analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| File name: | Kidux.rar |
| Full analysis: | https://app.any.run/tasks/4d566388-3e31-4952-a601-976f5aec3607 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 08:44:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DCD6497E0E57DE812F682D0D8F26B55B |
| SHA1: | 4D924CA6E0BFE51CAE581095CD01D3C92FB8B2D9 |
| SHA256: | 040101AFDC5FAB28BB054FEAF16C6DFD480D30E83404B337E09511B22F3F4336 |
| SSDEEP: | 49152:gn0dkNs1VGr67gFKi4AfhIv2hEhluKM6NSieiAqbzb9ehyluKupZeqbzb9ehn:gnmuso6MFNZwNQqhA27Qvfe2q |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3548)
Application was dropped or rewritten from another process
- Host del servicio Monitor.exe (PID: 4052)
- Microsoft Windows Protocol Services Host.exe (PID: 3672)
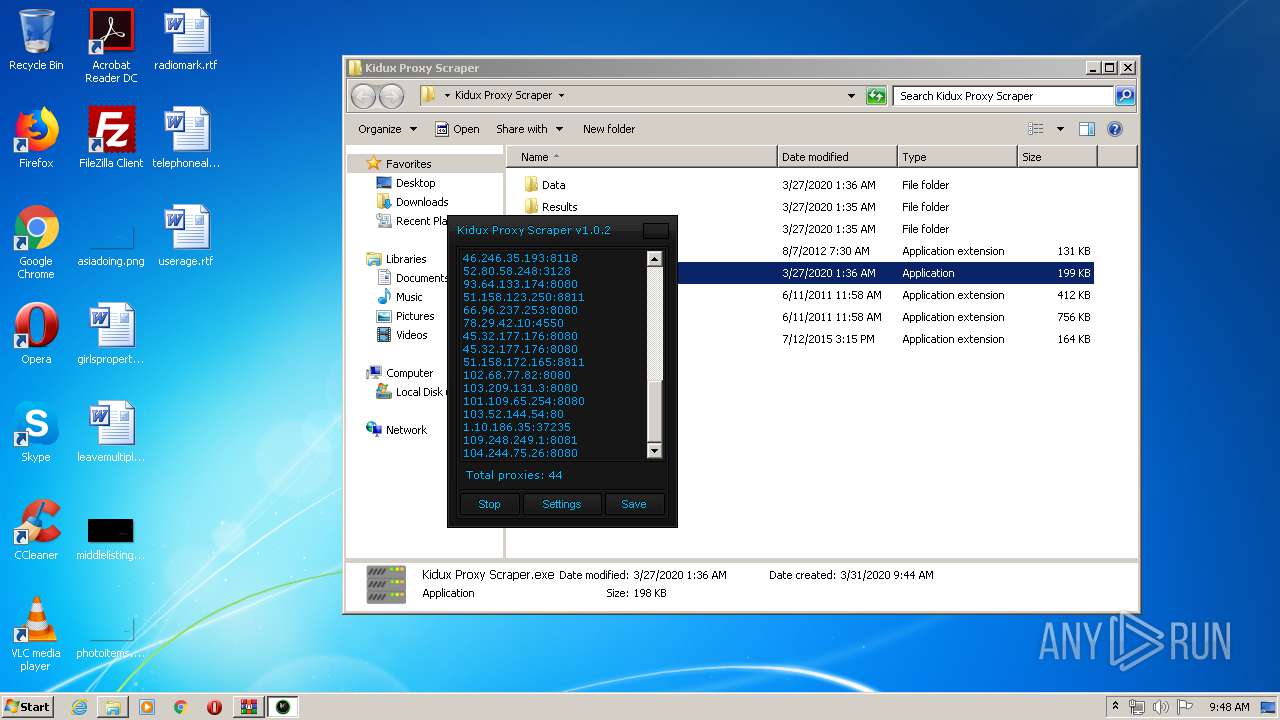
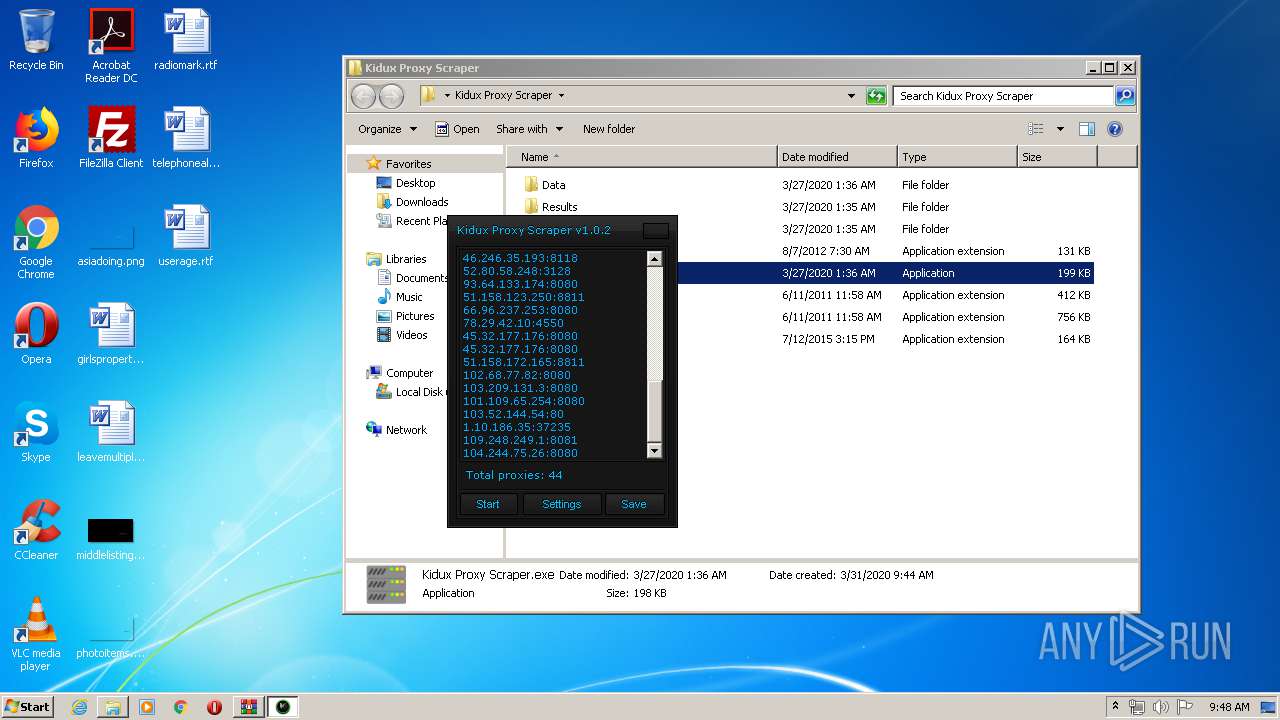
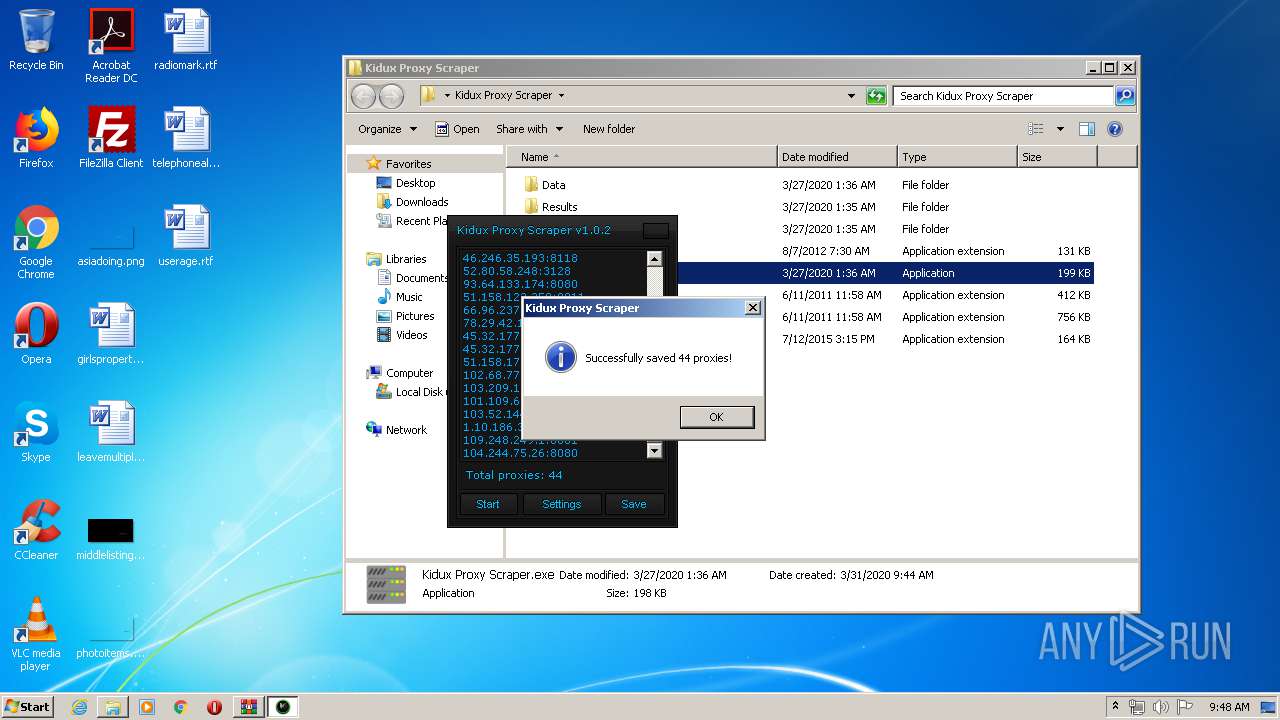
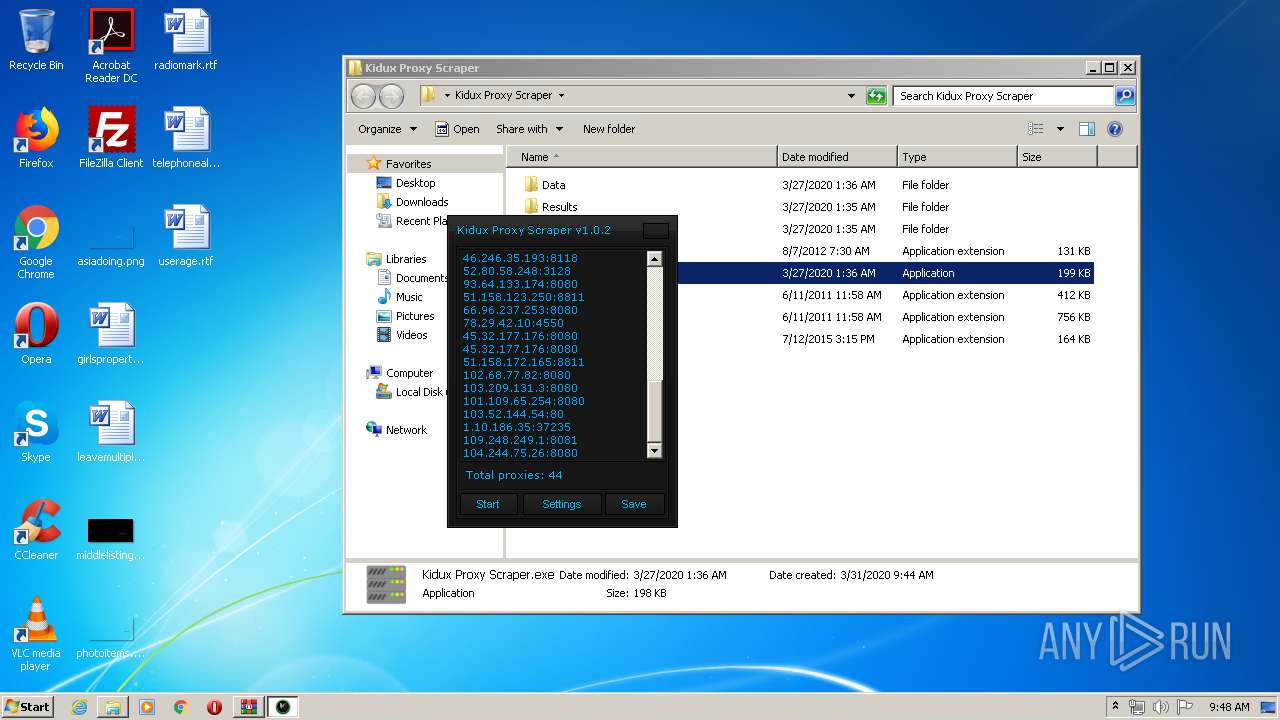
- Kidux Req.exe (PID: 2760)
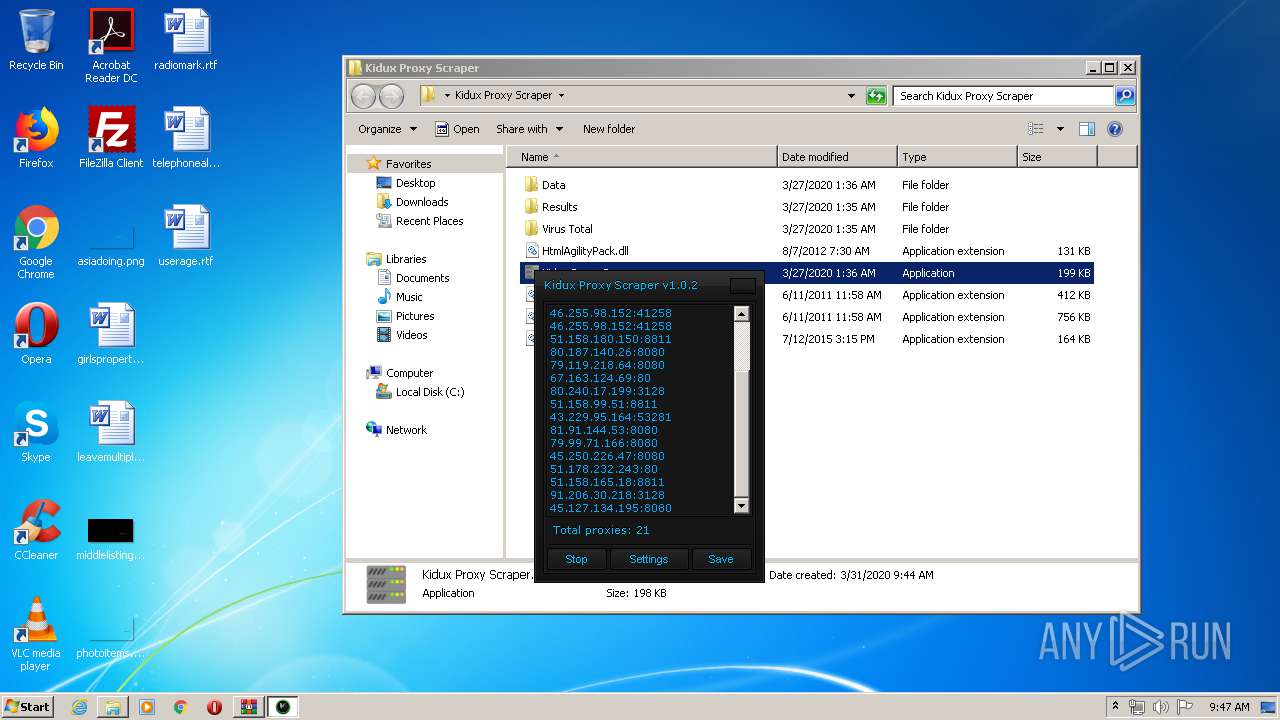
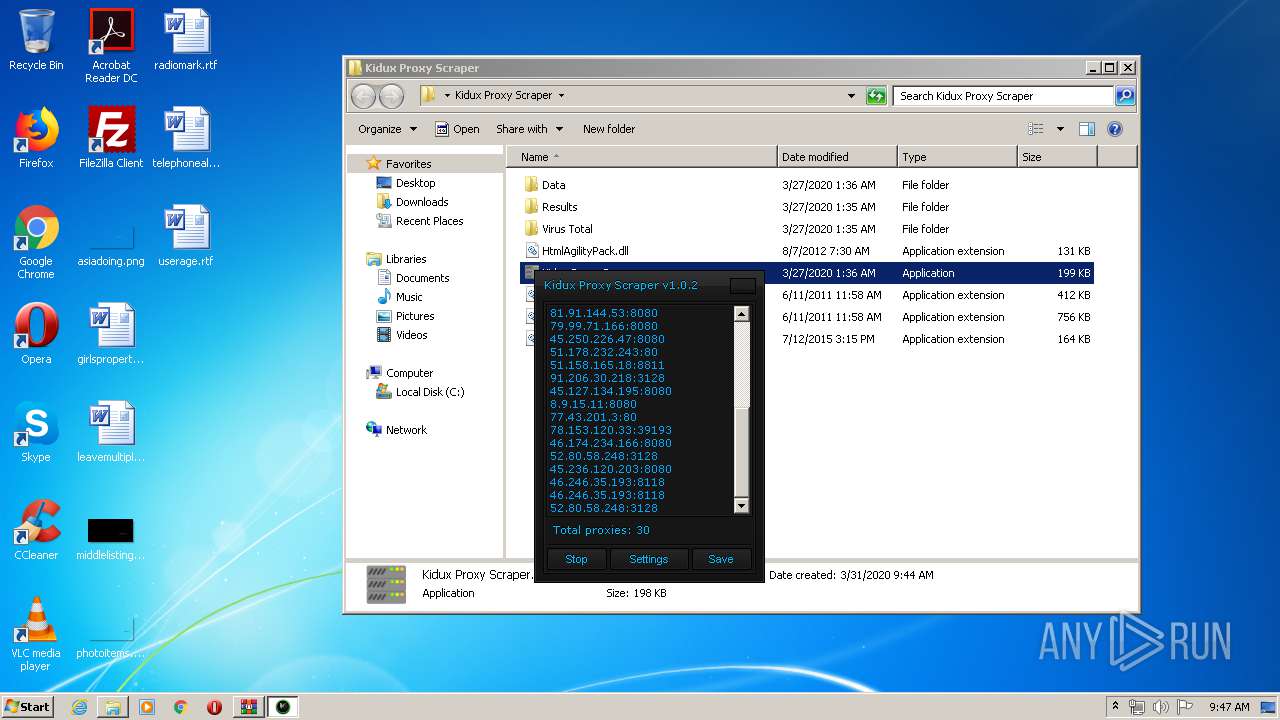
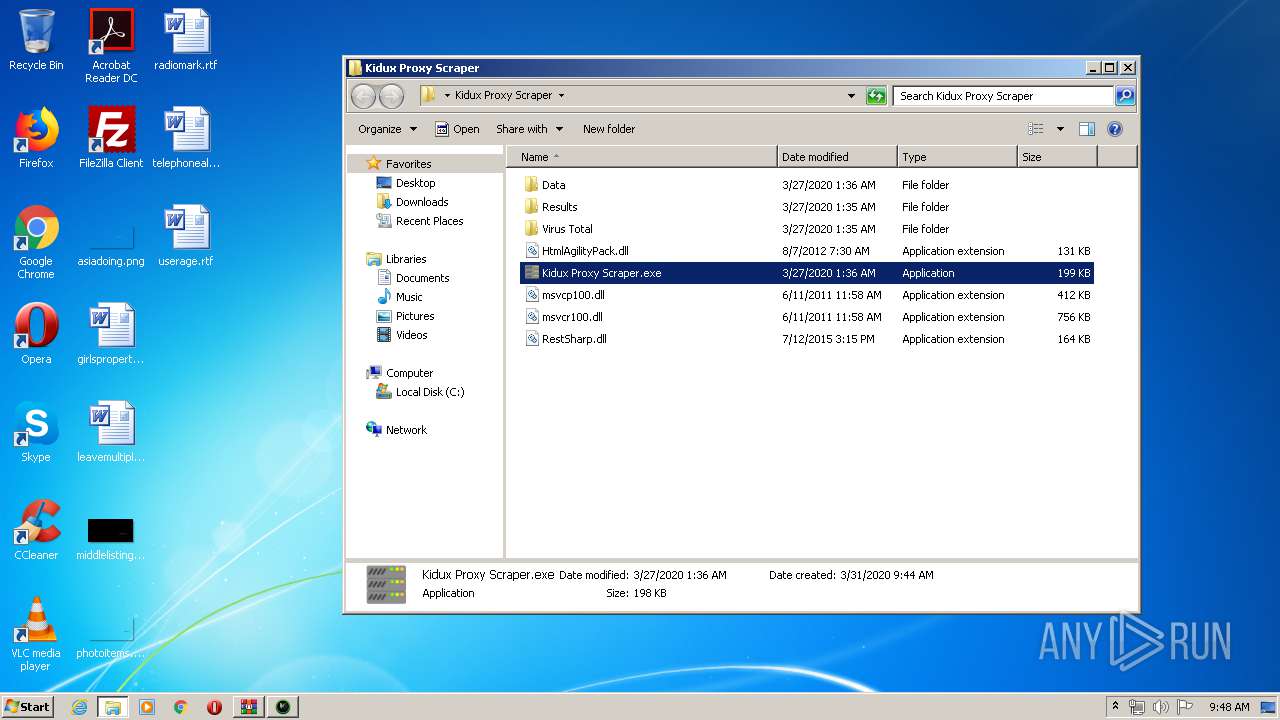
- Kidux Proxy Scraper.exe (PID: 3472)
Writes to a start menu file
- Kidux Proxy Scraper.exe (PID: 3472)
Connects to CnC server
- Kidux Req.exe (PID: 2760)
Changes settings of System certificates
- Kidux Req.exe (PID: 2760)
SUSPICIOUS
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 3892)
Creates files in the program directory
- Kidux Proxy Scraper.exe (PID: 3472)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3892)
- Kidux Proxy Scraper.exe (PID: 3472)
Creates files in the Windows directory
- Kidux Proxy Scraper.exe (PID: 3472)
Creates files in the user directory
- Kidux Proxy Scraper.exe (PID: 3472)
Adds / modifies Windows certificates
- Kidux Req.exe (PID: 2760)
INFO
Manual execution by user
- Kidux Proxy Scraper.exe (PID: 3472)
- NOTEPAD.EXE (PID: 2440)
Reads settings of System Certificates
- Kidux Req.exe (PID: 2760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
46
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3892 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Kidux.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.60.0 Modules
| |||||||||||||||
| 3548 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
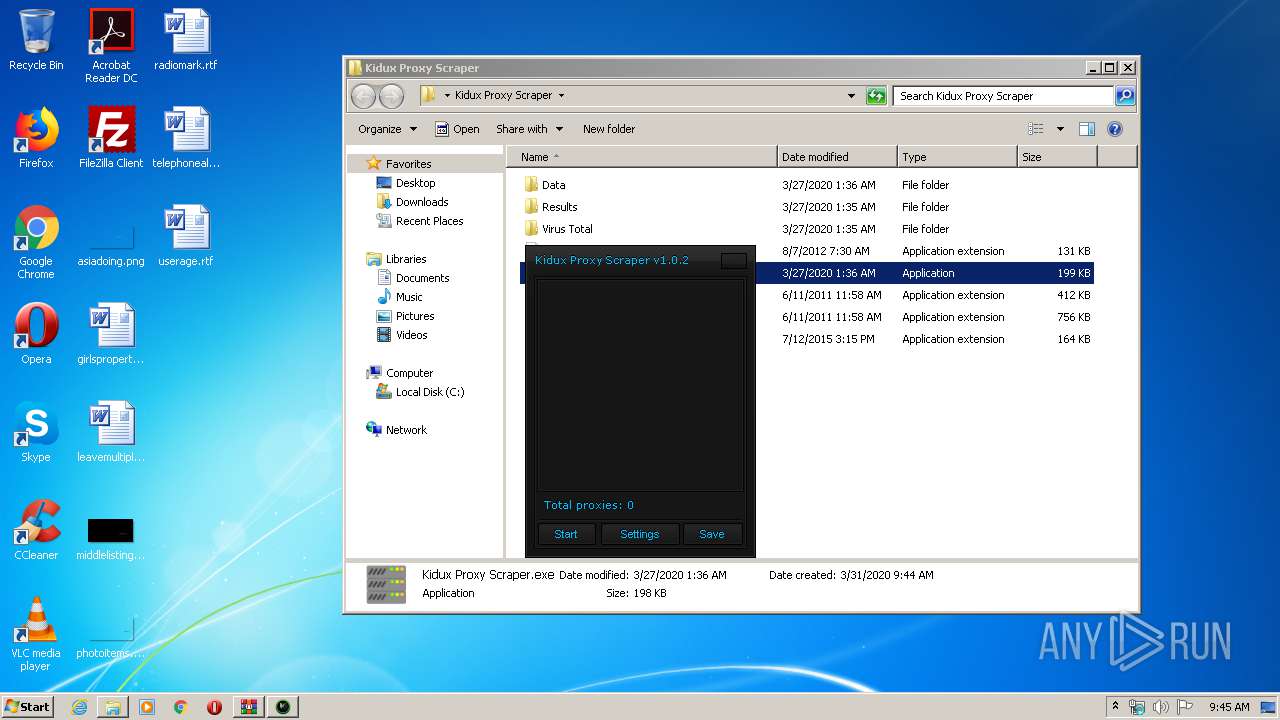
| 3472 | "C:\Users\admin\Desktop\Kidux Proxy Scraper\Kidux Proxy Scraper.exe" | C:\Users\admin\Desktop\Kidux Proxy Scraper\Kidux Proxy Scraper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: interface Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3672 | "C:\Windows\Program Files (x86)\Microsoft Host Interface\Data\Microsoft Windows Protocol Services Host.exe" {Arguments If Needed} | C:\Windows\Program Files (x86)\Microsoft Host Interface\Data\Microsoft Windows Protocol Services Host.exe | — | Kidux Proxy Scraper.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Microsoft Windows Protocol Services Host Version: 1.0.0.0 Modules
| |||||||||||||||
| 2760 | "C:\Users\admin\Desktop\Kidux Proxy Scraper\Data\Kidux Req.exe" {Arguments If Needed} | C:\Users\admin\Desktop\Kidux Proxy Scraper\Data\Kidux Req.exe | Kidux Proxy Scraper.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Kidux Proxy Scraper Version: 1.0.0.0 Modules
| |||||||||||||||
| 4052 | "C:\Windows\Program Files (x86)\Microsoft Host Interface\Data\Host del servicio Monitor.exe" | C:\Windows\Program Files (x86)\Microsoft Host Interface\Data\Host del servicio Monitor.exe | — | Microsoft Windows Protocol Services Host.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Microsoft Windows Protocol Monitor Version: 1.0.0.0 Modules
| |||||||||||||||
| 2440 | "C:\Windows\system32\NOTEPAD.EXE" C:\44 Parsed HTTP proxies with Kidux Proxy Scraper.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
36 505
Read events
6 303
Write events
0
Delete events
0
Modification events
Executable files
14
Suspicious files
12
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\geo.mmdb | — | |
MD5:— | SHA256:— | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\configs.gp | text | |
MD5:85744419544DAFDAE36CBDA9A6AF9E71 | SHA256:83F0E8AFEF0062A69BC6A1616DD5FDE2194AD6C4647BF128219DCE4DB595EC0C | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Kidux Proxy Scraper.exe | executable | |
MD5:C6A574413182F2464A4254E980C6FEF4 | SHA256:F21A7290E5E25843972285A0C811D930323D0EC864742442BC1327FF69F7D41F | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\urls.txt | text | |
MD5:4CC69F8FE5A6069C12BE5234A5EA14FD | SHA256:094919C37E1C7784BD89825E61DC5E298C73A8DDBF4D2F9C8FAFD80E868D679C | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\Kidux Req.exe | executable | |
MD5:932EDD3DF442AD62AF3CA8C8ED0B44D9 | SHA256:33043D752E3F68AEF12DFAB8AE7770132BE91B8C2A86335CFF5BA05670225E06 | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\RestSharp.dll | executable | |
MD5:07187F3DD0263CDCABA9C800444379A5 | SHA256:317690CB0B82E5632E132AA384843729CD31E24CCC4B1FA00BA8157CB8D82F7E | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\autosp.ini | text | |
MD5:0AB7386476BFD6E6A7FDCAA91DA04D4F | SHA256:BA4DB1C4843A36822F68556D4F2AC5B815F3E7B063D28D8905FD6084B594EC40 | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\ref.ref | text | |
MD5:EDF1E41F9FE226BE3E61845B747A2C6E | SHA256:C78BA0953491DCCBD7EE2B03CF6AE3A295676715D524B278345FBB31245FBCD5 | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\planetlab.txt | text | |
MD5:4AA755C53F5741125462955E02440DD1 | SHA256:B26C86587F82AE186D1860BD03F71858C74F2E1DBA624E7FF85A9DE67FE80D56 | |||
| 3892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3892.12101\Kidux Proxy Scraper\Data\HtmlAgilityPack.dll | executable | |
MD5:B768306987227D31BF07277C1AE65A57 | SHA256:DB48B1FEA16C5DA3B80CBDE4D351D614957240CA70213FA82B6A7535B02AAF28 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1 307
TCP/UDP connections
1 818
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2760 | Kidux Req.exe | CONNECT | — | 101.4.136.34:8080 | http://www.example.com:8080www.example.com:443 | CN | — | — | suspicious |
2760 | Kidux Req.exe | CONNECT | — | 101.4.136.34:80 | http://www.example.comwww.example.com:443 | CN | — | — | suspicious |
2760 | Kidux Req.exe | CONNECT | — | 102.129.249.120:8080 | http://www.example.com:8080www.example.com:443 | unknown | — | — | suspicious |
2760 | Kidux Req.exe | CONNECT | — | 103.119.146.37:80 | http://www.example.comwww.example.com:443 | unknown | — | — | unknown |
2760 | Kidux Req.exe | CONNECT | — | 103.125.253.251:8080 | http://www.example.com:8080www.example.com:443 | unknown | — | — | unknown |
2760 | Kidux Req.exe | CONNECT | — | 1.179.144.182:80 | http://www.example.comwww.example.com:443 | TH | — | — | unknown |
2760 | Kidux Req.exe | CONNECT | — | 103.111.199.18:8080 | http://www.example.com:8080www.example.com:443 | unknown | — | — | unknown |
2760 | Kidux Req.exe | CONNECT | — | 101.109.33.170:8080 | http://www.example.com:8080www.example.com:443 | TH | — | — | unknown |
2760 | Kidux Req.exe | CONNECT | — | 101.108.149.99:8080 | http://www.example.com:8080www.example.com:443 | TH | — | — | unknown |
2760 | Kidux Req.exe | CONNECT | — | 1.0.139.36:8080 | http://www.example.com:8080www.example.com:443 | TH | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2760 | Kidux Req.exe | 1.0.139.36:8080 | — | TOT Public Company Limited | TH | unknown |
2760 | Kidux Req.exe | 101.51.104.50:8080 | — | TOT Public Company Limited | TH | unknown |
2760 | Kidux Req.exe | 101.108.149.99:8080 | — | TOT Public Company Limited | TH | unknown |
2760 | Kidux Req.exe | 102.129.249.120:8080 | — | — | — | suspicious |
2760 | Kidux Req.exe | 101.4.136.34:81 | — | China Education and Research Network Center | CN | suspicious |
2760 | Kidux Req.exe | 1.20.203.92:8080 | — | TOT Public Company Limited | TH | unknown |
2760 | Kidux Req.exe | 1.10.153.242:8080 | — | TOT Public Company Limited | TH | unknown |
2760 | Kidux Req.exe | 1.179.144.182:80 | — | TOT Public Company Limited | TH | unknown |
2760 | Kidux Req.exe | 102.129.249.120:3128 | — | — | — | suspicious |
2760 | Kidux Req.exe | 101.109.255.246:44136 | — | TOT Public Company Limited | TH | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.proxyserverlist24.top |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2760 | Kidux Req.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2760 | Kidux Req.exe | Generic Protocol Command Decode | SURICATA STREAM FIN out of window |
2760 | Kidux Req.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (CONNECT) |
2760 | Kidux Req.exe | Generic Protocol Command Decode | SURICATA STREAM FIN out of window |
2760 | Kidux Req.exe | Generic Protocol Command Decode | SURICATA STREAM FIN out of window |
2760 | Kidux Req.exe | Generic Protocol Command Decode | SURICATA STREAM FIN out of window |
2760 | Kidux Req.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (CONNECT) |
2760 | Kidux Req.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2760 | Kidux Req.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (CONNECT) |
4 ETPRO signatures available at the full report