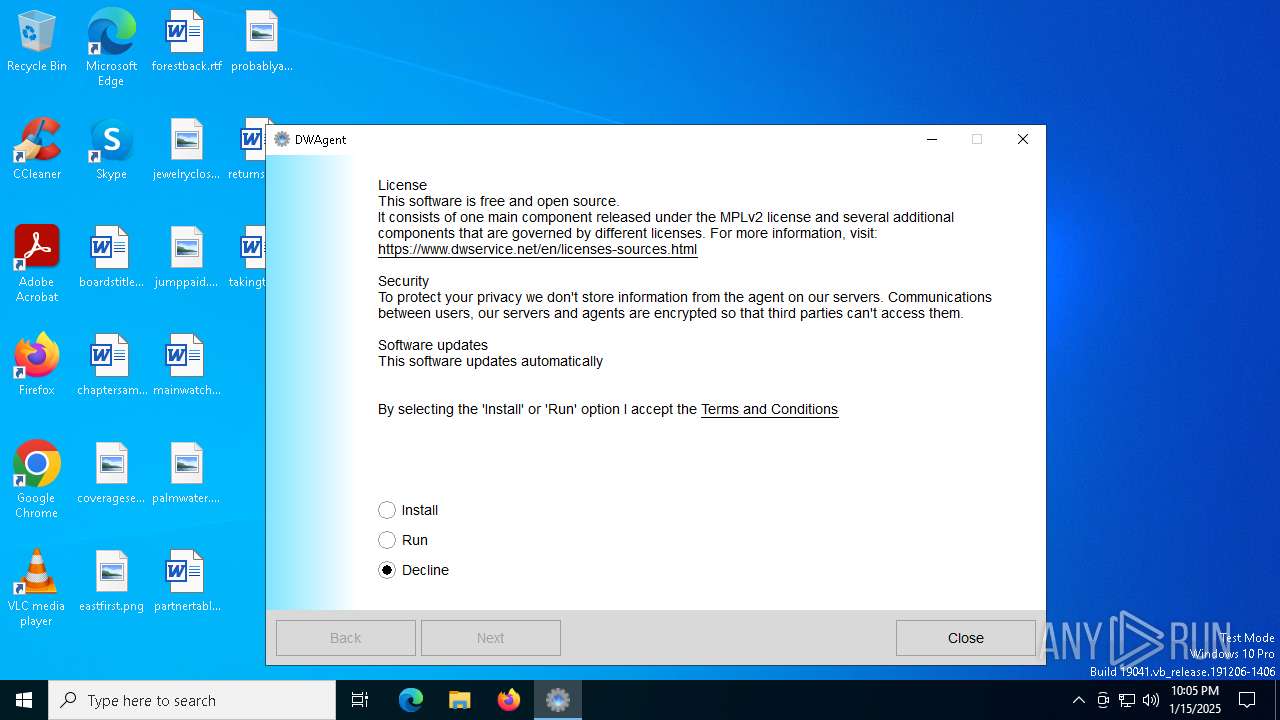
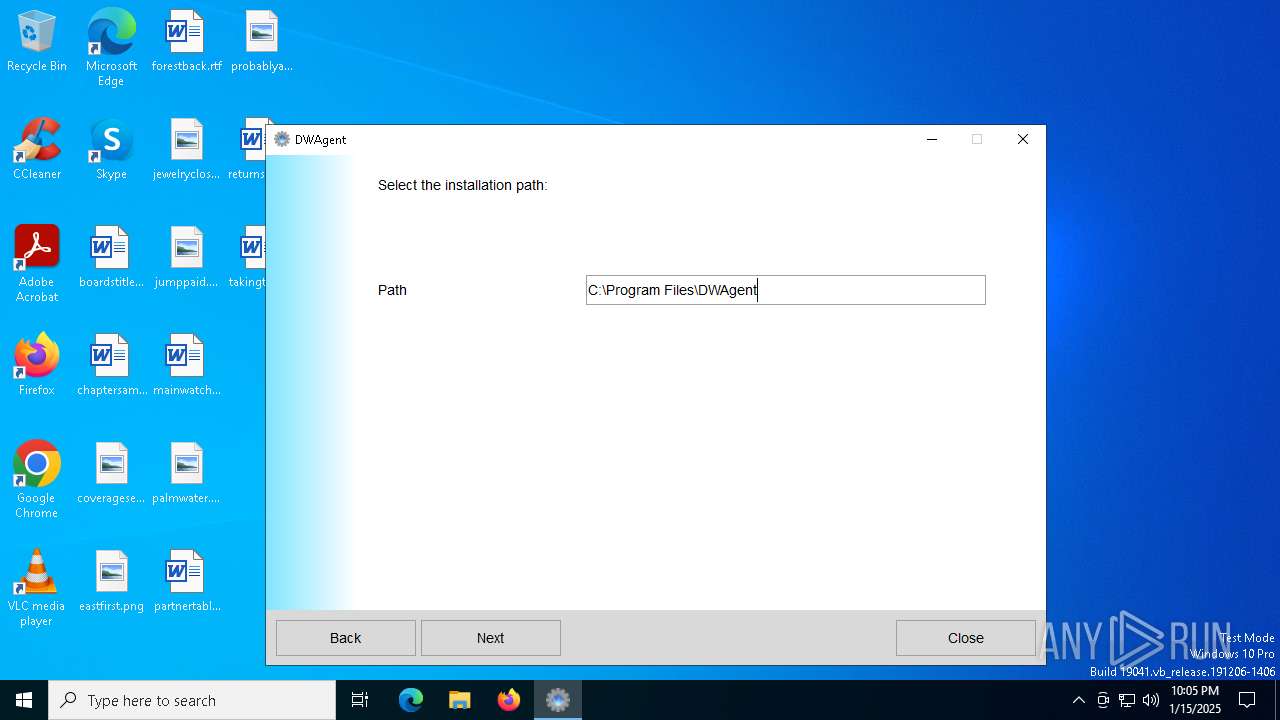
| File name: | dwagent (2).exe |
| Full analysis: | https://app.any.run/tasks/4426fbbb-70a5-420a-80da-54c63e88f6ca |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2025, 22:05:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 8 sections |
| MD5: | B10D12B91357828FA4FF83729A3840F3 |
| SHA1: | 9CE3B4ABCDC314449A341A19579578DFAF38105A |
| SHA256: | 04313637D81F1EE9D55BBF82713C89BA78C8C593C5ED2289BF5B79A51C8D227E |
| SSDEEP: | 98304:meMy7RXVGMBpsjMOher5vw+Owk0tBVIFcGIw9OWUEUVmnUBzdskLBOtf0CQJ41Sb:fQ78S5wkxk5Dp9Jb9V1i3DhA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- dwagent (2).exe (PID: 6516)
- dwagent.exe (PID: 3820)
Process drops legitimate windows executable
- dwagent (2).exe (PID: 6516)
- dwagent.exe (PID: 3820)
Process drops python dynamic module
- dwagent (2).exe (PID: 6516)
- dwagent.exe (PID: 3820)
The process drops C-runtime libraries
- dwagent (2).exe (PID: 6516)
- dwagent.exe (PID: 3820)
Loads Python modules
- dwagent.exe (PID: 7160)
- dwagent.exe (PID: 3820)
- dwagent.exe (PID: 6756)
- dwagent.exe (PID: 5404)
Reads security settings of Internet Explorer
- dwagent (2).exe (PID: 6516)
- dwagent (2).exe (PID: 848)
- dwaglnc.exe (PID: 2280)
Application launched itself
- dwagent (2).exe (PID: 6516)
Starts CMD.EXE for commands execution
- dwagent.exe (PID: 3820)
- dwagent.exe (PID: 6756)
- dwagent.exe (PID: 5404)
- dwagent.exe (PID: 7160)
Executes as Windows Service
- dwagsvc.exe (PID: 6748)
INFO
Checks supported languages
- dwagent (2).exe (PID: 6516)
- dwagent.exe (PID: 7160)
- dwagent (2).exe (PID: 848)
- dwagent.exe (PID: 3820)
- dwaglnc.exe (PID: 2280)
- dwagsvc.exe (PID: 4328)
- dwagsvc.exe (PID: 1344)
- dwagsvc.exe (PID: 6628)
- dwagsvc.exe (PID: 712)
- dwagent.exe (PID: 5404)
- dwagsvc.exe (PID: 2736)
Process checks computer location settings
- dwagent (2).exe (PID: 6516)
- dwagent (2).exe (PID: 848)
Create files in a temporary directory
- dwagent (2).exe (PID: 6516)
- dwagent.exe (PID: 7160)
- dwagent.exe (PID: 3820)
Reads the computer name
- dwagent (2).exe (PID: 6516)
- dwagent.exe (PID: 7160)
- dwagent.exe (PID: 3820)
- dwagent.exe (PID: 6756)
- dwaglnc.exe (PID: 2280)
- dwagsvc.exe (PID: 1344)
- dwagsvc.exe (PID: 6628)
- dwagsvc.exe (PID: 712)
The sample compiled with english language support
- dwagent (2).exe (PID: 6516)
- dwagent.exe (PID: 3820)
Python executable
- dwagent.exe (PID: 7160)
- dwagent.exe (PID: 3820)
- dwagent.exe (PID: 6756)
- dwagent.exe (PID: 5404)
The process uses the downloaded file
- dwagent (2).exe (PID: 6516)
Checks operating system version
- dwagent.exe (PID: 7160)
- dwagent.exe (PID: 3820)
- dwagent.exe (PID: 6756)
- dwagent.exe (PID: 5404)
Creates files in the program directory
- dwagent.exe (PID: 3820)
- dwagsvc.exe (PID: 6748)
- dwagent.exe (PID: 6756)
- dwagsvc.exe (PID: 712)
- dwagent.exe (PID: 5404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:11:18 12:45:44+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.3 |
| CodeSize: | 291328 |
| InitializedDataSize: | 355328 |
| UninitializedDataSize: | 26624 |
| EntryPoint: | 0x1490 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
171
Monitored processes
42
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | "C:\Program Files\DWAgent\native\dwagsvc.exe" installShortcuts | C:\Program Files\DWAgent\native\dwagsvc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 716 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | "C:\Users\admin\AppData\Local\Temp\dwagent (2).exe" "-asadmin=C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\\" | C:\Users\admin\AppData\Local\Temp\dwagent (2).exe | dwagent (2).exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 900 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\DWAgent\native\dwagsvc.exe" installShortcuts" | C:\Windows\System32\cmd.exe | — | dwagent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | "C:\Program Files\DWAgent\native\dwagsvc.exe" installService | C:\Program Files\DWAgent\native\dwagsvc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\DWAgent\native\dwagsvc.exe" removeAutoRun" | C:\Windows\System32\cmd.exe | — | dwagent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | "C:\Program Files\DWAgent\native\dwaglnc.exe" systray | C:\Program Files\DWAgent\native\dwaglnc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2612 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\DWAgent\native\dwagsvc.exe" installAutoRun" | C:\Windows\System32\cmd.exe | — | dwagent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 749
Read events
2 743
Write events
5
Delete events
1
Modification events
| (PID) Process: | (4328) dwagsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | DWAgentMon |
Value: | |||
| (PID) Process: | (7048) dwagsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | DWAgentMon |
Value: "C:\Program Files\DWAgent\native\dwaglnc.exe" systray | |||
| (PID) Process: | (712) dwagsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\DWAgent |
| Operation: | write | Name: | DisplayName |
Value: DWAgent | |||
| (PID) Process: | (712) dwagsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\DWAgent |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\DWAgent\ui\images\logo.ico | |||
| (PID) Process: | (712) dwagsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\DWAgent |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\DWAgent | |||
| (PID) Process: | (712) dwagsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\DWAgent |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\DWAgent\native\dwaglnc.exe" uninstall | |||
Executable files
91
Suspicious files
1 354
Text files
163
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\win.7z | — | |
MD5:— | SHA256:— | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\runtimepy2.7z | — | |
MD5:— | SHA256:— | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\runtimepy3.7z | — | |
MD5:— | SHA256:— | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\installer.py | text | |
MD5:9CEE6D24FAC8EFF02BBC698E9F88D21F | SHA256:0C8D48E98358B4BDA521564AD2AF73E733C94E79DABD28843BFFBAEF1B602EDE | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\communication.py | text | |
MD5:BBA6D4707661D3C5C085E3FEBB490D64 | SHA256:FA57CA1D9838278D17BC088F1ED66DDAE9FD60F4246FF753B47EF290A14DEECD | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\detectinfo.py | text | |
MD5:401F48BE24D349632A2438B5EC3B606E | SHA256:184A44033F071547A6077630458303A2729784AB10208ECC95F6F7F59906835F | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\cacerts.pem | text | |
MD5:75E9EBCEDD501B1FD93A3BB7C5F68A59 | SHA256:D309171C54A3C5ABE71A910EFC3F48D0586B94AB9D3AB029DED76B36D72DDF5E | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\resources.py | text | |
MD5:EFC381B9D9180DF5072CDC0EA6EE47EF | SHA256:EA61BC4453D02C8BD29921C329452038D253873EFD55A6A40C298B54680C813D | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\native.py | text | |
MD5:CA4D0231BE63091F5BFA1E25B479C36E | SHA256:FFB87E22348273AA6C4B007837535FAB5AE0BE57AC202DA3752ADF1455F8F07A | |||
| 6516 | dwagent (2).exe | C:\Users\admin\AppData\Local\Temp\dwagent (2)20250115220511\ui\gdi.py | text | |
MD5:332AC5D315D125781BF7AEF25397F252 | SHA256:32CE7ABEC3A75A2F1D9C2B92E3FB139C8249AD91DF04CB0F5632C16C85C74748 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
40
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6176 | backgroundTaskHost.exe | GET | 200 | 23.51.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 2.19.198.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6956 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6956 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1200 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6092 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 2.19.106.8:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |