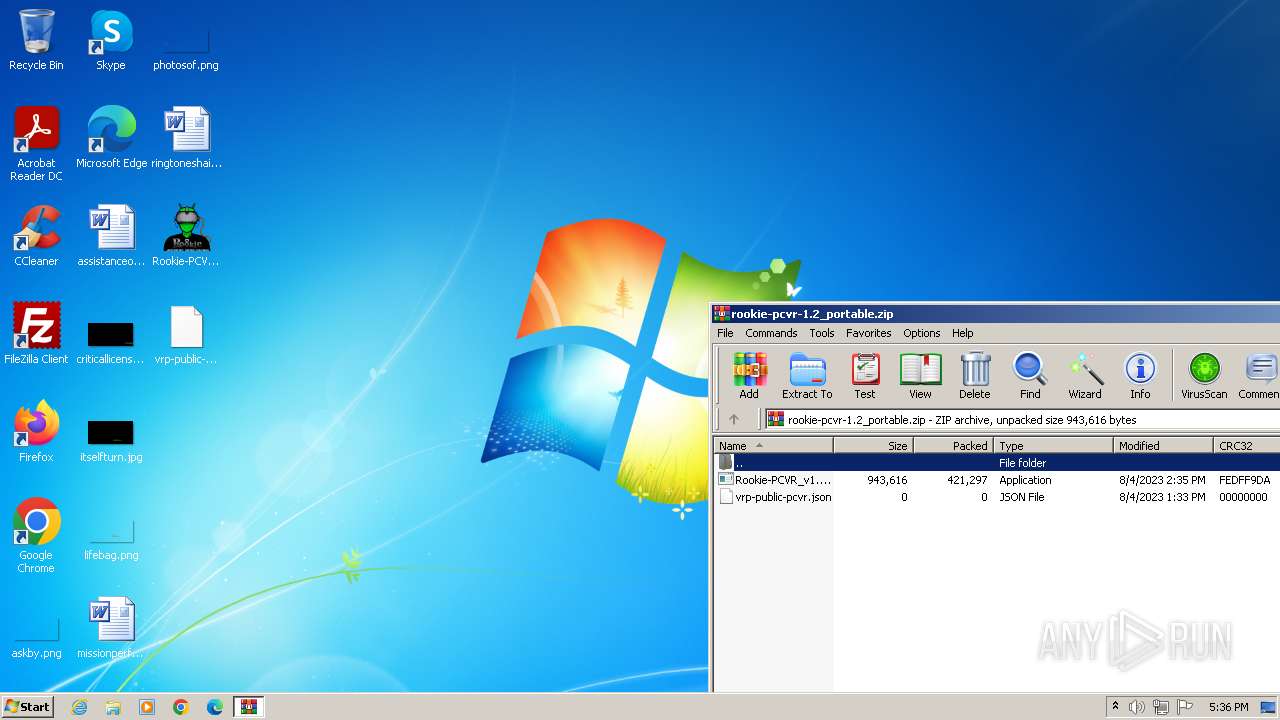
| File name: | rookie-pcvr-1.2_portable.zip |
| Full analysis: | https://app.any.run/tasks/578a6903-76c2-4e29-8632-e3a8ab7a4c65 |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2023, 17:36:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 1F19179920FB935B69FD224C9CF72C89 |
| SHA1: | BEB37FF31F4FD53B95CBAF57926503D75F2A9910 |
| SHA256: | 044B9210564DE54E445D9BB40F9FAE1E1B4C27F07EDF70CACB7D85B2B59CA775 |
| SSDEEP: | 12288:AuXwFvVTSUjphx7OP+s0L4Y97aa8PGy6SnIpRqA2ZoC2N8hG:AYwFvVTSUj/x7OP+s0kY9B8PGy6zpRqu |
MALICIOUS
Application was dropped or rewritten from another process
- Rookie-PCVR_v1.2.exe (PID: 3928)
- 7z.exe (PID: 3980)
- 7z.exe (PID: 2820)
Drops the executable file immediately after the start
- Rookie-PCVR_v1.2.exe (PID: 3928)
SUSPICIOUS
Reads the Internet Settings
- Rookie-PCVR_v1.2.exe (PID: 3928)
Reads settings of System Certificates
- Rookie-PCVR_v1.2.exe (PID: 3928)
- rclone.exe (PID: 3324)
Drops 7-zip archiver for unpacking
- Rookie-PCVR_v1.2.exe (PID: 3928)
Adds/modifies Windows certificates
- Rookie-PCVR_v1.2.exe (PID: 3928)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2752)
Checks supported languages
- Rookie-PCVR_v1.2.exe (PID: 3928)
- 7z.exe (PID: 3980)
- 7z.exe (PID: 2820)
- rclone.exe (PID: 3324)
- rclone.exe (PID: 2996)
Reads the computer name
- Rookie-PCVR_v1.2.exe (PID: 3928)
- 7z.exe (PID: 2820)
- 7z.exe (PID: 3980)
- rclone.exe (PID: 3324)
- rclone.exe (PID: 2996)
Reads Environment values
- Rookie-PCVR_v1.2.exe (PID: 3928)
Reads the machine GUID from the registry
- Rookie-PCVR_v1.2.exe (PID: 3928)
- rclone.exe (PID: 3324)
Manual execution by a user
- Rookie-PCVR_v1.2.exe (PID: 3928)
Creates files or folders in the user directory
- Rookie-PCVR_v1.2.exe (PID: 3928)
Create files in a temporary directory
- Rookie-PCVR_v1.2.exe (PID: 3928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:08:04 08:35:18 |
| ZipCRC: | 0xfedff9da |
| ZipCompressedSize: | 421297 |
| ZipUncompressedSize: | 943616 |
| ZipFileName: | Rookie-PCVR_v1.2.exe |
Total processes
52
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe8_ Global\UsGthrCtrlFltPipeMssGthrPipe8 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\rookie-pcvr-1.2_portable.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2820 | "7z.exe" x "C:\Users\admin\Desktop\meta.7z" -y -o"C:\Users\admin\Desktop\meta" -p"gL59VfgPxoHR" | C:\Users\admin\Desktop\7z.exe | — | Rookie-PCVR_v1.2.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 2996 | "C:\Users\admin\Desktop\rclone\rclone.exe" listremotes --config vrp.download.config | C:\Users\admin\Desktop\rclone\rclone.exe | — | Rookie-PCVR_v1.2.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rsync for cloud storage Exit code: 0 Version: 1.62.2 Modules
| |||||||||||||||
| 3324 | "C:\Users\admin\Desktop\rclone\rclone.exe" sync ":http:/meta.7z" "C:\Users\admin\Desktop" --http-url https://bactio.skizzle.cyou/ --tpslimit 1.0 --tpslimit-burst 3 | C:\Users\admin\Desktop\rclone\rclone.exe | Rookie-PCVR_v1.2.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rsync for cloud storage Exit code: 0 Version: 1.62.2 Modules
| |||||||||||||||
| 3928 | "C:\Users\admin\Desktop\Rookie-PCVR_v1.2.exe" | C:\Users\admin\Desktop\Rookie-PCVR_v1.2.exe | explorer.exe | ||||||||||||
User: admin Company: Rookie.WTF Integrity Level: MEDIUM Description: AndroidSideloader Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 3980 | "7z.exe" x "C:\Users\admin\Desktop\rclone.zip" -y -o"C:\Users\admin\Desktop" | C:\Users\admin\Desktop\7z.exe | — | Rookie-PCVR_v1.2.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
Total events
9 807
Read events
9 759
Write events
46
Delete events
2
Modification events
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3928) Rookie-PCVR_v1.2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3928) Rookie-PCVR_v1.2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
6
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\Desktop\rclone\vrp.download.config | — | |
MD5:— | SHA256:— | |||
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\AppData\Local\Temp\Cab3DA9.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:CF798460618288C732F4A1C695EAB5F4 | SHA256:CA1A40BA2F337ACFE1B6CBC630C5DBFE0651B1741A93C027C0798ED4E32468A7 | |||
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\AppData\Local\Temp\Tar3DAA.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\Desktop\vrp-public-pcvr.json | binary | |
MD5:813A9C8E88601C6DD32F134768CB9662 | SHA256:DE07FA47BC4C7C1AB648427FF6452BF02A22375BE48DE53E57BA9B9E8342B12C | |||
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\AppData\Local\Rookie.WTF\Rookie-PCVR_v1.2.exe_Url_fqnwn3o24hpqc0g4zrf1hgvobeh01prg\2.0.0.0\ti0iysts.newcfg | xml | |
MD5:BB1729349ABA8613308A187A3EAB0C41 | SHA256:570A51B6CEFD737166BAAC14AF4F5A5AC61656155C034187AFE6529E03AED955 | |||
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\AppData\Local\Rookie.WTF\Rookie-PCVR_v1.2.exe_Url_fqnwn3o24hpqc0g4zrf1hgvobeh01prg\2.0.0.0\user.config | xml | |
MD5:BB1729349ABA8613308A187A3EAB0C41 | SHA256:570A51B6CEFD737166BAAC14AF4F5A5AC61656155C034187AFE6529E03AED955 | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\Rookie-PCVR_v1.2.exe | executable | |
MD5:6F7671B6F4C5583653891C8CCD85411B | SHA256:931CCA55BD22449CD1128FE9537157627DFBD63A3DBA9AB86C510CC9C52814D9 | |||
| 3928 | Rookie-PCVR_v1.2.exe | C:\Users\admin\Desktop\rclone\vrp.upload.config | text | |
MD5:F06F4B0A6775A75A4EC9904520EC8D91 | SHA256:1A47B327964843C1C614F7296D6939B69A36A9A0395179C13FC1BDC9D5F05932 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3928 | Rookie-PCVR_v1.2.exe | GET | 200 | 46.228.146.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?cbff904c349f9121 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3928 | Rookie-PCVR_v1.2.exe | 185.165.171.105:443 | wiki.vrpirates.club | Flokinet Ltd | SC | unknown |
3928 | Rookie-PCVR_v1.2.exe | 46.228.146.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
3928 | Rookie-PCVR_v1.2.exe | 95.217.6.16:443 | downloads.rclone.org | Hetzner Online GmbH | FI | unknown |
3928 | Rookie-PCVR_v1.2.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
3928 | Rookie-PCVR_v1.2.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
3324 | rclone.exe | 188.114.96.3:443 | bactio.skizzle.cyou | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wiki.vrpirates.club |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
downloads.rclone.org |
| unknown |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
bactio.skizzle.cyou |
| unknown |