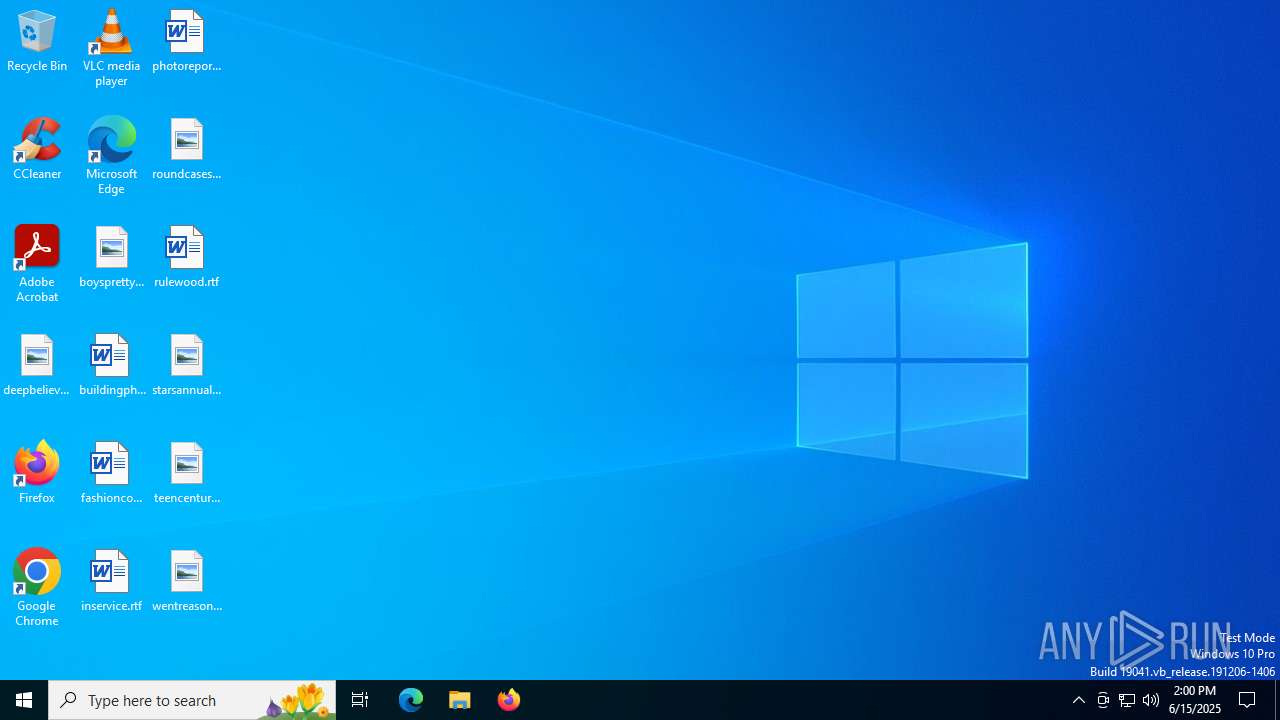
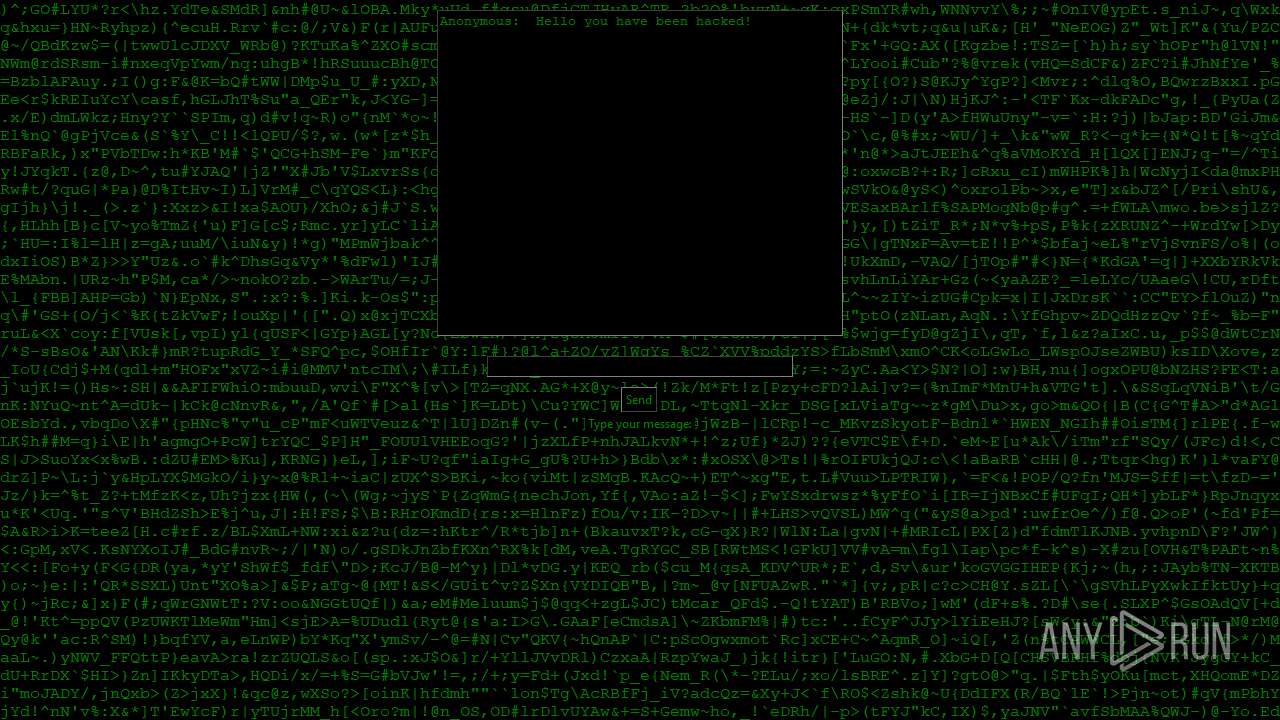
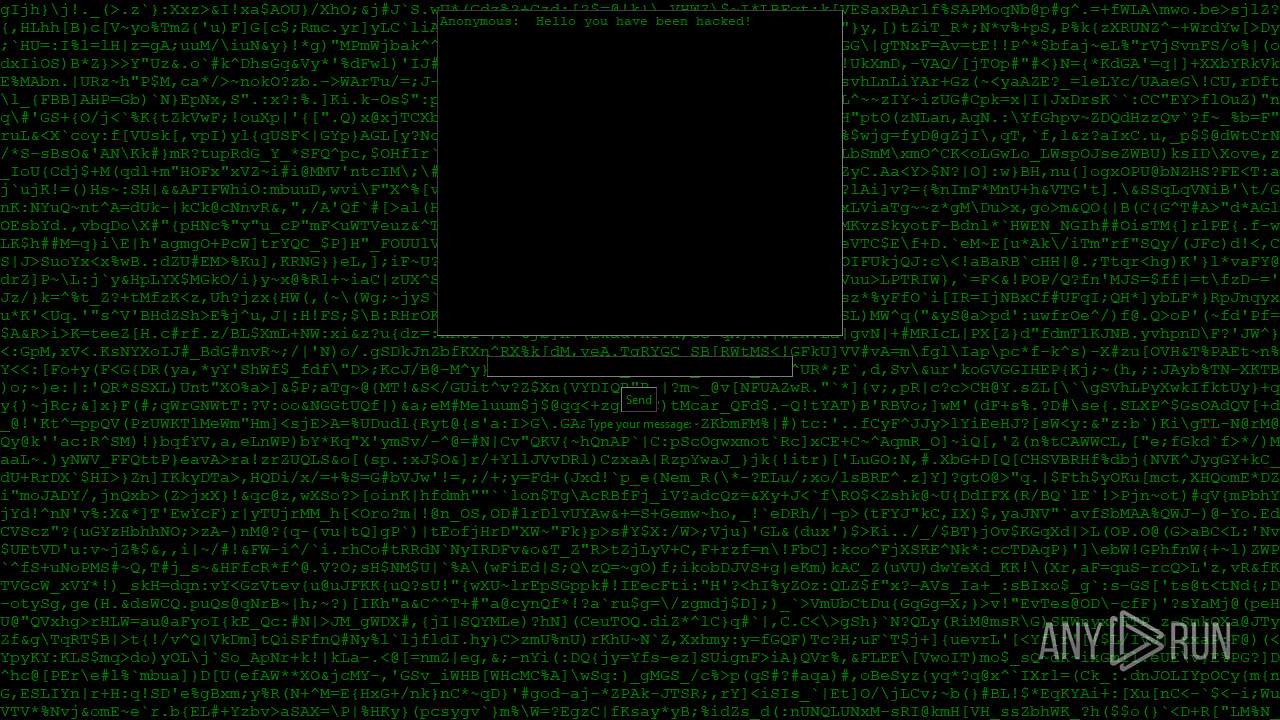
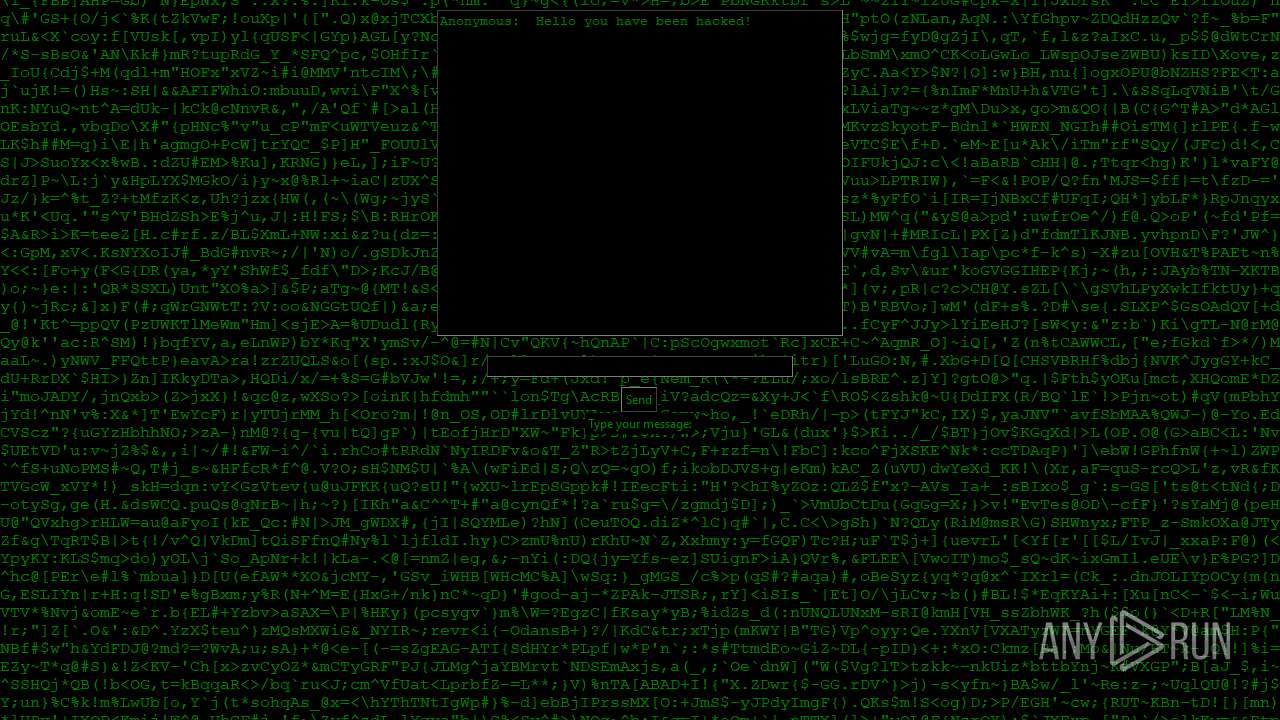
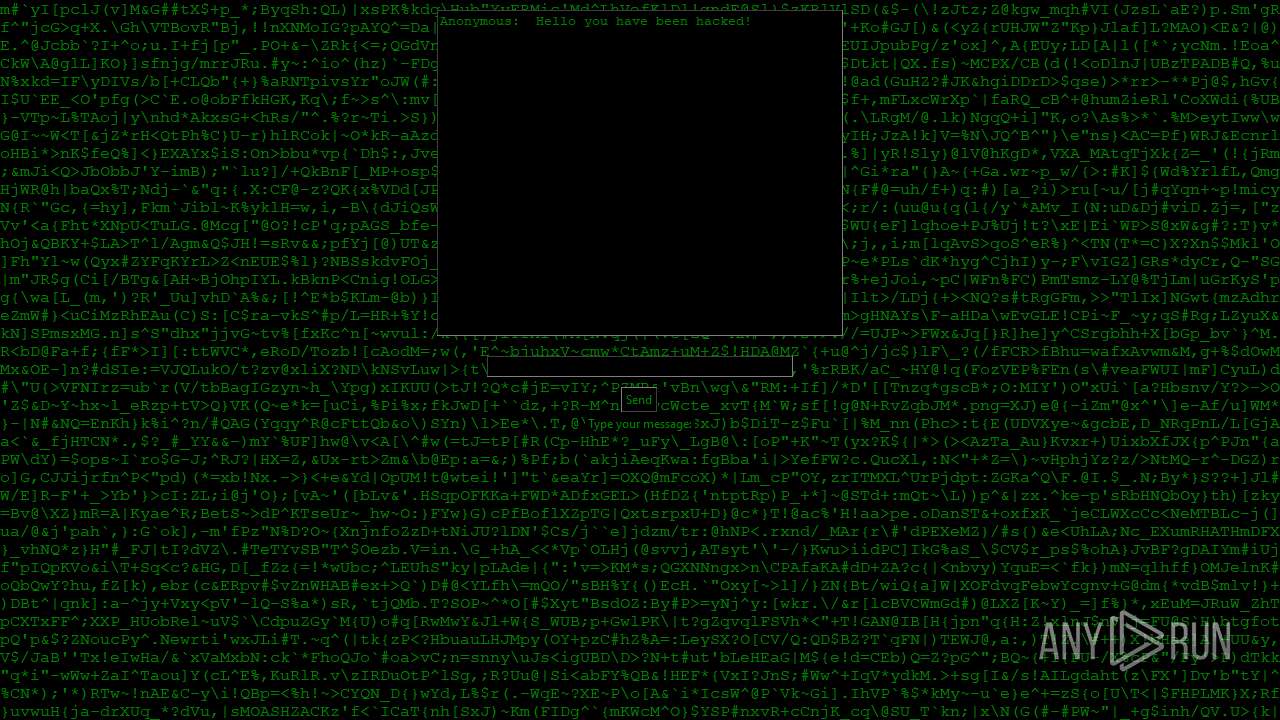
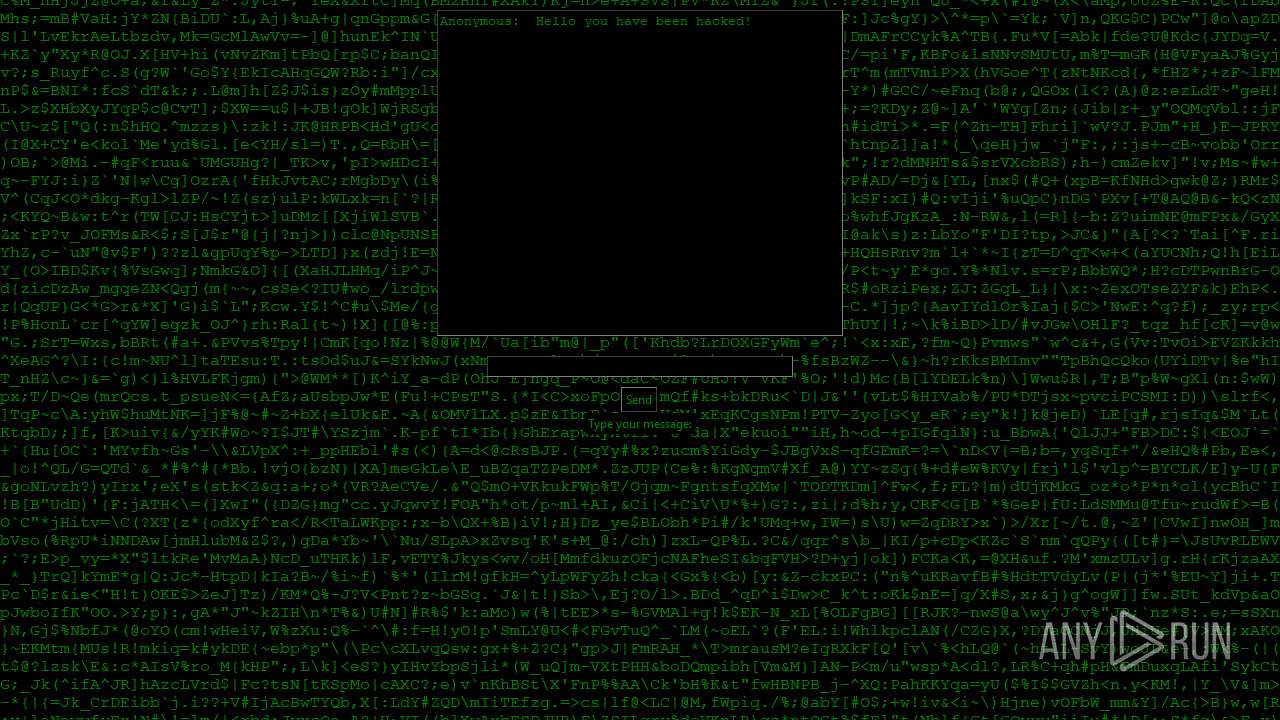
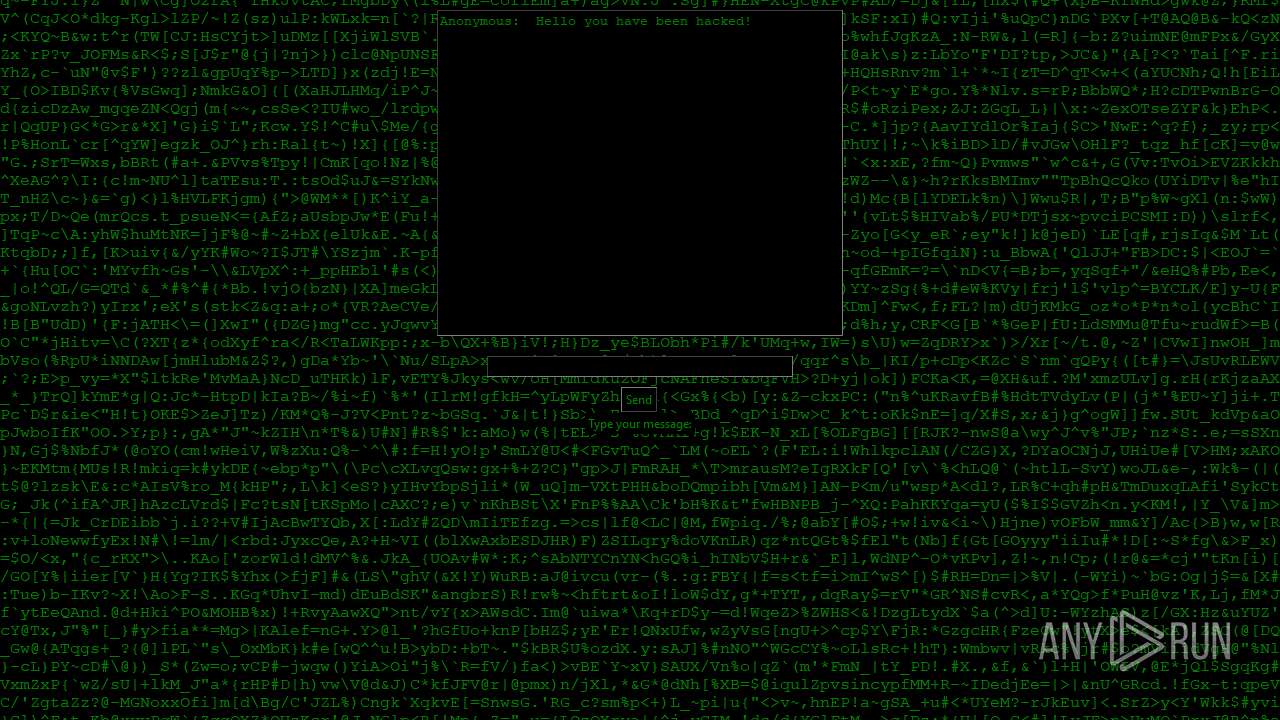
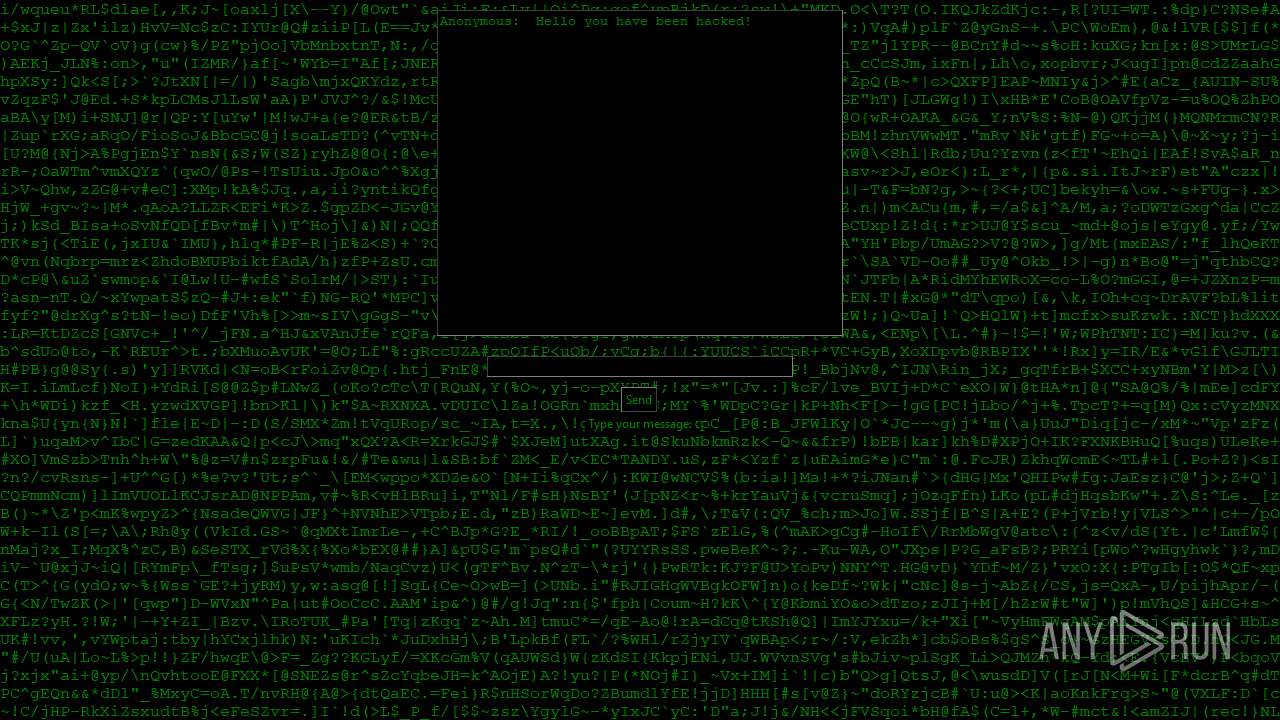
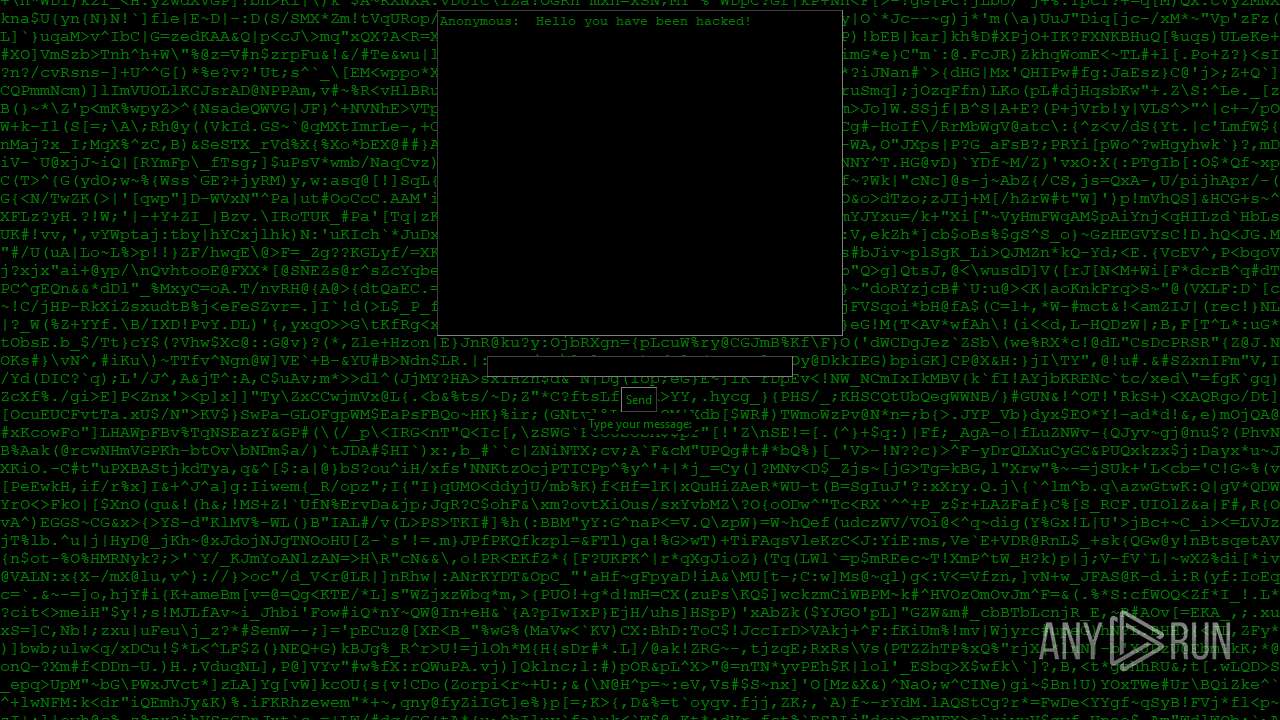
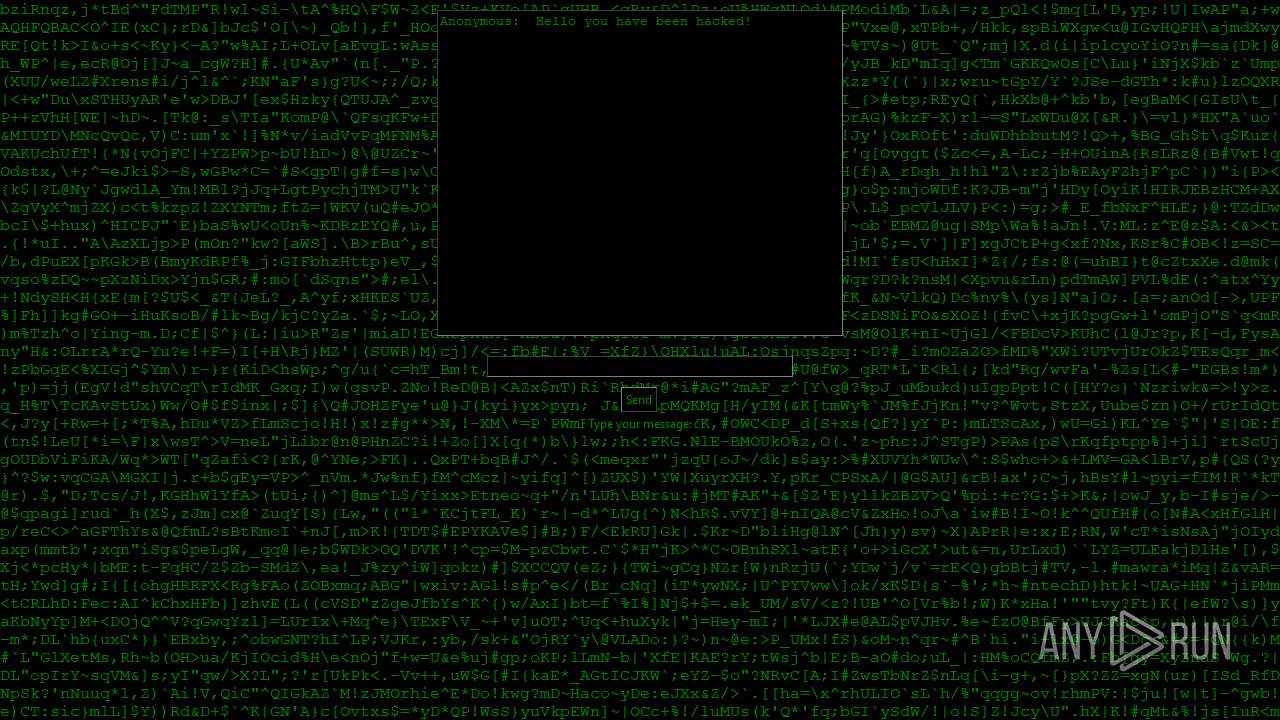
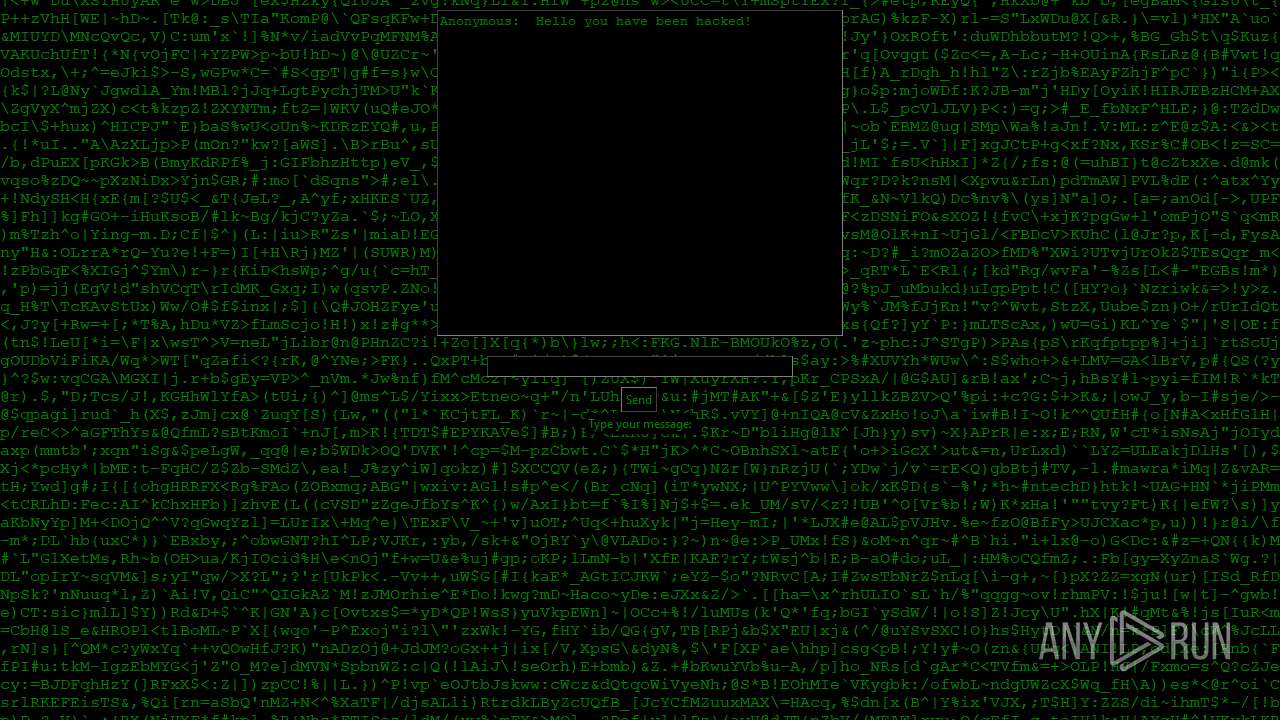
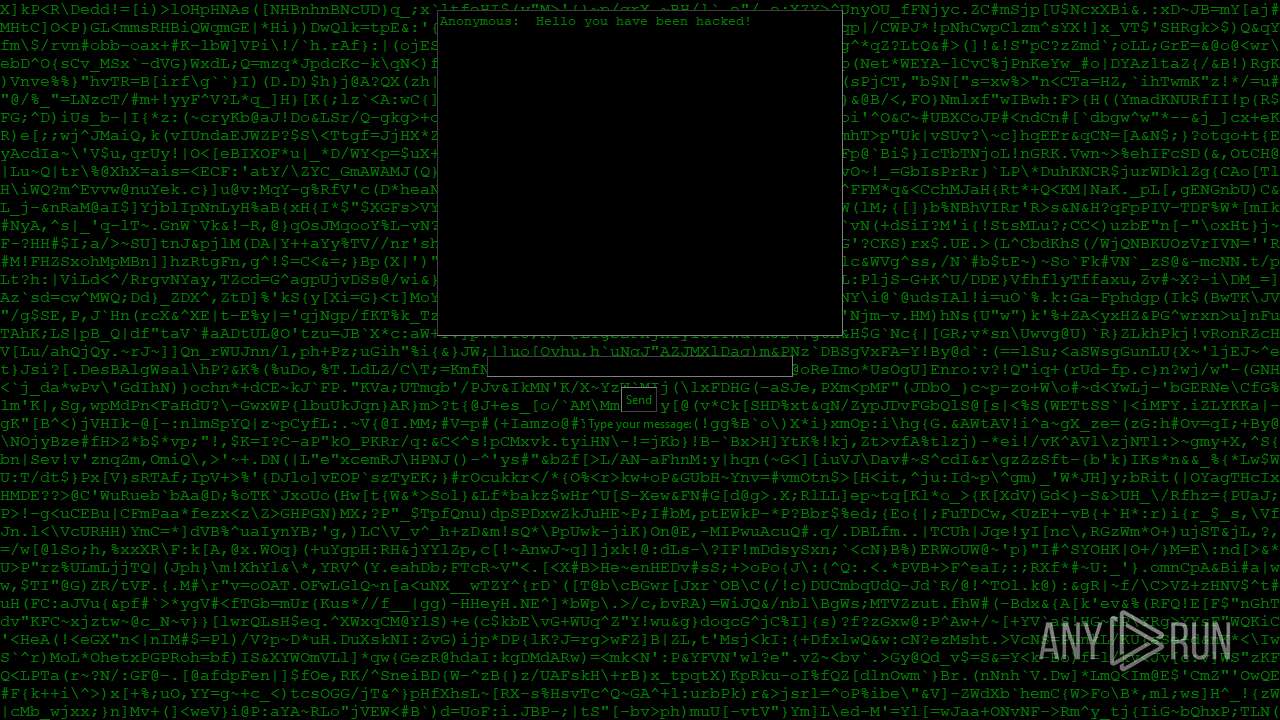
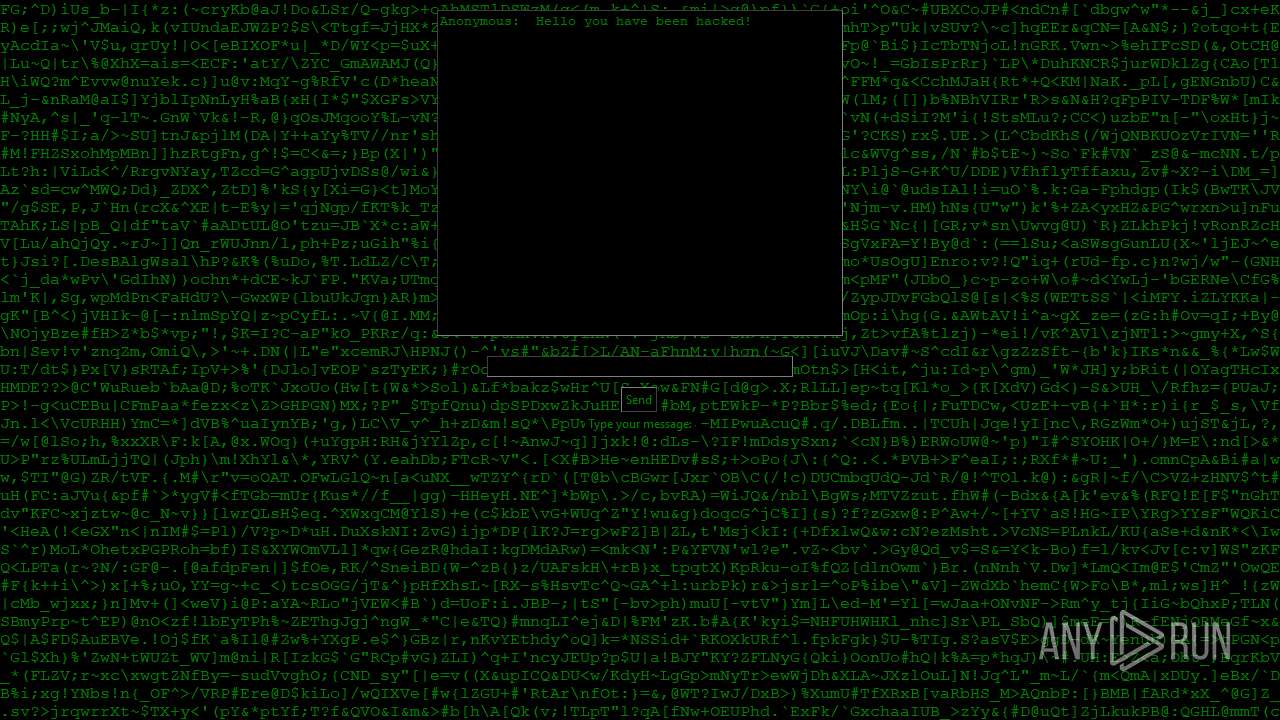
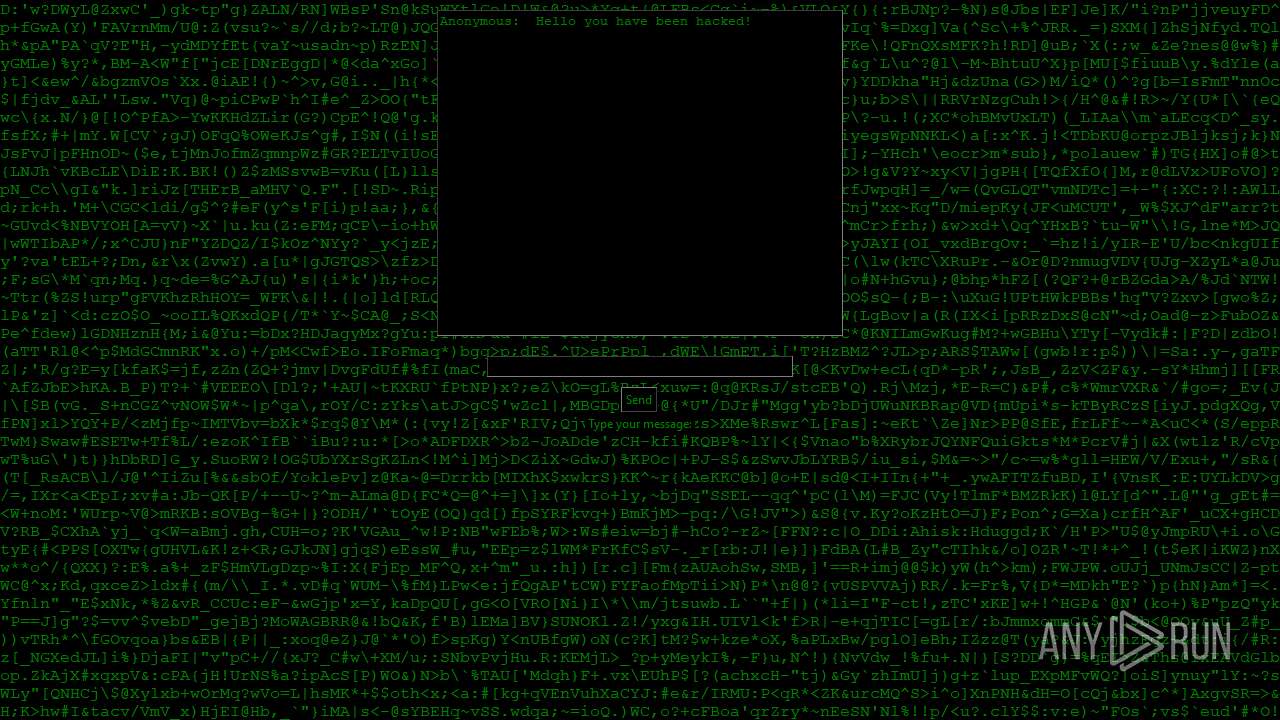
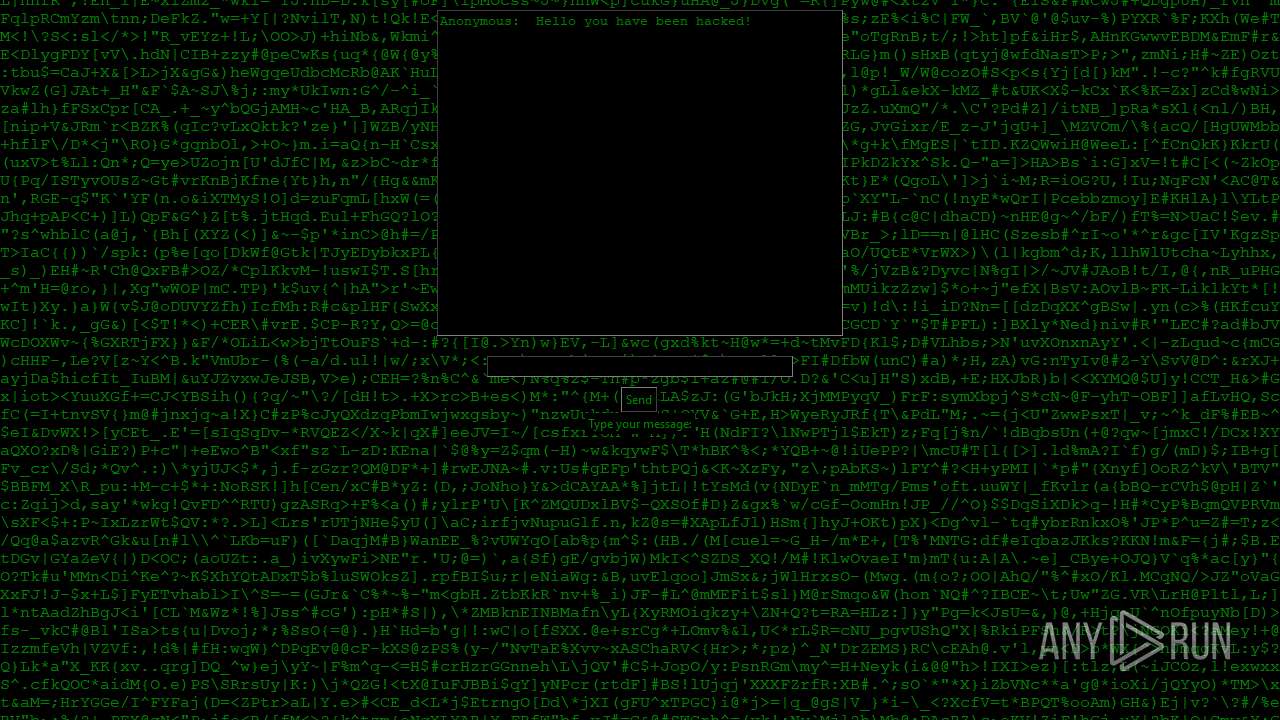
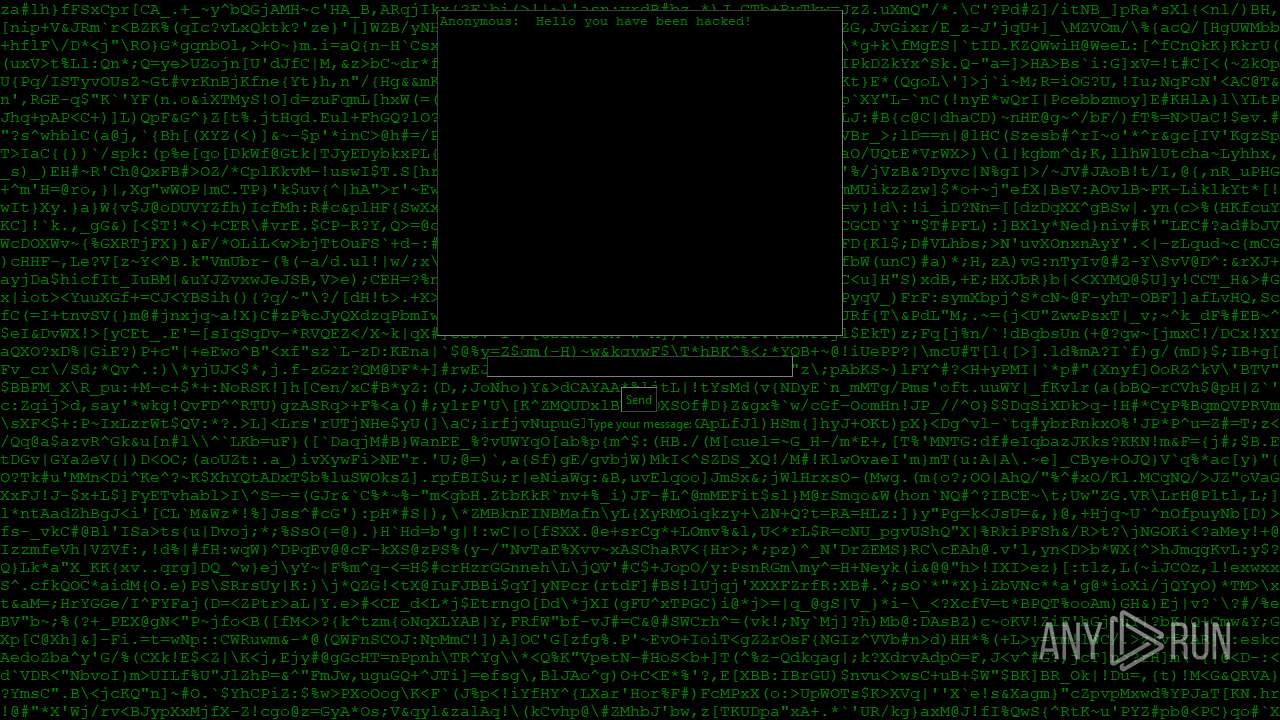
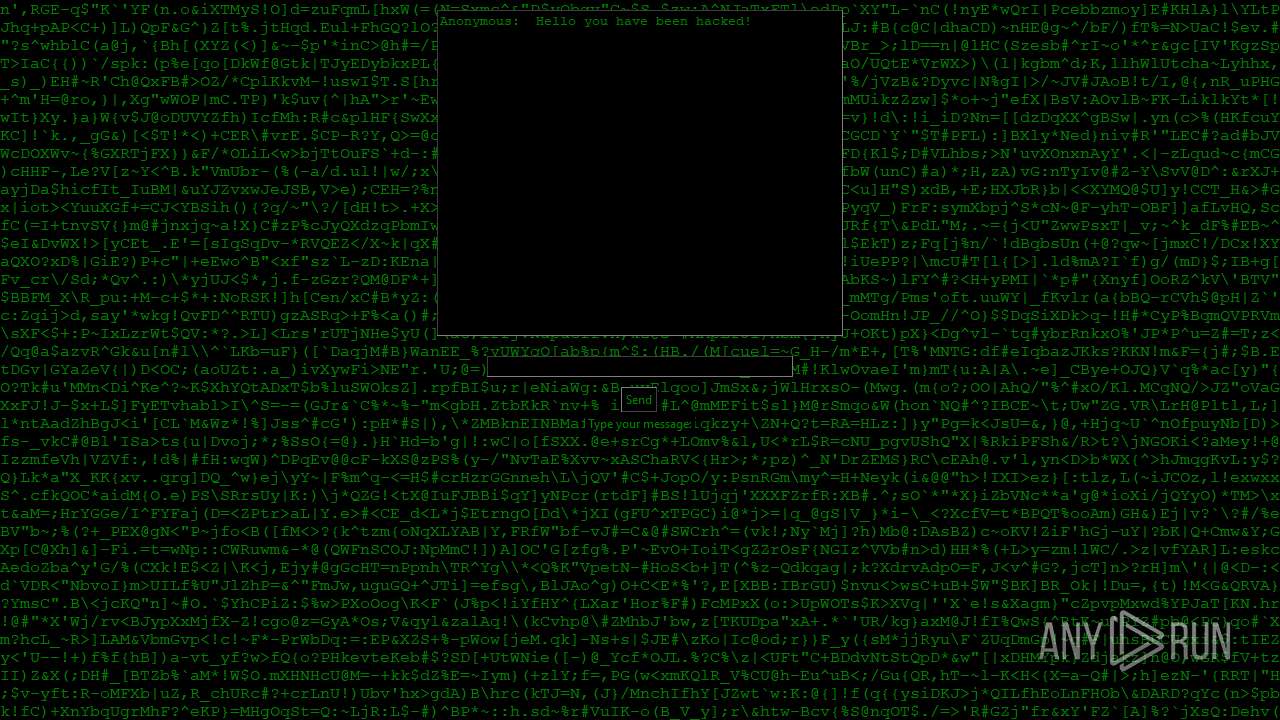
| File name: | PWNED.exe |
| Full analysis: | https://app.any.run/tasks/2accb478-fda7-49ab-a605-5c559c83eaf2 |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2025, 14:00:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | B3C12617F64B144D2BEFE191B58AF3C6 |
| SHA1: | BB2F1119CD870F24AF458B3BBB2828E5118B518F |
| SHA256: | 040BA3FA1E085839D17B9B4D2EE7C2C943293D85D0B9300B8F587DA1DEDD7E97 |
| SSDEEP: | 98304:5bXl+Cz5heshxAp9lnsuD8+62qWXAz+lrEnzHtaMvZA4OFKAbYpB4RplQ94geo7R:aNeYXhji+GQ6xI45r+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- PWNED.exe (PID: 6640)
Executable content was dropped or overwritten
- PWNED.exe (PID: 6640)
The process drops C-runtime libraries
- PWNED.exe (PID: 6640)
Process drops legitimate windows executable
- PWNED.exe (PID: 6640)
There is functionality for taking screenshot (YARA)
- PWNED.exe (PID: 6640)
- PWNED.exe (PID: 1728)
Application launched itself
- PWNED.exe (PID: 6640)
Loads Python modules
- PWNED.exe (PID: 1728)
INFO
Checks supported languages
- PWNED.exe (PID: 6640)
- PWNED.exe (PID: 1728)
The sample compiled with english language support
- PWNED.exe (PID: 6640)
Reads the computer name
- PWNED.exe (PID: 6640)
- PWNED.exe (PID: 1728)
PyInstaller has been detected (YARA)
- PWNED.exe (PID: 6640)
- PWNED.exe (PID: 1728)
Create files in a temporary directory
- PWNED.exe (PID: 6640)
Reads the software policy settings
- slui.exe (PID: 1180)
Checks proxy server information
- slui.exe (PID: 1180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:01:05 20:48:58+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.34 |
| CodeSize: | 165888 |
| InitializedDataSize: | 302080 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb310 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
134
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1180 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1728 | "C:\Users\admin\Desktop\PWNED.exe" | C:\Users\admin\Desktop\PWNED.exe | — | PWNED.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6640 | "C:\Users\admin\Desktop\PWNED.exe" | C:\Users\admin\Desktop\PWNED.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 645
Read events
3 645
Write events
0
Delete events
0
Modification events
Executable files
57
Suspicious files
3
Text files
920
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\_decimal.pyd | executable | |
MD5:692C751A1782CC4B54C203546F238B73 | SHA256:C70F05F6BC564FE400527B30C29461E9642FB973F66EEC719D282D3D0B402F93 | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\_bz2.pyd | executable | |
MD5:A62207FC33140DE460444E191AE19B74 | SHA256:EBCAC51449F323AE3AE961A33843029C34B6A82138CCD9214CF99F98DD2148C2 | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\_ctypes.pyd | executable | |
MD5:9B344F8D7CE5B57E397A475847CC5F66 | SHA256:B1214D7B7EFD9D4B0F465EC3463512A1CBC5F59686267030F072E6CE4B2A95CF | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\_queue.pyd | executable | |
MD5:06248702A6CD9D2DD20C0B1C6B02174D | SHA256:AC177CD84C12E03E3A68BCA30290BC0B8F173EEE518EF1FA6A9DCE3A3E755A93 | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\VCRUNTIME140.dll | executable | |
MD5:4585A96CC4EEF6AAFD5E27EA09147DC6 | SHA256:A8F950B4357EC12CFCCDDC9094CCA56A3D5244B95E09EA6E9A746489F2D58736 | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:F1534C43C775D2CCEB86F03DF4A5657D | SHA256:6E6BFDC656F0CF22FABBA1A25A42B46120B1833D846F2008952FE39FE4E57AB2 | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:71F1D24C7659171EAFEF4774E5623113 | SHA256:C45034620A5BB4A16E7DD0AFF235CC695A5516A4194F4FEC608B89EABD63EEEF | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:BFFFA7117FD9B1622C66D949BAC3F1D7 | SHA256:1EA267A2E6284F17DD548C6F2285E19F7EDB15D6E737A55391140CE5CB95225E | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:EA00855213F278D9804105E5045E2882 | SHA256:F2F74A801F05AB014D514F0F1D0B3DA50396E6506196D8BECCC484CD969621A6 | |||
| 6640 | PWNED.exe | C:\Users\admin\AppData\Local\Temp\_MEI66402\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:D584C1E0F0A0B568FCE0EFD728255515 | SHA256:3DE40A35254E3E0E0C6DB162155D5E79768A6664B33466BF603516F3743EFB18 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4680 | RUXIMICS.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
4680 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4680 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4680 | RUXIMICS.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |