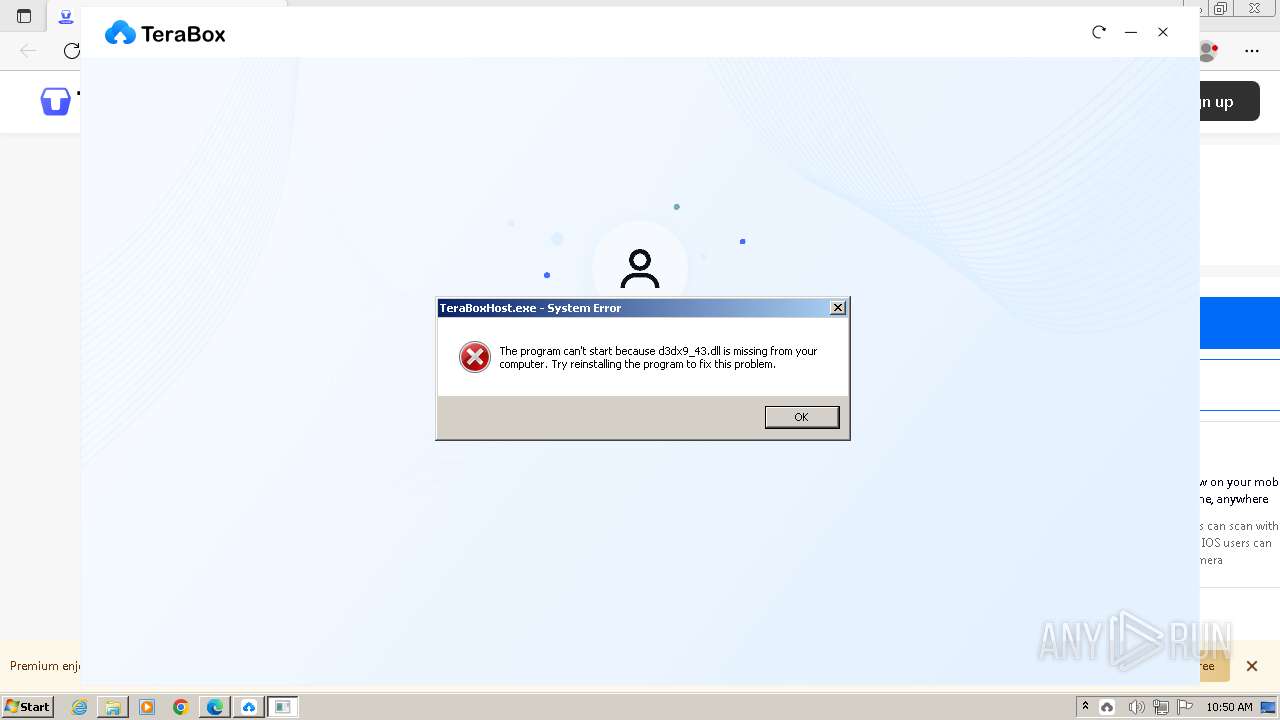
Drops the executable file immediately after the start
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
Changes the autorun value in the registry
- TeraBox.exe (PID: 3188)
Registers / Runs the DLL via REGSVR32.EXE
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
Creates a writable file in the system directory
- YunUtilityService.exe (PID: 1800)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
Executable content was dropped or overwritten
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
The process creates files with name similar to system file names
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
- TeraBoxRender.exe (PID: 3288)
The process drops C-runtime libraries
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
Process drops legitimate windows executable
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
Reads the Internet Settings
- TeraBoxWebService.exe (PID: 4092)
- TeraBox.exe (PID: 336)
Reads the date of Windows installation
- TeraBox.exe (PID: 3188)
Creates a software uninstall entry
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 956)
- regsvr32.exe (PID: 1848)
Reads security settings of Internet Explorer
- TeraBoxWebService.exe (PID: 4092)
- TeraBox.exe (PID: 336)
Reads settings of System Certificates
- TeraBox.exe (PID: 336)
- TeraBoxRender.exe (PID: 3612)
Checks Windows Trust Settings
- TeraBox.exe (PID: 336)
- YunUtilityService.exe (PID: 1800)
Executes as Windows Service
- YunUtilityService.exe (PID: 1800)
Adds/modifies Windows certificates
- YunUtilityService.exe (PID: 1800)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2272)
- TeraBox_sl_b_1.30.0.2.exe (PID: 1044)
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
Application launched itself
- msedge.exe (PID: 3976)
Checks supported languages
- wmpnscfg.exe (PID: 2272)
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
- TeraBox.exe (PID: 336)
- YunUtilityService.exe (PID: 3380)
- TeraBoxWebService.exe (PID: 3852)
- TeraBoxWebService.exe (PID: 4092)
- TeraBox.exe (PID: 3188)
- TeraBoxRender.exe (PID: 3288)
- TeraBoxRender.exe (PID: 3016)
- TeraBoxRender.exe (PID: 3612)
- TeraBoxRender.exe (PID: 4044)
- TeraBoxRender.exe (PID: 1576)
- YunUtilityService.exe (PID: 1800)
- TeraBoxHost.exe (PID: 2456)
- TeraBoxHost.exe (PID: 3204)
Reads the computer name
- wmpnscfg.exe (PID: 2272)
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
- TeraBox.exe (PID: 3188)
- YunUtilityService.exe (PID: 3380)
- TeraBoxWebService.exe (PID: 4092)
- TeraBox.exe (PID: 336)
- TeraBoxRender.exe (PID: 3288)
- TeraBoxRender.exe (PID: 3612)
- TeraBoxRender.exe (PID: 1576)
- YunUtilityService.exe (PID: 1800)
- TeraBoxHost.exe (PID: 2456)
Executable content was dropped or overwritten
- msedge.exe (PID: 3976)
Drops the executable file immediately after the start
- msedge.exe (PID: 3976)
The process uses the downloaded file
- msedge.exe (PID: 1932)
Reads Environment values
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
Create files in a temporary directory
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
- TeraBox.exe (PID: 336)
- TeraBoxRender.exe (PID: 3612)
Creates files or folders in the user directory
- TeraBox_sl_b_1.30.0.2.exe (PID: 1832)
- TeraBox.exe (PID: 3188)
- TeraBoxWebService.exe (PID: 4092)
- TeraBox.exe (PID: 336)
- TeraBoxHost.exe (PID: 2456)
Reads the machine GUID from the registry
- TeraBox.exe (PID: 3188)
- TeraBoxWebService.exe (PID: 4092)
- TeraBox.exe (PID: 336)
- YunUtilityService.exe (PID: 1800)
- TeraBoxRender.exe (PID: 3612)
- TeraBoxHost.exe (PID: 2456)
Checks proxy server information
- TeraBoxWebService.exe (PID: 4092)
- TeraBox.exe (PID: 336)
Process checks computer location settings
- TeraBox.exe (PID: 336)
- TeraBoxRender.exe (PID: 4044)
- TeraBoxRender.exe (PID: 3016)
Reads the software policy settings
- TeraBox.exe (PID: 336)
- YunUtilityService.exe (PID: 1800)
- TeraBoxRender.exe (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
99
Monitored processes
54
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1376 --field-trial-handle=1288,i,12563438504894062406,7155727255082959443,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3636 --field-trial-handle=1288,i,12563438504894062406,7155727255082959443,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 336 | C:\Users\admin\AppData\Roaming\TeraBox\TeraBox.exe | C:\Users\admin\AppData\Roaming\TeraBox\TeraBox.exe | TeraBox_sl_b_1.30.0.2.exe | ||||||||||||
User: admin Company: Flextech Inc. Integrity Level: MEDIUM Description: TeraBox Version: 1.30.0.2 Modules
| |||||||||||||||
| 728 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2204 --field-trial-handle=1288,i,12563438504894062406,7155727255082959443,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2220 --field-trial-handle=1288,i,12563438504894062406,7155727255082959443,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4216 --field-trial-handle=1288,i,12563438504894062406,7155727255082959443,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 956 | "C:\Windows\system32\regsvr32.exe" "/s" "C:\Users\admin\AppData\Roaming\TeraBox\YunShellExt.dll" | C:\Windows\System32\regsvr32.exe | — | TeraBox_sl_b_1.30.0.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\Downloads\TeraBox_sl_b_1.30.0.2.exe" | C:\Users\admin\Downloads\TeraBox_sl_b_1.30.0.2.exe | — | explorer.exe | |||||||||||
User: admin Company: Flextech Integrity Level: MEDIUM Description: TeraBox Installer Exit code: 3221226540 Version: 1.30.0.2 Modules
| |||||||||||||||
| 1064 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1256 --field-trial-handle=1288,i,12563438504894062406,7155727255082959443,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=2176 --field-trial-handle=1288,i,12563438504894062406,7155727255082959443,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
44 351
Read events
43 866
Write events
447
Delete events
38
Modification events
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: 0B868F5570762F00 | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (3976) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
84
Suspicious files
289
Text files
173
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\c1d58f68-c546-4a8f-b60a-161b51058af3.tmp | — | |
MD5:— | SHA256:— | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF104538.TMP | — | |
MD5:— | SHA256:— | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF104538.TMP | — | |
MD5:— | SHA256:— | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF104548.TMP | — | |
MD5:— | SHA256:— | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF104623.TMP | — | |
MD5:— | SHA256:— | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:61FE7896F9494DCDF53480A325F4FB85 | SHA256:ACFD3CD36E0DFCF1DCB67C7F31F2A5B9BA0815528A0C604D4330DFAA9E683E51 | |||
| 3976 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RF104558.TMP | text | |
MD5:0FFCDE9AA0F7BF34DC35C8AEADCA5BA5 | SHA256:5A9F6E7DDB2557B2C5921117AE4D6A407BB2504F6728DD1352FF88492E0ECC3D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
122
DNS requests
110
Threats
37
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
112 | msedge.exe | GET | 204 | 13.107.6.158:80 | http://edge-http.microsoft.com/captiveportal/generate_204 | unknown | — | — | unknown |
4092 | TeraBoxWebService.exe | GET | 404 | 210.148.85.47:80 | http://www.terabox.com/box-static/base/widget/httpProxy/_nomd5/crossdomain.xml | unknown | — | — | unknown |
1800 | YunUtilityService.exe | GET | 304 | 88.221.110.91:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b498c5b4c338ba2b | unknown | — | — | unknown |
336 | TeraBox.exe | POST | 200 | 210.148.85.47:80 | http://terabox.com/statistics?clienttype=8&devuid=TBIMXV2%2DO%5F70978CB5C36C447BA453C44D6C26B01A%2DC%5F0%2DD%5F4d51303030302031202020202020202020202020%2DM%5F12A9866C77DE%2DV%5FC4BA3647&channel=00000000000000000000000001000002&version=1.30.0.2&ver=1&id=171507543291B985BE44B24CF59219E40B67C89F17&vip=0 | unknown | — | — | unknown |
1800 | YunUtilityService.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGEJFcIpBz28BuO60qVQ%3D | unknown | — | — | unknown |
1800 | YunUtilityService.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | — | — | unknown |
1800 | YunUtilityService.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | unknown |
1800 | YunUtilityService.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDCnIy0MdV2V3V%2FtH%2FA%3D%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3976 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
112 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
112 | msedge.exe | 210.148.85.41:443 | teraboxapp.com | Internet Initiative Japan Inc. | JP | unknown |
112 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
112 | msedge.exe | 210.148.85.14:443 | www.terabox.app | Internet Initiative Japan Inc. | JP | unknown |
112 | msedge.exe | 2.23.209.148:443 | www.bing.com | Akamai International B.V. | GB | unknown |
112 | msedge.exe | 128.1.34.163:443 | www.staticcc.com | ZEN-ECN | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
teraboxapp.com |
| unknown |
edge.microsoft.com |
| whitelisted |
www.terabox.app |
| unknown |
www.staticcc.com |
| unknown |
blog.terabox.com |
| unknown |
data.terabox.app |
| unknown |
ymg-api.terabox.app |
| unknown |
www.bing.com |
| whitelisted |
s2.teraboxcdn.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
112 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
112 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
— | — | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
— | — | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
112 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
112 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
— | — | Misc activity | ET INFO Observed File Sharing Domain (terabox .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed File Sharing Domain (terabox .com in TLS SNI) |
112 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
112 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |