| File name: | Payout Receipt.pptx |
| Full analysis: | https://app.any.run/tasks/ababf26a-6781-4f22-88a2-a9bd8f7a3efe |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2024, 09:32:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| MIME: | application/vnd.openxmlformats-officedocument.presentationml.presentation |
| File info: | Microsoft PowerPoint 2007+ |
| MD5: | 9B2A454E1D8764CEF9CEEBC536B0A4C4 |
| SHA1: | 01D63E75CF02B1ACD2DFCB18F64BADBBD1E5F5A9 |
| SHA256: | 03F6F5E789A4E9A7E50CFE58614A63B7C47753C8B54DEB4CC3537743464E2FE1 |
| SSDEEP: | 6144:5pH4B11MAbivnEMrOjairk2vO4vNH/ItMEwjTgyVKK9a+:rk11nbaA3k2WaN94yI8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
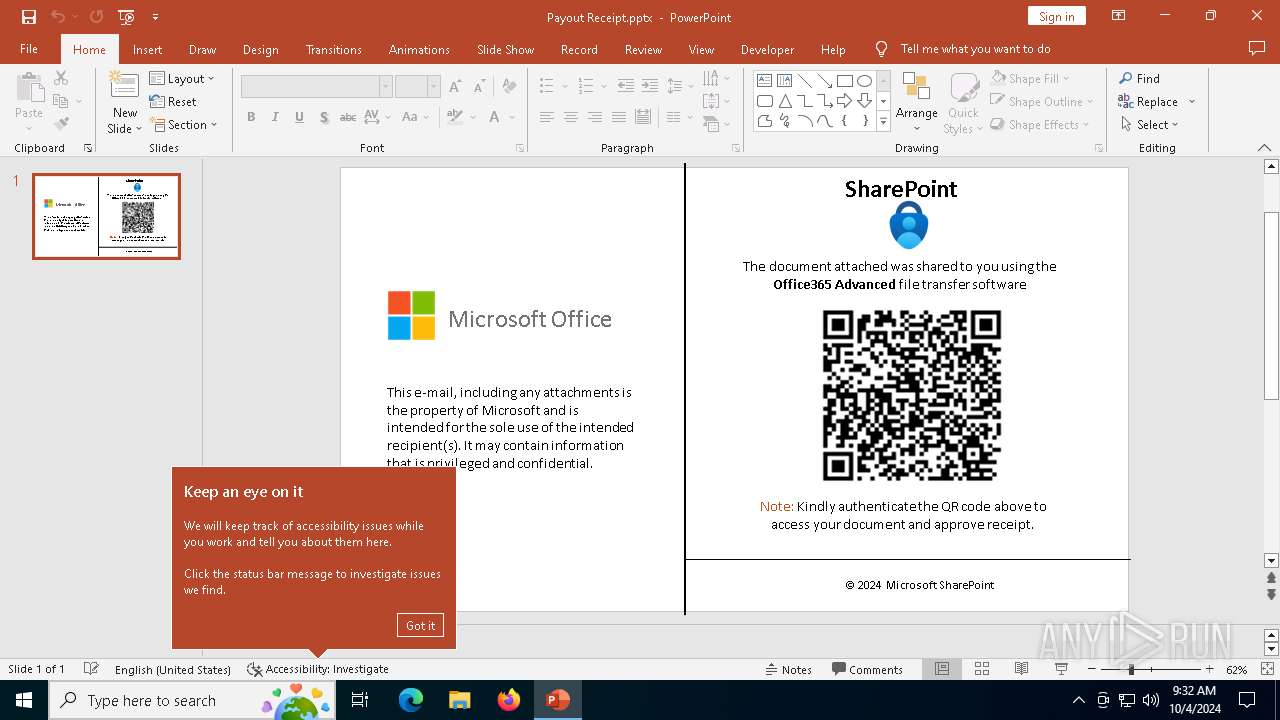
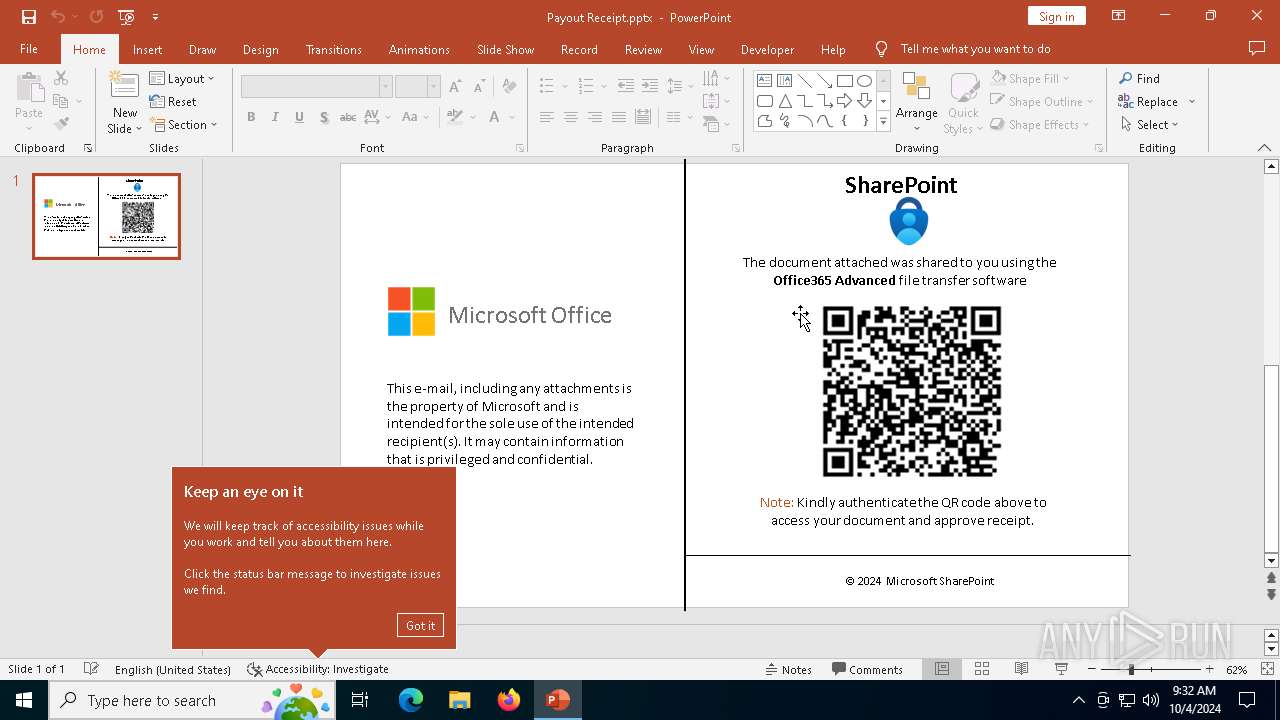
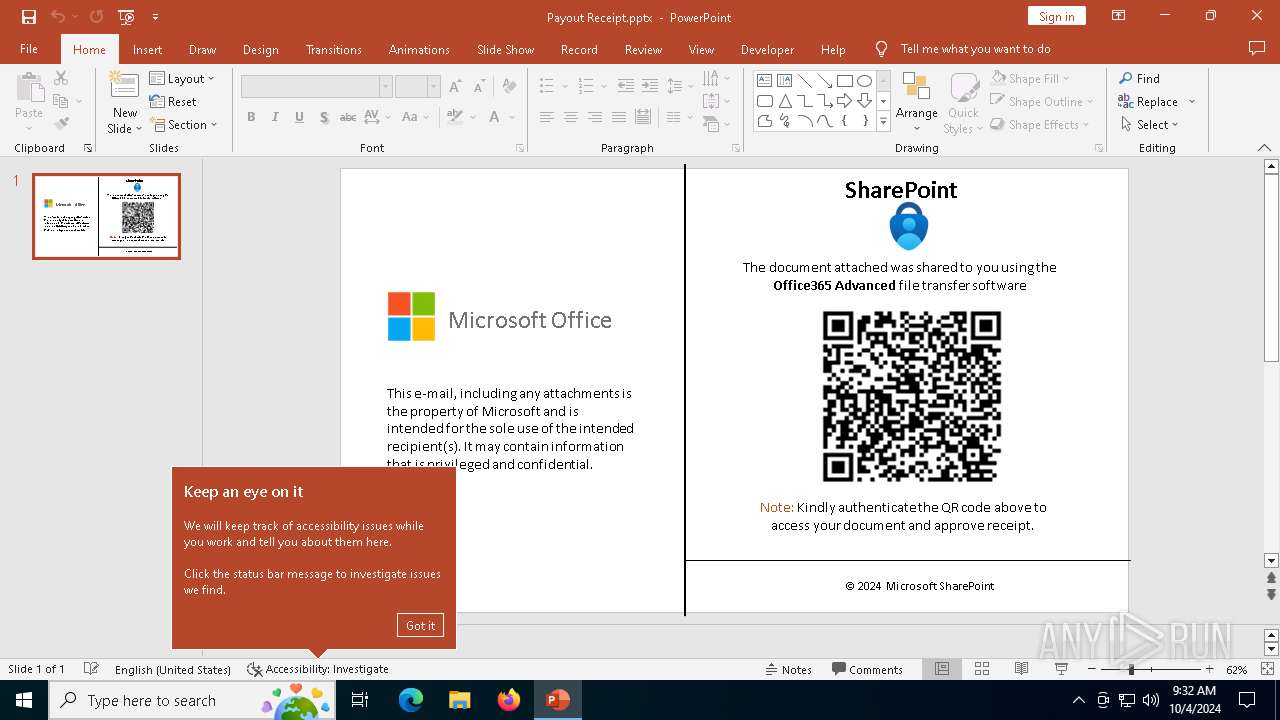
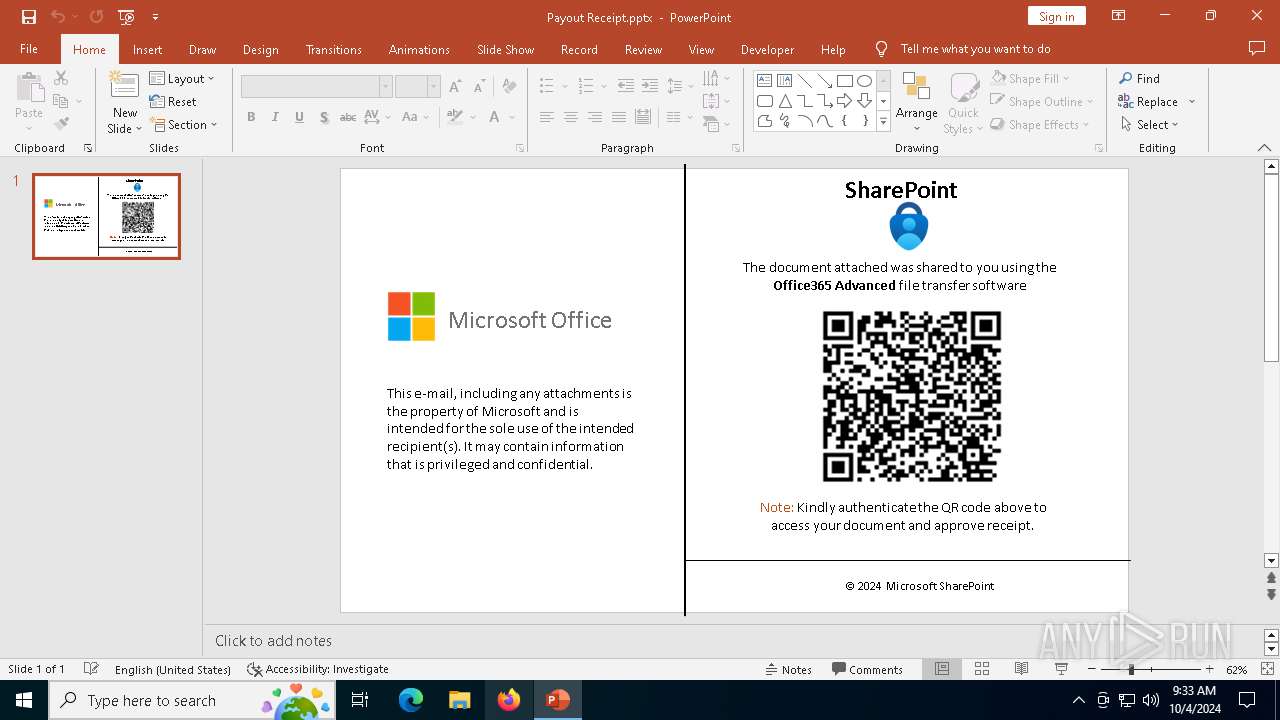
Detected QR code with redirect chain
- POWERPNT.EXE (PID: 2328)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .pptx | | | PowerPoint Microsoft Office Open XML Format document (87) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (10.5) |
| .zip | | | ZIP compressed archive (2.4) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xfabb30d7 |
| ZipCompressedSize: | 481 |
| ZipUncompressedSize: | 3599 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Creator: | Carl Hennrich |
XML
| LastModifiedBy: | Carl Hennrich |
|---|---|
| RevisionNumber: | 24 |
| CreateDate: | 2024:09:25 14:23:28Z |
| ModifyDate: | 2024:10:03 02:27:18Z |
| TotalEditTime: | 5.1 hours |
| Words: | 73 |
| Application: | Microsoft Macintosh PowerPoint |
| PresentationFormat: | Widescreen |
| Paragraphs: | 7 |
| Slides: | 1 |
| Notes: | 1 |
| HiddenSlides: | - |
| MMClips: | - |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: |
|
| Company: | - |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
131
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2328 | "C:\Program Files\Microsoft Office\Root\Office16\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\Payout Receipt.pptx" /ou "" | C:\Program Files\Microsoft Office\root\Office16\POWERPNT.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
11 593
Read events
11 250
Write events
324
Delete events
19
Modification events
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 3 |
Value: 011C08000000001000B24E9A3E01000000000000000300000000000000 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\POWERPNT\2328 |
| Operation: | write | Name: | 0 |
Value: 0B0E10BD08FE4EB4876E42B4904C62349137A5230046EE8AF88086C8C5ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5119812D2120C70006F0077006500720070006E0074002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (2328) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
5
Suspicious files
104
Text files
17
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:5F94FBE52FE2FA58DB625593C6F45279 | SHA256:469A3D132C49DD2CB05FF4008CCDE9B00C64AD1B14BFA24DB4F29005665B0688 | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\1BE89619-2F16-47CA-9E4A-9A2CDA849D93 | xml | |
MD5:F607E80ADA2A57387ABE53B1B30994B8 | SHA256:475D4FC2CDA82934A5D2690689B2CA734063460A13A60A3D9EB5A4D3E6E9F00D | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:3CE4719DBBE6D71AE257D70A1ADB2C9B | SHA256:559EE0C16A6138811604C99E7B8ED2B861FC228E63D3BAF2016DD7347E46D5F0 | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:3461ADBBB1CD67B05F1D7E90883AC992 | SHA256:C9A7778C8A75285A9A9386DE0764D119C54B8CA408F915EA65E30B48F3430F74 | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JAOWBI3APYAZOO2UBA0A.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\cab9C7E.tmp | compressed | |
MD5:E3C64173B2F4AA7AB72E1396A9514BD8 | SHA256:16C08547239E5B969041AB201EB55A3E30EAD400433E926257331CB945DFF094 | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\cab9C6C.tmp | compressed | |
MD5:66C5199CF4FB18BD4F9F3F2CCB074007 | SHA256:4A7DC4ED098E580C8D623C51B57C0BC1D601C45F40B60F39BBA5F063377C3C1F | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\cab9CD0.tmp | compressed | |
MD5:F913DD84915753042D856CEC4E5DABA5 | SHA256:AA03AFB681A76C86C1BD8902EE2BBA31A644841CE6BCB913C8B5032713265578 | |||
| 2328 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\PowerPoint\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:5F028BCDD586C5A18C93B1B52CCC7276 | SHA256:07760E4B405E905F76DE829AE362DF10FFFE4D2EF2FD15C6504E561A6CCDED99 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
82
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2328 | POWERPNT.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4744 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2328 | POWERPNT.EXE | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
2328 | POWERPNT.EXE | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
2328 | POWERPNT.EXE | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
2328 | POWERPNT.EXE | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
3836 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3300 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2328 | POWERPNT.EXE | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2356 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2328 | POWERPNT.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2328 | POWERPNT.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2328 | POWERPNT.EXE | 23.48.23.30:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
4324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |